Andes building a secure platform with the enhanced iopmp
0 likes326 views
The document provides an overview of building a secure platform using the enhanced IOPMP (Input/Output Physical Memory Protection). It discusses why IOPMP is needed to check accesses from non-RISC-V bus masters, describes the enhancements made to IOPMP including supporting multiple bus masters and flexible response options. It then provides an example of how IOPMP, PMP, and secure boot can establish a root of trust for the platform and describes AndeSentry, an open security framework from Andes Technology.
1 of 33
Download to read offline















![Taking RISC-V® Mainstream 17
MID[3:0]
MID Encoding in IOPMP Entry
• An MID uses up to 14 bits, or 16,384 MIDs.
• An IOPMP entry contains up to 16 MIDs, by “MID.h” and “MID.l”.
MID[13:0]
MID.h[9:0] MID.l[15:0]
==
&&
Does the entry contain the MID?
MID[13:4]
Lower 4 bits uses
bitmap encoding
Upper 10 bits uses
binary encoding](https://image.slidesharecdn.com/andesbuildingasecureplatformwiththeenhancediopmp-210315173210/85/Andes-building-a-secure-platform-with-the-enhanced-iopmp-17-320.jpg)















Ad
Recommended
“Advancing Embedded Vision for an Autonomous World,” a Presentation from Qual...



“Advancing Embedded Vision for an Autonomous World,” a Presentation from Qual...Edge AI and Vision Alliance The document discusses Qualcomm's automotive technologies including biometrics, 3D vision capabilities, ADAS, autonomous driving solutions, and human-centric vision products. It describes Qualcomm's Snapdragon platforms that provide capabilities like telematics, infotainment, driver monitoring systems, and autonomous driving stacks to power advanced driver assistance systems and autonomous vehicles. The platforms utilize Qualcomm's CPU, GPU, DSP, and other technologies to deliver solutions spanning biometrics, computer vision, ADAS, autonomous driving, and more.
Andes RISC-V processor solutions



Andes RISC-V processor solutionsRISC-V International This document discusses Andes Technology Corporation's RISC-V processor IP solutions. It summarizes that Andes is a leading RISC-V CPU IP vendor that provides a portfolio of RISC-V processor cores ranging from embedded control to application processing. It also develops tools like the AndeSight IDE and provides customization services through its AndeSentry security framework and scalable acceleration architecture.
Optimizing ARM cortex a and cortex-m based heterogeneous multiprocessor syste...



Optimizing ARM cortex a and cortex-m based heterogeneous multiprocessor syste...Arm The document discusses optimizing heterogeneous multiprocessor systems using ARM Cortex processors. It covers topics like system design considerations, software challenges, and ARM's activities to make heterogeneous computing easier. Specifically, it addresses issues like memory mapping, interrupt handling, communication between processors, and security models when combining Cortex-A, Cortex-R, and Cortex-M processors on a single system.
Unit 4 _ ARM Processors .pptx



Unit 4 _ ARM Processors .pptxVijayKumar201823 Originally conceived as a processor for desktop systems, ARM processors are now widely used in embedded applications and markets. Some significant products that used ARM processors include the Apple Newton PDA (ARM6 core), Apple iPod (ARM7 core), and Apple iPhone and Nokia N93/N100 (ARM11 core). ARM processors are based on reduced instruction set computer (RISC) architecture. They are designed for low power consumption applications like mobile devices. Some key features of ARM processors include 32-bit instruction set with 16-bit Thumb extension, unified memory address space, and relatively low power consumption.
Introduction to ARM Architecture



Introduction to ARM ArchitectureRacharla Rohit Varma This document provides an introduction and overview of ARM processors. It discusses the background and concepts of ARM, including that ARM is a RISC architecture designed for efficiency. It describes key ARM architectural features like the Harvard architecture and conditional execution. The document also covers ARM memory organization, registers, instruction set, programming model, and exceptions.
Static partitioning virtualization on RISC-V



Static partitioning virtualization on RISC-VRISC-V International This document summarizes a presentation on static partitioning virtualization for RISC-V. It discusses the motivation for embedded virtualization, an overview of static partitioning hypervisors like Jailhouse and Xen, and the Bao hypervisor. It then provides an overview of the RISC-V hypervisor specification and extensions, including implemented features. It evaluates the performance overhead and interrupt latency of a prototype RISC-V hypervisor implementation with and without interference mitigations like cache partitioning.
PART-1 : Mastering RTOS FreeRTOS and STM32Fx with Debugging



PART-1 : Mastering RTOS FreeRTOS and STM32Fx with DebuggingFastBit Embedded Brain Academy Join this video course on Udemy. Click the below link
https://www.udemy.com/mastering-rtos-hands-on-with-freertos-arduino-and-stm32fx/?couponCode=SLIDESHARE
>> The Complete FreeRTOS Course with Programming and Debugging <<
"The Biggest objective of this course is to demystifying RTOS practically using FreeRTOS and STM32 MCUs"
STEP-by-STEP guide to port/run FreeRTOS using development setup which includes,
1) Eclipse + STM32F4xx + FreeRTOS + SEGGER SystemView
2) FreeRTOS+Simulator (For windows)
Demystifying the complete Architecture (ARM Cortex M) related code of FreeRTOS which will massively help you to put this kernel on any target hardware of your choice.
Embedded Android : System Development - Part III (Audio / Video HAL)



Embedded Android : System Development - Part III (Audio / Video HAL)Emertxe Information Technologies Pvt Ltd Android Audio HAL – Audio Architecture – Audio HAL interface – Audio Policy – Audio HAL compilation & verification – Overview of Tinyalsa
Android Video HAL – Camera Architecture – Overview of camera HAL interface – Overview of V4L2 – Enabling V4l2 in kernel – Camera HAL compilation and verification
Arm architecture



Arm architectureMinYeop Na The document discusses the ARM architecture and interrupt handling. It provides background on ARM and compares RISC and CISC architectures. It describes ARM's instruction sets, data sizes, registers including the program counter and current program status register. It discusses exception handling in ARM, including saving state on exception entry and exit. Interrupts and exceptions are compared to system calls. Memory organization during exceptions is also covered.
18CS44-MES-Module-1.pptx



18CS44-MES-Module-1.pptxrakshitha481121 The document discusses the Microcontroller and Embedded Systems course offered at SJEC Mangaluru. It provides an overview of the course outcomes, learning objectives, modules, topics covered in each module, textbook and reference books. The key topics covered are microprocessors vs microcontrollers, ARM architecture, embedded system hardware components, ARM instruction set, assembly language programming, embedded system design concepts, RTOS, and development tools. The assessment includes 5 full questions to be answered from the 5 modules.
Embedded Android : System Development - Part III



Embedded Android : System Development - Part IIIEmertxe Information Technologies Pvt Ltd For new age touch-based embedded devices, Android is becoming a popular OS going beyond mobile phones. With its roots from Embedded Linux, Android framework offers benefits in terms of rich libraries, open-source and multi-device support. Emertxe’s hands-on Embedded Android Training Course is designed to customize, build and deploy custom Embedded OS on ARM target. Rich set of projects will make your learning complete.
LCU14-103: How to create and run Trusted Applications on OP-TEE



LCU14-103: How to create and run Trusted Applications on OP-TEELinaro LCU14-103: How to create and run Trusted Applications on OP-TEE
---------------------------------------------------
Speaker: Joakim Bech
Date: September 15, 2014
---------------------------------------------------
Coresight is the name given to a set of IP blocks providing hardware assisted tracing for ARM based SoCs. This presentation will give an introduction to the technology, how it works and offer a glimpse of the capabilities it offers. More specifically we will go over the components that are part of the architecture and how they are used. Next will be presented the framework Linaro is working on in an effort to provide consolidation and standardization of interfaces to the coresight subsystem. We will conclude with a status of our current upstreaming efforts and how we see the coming months unfolding.
---------------------------------------------------
★ Resources ★
Zerista: http://lcu14.zerista.com/event/member/137703
Google Event: https://plus.google.com/u/0/events/cvb85kqv10dsc4k3e0hcvbr6i58
Presentation: http://www.slideshare.net/linaroorg/lcu14-101-coresight-overview
Video: https://www.youtube.com/watch?v=IQhbM55F23U&list=UUIVqQKxCyQLJS6xvSmfndLA
Etherpad: http://pad.linaro.org/p/lcu14-101
---------------------------------------------------
★ Event Details ★
Linaro Connect USA - #LCU14
September 15-19th, 2014
Hyatt Regency San Francisco Airport
---------------------------------------------------
Yocto Project introduction



