Buffer overflow attacks
- 1. Buffer Overflow Attacks Abstract A buffer-overflow is vulnerability in computer software that could be exploited to run arbitrary machine instructions on the microprocessor. Almost all computing software platforms/hardware are vulnerable to this class of attack. When a malicious computer user/computer hacker or a virus writer can exploit a typical software system and prompt it to execute arbitrary machine instructions it could use this class of attack as a virus spreading or a virus inflection technique. Most of the computer worms [ viruses that can spread through a network medium without user intervention] are written using this technique. Terms and Explanation: Computer Virology: The study about computer viruses and how it affects , what mechanisms it uses and how to defend from it are covered under the computer virology. Vulnerability: Vulnerability is a weakness of a particular system. For a example if your blood have low count of white cell counts then it’s said that your vulnerable to many viruses and flu’s. The same idea exists on computing too, for a example if you won’t update your operating system in time your computer Is vulnerable to lots of security related threats. NOTE: Every vulnerability is not a computer security weakness outside the computer security there can be weaknesses in a particular computer system or software. Class Of Attack: We can classify computer security vulnerabilities into classes of attacks , which clearly defines the security problem which is related to security ,defines mechanisms and procedures exploit it and also how to defend with the problem. Flaw: a Flaw in a computer system means a malfunction, it’s exists due to a careless Engineering. Note that every malfunction won’t be Other Classes Of Attacks: Buffer overflows are just only a one class of attack. And there are other classes of attacks. The bellow list defines few. Brute Force Attacks. SQL injection Attack. XXS [Cross Site Scripting]. Distributed Denial Of Service. [DDos]. Smurf Attacks. String Injection Techniques. XML poisoning. … and many more. So you can clearly see there is a huge area of classifications under computer vulnerabilities. In Computer security the weakest security is equal to the system security. So if a hacker can find any vulnerability under any classification [class ] then he can easily make the complete system security to zero. Vulnerability : Case Study: As I already explained vulnerability in a system means a weakness of a system which can alter the system integrity. So Let’s take a simple case study about a vulnerability which is related to a well known operating system windows XP before the Service pack 1.Windows XP have a default screen saver and it’s running as a background process no matter user logs in or not. When a user logs on it will run as a system process. A system process is a process which have the highest privileges so a attack can perform critical operations including the malicious once. Since the path to the default screen saver is stored in a register key , and a attack who logged as a non-administrator and he have the privileges to alter that register key, He could easily change the “default.scr” to “cmd.exe” and obtain a higher privileged command prompt.
- 2. So What’s a Bufferoverflow Attack: As it derived from it’s name it’s something to do with a buffer, a buffer is a segment of memory which is you can store some data. Every buffer have a bound or a limit. When a user/computer program violates the bound it’s known as a overflow. A overflow condition may end with a exception behavior or overwriting some other data which is stored for other purpose. Memory Exceptions: Modern operating systems and practically with help of hardware , have implements a defense against memory violations, Memory are divided into the segments in Modern operating systems and each segment of memory have implements flags/info how different processes can access the segment. There are levels of access , They are known as read, write and execution privileges’. When if a process violates the privileges’ it have , the microprocessor will generate a interrupt and transfer the control to the operating system, so the operating system can deal with it in it’s own way. Case Study: Segmented Memory Protection In the x86 computer platform , the modern processors above i386 have a mode called protected mode. As it name implies it’s a protected mode. It implements the segment based memory protection. X86 architecture have something called a “descriptor register” and it holds a address to a array of 8 bytes data structure known as segment descriptor. When a process wants to access memory location [for a example move ax , DS:[memory_location] ] , the microprocessor do some bound checking’s with the base address filed and segment limit field. And also checks whether it violates privileges’ using the DPL and S fields of the above data structure. DPL : Descriptor Priviledge level. S : System descriptor or a data or code descriptor. ^ image is scanned from the book The Intel Microprocessors Architecture ,Programming and Interfacing by Barry. B Brey.
