Comp conn 3 bits and bytes
Download as ppt, pdf1 like879 views
The document explains how computers use binary code to process information. It discusses how bits store either 1s or 0s to represent data as on or off signals. Eight bits are grouped together to form a byte, which can have one of 256 possible combinations of 1s and 0s. This binary code allows computers to interpret keyboard inputs and display letters on screens. Memory and storage capacities are measured in bytes, kilobytes, megabytes and gigabytes based on groups of bits and bytes.
1 of 9
Downloaded 31 times








Ad
Recommended
bit, Byte, Kilobyte 



bit, Byte, Kilobyte Poliano123 The document discusses the components inside a computer system unit. It describes how computers represent and store data, the components on the motherboard like the CPU and memory, and how the CPU processes instructions. It also outlines various connectors and ports on the exterior of the system unit that allow connection of peripheral devices.
Binary number system (part 1)



Binary number system (part 1)Billy Jean Morado The binary number system uses only two digits, 0 and 1, while the decimal system uses ten digits, 0-9. Binary is useful for computers and digital electronics because circuits can be designed to represent "on" and "off" as 1 and 0. A single binary digit is called a bit, while 8 bits form a byte. To convert between binary and decimal, binary uses place values like decimal (ones, twos, fours, eights etc.) and decimal uses long division, with remainders becoming the binary digits.
Exploring Ethics - 8th Grade



Exploring Ethics - 8th Gradeallsaintstech To protect their ownership and control over how their intellectual property is used. Requiring permission ensures they can determine appropriate and legal uses of their creative works.
Storage unit



Storage unitMohsinHusenManasiya 1) A bit is the smallest unit of computer data and can have a value of 0 or 1. 8 bits form a byte.
2) Common units of computer data storage are the kilobyte (KB), megabyte (MB), gigabyte (GB), terabyte (TB), petabyte (PB), exabyte (EB), zettabyte (ZB), and yottabyte (YB), with each being 1024 times larger than the previous unit.
3) These units are used to measure and describe computer memory, storage, and data transmission speeds in bytes, kilobytes, megabytes etc. depending on the size of the data or storage being referred to
2nd Quarter CSS Week 1.pptx



2nd Quarter CSS Week 1.pptxJOSEKARLOSMPABLO Here are the answers without showing work:
1. Schematic diagram
2. Charts
3. Block diagram
4. Lay-out plans/Floor plan
.Comp Org and Arch All_Slide_1711695396000.pptx



.Comp Org and Arch All_Slide_1711695396000.pptxshambelworku8 Various technologies have been discussed to reduce the incidence of certificate forgeries and ensure that the security, validity and confidentiality of graduation certificates, even though there are many limitations regarding the security and privacy of data. A new block chain-based system reduces the certificate forgery.
CSS L03 - Mensuration and Calculation in CSS



CSS L03 - Mensuration and Calculation in CSSMarvin Bronoso This document discusses digital representation and binary conversion. It defines a bit as the basic unit of data in computing and explains how ASCII uses binary codes to represent letters, numbers, and characters. It then demonstrates how to convert between decimal and binary numbers through long division and provides an example of converting 25 to its binary equivalent of 11001. Finally, it includes tables defining bytes, kilobytes, megabytes, gigabytes and terabytes in terms of bits and bytes.
An Introduction To Python - Understanding Computers



An Introduction To Python - Understanding ComputersBlue Elephant Consulting This presentation is a part of the COP2271C college level course taught at the Florida Polytechnic University located in Lakeland Florida. The purpose of this course is to introduce Freshmen students to both the process of software development and to the Python language.
The course is one semester in length and meets for 2 hours twice a week. The Instructor is Dr. Jim Anderson.
A video of Dr. Anderson using these slides is available on YouTube at: https://www.youtube.com/watch?feature=player_embedded&v=ar8cV0ynWAw
Learning Area 2



Learning Area 2norshipa The document provides an overview of computer systems and their components. It can be summarized as follows:
1) A computer system consists of four major hardware components: input devices, output devices, a processor, and storage devices. It requires both hardware and software to function, with software providing instructions to tell the hardware what to do.
2) Input devices such as keyboards and mice are used to enter data into the system. Processing is carried out by the central processing unit (CPU). Output devices like monitors and printers are used to display or print the processed data. Storage devices hold data, programs and files for future use.
3) The information processing cycle involves a user inputting data, the processor carrying out
Learning Area 2



Learning Area 2norshipa The document provides an overview of computer systems and their components. It can be summarized as follows:
1) A computer system consists of four major hardware components: input devices, output devices, a processor, and storage devices. It requires both hardware and software to function, with software providing instructions to tell the hardware what to do.
2) Common input devices include keyboards, mice, and scanners. Output devices display processed data through monitors, printers, and speakers. Storage holds data and programs, while the processor controls activities and executes instructions.
3) The information processing cycle involves a user inputting data, the processor accessing stored programs and data to process the input, and output devices presenting the processed output back
03. language of computer & translators



