Encryption Deep Dive
- 2. @diego_pacheco ❏ Cat's Father ❏ Head of Software Architect ❏ Agile Coach ❏ SOA/Microservices Expert ❏ DevOps Practitioner ❏ Speaker ❏ Author diegopacheco http://diego-pacheco.blogspot.com.br/ About me... https://diegopacheco.github.io/
- 4. Asymmetrical Encryption ❏ Protect Data at Transit ❏ Public Key Cryptography ❏ Public Key does Encryption ❏ Private Key does Decryption ❏ Used on TLS/mTLS(HTTPS), SSH ❏ Algos: RSA, Diffie-Hellman, ECC ❏ Key Size often from 1 to 4kb
- 5. Symmetrical Encryption ❏ Protect Data at Rest (Payment, PII, etc…) ❏ Requires RNG and PRNG ❏ Biggest problem: Share / Access the encryption keys ❏ Block vs Stream Algos ❏ Algos: AES, RC4, RC5 ❏ Key Sizes: 128, 192, 256 ❏ C = E(K,P ) - P = D(K,C)
- 6. Symmetrical Encryption ❏ Ciphertext same or slightly bigger than the plaintext ❏ Ciphertext is never smaller than the plaintext ❏ Permutations should be determined by the key ❏ Different keys should result in different permutation ❏ The permutation should look random ❏ Kerckhoffs Principle - 1883 - Really on a secret key - not on the secrecy of the Cipher ❏ Storage vs Application level encryption
- 7. Application side encryption Drawbacks ❏ For sure more secure, however… ❏ Requires Engineering Discipline ❏ Requires constant Education / Training ❏ Cripple Features (Uniquines, Joins, Search) ❏ Bugs, Changes, Improvements Intrusive Require Migrations ❏ Key Scoping is mirror by Conway’s law / Architecture
- 8. Protecting Keys ❏ Storing the key on a hardware token(Smart Card or USB dongle) ❏ On the fly generation from a password ❏ Wrapping - protecting the key with another key ❏ Key Management System
- 9. Randomness ❏ Randomness is a probability distribution ❏ Probability is about the likelihood of something happening: 0 never, 1 certain. ❏ Uniform Distribution when all probabilities are equal chance do happens ❏ Toss a coin (Tail or Head) is 1/2 + 1/2 = 1, 1/2 chance head, 1/2 chance tail.
- 10. Entropy ❏ Entropy as a measure of Uncertain ❏ The measure of disorder in a system ❏ Entropy is the amount of surprise found in the result of a random process ❏ Higher entropy less the certain found on the result ❏ Entropy is maximized when the distribution is uniform
- 11. RNG ❏ A Source of incertain, or a source of entropy ❏ A Crypto algo to produce high-quality bits from the source of entropy ❏ RNG could be sampling from(Sources of entropy): ❏ measurements of temperature, acoustic noise, air turbulence, or electric static (which are not always available) ❏ Entropy from OS: sensors, I/O devices, network, disk, logs, running process (But can be fragile and manipulated by an attacker)
- 12. PRNG ❏ Relly on RNG ❏ RNG product random bits(Analog) but slow and no deterministic and no guarantee of high entropy ❏ PRNG: Random looking data, Quickly from Digital Sources, deterministic and maximum entropy.
- 13. PRNG ❏ PRNG needs to ensure backtracking resistance (previously generated bits are impossible to recover) ❏ PRNG needs to ensure prediction resistance (impossible to predict future bits) ❏ /dev/random vs /dev/urandom (un-blocking) ❏ Java Secure Random
- 14. AES ❏ World defacto standard encryption ❏ NSA approved AES for TOP-Secret information ❏ AES is more Belgian than American ❏ Blocks of 128 bits (128, 192, 256) ❏ AES will never be broken ❏ All input bytes depends on output bytes in some complex pseudo random way
- 15. AES ❏ 2011 - People found a way to recover AES 128 bits key but require an insane amount of data plaintext ciphertext pairs 2 ^ 88 bits (so we don't need to worry about it) ❏ The biggest threat is not the CORE algo bug the Operation Modes ❏ Authentication vs Confidentiality modes
- 16. AES Operational Modes ❏ Authenticated Encryption ❏ GCM ❏ CCM ❏ SIV ❏ AES-GCM-SIV ❏ Confidentiality only ❏ ECB ❏ CBC ❏ PCBC ❏ CFB, OFB and CTR
- 17. AES Operational Modes - ECB (Electronic Code Book)
- 18. AES Operational Modes - ECB (Electronic Code Book)
- 19. AES Operational Modes - CBC (Cipher Block Chaining)
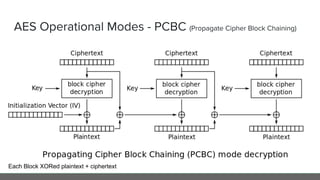
- 20. AES Operational Modes - PCBC (Propagate Cipher Block Chaining) Each Block XORed plaintext + ciphertext
- 21. AES Operational Modes - CFB (Cipher Feedback) ❏ Stream Cipher ❏ Decrypt Parallel ❏ Encryption Blocking
- 22. AES Operational Modes - OFB (Output Feedback) ❏ Stream Cipher ❏ Encrypt IV ❏ XOR plaintext ❏ Does not require Padding Data
- 23. AES Operational Modes - CTR encryption/decryption parallelization
- 27. Java Encrypt
- 28. Java Encrypt
- 29. Java Decrypt
- 30. Java Decrypt
- 31. Keys & Data Rotations ❏ Use cases: Regular or Breach ❏ Standard Industry Practice ❏ In AVG around 90 days ❏ Downtime vs No-Downtime ❏ Can have reliability implications ❏ Requires Data Catalogs ❏ Operationality, Observability, Rowbacability challenges
- 32. Envelope Encryption ❏ More Secure ❏ Industry Standard ❏ Keys with the Data ❏ Key Encrypting: Keys, Metadata and Data ❏ Bootstrapping problem ❏ KMS
- 33. AWS KMS ❏ Uses Cloud HSM to protect the Keys ❏ Keys lever leave AWS ❏ Remote Encryption always ❏ Symmetrical and Asymmetrical encryption ❏ Integrated with IAM and other services(EBS, S3, Kinesis, RedShift, etc...) ❏ Cloud Trail
- 34. AWS KMS
- 35. Books