Jaimin chp-1 - introduction - 2011 batch
- 1. Computer Networks, Fourth Edition by Andrew S. Tanenbaum
- 2. Chapter 1
- 3. Physical layer (e.g., copper, fiber, wireless, satellites, and Internet over cable) Data link layer (e.g., protocol principles, protocol verification, HDLC, and PPP) MAC Sublayer (e.g., gigabit Ethernet, 802.11, broadband wireless, and switching) Network layer (e.g., routing algorithms, congestion control, QoS, IPv4, and IPv6) Transport layer (e.g., socket programming, UDP, TCP, RTP, and network performance) Application layer (e.g., e-mail, the Web, PHP, wireless Web, MP3, and streaming audio) Network security (e.g., AES, RSA, quantum cryptography, IPsec, and Web security)
- 4. Section 1.1. Uses of Computer Networks Section 1.2. Network Hardware Section 1.3. Network Software Section 1.4. Reference Models Section 1.5. Example Networks Section 1.6. Network Standardization Section 1.7. Metric Units
- 5. Business Applications online buying Home Applications mail, chat Mobile Users wireless: laptops, PDA, mobile, in plane Social Issues
- 6. A network with two clients and one server. Check bank account Pay bills Reserve ticket Big companies have offices @ various sites leads CS model The client-server model involves requests and replies.
- 7. Resource (inf0,data,device) sharing Communication – email Videoconferencing e-Commerece
- 8. Access to remote information Leaning online, downloading(P2P – torrent) ,digital libraries, Newspapers and blogs Person-to-person communication chat (Yahoo-AIM-MSN), phone (VoIP- Video Chat) Interactive entertainment games, movies, … Electronic commerce
- 9. Peer-to-peer (P2P) Kazaa, Emule, E-commerce
- 10. Combinations of wireless networks and mobile computing. Wireless parking meters Rental cars on busy airports Food, drink, and other vending machines PDA – replacement of plastic currency fixed wireless ≠ mobile wireless
- 11. Discussions about politics, religion, … Hack and robbery Political issues: Google in China Changing habits of “Netizens”
- 12. Transmission hardware Special-purpose hardware devices interconnect transmission media control transmission run protocol software Protocol software encodes and formats data detects and corrects problems
- 13. Transmission technology (2 types) Broadcast links - Unicast - Multicast Point-to-point links point-to-point networks consist of many connections between individual pairs of machines Ex: DSL,ISDN,T1 Scale Local Area Networks (LAN) Metropolitan Area Networks (MAN) Wide Area Networks (WAN) Wireless Networks Home Networks Internetworks Media Wired Wireless
- 14. Types of transmission technology Broadcast links Point-to-point links
- 15. There are A single communication link for all systems in network = Broadcasting TV programs: IRI B (Islamic Republic of Iran Broadcast ), … Messages ( Packets ) contain destination address Multicasting : A subset of systems can get the message Usually used in small networks like LANs
- 16. Individual connections between pairs of machines. There are many paths from one machine to another Need efficient routing algorithms Usually used in large scale networks like WAN
- 17. Packets Messages - the "chunk" of data transmitted from one machine to the next. Addressing One to one: Packet contains specific target address. Broadcasting: All machines on the network receive and process the packet. Multicasting: A subset of machines receive and process the packet
- 18. Classification of interconnected processors by scale.
- 19. Privately owned. Can be up to several kilometers long; Ex. in a building Separated by their: Size: Restricted so worst case transmission time can be contained. Transmission technology: Single channel with multiple machines connected to it. Run at speeds of 10, 100, or more Mbps. Topology: two popular broadcast networks: Bus Ring
- 32. Topology … Bus Ethernet ( IEEE 802.3): Bus based broadcast network with decentralized control at 10 or 100 Mbps. Ring Token Ring (IEEE 802.5): Ring based broadcast network with token arbitration at 4 or 16 Mbps. Low delay. High reliability. Requires collision arbitration
- 33. Larger version of LAN ("city" wide). Public or private / data or voice. Broadcast - no switches. Can be distinguished from LANs based on wiring mechanism. DQDB (Distributed Queue Dual Bus), IEEE 802.6 Ex. A metropolitan area network based on cable TV
- 34. Networks spanning large distances. Ex. Relation between hosts on LANs and the subnet. Hosts or End Systems: Machines running user applications.
- 35. (Communication) Subnet : Connections between hosts - transmission lines + switches. A "locality" understanding each other's addresses. Circuits (Channels, Trunks): Transmission lines move the bits. Packet switching nodes ( Router , Intermediate systems): Specialized computers moving data between several inputs to several outputs. Point-to-point/Store-and-forward/Packet-switched - Moving through a series of routers, packets are received at a router, stored there, then forwarded to the next router.