03. language of computer & translatorsTimesRide Basic training on computer and internet for all age group. Now learn computer and internet on your own and surprise your loved ones! :)
Youtube Link: https://youtu.be/OihTQZ6ryhk
https://youtu.be/C4t-GTWOPxY
Lets Just Go For It! Wish you an Awesome Leaning Experience.
Subscribe to our YouTube channel: https://www.youtube.com/c/TimesRide?sub_confirmation=1
Our Official Website: http://timesride.com
Follow us:
Facebook: https://www.facebook.com/rs.agrawal.9026
Instagram: https://www.instagram.com/timesridenetwork/
Twitter: https://twitter.com/TimesRide
Pinterest: https://in.pinterest.com/ride0472/
Thank You
#AwesomeLearningExperience
#SmartQuickTips&Tricks #LeaningVideos #TimesRide #Keep Learning to Keep Winning!
Chapter 2



Chapter 2Hajar Len This document provides information about computer systems and their components. It discusses that a computer accepts data as input, processes it according to rules, produces output, and stores results. It also describes the functions of input, output, storage, and processing devices. The central processing unit (CPU) controls and coordinates the computer's operations by fetching instructions, decoding them, executing them, and storing results. Data is represented digitally using bits, bytes, and character encoding schemes like ASCII. Units of data measurement like kilobytes and clockspeed measures like megahertz and gigahertz are also explained.
Data_Storage_Units_and_System_Components.pptx



Data_Storage_Units_and_System_Components.pptxAyesha Saeed Basic units of data storage
Bit
Byte
Kilo byte KB
Mega byte MB
Giga byte GB
Tera byte TB
Word
System and its components and procedures
Hardware
Software
User
Data/information
Communication
Bsc cs 1 fit u-1 computer hardware system



Bsc cs 1 fit u-1 computer hardware systemRai University The document discusses the history and components of computers. It covers:
1) The evolution of computers from the 1800s to present day, moving from vacuum tubes to transistors to integrated circuits.
2) The basic components of a computer including the CPU, control unit, arithmetic logic unit, and different logic gates like AND, OR, XOR.
3) An overview of computer memory, how it is measured, the two main types of primary memory (RAM and ROM), and what each stores.
8085 Microprocessor - Ramesh Gaonkar.pdf-27 (1).pptx



8085 Microprocessor - Ramesh Gaonkar.pdf-27 (1).pptxsruti009988 The microprocessor is a programmable device that processes binary numbers according to instructions stored in memory. It contains arithmetic, logic, and control circuits on a single silicon chip. Early processors used discrete components but were large and slow. The invention of the microchip led to much smaller and faster processors by integrating all components onto a single silicon slice. Modern microprocessors manipulate 32-bit or 64-bit words and have instruction sets that define their capabilities. The 8085 was an 8-bit microprocessor that used multiplexed address/data lines, requiring external latching to separate addresses from data.
Introduction to programming concepts



Introduction to programming conceptshermiraguilar The document discusses the basics of computer hardware and software components. It begins by defining a computer and its characteristics of receiving input, storing data, and providing output. It then describes the principal hardware components of a basic computer system, including the central processing unit, memory, input/output devices, and storage devices. It also discusses computer data representation and software components. The document provides an overview of key concepts in an introductory manner.
ICT8_Q4_Week_1&2.pptx



ICT8_Q4_Week_1&2.pptxEdelmarBenosa3 This document contains information about various topics related to information and communication technology. It discusses measuring instruments and their use in quantifying physical amounts against standard units. It also describes computer components like memory, data storage capacity, processors, and video cards. Various units of measurement for electronic data like bits, bytes, kilobytes and gigabytes are defined. Basic electrical theory is covered, including definitions of electricity, current, direct and alternating current. Ohm's Law relating voltage, current and resistance in a circuit is also explained.
Introduction to programming concepts



Introduction to programming conceptshermiraguilar The document discusses the basics of computer hardware and software components. It defines what a computer is and describes the principal hardware components including the central processing unit, memory, input/output devices, and storage devices. It also discusses computer data representation in binary form, computer codes like ASCII and Unicode. The document then covers the basics of computer software, the different types of software, and the software development life cycle.
Computer Introduction



Computer IntroductionSpy Seat This document provides an agenda for a computer introduction class that covers various topics including:
- Class work such as quizzes and programming lessons
- Homework assignments involving discovery tasks and simple projects
- Topics like human cognition, binary numbering, keyboard technology, computer components like memory and processors
- Concepts like input/output, memory types, ASCII encoding, how computers work, and differences between 32-bit and 64-bit systems
ICT-Binary & Memory Computer Subject Topic



ICT-Binary & Memory Computer Subject TopicJhonVergelOrpiana This lesson is about to know how binary works in our computer; and how we interpret it.
Dhacaini



