Developing Secure Apps
Download as PPTX, PDF0 likes94 views
This document discusses the importance of developing secure mobile applications. It outlines best practices for secure app development, including implementing secure coding practices, encrypting sensitive data, and conducting security testing. The document also discusses the role of user education and awareness in overall app security. Developing secure apps is essential to protect user data, maintain trust with users, and prevent security breaches and data leaks.
1 of 26
Download to read offline

























Ad
Recommended
How to Ensure Security in Software Application Development.pdf



How to Ensure Security in Software Application Development.pdfhimanshuwowit In today’s fast-evolving digital landscape, ensuring security in software application development is more critical than ever.
Secure Enterprise App Development_ Best Practices.pdf



Secure Enterprise App Development_ Best Practices.pdfEwenjlin Smith This article explores key security practices for enterprise apps and highlights how partnering with a mobile app development company in USA can help implement effective security solutions.
Discuss Best Practices for Integrating Security Measures into Mobile App Deve...



Discuss Best Practices for Integrating Security Measures into Mobile App Deve...IPH Technologies This comprehensive blog explores the imperative need for robust security measures in mobile app development, particularly concerning safeguarding user data. It discusses the escalating importance of mobile app security, outlines common threats, and emphasizes the consequences of poor security practices. The blog delineates best practices across various facets of secure development, including coding, data encryption, authentication, and API security. Additionally, it underscores the significance of user education, compliance with data protection regulations, collaboration with security experts, and learning from case studies. The conclusion emphasizes the necessity of proactive security measures and continuous adaptation to evolving threats in the digital landscape.
Importance Of Testing Mobile Apps For Security Vulnerabilities.pdf



Importance Of Testing Mobile Apps For Security Vulnerabilities.pdfpcloudy2 In today’s hyper-connected world, mobile applications have become an integral part of our daily lives, serving as gateways to a myriad of services and functionalities.
Best Practices for Secure Web Application Development by Site Invention.pdf



Best Practices for Secure Web Application Development by Site Invention.pdfsiteseo In the era of digital transformation, web applications have become an essential part of business operations. However, there is a greater chance of security breaches as web apps become more and more reliant upon. This comprehensive guide will explore the best practices for secure web application development, with insights specifically tailored for web application development in Mumbai by the leading experts at Site Invention.
Mobile App Security_ Best Practices to Protect Your App.pdf



Mobile App Security_ Best Practices to Protect Your App.pdfRahimMakhani2 It has become important to implement strong security measures for developers with the increasing use of mobile. This introduction applies the base for understanding the difficulties and challenges associated with assuring mobile applications against a backdrop of complex cyber threats.
Best Practices for Mobile App Security.docx



Best Practices for Mobile App Security.docxAppinnovix Technologies Prioritizing mobile app security is not just a technical requirement; it’s a commitment to your users' trust and privacy. Collaborating with a mobile app development agency that understands these best practices can help ensure that your app is not only functional but also secure. By adopting these strategies, you can protect your app and its users from potential threats.
Security-First Development_ Safeguarding Your Software from Threats.pdf



Security-First Development_ Safeguarding Your Software from Threats.pdfTyrion Lannister This article delves into the concept of security-first development and offers insights into how it can effectively safeguard software from a wide range of threats.
Security in Mobile App Development Protecting User Data and Preventing Cybera...



Security in Mobile App Development Protecting User Data and Preventing Cybera...madhuri871014 In the era of digitalization, mobile apps have become an integral part of our daily lives. From banking and shopping to social networking and entertainment, we rely on mobile apps for convenience and accessibility. However, with the increase in cyber threats and data breaches, ensuring the security of user data has become a paramount concern for both app developers and users.
A Comprehensive Guide to Mobile Application Penetration Testing



A Comprehensive Guide to Mobile Application Penetration TestingMobile Security Mobile applications have become an integral part of our daily lives, from banking and e-commerce to social networking and entertainment. With their growing prominence, they have also become prime targets for cyberattacks. Mobile application penetration testing is a critical process for ensuring the security and resilience of these apps against potential threats.
Mobile App Security Protecting Your App from Cyber Threats.edited.docx



Mobile App Security Protecting Your App from Cyber Threats.edited.docxmadhuri871014 This has the potential to deceive individuals into downloading the mobile app to obtain absolutely nothing and enable the provider another opportunity to turn individuals into loyal customers. The use of in-app advertising is another prevalent strategy that lets you showcase relevant advertisements from within the application.
Boosting IoT Protection: An Enterprise Risk Imperative



Boosting IoT Protection: An Enterprise Risk ImperativeNational Retail Federation The document discusses the risks of IoT devices and the need for improved security practices. It notes that many applications contain inherited vulnerabilities from reused components and fail to meet basic security standards. The document outlines UL's new 2900 security certification for network-connected products which evaluates vendors' risk management processes and requires documentation of a product's design, use, vulnerabilities, and security controls.
Secure Software Development: Best practice and strategies.pdf



