Introduction to VoIP, RTP and SIP
13 likes10,306 views
Join us for an introductory webinar on VoIP and learn: - The fundamental principles of VoIP including RTP and SIP - What voice metrics to measure and why they matter - The different methods to monitor and troubleshoot VoIP
1 of 20
Downloaded 322 times













![15
E-Model (ITU-T Recommendation G.107, 1998-2014)
Based on a mathematical model in which the individual transmission parameters are transformed into
different individual "impairment factors” such as codec characteristics, delay, loss ratio, discard ratio,
etc., to obtain a quality metric called R factor:
Mean Opinion Score (MOS)
Basic signal-
to-noise ratio
Delay
impairment
Equipment
impairment
Advantage
factor
(expectation)
• Network latency
• De-jitter buffer size
• Ie (codec)
• Packet loss robustness (codec)
• Packet loss probability
• Network latency
Simultaneous
impairment
1 Calculation of the transmission rating factor, R
ccording to the equipment impairment factor method, the fundamental principle of the E-model
ased on a concept given in the description of the OPINE model (see [b-ITU-T P-Sup.3]).
sychological factors on the psychological scale are additive.
he result of any calculation with the E-model in a first step is a transmission rating factor R, whic
ombines all transmission parameters relevant for the considered connection. This rating factor R
omposed of:
AIe-effIdIsRoR +−−−= (7-1
o represents in principle the basic signal-to-noise ratio, including noise sources such as circu
oise and room noise. Factor Is is a combination of all impairments which occur more or le
multaneously with the voice signal. Factor Id represents the impairments caused by delay and th
fective equipment impairment factor Ie-eff represents impairments caused by low bit-rate codec
also includes impairment due to randomly distributed pack losses. The advantage factor A allow
r compensation of impairment factors when the user benefits from other types of access to th
ser. The term Ro and the Is and Id values are subdivided into further specific impairment value
he following clauses give the equations used in the E-model.](https://image.slidesharecdn.com/introductiontovoiceslideshare-160930204501/85/Introduction-to-VoIP-RTP-and-SIP-16-320.jpg)




Ad
Recommended
Wazuh Pre.pptx



Wazuh Pre.pptxemnabenamor3 wazuh est une solution open source d dd ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff ggg ggg ggg gttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttttt
Curso - traduccion_Leo.pptx



Curso - traduccion_Leo.pptxNelsonFigueira6 The document provides an introduction to Issabel, an open-source unified communications solution. It discusses that Issabel is a free licensed software based on Asterisk that allows for IP telephony, email, fax, instant messaging and other integrations. It also covers Issabel's architecture, versioning process, supported hardware, functionalities such as call recording and IVR, and history starting as a reporting interface for Asterisk.
Mpls technology



Mpls technologyNaveen Sihag MPLS is a technology that allows traffic to be forwarded through networks based on short fixed length labels rather than long network addresses, enabling traffic engineering and quality of service. It works by classifying packets into forwarding equivalency classes, assigning labels when packets enter the MPLS domain, and using label switching to forward packets along label switched paths. MPLS provides advantages like simplified packet forwarding, efficient traffic engineering capabilities, and virtual private networks.
Pstn (Public Switched Telephone Networks)



Pstn (Public Switched Telephone Networks)rahuldaredia21 PSTN is the global collection of interconnects originally designed to support circuit switched voice communication.
The PSTN provides traditional Plain Old Telephone Service (POTS), also known as “landline phone” service , to residences & many other establishments.
Parts of the PSTN are also utilized for DSL, voIP & other Internet based network technologies.
Gpon the technology --rev 1



Gpon the technology --rev 1guerrid This document discusses the GPON (Gigabit-capable Passive Optical Network) technology for fiber access networks. Some key points:
- GPON supports high-bandwidth, long-reach (up to 20km), and triple-play services, making it widely adopted by carriers.
- It uses a point-to-multipoint architecture with a single optical fiber shared between an OLT and multiple ONUs using passive splitters.
- Wavelength division multiplexing is used with downstream at 1490nm and upstream at 1310nm. Time division multiple access manages upstream bandwidth sharing between ONUs.
- Typical deployments include fiber to the home (FTTH),
Public Switched Telephone Network (PSTN)



Public Switched Telephone Network (PSTN)J.T.A.JONES The document discusses various aspects of the Public Switched Telephone Network (PSTN). It covers topics like modulation/demodulation schemes used to convert between analog and digital signals, the bandwidth of telephone lines, traditional modem standards like V.32, V.90, ADSL, techniques used for multiplexing like TDM and WDM, and components within switching offices. It provides technical details on how analog voice signals are converted to digital, transmitted through digital trunks, and switched within the network.
Voice over Internet Protocol (VoIP)



Voice over Internet Protocol (VoIP)Fringe Division Presentation on VoIP and its applications
especially focused on medical applications of VoIP
Everything You Need To Know About ChatGPT



Everything You Need To Know About ChatGPTExpeed Software ChatGPT is a revolutionary addition to the world since its introduction in 2022. A big shift in the sector of information gathering and processing happened because of this chatbot. What is the story of ChatGPT? How is the bot responding to prompts and generating contents? Swipe through these slides prepared by Expeed Software, a web development company regarding the development and technical intricacies of ChatGPT!
Introduction into SIP protocol



Introduction into SIP protocolMichal Hrncirik Brief introduction into SIP protocol, how it works, common problems to solve. Tech. details about handshake, SIP Trunks and SIP trunking. Market research.
Session initiation-protocol



Session initiation-protocolSanthosh Somu The document discusses the Session Initiation Protocol (SIP), which allows for multimedia communication sessions over IP networks. SIP establishes sessions for voice, video, messaging and other applications. It uses requests and responses to initiate sessions between users, locate users, invite them to sessions, and terminate sessions. SIP relies on user agents, proxy servers, redirect servers and registrar servers. It enables mobility and flexibility in setting up and modifying communication sessions across different devices.
Sip



SipAnirban Roy The Session Initiation Protocol (SIP) is the dominant signaling protocol used in VoIP today. It is
responsible for the establishment, control and termination of sessions by exchanging ASCII-text-based
messages between the endpoints. This post goes through the basic components of SIP: messages and
logical entities.
Calling VoWiFi... The Next Mobile Operator Service is here... 



Calling VoWiFi... The Next Mobile Operator Service is here... Cisco Canada The document provides housekeeping notes for a Cisco Connect Toronto 2015 session. It reminds attendees to silence phones and laptops, ask questions during the session, and complete a survey for a chance to win a headset. It also provides information on Cisco dCloud and accessing demos and labs, and discusses VoWiFi including benefits for mobile operators, architectures, and call flows.
Introduction to SIP(Session Initiation Protocol)



Introduction to SIP(Session Initiation Protocol)William Lee Session Initiation Protocol (SIP) is a signaling protocol for managing multimedia communication sessions over Internet Protocol (IP) networks. SIP can be used to establish two-party or multiparty sessions that include voice, video, chat, gaming, and other forms of media. The document introduces SIP architecture, message format, and common call flows including registration, basic call setup, call modification, call hold, and three-way conferencing.
Voip