Yocto Project introductionYi-Hsiu Hsu The document provides an introduction to the Yocto Project, including what it is, its main components, and workflow. It describes the Yocto Project as being comprised of Poky (the build system), tools, and upstreams. Poky contains BitBake (the build engine) and metadata (task configurations and definitions). It outlines the main components, including sub-projects, and compares the Yocto Project to OpenEmbedded. Finally, it summarizes the Yocto Project workflow, which involves configuring the build using recipes and layers then building packages, images, and cross-development toolchains.
Message Signaled Interrupts



Message Signaled InterruptsAnshuman Biswal 1) The document discusses Message Signaled Interrupts (MSI), an improvement over the traditional interrupt handling method. MSI allows interrupt information to be delivered in one step from a device directly to the CPU.
2) MSI was introduced in PCI 2.2 and improved in PCI 3.0 with MSI-X, which supports more interrupts per device. MSI uses a memory write to trigger an interrupt, while traditional interrupts use dedicated pins.
3) The benefits of MSI include faster response, less hardware requirements, guarantee of unique interrupts, and ability to send data with the interrupt. MSI also avoids ordering issues with traditional interrupts.
Linux scheduler



Linux schedulerLiran Ben Haim A brief overview of linux scheduler, context switch , priorities and scheduling classes as well as new features. Also provides an overview of preemption models in linux and how to use each model. all the examples are taken from http://www.discoversdk.com
DAIS19: On the Performance of ARM TrustZone



DAIS19: On the Performance of ARM TrustZoneLEGATO project Presented by Valerio Schiavoni @vschiavoni at DAIS 19
The TrustZone technology, available in the vast majority of recent Arm processors, allows the execution of code inside a so-called secure world. It effectively provides hardware-isolated areas of the processor for sensitive data and code, i.e., a trusted execution environment (TEE). The Op-Tee framework provides a collection of toolchain, opensource libraries and secure kernel specifically geared to develop applications for TrustZone. This paper presents an in-depth performance- and energy-wise study of TrustZone using the Op-Tee framework, including secure storage and the cost of switching between secure and unsecure worlds, using emulated and hardware measurements.
Memory model



Memory modelYi-Hsiu Hsu This document discusses memory ordering and synchronization in multithreaded programs. It begins with background on mutexes, semaphores, and their differences. It then discusses problems that can occur with locking-based synchronization methods like mutexes, such as deadlocks, priority inversion, and performance issues. Alternative lock-free programming techniques using atomic operations are presented as a way to synchronize access without locks. Finally, memory ordering, consistency models, barriers, and their implementations in compilers, Linux kernels, and ARM architectures are covered in detail.
Virtualization Support in ARMv8+



Virtualization Support in ARMv8+Aananth C N This slide provides a basic understanding of hypervisor support in ARM v8 and above processors. And these slides (intent to) give some guidelines to automotive engineers to compare and choose right solution!
U Boot or Universal Bootloader



U Boot or Universal BootloaderSatpal Parmar The document provides an overview of Das U-Boot, a universal boot loader used to load operating systems and applications into memory on embedded systems. It discusses U-Boot's features such as its command line interface, ability to load images from different sources, and support for various architectures and boards. It also covers compiling and configuring U-Boot, as well as its basic command set and image support capabilities.
Poll mode driver integration into dpdk



Poll mode driver integration into dpdkVipin Varghese This document discusses integrating a custom Poll Mode Driver (PMD) into DPDK to enable offloading packet processing tasks to multicore or application-specific integrated circuit (ASIC) hardware. A use case of offloading intrusion detection system and IPsec processing to multicore hardware while encrypted SSL traffic is decrypted via the multicore is presented. Developing a custom PMD allows leveraging multicore/ASIC as a line card or load balancer while avoiding issues like extra overhead from additional interfaces, frame reprocessing, and increased latency when using network connections between DPDK and hardware. Performance is improved by directly connecting the multicore/ASIC to DPDK which removes overhead and provides a high-throughput interface.
ARM



ARMPune University ARM processors use RISC architecture and load/store instruction sets. They have low power consumption and support pipelining. ARM profiles include classic processors like ARM7 and ARM9, Cortex-M series for microcontrollers, Cortex-R for real-time systems, and Cortex-A series for operating systems. The ARM register set includes 37 32-bit registers that are accessible in different subsets depending on the processor mode like supervisor, interrupt, abort, or user mode.
Kernel Recipes 2017 - An introduction to the Linux DRM subsystem - Maxime Ripard



Kernel Recipes 2017 - An introduction to the Linux DRM subsystem - Maxime RipardAnne Nicolas Every modern multimedia-oriented ARM SoC usually has a number of display controllers, to drive a screen or an LCD panel, and a GPU, to provide 3D acceleration. The Linux kernel framework of choice to support these controllers is the DRM subsystem.
This talk will walk through the DRM stack, the architecture of a DRM/KMS driver and the interaction between the display and GPU drivers. The presentation is based on the work we have done to develop a DRM driver for the Allwinner SoCs display controller with multiple outputs, such as parallel display interfaces, HDMI or MIPI-DSI. The work done to make the ARM Mali OpenGL driver work on top of a mainline DRM/KMS driver will also be detailed, as well as the more traditional, Mesa-based, solution used in a variety of other platforms.
Maxime Ripard, Free Electrons
Arm modes



Arm modesabhi165 This presentation aims to provide information regarding all seven operational modes of the arm processor except the monitor mode.
Is Linux ready for safety related applications?



Is Linux ready for safety related applications?Alexander Much The presentation is from a talk I gave at the ETAS Connections 2018 event. It details the reasoning for the use of Linux in the Automotive domain for safety-critical systems.
The content is based on our OSADL approach taken in the SIL2MP Linux project
Xvisor: embedded and lightweight hypervisor



Xvisor: embedded and lightweight hypervisorNational Cheng Kung University Xvisor is an open source lightweight hypervisor for ARM architectures. It uses a technique called cpatch to modify guest operating system binaries, replacing privileged instructions with hypercalls. This allows the guest OS to run without privileges in user mode under the hypervisor. Xvisor also implements virtual CPU and memory management to isolate guest instances and virtualize physical resources for multiple operating systems.
Presentation on Raspberry Pi by Sazzad H. IIUC



Presentation on Raspberry Pi by Sazzad H. IIUCshssn7 The document provides information on building a smart mirror using a Raspberry Pi. It discusses that the Raspberry Pi is a small, inexpensive computer that can be used for tasks like word processing and playing videos. It notes that over 3 million Raspberry Pi units have been sold. It then covers the hardware components of the Raspberry Pi, operating systems that can be used, and provides step-by-step instructions for setting up a Raspberry Pi to power a smart mirror, including downloading required software, configuring settings, and rotating the display.
Network Drivers



Network DriversAnil Kumar Pugalia The document discusses Linux network drivers and provides information about:
- The Linux network subsystem and protocol stack, typically using TCP/IP.
- Network interface card (NIC) drivers which provide a uniform interface for the network layer to access physical network cards.
- Key data structures like struct sk_buff and struct net_device that network drivers interact with for packet handling and device operations.
- Functions for network device registration, open/close, interrupt handling, and flow control.
- Examples of simple network drivers and how to write one for a Realtek NIC.
Basic network training2