Secure Software Development: Best practice and strategies.pdfNexflare Dynamics In a world where cyber threats are constantly evolving, secure software development is not just an option—it’s a necessity. Building secure applications from the ground up ensures that sensitive data remains protected, systems remain resilient, and users can trust your software. This blog delves into the essentials of secure software development, highlighting its importance, best practices, and actionable strategies.
What are security considerations for mobile app development? MAE



What are security considerations for mobile app development? MAEmobile app experts India Our company Mobile App Experts India is the best mobile app development company in India We understand very well how important security is. We incorporate these security considerations throughout the entire development lifecycle from starting design and development to ongoing maintenance support.
Mobile Apps Security Testing -1



Mobile Apps Security Testing -1Krisshhna Daasaarii Mobile application security testing is important to identify vulnerabilities and protect sensitive user data. The key concepts of mobile app security testing include authentication, authorization, availability, confidentiality, integrity and non-repudiation. Common mobile security threats include malware, spyware, privacy threats and vulnerable applications. Effective security testing employs strategies like strong authentication, encryption, access control and session management. The testing methodology involves profiling the app, analyzing threats, planning tests, executing tests, and providing daily status reports. Deliverables include management reports, technical vulnerability reports, and best practices documents.
HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdf



HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdfasiyahanif9977 In today’s Graphic Design in the UAE age, where the internet and mobile applications have become an integral part of our lives, ensuring User Data Security has become paramount.
HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdf



HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdfasiyahanif9977 https://nexusbeez.com/
In today’s Graphic Design in UAE age, where the internet and mobile applications have become an integral part of our lives, ensuring User Data Security has become paramount.
Mobile App Security: Essential Guide to Protecting Your App and Data



Mobile App Security: Essential Guide to Protecting Your App and DataScalaCode Learn everything you need to know about mobile app security in our comprehensive guide. Discover key strategies to protect your app from vulnerabilities, secure sensitive data, and prevent cyber threats. From encryption and authentication to best practices for secure app development, we cover all essential aspects of mobile app security. Ensure your app provides a safe, reliable user experience while maintaining compliance with industry standards. Stay ahead of potential risks and safeguard your mobile app with expert security insights.
In-App Protection for High-Value Applications_ Strategies for Enhanced Securi...



In-App Protection for High-Value Applications_ Strategies for Enhanced Securi...GargiBen In-App Protection offerings continue to strengthen their value proposition by significantly investing in enhancing capabilities such as prevention, detection, anti-bot, clickjacking, runtime application self-protection, multifactor authentication, risk analysis, and more.
Top 10 Important Thing for Developing a Mobile App| MAE



Top 10 Important Thing for Developing a Mobile App| MAEmobile app experts India Our company Mobile App Experts India is the best mobile app development company in India We understand very well how important security is. We incorporate these security considerations throughout the entire development lifecycle from starting design and development to ongoing maintenance support.
Application Security 101_ Protecting Software from Cyber Threats.pdf



Application Security 101_ Protecting Software from Cyber Threats.pdfaashinn15 In today’s digital landscape, the increasing complexity and dependency on software applications have made them prime targets for cyber threats. With businesses shifting toward more digital-first strategies, safeguarding the software they develop and deploy has never been more important. This is where Application Security (AppSec) and Application Security Posture Management (ASPM) come into play. In this article, we will explore the significance of application security, how to manage your application's security posture, and the tools and strategies businesses can adopt to stay ahead of cybercriminals.
Source- https://blogosm.com/application-security-101-protecting-software-from-cyber-threats
Top 6 Web Application Security Best Practices.pdf



Top 6 Web Application Security Best Practices.pdfSolviosTechnology Want to know how to secure your web apps from cyber-attacks? Looking to know the Best Web Application Security Best Practices? Check this article, we delve into six essential web application security best practices that are important for safeguarding your web applications and preserving the sanctity of your valuable data.
How to Secure Your Mobile App from Cyber Threats.pdf



How to Secure Your Mobile App from Cyber Threats.pdfRajmith Mobile apps have become a vital part of our existence throughout the course of the day, especially in the banking, shopping, and social networking realms. The mobile applications have scaled up the interaction between man and the world. With increased usage of mobile apps, there grow values of cyber threats in it. Protection for your mobile app against cyber threats is no more optional-it is a must.
building-a-secure-medical-app-with-dot-net.pdf



building-a-secure-medical-app-with-dot-net.pdfPixelQA In today's digital age, mobile applications have become invaluable tools for patients, healthcare experts, and related institutions medical applications can maintain patient care through improved efficiency and access significantly.
Data Security in Mobile App Development_ Importance and Strategies (1).pdf



Data Security in Mobile App Development_ Importance and Strategies (1).pdfRahimMakhani2 Data security is important in mobile app development, as applications often regulate liable user information.
Mobile App Security How Bahrain Development Companies Ensure Protection.edite...