VoipMuhammad Hamza This document discusses VoIP (Voice over Internet Protocol) technologies. It begins by defining VoIP and how it allows phone calls to be made over the internet instead of traditional telephone networks. It then explores enterprise VoIP systems, hosted VoIP, VoIP phones, and the differences between circuit switching used in PSTN networks and packet switching used in VoIP. Challenges of VoIP like latency, jitter and packet loss are outlined, as well as advantages such as lower costs, flexibility and portability. Popular VoIP service providers like Google Voice and Skype are compared.
session initiation protocol - SIP



session initiation protocol - SIPMahmoud Abudaqa SIP is an application-layer protocol for establishing multimedia sessions over IP networks. It can be used to initiate voice, video, and instant messaging communications. SIP works by having user agents (clients and servers) exchange SIP request and response messages. These messages contain information about session setup, modification, and termination. Some key SIP components include user agents, proxy servers, registrar servers, and redirect servers. SIP messages use a request-response transaction model and contain start lines, headers, and optional message bodies. Common request methods are INVITE, ACK, BYE, and REGISTER. Typical response codes include 100-199 (informational), 200-299 (success), 300-399 (redirection), 400-499
VoWifi 03 - vowifi epdg aaa and architecture (pdf ppt)



VoWifi 03 - vowifi epdg aaa and architecture (pdf ppt)Vikas Shokeen This document provides an overview of Voice over WiFi (VoWifi) including the key nodes involved and their roles. It discusses the user equipment (UE), evolved Packet Data Gateway (ePDG), AAA server, PGW, HSS, IMS, and PCRF nodes. The UE establishes an IPsec tunnel with the ePDG to access the EPC over an untrusted WiFi network. The ePDG and AAA server perform authentication. The existing PGW, HSS, IMS, and PCRF nodes are reused to support VoWifi calls and handovers between VoLTE and VoWifi. Key performance indicators for each node are also measured to ensure quality of VoWifi user experience
OSI Layers



OSI LayersKishore Kumar This study guide is intended to provide those pursuing the CCNA certification with a framework of what concepts need to be studied. This is not a comprehensive document containing all the secrets of the CCNA, nor is it a “braindump” of questions and answers.
I sincerely hope that this document provides some assistance and clarity in your studies.
SIP - Introduction to SIP Protocol



SIP - Introduction to SIP ProtocolLivePerson SIP - More than meets the eye
Speakers:
Ofer Cohen - VOIP Group Leader, LivePerson
Yossi Maimon - VOIP Technical Leader, LivePerson
An Introduction to the SIP protocol.
SIP Position in telecommunication networks and the content services.
What is SIP:
The Session Initiation Protocol (SIP) is a signaling communications protocol, widely used for controlling multimedia communication sessions such as voice and video calls over Internet Protocol (IP) networks.
The protocol defines the messages that are sent between peers which govern establishment, termination and other essential elements of a call. SIP can be used for creating, modifying and terminating sessions consisting of one or several media streams. SIP can be used for two-party (unicast) or multiparty (multicast) sessions. Other SIP applications include video conferencing, streaming multimedia distribution, instant messaging, presence information, file transfer, fax over IP and online games.
(Source: Wikipedia)
Voip



VoipRajan Kumar VoIP is a technology that allows phone calls to be made over the internet. It works by converting analog voice signals to digital data that is sent in packets over IP networks. Common VoIP technologies include H.323, SIP, and RTP. VoIP can be implemented through analog telephone adapters, IP phones, or computer-to-computer calls. While VoIP provides benefits like low costs and integration with other applications, it also faces challenges related to quality of service, emergency calls, and lack of redundancy in case of power failures.
SIP Trunking



SIP Trunkingorionnow SIP (Session Initiation Protocol) trunking connects a company's PBX to the existing telephone network infrastructure via the internet using VoIP. It was originally designed in 1996 and standardized in 2000. SIP trunking provides benefits like virtual phone numbers, reduced equipment needs, business continuity, and flexible trunk quantities. However, considerations must include system compatibility, additional bandwidth requirements, and challenges like supporting fax/modem traffic and 911 calls. The document discusses ideal environments for SIP trunking like companies with multiple locations, seasonal needs, or those seeking increased functionality. It also reviews cost components and provides an overview of SIP trunking.
SOMEIP-protocol.pptx



SOMEIP-protocol.pptxPushkarBaheti1 SOME/IP is a protocol specification that defines formats and communication patterns for sharing services over IP networks in vehicles. It includes an on-wire format that defines fields like service ID, method ID, and message type. The protocol uses UDP and TCP transports and defines request/response and publish/subscribe communication patterns. Events are always grouped in event groups and can be subscribed to, while fields use request/response calls.
Understanding Session Border Controllers



Understanding Session Border Controllersstefansayer Over the past 10 years the Session Initiation Protocol (SIP) has moved from the toy of researchers and academics to the de-facto standard for telephony and multimedia services in mobile and fixed networks.
Probably one of the most emotionally fraught discussions in the context of SIP was whether Session Border Controllers (SBC) are good or evil.
SIP was designed with the vision of revolutionizing the way communication services are developed, deployed and operated. Following the end-to-end spirit of the Internet SIP was supposed to turn down the walled gardens of PSTN networks and free communication services from the grip of large telecom operators. By moving the intelligence to the end systems, developers were supposed to be able to develop new communication services that will innovate the way we communicate with each other.
This was to be achieved without having to wait for the approval of the various telecommunication standardization groups such as ETSI or the support of incumbent telecoms.
Session border controllers are usually implemented as SIP Back-to-Back User Agents (B2BUA) that are placed between a SIP user agent and a SIP proxy. The SBC then acts as the contact point for both the user agents and the proxy. Thereby the SBC actually breaks the end-to-end behavior of SIP, which has led various people to deem the SBC as an evil incarnation of the old telecom way of thinking. Regardless of this opposition, SBCs have become a central part of any SIP deployment.
In this paper we will first give a brief overview of how SIP works and continue with a description of what SBCs do and the different use cases for deploying SBCs.
SIP (Session Initiation Protocol) - Study Notes



SIP (Session Initiation Protocol) - Study NotesMarius FAILLOT DEVARRE This document provides an overview of Session Initiation Protocol (SIP) including its components and standards. SIP is an application-layer control protocol that establishes, modifies, and terminates multimedia sessions and communications. It can be used for voice and video calls over Internet Protocol (IP). The document defines SIP user agents, servers, and standards such as Session Description Protocol. It describes common SIP components like IP phones, gateways, proxy servers, redirect servers, and registrar servers.
SIP - The Basics



SIP - The BasicsJonas Borjesson SIP is a protocol for setting up and managing sessions over the internet, including voice and video calls. It allows users to locate each other and establish communication sessions between endpoints. SIP sets up sessions but does not handle the actual media, like audio, which is transported separately using protocols like RTP. SIP works by routing request and response messages between user agents through proxies and servers to initiate, negotiate, and terminate communication sessions.
Introduction to DIAMETER



Introduction to DIAMETERHossein Yavari Diameter is an authentication, authorization, and accounting (AAA) protocol that was developed as a successor to RADIUS. Some key points:
- Diameter was developed to address limitations in RADIUS such as reliability, security, failover support, and extensibility.
- It uses TCP or SCTP for reliable transport and supports features like transport layer security, failover mechanisms, and more flexible extensions compared to RADIUS.
- Diameter is composed of a base protocol and applications that allow it to be extended for different services. The base protocol specifies the message format, transport, and peer connections while applications define additional messages and service logic.
VOIP BASIC



VOIP BASICdhara patel This document provides an overview of Voice over IP (VoIP) technology. It discusses how VoIP works by digitizing and transmitting voice signals over the internet using IP packets. It describes common VoIP protocols like H.323 and SIP. The advantages of VoIP include lower costs, flexibility, and the ability to make calls from any internet connection. Disadvantages include reliance on internet access and potential quality issues during network congestion. The document provides details on how to implement VoIP securely and protect against risks.
Sip Detailed , Call flows , Architecture descriptions , SIP services , sip se...