Dhacainichrispaul8676 Computers use binary digits (0s and 1s) to represent all data as these are the only two states that electronics can interpret. Characters are encoded using patterns of bits and bytes, with ASCII and Unicode being the most common encoding schemes to represent a wide range of languages. For a character to be displayed, it is converted through various stages from a keyboard press to a binary code to the appropriate character on screen.
data representation



data representationchrispaul8676 Computers use binary digits (0s and 1s) to represent all data as these are the only two states that electronics can recognize. Characters are represented by patterns of bits (the smallest unit of data) that are grouped into bytes. Initially, the ASCII coding scheme was used to represent English and Western European languages using 7-bit bytes, but Unicode superseded it using 16-bit bytes and supports over 65,000 characters for many languages. When typing on a keyboard, keys are converted to electronic signals then binary codes which are processed and converted back to recognizable characters on a screen.
fundamental of computer-u-1-computer hardware system



fundamental of computer-u-1-computer hardware systemRai University This document provides information about the history and generations of computers. It discusses:
- The first generation of computers from 1949-1955 used vacuum tubes and machine language. Computers were large in size.
- The second generation from 1956-1965 saw the introduction of transistors, magnetic core memory, and magnetic disk storage. Computers became smaller, more reliable, and assembly language was introduced.
- The third generation from 1966-1975 replaced transistors with integrated circuits, making computers faster and more reliable. High-level programming languages also appeared.
- The fourth generation from 1976 to present saw the development of microprocessors and very large scale integrated circuits. Portable computers emerged and data communication advanced. Secondary memory increased
Bba i-introduction to computer-u-1-computer hardware system



Bba i-introduction to computer-u-1-computer hardware systemRai University This document provides information about the history and generations of computers. It discusses:
- The first generation of computers from 1949-1955 used vacuum tubes and machine language. Examples include ENIAC and EDVAC.
- The second generation from 1956-1965 used transistors instead of vacuum tubes, developed core memory, and had programming in machine and assembly languages.
- The third generation from 1966-1975 replaced transistors with integrated circuits, which made computers smaller, faster, and more reliable with programming in high-level languages.
- The fourth generation from 1976-present used microprocessors and saw development of portable computers, data communication, and storage technologies like hard disks and CD-ROMs.
Lesson4.2 u4 l1 binary squences



Lesson4.2 u4 l1 binary squencesLexume1 This document discusses how computers represent and store data using binary sequences. It explains that all digital data is ultimately stored as sequences of zeros and ones at the lowest level of abstraction. Higher-level abstractions include integers, floating point numbers, text strings, and other data types which are interpreted based on how many bits are used. The document also discusses limitations of fixed bit representations and different units for measuring data transmission capabilities.
EE5440 – Computer Architecture - Lecture 1



EE5440 – Computer Architecture - Lecture 1Dilawar Khan Topics included:
===============================================
The different types of computers
The basic structure of a computer and its operation
Machine instructions and their execution
Integer, floating-point, and character representations
Addition and subtraction of binary numbers
Basic performance issues in computer systems
A brief history of computer development
Mca i-fundamental of computer-u-1-computer hardware system



Mca i-fundamental of computer-u-1-computer hardware systemRai University The document provides information on the history and generations of computers. It discusses:
- The early pioneers and development of computers from the 1800s to the present across 5 generations from vacuum tubes to integrated circuits.
- The evolution of microcomputers with Apple and IBM PCs in the late 1970s and early 1980s.
- Definitions of what a computer is and how it works by accepting input, processing data according to instructions, and producing useful output.
- The basic components of a computer including the CPU, control unit, ALU, and different logic gates like AND, OR and XOR gates.
- An overview of computer memory including primary memory (RAM and ROM) and secondary
Digital Electronics - Logic Gates Lectures-2.pptx



Digital Electronics - Logic Gates Lectures-2.pptxJonathanCasilla3 Digital Electronics - Logic Gates - Binary Codes
Edit menu 3rd



Edit menu 3rdallsaintstech The document describes the functions of common editing commands including cut, copy, and paste which allow removing, duplicating, and repositioning selected text or data. It also discusses undo and redo commands which cancel or redo the previous editing action.
File Menu - 3rd Grade



File Menu - 3rd Gradeallsaintstech The document describes the File Menu options in Microsoft Word, including New, Open, Close, Save, and Print. New creates a new document, Open accesses existing files, Close closes the current document without exiting the program, Save stores the current document, and Print outputs the document. Saving a file requires naming the file and specifying a storage location.
Ad
More Related Content
Similar to Comp conn 3 bits and bytes (20)
Learning Area 2



Learning Area 2norshipa The document provides an overview of computer systems and their components. It can be summarized as follows:
1) A computer system consists of four major hardware components: input devices, output devices, a processor, and storage devices. It requires both hardware and software to function, with software providing instructions to tell the hardware what to do.
2) Input devices such as keyboards and mice are used to enter data into the system. Processing is carried out by the central processing unit (CPU). Output devices like monitors and printers are used to display or print the processed data. Storage devices hold data, programs and files for future use.
3) The information processing cycle involves a user inputting data, the processor carrying out
Learning Area 2



Learning Area 2norshipa The document provides an overview of computer systems and their components. It can be summarized as follows:
1) A computer system consists of four major hardware components: input devices, output devices, a processor, and storage devices. It requires both hardware and software to function, with software providing instructions to tell the hardware what to do.
2) Common input devices include keyboards, mice, and scanners. Output devices display processed data through monitors, printers, and speakers. Storage holds data and programs, while the processor controls activities and executes instructions.
3) The information processing cycle involves a user inputting data, the processor accessing stored programs and data to process the input, and output devices presenting the processed output back
03. language of computer & translators