- 3. But Why Doesn’t That above Segmented Protection Does Not Valid Against BufferOverflows? The above technique can only address the security between different segments, but not security inside segments. There can be several buffers stored in a one memory segment. And nothing prevents a process having enough requested priviledgs will accessing the contents of the anywhere in the segment. In the hardware level the smallest chunk of memory that can be protect is in the segment level. But segments are typically very large blocks of memory. Subcategories of Bufferoverflows: Bufferoverflow is just only a one class of attack , even it contains two different sub categories. Stack Based Overflow. Heap Based Overflow. Terms And Explanation: Stack: From the Oxford Learner’s dictionary the term “stack” is defined as “a pile of something , which usually netly arranged” [Ex-stack of Books] . A stack is something have LIFO (last in first out) characteristic. Where you can keep books in a stack , and you can first take out the book that you kept there last. Heap: Heap is a area of memory where computer programs can make a request to the operating system to allocate that block of memory for me. Large data-structures are typically stored in the heap. Introduction To Stack Computing In computing world , stack is a very useful data-structure. In x86 world , it’s normally implements as a whole segment. And the Stack Segment register (SS) will keep the base address, and register (SP) Stack Pointer is keeping the memory address where it can push next data. Stack have two operations , Push and Pop. In X86 computing world , they are implemented with machine instructions PUSH and POP. More than that basic two instructions X86 supports some additional instructions related to stack , for a example PUSHA, POPA, ENTER , LEAVE. Computer programs are very complex by it’s nature. As we look into It as a whole it’s sometimes beyond the human imaginary powers. So that complexity is decomposed into modules , which is a very common engineering concept in computer software engineering. Modules are normally implemented as functions and routines. So a large complex computer program is nothing more than a mess of functions and routines calling each other to perform a specific goal. When you calling a routine , for a example add two numbers , you need to pass parameters to that routine as input. You can easily allocate two Microprocessor registers to pass these values , but when the number of inputs grows you will probably need to store some stack like data structure to store parameters. Simply the caller can push the parameters to the stack and callee can pop them back and use them. Many callers can call a particular function or a routine. But when the function performed it’s operation it should return back to where it’s originally called. So there should be a mechanism to store the return address of a function. So here It comes the help of stack again. The return value also stored in the stack. You may notice that a module may require some local variables to store it’s temporary values, they should be created and destroyed on the fly. This can be done easily with the stack, simply you can allocate local space for local variables by subtracting the stack pointer by the number of bytes you need to allocate. And destroy then just adding the number of bytes you allocated. The intel x86 architecture also contains the a register called BP [base pointer] where it keeps the base address of the local variables.
- 4. A typical stack frame of a stack frame is illustrated in the bellow picture.with it’s disassembly. And you can see that. Figure 1.1 dissassembly for the program . #include <stdio.h> Void function(int a, int b) { int var1; int var2; char buffer[200]; scanf(“%s”,buffer); // do some computations // Return; } Program Listing 1.2
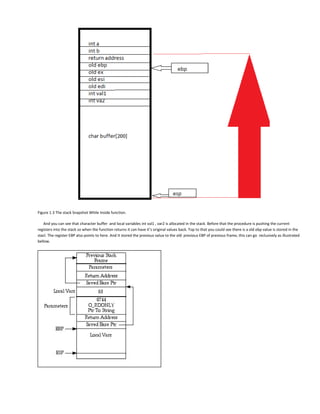
- 5. Figure 1.3 The stack Snapshot While Inside function. And you can see that character buffer and local variables int val1 , var2 is allocated in the stack. Before that the procedure is pushing the current registers into the stack so when the function returns it can have it’s original values back. Top to that you could see there is a old ebp value is stored in the stacl. The register EBP also points to here. And It stored the previous value to the old previous EBP of previous frame, this can go reclusively as illustrated bellow.