Sip Detailed , Call flows , Architecture descriptions , SIP services , sip se...ALTANAI BISHT The presentation is a compiled assembly from the SIP RFC' s, and original works of Alan Johnston and Henry Sinnreich . It contains Sip Detailed , Call flows , Architecture descriptions , SIP services , sip security , sip programming.
Voice Over IP (VoIP)



Voice Over IP (VoIP)habib_786 VoIP allows users to make phone calls using an Internet connection instead of a traditional phone line. It works by converting voice signals to digital data that is transmitted in packets over the Internet. A VoIP network uses protocols like SIP and RTP to setup calls and transmit voice data. Components include VoIP protocols, gateways to interface with the PSTN, and codecs to compress voice signals. Businesses are attracted to VoIP as it can help reduce costs while improving utilization of bandwidth and network management. However, security risks like hacking and eavesdropping exist since VoIP uses the public Internet.
Voice Quality Metrics in VoIP



Voice Quality Metrics in VoIPFraj Alshahibi This document outlines a project proposal to compare VoIP systems through simulation. The objectives are to analyze VoIP voice quality using different codecs, equipment, phone frequencies, and bandwidth requirements. An overview of VoIP technology is provided along with descriptions of common VoIP protocols like SIP, H.323, and MGCP. Factors that impact VoIP quality like packet loss, delay, and jitter are explained. Popular codecs like G.711, G.729, and GSM are described along with their bandwidth requirements. A timeline is given for the project with submission deadlines throughout April to July.
Introduction to VoIP using SIP



Introduction to VoIP using SIPKundan Singh The document introduces VoIP (Voice over IP) concepts. It discusses digitization of audio, real-time compression/encoding, transport over UDP, and problems with UDP like packet loss and jitter. It also covers protocols like SIP for signaling, SDP for session description, and RTP for media transport. Key VoIP services that can be implemented with SIP are discussed, like call transfer and voicemail.
Ad
More Related Content
What's hot (20)
Introduction into SIP protocol



Introduction into SIP protocolMichal Hrncirik Brief introduction into SIP protocol, how it works, common problems to solve. Tech. details about handshake, SIP Trunks and SIP trunking. Market research.
Session initiation-protocol



Session initiation-protocolSanthosh Somu The document discusses the Session Initiation Protocol (SIP), which allows for multimedia communication sessions over IP networks. SIP establishes sessions for voice, video, messaging and other applications. It uses requests and responses to initiate sessions between users, locate users, invite them to sessions, and terminate sessions. SIP relies on user agents, proxy servers, redirect servers and registrar servers. It enables mobility and flexibility in setting up and modifying communication sessions across different devices.
Sip



SipAnirban Roy The Session Initiation Protocol (SIP) is the dominant signaling protocol used in VoIP today. It is
responsible for the establishment, control and termination of sessions by exchanging ASCII-text-based
messages between the endpoints. This post goes through the basic components of SIP: messages and
logical entities.
Calling VoWiFi... The Next Mobile Operator Service is here... 



Calling VoWiFi... The Next Mobile Operator Service is here... Cisco Canada The document provides housekeeping notes for a Cisco Connect Toronto 2015 session. It reminds attendees to silence phones and laptops, ask questions during the session, and complete a survey for a chance to win a headset. It also provides information on Cisco dCloud and accessing demos and labs, and discusses VoWiFi including benefits for mobile operators, architectures, and call flows.
Introduction to SIP(Session Initiation Protocol)



Introduction to SIP(Session Initiation Protocol)William Lee Session Initiation Protocol (SIP) is a signaling protocol for managing multimedia communication sessions over Internet Protocol (IP) networks. SIP can be used to establish two-party or multiparty sessions that include voice, video, chat, gaming, and other forms of media. The document introduces SIP architecture, message format, and common call flows including registration, basic call setup, call modification, call hold, and three-way conferencing.
Voip



VoipMuhammad Hamza This document discusses VoIP (Voice over Internet Protocol) technologies. It begins by defining VoIP and how it allows phone calls to be made over the internet instead of traditional telephone networks. It then explores enterprise VoIP systems, hosted VoIP, VoIP phones, and the differences between circuit switching used in PSTN networks and packet switching used in VoIP. Challenges of VoIP like latency, jitter and packet loss are outlined, as well as advantages such as lower costs, flexibility and portability. Popular VoIP service providers like Google Voice and Skype are compared.
session initiation protocol - SIP



session initiation protocol - SIPMahmoud Abudaqa SIP is an application-layer protocol for establishing multimedia sessions over IP networks. It can be used to initiate voice, video, and instant messaging communications. SIP works by having user agents (clients and servers) exchange SIP request and response messages. These messages contain information about session setup, modification, and termination. Some key SIP components include user agents, proxy servers, registrar servers, and redirect servers. SIP messages use a request-response transaction model and contain start lines, headers, and optional message bodies. Common request methods are INVITE, ACK, BYE, and REGISTER. Typical response codes include 100-199 (informational), 200-299 (success), 300-399 (redirection), 400-499
VoWifi 03 - vowifi epdg aaa and architecture (pdf ppt)



VoWifi 03 - vowifi epdg aaa and architecture (pdf ppt)Vikas Shokeen This document provides an overview of Voice over WiFi (VoWifi) including the key nodes involved and their roles. It discusses the user equipment (UE), evolved Packet Data Gateway (ePDG), AAA server, PGW, HSS, IMS, and PCRF nodes. The UE establishes an IPsec tunnel with the ePDG to access the EPC over an untrusted WiFi network. The ePDG and AAA server perform authentication. The existing PGW, HSS, IMS, and PCRF nodes are reused to support VoWifi calls and handovers between VoLTE and VoWifi. Key performance indicators for each node are also measured to ensure quality of VoWifi user experience
OSI Layers



OSI LayersKishore Kumar This study guide is intended to provide those pursuing the CCNA certification with a framework of what concepts need to be studied. This is not a comprehensive document containing all the secrets of the CCNA, nor is it a “braindump” of questions and answers.
I sincerely hope that this document provides some assistance and clarity in your studies.
SIP - Introduction to SIP Protocol



SIP - Introduction to SIP ProtocolLivePerson SIP - More than meets the eye
Speakers:
Ofer Cohen - VOIP Group Leader, LivePerson
Yossi Maimon - VOIP Technical Leader, LivePerson
An Introduction to the SIP protocol.
SIP Position in telecommunication networks and the content services.
What is SIP:
The Session Initiation Protocol (SIP) is a signaling communications protocol, widely used for controlling multimedia communication sessions such as voice and video calls over Internet Protocol (IP) networks.
The protocol defines the messages that are sent between peers which govern establishment, termination and other essential elements of a call. SIP can be used for creating, modifying and terminating sessions consisting of one or several media streams. SIP can be used for two-party (unicast) or multiparty (multicast) sessions. Other SIP applications include video conferencing, streaming multimedia distribution, instant messaging, presence information, file transfer, fax over IP and online games.
(Source: Wikipedia)
Voip



VoipRajan Kumar VoIP is a technology that allows phone calls to be made over the internet. It works by converting analog voice signals to digital data that is sent in packets over IP networks. Common VoIP technologies include H.323, SIP, and RTP. VoIP can be implemented through analog telephone adapters, IP phones, or computer-to-computer calls. While VoIP provides benefits like low costs and integration with other applications, it also faces challenges related to quality of service, emergency calls, and lack of redundancy in case of power failures.
SIP Trunking