03. language of computer & translatorsTimesRide Basic training on computer and internet for all age group. Now learn computer and internet on your own and surprise your loved ones! :)
Youtube Link: https://youtu.be/OihTQZ6ryhk
https://youtu.be/C4t-GTWOPxY
Lets Just Go For It! Wish you an Awesome Leaning Experience.
Subscribe to our YouTube channel: https://www.youtube.com/c/TimesRide?sub_confirmation=1
Our Official Website: http://timesride.com
Follow us:
Facebook: https://www.facebook.com/rs.agrawal.9026
Instagram: https://www.instagram.com/timesridenetwork/
Twitter: https://twitter.com/TimesRide
Pinterest: https://in.pinterest.com/ride0472/
Thank You
#AwesomeLearningExperience
#SmartQuickTips&Tricks #LeaningVideos #TimesRide #Keep Learning to Keep Winning!
Chapter 2



Chapter 2Hajar Len This document provides information about computer systems and their components. It discusses that a computer accepts data as input, processes it according to rules, produces output, and stores results. It also describes the functions of input, output, storage, and processing devices. The central processing unit (CPU) controls and coordinates the computer's operations by fetching instructions, decoding them, executing them, and storing results. Data is represented digitally using bits, bytes, and character encoding schemes like ASCII. Units of data measurement like kilobytes and clockspeed measures like megahertz and gigahertz are also explained.
Data_Storage_Units_and_System_Components.pptx



Data_Storage_Units_and_System_Components.pptxAyesha Saeed Basic units of data storage
Bit
Byte
Kilo byte KB
Mega byte MB
Giga byte GB
Tera byte TB
Word
System and its components and procedures
Hardware
Software
User
Data/information
Communication
Bsc cs 1 fit u-1 computer hardware system



Bsc cs 1 fit u-1 computer hardware systemRai University The document discusses the history and components of computers. It covers:
1) The evolution of computers from the 1800s to present day, moving from vacuum tubes to transistors to integrated circuits.
2) The basic components of a computer including the CPU, control unit, arithmetic logic unit, and different logic gates like AND, OR, XOR.
3) An overview of computer memory, how it is measured, the two main types of primary memory (RAM and ROM), and what each stores.
8085 Microprocessor - Ramesh Gaonkar.pdf-27 (1).pptx



8085 Microprocessor - Ramesh Gaonkar.pdf-27 (1).pptxsruti009988 The microprocessor is a programmable device that processes binary numbers according to instructions stored in memory. It contains arithmetic, logic, and control circuits on a single silicon chip. Early processors used discrete components but were large and slow. The invention of the microchip led to much smaller and faster processors by integrating all components onto a single silicon slice. Modern microprocessors manipulate 32-bit or 64-bit words and have instruction sets that define their capabilities. The 8085 was an 8-bit microprocessor that used multiplexed address/data lines, requiring external latching to separate addresses from data.
Introduction to programming concepts



Introduction to programming conceptshermiraguilar The document discusses the basics of computer hardware and software components. It begins by defining a computer and its characteristics of receiving input, storing data, and providing output. It then describes the principal hardware components of a basic computer system, including the central processing unit, memory, input/output devices, and storage devices. It also discusses computer data representation and software components. The document provides an overview of key concepts in an introductory manner.
ICT8_Q4_Week_1&2.pptx



ICT8_Q4_Week_1&2.pptxEdelmarBenosa3 This document contains information about various topics related to information and communication technology. It discusses measuring instruments and their use in quantifying physical amounts against standard units. It also describes computer components like memory, data storage capacity, processors, and video cards. Various units of measurement for electronic data like bits, bytes, kilobytes and gigabytes are defined. Basic electrical theory is covered, including definitions of electricity, current, direct and alternating current. Ohm's Law relating voltage, current and resistance in a circuit is also explained.
Introduction to programming concepts



Introduction to programming conceptshermiraguilar The document discusses the basics of computer hardware and software components. It defines what a computer is and describes the principal hardware components including the central processing unit, memory, input/output devices, and storage devices. It also discusses computer data representation in binary form, computer codes like ASCII and Unicode. The document then covers the basics of computer software, the different types of software, and the software development life cycle.
Computer Introduction



Computer IntroductionSpy Seat This document provides an agenda for a computer introduction class that covers various topics including:
- Class work such as quizzes and programming lessons
- Homework assignments involving discovery tasks and simple projects
- Topics like human cognition, binary numbering, keyboard technology, computer components like memory and processors
- Concepts like input/output, memory types, ASCII encoding, how computers work, and differences between 32-bit and 64-bit systems
ICT-Binary & Memory Computer Subject Topic



ICT-Binary & Memory Computer Subject TopicJhonVergelOrpiana This lesson is about to know how binary works in our computer; and how we interpret it.
Dhacaini