- 36. Ex. A stream of packets from sender to receiver.
- 37. Categories of wireless networks: System interconnection Wireless LANs Wireless WANs
- 38. Used where computer is mobile or far away from wires. Only 1 - 2 Mbps, higher error rates, interference Use Sound Light and mirrors Infrared RF Microwave
- 39. (a) Bluetooth configuration (b) Wireless LAN
- 40. (a) Individual mobile computers (b) A flying LAN
- 41. Protocol Hierarchies Design Issues for the Layers Connection-Oriented and Connectionless Services Service Primitives The Relationship of Services to Protocols
- 42. Primary networks more depend on hardware It talks about the philosophy of connecting together two entities. “ Layering” is the key word Protocol Hierarchies Design Issues for the Layers The Relationship of Services to Protocols
- 43. Layers : The concept that network software is organized functionally into levels. A level on one host talks to the same level on another host (its peer). Protocol : The protocol is the convention or standard that a layer uses to talk to the other layer. An agreement or standard on the conversation .
- 44. Layers, Important that each layer perform specific actions. protocols, Interfaces Defines the services That one layer offers another (either up or down.)
- 45. Ex. Protocol of philosopher-translator-secretary architecture.
- 46. Ex. Protocol Hierarchies information flow supporting virtual communication in layer 5
- 47. Physical Medium: Underneath the layers is the wire or fiber or whatever. Network architecture: A set of layers and protocols. It contains details on what happens in the layer and what the layers says to its peer. Functional interfaces and implementation details are not part of the spec, since that's not visible outside the machine. Protocol stack: A list of protocols used by a system, one protocol per layer . Information flow: "Send_to_peer" rather than "call_next_layer_down".
- 48. Addressing Error control. (garbled or missing.) Preservation of message ordering. Flow control. Breaking up messages into a smaller chunks (and reassembly.) Multiplexing messages on same connection. Routing - how to get from one host to another. Connection Both Directions Simultaneous Simplex No No Half duplex Yes No Full duplex Yes Yes
- 49. Connection oriented service: Like the phone system. The system establishes a connection, uses it, and closes it. Acts like a tube. Data comes out the other end in the same order as it goes in. Connection Setup Data Transfer Connection Termination Connectionless service: Like the post office. Each message has the entire address on it. Each message may follow a different route to its destination. Ordering not maintained. Data Transfer
- 50. Quality of service (QoS): Will the message arrive? A reliable connection-oriented service guarantees success. Message sequence - message boundaries and order are maintained. Byte streams - messages are broken up or combined; flow is bytes. Can pair mechanism with upper-layer requirements. Datagram Service: Like junk mail. It's not worth the cost to determine if it actually arrived. Needs a high probability of arrival, but 100% not required. Connectionless, no acknowledgment. Acknowledged datagram service: As above, but improved reliability via acknowledgment. Request-reply service: Acknowledgment is in the form of a reply.
- 51. Summary of six different types of service.
- 52. Service Primitives for connection-oriented service Example Connect.indication Connect.request Connect.confirm Data.indication Data.request Data.request Data.indication Disconnect.indication Disconnect.request Disconnect.confirm
- 54. Computers (desktop PC, PDA, shared peripherals Entertainment (TV, DVD, VCR, camera, stereo, MP3) Telecomm (telephone, cell phone, intercom, fax) Appliances (microwave, fridge, clock, furnace, airco) Telemetry (utility meter, burglar alarm, babycam).
- 55. Services are primitives that a layer provides for the layer above it. Protocols are rules governing the meaning of frames/packets/messages exchanged with the peer entity.
- 57. Headers, Data, and Trailers Encapsulation
- 58. The OSI Reference Model The TCP/IP Reference Model A Comparison of OSI and TCP/IP A Critique of the OSI Model and Protocols A Critique of the TCP/IP Reference Model
- 59. Comparison of OSI and TCP/IP
- 60. There are two competing models for how the software is layered. These are the OSI and the TCP models. OSI (Open Systems Interconnection) Developed by ISO (International Standards Organization) 7 layers TCP (Transfer Control Protocol) Used in the Arpanet and in the Internet . Common mechanism that is surpassing the OSI Model. 5 layers
- 61. Principles used to develop OSI Layering: 1. Need a layer for each different level of abstraction. 2. Each layer performs a well defined function. 3. Each layer should be standardizable. 4. Layer boundaries should minimize data flow across those boundaries. 5. The right number of layers - don't put too many functions together, but not too many layers either.
