Ad
A PROJECT REPORT ON SECURED FUZZY BASED ROUTING FRAMEWORK FOR DYNAMIC WIRELESS SENSOR NETWORKS
- 1. 1. INTRODUCTION 1.1 MOTIVATION The main motivation of the project is to improvise the security parameters for a wireless sensor networks and to regularize the multi-hop routing techniques. The proposed work is developed using a fuzzy based trust model which simultaneously consider multiple constrains and provides better security and energy conservation. Wireless sensor network exhibits various characteristics such as tree structured routing, computation and phased transmission periods, data aggregation mechanisms, in-network filtering methods and acceptable failures. Due to mobility in wireless sensor networks ,the harm of various malicious attacks based on the technique of replaying routing information is further exaggerated and the network behavior becomes aggressive. Although mobility concept is for efficient data collection, it generally increases the chance of communication between the actual sensor nodes and the attackers. The applications for WSNs are many and varied. They are used in commercial and industrial applications to monitor data that would be difficult or expensive to monitor using wired sensors. They could be deployed in wilderness areas, where they would remain for many years (monitoring some environmental variable) without the need to recharge/replace their power supplies. They could form a perimeter about a property and monitor the progression of intruders (passing information from one node to the next). A typical wireless sensor network consists of a base station and several nodes distributed or positioned in the environment of interest. Each node is expected to detect events of interest and estimate parameters that characterize these events. The resulting information at a node needs to be transmitted to the base station either directly or in “multi-hop” fashion involving automatic routing through several other nodes in the network. Implementation of such a network requires hardware components and corresponding software modules to program these components in a cooperative manner. 1
- 2. 1.2 PROBLEM DEFINITION Wireless sensor networks involve multi-hop routing and it offer minor security against identity deception through replaying routing information. Secure data aggregation is an important criterion that attracts serious research work. The factors responsible in such harsh wireless sensor networks are increased complexity, high overhead and poor link quality in case of various cryptographic techniques. 1.3 OBJECTIVE OF PROJECT The objective of this project was to develop a java program which provides energy-efficient routing and reliable trust using a fuzzification methods and to provide better security and energy conservation. To achieve this target, we have proposed an appropriate framework mechanisms. FBTARF(fuzzy based Trust aware routing framework) provides the effective solution against harmful attacks due to identity deception and it is the proposed method for security improvisation in dynamic wireless sensor networks. Using a fuzzy logic routing over a network is done and energy cost and trust values of sensor nodes are calculated. a packet is transferred from source to the sink node . 1.4 LIMITATIONS OF THE PROJECT • This project is limited only in finding the values Energy cost, Trust level and power level of each node but not the performance capacity of each node. • Transferring of files in text format is only supported but images cannot be transmitted. 1.5 ORGANIZATION OF DOCUMENTATION In this documentation, we have initially highlighted the definition and objectives of the project as well as the design of the project which is followed by implementation, testing, conclusion and Future Enhancements. 2
- 3. 2. LITERATURE SURVEY Literature survey is the most important step in software development process. Before developing the tool it is necessary to determine the time factor, economy and company strength. Once these things are satisfied, next step is to determine which operating system and language can be used for developing the tool. Once the programmers start building the tool, the programmers need lot of external support. This support can be obtained from senior programmers, from book or from web sites. Before building the system the above considerations are taken into an account for developing the proposed system. 2.1 INTRODUCTION Wireless sensor networks (WSN) are the domain mostly engaged in military surveillance and detection of forest fire. Battery-powered senor nodes are interconnected with tremendously limited processing capabilities in WSN. A sensor node or device connected in a WSN environment sends information to the destination through the multi-hop routing path within the coverage area of allotted radio communication range. This multi-hop routing often becomes victim for the suspicious malicious attacks. An attacker may intrude the nodes physically, collide with the sensor nodes during transmission, drop the data messages or misdirect messages in the intermediate route path or block the communication channel by jamming the radio interference. Due to identity inception, the attacker can launch various unidentifiable attacks and malicious intrusions which are hard to detect during the normal course of transmission. This research paper deals with various kinds of attacks where in the intruders mislead the network traffic and messages by identity deception through routing information change. In terms of security, WSN is one domain which is more vulnerable to various attacks. In order to achieve better security, several works have been proposed in the related area but the integration parameters for various attack detection and control are still in the initial stages. WSN exhibits various characteristics such as tree structured routing, computation and phased transmission periods, data aggregation mechanisms, in-network filtering methods and acceptable failures. Due to the mobility in wireless sensor networks, the harm of various malicious attacks based on the technique of replaying routing information is further exaggerated and the network behavior becomes aggressive. 3
- 4. Although mobility concept is for efficient data collection, it greatly increases the chance of communication between the actual sensor nodes and the attackers as shown in various applications. Minimizing energy conservation and the medium access layer arguments are the main criteria to be considered for data aggregation using distributed processing. For effective Routing analysis, data aggregation is the vital parameter. In data aggregation, the following steps are to be followed. Merging all the information from various sources, routing and removing the duplicate information, minimizing the transmission number and conserving the energy are the salient features of data aggregation. By means of data aggregation process, redundancy of data from other sensor nodes can be prohibited. Data Extraction is also possible from the raw data. Another important factor is sustaining high occurrence to preserve energy for a long lifetime in the network. Fig1:wireless sensor network 4
- 5. 2.2 EXISTING SYSTEM In Existing system, when the file send from base station in that situation hackers aggravated network conditions. A traditional cryptographic techniques effort does not address the severe problems. That time the file could be affected by hackers. So, the network will be damaged. An attacker may tamper nodes physically, create traffic collision with seemingly valid transmission, drop or misdirect messages in routes, or jam the communication channel by creating radio interference. 2.3 DISADVANTAGES High transmission overhead High data complexity Complex encryption process High bandwidth occupancy Poor reliability Poor data confidentiality 2.4 PROPOSED SYSTEM To overcome these problems, secured fuzzy based trust aware routing framework is implemented for the data aggregation process in WSN environment. To secure the wireless sensor networks and to regularize the multi-hop routing techniques, the present work h.as been designed and implemented. 2.5 ADVANTAGES OF PROPOSED SYSTEM The advantages of proposed system are: • It provides effective and efficient routing in the dynamic wireless sensor network environment. • It provides better security, energy conservation and packet delivery ratio. • Secured data aggregation is achieved through this framework mechanism 5
- 6. 3 ANALYSIS 3.1 SOFTWARE REQUIREMENTS SPECIFICATION: 3.1.1 User Requirements: Java Technology: Java technology is both a programming language and a platform. The Java Programming Language: The Java programming language is a high-level language that can be characterized by all of the following buzzwords: Simple Architecture neutral Object oriented Portable Distributed High performance With most programming languages, you either compile or interpret a program so that you can run it on your computer. The Java programming language is unusual in that a program is both compiled and interpreted. With the compiler, first you translate a program into an intermediate language called Java byte codes —the platform-independent codes interpreted by the interpreter on the Java platform. The interpreter parses and runs each Java byte code instruction on the computer. Compilation happens just once; interpretation occurs each time the program is executed. The following figure illustrates how this works. 6