Dhacainichrispaul8676 Computers use binary digits (0s and 1s) to represent all data as these are the only two states that electronics can interpret. Characters are encoded using patterns of bits and bytes, with ASCII and Unicode being the most common encoding schemes to represent a wide range of languages. For a character to be displayed, it is converted through various stages from a keyboard press to a binary code to the appropriate character on screen.
data representation



data representationchrispaul8676 Computers use binary digits (0s and 1s) to represent all data as these are the only two states that electronics can recognize. Characters are represented by patterns of bits (the smallest unit of data) that are grouped into bytes. Initially, the ASCII coding scheme was used to represent English and Western European languages using 7-bit bytes, but Unicode superseded it using 16-bit bytes and supports over 65,000 characters for many languages. When typing on a keyboard, keys are converted to electronic signals then binary codes which are processed and converted back to recognizable characters on a screen.
fundamental of computer-u-1-computer hardware system



fundamental of computer-u-1-computer hardware systemRai University This document provides information about the history and generations of computers. It discusses:
- The first generation of computers from 1949-1955 used vacuum tubes and machine language. Computers were large in size.
- The second generation from 1956-1965 saw the introduction of transistors, magnetic core memory, and magnetic disk storage. Computers became smaller, more reliable, and assembly language was introduced.
- The third generation from 1966-1975 replaced transistors with integrated circuits, making computers faster and more reliable. High-level programming languages also appeared.
- The fourth generation from 1976 to present saw the development of microprocessors and very large scale integrated circuits. Portable computers emerged and data communication advanced. Secondary memory increased
Bba i-introduction to computer-u-1-computer hardware system



Bba i-introduction to computer-u-1-computer hardware systemRai University This document provides information about the history and generations of computers. It discusses:
- The first generation of computers from 1949-1955 used vacuum tubes and machine language. Examples include ENIAC and EDVAC.
- The second generation from 1956-1965 used transistors instead of vacuum tubes, developed core memory, and had programming in machine and assembly languages.
- The third generation from 1966-1975 replaced transistors with integrated circuits, which made computers smaller, faster, and more reliable with programming in high-level languages.
- The fourth generation from 1976-present used microprocessors and saw development of portable computers, data communication, and storage technologies like hard disks and CD-ROMs.
Lesson4.2 u4 l1 binary squences



Lesson4.2 u4 l1 binary squencesLexume1 This document discusses how computers represent and store data using binary sequences. It explains that all digital data is ultimately stored as sequences of zeros and ones at the lowest level of abstraction. Higher-level abstractions include integers, floating point numbers, text strings, and other data types which are interpreted based on how many bits are used. The document also discusses limitations of fixed bit representations and different units for measuring data transmission capabilities.
EE5440 – Computer Architecture - Lecture 1



EE5440 – Computer Architecture - Lecture 1Dilawar Khan Topics included:
===============================================
The different types of computers
The basic structure of a computer and its operation
Machine instructions and their execution
Integer, floating-point, and character representations
Addition and subtraction of binary numbers
Basic performance issues in computer systems
A brief history of computer development
Mca i-fundamental of computer-u-1-computer hardware system



Mca i-fundamental of computer-u-1-computer hardware systemRai University The document provides information on the history and generations of computers. It discusses:
- The early pioneers and development of computers from the 1800s to the present across 5 generations from vacuum tubes to integrated circuits.
- The evolution of microcomputers with Apple and IBM PCs in the late 1970s and early 1980s.
- Definitions of what a computer is and how it works by accepting input, processing data according to instructions, and producing useful output.
- The basic components of a computer including the CPU, control unit, ALU, and different logic gates like AND, OR and XOR gates.
- An overview of computer memory including primary memory (RAM and ROM) and secondary
Digital Electronics - Logic Gates Lectures-2.pptx



Digital Electronics - Logic Gates Lectures-2.pptxJonathanCasilla3 Digital Electronics - Logic Gates - Binary Codes
More from allsaintstech (6)
Edit menu 3rd



Edit menu 3rdallsaintstech The document describes the functions of common editing commands including cut, copy, and paste which allow removing, duplicating, and repositioning selected text or data. It also discusses undo and redo commands which cancel or redo the previous editing action.
File Menu - 3rd Grade



File Menu - 3rd Gradeallsaintstech The document describes the File Menu options in Microsoft Word, including New, Open, Close, Save, and Print. New creates a new document, Open accesses existing files, Close closes the current document without exiting the program, Save stores the current document, and Print outputs the document. Saving a file requires naming the file and specifying a storage location.
Computer Software - 7th Grade



Computer Software - 7th Gradeallsaintstech This document discusses different types of computer software. It defines hardware as the physical components of a computer and software as programs that tell the computer how to perform tasks. The main categories of software are operating systems, application software, and utility software. Operating systems control other programs and allow basic tasks, while application software performs specific functions like writing or email. Utility software maintains and optimizes the computer system. Popular operating systems include Windows, Mac OS, Linux, and mobile OS.
Going Online



Going Onlineallsaintstech The document discusses how to connect to and use the Internet and World Wide Web. It explains that the Internet is a network connecting computers worldwide, while the World Wide Web is a system for accessing information on the Internet through websites. It describes the components needed to connect, including a computer, Internet service provider, modem, and web browser. It also defines key terms like website, URL, search engine, and how the earliest networks like ARPANET evolved into today's Internet.
Computers connections 2