Basic network training2Arunchai Seangparch This document provides an overview of a basic network training conducted by Global Technology Services, ASEAN. The training covered transport protocols like TCP and UDP, port addressing, routing table structure, router configuration, and packet switching. Key topics included the purpose of routers in forwarding packets, how routing tables determine the best path, and the encapsulation/de-encapsulation process performed by routers at each hop as packets traverse the network from source to destination.
Maximizing High Performance Applications with CAN Bus



Maximizing High Performance Applications with CAN BusJanel Heilbrunn CAN Bus offers speed, reliability and flexibility at an affordable cost, which makes it perfect for embedded applications requiring budget-friendly multi-processor communication. This brand-new ICS webinar offers an introduction to CAN Bus, and is directed at developers with no previous experience with CAN Bus or related technologies.
Ad
More Related Content
What's hot (20)
Arm architecture



Arm architectureMinYeop Na The document discusses the ARM architecture and interrupt handling. It provides background on ARM and compares RISC and CISC architectures. It describes ARM's instruction sets, data sizes, registers including the program counter and current program status register. It discusses exception handling in ARM, including saving state on exception entry and exit. Interrupts and exceptions are compared to system calls. Memory organization during exceptions is also covered.
18CS44-MES-Module-1.pptx



18CS44-MES-Module-1.pptxrakshitha481121 The document discusses the Microcontroller and Embedded Systems course offered at SJEC Mangaluru. It provides an overview of the course outcomes, learning objectives, modules, topics covered in each module, textbook and reference books. The key topics covered are microprocessors vs microcontrollers, ARM architecture, embedded system hardware components, ARM instruction set, assembly language programming, embedded system design concepts, RTOS, and development tools. The assessment includes 5 full questions to be answered from the 5 modules.
Embedded Android : System Development - Part III



Embedded Android : System Development - Part IIIEmertxe Information Technologies Pvt Ltd For new age touch-based embedded devices, Android is becoming a popular OS going beyond mobile phones. With its roots from Embedded Linux, Android framework offers benefits in terms of rich libraries, open-source and multi-device support. Emertxe’s hands-on Embedded Android Training Course is designed to customize, build and deploy custom Embedded OS on ARM target. Rich set of projects will make your learning complete.
LCU14-103: How to create and run Trusted Applications on OP-TEE



LCU14-103: How to create and run Trusted Applications on OP-TEELinaro LCU14-103: How to create and run Trusted Applications on OP-TEE
---------------------------------------------------
Speaker: Joakim Bech
Date: September 15, 2014
---------------------------------------------------
Coresight is the name given to a set of IP blocks providing hardware assisted tracing for ARM based SoCs. This presentation will give an introduction to the technology, how it works and offer a glimpse of the capabilities it offers. More specifically we will go over the components that are part of the architecture and how they are used. Next will be presented the framework Linaro is working on in an effort to provide consolidation and standardization of interfaces to the coresight subsystem. We will conclude with a status of our current upstreaming efforts and how we see the coming months unfolding.
---------------------------------------------------
★ Resources ★
Zerista: http://lcu14.zerista.com/event/member/137703
Google Event: https://plus.google.com/u/0/events/cvb85kqv10dsc4k3e0hcvbr6i58
Presentation: http://www.slideshare.net/linaroorg/lcu14-101-coresight-overview
Video: https://www.youtube.com/watch?v=IQhbM55F23U&list=UUIVqQKxCyQLJS6xvSmfndLA
Etherpad: http://pad.linaro.org/p/lcu14-101
---------------------------------------------------
★ Event Details ★
Linaro Connect USA - #LCU14
September 15-19th, 2014
Hyatt Regency San Francisco Airport
---------------------------------------------------
Yocto Project introduction



Yocto Project introductionYi-Hsiu Hsu The document provides an introduction to the Yocto Project, including what it is, its main components, and workflow. It describes the Yocto Project as being comprised of Poky (the build system), tools, and upstreams. Poky contains BitBake (the build engine) and metadata (task configurations and definitions). It outlines the main components, including sub-projects, and compares the Yocto Project to OpenEmbedded. Finally, it summarizes the Yocto Project workflow, which involves configuring the build using recipes and layers then building packages, images, and cross-development toolchains.
Message Signaled Interrupts



Message Signaled InterruptsAnshuman Biswal 1) The document discusses Message Signaled Interrupts (MSI), an improvement over the traditional interrupt handling method. MSI allows interrupt information to be delivered in one step from a device directly to the CPU.
2) MSI was introduced in PCI 2.2 and improved in PCI 3.0 with MSI-X, which supports more interrupts per device. MSI uses a memory write to trigger an interrupt, while traditional interrupts use dedicated pins.
3) The benefits of MSI include faster response, less hardware requirements, guarantee of unique interrupts, and ability to send data with the interrupt. MSI also avoids ordering issues with traditional interrupts.
Linux scheduler



Linux schedulerLiran Ben Haim A brief overview of linux scheduler, context switch , priorities and scheduling classes as well as new features. Also provides an overview of preemption models in linux and how to use each model. all the examples are taken from http://www.discoversdk.com
DAIS19: On the Performance of ARM TrustZone



DAIS19: On the Performance of ARM TrustZoneLEGATO project Presented by Valerio Schiavoni @vschiavoni at DAIS 19
The TrustZone technology, available in the vast majority of recent Arm processors, allows the execution of code inside a so-called secure world. It effectively provides hardware-isolated areas of the processor for sensitive data and code, i.e., a trusted execution environment (TEE). The Op-Tee framework provides a collection of toolchain, opensource libraries and secure kernel specifically geared to develop applications for TrustZone. This paper presents an in-depth performance- and energy-wise study of TrustZone using the Op-Tee framework, including secure storage and the cost of switching between secure and unsecure worlds, using emulated and hardware measurements.
Memory model



Memory modelYi-Hsiu Hsu This document discusses memory ordering and synchronization in multithreaded programs. It begins with background on mutexes, semaphores, and their differences. It then discusses problems that can occur with locking-based synchronization methods like mutexes, such as deadlocks, priority inversion, and performance issues. Alternative lock-free programming techniques using atomic operations are presented as a way to synchronize access without locks. Finally, memory ordering, consistency models, barriers, and their implementations in compilers, Linux kernels, and ARM architectures are covered in detail.
Virtualization Support in ARMv8+



Virtualization Support in ARMv8+Aananth C N This slide provides a basic understanding of hypervisor support in ARM v8 and above processors. And these slides (intent to) give some guidelines to automotive engineers to compare and choose right solution!
U Boot or Universal Bootloader



U Boot or Universal BootloaderSatpal Parmar The document provides an overview of Das U-Boot, a universal boot loader used to load operating systems and applications into memory on embedded systems. It discusses U-Boot's features such as its command line interface, ability to load images from different sources, and support for various architectures and boards. It also covers compiling and configuring U-Boot, as well as its basic command set and image support capabilities.
Poll mode driver integration into dpdk



Poll mode driver integration into dpdkVipin Varghese This document discusses integrating a custom Poll Mode Driver (PMD) into DPDK to enable offloading packet processing tasks to multicore or application-specific integrated circuit (ASIC) hardware. A use case of offloading intrusion detection system and IPsec processing to multicore hardware while encrypted SSL traffic is decrypted via the multicore is presented. Developing a custom PMD allows leveraging multicore/ASIC as a line card or load balancer while avoiding issues like extra overhead from additional interfaces, frame reprocessing, and increased latency when using network connections between DPDK and hardware. Performance is improved by directly connecting the multicore/ASIC to DPDK which removes overhead and provides a high-throughput interface.
ARM



ARMPune University ARM processors use RISC architecture and load/store instruction sets. They have low power consumption and support pipelining. ARM profiles include classic processors like ARM7 and ARM9, Cortex-M series for microcontrollers, Cortex-R for real-time systems, and Cortex-A series for operating systems. The ARM register set includes 37 32-bit registers that are accessible in different subsets depending on the processor mode like supervisor, interrupt, abort, or user mode.
Kernel Recipes 2017 - An introduction to the Linux DRM subsystem - Maxime Ripard



Kernel Recipes 2017 - An introduction to the Linux DRM subsystem - Maxime RipardAnne Nicolas Every modern multimedia-oriented ARM SoC usually has a number of display controllers, to drive a screen or an LCD panel, and a GPU, to provide 3D acceleration. The Linux kernel framework of choice to support these controllers is the DRM subsystem.
This talk will walk through the DRM stack, the architecture of a DRM/KMS driver and the interaction between the display and GPU drivers. The presentation is based on the work we have done to develop a DRM driver for the Allwinner SoCs display controller with multiple outputs, such as parallel display interfaces, HDMI or MIPI-DSI. The work done to make the ARM Mali OpenGL driver work on top of a mainline DRM/KMS driver will also be detailed, as well as the more traditional, Mesa-based, solution used in a variety of other platforms.
Maxime Ripard, Free Electrons
Arm modes



Arm modesabhi165 This presentation aims to provide information regarding all seven operational modes of the arm processor except the monitor mode.
Is Linux ready for safety related applications?