- 7. Fig2: working of java You can think of Java bytecodes as the machine code instructions for the Java Virtual Machine (Java VM). Every Java interpreter, whether it’s a development tool or a Web browser that can run applets, is an implementation of the Java VM. Java bytecodes help make “write once, run anywhere” possible. You can compile your program into bytecodes on any platform that has a Java compiler. The bytecodes can then be run on any implementation of the Java VM. That means that as long as a computer has a Java VM, the same program written in the Java programming language can run on Windows 2000, a Solaris workstation, or on an iMac. The Java Platform: A platform is the hardware or software environment in which a program runs. We’ve already mentioned some of the most popular platforms like Windows 2000, Linux, Solaris, and MacOS. Most platforms can be described as a combination of the operating system and hardware. The Java platform differs from most other platforms in that it’s a software-only platform that runs on top of other hardware-based platforms. The Java platform has two components: • The Java Virtual Machine (Java VM) • The Java Application Programming Interface (Java API) You’ve already been introduced to the Java VM. It’s the base for the Java platform and is ported onto various hardware-based platforms. The Java API is a large collection of ready-made software components that provide many useful capabilities, such as graphical user interface (GUI) widgets. The Java API is grouped into libraries of related classes and interfaces; these libraries are 7
- 8. known as packages. The next section, What Can Java Technology Do?, highlights what functionality some of the packages in the Java API provide. The following figure depicts a program that’s running on the Java platform. As the figure shows, the Java API and the virtual machine insulate the program from the hardware. Fig3: The java platform Native code is code that after you compile it, the compiled code runs on a specific hardware platform. As a platform-independent environment, the Java platform can be a bit slower than native code. However, smart compilers, well-tuned interpreters, and just-in-time bytecode compilers can bring performance close to that of native code without threatening portability. Java provides more packages to develop all kind of applications and applets. Some of them are listed below. java.lang - handles all basic operations and contains the data types. java.io - handles all kinds of input and output operations. java.util - contains collection based classes and interfaces. java.awt - contains user interface components. java.awt.event - contains user interface component event listeners. java.awt.image - contains image handling classes and interfaces. 8
- 9. javax.swing - contains enhanced user interface components. javax.swing.event - contains event listeners of enhanced user interface components. Swings: Swing is a platform-independent, Model-View-Controller GUI framework for Java. It follows a single-threaded programming model, and possesses the following traits: Platform independence Swing is platform independent both in terms of its expression (Java) and its implementation (non-native universal rendering of widgets). Swing is the primary Java GUI widget toolkit. It is part of Sun Microsystems' Java Foundation Classes (JFC) — an API for providing a graphical user interface (GUI) for Java programs.Swing was developed to provide a more sophisticated set of GUI components than the earlier Abstract Window Toolkit. Swing provides a native look and feel that emulates the look and feel of several platforms, and also supports a pluggable look and feel that allows applications to have a look and feel unrelated to the underlying platform. The Swing Architecture Swing is a platform-independent, Model-View-Controller GUI framework for Java. It follows a single-threaded programming model, and possesses the following traits: Foundations Swing is platform independent both in terms of expression (Java) and implementation (Look-and-Feel). 9
- 10. Extensible Swing is a highly partitioned architecture, which allows for the "plugging" of various custom implementations of specified framework interfaces: Users can provide their own custom implementation(s) of these components to override the default implementations. In general, Swing users can extend the framework by extending existing (framework) classes and/or providing alternative implementations of core components. Customizable Given the programmatic rendering model of the Swing framework, fine control over the details of rendering of a component is possible in Swing. As a general pattern, the visual representation of a Swing component is a composition of a standard set of elements, such as a "border", "inset", decorations, etc. Typically, users will programmatically customize a standard Swing component (such as a JTable) by assigning specific Borders, Colors, Backgrounds, opacities, etc., as the properties of that component. The core component will then use these properties (settings) to determine the appropriate renderers to use in painting its various aspects. However, it is also completely possible to create unique GUI controls with highly customized visual representation. Configurable Swing's heavy reliance on runtime mechanisms and indirect composition patterns allows it to respond at runtime to fundamental changes in its settings. For example, a Swing-based application can change its look and feel at runtime. Further, users can provide their own look and feel implementation, which allows for uniform changes in the look and feel of existing Swing applications without any programmatic change to the application code. Lightweight GUI Swing's configurability is a result of a choice not to use the native host OS's GUI controls for displaying itself. Swing "paints" its controls programmatically through the use of Java 2D APIs, rather than calling into a native user interface 10
- 11. toolkit. Thus, a Swing component does not have a corresponding native OS GUI component, and is free to render itself in any way that is possible with the underlying graphics APIs. However, at its core every Swing component relies on an AWT container, since (Swing's) JComponent extends (AWT's) Container. This allows Swing to plug into the host OS's GUI management framework, including the crucial device/screen mappings and user interactions, such as key presses or mouse movements. Swing simply "transposes" its own (OS agnostic) semantics over the underlying (OS specific) components. So, for example, every Swing component paints its rendition on the graphic device in response to a call to component. Paint (), which is defined in (AWT) Container. But unlike AWT components, which delegated the painting to their OS-native "heavyweight" widget, Swing components are responsible for their own rendering. This transposition and decoupling is not merely visual, and extends to Swing's management and application of its own OS-independent semantics for events fired within its component containment hierarchies. Generally speaking, the Swing Architecture delegates the task of mapping the various flavors of OS GUI semantics onto a simple, but generalized, pattern to the AWT container. Building on that generalized platform, it establishes its own rich and complex GUI semantics in the form of the JComponent model. Loosely-Coupled and MVC Swing library makes heavy use of the Model/View/Controller software design pattern, which conceptually decouples the data being viewed from the user interface controls through which it is viewed. Because of this, most Swing components have associated models (which are specified in terms of Java interfaces), and the programmer can use various default implementations or provide their own. The framework provides default implementations of model interfaces for all of its concrete components. The view component of a Swing JComponent is the object used to graphically "represent" the conceptual GUI control. A distinction of Swing, as a GUI framework, is in its reliance on programmatically-rendered GUI controls (as opposed to the use of the native host OS's GUI controls). Prior to Java 6 Update 10, this 11
- 12. distinction was a source of complications when mixing AWT controls, which use native controls, with Swing controls in a GUI (see Mixing AWT and Swing components). Finally, in terms of visual composition and management, Swing favors relative layouts (which specify the positional relationships between components) as opposed to absolute layouts (which specify the exact location and size of components). This bias towards "fluid"' visual ordering is due to its origins in the applet operating environment that framed the design and development of the original Java GUI toolkit. (Conceptually, this view of the layout management is quite similar to that which informs the rendering of HTML content in browsers, and addresses the same set of concerns that motivated the former.) Features of Swing components: i. Swing buttons and labels can display images instead of, or in addition to text. ii. User can easily add or change the borders drawn around most swing components. iii. Users can easily change the behavior or appearance of a swing component by either invoking methods on it or creating a subclass of it. iv. Swing components don’t have to be rectangular, buttons, for e.g., can be round. v. Assistive technologies such as screen renders can get information from swing components. vi. Swing let’s to specify which look and feel a program’s GUI uses. Swing components are implemented with no native code and aren’t restricted to the least common denominator. The Swing API is flexible, powerful and immense. It is available in Two forms: 1. As a core part of the Java2 platform 2. JFC1.1 12
