Java performance
2 likes515 views
Java Performance notes. Subtle changes that could make a difference. Generally interesting concepts (I hope), food for thought/ for debate.
1 of 34
Downloaded 12 times













![Cache Field Lookups
Accessing object
fields is much
slower than
accessing local
variables.
Instead of:
for (int i=0; i<this.mCount; i++)
dumpItem(this.mItems[i]);
Write:
int count = this.mCount;
Item[] items = this.mItems;
for (int i = 0; i < count; i++)
dumpItems(items[i]);](https://image.slidesharecdn.com/javaperformancenotes-131011231338-phpapp02/85/Java-performance-14-320.jpg)



















Ad
Recommended
An introduction to javascript



An introduction to javascriptMD Sayem Ahmed The document provides an overview of key JavaScript data types and concepts including:
- Primitive data types like numbers, strings, booleans, objects, functions, arrays, dates, regular expressions, and special values like NaN and undefined.
- How numbers are stored as floats and to be careful of precision issues. The Math object can be used for advanced math.
- Strings can represent character sequences and have useful methods.
- Objects are collections of key-value pairs that can contain other objects. Arrays are object that are for storing lists of values.
- Functions are objects that can take parameters and return values. Functions have access to an arguments object.
C traps and pitfalls for C++ programmers



C traps and pitfalls for C++ programmersRichard Thomson C++ provides backwards compatability with C, but you will have an easier time if you stay away from certain C-style programming habits. This presentation outlines traps and pitfalls from C style programming in C++ and recommends pure C++ alternatives that lead to fewer surprises, fewer errors and better code. This presentation hasn't been updated for C++11 and is based on C++03.
Best practices in Java



Best practices in JavaMudit Gupta - Best Practices in Java
- Avoiding garbage collection
- Loop Optimizaiton
- Exception Handling
- Object Oriented Design Principles
- Avoiding null pointer exception
Functors, Applicatives and Monads In Scala



Functors, Applicatives and Monads In ScalaKnoldus Inc. The document discusses functors, applicatives, and monads. It defines each concept and provides examples. Functors allow mapping a function over a wrapped value using map. Applicatives allow applying a function wrapped in a context to a value wrapped in a context using apply. Monads allow applying a function that returns a wrapped value to a wrapped value using flatMap. Examples of each include Option for functors, lists for applicatives, and futures for monads.
Of Lambdas and LINQ



Of Lambdas and LINQBlackRabbitCoder A small presentation I developed that introduces lambda expressions and many of the common LINQ extension methods for a group of developers that were less familiar with these concepts.
More Little Wonders of C#/.NET



More Little Wonders of C#/.NETBlackRabbitCoder We've all seen the big "macro" features in .NET, this presentation is to give praise to the "Little Wonders" of .NET -- those little items in the framework that make life as a developer that much easier!
Oo Design And Patterns



Oo Design And PatternsAnil Bapat The document discusses object-oriented (OO) design and patterns. It defines OO design as organizing software around objects rather than functions, using techniques like abstraction, encapsulation, inheritance, and polymorphism. C++ supports these OO mechanisms, making it an OO language. Classes in C++ enable abstraction and encapsulation. Inheritance and polymorphism allow modeling "is-a" relationships and enable code reuse. Common design patterns like singleton, factory, and observer are also discussed. The key to OO project success is identifying the right abstractions.
Yellowbrick: Steering machine learning with visual transformers



Yellowbrick: Steering machine learning with visual transformersRebecca Bilbro In machine learning, model selection is a bit more nuanced than simply picking the 'right' or 'wrong' algorithm. In practice, the workflow includes (1) selecting and/or engineering the smallest and most predictive feature set, (2) choosing a set of algorithms from a model family, and (3) tuning the algorithm hyperparameters to optimize performance. Recently, much of this workflow has been automated through grid search methods, standardized APIs, and GUI-based applications. In practice, however, human intuition and guidance can more effectively hone in on quality models than exhaustive search.
This talk presents a new Python library, Yellowbrick, which extends the Scikit-Learn API with a visual transfomer (visualizer) that can incorporate visualizations of the model selection process into pipelines and modeling workflow. Yellowbrick is an open source, pure Python project that extends Scikit-Learn with visual analysis and diagnostic tools. The Yellowbrick API also wraps matplotlib to create publication-ready figures and interactive data explorations while still allowing developers fine-grain control of figures. For users, Yellowbrick can help evaluate the performance, stability, and predictive value of machine learning models, and assist in diagnosing problems throughout the machine learning workflow.
In this talk, we'll explore not only what you can do with Yellowbrick, but how it works under the hood (since we're always looking for new contributors!). We'll illustrate how Yellowbrick extends the Scikit-Learn and Matplotlib APIs with a new core object: the Visualizer. Visualizers allow visual models to be fit and transformed as part of the Scikit-Learn Pipeline process - providing iterative visual diagnostics throughout the transformation of high dimensional data.
DotNet programming & Practices