Is Linux ready for safety related applications?Alexander Much The presentation is from a talk I gave at the ETAS Connections 2018 event. It details the reasoning for the use of Linux in the Automotive domain for safety-critical systems.
The content is based on our OSADL approach taken in the SIL2MP Linux project
Xvisor: embedded and lightweight hypervisor



Xvisor: embedded and lightweight hypervisorNational Cheng Kung University Xvisor is an open source lightweight hypervisor for ARM architectures. It uses a technique called cpatch to modify guest operating system binaries, replacing privileged instructions with hypercalls. This allows the guest OS to run without privileges in user mode under the hypervisor. Xvisor also implements virtual CPU and memory management to isolate guest instances and virtualize physical resources for multiple operating systems.
Presentation on Raspberry Pi by Sazzad H. IIUC



Presentation on Raspberry Pi by Sazzad H. IIUCshssn7 The document provides information on building a smart mirror using a Raspberry Pi. It discusses that the Raspberry Pi is a small, inexpensive computer that can be used for tasks like word processing and playing videos. It notes that over 3 million Raspberry Pi units have been sold. It then covers the hardware components of the Raspberry Pi, operating systems that can be used, and provides step-by-step instructions for setting up a Raspberry Pi to power a smart mirror, including downloading required software, configuring settings, and rotating the display.
Network Drivers



Network DriversAnil Kumar Pugalia The document discusses Linux network drivers and provides information about:
- The Linux network subsystem and protocol stack, typically using TCP/IP.
- Network interface card (NIC) drivers which provide a uniform interface for the network layer to access physical network cards.
- Key data structures like struct sk_buff and struct net_device that network drivers interact with for packet handling and device operations.
- Functions for network device registration, open/close, interrupt handling, and flow control.
- Examples of simple network drivers and how to write one for a Realtek NIC.
Similar to Andes building a secure platform with the enhanced iopmp (20)
Basic network training2



Basic network training2Arunchai Seangparch This document provides an overview of a basic network training conducted by Global Technology Services, ASEAN. The training covered transport protocols like TCP and UDP, port addressing, routing table structure, router configuration, and packet switching. Key topics included the purpose of routers in forwarding packets, how routing tables determine the best path, and the encapsulation/de-encapsulation process performed by routers at each hop as packets traverse the network from source to destination.
Maximizing High Performance Applications with CAN Bus



Maximizing High Performance Applications with CAN BusJanel Heilbrunn CAN Bus offers speed, reliability and flexibility at an affordable cost, which makes it perfect for embedded applications requiring budget-friendly multi-processor communication. This brand-new ICS webinar offers an introduction to CAN Bus, and is directed at developers with no previous experience with CAN Bus or related technologies.
Maximizing High-Performance Applications with CAN Bus



Maximizing High-Performance Applications with CAN BusICS CAN Bus offers speed, reliability and flexibility at an affordable cost, which makes it perfect for embedded applications requiring budget-friendly multi-processor communication. This brand-new ICS webinar offers an introduction to CAN Bus, and is directed at developers with no previous experience with CAN Bus or related technologies.
FALLSEM2024-25_BEEE309L_TH_VL2024250101214_2024-11-11_Reference-Material-I.pptx



FALLSEM2024-25_BEEE309L_TH_VL2024250101214_2024-11-11_Reference-Material-I.pptxRahultater4 FALLSEM2024-25_BEEE309L_TH_VL2024250101214_2024-10-05_Reference-Material-I.pptx
Chapter14ccna



Chapter14ccnaLakshan Perera This document provides an overview of wide area networks (WANs) and common WAN technologies. It defines WAN terminology like customer premises equipment and demarcation. It describes different WAN connection types and protocols like HDLC, PPP, Frame Relay and VPNs. PPP is examined in detail, including its components, establishment process and authentication methods. Frame Relay is also covered in depth, discussing its encapsulation, DLCI addressing, subinterfaces, mapping and monitoring. Troubleshooting tips are provided for common Frame Relay issues. Finally, an introduction to VPN technologies is given for remote access, site-to-site and extranet deployments.
SMT Verification of the POWER5 and POWER6 High-Performance Processors



SMT Verification of the POWER5 and POWER6 High-Performance ProcessorsDVClub The document discusses the verification of simultaneous multi-threading (SMT) in IBM's POWER5 and POWER6 high-performance processors. It describes the methodology used to verify SMT, including testing shared resource conflicts between threads and dynamic switching between SMT and single-threaded modes. It also compares the microarchitectures of POWER5, which had a centralized out-of-order design, and POWER6, which used a simpler in-order core design.
Arm arc-2016



Arm arc-2016Mohammed Gomaa the First session in ARM Zero to Hero Embedded systems programming course , first part ARM architecture review
chapter 1 &2 RIPv1&2.ppt



chapter 1 &2 RIPv1&2.pptbirhanugebisa1 Routers are networking devices that connect multiple networks and determine the best path for forwarding packets towards their destination. RIP is a distance-vector routing protocol that uses hop counts as its metric to determine the best path. RIP routers exchange routing information every 30 seconds and update their routing tables dynamically based on the information received from neighbor routers.
Introduction to arm processor



Introduction to arm processorRAMPRAKASHT1 This document provides an introduction to the ARM processor architecture. It discusses key aspects of ARM including the ARM programming model, instruction set, memory hierarchy, and development tools. ARM is a popular reduced instruction set computing (RISC) architecture used in many portable electronic devices due to its low power consumption.
Arm Processors Architectures



Arm Processors ArchitecturesMohammed Hilal This document provides information about ARM Ltd and the ARM architecture. It discusses the history and founding of ARM, the basic operating modes and registers in the ARM architecture, the instruction sets and pipeline stages of various ARM processors, and the features of ARM Cortex processors like the Cortex-A8 and Cortex-A9.
How to convert your Linux box into Security Gateway - Part 1



How to convert your Linux box into Security Gateway - Part 1n|u - The Open Security Community How to convert your Linux box into Security Gateway - Part 1 by Murtuja Bharmal @ null Pune Meet, November, 2010
18CS44-MODULE1-PPT.pdf



18CS44-MODULE1-PPT.pdfVanshikaRajvanshi1 The document provides an overview of ARM microprocessors and embedded systems. It discusses ARM architecture basics, including that ARM is a leading provider of RISC microprocessors used widely in embedded systems. It describes typical components of an ARM-based embedded device including the ARM processor, controllers, peripherals, and bus. It also covers memory, software components like boot code and operating systems, and common applications of ARM processors.
An entire concept of embedded systems entire ppt



An entire concept of embedded systems entire pptPrabhakar Captain Introduction to Embedded systems
Embedded Processors & their Architectures
Serial communication
RTOS Concepts
An Entire Concept of Embedded systems 