- 13. JFrame: The JFrame class is slightly incompatible with Frame. Like all other JFC/Swing top-level containers, a JFrame contains a JRootPane as its only child. The content pane provided by the root pane should, as a rule, contain all the non-menu components displayed by the JFrame. This is different from the AWT Frame case. JPanel: JPanel is an extension of Jcomponent used for grouping together other components. It gets most of its implementations from its superclasses. JButton: JButton is a push button that is a replacement for java.awt.Button. Like AWT buttons, Swing button fire action events when they activated. An action Listener can register with a button, and the listener’s action performed method will be invoked whenever the button is activated. JTextField: JTextField allow the user to enter a single line of text, scrolling the text if its size exceeds the physical size of the field. Horizontal alignment either LEFT, RIGHT or CENTER can be specified for a text field’s text. JTabbedPane: The JTabbedPane is used for creating your own tabbed pane with tab activation components, very quickly. 13
- 14. Relationship to AWT Fig4: AWT and Swing class hierarchy Since early versions of Java, a portion of the Abstract Window Toolkit (AWT) has provided platform-independent APIs for user interface components. In AWT, each component is rendered and controlled by a native peer component specific to the underlying windowing system. By contrast, Swing components are often described as lightweight because they do not require allocation of native resources in the operating system's windowing toolkit. The AWT components are referred to as heavyweight components. Much of the Swing API is generally a complementary extension of the AWT rather than a direct replacement. In fact, every Swing lightweight interface ultimately exists within an AWT heavyweight component because all of the top-level components in Swing (JApplet, JDialog, JFrame, and JWindow) extend an AWT top- level container. Prior to Java 6 Update 10, the use of both lightweight and heavyweight components within the same window was generally discouraged due to Z-order incompatibilities. However, later versions of Java have fixed these issues, and both Swing and AWT components can now be used in one GUI without Z-order issues. The core rendering functionality used by Swing to draw its lightweight components is provided by Java 2D, another part of JFC. 14
- 15. 3.1.2 Software Requirements • JAVA SWINGS • JFRAME BUILDER • WINDOWS XP / WINDOWS 7 3.1.3 Hardware Requirements SYSTEM : Pentium Dual-Core CPU E5400 2.70GHZ HARD DISK : 40 GB FLOPPY DRIVE : 1.44 MB MONITOR : 15 VGA colour MOUSE : Logitech. RAM : 1GB 3.2 System Requirements Analysis 3.2.1 Feasibility Study: Once the proposals are generated, they are evaluated. Evaluation looks at the technical, operational and economic feasibility of the project. All are feasible within the presence of unlimited resources and time. Unfortunately the development of a computer based system is more likely to be plagued by a scarcity of resources and difficult delivery dates. It is both necessary and prudent to evaluate the feasibility of a project at the earliest possible time. Months and years of effort, thousands or millions of dollars and untold professional embarrassment can be averted if an ill conceived system is recognized early in the definition phase. 3.2.2 Technical Feasibility: This evaluation determines whether the technology needed for the proposed system is available, and how it can be integrated within the organization. For proposed system, the minimum requirements needed to develop the system are found. 15
- 16. Since this system uses graphics, more processing speed and memory are needed. The organization has the expertise to use it. 3.2.3 Operational Feasibility: Operational feasibility covers two aspects. One is a technical performance aspect and the other is acceptance within the organization. Technically, the proposed system has a good operational feasibility because of the availability of the resources such as processing speed and memory. The proposed system will definitely deliver the right information in right time. Coming to acceptance within the organization, it will fit in with the current operations and no additional skills are required and are acceptable to the current users. 3.2.4Economic Feasibility: Economic feasibility concerns returns from investments in a project. It determines whether it is worthwhile to invest the money in the proposed project or whether something else should be done with it. Some organizations, especially those with larger projects. Place great emphasis on economic analysis. 3.3 CONTENT DIAGRAM OF PROJECT 16
- 17. Fig5: Architecture diagram for FBTARF 3.4 FLOWCHART 17
- 19. 4 DESIGN 4.1 INTRODUCTION The design phase is concerned with the physical construction of the system. The main objective of this phase is to transform the previously defined requirements into a complete and detailed set of specifications which will be used during the next phase. Some of the activities that need to take place during the design phase are: i. Design the application ii. Design and integrate the network iii. Create a contingency plan iv. Start a Maintenance, Training and Operations plan v. Review the design vi. Establish a transition strategy vii. Deliver the System Design Document viii. Review final design. 4.2 UML DIAGRAMS UML is a language used for • visualizing, • specifying, • constructing and • documentary of the system 4.2.1 Use Case Diagram Use Case diagrams identify the functionality provided by the system (use cases), the users who interact with the system (actors), and the association between the users and the functionality. In other words an Use Case diagram is a diagram that has set of use cases, actors and their relationships. Graphical Notation The basic components of an Use Case diagrams are the Actor, the Use Case, and the Association. 19
- 20. Fig 7: Use case diagram 4.2.2 Sequence Diagram Sequence diagrams document the interactions between classes to achieve a result, such as an usecase. Because UML is designed for Object-Oriented Programming, these communications between classes are known as messages. The Sequence diagram lists objects horizontally, and time vertically, that represents the time ordering of messages. Graphical Notation 20
- 21. In a Sequence Diagram, Classes and Actors are listed as columns, with vertical lifelines indicating the lifetime of the object over time. Fig 8: Sequence diagram 4.2.3 Activity Diagram 21
- 22. Activity diagrams are graphical representations of workflows of stepwise activities and actions with support for choice, iteration and concurrency. In the Unified Modeling Language, activity diagrams can be used to describe the business and operational step-by-step workflows of components in a system. An activity diagram shows the overall flow of control. Graphical Notation: Activity diagrams are constructed from a limited number of shapes, connected with arrows. Arrows run from the start towards the end and represent the order in which activities happen.An activity diagram shows the flow from activity to activity. An activity is an ongoing non atomic execution within a state machine. Activity diagrams commonly contain Activity states and action states Transitions Objects 22
- 23. Fig 9: Activity diagram 23
- 24. 4.3 INPUT DESIGN The input design is the link between the information system and the user. It comprises the developing specification and procedures for data preparation and those steps are necessary to put transaction data in to a usable form for processing can be achieved by inspecting the computer to read data from a written or printed document or it can occur by having people keying the data directly into the system. The design of input focuses on controlling the amount of input required, controlling the errors, avoiding delay, avoiding extra steps and keeping the process simple. The input is designed in such a way so that it provides security and ease of use with retaining the privacy. Input Design considered the following things: What data should be given as input? How the data should be arranged or coded? The dialog to guide the operating personnel in providing input. Methods for preparing input validations and steps to follow when error occur. OBJECTIVES • Input Design is the process of converting a user-oriented description of the input into a computer-based system. This design is important to avoid errors in the data input process and show the correct direction to the management for getting correct information from the computerized system. • It is achieved by creating user-friendly screens for the data entry to handle large volume of data. The goal of designing input is to make data entry easier and to be free from errors. The data entry screen is designed in such a way that all the data manipulates can be performed. It also provides record viewing facilities. 24