- 6. So How It Works ? In the previous pages, I have explained how the stack operates and now you have a good technical understanding how functions are calling and how the stack frame is working. But how it affects. To that let me write a small program as I also illustrated in figure 1.2 for you. It take 2 int parameters as inputs , and create another two int‟s as local variables and a big char array of size 200. And the address to that char array is passed to the scanf() function as a buffer to take some user input.. It won‟t matter if user enters a input string of 200 or less characters, but what will happen when it‟s 201 characters. Then it will go beyond it and override some part of the „int val2‟ variable. Like this a one can easily override up to the return address too. Which will alter the value of the return address due to a user input. This is a dangours thing , because all the users who are using this application are not 100% pure genuine users. So for them they have a possibility to alter the return address to a arbitrary value of their choice.[note the big red arrow of Figure 1.3] and in the worst thing is not only a user can alter the return address, and return. He can easily inject some arbitrary instructions to the buffer and manipulate the return address to return back to there. In that way a malicious computer user can easily execute arbitrary instructions. So What‟s The Fancy Thing About This Buffer? If the user of the computer system also the owner then it won‟t affect. But Suppose in a case of a internet HTTP server or a bank teller machine. There are places where it uses lots of buffers in those places , for a example in HTTP server packet may stored in a buffer, in that case if a hacker found some buffer overflow vulnerability in the server he may use it to execute the machine instructions in somebody‟s else‟s computer. In the case of bank teller , the key card contains some data structure to tell to the bank about the user. What if a hacker able to found a overflow condition of that buffers? He an easily bypass all the security and made the system to call a function that throws money out of his choice. More than the above extremely high illegal things , ppl do use to write viruses using this technique. Probably the network worms. where you it don‟t need any user intervention to spread over the internet. Not only computers , they can be engineered to inflect to network routers . There was a worm that threatened the whole internet by attacking the root name servers in the internet. Fortunately computer virus researches have identified it‟s code structure and block it before inflecting all the 13 name servers, it was a real risk and everybody at that time believed that it‟s the end of the whole internet. Another worm that kept a history record is , Code Red worm. It was engineered to inflect Microsoft IIS server. Defend Against Buffer-Overflow Attacks Even through the computing and internet is a hostile place, we can‟t live without it. Businesses to the Missile control systems are all depends on the internet and the computing. So we probably have to find a well suitable defend against. There are hardware and software techniques to defend against buffer overflows. Hardware Techniques: As I already explained a segmented memory addressing is a one way of keeping memory safe. But it won‟t affect someone will violate a memory bound inside a segment. However you can say “please do not execute on stack segment” to the microprocessor. Modern day microprocessors have implemented a feature called DEP [data execution presentation], to avoid stack based and heap based buffer overflows. It‟s nothing more than just a flag, where enabling that flag , and if the segment is marked as a data segment in the descriptor and if you tried to execute on it, it will simply throw a exception and pass the control to the operating system [ exception handler]. Terms And Explanations: Exception handler: Exceptions are thrown when there is unrecoverable error occurred in a computer system. For a example divide by zero ,or a memory violation. It was implemented on the hardware level , where you also could throw exceptions using the interrupt mechanism. There is a link list called SEH Standard Exception Handler , where every module have a address to a exception handling routine and also keeps the address to the previous exception handler. Typically when a exception handler function is called , it will dump memory , log the status or do something like that to help someone who need to fix the program.
- 7. Software Techiniques. There are software techniques to defend against the Buffer-Overflow attacks. They are twofold, *static * dynamic Dynamic methods are IDS firewalls, Antivirus programs and software firewalls. Vendor examples are nortan , Macafee , zone alarm etc. When it comes to static techniques , we are not talking about a running program or invoke security while it‟s running. Under the static techniques we can fist take static code analysis techniques. Compilers , IDE‟s and developer tools can be build with static code analysis and warn the developers about possible bufferoverflow condition. For a example , the Microsoft visual studio C compiler prompt me with this message, warning C4996: 'strcpy' was declared deprecated. The compiler have warn me about using the function strcpy. Because it may lead to a buffer-overflow condition. The next static technique is using security policy procedures in the developer libraries and runtime libraries. For a example before execute the return instruction a program may call another function to ensure whether anyhow it will override the return address or not? There it can protect the integrity of the return address.For a example before returning you can see it’s calling some other stack security related functions in the disassembly listing bellow. Figure 1.4 Stack Security Calls Before Call ‘ret’
- 8. ROOTS OF EVIL: Not Enough Software Testing. Week people development teams. Two different Mindsets of Computer Hacker and a Computer Programmer Heavy usage of C compiler and stack based C programming language. REMARKS: Almost all computer platforms are using a stack. There are very few platforms and microprocessors which are not depend on a stack. Even through they are still vulnerable to the heap based overflows. There are records about top security places got hacked , including CIA, Pentagon and even Military Satiates. The ultimate security is keep the computer turned off. So ultimate security does not exists. There are three partial factors of computer security they are Confidentiality Accessibility Integrity. In theory you only can have a optimized balance on those three factors , never can achieve ultimate security. For a example if we increase the factor confidentiality then it will lead to decrease the accessibility. And when we increasing the integrity by redundancy it will affect badly on confidentiality. Summary Buffer-Overflows are Just a One class of attacks which can lead to a huge security flaw. it’s a common exploit among x86 platform because it’s huge use of stack. There are defend against this type of attacks, but the drawback is defend is limited while attack probability is not.