SIP Trunkingorionnow SIP (Session Initiation Protocol) trunking connects a company's PBX to the existing telephone network infrastructure via the internet using VoIP. It was originally designed in 1996 and standardized in 2000. SIP trunking provides benefits like virtual phone numbers, reduced equipment needs, business continuity, and flexible trunk quantities. However, considerations must include system compatibility, additional bandwidth requirements, and challenges like supporting fax/modem traffic and 911 calls. The document discusses ideal environments for SIP trunking like companies with multiple locations, seasonal needs, or those seeking increased functionality. It also reviews cost components and provides an overview of SIP trunking.
SOMEIP-protocol.pptx



SOMEIP-protocol.pptxPushkarBaheti1 SOME/IP is a protocol specification that defines formats and communication patterns for sharing services over IP networks in vehicles. It includes an on-wire format that defines fields like service ID, method ID, and message type. The protocol uses UDP and TCP transports and defines request/response and publish/subscribe communication patterns. Events are always grouped in event groups and can be subscribed to, while fields use request/response calls.
Understanding Session Border Controllers



Understanding Session Border Controllersstefansayer Over the past 10 years the Session Initiation Protocol (SIP) has moved from the toy of researchers and academics to the de-facto standard for telephony and multimedia services in mobile and fixed networks.
Probably one of the most emotionally fraught discussions in the context of SIP was whether Session Border Controllers (SBC) are good or evil.
SIP was designed with the vision of revolutionizing the way communication services are developed, deployed and operated. Following the end-to-end spirit of the Internet SIP was supposed to turn down the walled gardens of PSTN networks and free communication services from the grip of large telecom operators. By moving the intelligence to the end systems, developers were supposed to be able to develop new communication services that will innovate the way we communicate with each other.
This was to be achieved without having to wait for the approval of the various telecommunication standardization groups such as ETSI or the support of incumbent telecoms.
Session border controllers are usually implemented as SIP Back-to-Back User Agents (B2BUA) that are placed between a SIP user agent and a SIP proxy. The SBC then acts as the contact point for both the user agents and the proxy. Thereby the SBC actually breaks the end-to-end behavior of SIP, which has led various people to deem the SBC as an evil incarnation of the old telecom way of thinking. Regardless of this opposition, SBCs have become a central part of any SIP deployment.
In this paper we will first give a brief overview of how SIP works and continue with a description of what SBCs do and the different use cases for deploying SBCs.
SIP (Session Initiation Protocol) - Study Notes



SIP (Session Initiation Protocol) - Study NotesMarius FAILLOT DEVARRE This document provides an overview of Session Initiation Protocol (SIP) including its components and standards. SIP is an application-layer control protocol that establishes, modifies, and terminates multimedia sessions and communications. It can be used for voice and video calls over Internet Protocol (IP). The document defines SIP user agents, servers, and standards such as Session Description Protocol. It describes common SIP components like IP phones, gateways, proxy servers, redirect servers, and registrar servers.
SIP - The Basics



SIP - The BasicsJonas Borjesson SIP is a protocol for setting up and managing sessions over the internet, including voice and video calls. It allows users to locate each other and establish communication sessions between endpoints. SIP sets up sessions but does not handle the actual media, like audio, which is transported separately using protocols like RTP. SIP works by routing request and response messages between user agents through proxies and servers to initiate, negotiate, and terminate communication sessions.
Introduction to DIAMETER



Introduction to DIAMETERHossein Yavari Diameter is an authentication, authorization, and accounting (AAA) protocol that was developed as a successor to RADIUS. Some key points:
- Diameter was developed to address limitations in RADIUS such as reliability, security, failover support, and extensibility.
- It uses TCP or SCTP for reliable transport and supports features like transport layer security, failover mechanisms, and more flexible extensions compared to RADIUS.
- Diameter is composed of a base protocol and applications that allow it to be extended for different services. The base protocol specifies the message format, transport, and peer connections while applications define additional messages and service logic.
VOIP BASIC



VOIP BASICdhara patel This document provides an overview of Voice over IP (VoIP) technology. It discusses how VoIP works by digitizing and transmitting voice signals over the internet using IP packets. It describes common VoIP protocols like H.323 and SIP. The advantages of VoIP include lower costs, flexibility, and the ability to make calls from any internet connection. Disadvantages include reliance on internet access and potential quality issues during network congestion. The document provides details on how to implement VoIP securely and protect against risks.
Sip Detailed , Call flows , Architecture descriptions , SIP services , sip se...



Sip Detailed , Call flows , Architecture descriptions , SIP services , sip se...ALTANAI BISHT The presentation is a compiled assembly from the SIP RFC' s, and original works of Alan Johnston and Henry Sinnreich . It contains Sip Detailed , Call flows , Architecture descriptions , SIP services , sip security , sip programming.
Voice Over IP (VoIP)



Voice Over IP (VoIP)habib_786 VoIP allows users to make phone calls using an Internet connection instead of a traditional phone line. It works by converting voice signals to digital data that is transmitted in packets over the Internet. A VoIP network uses protocols like SIP and RTP to setup calls and transmit voice data. Components include VoIP protocols, gateways to interface with the PSTN, and codecs to compress voice signals. Businesses are attracted to VoIP as it can help reduce costs while improving utilization of bandwidth and network management. However, security risks like hacking and eavesdropping exist since VoIP uses the public Internet.
Viewers also liked (20)
Voice Quality Metrics in VoIP



Voice Quality Metrics in VoIPFraj Alshahibi This document outlines a project proposal to compare VoIP systems through simulation. The objectives are to analyze VoIP voice quality using different codecs, equipment, phone frequencies, and bandwidth requirements. An overview of VoIP technology is provided along with descriptions of common VoIP protocols like SIP, H.323, and MGCP. Factors that impact VoIP quality like packet loss, delay, and jitter are explained. Popular codecs like G.711, G.729, and GSM are described along with their bandwidth requirements. A timeline is given for the project with submission deadlines throughout April to July.
Introduction to VoIP using SIP



Introduction to VoIP using SIPKundan Singh The document introduces VoIP (Voice over IP) concepts. It discusses digitization of audio, real-time compression/encoding, transport over UDP, and problems with UDP like packet loss and jitter. It also covers protocols like SIP for signaling, SDP for session description, and RTP for media transport. Key VoIP services that can be implemented with SIP are discussed, like call transfer and voicemail.
ThousandEyes VoIP Performance Management 



ThousandEyes VoIP Performance Management ThousandEyes Modern enterprises are adopting VoIP throughout branch offices, but don’t have great tools for pre-deployment testing, capacity planning and troubleshooting when voice performance issues arise. Software Engineer Joao Antunes demos the ThousandEyes VoIP network test.
VoIP Techniques and Challenges PRESENTATION



VoIP Techniques and Challenges PRESENTATIONKarama Said(BEng,MSc) This document provides an overview of VoIP techniques and challenges. It begins with an introduction to VoIP and what it is. It then discusses quality of service (QoS) and the importance of providing prioritized delivery services for applications like VoIP. The main challenges for VoIP are then outlined as system capacity/available bandwidth, packet loss, delay/network latency, jitter, echo, and security. Specific causes and issues are described for each challenge. The conclusion is that while VoIP provides a cheaper alternative to PSTN, it has lower quality of service due to these challenges, and the internet is not perfectly designed to carry voice.
VoIP Monitoring and Troubleshooting



VoIP Monitoring and TroubleshootingThousandEyes Planning and Troubleshooting VoIP Performance shares insights on ThousandEyes helps visualize VoIP routing between branch offices and across the internet, optimize and plan new VoIP deployments and expansions, and troubleshoot VoIP performance to specific problem nodes, links and networks.
ServicePilot VoIP and UC monitoring for Shoretel