DotNet programming & PracticesDev Raj Gautam DotNet Programming & Practices discusses various best practices for .NET development including:
1. Using proper naming conventions like PascalCasing for classes and methods and camelCasing for variables.
2. Properly documenting code with XML comments and avoiding inline comments. Only using regions for private fields, nested classes, and interface implementations.
3. Methods should perform a single task, not combine multiple jobs, and generally not exceed 25 lines. This increases maintainability.
4. Properties should be used over methods when the work is expensive or represents a conversion, and methods should be used when the result changes or causes side effects beyond the property.
(Py)testing the Limits of Machine Learning



(Py)testing the Limits of Machine LearningRebecca Bilbro Despite the hype cycle, each day machine learning becomes a little less magic and a little more real. Predictions increasingly drive our everyday lives, embedded into more of our everyday applications. To support this creative surge, development teams are evolving, integrating novel open source software and state-of-the-art GPU hardware, and bringing on essential new teammates like data ethicists and machine learning engineers. Software teams are also now challenged to build and maintain codebases that are intentionally not fully deterministic.
This nondeterminism can manifest in a number of surprising and oftentimes very stressful ways! Successive runs of model training may produce slight but meaningful variations. Data wrangling pipelines turn out to be extremely sensitive to the order in which transformations are applied, and require thoughtful orchestration to avoid leakage. Model hyperparameters that can be tuned independently may have mutually exclusive conditions. Models can also degrade over time, producing increasingly unreliable predictions. Moreover, open source libraries are living, dynamic things; the latest release of your team's favorite library might cause your code to suddenly behave in unexpected ways.
Put simply, as ML becomes more of an expectation than an exception in our industry, testing has never been more important! Fortunately, we are lucky to have a rich open source ecosystem to support us in our journey to build the next generation of apps in a safe, stable way. In this talk we'll share some hard-won lessons, favorite open source packages, and reusable techniques for testing ML software components.
Escaping the Black Box



Escaping the Black BoxRebecca Bilbro In machine learning, model selection is a bit more nuanced than simply picking the 'right' or 'wrong' algorithm. In practice, the workflow includes (1) selecting and/or engineering the smallest and most predictive feature set, (2) choosing a set of algorithms from a model family, and (3) tuning the algorithm hyperparameters to optimize performance. Recently, much of this workflow has been automated through grid search methods, standardized APIs, and GUI-based applications. In practice, however, human intuition and guidance can more effectively hone in on quality models than exhaustive search.
This talk presents a new open source Python library, Yellowbrick, which extends the Scikit-Learn API with a visual transfomer (visualizer) that can incorporate visualizations of the model selection process into pipelines and modeling workflow. Visualizers enable machine learning practitioners to visually interpret the model selection process, steer workflows toward more predictive models, and avoid common pitfalls and traps. For users, Yellowbrick can help evaluate the performance, stability, and predictive value of machine learning models, and assist in diagnosing problems throughout the machine learning workflow.
A Survey of Concurrency Constructs



A Survey of Concurrency ConstructsTed Leung The document provides an overview of concurrency constructs and models. It discusses threads and locks, and some of the problems with locks like manually locking/unlocking and lock ordering issues. It then covers theoretical models like actors, CSP, and dataflow. Implementation details and problems with different models are discussed. Finally, it highlights some open problems and areas for further work.
EuroSciPy 2019: Visual diagnostics at scale



EuroSciPy 2019: Visual diagnostics at scaleRebecca Bilbro The hunt for the most effective machine learning model is hard enough with a modest dataset, and much more so as our data grow! As we search for the optimal combination of features, algorithm, and hyperparameters, we often use tools like histograms, heatmaps, embeddings, and other plots to make our processes more informed and effective. However, large, high-dimensional datasets can prove particularly challenging. In this talk, we’ll explore a suite of visual diagnostics, investigate their strengths and weaknesses in face of increasingly big data, and consider how we can steer the machine learning process, not only purposefully but at scale!
Fuel Up JavaScript with Functional Programming