- 25. • When the data is entered it will check for its validity. Data can be entered with the help of screens. Appropriate messages are provided as when needed so that the user can do it. 4.4 OUTPUT DESIGN A quality output is one, which meets the requirements of the end user and presents the information clearly. In any system results of processing are communicated to the users and to other system through outputs. In output design it is determined how the information is to be displaced for immediate need and also the hard copy output. It is the most important and direct source information to the user. Efficient and intelligent output design improves the system’s relationship to help user decision-making. The output form of an information system should accomplish one or more of the following objectives. Convey information about past activities, current status or projections of the future Signal important events, opportunities, problems, or warnings. Trigger an action. Confirm an action. 4.5 MODULE DESIGN & ORGANIZATION MODULES DESCRIPTION 1. Transfer File 2. Energy Watcher 3. Trust Manager 4. Fuzzy routing 5. Receive File 1.Transfer File Module 25
- 26. In this module, Analysis the Shortest Path algorithm independently routes each logical link on a physical path with the minimum number of hops in trusted network basis. Since we are assuming that every physical link fails with the same probability, the failure probability of path is minimized when it is routed over the shortest path. Hence, under the algorithm Shortest Path, each light- path greedily takes the most reliable route and transfers the file. 2. Energy Watcher Module In this module Cluster-based WSNs allows for the great savings of energy and bandwidth through aggregating data from children nodes and performing routing and transmission for children nodes. In a cluster-based WSN, the cluster headers themselves form a sub-network, after certain data reach a cluster header, the aggregated data will be routed to a base station only through such a subnetwork consisting of the cluster headers. Our framework can then be applied to this sub- network to achieve secure routing for cluster based WSNs. Here ,for transferring k-bit message over a distance of d, the energy consume is calculated by the radio model. Etrans=Eelec(k,d)+Eamp(k,d) =k*Eelec+k*€fs =k*Eelec+k*€mp Where, k=The number of forwarded bits for a distance d Eelec=The transmitter circuitry dissipation per bit €=The transmitter amplifier dissipation per bit The Receiving cost is computed by the following equation Erecie=k*Eelec Model Equation for Total Energy consume Etotal=Etrans+Eprocess+Esense 26
- 27. Where Etotal=Total network Energy cost Etrans=The transmission cost Erecie=The receiving cost Eprocess=The Energy cost while processing Esense=The Energy cost while sensing Fig 10: radio model-energy consumption 3. Trust Manager Module Trust Manager encourages a node to choose another route when its current route frequently fails to deliver data to the base station. Though only those legal neighboring nodes of an attacker might have correctly identified the adversary. Trust value is calculated by reliable and unreliable of the nodes For instance, the cluster possess 5 sensor nodes i.e., n1, n2, n3, n4 and n5. Then the distance between the successive nodes is calculated as d1, d2, d3, d4 and d5. The average of the values is calculated, 1 and compared with threshold value, δ1 of the cluster. Forƞ instance, the cluster possesses 5 sensor nodes i.e., n1, n2, n3, n4 and n5 and the difference between the successive readings of every node is rl, r2, r3, r4 and r5. Then the average value 2 of the readings is compared with its threshold value, 02 of theƞ cluster. If 1> δ1 and 2< δ2, then the nodes are unreliable. If 1< δ1and 2< δ2,ƞ ƞ ƞ ƞ 27
- 28. then the nodes are reliable. Two counters called reliable sensing watcher and unreliable sensing watcher are maintained, for the values of 2 and δ2. It indicates theƞ reliability of the sensor node. The sensor nodes can be classified as malicious or compromised node based on the reliability factor. Thus it helps in maintaining the network data away from that of the malicious nodes. The RELIABLITY VALUE is estimated using the formula RVi=RSWi-URWi/RSWi+URWi Where RVi=The reliable value of node(1<i<k) RSWi=The reliable sensing watch of node i URWi=The unreliable sensing watch of node i Therefore, the TOTAL TRUST VALUE of the node i is calculated as follows TTV=W1Ri+W2PDRi+W3RVi/W1+W2+W3 Where TTV=Total Trust value PDRi=Packet Delivery Rate of node(1<i<k) Ri=Residual Energy value of node(1<i<k) 4. FUZZY ROUTING Module In this module, the networks embedded on the physical fiber topology. However, assessing the performance reliability achieved independent logical links can share the same physical link, which can lead to correlated failures. Mainly, we focus on assessing the reliability of energy level and trusted network by using a fuzzy logic The rule description is characterized by a membership function which are effortlessly implemented by fuzzy conditional statements.if the precursor is true to some degree of membership then the resulting is also true to that same degree. For the three inputs: distance, power consumed, and trust the resulting possibilities are BestNode,WorstNode and NormalNode.Here the input can take two values: Less and High. 28
- 29. The final decision is made on the basis of output of the intersection of the equivalent members of the fuzzy sets of the three parameters: distance, power consumed and trust value as shown in the following table fig:Fuzzy rules 5. RECEIVE FILE Module This module will receive file at the sink node that has been transferred which is used for the client to view the text in a readable format. 29
- 30. 5 IMPLEMENTATION & RESULTS 5.1 INTRODUCTION Implementation is the stage of the project when the theoretical design is turned out into a working system. Thus it can be considered to be the most critical stage in achieving a successful new system and in giving the user, confidence that the new system will work and be effective. The implementation stage involves careful planning, investigation of the existing system and it’s constraints on implementation, designing of methods to achieve changeover and evaluation of changeover methods. During this phase, the system will be installed and evaluated in the Organization’s operational environment. Key security activities for this phase include: i. Integrate the information system into its environment; ii. Plan and conduct system certification activities in synchronization with testing of security controls; and iii. Complete system accreditation activities. Core Functions: Simple programs that demonstrate basic commands. These are included with the java programming environment. if (conditional) and ==, !=, <, > (comparison operators) if, which is used in conjunction with a comparison operator, tests whether a certain condition has been reached, such as an input being above a certain number. The format for an if test is: if (someVariable > 50) { // do something here 30
- 31. } The program tests to see if some Variable is greater than 50. If it is, the program takes a particular action. Put another way, if the statement in parentheses is true, the statements inside the brackets are run. If not, the program skips over the code. The brackets may be omitted after an if statement. If this is done, the next line (defined by the semicolon) becomes the only conditional statement. if / else if/else allows greater control over the flow of code than the basic if statement, by allowing multiple tests to be grouped together. For example, an analog input could be tested and one action taken if the input was less than 500, and another action taken if the input was 500 or greater. The code would look like this: if (Input < 500) { // action A } else { // action B } else can proceed another if test, so that multiple, mutually exclusive tests can be run at the same time. Note that an else if block may be used with or without a terminating else block and vice versa. An unlimited number of such else if branches are allowed. Another way to express branching, mutually exclusive tests, is with the switch case statement. 31
- 32. Semicolon Used to end a statement. Example int a = 13; Comments Comments are lines in the program that are used to inform yourself or others about the way the program works. They are ignored by the compiler, and not exported to the processor. Comments only purpose are to help you understand (or remember) how your program works or to inform others how your program works. There are two different ways of marking a line as a comment: Example x = 5; // This is a single line comment. Anything after the slashes is a // comment to the end of the line Define #define is a useful C component that allows the programmer to give a name to a constant value before the program is compiled.The compiler will replace references to these constants with the defined value at compile time. This can have some unwanted side effects though, if for example, a constant name that had been #defined is included in some other constant or variable name. In that case the text would be replaced by the #defined number (or text). 32