ServicePilot VoIP and UC monitoring for ShoretelServicePilot This document describes the capabilities of ServicePilot's monitoring and analysis solution for ShoreTel VoIP environments. The solution monitors infrastructure components, end user experience, security and events. It provides visibility into availability, performance, call quality, unauthorized activities and more. The all-in-one solution monitors ShoreTel servers, databases, virtual environments and networks without hidden costs.
SIP dilivery methods and ROI



SIP dilivery methods and ROImarkbiltonsmith This document discusses SIP trunking, which uses the Session Initiation Protocol (SIP) to connect an IP PBX or hybrid phone system to the existing telephone network infrastructure (PSTN) via a managed data service or internet connection. It outlines various VoIP protocols, bandwidth requirements, delivery methods (managed vs unmanaged internet), considerations around quality of service, and examples of pricing models and ROI comparisons between SIP trunking and traditional phone lines.
Bright talk voip vofi webinar jan2015-v2



Bright talk voip vofi webinar jan2015-v2Savvius, Inc With over 10 years of deployment history, VoIP is the primary voice solution for just about every company in existence - large, medium, or small. But even with all that history, recent research from TRAC shows that VoIP is still the number one IT initiative impacting network performance. And with the growth of 802.11 and Wi-Fi enabled smart phones, the use of voice over Wi-Fi (VoFi) promises to increase the volume of VoIP traffic even more.
Analyzing VoIP traffic alone is not enough. VoIP analysis must be part of your overall network performance analysis. After all, VoIP is just another data type on your network, and according to TRAC, it is impacting your network performance, so you must monitor and analyze the network as a whole, including voice and video over IP. Watch to see how easy it is to capture and analyze voice, video, and data traffic simultaneously, allowing you to pinpoint the impact of each data type on your overall network performance.
Take a sip of sip



Take a sip of sipLuxoftTraining SIP (Session Initiation Protocol) is a signaling protocol used to create, manage and terminate sessions in an IP based network. This course is for beginners and aims to give a brief introduction to SIP before one ventures into the long RFC documents.
Voxeo Summit Day 2 -What's new in CXP 14



Voxeo Summit Day 2 -What's new in CXP 14Voxeo Corp The document summarizes new features and enhancements planned for Voxeo CXP 14. Key points include:
1) Improved scalability and security to support thousands of services deployed in parallel on one server cluster with faster startup times and capacity limited only by memory.
2) Enhanced SOAP support by replacing the SOAP library to remove limitations and allow out-of-the-box integration in customer projects.
3) Business User Interface 2.0 integrated into CXP Developer to enable business users to access configuration without developers/admins and offer more fine-grained access management and built-in file uploads.
4) Deeper mobile web integration and support for jQuery Mobile themes and
SIP in Service Quality Monitoring



SIP in Service Quality MonitoringTTI Telecom The document discusses service quality monitoring in SIP-based networks. It describes monitoring the performance of SIP sessions through metrics that measure registration request delay, session request delay, session disconnect delay, and more. It outlines a holistic approach to SIP monitoring involving four phases: session processing, metric dimensioning and creation, service degradation rules, and root-cause isolation. The goal is to understand customer experience, proactively identify quality issues, and ensure service level agreements are met.
SIP for geeks



SIP for geeksKundan Singh Kundan Singh provides an overview of Session Initiation Protocol (SIP) for networking experts. He has a PhD in Internet telephony from Columbia University and has worked on SIP implementations and open source projects since 1999. The document summarizes what attendees will learn about SIP including its history, standards, architecture, protocols, call flows, challenges, and hands-on exercises. It also provides background on Kundan's expertise in areas like VoIP, audio coding, and real-time protocols.
VOIP QOS



VOIP QOSThomas Mangin This document discusses quality of service (QoS) requirements for voice over IP (VoIP) and how QoS can be implemented in packet switched networks to address issues like jitter, latency, bandwidth congestion, and packet loss that can negatively impact call quality. It explains that QoS aims to guarantee a certain level of performance for applications like VoIP through techniques like traffic classification, marking, and queuing. The document also provides recommendations for applying QoS on the network edge, core, and internet exchange points to help improve end-to-end call quality.
Introduction to TTI Telecom



Introduction to TTI TelecomTTI Telecom TTI Telecom is an Israeli company founded in 1987 that provides service assurance products and services for telecommunications networks. It has over 70 customers in more than 25 countries. In 2009 it had revenues of $43 million and employed 345 people. Its vision is to be the leading provider of innovative service assurance solutions for converged networks.
Internet Telephony by Aria technologies



Internet Telephony by Aria technologiesDavid Meadow Internet Telephony uses the Internet Protocol to send audio, video an data between two or more users in the real time.
Internet telephony by abhishek mahajan



Internet telephony by abhishek mahajanAbhishek Mahajan Internet telephony allows users to make voice calls over the Internet. It works by digitizing voice data and transmitting it as packets over the Internet using IP protocols. As technology has advanced, internet telephony has improved in voice quality and compression techniques. It provides a low-cost alternative to traditional telephone networks and enables communication between computer users in real-time.
Introducing Savvius Vigil



Introducing Savvius VigilSavvius, Inc Savvius Vigil is the first network appliance able to intelligently store months of packet-level information to enhance security investigations. Savvius Vigil integrates with your existing SIEM platform to examine packets related to a breach weeks or months after the incident occurred. This information is often vital to a full understanding of the threat.
Infomation System Security



Infomation System SecurityKiran Munir Information system security deals with securing systems, information in transit, and establishing security services, mechanisms, and policies. It aims to provide confidentiality, integrity, authentication, and controlled access. Cryptography is the study of mathematical techniques used for these security objectives and includes symmetric and asymmetric encryption methods. Cryptanalysis involves attempting to defeat cryptographic techniques.
Voice over internet protocol



Voice over internet protocolVarinder Singh Walia This tutorial gives very good understanding on CCNA (VOIP). After completing this tutorial.You will find yourself at a moderate level of expertise in knowing Advance Networking(CCNA)
Voice Over IP (VoIP) and STREAMING



Voice Over IP (VoIP) and STREAMINGRagheb Gmira Voice over Internet Protocol (VoIP), is a technology that allows to make voice calls using a broadband Internet connection instead of a regular (or analog) phone line (PSTN).
Ad
Similar to Introduction to VoIP, RTP and SIP (20)
VOIP services



VOIP servicesPankaj Saharan This document provides an overview of VoIP services through a seminar presentation. It discusses how VoIP came about as an alternative to traditional circuit-switched telephony using the PSTN. VoIP allows carrying voice calls over an IP network by digitizing and packetizing voice streams using protocols like SIP and H.323. Some key benefits of VoIP include reduced costs, increased flexibility, and mobility. Popular VoIP service providers include Skype, while security poses ongoing challenges to VoIP adoption.
VOIP



VOIPguest43d211 the ppt describes about voip,its advantages and disadvantages.it also describes the protocols and the packet formats involved in a voip session .
cs522_presentation.ppt



cs522_presentation.ppthajAli4 VoIP uses SIP and RTP protocols to transmit voice data over IP networks. SIP establishes and terminates voice calls by sending INVITE, ACK, BYE messages between user agents like phones and softphones. RTP carries the encoded voice data with timestamps and sequence numbers to ensure quality of service. Common issues with VoIP include delay, jitter, packet loss and speech coding that impact voice quality.
VoIP and multimedia networking