An Entire Concept of Embedded systems Prabhakar Captain This document provides an overview of embedded systems topics including:
1. It outlines an agenda to cover embedded system basics, processors and architectures, serial communication, real-time operating systems, and embedded programming demos.
2. It defines embedded systems as systems with dedicated software embedded in hardware to perform specific tasks as part of a larger system.
3. It discusses different processor types including microprocessors, microcontrollers, digital signal processors, and application specific integrated processors.
PIC Microcontrollers: Powering Versatile Embedded Solutions"



PIC Microcontrollers: Powering Versatile Embedded Solutions"aadithyaaa2005 PIC microcontrollers, produced by Microchip Technology, are renowned for their robustness, versatility, and widespread use in embedded systems across various industries. These microcontrollers adhere to the principles of RISC (Reduced Instruction Set Computing) architecture and operate on the Harvard architecture, which separates program memory from data memory. This architectural design enhances performance by allowing simultaneous access to both program instructions and data, thereby accelerating execution speed and efficiency.
### Key Features and Architecture
#### CPU Core and Registers:
PIC microcontrollers typically feature an 8-bit or 16-bit CPU core, depending on the model series. The CPU executes instructions fetched from program memory, which is usually implemented as Flash memory or ROM (Read-Only Memory). The core is supported by a set of General Purpose Registers (GPRs) and Special Function Registers (SFRs). GPRs are used for data manipulation and temporary storage during program execution, while SFRs control the operation of peripherals and system configuration.
#### Memory Organization:
PIC microcontrollers utilize a segmented memory model:
- **Program Memory**: Stores the firmware or executable code. This memory can be reprogrammed multiple times in Flash-based microcontrollers, allowing for flexibility in firmware updates and debugging.
- **Data Memory (RAM)**: Stores data variables used during program execution. RAM is volatile, meaning it loses its content when the microcontroller loses power.
- **EEPROM (Electrically Erasable Programmable Read-Only Memory)**: Some PIC microcontrollers incorporate EEPROM memory, which allows for non-volatile storage of data that needs to be retained even when the microcontroller is powered off.
#### Peripherals:
PIC microcontrollers are equipped with a wide range of integrated peripherals, making them highly adaptable to diverse application requirements. Common peripherals include:
- **Timers and Counters**: Used for generating precise time delays, measuring time intervals, and event counting.
- **Analog-to-Digital Converter (ADC)**: Converts analog signals from sensors or external devices into digital values for processing.
- **USART (Universal Synchronous Asynchronous Receiver Transmitter)**: Facilitates serial communication protocols such as RS232, RS485, SPI (Serial Peripheral Interface), and I2C (Inter-Integrated Circuit).
- **PWM (Pulse Width Modulation)**: Generates analog-like signals for controlling devices such as motors, LEDs, and audio amplifiers.
- **Comparators and Voltage References**: Used for comparing analog voltages and generating reference voltages for precise measurement.
#### Oscillator Options:
PIC microcontrollers support various oscillator configurations, including:
- **Internal Oscillator**: Built-in oscillator circuits provide a clock signal for the microcontroller's operation.
- **External Crystal/Ceramic Resonator**: Offers higher accuracy and stability for app
The_MSP430_Slides.pptx



The_MSP430_Slides.pptxGopinathSamydurai The document provides an overview of the MSP430 microcontroller architecture and programming. It discusses the key features of MSP430 including its low power, low cost, and flexible design. The document describes the MSP430 hardware components such as memory, central processing unit, registers, arithmetic logic unit, input/output ports, and peripherals. It also provides details about the MSP430FR2355 microcontroller and associated LaunchPad documentation.
RISC-V 30908 patra



RISC-V 30908 patraRISC-V International This document discusses building cache-coherent scaleout systems using OmniXtend. It describes the OmniXtend architecture, which uses a fully open cache-coherence protocol that works over Ethernet. It then discusses the OmniXtend reference design, compute node architecture, address space, and hardware design. It also covers the single operating system and independent nodes system models, the unified boot process, and status of the current implementation. Lastly, it proposes ways to further develop the system through simulation, emulation, and future work.
Ppt on six month training on embedded system & IOT



Ppt on six month training on embedded system & IOTpreetigill309 the embedded system is a basic building block of IOT. so in this ppt, i have shared my training experience
arm_3.ppt



arm_3.pptMostafaParvin1 The document provides an introduction and overview of the ARM processor architecture. It discusses:
- The origins and evolution of ARM from the original ARM1 through to newer models like ARM7, ARM9, and ARM10.
- The key features of the ARM7 processor, including its 32-bit RISC design, low power consumption, and applications in areas like telecoms, portable devices, and automotive.
- The programmer's model of ARM7 including hardware configurations, operating modes, registers, exceptions, and instruction set. Banked registers allow different modes to have private register sets.
- Exceptions in ARM7 include interrupts, aborts, undefined instructions. Exceptions are prioritized with FI
Ad
More from RISC-V International (20)
WD RISC-V inliner work effort



WD RISC-V inliner work effortRISC-V International One presenter discussed weaknesses found in the LLVM inliner's ability to find optimization opportunities for RISC-V code compared to other compilers, resulting in larger code size. A new approach called mutual inlining (MI) looks at the whole call graph to make inlining decisions and could provide more insights than the LLVM inliner. Integrating MI inside the LLVM inliner by replacing the current inliner with MI was suggested to address these weaknesses.
RISC-V Zce Extension



RISC-V Zce ExtensionRISC-V International The document proposes several extensions to the RISC-V ISA to improve code size efficiency. It analyzes benchmark programs to identify optimization opportunities where common instruction sequences can be fused into single instructions. New instructions proposed include TBLJAL for table-based function calls and jumps, PUSHPOP for saving/restoring multiple registers, and MULIADD for fusing load, multiply and add instructions. Evaluation shows the proposed instructions reduce code size by up to 10% on average across benchmarks when implemented in the compiler.
RISC-V Online Tutor



RISC-V Online TutorRISC-V International This document summarizes a presentation given at the London Open Source Meetup for RISC-V on April 19, 2021. The presentation introduced the RISC-V Online Tutor, an online course for learning RISC-V fundamentals from digital logic to C programming. It provided an overview of the course structure and lessons, which take students through RISC-V assembly, processor design, and application development. It also demonstrated the online learning platform and its ability to interact with remote FPGA hardware during lessons. The goal is to invite community participation and collaboration to further develop the Online Tutor.
London Open Source Meetup for RISC-V



London Open Source Meetup for RISC-VRISC-V International The document announces a London open source meetup for RISC-V on April 19th. RISC-V is a free and open instruction set architecture that enables new processor innovation through open collaboration. It provides free and extensible software and hardware freedom. RISC-V International is a nonprofit organization with over 1,000 members in more than 50 countries that was founded in 2015. The document also advertises upcoming events from the BCS Open Source Specialist Group, including an advocacy event on May 20th and an event on open source in space.
RISC-V Introduction



RISC-V IntroductionRISC-V International Learn about RISC-V, where the technology is, where it's going, workgroups, visibility benefits, and how to engage.
Ziptillion boosting RISC-V with an efficient and os transparent memory comp...