Fuel Up JavaScript with Functional ProgrammingShine Xavier JavaScript is the lingua franca of web development for over a decade. It has evolved tremendously along with the Web and has entrenched in modern browsers, complex Web applications, mobile development, server-side programming, and in emerging platforms like the Internet of Things.
Eventhough JavaScript has come a long way, a reinforced makeover to it will help build concurrent and massive systems that handle Big Data, IoT peripherals and many other complex eco systems. Functional Programming is the programming paradigm that could empower JavaScript to to enable more effective, robust, and flexible software development.
These days, Functional Programming is at the heart of every new generation programming technologies. The inclusion of Functional Programming in JavaScript will lead to advanced and futuristic systems.
The need of the hour is to unwrap the underlying concepts and its implementation in the software development process.
The 46th edition of FAYA:80 provides a unique opportunity for the JavaScript developers and technology enthusiasts to shed light on the functional programming paradigm and on writing efficient functional code in JavaScript.
Join us for the session to know more.
Topics Covered:
· Functional Programming Core Concepts
· Function Compositions & Pipelines
· Use of JS in Functional Programming
· Techniques for Functional Coding in JS
· Live Demo
Xbase - Implementing Domain-Specific Languages for Java



Xbase - Implementing Domain-Specific Languages for Javameysholdt This document discusses using Xtext to implement domain-specific languages for Java. Xtext allows defining the grammar of a DSL and generates an IDE and runtime. Key points:
- Xtext generates editors, compilers/interpreters, debuggers from a DSL grammar. The grammar reuse and customization allow adapting Xtext to different needs.
- Xbase provides a reusable expression language that can be embedded in Xtext DSLs, providing features like lambda expressions, extension methods, and type inference.
- A JvmModel inference performs a model-to-model transformation to map DSL models to equivalent Java classes, providing context for linking, type system, and compilation of DSL expressions.
2CPP04 - Objects and Classes



2CPP04 - Objects and ClassesMichael Heron This is an intermediate conversion course for C++, suitable for second year computing students who may have learned Java or another language in first year.
The Little Wonders of C# 6



The Little Wonders of C# 6BlackRabbitCoder The document summarizes several new features in C# 6, including the nameof() operator, auto-property initialization, indexed initializer lists, the using static directive, method and property expressions, string interpolation, enhanced exception filtering, and the null conditional operator (?.). Some key features allow getting a string representation of an identifier with nameof(), initializing auto-properties to non-default values more easily, using indexers for initialization lists, importing static members to simplify code, string interpolation for building strings with values inline, filtering exceptions based on logical conditions, and safely accessing members and indexers of objects that may be null with the null conditional operator. Overall, the new features add syntactic sugar to help reduce boilerplate code and improve readability
Pattern Matching - at a glance



Pattern Matching - at a glanceKnoldus Inc. This document discusses pattern matching in Scala. [1] Case classes allow for convenient pattern matching by adding methods like toString and equals. [2] Pattern matching uses match expressions to select alternatives based on patterns. Common patterns include wildcards, constants, variables, constructor patterns for case classes, sequences, tuples, and typed patterns. Patterns can also be used in variable definitions and for expressions.
Java8 javatime-api



Java8 javatime-apiJini Lee - Java 8 introduced a new date and time API in the java.time package that is immutable, thread-safe, and supports multiple calendar systems.
- The API separates the concepts of date, time, and timestamps (LocalDate, LocalTime, LocalDateTime) from calendar systems and timezones (ZonedDateTime).
- The API provides methods to query, manipulate, and convert between date/time objects using static factories, instance methods, and temporal adjusters.
Introduction to Machine Learning with Spark



Introduction to Machine Learning with Sparkdatamantra Talk about implementing machine learning in Apache Spark.Presented at Bangalore Spark meetup group at Bangalore by Madhukara Phatak on 05/09/2015.
What To Leave Implicit



What To Leave ImplicitMartin Odersky This document summarizes Martin Odersky's talk on implicits in Scala. The key points are:
1. Implicits allow certain values or functions to be passed implicitly rather than explicitly as parameters. This can avoid tedious repetition when many parameters rarely change.
2. Implicits are commonly used to establish context, inject dependencies, implement type classes, and prove theorems by modeling types as theorems and programs as proofs.
3. Future changes to implicits in Scala 3 include allowing multiple implicit parameter lists, implicit by-name parameters, and implicit function types which avoid wrapping implicits in monads.
Ae31225230



Ae31225230IJERA Editor This document summarizes two GPU programming models - Accelerator and CUDA. It describes the basic steps in Accelerator programming including creating data arrays, loading them into data-parallel array objects, processing the arrays using Accelerator operations, creating a result object, and evaluating the result on a target processor. It also provides an example code showing the use of ParallelArrays and FloatParallelArray objects. The document then briefly introduces CUDA as a parallel computing platform and programming model for GPUs that provides lower and higher-level APIs.
Introduction to Spark