Computers connections 2allsaintstech Computers are made up of many electronic components that work together, including the motherboard, CPU, RAM, power supply, expansion cards, hard drive, and disk drives. The motherboard contains the CPU and holds other circuit boards. Expansion cards like the sound card, video card, and modem have special purposes. The CPU is the computer's brain that controls information. RAM temporarily stores information but forgets when powered off, while ROM permanently stores basic information needed to start the computer. Disk drives like the hard drive and CD-ROM are used to read and write information for storage and programs.
Computer lesson 7 files & folders



Computer lesson 7 files & foldersallsaintstech Files and folders are used to organize data on a computer. A file is a collection of data that is stored together and can be given a name, type, and location. Files are organized into folders, also called directories, to further group them together. The location and name of a file, including the file type extension, allows the computer to identify and retrieve the correct file when needed. Maintaining an organized folder structure with descriptive file names is important for efficiently finding and working with files on a computer.
Ad
Recently uploaded (20)
How Top Companies Benefit from Outsourcing



How Top Companies Benefit from OutsourcingNascenture Explore how leading companies leverage outsourcing to streamline operations, cut costs, and stay ahead in innovation. By tapping into specialized talent and focusing on core strengths, top brands achieve scalability, efficiency, and faster product delivery through strategic outsourcing partnerships.
In-App Guidance_ Save Enterprises Millions in Training & IT Costs.pptx



In-App Guidance_ Save Enterprises Millions in Training & IT Costs.pptxaptyai Discover how in-app guidance empowers employees, streamlines onboarding, and reduces IT support needs-helping enterprises save millions on training and support costs while boosting productivity.
Understanding SEO in the Age of AI.pdf



Understanding SEO in the Age of AI.pdfFulcrum Concepts, LLC This presentation dives into how artificial intelligence has reshaped Google's search results, significantly altering effective SEO strategies. Audiences will discover practical steps to adapt to these critical changes.
https://www.fulcrumconcepts.com/ai-killed-the-seo-star-2025-version/
Dark Dynamism: drones, dark factories and deurbanization



Dark Dynamism: drones, dark factories and deurbanizationJakub Šimek Startup villages are the next frontier on the road to network states. This book aims to serve as a practical guide to bootstrap a desired future that is both definite and optimistic, to quote Peter Thiel’s framework.
Dark Dynamism is my second book, a kind of sequel to Bespoke Balajisms I published on Kindle in 2024. The first book was about 90 ideas of Balaji Srinivasan and 10 of my own concepts, I built on top of his thinking.
In Dark Dynamism, I focus on my ideas I played with over the last 8 years, inspired by Balaji Srinivasan, Alexander Bard and many people from the Game B and IDW scenes.
Multi-Agent AI Systems: Architectures & Communication (MCP and A2A)



Multi-Agent AI Systems: Architectures & Communication (MCP and A2A)HusseinMalikMammadli Multi-Agent AI Systems: Architectures & Communication (MCP and A2A)
UiPath AgentHack - Build the AI agents of tomorrow_Enablement 1.pptx



UiPath AgentHack - Build the AI agents of tomorrow_Enablement 1.pptxanabulhac Join our first UiPath AgentHack enablement session with the UiPath team to learn more about the upcoming AgentHack! Explore some of the things you'll want to think about as you prepare your entry. Ask your questions.
Top Hyper-Casual Game Studio Services



Top Hyper-Casual Game Studio ServicesNova Carter BR Softech is a leading hyper-casual game development company offering lightweight, addictive games with quick gameplay loops. Our expert developers create engaging titles for iOS, Android, and cross-platform markets using Unity and other top engines.
ICDCC 2025: Securing Agentic AI - Eryk Budi Pratama.pdf



ICDCC 2025: Securing Agentic AI - Eryk Budi Pratama.pdfEryk Budi Pratama Title: Securing Agentic AI: Infrastructure Strategies for the Brains Behind the Bots
As AI systems evolve toward greater autonomy, the emergence of Agentic AI—AI that can reason, plan, recall, and interact with external tools—presents both transformative potential and critical security risks.
This presentation explores:
> What Agentic AI is and how it operates (perceives → reasons → acts)
> Real-world enterprise use cases: enterprise co-pilots, DevOps automation, multi-agent orchestration, and decision-making support
> Key risks based on the OWASP Agentic AI Threat Model, including memory poisoning, tool misuse, privilege compromise, cascading hallucinations, and rogue agents
> Infrastructure challenges unique to Agentic AI: unbounded tool access, AI identity spoofing, untraceable decision logic, persistent memory surfaces, and human-in-the-loop fatigue
> Reference architectures for single-agent and multi-agent systems
> Mitigation strategies aligned with the OWASP Agentic AI Security Playbooks, covering: reasoning traceability, memory protection, secure tool execution, RBAC, HITL protection, and multi-agent trust enforcement
> Future-proofing infrastructure with observability, agent isolation, Zero Trust, and agent-specific threat modeling in the SDLC
> Call to action: enforce memory hygiene, integrate red teaming, apply Zero Trust principles, and proactively govern AI behavior
Presented at the Indonesia Cloud & Datacenter Convention (IDCDC) 2025, this session offers actionable guidance for building secure and trustworthy infrastructure to support the next generation of autonomous, tool-using AI agents.
論文紹介:"InfLoRA: Interference-Free Low-Rank Adaptation for Continual Learning" ...