- 62. The OSI reference model.
- 63. Flow of data through the OSI Model
- 64. Physical Layer: Purpose: Transmits raw bits across a medium. Electrical: Concerns are voltage, timing, duplexing, connectors, etc. Data Link Layer: Framing : Breaks apart messages into frames . Reassembles frames into messages. Error handling : solves damaged, lost, and duplicate frames. Flow control : keeps a fast transmitter from flooding a slow receiver. Gaining Access : if many hosts have usage of the medium, how is access arbitrated.
- 65. Network Layer: Routing : What path is followed by packets from source to destination. Can be based on a static table, when the connection is created, or when each packet is sent. Congestion : Controls the number packets in the subnet. Accounting : Counts packets/bytes for billing purposes.
- 66. Transport Layer: Reliability : Ensures that packets arrive at their destination. Reassembles out of order messages. Hides network : Allows details of the network to be hidden from higher level layers. Service Decisions : What type of service to provide; error-free point to point, datagram, etc. Mapping : Determines which messages belong to which connections. Naming : "Send to node ZZZ" must be translated into an internal address and route. Flow control : keeps a fast transmitter from flooding a slow receiver. TCP (Transmission Control Protocol): provides a reliable connection oriented protocol that delivers a byte stream from one node to another. Guarantees delivery and provides flow control. UDP (User Datagram Protocol) provides an unreliable connection-less protocol for applications that provide their own.
- 67. Session Layer: Sessions : Provides services that span a particular message. For instance, a login session could be logged. Synchronization : Provide way to subdivide a long mechanism for reliability. Presentation Layer: Prettiness : Syntax and Jamul Miss. body is.of information transmitted. Understands the nature of the data being transmitted. Converts ASCII/EBCDIC, big endian/little endian \ Interfacing : Terminal type translation. File transfer : Programs able to understand directory structures and naming conventions and map them onto various systems.
- 68. Data Transmission in the OSI Model
- 69. Internet Layer Connector : Provides packet switched connectionless service. Routing : The IP (Internet Protocol) does delivery and congestion control. Transport Layer TCP (Transmission Control Protocol): provides a reliable connection oriented protocol that delivers a byte stream from one node to another. Guarantees delivery and provides flow control. UDP (User Datagram Protocol) provides an unreliable connection-less protocol for applications that provide their own.
- 70. Application Layer Terminal Telnet File transfer FTP The Web HTTP Mail SMTP
- 74. The relationship between a service and a protocol.
- 75. Protocols and networks in the TCP/IP model initially.
- 76. Why OSI did not take over the world Bad timing Bad technology Bad implementations Bad politics
- 77. The apocalypse of the two elephants.
- 78. Problems: Service, interface, and protocol not distinguished Not a general model Host-to-network “layer” not really a layer No mention of physical and data link layers Minor protocols deeply entrenched, hard to replace
- 79. The hybrid reference model to be used in this book.
- 80. The Internet Connection-Oriented Networks: X.25, Frame Relay, and ATM Ethernet Wireless LANs: 802:11
- 81. (a) Structure of the telephone system. (b) Baran’s proposed distributed switching system.
- 82. The original ARPANET design.
- 83. Growth of the ARPANET (a) December 1969. ( b) July 1970. (c) March 1971. (d) April 1972. (e) September 1972.
- 84. The NSFNET backbone in 1988.
- 85. Traditional applications (1970 – 1990) E-mail News Remote login File transfer
- 86. Overview of the Internet.
- 88. An ATM cell.
- 89. The ATM reference model.
- 90. The ATM layers and sublayers and their functions.
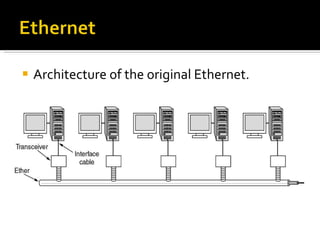
- 91. Architecture of the original Ethernet.
- 92. (a) Wireless networking with a base station. (b) Ad hoc networking.
- 93. The range of a single radio may not cover the entire system.
- 94. A multicell 802.11 network.
- 95. Who’s Who in the Telecommunications World Who’s Who in the International Standards World Who’s Who in the Internet Standards World
- 96. Main sectors Radio communications Telecommunications Standardization Development Classes of Members National governments Sector members Associate members Regulatory agencies
- 97. The 802 working groups. The important ones are marked with *. The ones marked with are hibernating. The one marked with † gave up.
- 98. The principal metric prefixes.