- 33. In general, the const keyword is preferred for defining constants and should be used instead of #define. Syntax #define constantName value Example #define ledPin 3 // The compiler will replace any mention of ledPin with the value 3 at compile time. Curly Braces Curly braces (also referred to as just "braces" or as "curly brackets") are a major part of the java programming language. They are used in several different constructs, outlined below, and this can sometimes be confusing for beginners. An opening curly brace "{" must always be followed by a closing curly brace "}". This is a condition that is often referred to as the braces being balanced. Just select a brace, or even click the insertion point immediately following a brace, and its logical companion will be highlighted. Beginning programmers, and programmers coming to C from the BASIC language often find using braces confusing or daunting. After all, the same curly braces replace the RETURN statement in a subroutine (function), the ENDIF statement in a conditional and the NEXT statement in a FOR loop. Because the use of the curly brace is so varied, it is good programming practice to type the closing brace immediately after typing the opening brace when inserting a construct which requires curly braces. Then insert some carriage returns between your braces and begin inserting statements. Your braces, and your attitude, will never become unbalanced. Unbalanced braces can often lead to cryptic, impenetrable compiler errors that can sometimes be hard to track down in a large program. Because of their varied 33
- 34. usages, braces are also incredibly important to the syntax of a program and moving a brace one or two lines will often dramatically affect the meaning of a program. The main uses of curly braces Functions void myfunction(datatype argument) { statements(s) } Loops while (boolean expression) { statement(s) } do { statement(s) } while (boolean expression); for (initialisation; termination condition; incrementing expr) { statement(s) } Data types: Void The void keyword is used only in function declarations. It indicates that the function is expected to return no information to the function from which it was called. 34
- 35. unsigned int Description The Due stores a 4 byte (32-bit) value, ranging from 0 to 4,294,967,295 (2^32 - 1). The difference between unsigned ints and (signed) ints, lies in the way the highest bit, sometimes refered to as the "sign" bit, is interpreted. In the Arduino int type (which is signed), if the high bit is a "1", the number is interpreted as a negative number, and the other 15 bits are interpreted with 2's complement math. Syntax unsigned int var = val; • var - your unsigned int variable name • val - the value you assign to that variable Example • unsigned int ledPin = 13; 5.2 EXPLANATION OF KEY FUNCTIONS 5.2.1 Basic Design of a FBTARF The FBTARF is created using the JTabbedPane. This Component includes three panels namely Transfer file, Energy Watcher and Trust Manager. The syntax for creating the FBTARF using tabbed pane is: JTabbedPane tabbedpane = new JTabbedPane(); 5.2.2 Accessing Notepad files through Java 35
- 36. The sensing data of a sensor node can be saved into the notepad file and can be accessed by browsing the file and this file is send to the sink node by using fuzzy based routing. The notepad files can be accessed by the following syntax JFileChooser chooser = new JFileChooser(); File f = new File(new File("").getCanonicalPath()); File field = chooser.getSelectedFile(); 5.2.3 Accessing EnergyWatcher through Java Here to calculate the total energy cost of a wireless sensor network a EnergyWatcher class is invoked by using the following syntax EnergyWatcher e= new EnergyWatcher (); new EnergyWatcher (); By accessing this class we can calculate the transmission, receiving and total energy cost of a wireless sensor network is calculated. 5.2.4 Accessing TrustManager through Java Here to calculate the trust values of a wireless sensor network a TrustManager class is invoked by the following syntax TrustManager e= new TrustManager(); new TrustManager(); By accessing this class we can calculate the trust values of a wireless sensor network and the source file is routed to the sensor node whose trust value is high by considering the node as best node or normal node. 36
- 37. 5.3METHOD OF IMPLEMENTATION import java.awt.Color; import java.awt.Container; import java.awt.Font; import java.awt.Image; import java.awt.Toolkit; import java.awt.event.ActionEvent; import java.awt.event.ActionListener; import java.awt.event.KeyEvent; import java.io.BufferedInputStream; import java.io.BufferedOutputStream; import java.io.BufferedReader; import java.io.BufferedWriter; import java.io.DataInputStream; import java.io.File.*; import java.io.IOException; import java.io.InputStreamReader; import java.io.PrintStream; import javax.swing.ImageIcon; import javax.swing.JButton; import javax.swing.JFileChooser; import javax.swing.JFrame; import javax.swing.JLabel; import javax.swing.JOptionPane; 37
- 38. import javax.swing.JPanel; import javax.swing.JScrollPane; import javax.swing.JTextArea; import javax.swing.JTextField; import java.awt.BorderLayout; import java.util.Random; import java.util.*; class FBTARF extends JFrame { public FBTARF() { final JFrame frame = new JFrame("SECURED FUZZY BASED ROUTING FRAMEWORK FOR DYNAMIC WIRELESS SENSOR NETWORKS"); frame.setSize(815,750); frame.setVisible(true); frame.setDefaultCloseOperation(JFrame.EXIT_ON_CLOSE); frame.getContentPane().setLayout(new GridLayout(1,1)); frame.getContentPane().setLayout(new BorderLayout()); JTabbedPane tabbedPane = new JTabbedPane(JTabbedPane.TOP); tabbedPane.addTab("FILE TRANSFER",new source()); tabbedPane.addTab("ENERGY WATCHER",new EnergyWatcher()); tabbedPane.addTab("TRUST MANAGER", new TrustManager()); frame.getContentPane().add(tabbedPane); } private static JPanel makePanel(String text) { JPanel p = new JPanel(); p.add(new Label(text)); p.setLayout(new GridLayout(1,1)); return p; } Public source() { greengr = new ImageIcon(this.getClass().getResource("bgc.png")); back.setIcon(greengr); 38
- 39. back.setBounds(0,-140,650, 750); BorderLayout b=new BorderLayout(); setLayout(b); setSize(815,750); //jf.setResizable(false); setBackground(new Color(51,102,0)); bf.setIcon(new javax.swing.ImageIcon("SOURCE.png")); bf.setBounds(0, 0, 799, 699); T1a.setBounds(65, 5, 650,45); T1a.setFont(f); T1a.setForeground(Color.white); T1b.setBounds(175, 40, 450,45); T1b.setFont(f); T1b.setForeground(Color.white); TitledBorder leftBorder = BorderFactory.createTitledBorder("File Transmition"); leftBorder.setTitleJustification(TitledBorder.LEFT); leftButton = new JLabel(); leftButton.setBorder(leftBorder); leftButton.setBounds(70,140,500,350); leftBorder.setTitleColor(Color.ORANGE); TitledBorder leftBorder1 = BorderFactory.createTitledBorder("Proxy Question"); leftBorder.setTitleJustification(TitledBorder.LEFT); leftBorder1.setTitleColor(Color.ORANGE); T2.setBounds(150, 280, 250,45); T2.setFont(f2); T2.setForeground(Color.LIGHT_GRAY); txt1.setBounds(30, 350, 350,40); txt1.setFont(f1); T4.setBounds(225, 540, 250,45); T4.setFont(f2); T4.setForeground(Color.RED); txt2.setBounds(220, 595, 250,30); txt2.setForeground(Color.BLUE); 39
- 40. txt2.setFont(f1); proposed.setIcon(new javax.swing.ImageIcon("Proposal.png")); proposed.setBounds(580,220,180,50); proposed.setFont(f3); proposed.setForeground(new Color(120,0,0)); btn.setIcon(new javax.swing.ImageIcon("send.png")); btn.setBounds(485,625,180,50); btn.setFont(f3); btn.setForeground(new Color(120,0,0)); btn1.setIcon(new javax.swing.ImageIcon("browse.png")); btn1.setBounds(120,420,180,50); btn1.setFont(f3); btn1.setForeground(new Color(120,0,0)); txt.setBounds(260,150,180,25); txt.setForeground(Color.BLUE); txt.setFont(f1); pane.setBounds(398, 275, 375, 345); tf.setColumns(20); tf.setForeground(Color.MAGENTA); tf.setFont(f1); tf.setRows(10); tf.setName("tf"); pane.setName("pane"); pane.setViewportView(tf); jp.setBounds(30,200,350,480); jp.setBackground(new Color(102,102,102)); jp1.setBounds(390,200,390,480); jp1.setBackground(new Color(102,102,102)); btn1.addActionListener(this); btn.addActionListener(this); btn1.setMnemonic(KeyEvent.VK_B); btn.setMnemonic(KeyEvent.VK_S); proposed.addActionListener(this); txt2.setEnabled(false); 40
- 41. show(); add(txt1); add(btn); add(proposed); add(T2); add(T4); add(pane,BorderLayout.CENTER); add(btn1); add(jp); add(jp1); add(bf); } public void actionPerformed(ActionEvent e) { DataInputStream input; BufferedInputStream bis; BufferedOutputStream bos = null; BufferedWriter writer = null; int in; String str="MobileTerminal,Foriegn Agent A,Gateway FA A"; byte[] byteArray=str.getBytes(); StringBuffer buffer = new StringBuffer(); String strLine = null; String newline = "n"; if (e.getSource()== btn1) { JFileChooser chooser = new JFileChooser(); try { File f = new File(new File("").getCanonicalPath()); chooser.setSelectedFile(f); } catch (IOException e1) {} chooser.showOpenDialog(btn1); int retval = chooser.showOpenDialog(btn1); 41
- 42. if (retval == JFileChooser.APPROVE_OPTION){ File field = chooser.getSelectedFile(); txt1.setText(field.getAbsolutePath()); } File curFile = chooser.getSelectedFile(); try{ FileInputStream fstream = new FileInputStream(curFile); DataInputStream ins = new DataInputStream(fstream); BufferedReader br = new BufferedReader(new InputStreamReader(ins)); while ((strLine = br.readLine()) != null){ System.out.println (strLine); buffer.append(strLine+ "n"); } tf.setText(buffer.toString()); System.out.println("THE ORIGINAL FILE SIZE"+tf.getText().trim().length()); }catch (Exception e1){ System.err.println("Error: " + e1.getMessage()); } } if(e.getSource()== btn) { if(send=="proposed"){ Socket client = null; try { client = new Socket(txt.getText().trim(), 4000); bos = new BufferedOutputStream(client.getOutputStream()); byteArray =(send+tf.getText()).getBytes(); bos.write(byteArray, 0, byteArray.length); bos.flush(); bos.close(); client.close(); 42