Mobile App Security How Bahrain Development Companies Ensure Protection.edite...madhuri871014 Mobile apps have become integral to our daily lives. From ordering food and booking rides to managing finances and staying connected with loved ones, there seems to be an app for everything. Behind the scenes, however, a technological revolution is taking place, completely transforming the way mobile apps are developed. The introduction of artificial intelligence (AI) and machine learning has brought about a paradigm shift in the app development process, enhancing efficiency, personalization, and user experience like never before.
Selecting an App Security Testing Partner: An eGuide



Selecting an App Security Testing Partner: An eGuideHCLSoftware In the age of digital transformation, global businesses leverage web application scanning tools to shape innovative employee cultures, business processes, and customer experiences. The surge in remote work, cloud computing, and online services unveils unprecedented vulnerabilities and threats.
Learn more: https://hclsw.co/ftpwvz
Procuring an Application Security Testing Partner



Procuring an Application Security Testing PartnerHCLSoftware Procuring an Application Security Testing Partner is crucial for safeguarding digital assets. An Application Security Testing Partner specializes in conducting comprehensive assessments using keywords like vulnerability scanning, penetration testing, code review, and threat modeling. Their expertise ensures your applications are fortified against cyber threats, providing peace of mind in an increasingly interconnected digital landscape.
Learn More: https://hclsw.co/ftpwvz
Web Performance Optimization



Web Performance OptimizationLivares Technologies Pvt Ltd Pragathi Technical Session
'Web Performance Optimization'
By, Athira Vinod
Pragathi - Tech & Socio Cultural Activity Group Livares Technologies
#livares #pragathi #technicalsession #technology #technicaldiscussion #WebPerformanceOptimization
Supervised Machine Learning



Supervised Machine LearningLivares Technologies Pvt Ltd Supervised machine learning uses labeled training data to build models that can predict outputs. There are two main types: regression predicts continuous variables, while classification predicts categorical variables. Supervised learning algorithms include linear regression, which finds a linear relationship between variables, and logistic regression or decision trees for classification. The process involves collecting labeled data, training an algorithm on part of the data, and evaluating its accuracy on test data.
Ad
More Related Content
Similar to Developing Secure Apps (20)
Security in Mobile App Development Protecting User Data and Preventing Cybera...



Security in Mobile App Development Protecting User Data and Preventing Cybera...madhuri871014 In the era of digitalization, mobile apps have become an integral part of our daily lives. From banking and shopping to social networking and entertainment, we rely on mobile apps for convenience and accessibility. However, with the increase in cyber threats and data breaches, ensuring the security of user data has become a paramount concern for both app developers and users.
A Comprehensive Guide to Mobile Application Penetration Testing



A Comprehensive Guide to Mobile Application Penetration TestingMobile Security Mobile applications have become an integral part of our daily lives, from banking and e-commerce to social networking and entertainment. With their growing prominence, they have also become prime targets for cyberattacks. Mobile application penetration testing is a critical process for ensuring the security and resilience of these apps against potential threats.
Mobile App Security Protecting Your App from Cyber Threats.edited.docx



Mobile App Security Protecting Your App from Cyber Threats.edited.docxmadhuri871014 This has the potential to deceive individuals into downloading the mobile app to obtain absolutely nothing and enable the provider another opportunity to turn individuals into loyal customers. The use of in-app advertising is another prevalent strategy that lets you showcase relevant advertisements from within the application.
Boosting IoT Protection: An Enterprise Risk Imperative



Boosting IoT Protection: An Enterprise Risk ImperativeNational Retail Federation The document discusses the risks of IoT devices and the need for improved security practices. It notes that many applications contain inherited vulnerabilities from reused components and fail to meet basic security standards. The document outlines UL's new 2900 security certification for network-connected products which evaluates vendors' risk management processes and requires documentation of a product's design, use, vulnerabilities, and security controls.
Secure Software Development: Best practice and strategies.pdf



Secure Software Development: Best practice and strategies.pdfNexflare Dynamics In a world where cyber threats are constantly evolving, secure software development is not just an option—it’s a necessity. Building secure applications from the ground up ensures that sensitive data remains protected, systems remain resilient, and users can trust your software. This blog delves into the essentials of secure software development, highlighting its importance, best practices, and actionable strategies.
What are security considerations for mobile app development? MAE



What are security considerations for mobile app development? MAEmobile app experts India Our company Mobile App Experts India is the best mobile app development company in India We understand very well how important security is. We incorporate these security considerations throughout the entire development lifecycle from starting design and development to ongoing maintenance support.
Mobile Apps Security Testing -1



