Stop Passing the Bug: IoT Supply Chain Security
- 1. SESSION ID:SESSION ID: #RSAC Dr Ralf Huuck Stop Passing the Bug: IoT Supply Chain Security GPS-R03 Director & Senior Architect Synopsys
- 3. #RSAC Hack One – Control ‘Em All Each IoT Product million times the same. One Breach = One Clone Army. Billions of IoT devices in the near future.
- 5. #RSAC MIRAI IoT Botnet 145,607 hacked IP cameras and DVRs. Hardcoded PWD from supplied OEM components.
- 6. #RSAC Truly Complex IoT Systems
- 7. #RSAC Looking Inside Software Components
- 8. #RSAC X-Ray Your Software: How Bad Is It?
- 9. #RSAC Reference Vulnerability Source National Vulnerability Database (NVD) Common Vulnerabilities and Exposure (CVE) = vulnerability naming Common Vulnerability Scoring System (CVSS) = severity
- 10. #RSAC CVE Example Currently: 86575 CVE entries
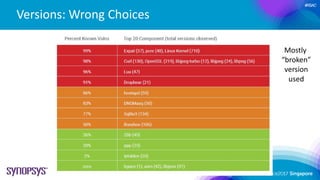
- 11. © 2016 Synopsys, Inc. 11 5,767 Total Software Scanned 2,041 Vulnerable Software 35.2% 49,478 Identified Third-Party Components 13,098 Vulnerable Components 26.5% A total of 5,767 pieces of software were scanned. 35.22% contained at least 1 vulnerable components A total of 49,478 third-party components were identified within the scanned software. 26.47% of the 3rd-party components contained vulnerabilities 2014 Study Results Products Components
- 12. © 2016 Synopsys, Inc. 12 Who is Affected? ROUTER 4,269 CVEs affecting 70 Components SMART TV MULTIFUNCTION PRINTER WI-FI ACCESS POINT BABY MONITOR CAR INFOTAINMENT THERMOSTAT INFUSION PUMP SMART PHONE SECURITY CAMERA 407 CVEs affecting 6 Components 9 CVEs affecting 18 Components 724 CVEs affecting 18 Components 909 CVEs affecting 44 Components 888 CVEs affecting 26 Components 858 CVEs affecting 17 Components 1,174 CVEs affecting 17 Components 54 CVEs affecting 1 Components 226 CVEs affecting 3 Components
- 13. #RSAC Rinse, Repeat: 2017 Open Source
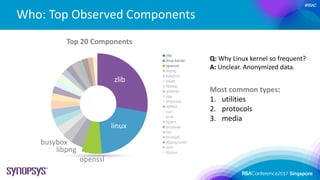
- 15. #RSAC Who: Top Observed Components Q: Why Linux kernel so frequent? A: Unclear. Anonymized data. zlib linux openssl libpng busybox Top 20 Components Most common types: 1. utilities 2. protocols 3. media
- 16. #RSAC How Often: Distribution of All CVEs Frequency of all CVEs Observed Heartbleed (CVE 2014-0160) still in top 50%
- 17. #RSAC How old? CVEs by Age dates back to 1999! CVE Entries by Year 45% from 2013 or older 2016 2015 2014 2013
- 18. #RSAC Impact: Distribution By Severity (CVSS) 58 3
- 20. #RSAC How did the Celebrities Fare?
- 21. #RSAC 2017 Most Common Causes Most Common CWE: #119 Improper restrictions of Operations within Memory Buffer. Second: #20: Improper Input Validation
- 26. #RSAC Your IoT Supply Chain
- 27. #RSAC Securing IoT Supply Chain
- 28. #RSAC Securing IoT Supply Chain
- 29. #RSAC Your Approved IoT Device
- 30. #RSAC 3 Core Steps 1. Secure Each Component 2. Trust but Verify Composition 3. Independent Validation
- 31. #RSAC Step 1: Secure Each Component
- 32. #RSAC Step 1: Secure Each Component IoT Security Ideal inexpensive minimal expertise quick to achieve
- 33. #RSAC Automatic Tools to the Rescue Static Analysis Runtime Monitors Penetration Testing
- 34. #RSAC Static Analysis: Automatic Code Inspection XSS, Injections, CSRF, Security vulnerabilities Memory violations, Logic errors, Defects Race conditions, Memory corruption, Concurrency errors, Deadlocks
- 35. #RSAC Example: Fix While Coding
- 36. #RSAC Pen Testing: Automatic Application Fuzzing dangerous data
- 37. #RSAC Example: Pen Testing APIs and Protocols Protocols Hardening Software systems and components communicate Hack Yourself First Finding unknown, exploitable vulnerabilities Proactive Fixes Patch holes before exploitation
- 38. #RSAC Runtime Monitoring: Augment Your Applications exercise common attack vectors observe failures and record causes
- 39. #RSAC Step 2: Secure Integration / Composition
- 40. #RSAC Step 2: Secure Integration / Composition IoT Security Ideal inexpensive minimal expertise quick to achieve
- 41. #RSAC Composition Analysis: Product In, Report Out
- 42. #RSAC Step 3: Independent Validation
- 43. #RSAC Step 3: Independent Validation
- 44. #RSAC Step 3: Independent Validation Standards Insurance Certification
- 45. #RSAC Example: UL 2900 Cybersecurity Assurance Program Assessment with time-bounded certification horizon.
- 48. #RSAC No Single Bullet IoT Security Solution 48
- 49. #RSAC Use (Automated) Tools Everything else does not scale. Don’t drive yourself crazy.
- 50. #RSAC Apply to Your Supply Chain 50 Next week: draw a map of 1st party and 3rd party components in your (sub)product “grep” for all licenses in your (sub)project In the first three months: look up CVE information of your 3rd party components in the NVD make a plan how to monitor CVE status for your 3rd party components Within six months: use FOSSology or similar to automate license discovery establish an automated CVE monitoring approach
- 51. #RSAC Thank You! [email protected] @ no twitter #D2 with M.Tech