- 43. } catch(UnknownHostException e1){ e1.printStackTrace(); }catch(Exception e1){} finally { } } else{ JOptionPane.showMessageDialog(null,"Please,Select proposal system and then send!","MessageBox",1); } } if(e.getSource()== proposed) { send="proposed"; } } public EnergyWatcher() { GridBagLayout gbag=new GridBagLayout(); GridBagConstraints gbc=new GridBagConstraints(); setLayout(gbag); JLabel heading=new JLabel("ENERGY COST CALCULATION"); JLabel dlab1=new JLabel("Enter distance for node1 and its neighbour"); JLabel dlab2=new JLabel("Enter distance for node2 and it's neighbour"); JLabel dlab3=new JLabel("Enter distance for node3 and it's neighbour"); JLabel dlab4=new JLabel("Enter distance for node4 and it's neighbour"); JLabel dlab5=new JLabel("Enter distance for node5 and it's neighbour"); JLabel dlab6=new JLabel("Enter distance for node6 and it's neighbour"); JLabel dlab7=new JLabel("Enter distance for node7 and it's neighbour"); JLabel dlab8=new JLabel("Enter distance for node8 and it's neighbour"); JLabel dlab9=new JLabel("Enter distance for node9 and it's neighbour"); JLabel dlab10=new JLabel("Enter distance for node10 and it's neighbour"); JLabel k=new JLabel("Enter no. of bits to be transfered"); JLabel dthr=new JLabel("Enter the threshold distance"); 43
- 44. JLabel model=new JLabel("The model used for routing is"); JLabel transmission=new JLabel("The Transmission energy cost is"); JLabel recieve=new JLabel("The Recieving Energy cost is"); JLabel total=new JLabel("The Total Energy cost is"); d0=new JTextField(10); d1=new JTextField(10); d2=new JTextField(10); d3=new JTextField(10); d4=new JTextField(10); d5=new JTextField(10); d6=new JTextField(10); d7=new JTextField(10); d8=new JTextField(10); d9=new JTextField(10); d10=new JTextField(10); k1=new JTextField(10); b1=new JButton("CHECK&COMPUTE"); m1=new JTextField(25); te=new JTextField(10); re=new JTextField(10); tot=new JTextField(10); gbc.weighty=25.0; gbc.gridwidth=GridBagConstraints.REMAINDER; gbc.anchor=GridBagConstraints.NORTH; gbag.setConstraints(heading,gbc); gbc.gridwidth=GridBagConstraints.RELATIVE; gbag.setConstraints(k,gbc); gbc.gridwidth=GridBagConstraints.REMAINDER; gbag.setConstraints(k1,gbc); gbc.gridwidth=GridBagConstraints.RELATIVE; gbag.setConstraints(dthr,gbc); gbc.gridwidth=GridBagConstraints.REMAINDER; gbag.setConstraints(d0,gbc); gbc.gridwidth=GridBagConstraints.RELATIVE; 44
- 47. add(d3); add(dlab4); add(d4); add(dlab5); add(d5); add(dlab6); add(d6); add(dlab7); add(d7); add(dlab8); add(d8); add(dlab9); add(d9); add(dlab10); add(d10); add(b1); add(model); add(m1); add(transmission); add(te); add(recieve); add(re); add(total); add(tot); b1.addActionListener(this); setSize(950,950); show(); } public void actionPerformed(ActionEvent ae) { if(ae.getActionCommand().equals("CHECK&COMPUTE")) { int x0,x1,x2,x3,x4,x5,x6,x7,x8,x9,x10; x0 =Integer.parseInt(d0.getText()); 47
- 48. x1= Integer.parseInt(d1.getText()); x2=Integer.parseInt(d2.getText()); x3=Integer.parseInt(d3.getText()); x4=Integer.parseInt(d4.getText()); x5=Integer.parseInt(d5.getText()); x6=Integer.parseInt(d6.getText()); x7=Integer.parseInt(d7.getText()); x8=Integer.parseInt(d8.getText()); x9=Integer.parseInt(d9.getText()); x10=Integer.parseInt(d10.getText()); if((x1>=x0)&&(x2>=x0)&&(x3>=x0)&&(x4>=x0)&&(x5>=x0)&&(x6>=x0)& &(x7>=x0)&&(x8>=x0)&&(x9>=x0)&&(x10>=x0)) { m1.setText("MULTI_PATH FADING MODEL"); int bit,etrans,eelec=3,erecie,eprocess=5,etotal,esense=4,mp=2; bit=Integer.parseInt(k1.getText()); etrans=((bit*eelec)+(bit*mp)); te.setText(String.valueOf(etrans)); erecie=(bit*eelec); re.setText(String.valueOf(erecie)); etotal=etrans+erecie+eprocess+esense; tot.setText(String.valueOf(etotal)); } else{ m1.setText("FREE SPACE CHANNEL MODEL"); int bit,etrans,eelec=3,erecie,eprocess=5,etotal,esense=4,fs=1; bit=Integer.parseInt(k1.getText()); etrans=((bit*eelec)+(bit*fs)); te.setText(String.valueOf(etrans)); erecie=(bit*eelec); re.setText(String.valueOf(erecie)); etotal=etrans+erecie+eprocess+esense; 48
- 49. tot.setText(String.valueOf(etotal)); } } } public void actionPerformed(ActionEvent ae) { if(ae.getActionCommand().equals("Reliability values")) { Random r=new Random(); int i ; float rv1,rv2,rv3,rv4,rv5; float rsw1,rsw2,rsw3,rsw4,rsw5; float urw1,urw2,urw3,urw4,urw5; urw1=r.nextInt(40); rsw1=100-urw1; urw2=r.nextInt(45); rsw2=100-urw2; urw3=r.nextInt(30); rsw3=100-urw3; urw4=r.nextInt(45); rsw4=100-urw4; urw5=r.nextInt(20); rsw5=100-urw5; rv1=((rsw1-urw1)/(rsw1+urw1)); rv2=((rsw2-urw2)/(rsw2+urw2)); rv3=((rsw3-urw3)/(rsw3+urw3)); rv4=((rsw4-urw4)/(rsw4+urw4)); rv5=((rsw5-urw5)/(rsw5+urw5)); d1.setText(String.valueOf(rv1)+ "RV"); d2.setText(String.valueOf(rv2) + "RV"); d3.setText(String.valueOf(rv3)+ "RV"); d4.setText(String.valueOf(rv4)+ "RV"); d5.setText(String.valueOf(rv5)+ "RV"); 49
- 50. System.out.println("THE RELIABLE SENSING WATCH OF NODE1: "+rsw1); System.out.println("THE UNRELIABLE SENSING WATCH OF NODE1: "+urw1); System.out.println("THE RELIABLE SENSING WATCH OF NODE2: "+rsw2); System.out.println("THE UNRELIABLE SENSING WATCH OF NODE2: "+urw2); System.out.println("THE RELIABLE SENSING WATCH OF NODE3: "+rsw3); System.out.println("THE UNRELIABLE SENSING WATCH OF NODE3: "+urw3); System.out.println("THE RELIABLE SENSING WATCH OF NODE4: "+rsw4); System.out.println("THE UNRELIABLE SENSING WATCH OF NODE4: "+urw4); System.out.println("THE RELIABLE SENSING WATCH OF NODE5: "+rsw5); } else if(ae.getActionCommand().equals("Packet Delivery Rate")) { Random r=new Random(); int i,n ; float pdr1,pdr2,pdr3,pdr4,pdr5; float str1,str2,str3,str4,str5; float pfr1,pfr2,pfr3,pfr4,pfr5; //System.out.println("Enter the number of Packets are being transfered"); //Scanner sc=new Scanner(System.in); //n=sc.nextInt(); pfr1=r.nextInt(4); str1=10-pfr1; pfr2=r.nextInt(3); str2=10-pfr2; pfr3=r.nextInt(5); 50
- 51. str3=10-pfr3; pfr4=r.nextInt(3); str4=10-pfr4; pfr5=r.nextInt(2); str5=10-pfr5; pdr1=((str1-pfr1)/(str1+pfr1)); pdr2=((str2-pfr2)/(str2+pfr2)); pdr3=((str3-pfr3)/(str3+pfr3)); pdr4=((str4-pfr4)/(str4+pfr4)); pdr5=((str5-pfr5)/(str5+pfr5)); d1.setText(String.valueOf(pdr1)+ "PDR"); d2.setText(String.valueOf(pdr2)+ "PDR"); d3.setText(String.valueOf(pdr3)+ "PDR"); d4.setText(String.valueOf(pdr4)+ "PDR"); d5.setText(String.valueOf(pdr5)+ "PDR"); System.out.println("The Success count of Packet Delivery Rate at NODE1: "+str1); System.out.println("The Failure count of Packet Delivery Rate at NODE1: "+pfr1); System.out.println("The Success count of Packet Delivery Rate at NODE2: "+str2); System.out.println("The Failure count of Packet Delivery Rate at NODE2: "+pfr2); System.out.println("The Success count of Packet Delivery Rate at NODE3: "+str3); System.out.println("The Failure count of Packet Delivery Rate at NODE3: "+pfr3); System.out.println("The Success count of Packet Delivery Rate at NODE4: "+str4); System.out.println("The Failure count of Packet Delivery Rate at NODE4: "+pfr4); System.out.println("The Success count of Packet Delivery Rate at NODE5: "+str5); 51
- 52. System.out.println("The Failure count of Packet Delivery Rate at NODE5: "+pfr5); } else if(ae.getActionCommand().equals("Total Trust Value")) { float r1,r2,r3,r4,r5; float rv1,rv2,rv3,rv4,rv5; float rsw1,rsw2,rsw3,rsw4,rsw5; float urw1,urw2,urw3,urw4,urw5; float pdr1,pdr2,pdr3,pdr4,pdr5; float str1,str2,str3,str4,str5; float pfr1,pfr2,pfr3,pfr4,pfr5; float ttv1,ttv2,ttv3,ttv4,ttv5; float w1,w2,w3; Random r=new Random(); Random rand=new Random(); w1=r.nextInt(2); w2=r.nextInt(3); w3=r.nextInt(4); urw1=r.nextInt(40); rsw1=100-urw1; urw2=r.nextInt(45); rsw2=100-urw2; urw3=r.nextInt(30); rsw3=100-urw3; urw4=r.nextInt(45); rsw4=100-urw4; urw5=r.nextInt(20); rsw5=100-urw5; rv1=((rsw1-urw1)/(rsw1+urw1)); rv2=((rsw2-urw2)/(rsw2+urw2)); rv3=((rsw3-urw3)/(rsw3+urw3)); rv4=((rsw4-urw4)/(rsw4+urw4)); rv5=((rsw5-urw5)/(rsw5+urw5)); 52
- 53. pfr1=r.nextInt(4); str1=10-pfr1; pfr2=r.nextInt(3); str2=10-pfr2; pfr3=r.nextInt(5); str3=10-pfr3; pfr4=r.nextInt(3); str4=10-pfr4; pfr5=r.nextInt(2); str5=10-pfr5; pdr1=((str1-pfr1)/(str1+pfr1)); pdr2=((str2-pfr2)/(str2+pfr2)); pdr3=((str3-pfr3)/(str3+pfr3)); pdr4=((str4-pfr4)/(str4+pfr4)); pdr5=((str5-pfr5)/(str5+pfr5)); r1=rand.nextInt(5); r2=rand.nextInt(4); r3=rand.nextInt(3); r4=rand.nextInt(4); r5=rand.nextInt(3); ttv1=((w1*r1)+(w2*pdr1)+(w3*rv1))/(w1+w2+w3); ttv2=((w1*r2)+(w2*pdr2)+(w3*rv2))/(w1+w2+w3); ttv3=((w1*r3)+(w2*pdr3)+(w3*rv3))/(w1+w2+w3); ttv4=((w1*r4)+(w2*pdr4)+(w3*rv4))/(w1+w2+w3); ttv5=((w1*r5)+(w2*pdr5)+(w3*rv5))/(w1+w2+w3); d1.setText(String.valueOf(ttv1)+ "TTV"); d2.setText(String.valueOf(ttv2)+ "TTV"); d3.setText(String.valueOf(ttv3)+ "TTV"); d4.setText(String.valueOf(ttv4)+ "TTV"); d5.setText(String.valueOf(ttv5)+ "TTV"); } public static void main(String[] args) { FBTARF e = new FBTARF(); 53