Mobile Apps Security Testing -1Krisshhna Daasaarii Mobile application security testing is important to identify vulnerabilities and protect sensitive user data. The key concepts of mobile app security testing include authentication, authorization, availability, confidentiality, integrity and non-repudiation. Common mobile security threats include malware, spyware, privacy threats and vulnerable applications. Effective security testing employs strategies like strong authentication, encryption, access control and session management. The testing methodology involves profiling the app, analyzing threats, planning tests, executing tests, and providing daily status reports. Deliverables include management reports, technical vulnerability reports, and best practices documents.
HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdf



HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdfasiyahanif9977 In today’s Graphic Design in the UAE age, where the internet and mobile applications have become an integral part of our lives, ensuring User Data Security has become paramount.
HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdf



HOW TO SECURE WEB AND APP DEVELOPMENT USER DATA SECURITY.pdfasiyahanif9977 https://nexusbeez.com/
In today’s Graphic Design in UAE age, where the internet and mobile applications have become an integral part of our lives, ensuring User Data Security has become paramount.
Mobile App Security: Essential Guide to Protecting Your App and Data



Mobile App Security: Essential Guide to Protecting Your App and DataScalaCode Learn everything you need to know about mobile app security in our comprehensive guide. Discover key strategies to protect your app from vulnerabilities, secure sensitive data, and prevent cyber threats. From encryption and authentication to best practices for secure app development, we cover all essential aspects of mobile app security. Ensure your app provides a safe, reliable user experience while maintaining compliance with industry standards. Stay ahead of potential risks and safeguard your mobile app with expert security insights.
In-App Protection for High-Value Applications_ Strategies for Enhanced Securi...



In-App Protection for High-Value Applications_ Strategies for Enhanced Securi...GargiBen In-App Protection offerings continue to strengthen their value proposition by significantly investing in enhancing capabilities such as prevention, detection, anti-bot, clickjacking, runtime application self-protection, multifactor authentication, risk analysis, and more.
Top 10 Important Thing for Developing a Mobile App| MAE



Top 10 Important Thing for Developing a Mobile App| MAEmobile app experts India Our company Mobile App Experts India is the best mobile app development company in India We understand very well how important security is. We incorporate these security considerations throughout the entire development lifecycle from starting design and development to ongoing maintenance support.
Application Security 101_ Protecting Software from Cyber Threats.pdf



Application Security 101_ Protecting Software from Cyber Threats.pdfaashinn15 In today’s digital landscape, the increasing complexity and dependency on software applications have made them prime targets for cyber threats. With businesses shifting toward more digital-first strategies, safeguarding the software they develop and deploy has never been more important. This is where Application Security (AppSec) and Application Security Posture Management (ASPM) come into play. In this article, we will explore the significance of application security, how to manage your application's security posture, and the tools and strategies businesses can adopt to stay ahead of cybercriminals.
Source- https://blogosm.com/application-security-101-protecting-software-from-cyber-threats
Top 6 Web Application Security Best Practices.pdf



Top 6 Web Application Security Best Practices.pdfSolviosTechnology Want to know how to secure your web apps from cyber-attacks? Looking to know the Best Web Application Security Best Practices? Check this article, we delve into six essential web application security best practices that are important for safeguarding your web applications and preserving the sanctity of your valuable data.
How to Secure Your Mobile App from Cyber Threats.pdf



How to Secure Your Mobile App from Cyber Threats.pdfRajmith Mobile apps have become a vital part of our existence throughout the course of the day, especially in the banking, shopping, and social networking realms. The mobile applications have scaled up the interaction between man and the world. With increased usage of mobile apps, there grow values of cyber threats in it. Protection for your mobile app against cyber threats is no more optional-it is a must.
building-a-secure-medical-app-with-dot-net.pdf



building-a-secure-medical-app-with-dot-net.pdfPixelQA In today's digital age, mobile applications have become invaluable tools for patients, healthcare experts, and related institutions medical applications can maintain patient care through improved efficiency and access significantly.
Data Security in Mobile App Development_ Importance and Strategies (1).pdf



Data Security in Mobile App Development_ Importance and Strategies (1).pdfRahimMakhani2 Data security is important in mobile app development, as applications often regulate liable user information.
Mobile App Security How Bahrain Development Companies Ensure Protection.edite...