![Buffer Overflow Attacks
Abstract
A buffer-overflow is vulnerability in computer software that could be exploited to run arbitrary machine instructions on the microprocessor.
Almost all computing software platforms/hardware are vulnerable to this class of attack. When a malicious computer user/computer hacker or a virus
writer can exploit a typical software system and prompt it to execute arbitrary machine instructions it could use this class of attack as a virus spreading or
a virus inflection technique. Most of the computer worms [ viruses that can spread through a network medium without user intervention] are written
using this technique.
Terms and Explanation:
Computer Virology: The study about computer viruses and how it affects , what mechanisms it uses and how to defend from it are covered
under the computer virology.
Vulnerability: Vulnerability is a weakness of a particular system. For a example if your blood have low count of white cell counts then it’s said
that your vulnerable to many viruses and flu’s. The same idea exists on computing too, for a example if you won’t update your operating system
in time your computer Is vulnerable to lots of security related threats. NOTE: Every vulnerability is not a computer security weakness outside
the computer security there can be weaknesses in a particular computer system or software.
Class Of Attack: We can classify computer security vulnerabilities into classes of attacks , which clearly defines the security problem which is
related to security ,defines mechanisms and procedures exploit it and also how to defend with the problem.
Flaw: a Flaw in a computer system means a malfunction, it’s exists due to a careless Engineering. Note that every malfunction won’t be
Other Classes Of Attacks:
Buffer overflows are just only a one class of attack. And there are other classes of attacks. The bellow list defines few.
Brute Force Attacks.
SQL injection Attack.
XXS [Cross Site Scripting].
Distributed Denial Of Service. [DDos].
Smurf Attacks.
String Injection Techniques.
XML poisoning.
… and many more.
So you can clearly see there is a huge area of classifications under computer vulnerabilities. In Computer security the weakest security is equal to the
system security. So if a hacker can find any vulnerability under any classification [class ] then he can easily make the complete system security to zero.
Vulnerability : Case Study:
As I already explained vulnerability in a system means a weakness of a system which can alter the system integrity. So Let’s take a simple case study about
a vulnerability which is related to a well known operating system windows XP before the Service pack 1.Windows XP have a default screen saver and it’s
running as a background process no matter user logs in or not. When a user logs on it will run as a system process. A system process is a process which
have the highest privileges so a attack can perform critical operations including the malicious once. Since the path to the default screen saver is stored in a
register key , and a attack who logged as a non-administrator and he have the privileges to alter that register key, He could easily change the “default.scr”
to “cmd.exe” and obtain a higher privileged command prompt.](https://image.slidesharecdn.com/bufferoverflowattacks-111225081652-phpapp01/85/Buffer-overflow-attacks-1-320.jpg)
![So What’s a Bufferoverflow Attack:
As it derived from it’s name it’s something to do with a buffer, a buffer is a segment of memory which is you can store some data. Every buffer have a
bound or a limit. When a user/computer program violates the bound it’s known as a overflow. A overflow condition may end with a exception behavior or
overwriting some other data which is stored for other purpose.