論文紹介:"InfLoRA: Interference-Free Low-Rank Adaptation for Continual Learning" ...Toru Tamaki Yan-Shuo Liang, Wu-Jun Li,"Adaptive Plasticity Improvement for Continual Learning" CVPR2023
https://openaccess.thecvf.com/content/CVPR2023/html/Liang_Adaptive_Plasticity_Improvement_for_Continual_Learning_CVPR_2023_paper.html
Yan-Shuo Liang, Wu-Jun Li,"InfLoRA: Interference-Free Low-Rank Adaptation for Continual Learning" CVPR2024
https://openaccess.thecvf.com/content/CVPR2024/html/Liang_InfLoRA_Interference-Free_Low-Rank_Adaptation_for_Continual_Learning_CVPR_2024_paper.html
Who's choice? Making decisions with and about Artificial Intelligence, Keele ...



Who's choice? Making decisions with and about Artificial Intelligence, Keele ...Alan Dix Invited talk at Designing for People: AI and the Benefits of Human-Centred Digital Products, Digital & AI Revolution week, Keele University, 14th May 2025
https://www.alandix.com/academic/talks/Keele-2025/
In many areas it already seems that AI is in charge, from choosing drivers for a ride, to choosing targets for rocket attacks. None are without a level of human oversight: in some cases the overarching rules are set by humans, in others humans rubber-stamp opaque outcomes of unfathomable systems. Can we design ways for humans and AI to work together that retain essential human autonomy and responsibility, whilst also allowing AI to work to its full potential? These choices are critical as AI is increasingly part of life or death decisions, from diagnosis in healthcare ro autonomous vehicles on highways, furthermore issues of bias and privacy challenge the fairness of society overall and personal sovereignty of our own data. This talk will build on long-term work on AI & HCI and more recent work funded by EU TANGO and SoBigData++ projects. It will discuss some of the ways HCI can help create situations where humans can work effectively alongside AI, and also where AI might help designers create more effective HCI.
Building a research repository that works by Clare Cady



Building a research repository that works by Clare CadyUXPA Boston Are you constantly answering, "Hey, have we done any research on...?" It’s a familiar question for UX professionals and researchers, and the answer often involves sifting through years of archives or risking lost insights due to team turnover.
Join a deep dive into building a UX research repository that not only stores your data but makes it accessible, actionable, and sustainable. Learn how our UX research team tackled years of disparate data by leveraging an AI tool to create a centralized, searchable repository that serves the entire organization.
This session will guide you through tool selection, safeguarding intellectual property, training AI models to deliver accurate and actionable results, and empowering your team to confidently use this tool. Are you ready to transform your UX research process? Attend this session and take the first step toward developing a UX repository that empowers your team and strengthens design outcomes across your organization.
Developing Product-Behavior Fit: UX Research in Product Development by Krysta...



Developing Product-Behavior Fit: UX Research in Product Development by Krysta...UXPA Boston What if product-market fit isn't enough?
We’ve all encountered companies willing to spend time and resources on product-market fit, since any solution needs to solve a problem for people able and willing to pay to solve that problem, but assuming that user experience can be “added” later.
Similarly, value proposition-what a solution does and why it’s better than what’s already there-has a valued place in product development, but it assumes that the product will automatically be something that people can use successfully, or that an MVP can be transformed into something that people can be successful with after the fact. This can require expensive rework, and sometimes stops product development entirely; again, UX professionals are deeply familiar with this problem.
Solutions with solid product-behavior fit, on the other hand, ask people to do tasks that they are willing and equipped to do successfully, from purchasing to using to supervising. Framing research as developing product-behavior fit implicitly positions it as overlapping with product-market fit development and supports articulating the cost of neglecting, and ROI on supporting, user experience.
In this talk, I’ll introduce product-behavior fit as a concept and a process and walk through the steps of improving product-behavior fit, how it integrates with product-market fit development, and how they can be modified for products at different stages in development, as well as how this framing can articulate the ROI of developing user experience in a product development context.
May Patch Tuesday



May Patch TuesdayIvanti Ivanti’s Patch Tuesday breakdown goes beyond patching your applications and brings you the intelligence and guidance needed to prioritize where to focus your attention first. Catch early analysis on our Ivanti blog, then join industry expert Chris Goettl for the Patch Tuesday Webinar Event. There we’ll do a deep dive into each of the bulletins and give guidance on the risks associated with the newly-identified vulnerabilities.
Top 5 Qualities to Look for in Salesforce Partners in 2025



Top 5 Qualities to Look for in Salesforce Partners in 2025Damco Salesforce Services 🔍 Top 5 Qualities to Look for in Salesforce Partners in 2025
Choosing the right Salesforce partner is critical to ensuring a successful CRM transformation in 2025.
Integrating FME with Python: Tips, Demos, and Best Practices for Powerful Aut...