Mobile App Security How Bahrain Development Companies Ensure Protection.edite...madhuri871014 Mobile apps have become integral to our daily lives. From ordering food and booking rides to managing finances and staying connected with loved ones, there seems to be an app for everything. Behind the scenes, however, a technological revolution is taking place, completely transforming the way mobile apps are developed. The introduction of artificial intelligence (AI) and machine learning has brought about a paradigm shift in the app development process, enhancing efficiency, personalization, and user experience like never before.
Selecting an App Security Testing Partner: An eGuide



Selecting an App Security Testing Partner: An eGuideHCLSoftware In the age of digital transformation, global businesses leverage web application scanning tools to shape innovative employee cultures, business processes, and customer experiences. The surge in remote work, cloud computing, and online services unveils unprecedented vulnerabilities and threats.
Learn more: https://hclsw.co/ftpwvz
Procuring an Application Security Testing Partner



Procuring an Application Security Testing PartnerHCLSoftware Procuring an Application Security Testing Partner is crucial for safeguarding digital assets. An Application Security Testing Partner specializes in conducting comprehensive assessments using keywords like vulnerability scanning, penetration testing, code review, and threat modeling. Their expertise ensures your applications are fortified against cyber threats, providing peace of mind in an increasingly interconnected digital landscape.
Learn More: https://hclsw.co/ftpwvz
More from Livares Technologies Pvt Ltd (20)
Web Performance Optimization



Web Performance OptimizationLivares Technologies Pvt Ltd Pragathi Technical Session
'Web Performance Optimization'
By, Athira Vinod
Pragathi - Tech & Socio Cultural Activity Group Livares Technologies
#livares #pragathi #technicalsession #technology #technicaldiscussion #WebPerformanceOptimization
Supervised Machine Learning



Supervised Machine LearningLivares Technologies Pvt Ltd Supervised machine learning uses labeled training data to build models that can predict outputs. There are two main types: regression predicts continuous variables, while classification predicts categorical variables. Supervised learning algorithms include linear regression, which finds a linear relationship between variables, and logistic regression or decision trees for classification. The process involves collecting labeled data, training an algorithm on part of the data, and evaluating its accuracy on test data.
Software Architecture Design



Software Architecture DesignLivares Technologies Pvt Ltd Pragathi Technical Session
'Software Architecture Design''
By, Rineez Ahmed N @rineezahmed
Chief Technology Officer, Livares Technologies Pvt Ltd
Pragathi - Tech & Socio Cultural Activity Group Livares Technologies
#pragathi #livares #softwarearchitecture #softwarearchitecturedesign #technicalsession #technopark
Automation using Appium



Automation using AppiumLivares Technologies Pvt Ltd Pragathi Technical Session
'Automation using Appium'
By, Adarsh S Anil
Pragathi - Tech & Socio Cultural Activity Group Livares Technologies
#pragathi #livares #automatedtesting #technicalsession #technopark
Bubble(No code Tool)



Bubble(No code Tool)Livares Technologies Pvt Ltd Pragathi Technical Session
'Bubble - No Code Development'
By, Arya T S
Pragathi - Tech & Socio Cultural Activity Group Livares Technologies
Unsupervised Machine Learning



Unsupervised Machine LearningLivares Technologies Pvt Ltd Pragathi Technical Session
'Unsupervised Machine Learning'
By, Rateesh Babu
Pragathi - Tech & Socio Cultural Activity Group Livares Technologies
Micro-Frontend Architecture



Micro-Frontend ArchitectureLivares Technologies Pvt Ltd The document discusses micro-frontend architecture, which divides the frontend UI into smaller, semi-independent applications. It covers the core ideas like technological independence and faster development. Integration approaches include server-side templates, build-time integration using packages, and runtime integration with iframes or JavaScript. Challenges include complexity, coordination, and performance, which can be overcome with standardization and DevOps practices. Popular companies using microfrontends are IKEA, Upwork, and Spotify.
Apache J meter



Apache J meterLivares Technologies Pvt Ltd Presented by,
Ms. Anjali K G
Quality Assurance Engineer, Livares Technologies
Java open source desktop application
Designed to analyze and measure performance of web applications
JMeter has friendly GUI
Platform independent
Full multithreading framework
Visualize test result
Easy installation
Support multi protocol
Record and play back
Can be integrated with selenium for automated testing
Introduction to Angular JS



Introduction to Angular JSLivares Technologies Pvt Ltd This document provides an introduction to Angular JS, including its features and architecture. Angular JS is a front end JavaScript framework that uses MVC architecture. It allows for code organization, increases productivity, and has features like data binding and built-in unit testing. The core components of Angular include modules, components, and services. Modules provide context and organization. Components define views using templates. Services define application logic and data. Routing is also covered, allowing navigation between different views and paths.
An Insight into Quantum Computing



An Insight into Quantum ComputingLivares Technologies Pvt Ltd This document provides an overview of quantum computing. It discusses how quantum computing takes advantage of quantum mechanics to perform calculations exponentially faster than classical computers. Some key topics covered include the need for quantum computers to solve optimization and machine learning problems, basic concepts like qubits and quantum gates, as well as recent achievements in building quantum computers with over 50 qubits. The document also notes some current limitations like the challenges of maintaining quantum states and the need to isolate systems from noise.
Just in Time (JIT)