Memory Exceptions:
Modern operating systems and practically with help of hardware , have implements a defense against memory violations, Memory are divided into the
segments in Modern operating systems and each segment of memory have implements flags/info how different processes can access the segment. There
are levels of access , They are known as read, write and execution privileges’. When if a process violates the privileges’ it have , the microprocessor will
generate a interrupt and transfer the control to the operating system, so the operating system can deal with it in it’s own way.
Case Study: Segmented Memory Protection
In the x86 computer platform , the modern processors above i386 have a mode called protected mode. As it name implies it’s a protected mode. It
implements the segment based memory protection.
X86 architecture have something called a “descriptor register” and it holds a address to a array of 8 bytes data structure known as segment descriptor.
When a process wants to access memory location [for a example move ax , DS:[memory_location] ] , the microprocessor do some bound checking’s with
the base address filed and segment limit field. And also checks whether it violates privileges’ using the DPL and S fields of the above data structure.
DPL : Descriptor Priviledge level.
S : System descriptor or a data or code descriptor.
^ image is scanned from the book The Intel Microprocessors Architecture ,Programming and Interfacing by Barry. B Brey.](https://image.slidesharecdn.com/bufferoverflowattacks-111225081652-phpapp01/85/Buffer-overflow-attacks-2-320.jpg)
![But Why Doesn’t That above Segmented Protection Does Not Valid Against BufferOverflows?
The above technique can only address the security between different segments, but not security inside segments. There can be several buffers stored in a
one memory segment. And nothing prevents a process having enough requested priviledgs will accessing the contents of the anywhere in the segment. In
the hardware level the smallest chunk of memory that can be protect is in the segment level. But segments are typically very large blocks of memory.
Subcategories of Bufferoverflows:
Bufferoverflow is just only a one class of attack , even it contains two different sub categories.
Stack Based Overflow.
Heap Based Overflow.
Terms And Explanation:
Stack: From the Oxford Learner’s dictionary the term “stack” is defined as “a pile of something , which usually netly arranged” [Ex-stack of
Books] . A stack is something have LIFO (last in first out) characteristic. Where you can keep books in a stack , and you can first take out the
book that you kept there last.
Heap: Heap is a area of memory where computer programs can make a request to the operating system to allocate that block of memory for
me. Large data-structures are typically stored in the heap.
Introduction To Stack Computing
In computing world , stack is a very useful data-structure. In x86 world , it’s normally implements as a whole segment. And the Stack Segment register (SS)
will keep the base address, and register (SP) Stack Pointer is keeping the memory address where it can push next data.
Stack have two operations , Push and Pop. In X86 computing world , they are implemented with machine instructions PUSH and POP. More than that basic
two instructions X86 supports some additional instructions related to stack , for a example PUSHA, POPA, ENTER , LEAVE.
Computer programs are very complex by it’s nature. As we look into It as a whole it’s sometimes beyond the human imaginary powers. So that complexity
is decomposed into modules , which is a very common engineering concept in computer software engineering. Modules are normally implemented as
functions and routines. So a large complex computer program is nothing more than a mess of functions and routines calling each other to perform a
specific goal. When you calling a routine , for a example add two numbers , you need to pass parameters to that routine as input. You can easily allocate
two Microprocessor registers to pass these values , but when the number of inputs grows you will probably need to store some stack like data structure to
store parameters. Simply the caller can push the parameters to the stack and callee can pop them back and use them.
Many callers can call a particular function or a routine. But when the function performed it’s operation it should return back to where it’s originally called.
So there should be a mechanism to store the return address of a function. So here It comes the help of stack again. The return value also stored in the
stack.
You may notice that a module may require some local variables to store it’s temporary values, they should be created and destroyed on the fly. This can be
done easily with the stack, simply you can allocate local space for local variables by subtracting the stack pointer by the number of bytes you need to
allocate. And destroy then just adding the number of bytes you allocated.
The intel x86 architecture also contains the a register called BP [base pointer] where it keeps the base address of the local variables.](https://image.slidesharecdn.com/bufferoverflowattacks-111225081652-phpapp01/85/Buffer-overflow-attacks-3-320.jpg)
![A typical stack frame of a stack frame is illustrated in the bellow picture.with it’s disassembly. And you can see that.