VoIP and multimedia networkingsangusajjan VoIP uses packet networks to carry voice calls in addition to data. It works by converting analog voice signals to digital data packets which are transmitted over IP networks and reconverted to analog at the receiving end. Key components include IP phones, signaling servers, and protocols like SIP and H.323 which handle call setup and signaling. Quality of service for VoIP depends on factors like packet loss, delay, and jitter which can be managed through queuing and reserving bandwidth for voice traffic.
Voip



VoipSumit Joshi This document discusses Voice over Internet Protocol (VoIP). It begins by introducing VoIP and how it allows phone calls and faxes to be sent over IP-based data networks. It then discusses how VoIP works by digitizing voice, compressing it into packets, transmitting the packets over the internet, and reconstructing the voice signal at the receiving end. The document also covers some key components of a VoIP system such as encoders, decoders, and quality of service mechanisms. Finally, it briefly mentions that most VoIP implementations follow the ITU H.323 standard.
A glance-at-voip



A glance-at-voipNicola Marinelli VoIP allows voice calls over the internet using IP packets. It has advantages over traditional telephone networks like lower costs and ability to make calls anywhere internet can reach. Quality of service for VoIP calls can be impacted by packet loss, delay, and jitter. Standards like H.323 and SIP define protocols for call signaling, while RTP and SRTP are used for media transport and security. H.323 specifies components like terminals, gateways, MCUs and gatekeepers that work together to enable VoIP calls.
Voice Over IP Overview w/Secuirty



Voice Over IP Overview w/SecuirtyChristopher Duffy VoIP security involves threats like denial of service attacks, eavesdropping, and quality of service issues. Best practices include using firewalls with application layer gateways or session border controllers, encrypting media and signaling, prioritizing bandwidth for VoIP, and restricting access to call managers through physical and logical security measures. NIST recommends logically separate networks, endpoint encryption, and avoiding vulnerabilities in softphones and wireless networks without encryption.
VOIP security



VOIP securityRohit Gurjar This document provides an overview of VoIP security. It discusses the basics of VoIP security including authentication, authorization, availability, and encryption. It outlines some common attack vectors such as accessing an unsecured local network connection, wireless network, or public network. It also mentions threats from compromising a phone's configuration file or uploading a malicious file. The document summarizes some unconventional VoIP security threats like phishing, caller ID spoofing, eavesdropping, call redirection, and spam over internet telephony.
Voice over IP: Issues and Protocols



Voice over IP: Issues and ProtocolsVideoguy Voice over IP (VoIP) allows voice traffic to be carried over an IP data network at lower bandwidth than traditional telephone networks. It provides benefits such as lower communication costs, convergence of voice and data infrastructure, and new multimedia applications. However, VoIP also faces issues including delay, congestion, jitter, packet loss, bandwidth limitations, echo, interoperability between different systems, and ensuring scalability. The two main VoIP protocols are the Session Initiation Protocol (SIP) and H.323. VoIP adoption is growing due to the increasing use of IP networks, and it provides opportunities for lower telephone costs and innovative services. However, challenges remain regarding quality of service, interoperability, and developing carrier-grade
2.Intro-to-VoIP.ppt



2.Intro-to-VoIP.pptssuser05aebc1 This document discusses the requirements and considerations for implementing voice over IP (VoIP) networks. It covers topics like the impact of packet loss, delay and jitter on voice quality in an IP network. It also addresses the need for consistent throughput, reliability, and different types of gateways. Additional sections provide details on encapsulating voice in IP packets, major VoIP protocols like RTP and RTCP, and calculating bandwidth requirements.
2.Intro-to-VoIP.ppt



2.Intro-to-VoIP.pptnebepa7907 This document discusses the requirements and considerations for implementing voice over IP (VoIP) networks. It covers topics like the effects of packet loss, delay and jitter on voice quality in an IP network. It also addresses the need for consistent throughput, reliability, and different types of gateways. Additional sections provide details on encapsulating voice in IP packets, major VoIP protocols like RTP and RTCP, and calculating bandwidth requirements.
1. VoIP.ppt



1. VoIP.pptshabdrang This document discusses the requirements and considerations for implementing voice over IP (VoIP) networks. It covers topics like the impact of packet loss, delay and jitter on voice quality in an IP network. It also addresses the need for consistent throughput, reliability, and different types of gateways. Additional sections provide details on encapsulating voice in IP packets, major VoIP protocols like RTP and RTCP, and calculating bandwidth requirements.
tftyfty.ppt



tftyfty.pptAlKir1 This document discusses the requirements and considerations for implementing voice over IP (VoIP) networks. It covers topics like the impact of packet loss, delay and jitter on voice quality in an IP network. It also addresses the need for consistent throughput, reliability, and different types of gateways. Additional sections provide details on encapsulating voice in IP packets, major VoIP protocols like RTP and RTCP, and calculating bandwidth requirements.
Vo ip sip



Vo ip sipIazon Danelia This document provides an overview and introduction to VoIP and SIP signaling. It discusses key topics such as VoIP architecture and components, the process of a VoIP telephone call including conversion between analog and digital signals and quality of service, SIP architecture including what SIP is, its capabilities and message format, and SIP call flow. The document is intended as a training presentation that includes definitions of terms, descriptions of concepts, diagrams, and quizzes related to VoIP and SIP.
Positive Hack Days. Gritsai. VOIP insecurities workshop



Positive Hack Days. Gritsai. VOIP insecurities workshopPositive Hack Days Участник получит представление об основе IP-телефонии, а также базовые навыки поиска уязвимостей на примере распространенных IP-PBX и абонентских устройств. Рассматриваются как типовые сетевые уязвимости, так и сложные случаи, обнаруживаемые в ходе анализа защищенности реальных сетей.
Telefonia_IP (1).ppt



Telefonia_IP (1).pptacaldere Voice over Internet Protocol (VoIP) uses digital compression techniques and packet switching to transmit voice conversations over the Internet or other IP-based networks. There are two main types of call setup in telephony networks - centralized call control where one device controls the call, and distributed call control where devices collaborate to control the call. For VoIP to work effectively, quality of service measures must be implemented to guarantee delivery, minimize packet loss and jitter, and ensure calls can tolerate delays of up to 150ms.
Understanding VoIP - 1



Understanding VoIP - 1Adebayo Ojo The document provides an overview of VoIP components, standards, architectures and implementation choices. It discusses key VoIP elements like terminals, packetized voice, soft switches, media servers, gateways, LANs/WANs and standards. It also describes common VoIP architectures for computer-computer, computer-phone, phone-phone communication over the internet. Finally, it outlines VoIP solutions for businesses using VoIP-enabled PBXs, replacing PBXs with softswitches, and hosted PBX solutions.
VoIP (Voice over Internet Protocol)



VoIP (Voice over Internet Protocol)Abdullah Shah VoIP allows users to make voice calls over the internet instead of traditional phone lines. It works by converting voice signals to digital data packets that are transmitted over the internet and then reconverted at their destination. Key components include gateways, codecs, servers, and protocols like SIP and H.323. VoIP offers advantages like lower costs and integration with other systems but relies on internet connectivity and faces some security risks.
Ad
More from ThousandEyes (20)
How to Optimize Your AWS Environment for Improved Cloud Performance



How to Optimize Your AWS Environment for Improved Cloud PerformanceThousandEyes How to Optimize Your AWS Environment for Improved Cloud Performance
Assuring Your SD-WAN to Deliver Unparalleled Digital Experiences



Assuring Your SD-WAN to Deliver Unparalleled Digital ExperiencesThousandEyes Presented by Jonathan Zarkower
Assuring Your SD-WAN to Deliver Unparalleled Digital Experiences



Assuring Your SD-WAN to Deliver Unparalleled Digital ExperiencesThousandEyes Presented by Jonathan Zarkower
How to Optimize Your AWS Environment for Improved Cloud Performance