Just in Time (JIT)Livares Technologies Pvt Ltd The document discusses the philosophy and principles of Just-in-Time (JIT) manufacturing. It describes how JIT originated in Japan after WWII to maximize efficient use of limited resources. Toyota was an early adopter of JIT in the 1970s. The key aspects of JIT are eliminating waste and continuous process improvement by producing only what is needed when it is needed with perfect quality and minimal lead times. JIT aims to reduce setup times, inventory levels, and transportation. While reducing costs, it also increases responsiveness and quality but requires strong supplier relationships and commitment to be effective long-term.
Introduction to Bitcoin 



Introduction to Bitcoin Livares Technologies Pvt Ltd Bitcoin is a decentralized digital currency that was created in 2009. It functions without a central bank or single administrator through a peer-to-peer network and blockchain technology. Bitcoin is mined through the use of computer processing power to verify transactions and add them to the blockchain. Miners are rewarded with newly minted bitcoins and transaction fees for their work maintaining the integrity of the blockchain. There will only ever be 21 million bitcoins created as the block reward gets cut in half approximately every four years.
Data Mining Technniques



Data Mining TechnniquesLivares Technologies Pvt Ltd Presented by,
Mr. Blesson Joseph
Senior Software Engineer, Livares Technologies
What is data mining?
Data mining is the process of analyzing data and summarizing it to produce useful information.
Queries based on SQL, a database programming language, are used to answer basic questions about data.
But, as the collection of data grows in a database, the amount of data can easily become overwhelming.
A data warehouse is a collection of databases that work together. A data warehouse makes it possible to integrate data from multiple databases, which can give new insights into the data.
The ultimate goal of a database is not just to store data, but to help businesses make decisions based on that data.
Goal of Data Mining
The overall goal of the data mining
process is to extract information from a
data set and transform it into an
understandable structure for further use.
Data mining is the computing process of
discovering patterns in large data sets
involving methods.
These patterns can be used for predictive
analytics.
Facade Design Pattern



Facade Design PatternLivares Technologies Pvt Ltd Presented by,
Ms. Nandana S V
Team Lead, Sr Software Engineer, Livares Technologies
Facade design pattern
Facade is a part of Gang of Four design pattern (23 others).
As the name suggests, it means the face of the building.
The people walking past the road can only see this glass face of the building.
They do not know anything about it, the wiring, the pipes and other complexities.
It hides all the complexities of the building and displays a friendly face.
Facade design pattern
Same goes for the Facade Design Pattern. It hides the complexities of the system and provides an interface to the client from where the client can access the system.
Manual Vs Automation Testing



Manual Vs Automation TestingLivares Technologies Pvt Ltd Presented by,
Ms. Anjali K G
Quality Assurance Engineer, Livares Technologies
Manual Testing: Process of testing an application
manually for defects. It requires a tester to play the role
of an end user
Automation Testing: It is technique by using special
software to control the execution of tests and the
comparison of actual results with predicted results
Testing tools Ex: QTP, Winrunner, Selenium etc
Screenless display



Screenless displayLivares Technologies Pvt Ltd Presented by Mr. Arunsankar S
Sr Software Developer, Livares Technologies
What is screen-less display?
Screen-less display is the present evolving technology in the field of the computer-enhanced technologies.
It is going to be the one of the greatest technological development in the future years.
Several patents are still working on this new emerging technology which can change the whole spectacular view
of the screen-less displays.
Screen-less display technology has the main aim of displaying (or) transmitting the information without any help
of the screen (or) the projector.
Screen-less videos describe systems for transmitting visual information from a video source without the use of
the screen.
Database Overview



Database OverviewLivares Technologies Pvt Ltd Presented by,
Mr. Abhilash K
Database Architect, Livares Technologies
Introduction
About DBMS
A database management system (DBMS) is a software for
creating and managing databases. DBMS provides
users/programmers with a systematic way to create,
retrieve, update and manage data.
What is RDBMS
A type of DBMS in which the database is organized and
accessed according to the relationships between data
values. RDBMS are designed to take care of large amounts
of data and also the security of this data
An Introduction to Machine Learning



An Introduction to Machine LearningLivares Technologies Pvt Ltd 1. The document provides an introduction to machine learning, explaining how it works through examples of classifying songs based on an individual's music tastes and recognizing friends in tagged photos.
2. Key machine learning concepts are defined, including supervised learning, unsupervised learning, and generative adversarial networks (GANs). Examples are given of applications like recommending new songs, detecting credit card fraud, and generating fake images.
3. The popularity of machine learning is attributed to the huge amounts of data now available for training models, and examples are given of how Uber and other companies use machine learning applications in areas like predictive modeling.
An Introduction to Face Detection