- 54. }} Public router =new router(); Public destination() {ImageIcon img1 = new ImageIcon(this.getClass().getResource("servermonitor.PNG")); imagelabel.setIcon(img1); imagelabel.setBounds(190,140,550,300); jf = new JFrame(); c = jf.getContentPane(); c.setLayout(null); jf.setSize(815, 738); jf.setResizable(false); bf.setIcon(new javax.swing.ImageIcon("designation.png")); bf.setBounds(0, 0, 799, 699); dimg.setIcon(new javax.swing.ImageIcon("desj.png")); dimg.setBounds(230,400,400,300); T1a.setBounds(90, 5, 650,45); T1a.setFont(f); T1a.setForeground(Color.white); T1b.setBounds(195, 40, 450,45); T1b.setFont(f); T1b.setForeground(Color.white); Border lineBorder = BorderFactory.createLineBorder(new Color(211,217,184)); line = new JLabel(); line.setBorder(lineBorder); line.setBounds(70,140,500,280); TitledBorder leftBorder = BorderFactory.createTitledBorder("File Transmit"); leftBorder.setTitleJustification(TitledBorder.LEFT); leftButton = new JLabel(); leftButton.setBorder(leftBorder); leftButton.setBounds(70,200,500,300); leftBorder.setTitleColor(Color.ORANGE); TitledBorder leftBorder1 = BorderFactory.createTitledBorder("Received File"); leftBorder.setTitleJustification(TitledBorder.LEFT); 54
- 55. proxyques = new JLabel(); proxyques.setBorder(leftBorder1); proxyques.setBounds(70,430,500,280); leftBorder1.setTitleColor(Color.ORANGE); T0.setBounds(200,80,350,45); T0.setFont(f); rf.setBounds(300,200,350,45); rf.setFont(f); rf.setForeground(Color.WHITE); T0.setForeground(Color.CYAN); T2.setBounds(105, 660, 250,45); T2.setFont(f1); T2.setForeground(new Color(211,217,184)); T1.setForeground(new Color(211,217,184)); T1.setBounds(105, 570, 300, 150); T1.setFont(f1); txt1.setBounds(105, 280, 300,25); txt1.setFont(f1); T3.setBounds(265, 625, 250,45); T3.setFont(f1); T3.setForeground(Color.cyan); T4.setBounds(255, 660, 350,45); T4.setFont(f1); T4.setForeground(Color.RED); T5.setBounds(125, 590, 250,45); T5.setFont(f3); T5.setForeground(new Color(211,217,184)); txt2.setBounds(220, 595, 250,30); txt2.setForeground(Color.BLUE); txt2.setFont(f1); btn.setBounds(420,420,120,30); btn.setFont(f3); btn.setForeground(new Color(120,0,0)); btn1.setBounds(420,277,120,30); 55
- 56. btn1.setFont(f3); btn1.setForeground(new Color(120,0,0)); btn2.setBounds(420,650,120,30); btn2.setFont(f3); btn2.setForeground(new Color(120,0,0)); jp.setBounds(85,110,850,550); jp.setBackground(new Color(211,217,184)); jp1.setBounds(50,200,700,450); jp1.setBackground(new Color(102,102,102)); txt.setBounds(260,150,180,25); txt.setForeground(Color.BLUE); txt.setFont(f1); TAreu.setBounds(650,550,200,35); TAreu.addItem("Mesh Route"); TAreu.addItem(" Node "); TAreu.setFont(f3); TAreu.setForeground(Color.BLUE); TAreu.setFont(f); pane.setBounds(100, 250, 600, 240); tf.setColumns(20); tf.setForeground(Color.MAGENTA); tf.setFont(f1); tf.setRows(10); tf.setName("tf"); pane.setName("pane"); pane.setViewportView(tf); tfld.setBounds(410,160,200,30); tfld.setFont(f2); tfld.setForeground(new Color(120,0,0)); btn1.setMnemonic(KeyEvent.VK_B); btn.setMnemonic(KeyEvent.VK_S); jf.show(); c.add(rf); c.add(pane, BorderLayout.CENTER); 56
- 57. int[] ports = new int[] { 8889 }; for (int i = 0; i < 1; i++) { Thread t = new Thread(new PortListener(ports[i])); t.setName("Listener-" + ports[i]); t.start(); } c.add(dimg); c.add(jp1); c.add(bf); } public static void main(String args[]) { new destination(); } void writefile(){ try{ fout = new FileOutputStream ("F:/serverfile/"+fname); new PrintStream(fout).println (data); fout.close(); File f=new File("F:/serverfile/",fname); String path=f.getAbsolutePath(); T3.setText(path); T4.setText("File successfully Received by server"); }catch (IOException e){ System.err.println ("Unable to write to file"); } } } 57
- 59. Screen 01: Source Node Screen 02: File Transfering 59
- 60. Screen 03: Details of File 60
- 61. Screen 04: Energy Cost 61
- 62. Screen 05 :Reliability Value 62
- 63. Screen 06:Packet Delivery Rate 63
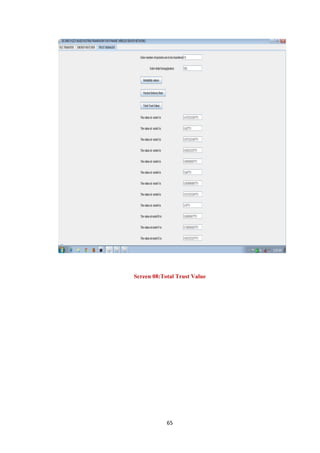
- 65. Screen 08:Total Trust Value 65
- 66. Screen 09: Fuzzy Based Routing 66
- 67. Screen 10:Recived File at Sink node 67
- 68. 6. TESTING AND VALIDATION 6.1 INTRODUCTION Testing is a process of comparing the state of a system/application against a set of criteria. In the security industry, people frequently test against a set of mental criteria that are neither well defined nor complete. Validation checks that the product design satisfies or fits the intended use (high-level checking), i.e., the software meets the user requirements. This is done through dynamic testing and other forms of review. A perfect software product is built when every step is taken with full consideration that 'a right product is developed in a right manner'. 'Software Verification & Validation' is one such model, which helps the system designers and test engineers to confirm that a right product is built in the right way throughout the development process and improve the quality of the softwareproduct. 'Testing & Validation Model' makes it sure that, certain rules are followed at the time of development of a software product and also makes it sure that the product that is developed fulfills the required specifications. Software Testing and Validation is a disciplined approach to assessing software products throughout the product life cycle. A T&V effort strives to ensure that quality is built into the software. TYPES OF TESTS Unit testing Unit testing involves the design of test cases that validate that the internal program logic is functioning properly, and that program inputs produce valid outputs. All decision branches and internal code flow should be validated. It is the testing of individual software units of the application .it is done after the completion of an individual unit before integration. This is a structural testing, that relies on knowledge 68
- 69. of its construction and is invasive. Unit tests perform basic tests at component level and test a specific business process, application, and/or system configuration. Unit tests ensure that each unique path of a business process performs accurately to the documented specifications and contains clearly defined inputs and expected result. Integration testing Integration tests are designed to test integrated software components to determine if they actually run as one program. Testing is event driven and is more concerned with the basic outcome of screens or fields. Integration tests demonstrate that although the components were individually satisfaction, as shown by successfully unit testing, the combination of components is correct and consistent. Integration testing is specifically aimed at exposing the problems that arise from the combination of components. Functional test Functional tests provide systematic demonstrations that functions tested are available as specified by the business and technical requirements, system documentation, and user manuals. Functional testing is centered on the following items: Valid Input : identified classes of valid input must be accepted. Invalid Input : identified classes of invalid input must be rejected. Functions : identified functions must be exercised. Output : identified classes of application outputs must be exercised. Systems/Procedures: interfacing systems or procedures must be invoked. Organization and preparation of functional tests is focused on requirements, key functions, or special test cases. In addition, systematic coverage pertaining to identify Business process flows; data fields, predefined processes, and successive processes must be considered for testing. Before functional testing is complete, additional tests are identified and the effective value of current tests is determined. 69
- 70. System Test System testing ensures that the entire integrated software system meets requirements. It tests a configuration to ensure known and predictable results. An example of system testing is the configuration oriented system integration test. White Box Testing White Box Testing is a testing in which in which the software tester has knowledge of the inner workings, structure and language of the software, or at least its purpose. It is purpose. It is used to test areas that cannot be reached from a black box level. Black Box Testing Black Box Testing is testing the software without any knowledge of the inner workings, structure or language of the module being tested. Black box tests, as most other kinds of tests, must be written from a definitive source document, such as specification or requirements document, such as specification or requirements sdocument. It is a testing in which the software under test is treated, as a black box .you cannot “see” into it. The test provides inputs and responds to outputs without considering how the software works. Fig 11 : Black Box Testing This method is named so because the software program, in the eyes of the tester, is like a black box; inside which one cannot see. Black Box Testing is contrasted 70
- 71. with White Box Testing. View Differences between Black Box Testing and White Box Testing. This method of attempts to find errors in the following categories: a. Incorrect or missing functions b. Interface errors c. Errors in data structures or external database access d. Behavior or performance errors e. Initialization and termination errors. Advantages The advantages of this type of testing include: i. The test is unbiased because the designer and the tester are independent of each other. ii. The tester does not need knowledge of any specific programming languages. iii. The test is done from the point of view of the user, not the designer. iv. Test cases can be designed as soon as the specifications are complete. Disadvantages The disadvantages of this type of testing include: i. The test can be redundant if the software designer has already run a test case. ii. The test cases are difficult to design. iii. Testing every possible input stream is unrealistic because it would take a inordinate amount of time; therefore, many program paths will go untested 6.2 VALIDATION Unit Testing: 71