Figure 1.1 dissassembly for the program .
#include <stdio.h>
Void function(int a, int b)
{
int var1;
int var2;
char buffer[200];
scanf(“%s”,buffer);
// do some computations //
Return;
}
Program Listing 1.2](https://image.slidesharecdn.com/bufferoverflowattacks-111225081652-phpapp01/85/Buffer-overflow-attacks-4-320.jpg)
![So How It Works ?
In the previous pages, I have explained how the stack operates and now you have a good technical understanding how functions are calling and how the
stack frame is working. But how it affects.
To that let me write a small program as I also illustrated in figure 1.2 for you. It take 2 int parameters as inputs , and create another two int‟s as local
variables and a big char array of size 200.
And the address to that char array is passed to the scanf() function as a buffer to take some user input.. It won‟t matter if user enters a input string of 200 or
less characters, but what will happen when it‟s 201 characters. Then it will go beyond it and override some part of the „int val2‟ variable. Like this a one can
easily override up to the return address too. Which will alter the value of the return address due to a user input. This is a dangours thing , because all the
users who are using this application are not 100% pure genuine users. So for them they have a possibility to alter the return address to a arbitrary value of
their choice.[note the big red arrow of Figure 1.3]
and in the worst thing is not only a user can alter the return address, and return. He can easily inject some arbitrary instructions to the buffer and manipulate
the return address to return back to there. In that way a malicious computer user can easily execute arbitrary instructions.
So What‟s The Fancy Thing About This Buffer?
If the user of the computer system also the owner then it won‟t affect. But Suppose in a case of a internet HTTP server or a bank teller machine. There are
places where it uses lots of buffers in those places , for a example in HTTP server packet may stored in a buffer, in that case if a hacker found some buffer
overflow vulnerability in the server he may use it to execute the machine instructions in somebody‟s else‟s computer. In the case of bank teller , the key card
contains some data structure to tell to the bank about the user. What if a hacker able to found a overflow condition of that buffers? He an easily bypass all the
security and made the system to call a function that throws money out of his choice.
More than the above extremely high illegal things , ppl do use to write viruses using this technique. Probably the network worms. where you it don‟t need
any user intervention to spread over the internet. Not only computers , they can be engineered to inflect to network routers . There was a worm that
threatened the whole internet by attacking the root name servers in the internet. Fortunately computer virus researches have identified it‟s code structure and
block it before inflecting all the 13 name servers, it was a real risk and everybody at that time believed that it‟s the end of the whole internet.
Another worm that kept a history record is , Code Red worm. It was engineered to inflect Microsoft IIS server.
Defend Against Buffer-Overflow Attacks
Even through the computing and internet is a hostile place, we can‟t live without it. Businesses to the Missile control systems are all depends on the internet
and the computing. So we probably have to find a well suitable defend against.
There are hardware and software techniques to defend against buffer overflows.
Hardware Techniques:
As I already explained a segmented memory addressing is a one way of keeping memory safe. But it won‟t affect someone will violate a memory bound
inside a segment. However you can say “please do not execute on stack segment” to the microprocessor. Modern day microprocessors have implemented a
feature called DEP [data execution presentation], to avoid stack based and heap based buffer overflows. It‟s nothing more than just a flag, where enabling
that flag , and if the segment is marked as a data segment in the descriptor and if you tried to execute on it, it will simply throw a exception and pass the
control to the operating system [ exception handler].
Terms And Explanations:
Exception handler: Exceptions are thrown when there is unrecoverable error occurred in a computer system. For a example divide by zero ,or a
memory violation.
It was implemented on the hardware level , where you also could throw exceptions using the interrupt mechanism. There is a link list
called SEH Standard Exception Handler , where every module have a address to a exception handling routine and also keeps the address to the
previous exception handler. Typically when a exception handler function is called , it will dump memory , log the status or do something like
that to help someone who need to fix the program.](https://image.slidesharecdn.com/bufferoverflowattacks-111225081652-phpapp01/85/Buffer-overflow-attacks-6-320.jpg)