Integrating FME with Python: Tips, Demos, and Best Practices for Powerful Aut...Safe Software FME is renowned for its no-code data integration capabilities, but that doesn’t mean you have to abandon coding entirely. In fact, Python’s versatility can enhance FME workflows, enabling users to migrate data, automate tasks, and build custom solutions. Whether you’re looking to incorporate Python scripts or use ArcPy within FME, this webinar is for you!
Join us as we dive into the integration of Python with FME, exploring practical tips, demos, and the flexibility of Python across different FME versions. You’ll also learn how to manage SSL integration and tackle Python package installations using the command line.
During the hour, we’ll discuss:
-Top reasons for using Python within FME workflows
-Demos on integrating Python scripts and handling attributes
-Best practices for startup and shutdown scripts
-Using FME’s AI Assist to optimize your workflows
-Setting up FME Objects for external IDEs
Because when you need to code, the focus should be on results—not compatibility issues. Join us to master the art of combining Python and FME for powerful automation and data migration.
Mastering Testing in the Modern F&B Landscape



Mastering Testing in the Modern F&B Landscapemarketing943205 Dive into our presentation to explore the unique software testing challenges the Food and Beverage sector faces today. We’ll walk you through essential best practices for quality assurance and show you exactly how Qyrus, with our intelligent testing platform and innovative AlVerse, provides tailored solutions to help your F&B business master these challenges. Discover how you can ensure quality and innovate with confidence in this exciting digital era.
Build With AI - In Person Session Slides.pdf



Build With AI - In Person Session Slides.pdfGoogle Developer Group - Harare Build with AI events are communityled, handson activities hosted by Google Developer Groups and Google Developer Groups on Campus across the world from February 1 to July 31 2025. These events aim to help developers acquire and apply Generative AI skills to build and integrate applications using the latest Google AI technologies, including AI Studio, the Gemini and Gemma family of models, and Vertex AI. This particular event series includes Thematic Hands on Workshop: Guided learning on specific AI tools or topics as well as a prequel to the Hackathon to foster innovation using Google AI tools.
Cybersecurity Tools and Technologies - Microsoft Certificate



Cybersecurity Tools and Technologies - Microsoft CertificateVICTOR MAESTRE RAMIREZ Cybersecurity Tools and Technologies - Microsoft Certificate
Crazy Incentives and How They Kill Security. How Do You Turn the Wheel?



Crazy Incentives and How They Kill Security. How Do You Turn the Wheel?Christian Folini Everybody is driven by incentives. Good incentives persuade us to do the right thing and patch our servers. Bad incentives make us eat unhealthy food and follow stupid security practices.
There is a huge resource problem in IT, especially in the IT security industry. Therefore, you would expect people to pay attention to the existing incentives and the ones they create with their budget allocation, their awareness training, their security reports, etc.
But reality paints a different picture: Bad incentives all around! We see insane security practices eating valuable time and online training annoying corporate users.
But it's even worse. I've come across incentives that lure companies into creating bad products, and I've seen companies create products that incentivize their customers to waste their time.
It takes people like you and me to say "NO" and stand up for real security!
Design pattern talk by Kaya Weers - 2025 (v2)



Design pattern talk by Kaya Weers - 2025 (v2)Kaya Weers Talk: A design pattern goes to the supermarket
By: Kaya Weers
Given at various conferences and Meetups
Ad
Comp conn 3 bits and bytes
- 1. Computer Connections: Lesson 3 - Bits & Bytes
- 2. Did you know… • All information that travels through your computer is based on two commands?
- 3. On or Off • The only data a computer can understand is on and off. • But, the millions of combinations of those two commands given in series are what make a computer work.
- 4. Huh?!? • Remember the power supply that is inside your computer and how it sends electricity to all of the components? • That electricity is what creates an on signal.
- 5. bits • The memory chips inside your computer are divided into thousands of tiny compartments called bits. • Each bit has an electronic switch or gate. – On (1) = gate is open and letting electricity go through. – Off (0) = gate is closed gates because the electricity is blocked and cannot get through.
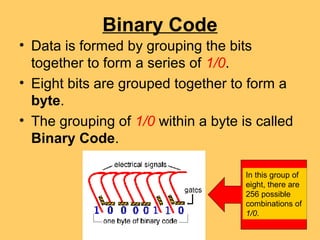
- 6. Binary Code • Data is formed by grouping the bits together to form a series of 1/0. • Eight bits are grouped together to form a byte. • The grouping of 1/0 within a byte is called Binary Code. In this group of eight, there are 256 possible combinations of 1/0.
- 7. How Binary Code Works: • type the letter A on your keyboard • electrical signals are sent from the keyboard to the CPU. • The CPU processes the signals and turns it into binary code. • The computer reads the binary code and sends it to the monitor to display the letter A.
- 8. B, KB, MB & GB • You may have seen these abbreviations many times before. • Do you know what they mean? 8 bits = 1 byte (B) 1,000 B = 1 Kilobyte (KB) 1,000 KB = 1 Megabyte (MB) 1,000 MB = 1 Gigabyte (GB) 1,000 GB = 1 Terabyte (TB)
- 9. Memory • Memory/Storage capacity is measured in Bytes. • Ex: 15GB hard drive = the hard drive has the capacity to store 15 billion bytes.
Editor's Notes
- #7: In this group of eight, there are 256 possible combinations of 1/0 .