- 72. Unit testing is usually conducted as part of a combined code and unit test phase of the software lifecycle, although it is not uncommon for coding and unit testing to be conducted as two distinct phases. Test strategy and approach Field testing will be performed manually and functional tests will be written in detail. Test objectives • All field entries must work properly. • Pages must be activated from the identified link. • The entry screen, messages and responses must not be delayed. Features to be tested • Verify that the entries are of the correct format • No duplicate entries should be allowed • All links should take the user to the correct page. Integration Testing Software integration testing is the incremental integration testing of two or more integrated software components on a single platform to produce failures caused by interface defects. The task of the integration test is to check that components or software applications, e.g. components in a software system or – one step up – software applications at the company level – interact without error. Test Results: All the test cases mentioned above passed successfully. No defects encountered. Acceptance Testing 72
- 73. User Acceptance Testing is a critical phase of any project and requires significant participation by the end user. It also ensures that the system meets the functional requirements. Test Results: All the test cases mentioned above passed successfully. No defects encountered. 7.CONCLUSION AND FUTURE ENHANCEMENT With the concept of innovative trust management, FBTARF enables a node to keep track of the trustworthiness of its neighbors and there by select a reliable route path. Our main submissions are listed below. 1) Fuzzy based TARF effectively protects WSN from severe attacks through dynamic replaying routing information. Without time synchronization and known geographic information, fuzzification rules are formed based on dynamic mobility of the nodes. 2). Extensive simulation and empirical analysis with large-scale WSN produces high resilience and scalability while using FBT ARF and its proved by the graphical analysis. 3). Finally, we demonstrate a proof-of-concept mobility based target detection application using trust, energy cost and distance estimators that are formulated on top of the Fuzzy based TARF. The work can be extended in building a Fuzzy based TARF algorithm that takes not only Trust level and power level of each node but also the performance capacity of each node for efficiency improvement. The algorithm can be added to any existing routing algorithm for Trust and power management. The effectiveness of node can be easily found out by adding additional data aggregation about each node's capacity. Our Technique FBT ARF is compared with multiple protocols like CTP and TARF to produce high throughput and PDR rate and less energy consumption. 73
- 74. BIBLIOGRAPHY [1] . Guoxing Zhan, Weisong Shi, Senior Member, IEEE, and Julia Deng - Design and Implementation of TARF: A Trust Aware Routing Framework for WSNs - IEEE 2012 Transactions on Dependable and Secure Computing, Volume: 9, Issue: 2 [2] . F. Zhao and L. Guibas, Wireless Sensor Networks: An Information Processing Ap proach. Morgan Kaufmann Publishers, 2004. [3]. A. Wood and J. Stankovic, "Denial of service in sensor networks," Computer, vol. 35, no. 10, pp. 54-62, Oct 2002. [4] . C. Karlof and D. Wagner, "Secure routing in wireless sensor networks: attacks and countermeasures," in Proceedings of the 1st IEEE International Workshop on Sensor Network Protocols and Ap plications, 2003. [5]. AI-Azawi, S., S. Boussakta and A. Yakovlev, 2012. Image compression algorithms using intensity based adaptive quantization coding. Am. J. Eng. Applied Sci., 4: 504-512. 001: I 0.3844/ajeassp.20 11.504.512 [6]. Bhoopathy, V. and R.M.S. Parvathi, 2012. Energy constrained secure hierarchical data aggregation in wireless sensor networks. Am. J. Applied Sci., 9: 858-864. 001: 1 0.3844/ajassp.20 12.858.864 74
- 75. [7]. Ozdemir, S. and Y. Xiao, 2009. Secure data aggregation in wireless sensor networks: A comprehensive overview. Comput. Netw., 53: 2022-2037. 001: 10.10 16/j.comnet.2009.02.023 [8]. L. Bai, F. Ferrese, K. Ploskina, and S. Biswas, "Performance analysis of mobile agent-based wireless sensor network," in Proceedings of the 8th International Conference on Reliability, Maintainability and Safety (ICRMS 2009), 20-24 2009,pp. 16 -19.s 75









































![show();
add(txt1);
add(btn);
add(proposed);
add(T2);
add(T4);
add(pane,BorderLayout.CENTER);
add(btn1);
add(jp);
add(jp1);
add(bf);
}
public void actionPerformed(ActionEvent e)
{
DataInputStream input;
BufferedInputStream bis;
BufferedOutputStream bos = null;
BufferedWriter writer = null;
int in;
String str="MobileTerminal,Foriegn Agent A,Gateway FA A";
byte[] byteArray=str.getBytes();
StringBuffer buffer = new StringBuffer();
String strLine = null;
String newline = "n";
if (e.getSource()== btn1)
{
JFileChooser chooser = new JFileChooser();
try {
File f = new File(new File("").getCanonicalPath());
chooser.setSelectedFile(f);
}
catch (IOException e1) {}
chooser.showOpenDialog(btn1);
int retval = chooser.showOpenDialog(btn1);
41](https://image.slidesharecdn.com/3fulldocument-171110061027/85/A-PROJECT-REPORT-ON-SECURED-FUZZY-BASED-ROUTING-FRAMEWORK-FOR-DYNAMIC-WIRELESS-SENSOR-NETWORKS-41-320.jpg)











![pfr1=r.nextInt(4);
str1=10-pfr1;
pfr2=r.nextInt(3);
str2=10-pfr2;
pfr3=r.nextInt(5);
str3=10-pfr3;
pfr4=r.nextInt(3);
str4=10-pfr4;
pfr5=r.nextInt(2);
str5=10-pfr5;
pdr1=((str1-pfr1)/(str1+pfr1));
pdr2=((str2-pfr2)/(str2+pfr2));
pdr3=((str3-pfr3)/(str3+pfr3));
pdr4=((str4-pfr4)/(str4+pfr4));
pdr5=((str5-pfr5)/(str5+pfr5));
r1=rand.nextInt(5);
r2=rand.nextInt(4);
r3=rand.nextInt(3);
r4=rand.nextInt(4);
r5=rand.nextInt(3);
ttv1=((w1*r1)+(w2*pdr1)+(w3*rv1))/(w1+w2+w3);
ttv2=((w1*r2)+(w2*pdr2)+(w3*rv2))/(w1+w2+w3);
ttv3=((w1*r3)+(w2*pdr3)+(w3*rv3))/(w1+w2+w3);
ttv4=((w1*r4)+(w2*pdr4)+(w3*rv4))/(w1+w2+w3);
ttv5=((w1*r5)+(w2*pdr5)+(w3*rv5))/(w1+w2+w3);
d1.setText(String.valueOf(ttv1)+ "TTV");
d2.setText(String.valueOf(ttv2)+ "TTV");
d3.setText(String.valueOf(ttv3)+ "TTV");
d4.setText(String.valueOf(ttv4)+ "TTV");
d5.setText(String.valueOf(ttv5)+ "TTV");
}
public static void main(String[] args)
{
FBTARF e = new FBTARF();
53](https://image.slidesharecdn.com/3fulldocument-171110061027/85/A-PROJECT-REPORT-ON-SECURED-FUZZY-BASED-ROUTING-FRAMEWORK-FOR-DYNAMIC-WIRELESS-SENSOR-NETWORKS-53-320.jpg)



![int[] ports = new int[] { 8889 };
for (int i = 0; i < 1; i++) {
Thread t = new Thread(new PortListener(ports[i]));
t.setName("Listener-" + ports[i]);
t.start();
}
c.add(dimg);
c.add(jp1);
c.add(bf);
}
public static void main(String args[])
{
new destination();
}
void writefile(){
try{
fout = new FileOutputStream ("F:/serverfile/"+fname);
new PrintStream(fout).println (data);
fout.close();
File f=new File("F:/serverfile/",fname);
String path=f.getAbsolutePath();
T3.setText(path);
T4.setText("File successfully Received by server");
}catch (IOException e){
System.err.println ("Unable to write to file");
}
}
}
57](https://image.slidesharecdn.com/3fulldocument-171110061027/85/A-PROJECT-REPORT-ON-SECURED-FUZZY-BASED-ROUTING-FRAMEWORK-FOR-DYNAMIC-WIRELESS-SENSOR-NETWORKS-57-320.jpg)















![BIBLIOGRAPHY
[1] . Guoxing Zhan, Weisong Shi, Senior Member, IEEE, and Julia Deng -
Design and Implementation of TARF: A Trust Aware Routing Framework for
WSNs - IEEE 2012 Transactions on Dependable and Secure Computing, Volume:
9, Issue: 2
[2] . F. Zhao and L. Guibas, Wireless Sensor Networks: An Information
Processing Ap proach. Morgan Kaufmann Publishers, 2004.
[3]. A. Wood and J. Stankovic, "Denial of service in sensor networks,"
Computer, vol. 35, no. 10, pp. 54-62, Oct 2002.
[4] . C. Karlof and D. Wagner, "Secure routing in wireless sensor networks:
attacks and countermeasures," in Proceedings of the 1st IEEE International
Workshop on Sensor Network Protocols and Ap plications, 2003.
[5]. AI-Azawi, S., S. Boussakta and A. Yakovlev, 2012. Image compression
algorithms using intensity based adaptive quantization coding. Am. J. Eng.
Applied Sci., 4: 504-512. 001: I 0.3844/ajeassp.20 11.504.512
[6]. Bhoopathy, V. and R.M.S. Parvathi, 2012. Energy constrained secure
hierarchical data aggregation in wireless sensor networks. Am. J. Applied Sci.,
9: 858-864. 001: 1 0.3844/ajassp.20 12.858.864
74](https://image.slidesharecdn.com/3fulldocument-171110061027/85/A-PROJECT-REPORT-ON-SECURED-FUZZY-BASED-ROUTING-FRAMEWORK-FOR-DYNAMIC-WIRELESS-SENSOR-NETWORKS-74-320.jpg)
![[7]. Ozdemir, S. and Y. Xiao, 2009. Secure data aggregation in wireless sensor
networks: A comprehensive overview. Comput. Netw., 53: 2022-2037. 001:
10.10 16/j.comnet.2009.02.023
[8]. L. Bai, F. Ferrese, K. Ploskina, and S. Biswas, "Performance analysis of
mobile agent-based wireless sensor network," in Proceedings of the 8th
International Conference on Reliability, Maintainability and Safety (ICRMS
2009), 20-24 2009,pp. 16 -19.s
75](https://image.slidesharecdn.com/3fulldocument-171110061027/85/A-PROJECT-REPORT-ON-SECURED-FUZZY-BASED-ROUTING-FRAMEWORK-FOR-DYNAMIC-WIRELESS-SENSOR-NETWORKS-75-320.jpg)


































