Ziptillion boosting RISC-V with an efficient and os transparent memory comp...RISC-V International This document summarizes a presentation about ZeroPoint Technologies' memory compression technology called Ziptilion. Some key points:
1) Ziptilion uses hardware-accelerated memory compression algorithms to double effective memory capacity and bandwidth. This helps address challenges from the end of Moore's Law.
2) It provides a virtual compressed memory pool (VCP) that is transparent to the operating system. Benchmark results show it provides 20% higher performance than an uncompressed baseline.
3) An evolution called Ziptilion+ aims for over 2.5x compression of machine learning workloads.
4) ZeroPoint also develops ZSWAP+/ZRAM+, which accelerates the popular ZSWAP
Standardizing the tee with global platform and RISC-V



Standardizing the tee with global platform and RISC-VRISC-V International GlobalPlatform provides standards for trusted execution environments (TEEs) that are deployed across billions of devices. The standards define hardware and software specifications for TEEs to securely deliver digital services. GlobalPlatform is working with RISC-V to define TEE configurations for lightweight IoT devices and leverage RISC-V's secure hardware enclave capabilities. The organization's protection profiles and security certification help service providers assess risks when using TEE technologies.
Semi dynamics high bandwidth vector capable RISC-V cores



Semi dynamics high bandwidth vector capable RISC-V coresRISC-V International SemiDynamics introduced two new RISC-V cores, AVISPADO 220 and ATREVIDO 220, both supporting the upcoming RISC-V Vector spec version 1.0. AVISPADO 220 is an in-order core with a technique called "Gazzillion Misses" that allows a high number of outstanding memory requests. ATREVIDO 220 is an out-of-order core also utilizing Gazzillion Misses. SemiDynamics also provides a customizable RISC-V Vector Processing Unit that implements the vector spec and can be integrated with the cores. Both cores and the vector unit are available for licensing.
Security and functional safety



Security and functional safetyRISC-V International The De-RISC initiative aims to develop the first space-amenable RISC-V based computing platform. It involves:
1) Cobham Gaisler developing a fault-tolerant multicore MPSoC based on NOEL-V RISC-V cores.
2) FentISS developing a space-qualified hypervisor called XtratuM for RISC-V.
3) The Barcelona Supercomputing Center developing an extended statistics unit to help manage multicore interference.
4) Thales assessing the platform through benchmarking, executing a satellite software stack, and evaluating a command and data handling use case.
The goal is to have an integrated and validated platform ready
Reverse Engineering of Rocket Chip



Reverse Engineering of Rocket ChipRISC-V International This document summarizes a presentation on reverse engineering the Rocket-Chip SoC generator to develop a customized SoC called Aghaaz. The presentation covers deconstructing the Rocket-Chip software architecture, developing a Micro-Architecture and Software Specification (MASS) document, configuring an Aghaaz SoC using the MASS document, and generating the SoC from the Rocket-Chip generator. Key aspects included developing object-oriented representations of Rocket-Chip modules, flowcharts to explain the code, and configuring an RV32 core with caches and extensions.
RISC-V NOEL-V - A new high performance RISC-V Processor Family



RISC-V NOEL-V - A new high performance RISC-V Processor FamilyRISC-V International This document summarizes the NOEL-V processor family from Cobham Gaisler. It describes the NOEL-V as a RISC-V compliant 64-bit processor with fault tolerance features. It provides details on the processor architecture, peripherals, software ecosystem, verification process, and commercial and open source availability. Examples of projects adopting the NOEL-V include the European H2020 funded De-RISC and SELENE projects for safety-critical computing.
RISC-V 30910 kassem_ summit 2020 - so_c_gen



RISC-V 30910 kassem_ summit 2020 - so_c_genRISC-V International This document proposes a no-human-in-the-loop open-source "idea to manufacturing" SoC compiler. It consists of SoCGen, which generates RTL from a JSON description, and OpenLANE, which produces a clean GDSII layout from the RTL with no human intervention. SoCGen includes a library of open-source verified IP cores and supports multiple bus architectures. OpenLANE uses carefully-curated open-source EDA tools tuned for an open PDK. The goal is to streamline and automate the entire custom SoC design process from concept to silicon to enable more widespread adoption.
RISC-V 30907 summit 2020 joint picocom_mentor



RISC-V 30907 summit 2020 joint picocom_mentorRISC-V International This document discusses the challenges of building and optimizing open RAN systems for 5G networks. It describes Picocom's 5G baseband system-on-chip architecture using multiple RISC-V clusters and hardware accelerators. Maintaining performance and detecting problems is difficult due to the complex timing requirements across hundreds of users. Mentor's embedded analytics solution monitors the system non-intrusively using on-chip sensors to detect issues like timing overruns and help optimize performance both during development and over the lifetime of deployments.
RISC-V 30906 hex five multi_zone iot firmware



RISC-V 30906 hex five multi_zone iot firmwareRISC-V International MultiZone IoT Firmware provides a trusted execution environment (TEE) that shields trusted applications from untrusted third party libraries. It works with any RISC-V processor and provides up to 4 separated hardware and software execution worlds. MultiZone includes pre-integrated security libraries, an RTOS, and connectivity standards to provide a complete and secure IoT stack.
RISC-V 30946 manuel_offenberg_v3_notes



RISC-V 30946 manuel_offenberg_v3_notesRISC-V International 1. Manuel Offenberg of Seagate discussed securing data at the edge using RISC-V and Keystone enclaves to protect data during creation and movement.
2. OpenTitan can provide another layer of trust by securing the root of trust.
3. Endpoint security is crucial for ensuring overall data integrity and trustworthiness when significant data is being generated at billions of sensors and IoT devices.
RISC-V software state of the union



RISC-V software state of the unionRISC-V International This document summarizes the evolution of the RISC-V software ecosystem from 2015 to 2020. It describes how initial ports of key software in 2015, like GCC and Linux, have expanded to include upstream support in most open source software projects today. It outlines remaining priorities like completing support for specifications and filling gaps in programming language and application software support. The document concludes by encouraging continued collaboration to further mature the RISC-V software ecosystem.
Ripes tracking computer architecture throught visual and interactive simula...

Ripes tracking computer architecture throught visual and interactive simula...RISC-V International Ripes is a visual processor simulator and assembly editor for RISC-V that was created to teach computer architecture concepts. It allows interactive simulation and visualization of different processor models, including single-cycle, pipelined, and models with caching. Ripes uses the Visual Simulation of Register Transfer Logic (VSRTL) framework, which generates circuit visualizations from processor descriptions. This allows Ripes to simulate various RISC-V processors and visualize their data paths during execution. Ripes has been expanded over time to support cache simulation and integration with C toolchains.
Porting tock to open titan



Porting tock to open titanRISC-V International This document discusses porting the Tock operating system to the OpenTitan project. It provides background on OpenTitan and Tock, describes the status of the porting work, and highlights a deep dive into implementing USB and CTAP support on Tock running on OpenTitan hardware. Key points covered include OpenTitan using the Ibex RISC-V core, Tock being designed for small platforms without MMUs and enforcing security through Rust, the interface for Tock applications, and modules already supported through the mainline Tock project.
Open j9 jdk on RISC-V



Open j9 jdk on RISC-VRISC-V International The document discusses porting OpenJ9 JDK to RISC-V architecture. It involves preparing the software toolchain for cross-compilation to RISC-V, preparing hardware like the HiFive Unleashed development board, and developing OpenJ9 JDK through a mix of local and cross compilation. The status shows OpenJ9 JDK can execute in interpreter mode on the RISC-V emulator and HiFive board running Debian, with future work planned on JIT support, different GC strategies, and supporting other Java versions.
Open source manufacturable pdk for sky water 130nm process node



Open source manufacturable pdk for sky water 130nm process nodeRISC-V International The document discusses an open source manufacturable process design kit (PDK) for the SkyWater 130nm process node developed by Google and SkyWater. It provides a link to slides about the PDK located at https://j.mp/rv20-sky130. The PDK will allow for open hardware design using the SkyWater 130nm fabrication process.
Ad
Recently uploaded (20)
HCL Nomad Web – Best Practices and Managing Multiuser Environments



HCL Nomad Web – Best Practices and Managing Multiuser Environmentspanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-and-managing-multiuser-environments/
HCL Nomad Web is heralded as the next generation of the HCL Notes client, offering numerous advantages such as eliminating the need for packaging, distribution, and installation. Nomad Web client upgrades will be installed “automatically” in the background. This significantly reduces the administrative footprint compared to traditional HCL Notes clients. However, troubleshooting issues in Nomad Web present unique challenges compared to the Notes client.
Join Christoph and Marc as they demonstrate how to simplify the troubleshooting process in HCL Nomad Web, ensuring a smoother and more efficient user experience.
In this webinar, we will explore effective strategies for diagnosing and resolving common problems in HCL Nomad Web, including
- Accessing the console
- Locating and interpreting log files
- Accessing the data folder within the browser’s cache (using OPFS)
- Understand the difference between single- and multi-user scenarios
- Utilizing Client Clocking
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
Linux Support for SMARC: How Toradex Empowers Embedded Developers