An Introduction to Face DetectionLivares Technologies Pvt Ltd Presented by Mr. Dinesh KS
Software Developer, Livares Technologies
Introduction
Object detection is a computer technology related to computer vision and image processing that
deals with detecting instances of semantic objects of a certain class (such as humans, buildings, or
cars) in digital images and videos.
Face detection is a computer technology being used in a variety of applications that identifies
human faces in digital images.
Smart water meter solutions using LoRa WAN - Troncart



Smart water meter solutions using LoRa WAN - TroncartLivares Technologies Pvt Ltd Smart Water Distribution Management System
Water Meter + Automated Meter Reading (AMR) + Advanced Metering Infrastructure (AMI)
Smart Water Meter, a flagship product of Troncart an
IoT & Embedded System service provider co-founded by
Livares Technologies Pvt Ltd and Tachlog Pvt Ltd.
Ad
Recently uploaded (20)
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
How Can I use the AI Hype in my Business Context?



How Can I use the AI Hype in my Business Context?Daniel Lehner 𝙄𝙨 𝘼𝙄 𝙟𝙪𝙨𝙩 𝙝𝙮𝙥𝙚? 𝙊𝙧 𝙞𝙨 𝙞𝙩 𝙩𝙝𝙚 𝙜𝙖𝙢𝙚 𝙘𝙝𝙖𝙣𝙜𝙚𝙧 𝙮𝙤𝙪𝙧 𝙗𝙪𝙨𝙞𝙣𝙚𝙨𝙨 𝙣𝙚𝙚𝙙𝙨?
Everyone’s talking about AI but is anyone really using it to create real value?
Most companies want to leverage AI. Few know 𝗵𝗼𝘄.
✅ What exactly should you ask to find real AI opportunities?
✅ Which AI techniques actually fit your business?
✅ Is your data even ready for AI?
If you’re not sure, you’re not alone. This is a condensed version of the slides I presented at a Linkedin webinar for Tecnovy on 28.04.2025.
Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...



Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...Noah Loul Artificial intelligence is changing how businesses operate. Companies are using AI agents to automate tasks, reduce time spent on repetitive work, and focus more on high-value activities. Noah Loul, an AI strategist and entrepreneur, has helped dozens of companies streamline their operations using smart automation. He believes AI agents aren't just tools—they're workers that take on repeatable tasks so your human team can focus on what matters. If you want to reduce time waste and increase output, AI agents are the next move.
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...



IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...organizerofv IEDM 2024 Tutorial2
Big Data Analytics Quick Research Guide by Arthur Morgan



Big Data Analytics Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
Drupalcamp Finland – Measuring Front-end Energy Consumption