How to Optimize Your AWS Environment for Improved Cloud PerformanceThousandEyes Presented by Ranjit Kalidasan, Chitra Shastri, and Martin Kowalewski
How to Optimize Your AWS Environment for Improved Cloud Performance



How to Optimize Your AWS Environment for Improved Cloud PerformanceThousandEyes Presented by Ranjit Kalidasan, Chitra Shastri, and Martin Kowalewski
What's New? ThousandEyes Product Features and Highlights for February 2025



What's New? ThousandEyes Product Features and Highlights for February 2025ThousandEyes What's New? ThousandEyes Product Features and Highlights for February 2025
Top Outages of 2024, Explained: Lessons in Digital Resilience



Top Outages of 2024, Explained: Lessons in Digital ResilienceThousandEyes Top Outages of 2024, Explained: Lessons in Digital Resilience
Top Outages of 2024, Explained: Lessons in Digital Resilience



Top Outages of 2024, Explained: Lessons in Digital ResilienceThousandEyes Presented by Kemal Sanjta and David Puzas
New ThousandEyes Product Features and Release Highlights: December 2024



New ThousandEyes Product Features and Release Highlights: December 2024ThousandEyes New ThousandEyes Product Features and Release Highlights: December 2024
ThousandEyes and Webex Assure Seamless Collaboration for Insight Global



ThousandEyes and Webex Assure Seamless Collaboration for Insight GlobalThousandEyes Presented by Brian Tobia, Chris Cavendish, and Suzanne Phillips
New ThousandEyes Product Features and Release Highlights: October 2024



New ThousandEyes Product Features and Release Highlights: October 2024ThousandEyes Presented by Brian Tobia
Troubleshooting Digital Experiences Across Owned and Unowned Networks



Troubleshooting Digital Experiences Across Owned and Unowned NetworksThousandEyes Presented by Mike Hicks
Troubleshooting Digital Experiences Across Owned and Unowned Networks



Troubleshooting Digital Experiences Across Owned and Unowned NetworksThousandEyes Presented by Suzanne Phillips and Brian Tobia
Recently uploaded (20)
Heap, Types of Heap, Insertion and Deletion



Heap, Types of Heap, Insertion and DeletionJaydeep Kale This pdf will explain what is heap, its type, insertion and deletion in heap and Heap sort
Splunk Security Update | Public Sector Summit Germany 2025



Splunk Security Update | Public Sector Summit Germany 2025Splunk Splunk Security Update
Sprecher: Marcel Tanuatmadja
HCL Nomad Web – Best Practices and Managing Multiuser Environments



HCL Nomad Web – Best Practices and Managing Multiuser Environmentspanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-and-managing-multiuser-environments/
HCL Nomad Web is heralded as the next generation of the HCL Notes client, offering numerous advantages such as eliminating the need for packaging, distribution, and installation. Nomad Web client upgrades will be installed “automatically” in the background. This significantly reduces the administrative footprint compared to traditional HCL Notes clients. However, troubleshooting issues in Nomad Web present unique challenges compared to the Notes client.
Join Christoph and Marc as they demonstrate how to simplify the troubleshooting process in HCL Nomad Web, ensuring a smoother and more efficient user experience.
In this webinar, we will explore effective strategies for diagnosing and resolving common problems in HCL Nomad Web, including
- Accessing the console
- Locating and interpreting log files
- Accessing the data folder within the browser’s cache (using OPFS)
- Understand the difference between single- and multi-user scenarios
- Utilizing Client Clocking
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
Build Your Own Copilot & Agents For Devs



Build Your Own Copilot & Agents For DevsBrian McKeiver May 2nd, 2025 talk at StirTrek 2025 Conference.
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
How Can I use the AI Hype in my Business Context?



How Can I use the AI Hype in my Business Context?Daniel Lehner 𝙄𝙨 𝘼𝙄 𝙟𝙪𝙨𝙩 𝙝𝙮𝙥𝙚? 𝙊𝙧 𝙞𝙨 𝙞𝙩 𝙩𝙝𝙚 𝙜𝙖𝙢𝙚 𝙘𝙝𝙖𝙣𝙜𝙚𝙧 𝙮𝙤𝙪𝙧 𝙗𝙪𝙨𝙞𝙣𝙚𝙨𝙨 𝙣𝙚𝙚𝙙𝙨?
Everyone’s talking about AI but is anyone really using it to create real value?
Most companies want to leverage AI. Few know 𝗵𝗼𝘄.
✅ What exactly should you ask to find real AI opportunities?
✅ Which AI techniques actually fit your business?
✅ Is your data even ready for AI?
If you’re not sure, you’re not alone. This is a condensed version of the slides I presented at a Linkedin webinar for Tecnovy on 28.04.2025.
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
Linux Support for SMARC: How Toradex Empowers Embedded Developers



Linux Support for SMARC: How Toradex Empowers Embedded DevelopersToradex Toradex brings robust Linux support to SMARC (Smart Mobility Architecture), ensuring high performance and long-term reliability for embedded applications. Here’s how:
• Optimized Torizon OS & Yocto Support – Toradex provides Torizon OS, a Debian-based easy-to-use platform, and Yocto BSPs for customized Linux images on SMARC modules.
• Seamless Integration with i.MX 8M Plus and i.MX 95 – Toradex SMARC solutions leverage NXP’s i.MX 8 M Plus and i.MX 95 SoCs, delivering power efficiency and AI-ready performance.
• Secure and Reliable – With Secure Boot, over-the-air (OTA) updates, and LTS kernel support, Toradex ensures industrial-grade security and longevity.
• Containerized Workflows for AI & IoT – Support for Docker, ROS, and real-time Linux enables scalable AI, ML, and IoT applications.
• Strong Ecosystem & Developer Support – Toradex offers comprehensive documentation, developer tools, and dedicated support, accelerating time-to-market.
With Toradex’s Linux support for SMARC, developers get a scalable, secure, and high-performance solution for industrial, medical, and AI-driven applications.
Do you have a specific project or application in mind where you're considering SMARC? We can help with Free Compatibility Check and help you with quick time-to-market
For more information: https://www.toradex.com/computer-on-modules/smarc-arm-family
HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungen



HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungenpanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-und-verwaltung-von-multiuser-umgebungen/
HCL Nomad Web wird als die nächste Generation des HCL Notes-Clients gefeiert und bietet zahlreiche Vorteile, wie die Beseitigung des Bedarfs an Paketierung, Verteilung und Installation. Nomad Web-Client-Updates werden “automatisch” im Hintergrund installiert, was den administrativen Aufwand im Vergleich zu traditionellen HCL Notes-Clients erheblich reduziert. Allerdings stellt die Fehlerbehebung in Nomad Web im Vergleich zum Notes-Client einzigartige Herausforderungen dar.
Begleiten Sie Christoph und Marc, während sie demonstrieren, wie der Fehlerbehebungsprozess in HCL Nomad Web vereinfacht werden kann, um eine reibungslose und effiziente Benutzererfahrung zu gewährleisten.
In diesem Webinar werden wir effektive Strategien zur Diagnose und Lösung häufiger Probleme in HCL Nomad Web untersuchen, einschließlich
- Zugriff auf die Konsole
- Auffinden und Interpretieren von Protokolldateien
- Zugriff auf den Datenordner im Cache des Browsers (unter Verwendung von OPFS)
- Verständnis der Unterschiede zwischen Einzel- und Mehrbenutzerszenarien
- Nutzung der Client Clocking-Funktion
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
Introduction to VoIP, RTP and SIP
- 1. 0 Introduction to VoIP, RTP and SIP Archana Kesavan Product Marketing Manager
- 2. 1 About ThousandEyes ThousandEyes delivers visibility into every network your organization relies on. Founded by network experts; strong investor backing Relied on for critical operations by leading enterprises Recognized as an innovative new approach 27 Fortune 500 5 top 5 SaaS Companies 4 top 6 US Banks
- 3. 2 Telephony – A Brief History Mr. Watson – Come here – I want to see you Manual Switchboard
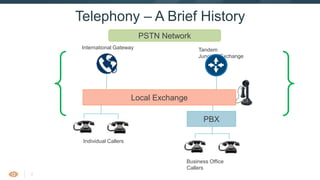
- 4. 3 Telephony – A Brief History Business Office Callers Local Exchange PBX Individual Callers International Gateway Tandem Junction/Exchange PSTN Network
- 5. 4 Voice-Over-IP • Set of protocols designed to deliver communication services over the IP network • Analog voice converted into data packets to be sent over the Internet. • Two phases • Phase 1: Signaling (SIP) • Phase 2: Audio transport (RTP)
- 6. 5 IP Telephony or Voice-Over-IP Local Exchange PBX Individual Callers International Gateway Tandem Junction PSTNNetwork IP- PBX VoIP Servers Ethernet (IP Network) Internet SIP Trunk Mobile Voice Mobile Data
- 7. 6 Type of VoIP Services On-Prem Branch Office Branch Office DMZ CRM Web Data Center IP-PBX VoIP server • All hardware and software owned and managed by the enterprise. • IP-PBX and adjoining systems reside in the datacenter or on premise. • Voice packets go through the LAN and WAN
- 8. 7 Type of VoIP Services Hosted • IP-phones are owned by the enterprise • All other equipment and software located in the service provider data center and provided as a service • VoIP packets travel over the Internet or dedicated WAN connectivity to the hosted site Data Center Branch Office Branch Office DMZ CRMWeb IP-PBX VoIP Provider Data Center Branch Office Branch Office DMZ CRMWeb IP-PBX VoIP Provider Data Center Data Center Enterprise A Enterprise B
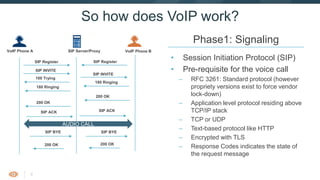
- 9. 8 So how does VoIP work? • Session Initiation Protocol (SIP) • Pre-requisite for the voice call – RFC 3261: Standard protocol (however propriety versions exist to force vendor lock-down) – Application level protocol residing above TCP/IP stack – TCP or UDP – Text-based protocol like HTTP – Encrypted with TLS – Response Codes indicates the state of the request message Phase1: Signaling VoIP Phone A SIP Server/Proxy VoIP Phone B SIP RegisterSIP Register SIP INVITE 100 Trying SIP INVITE 180 Ringing 180 Ringing 200 OK 200 OK AUDIO CALL SIP BYE 200 OK SIP ACK SIP ACK SIP BYE 200 OK
- 10. 9 So how does VoIP work? Phase1: Signaling VoIP Phone A SIP Server/Proxy VoIP Phone B SIP RegisterSIP Register SIP INVITE 100 Trying SIP INVITE 180 Ringing 180 Ringing 200 OK 200 OK AUDIO CALL SIP BYE 200 OK SIP ACK SIP ACK SIP BYE 200 OK REGISTER INVITE CONNECT DISCONNECT
- 11. 10 • Real Transport Protocol (RTP) – Analog voice signals converted into data packets and sent over UDP – Audio frames are encapsulated in RTP packets – RTP packets are encapsulated in UDP packets – UDP packets are encapsulated in IP packets So how does VoIP work? Phase 2: Audio Data IP header UDP header Frame 1 RTP header Frame 2 RTP Audio Stream SIP Network
- 12. 11 • How voice traffic is encoded and decoded • Determines the quality of the VoIP conversation • G.711, G.722, SILK Key VoIP Concepts • MoS • Latency • Jitter (De-Jitter buffer) • PDV Codecs VoIP Metrics • Prioritization of VoIP Traffic • DSCP codes – Traffic shaping, firewall and LB configuration – 3 bits for class: Best effort, Assured Forwarding, Expedited Forwarding, Voice Admit QoS
- 13. 12 Time Packet delay (from sender to receiver) Latency Packet 1 Packet 2 Packet 4Sent at Packet 1 Packet 2 Packet 4Received at Packet 3 Packet 3 Latency LatencyLatency Latency
- 14. 13 Time Variation of the latency Jitter Packet 1 Packet 2 Packet 4Sent at Packet 1 Packet 2 Packet 4Received at Packet 3 Packet 3 Min Latency Max Latency
- 15. 14 Time 99.9th percentile of the packet delay variation Packet Delay Variation Packet 1 Packet 2 Packet 4Sent at Packet 1 Packet 2 Packet 4Received at Packet 3 Packet 3 Played at Delayed playback Min Latency Max Latency PDV = max latency – min latency De-jitter buffer should be able to accommodate PDV.
- 16. 15 E-Model (ITU-T Recommendation G.107, 1998-2014) Based on a mathematical model in which the individual transmission parameters are transformed into different individual "impairment factors” such as codec characteristics, delay, loss ratio, discard ratio, etc., to obtain a quality metric called R factor: Mean Opinion Score (MOS) Basic signal- to-noise ratio Delay impairment Equipment impairment Advantage factor (expectation) • Network latency • De-jitter buffer size • Ie (codec) • Packet loss robustness (codec) • Packet loss probability • Network latency Simultaneous impairment 1 Calculation of the transmission rating factor, R ccording to the equipment impairment factor method, the fundamental principle of the E-model ased on a concept given in the description of the OPINE model (see [b-ITU-T P-Sup.3]). sychological factors on the psychological scale are additive. he result of any calculation with the E-model in a first step is a transmission rating factor R, whic ombines all transmission parameters relevant for the considered connection. This rating factor R omposed of: AIe-effIdIsRoR +−−−= (7-1 o represents in principle the basic signal-to-noise ratio, including noise sources such as circu oise and room noise. Factor Is is a combination of all impairments which occur more or le multaneously with the voice signal. Factor Id represents the impairments caused by delay and th fective equipment impairment factor Ie-eff represents impairments caused by low bit-rate codec also includes impairment due to randomly distributed pack losses. The advantage factor A allow r compensation of impairment factors when the user benefits from other types of access to th ser. The term Ro and the Is and Id values are subdivided into further specific impairment value he following clauses give the equations used in the E-model.
- 17. 16 • Data records that contain specific information about a call. For eg, timestamp, call duration etc • CDRs are generated at specified triggers • Record call quality, loss, latency experienced • Billing, Law Enforcement Monitoring Techniques for VoIP • Packet sniffer that can record every SIP and RTP transaction • Can typically decode speech and replay for call quality analysis • Detect MOS score and other voice metrics • Maximum overhead Call Detail Records Packet Capture • Simulate VoIP traffic from strategic vantage points in periodic intervals • Quickly pinpoint when and where an issue occurs • Real time detection of voice quality degradation • Less overhead Active Monitoring
- 18. 17 Demo • Dip in MOS score due to DSCP change • https://earhhpng.share.thousandeyes.com
- 19. 18 VoIP Metrics Average of packet delays 99.9th percentile of packet delay variation Packets dropped by the de-jitter buffer Packets dropped by the network MOS Score (1-5) Audio codec used Source Destination
- 20. 19 Thank You!