Linux Support for SMARC: How Toradex Empowers Embedded DevelopersToradex Toradex brings robust Linux support to SMARC (Smart Mobility Architecture), ensuring high performance and long-term reliability for embedded applications. Here’s how:
• Optimized Torizon OS & Yocto Support – Toradex provides Torizon OS, a Debian-based easy-to-use platform, and Yocto BSPs for customized Linux images on SMARC modules.
• Seamless Integration with i.MX 8M Plus and i.MX 95 – Toradex SMARC solutions leverage NXP’s i.MX 8 M Plus and i.MX 95 SoCs, delivering power efficiency and AI-ready performance.
• Secure and Reliable – With Secure Boot, over-the-air (OTA) updates, and LTS kernel support, Toradex ensures industrial-grade security and longevity.
• Containerized Workflows for AI & IoT – Support for Docker, ROS, and real-time Linux enables scalable AI, ML, and IoT applications.
• Strong Ecosystem & Developer Support – Toradex offers comprehensive documentation, developer tools, and dedicated support, accelerating time-to-market.
With Toradex’s Linux support for SMARC, developers get a scalable, secure, and high-performance solution for industrial, medical, and AI-driven applications.
Do you have a specific project or application in mind where you're considering SMARC? We can help with Free Compatibility Check and help you with quick time-to-market
For more information: https://www.toradex.com/computer-on-modules/smarc-arm-family
DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptx



DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptxJustin Reock Building 10x Organizations with Modern Productivity Metrics
10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, ‘The Coding War Games.’
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method we invent for the delivery of products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches actually work? DORA? SPACE? DevEx? What should we invest in and create urgency behind today, so that we don’t find ourselves having the same discussion again in a decade?
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
Semantic Cultivators : The Critical Future Role to Enable AI



Semantic Cultivators : The Critical Future Role to Enable AIartmondano By 2026, AI agents will consume 10x more enterprise data than humans, but with none of the contextual understanding that prevents catastrophic misinterpretations.
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
tecnologias de las primeras civilizaciones.pdf



tecnologias de las primeras civilizaciones.pdffjgm517 descaripcion detallada del avance de las tecnologias en mesopotamia, egipto, roma y grecia.
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
How Can I use the AI Hype in my Business Context?



How Can I use the AI Hype in my Business Context?Daniel Lehner 𝙄𝙨 𝘼𝙄 𝙟𝙪𝙨𝙩 𝙝𝙮𝙥𝙚? 𝙊𝙧 𝙞𝙨 𝙞𝙩 𝙩𝙝𝙚 𝙜𝙖𝙢𝙚 𝙘𝙝𝙖𝙣𝙜𝙚𝙧 𝙮𝙤𝙪𝙧 𝙗𝙪𝙨𝙞𝙣𝙚𝙨𝙨 𝙣𝙚𝙚𝙙𝙨?
Everyone’s talking about AI but is anyone really using it to create real value?
Most companies want to leverage AI. Few know 𝗵𝗼𝘄.
✅ What exactly should you ask to find real AI opportunities?
✅ Which AI techniques actually fit your business?
✅ Is your data even ready for AI?
If you’re not sure, you’re not alone. This is a condensed version of the slides I presented at a Linkedin webinar for Tecnovy on 28.04.2025.
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
Big Data Analytics Quick Research Guide by Arthur Morgan