Drupalcamp Finland – Measuring Front-end Energy ConsumptionExove How to measure web front-end energy consumption using Firefox Profiler. Presented in DrupalCamp Finland on April 25th, 2025.
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
Ad
Developing Secure Apps
- 1. DEVELOPING SECURE APPS Presented By Nandana SV Livares Technologies Pvt Ltd Tech & Socio-Cultural Group
- 2. Developing Secure Apps : Overview App security is of paramount importance in today's digital landscape, where mobile applications handle ● sensitive user information ● perform critical functions. Without proper security measures, apps are vulnerable to attacks, data breaches, and unauthorized access. Therefore, developers must prioritize app security to protect user data and maintain user trust.
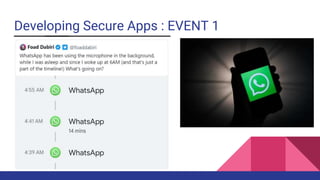
- 3. Developing Secure Apps : EVENT 1
- 4. Developing Secure Apps : EVENT 2
- 5. Developing Secure Apps : EVENT 3
- 6. Importance of App security ● Protecting User Data ● Preventing Data Breaches ● Building User Trust
- 7. Why App Security Matters 1. Growing Frequency 2. Diverse Range of Threats 3. Targeting Organizations 4. Financial Impacts 5. Personal Data Exposures 6. Reputational Damage 7. Regulatory and Legal Ramifications 8. Evolving Attack Techniques 9. Supply Chain Vulnerabilities 10. Increased Awareness and Preparedness
- 8. Common App Security Vulnerabilities 1. Injection Attacks - SQL Injection, Command Injection, Cross-Site Scripting (XSS) 2. Cross-Site Request Forgery (CSRF) 3. Insecure Direct Object References (IDOR) 4. Security Misconfigurations 5. Broken Authentication and Session Management 6. Insecure Data Storage 7. Buffer overflow
- 9. Common App Security Vulnerabilities 8. XML External Entity (XXE) Attacks 9. Insecure Third-Party Integrations 10. Inadequate Error Handling 11. Mobile-specific Vulnerabilities 12. DoS & DDoS 13. Local file inclusion (LFI) and Path traversal
- 10. Secure Development Lifecycle (SDL) The Secure Development Lifecycle (SDL) is a methodology used in software development to integrate security practices throughout the entire software development process. The primary goal of SDL is to create software that is secure by design and resilient to potential threats.
- 11. Secure Development Lifecycle (SDL) 1. Requirements and Design 2. Threat Modeling 3. Secure Coding / Code review 4. Testing 5. Deployment and Maintenance 6. Response and Recovery
- 12. Secure Development Lifecycle (SDL) SDL is an iterative process that emphasizes continuous improvement and learning from security incidents and evolving threats. It aims to build security into the software development lifecycle from the outset rather than treating it as an afterthought. By integrating security practices throughout the development process, SDL helps organizations create more secure and resilient software products.
- 13. Best Practices for Secure App Development Secure app development involves implementing a set of best practices to ensure that the applications being developed are robust against potential security threats. Here are some key best practices for secure app development: 1. Use Secure Coding Practices 2. Implement Strong Authentication and Authorization 3. Encrypt Sensitive Data 4. Regularly Update and Patch Software 5. Validate and Sanitize Input
- 14. Best Practices for Secure App Development 6. Follow the Principle of Least Privilege 7. Implement Secure Communication 8. Conduct Regular Security Testing 9. Handle Errors and Exceptions Securely 10. Educate and Train Developers 11. Implement Security Monitoring and Incident Response: 12. Regularly Review and Update Security Practices
- 15. Data Privacy and Compliance 1. Respect for User Rights 2. Obtaining User Consent 3. Secure Data Handling 4. Transparent Privacy Policies 5. Data Minimization and Purpose Limitation 6. Data Subject Rights Management 7. International Data Transfers 8. Consequences of Non-Compliance
- 16. Testing and Security Audits 1. Penetration Testing 2. Vulnerability Scanning 3. Code Review 4. Security Architecture Review 5. Security Testing for APIs 6. Security Regression Testing
- 17. User Education and Awareness 1. Recognizing Phishing and Social Engineering Attacks 2. Creating Strong Passwords and Enforcing Two-Factor Authentication 3. Understanding App Permissions 4. Regular Software Updates 5. Safe Internet and Wi-Fi Usage 6. Data Backup and Secure Storage 7. Reporting Security Incidents 8. Privacy Awareness 9. Social Media Security
- 18. Bug Bounty programs A bug bounty program, also known as a vulnerability rewards program (VRP), offers rewards to individuals for uncovering and reporting software bugs. As part of a vulnerability management strategy, these crowdsourcing initiatives are often used by companies to supplement penetration tests and internal code audits. https://www.guru99.com/bug-bounty-programs.html
- 19. Conclusion ● Secure app development involves integrating security practices throughout the software development lifecycle. ● User data privacy is crucial, and compliance with relevant regulations ● Obtaining user consent, handling data securely, and providing transparent privacy policies are important aspects of user data privacy. ● Rigorous testing and security audits throughout the development process help identify and address security weaknesses and vulnerabilities.Types of tests include penetration testing, vulnerability scanning, code review, security architecture review, and API security testing. ● User education and awareness are vital for overall app security. ● Clear instructions, security tips, and promoting safe user behaviors help prevent common security risks. ● Developing secure apps is essential to protect user data, maintain trust, and mitigate the risk of security breaches.
- 20. QUIZ
- 21. What is the purpose of secure coding practices? A. To make the code more readable B. To prevent security vulnerabilities C. To optimize code performance D. To enhance user experience
- 22. Why is user consent important in app development? A. It allows users to control their personal data B. It speeds up the app development process C. It reduces the need for security measures D. It ensures compliance with marketing regulations
- 23. What is the purpose of penetration testing? A. To identify vulnerabilities in an application B. To test the performance of the app under heavy load C. To optimize the user interface of the app D. To analyze user behavior and preferences
- 24. What is the role of user education in app security? A. It shifts the responsibility of security solely to the users B. It helps users make informed decisions and avoid common security risks C. It eliminates the need for security testing and audits D. It reduces the importance of secure coding practices
- 25. What are the potential consequences of non- compliance with data privacy regulations? A. Reputational damage, legal liabilities, and financial penalties B. Increased app visibility and popularity C. Streamlined development process and faster time to market D. Enhanced user experience and satisfaction
- 26. OUR CONTACT DETAILS Livares Technologies Pvt Ltd 5th Floor, Yamuna Building Technopark Phase III Campus Trivandrum, Kerala, India-695581 Livares Technologies Pvt Ltd Tech&Socio-Cultural Group Our helpline is always open to receive any inquiry or feedback.Please feel free to contact us www.livares.com [email protected] @livaresofficial www.facebook.com/livaresofficial +91-471-2710003 | +91-471- 2710004 THANK YOU