Big Data Analytics Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
Andes building a secure platform with the enhanced iopmp
- 1. Building a Secure Platform with the Enhanced IOPMP Shan-Chyun Ku, Deputy Technical Director Andes Technology December 9, 2020
- 2. Taking RISC-V® Mainstream 2 Biography of Shan-Chyun Ku Technical Areas • SoC Architect, SoC Security • Parallel Algorithms, System-level Performance Analysis Industry Experience Andes, 2019 Deputy Technical Director of Architecture Realtek, 2009 Manager of SoC, VoIP, and BSP Cadence, 2006 Member of Consulting Staff Faraday, 2001 Deputy Manager of Core Technology Education • PhD, CS, National Tsing-Hua University (Taiwan) • BS, CS, National Tsing-Hua University (Taiwan)
- 3. Why Have IOPMP? Enhanced IOPMP Example: Root-of-Trust AndeSentry™ Brief Agenda 1 2 3 4
- 4. Taking RISC-V® Mainstream 4 Why Have IOPMP?
- 5. Taking RISC-V® Mainstream 5 Why Have IOPMP? • Vulnerabilities of platforms give hackers the chance to access or tamper with sensitive data or devices. • PMP: checks the accesses issued from RISC-V harts. • IOPMP: checks the accesses issued from other bus masters.
- 6. Taking RISC-V® Mainstream 6 A Platform without an IOPMP mem controller RV hart PMP SRAM/ ROM eFuse General DMA non-RV core off-chip storage high-speed bus MMIO bus (arrow: bus cmd direction) trans. transactions issued from RV hart: checked by PMP
- 7. Taking RISC-V® Mainstream 7 A Platform without an IOPMP transactions issued from DMA: Never check Malicious SW can utilize DMA to access any data. mem controller RV hart PMP SRAM/ ROM eFuse General DMA non-RV core off-chip storage trans.
- 8. Taking RISC-V® Mainstream 8 A Platform with an IOPMP transactions issued from other masters: checked IOPMP mem controller RV hart PMP SRAM/ ROM eFuse General DMA non-RV core off-chip storage trans. IOPMP IOPMP
- 9. Taking RISC-V® Mainstream 9 What is an IOPMP?
- 10. Taking RISC-V® Mainstream 10 PMP and IOPMP • PMP: check the transactions issued from RISC-V harts • IOPMP: check the transactions issued by other bus maters or by another subsystem • Similarity: both are ordered rule-based checkers • Status: PMP is ratified while IOPMP is still ongoing
- 11. Taking RISC-V® Mainstream 11 Our Enhancement and Modification • What we modify to the current IOPMP proposals: – Skip checked transactions (especially checked by PMP) – Provide flexible methods to respond to an illegal access, e.g. forged data, a bus error, or an interrupt. – Optionally support speculative accesses. – Support up to 65,536 entries by using page and page index. – Support up to 16,384 bus masters, by modifying the encoding scheme. – Support “all bus masters” option, easer to block out all accesses. – Suggest methods to integrate with existing subsystems or nested subsystems. • IOPMP: refers to the proposed enhancement for the rest talk
- 12. Taking RISC-V® Mainstream 12 MID of Bus Masters • Master ID (MID): uniquely identify – a bus master, or – a group of masters with the same permission. • Be fixed before entering REE, if it is configurable. • Multi-channel DMA: one permission an MID • Multi-privilege DMA: one privilege an MID • MID=0 implies a trusted master. – A RISC-V core with a well-configured PMP. (more detail later)
- 13. Taking RISC-V® Mainstream 13 MID of a Transaction • Every transaction carries an MID, initialized to the MID of the master issuing the transaction. • The MID is changed to zero or even omitted after the transaction passes a checker. • Such a transaction bypasses subsequent IOPMPs’ checking.
- 14. Taking RISC-V® Mainstream 14 MID Examples mem controller Regulated RISC-V core SRAM/ ROM peripherals 2-ch DMA Other bus master (unregulated core or device w/ DMA) off-chip storage PMP MID=0 MID!=0 channel no ch0.MID (!=0) ch1.MID (!=0) IOPMP IOPMP
- 15. Taking RISC-V® Mainstream 15 MID Modification Rules • While a transaction passes a regulated checker, depicted later, its MID can be changed to zero or even be omitted: – Rule-1: MID 0 if the transaction passes 1+ regulated checker. – Rule-2: MID omitted on a bus if every slave port of it is a leaf device, not a bridge connecting to another bus as a master, or another Rule-2 bus, and all possible transactions sent to the bus are legal (e.g. MID=0 or no MID).
- 16. Taking RISC-V® Mainstream 16 Example of MID Modification Rules a bus WITHOUT MID a bus with MID RISC-V PMP MID=0 Bus Master MID!=0 IOPMP device device device device IOPMP RISC-V PMP IOPMP Bus Master MID!=0 no MID by R1 by R2 by R2 no MID no MID no MID
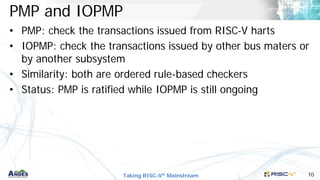
- 17. Taking RISC-V® Mainstream 17 MID[3:0] MID Encoding in IOPMP Entry • An MID uses up to 14 bits, or 16,384 MIDs. • An IOPMP entry contains up to 16 MIDs, by “MID.h” and “MID.l”. MID[13:0] MID.h[9:0] MID.l[15:0] == && Does the entry contain the MID? MID[13:4] Lower 4 bits uses bitmap encoding Upper 10 bits uses binary encoding
- 18. Taking RISC-V® Mainstream 18 Secure Boot • Secure boot plays an important role in a secure platform. • Basically initialize and lock: PMP, IOPMP, and MID – MIDs (if applicable) – Private regions for each master and each mode • e.g. keys, random seed, device id, private data, Monitor space, anti- rollback counter, IOPMP control registers and other peripherals’ control registers... – NX and prohibited regions for each master and mode • prevent Security Monitor from unintentionally executing malicious code • Bring up the Security Monitor that makes the runtime environment secured.
- 19. Taking RISC-V® Mainstream 19 Regulated Checkers • Initialized to provide Security Monitor and sensitive data a baseline protection. It should – prevent U/S-mode from accessing, – prevent Monitor from unintentionally executing unwanted codes, – prevent DMA from accessing unwanted space, – prevent non-Monitor from controlling IOPMPs, and – protect sensitive data even when Monitor is compromised.
- 20. Taking RISC-V® Mainstream 20 Regulated Checker • A PMP is a regulated checker if – It is initialized according to the previous requirements (P19), and – The initialization is performed during the secure boot. • A IOPMP is a regulated checker if – It is initialized according to the previous requirements, – All possible transactions to control the IOPMP are regulated. A transaction passing all regulated checkers on its way is regulated.
- 21. Taking RISC-V® Mainstream 21 Secure Platforms and IOPMPs • All possible transactions are regulated. • IOPMP can be placed close to masters or close to devices. IOPMP-1 mem controller RV-core PMP SRAM/ ROM IOPMP-2 eFuse Crypto engine NIC w/ DMA off-chip storage IOPMP-1 mem controller RV-core PMP SRAM/ ROM IOPMP-2 eFuse Crypto engine NIC w/ DMA off-chip storage close to devices close to masters
- 22. Taking RISC-V® Mainstream 22 An Example of Root-of-Trust
- 23. Taking RISC-V® Mainstream 23 An Example Root-of-Trust Utilizing PMP, IOPMP, and Secure Boot high-speed bus MMIO bus (arrow: bus cmd direction) mem controller RV hart PMP SRAM/ ROM eFuse Crypto Engine NIC w/ DMA off-chip storage K.B. Key ARcnt eFuse: store sensitive data • Keys: to encrypt and decrypt for networks or off-chip storages • ARcnt: an anti-rollback counter for updatable firmware Crypto engine: encryption & decryption • Direct memory access: cipher and plain text • Key buffer (K.B.): store cipher keys IOPMP-2 IOPMP-1
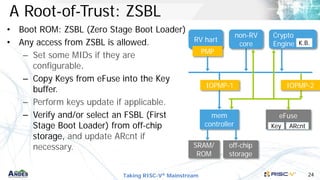
- 24. Taking RISC-V® Mainstream 24 A Root-of-Trust: ZSBL • Boot ROM: ZSBL (Zero Stage Boot Loader) • Any access from ZSBL is allowed. – Set some MIDs if they are configurable. – Copy Keys from eFuse into the Key buffer. – Perform keys update if applicable. – Verify and/or select an FSBL (First Stage Boot Loader) from off-chip storage, and update ARcnt if necessary. mem controller RV hart PMP SRAM/ ROM eFuse Crypto Engine non-RV core off-chip storage K.B. Key ARcnt IOPMP-2 IOPMP-1
- 25. Taking RISC-V® Mainstream 25 A Root-of-Trust: ZSBL to FSBL • Set and lock these rules in highest priority – eFuse: no access (PMP+IOPMP2) – Key buffer: no access (PMP+IOPMP2) – Control registers of Crypto engine: • PMP: M-mode only • IOPMP2: no one else but MID=0 • Jump to selected FSBL • Do system initialization. • Set more MIDs if necessary. • Verify and/or select one Security Monitor. • Load the Security Monitor into protected memory. mem controller RV hart PMP SRAM/ ROM eFuse Crypto Engine non-RV core off-chip storage K.B. Key ARcnt IOPMP-2 IOPMP-1
- 26. Taking RISC-V® Mainstream 26 A Root-of-Trust: FSBL • Set and lock more rules. Example: • Monitor region: – PMP for code and data: M-mode only – IOPMP-1 for code: no one else but MID=0 – IOPMP-1 for crypto buffer: Crypto engine only • DMA buffers: used by S/U-mode – PMP: NX for M-mode – IOPMP-1: the only place DMAs can access • Non-Monitor region: – PMP: NX M-mode – MID control registers: non-writable – IOPMP control registers: • PMP: M-mode only • IOPMP-2: no one else but MID=0 mem controller RV hart PMP SRAM/ ROM eFuse Crypto Engine non-RV core off-chip storage K.B. Key ARcnt IOPMP-2 IOPMP-1
- 27. Taking RISC-V® Mainstream 27 A Root-of-Trust: FSBL to Monitor • Finally, jump to Security Monitor! mem controller RV hart PMP SRAM/ ROM eFuse Crypto Engine non-RV core off-chip storage K.B. Key ARcnt IOPMP-2 IOPMP-1
- 28. Taking RISC-V® Mainstream 28 A Brief of AndeSentry™
- 29. Taking RISC-V® Mainstream 29 AndeSentry™ • An Open Framework: Threat mitigation: from cyber attacks to physical attacks – Flexible • Selectable components for different kind of requirements • Robustness driven, power driven, cost driven, and so on – Scalable • Systems built by single MCU, multi-core, or even sub-systems. – Trustable • Andes with over 15-year experience in the processor industry • Partners: strong domain know-how, and rich experience in the certification
- 30. Taking RISC-V® Mainstream 30 AndeSentry™ Security Framework AndeSentry™ Security Solution Trusted Execution Environment: Secure boot Security monitor Root-of-Trust Secure Interruption Physical Attack Mitigation: Side-channel mitigation Fault-injection protection Secure debugger Secure storage Security element Runtime Protection: Stack under/overflow protection ROP protection Code modification protection Control flow hijack protection Crypto Acceleration: Hardware crypto engine Crypto-efficiency ISA Security element
- 31. Taking RISC-V® Mainstream 31 AndeSentry™ Components PMP TRNG Root-of-Trust Security element Crypto-efficiency ISA Crypto engine Secure debug IOPMP Secure Storages off-chip on-chip Crypto Library Security Monitor REE OS TEE OS REE Apps TEE Apps M-mode U-mode and/or S-mode HW SW • • • • • • • • • • • • CRTL flow hijack protection Code protection ROT protection Fault injection protection Stack protection and many more...
- 32. Taking RISC-V® Mainstream 32 Andes Security Partners and Ecosystem
- 33. THANK YOU Insert the Subtitle of Your Presentation