Introduction to SparkSriram Kailasam This document introduces Spark, an open-source cluster computing framework. Spark improves on Hadoop MapReduce by keeping intermediate data in memory rather than disk, speeding up iterative jobs. Spark uses resilient distributed datasets (RDDs) that can tolerate failures using lineage graphs to recompute lost data. It runs on Hadoop YARN and HDFS and is programmed using Scala, a functional programming language that supports objects, higher-order functions, and nested functions.
Simplicitly



SimplicitlyMartin Odersky This document discusses implicit function types as a way to abstract over context in programming. It proposes implicit function types as a lighter-weight alternative to type classes and the reader monad for passing implicit context parameters. Implicit function types allow context to be provided implicitly based on the expected type rather than requiring it to be passed explicitly. The document outlines the typing rules and translation to the lambda calculus for implicit function types and provides examples of their use in a conference management system and the builder pattern.
Functional programming with Scala



Functional programming with ScalaNeelkanth Sachdeva Scala is a multi-paradigm programming language that blends object-oriented and functional programming. It is designed to express common programming patterns in a concise, elegant, and type-safe way. Scala runs on the Java Virtual Machine and interoperates seamlessly with Java, but also integrates concepts from languages such as Haskell, ML and Ruby. Some key features of Scala include support for functional programming, a static type system with type inference, pattern matching, actors and immutable data structures.
Practical pairing of generative programming with functional programming.



Practical pairing of generative programming with functional programming.Eugene Lazutkin The new wave of JavaScript techniques: Practical pairing of generative programming with functional programming. Eugene Lazutkin, ClubAjax, 6/4/2013
Constructors & Destructors



Constructors & DestructorsRokonuzzaman Rony Constructors are special member functions that are called automatically when objects are created. They initialize objects and are declared with the same name as the class but without a return type. Destructors are also special member functions that are called when objects are destroyed in order to perform cleanup tasks. Copy constructors are used to initialize objects as copies of other objects and are declared with a parameter of the class type passed by reference. Constructors and destructors perform important initialization and cleanup tasks but have certain limitations like not being able to return values.
What To Leave Implicit



What To Leave ImplicitMartin Odersky - Implicit function types are a powerful way to abstract over contexts by defining types that inject implicit values into a scope. This can fundamentally change the code we write by removing boilerplate around passing implicit parameters and configurations.
- Implicit parameters are a core Scala feature that allow removing repetition through parameterization while enabling use cases like proving theorems, establishing context, and implementing type classes. Their scope may be expanded through implicit function types.
- Future Scala versions aim to tighten rules for implicit conversions while introducing features like lazy implicits, multiple implicit parameter lists, and coherence to improve the discoverability and reasoning around implicits.
Linq To The Enterprise



Linq To The EnterpriseDaniel Egan The document provides a biography and background information on Daniel N. Egan, including his roles as a Microsoft Regional Director, Microsoft MVP for ASP.Net, author, and speaker. It then outlines the topics to be covered in the presentation, including object relational mappers, language enhancements in C# and VB.Net, LINQ goals, fundamentals and usage.
EuroAD 2021: ChainRules.jl 



EuroAD 2021: ChainRules.jl Lyndon White ChainRules.jl provides extensible, AD engine-agnostic custom differentiation rules for Julia. It defines rules for Julia's standard libraries that can be used by various AD engines like Zygote and ReverseDiff. ChainRules.jl is made up of three key packages - ChainRulesCore defines the system for creating rules, ChainRules defines rules for Julia, and ChainRulesTestUtils tests rule definitions. Polymorphism in Julia poses challenges for AD rules, such as ensuring tangents have the proper structure. Future work includes better support for selective differentiation.
Ad
More Related Content
What's hot (20)
DotNet programming & Practices



DotNet programming & PracticesDev Raj Gautam DotNet Programming & Practices discusses various best practices for .NET development including:
1. Using proper naming conventions like PascalCasing for classes and methods and camelCasing for variables.
2. Properly documenting code with XML comments and avoiding inline comments. Only using regions for private fields, nested classes, and interface implementations.
3. Methods should perform a single task, not combine multiple jobs, and generally not exceed 25 lines. This increases maintainability.
4. Properties should be used over methods when the work is expensive or represents a conversion, and methods should be used when the result changes or causes side effects beyond the property.
(Py)testing the Limits of Machine Learning



(Py)testing the Limits of Machine LearningRebecca Bilbro Despite the hype cycle, each day machine learning becomes a little less magic and a little more real. Predictions increasingly drive our everyday lives, embedded into more of our everyday applications. To support this creative surge, development teams are evolving, integrating novel open source software and state-of-the-art GPU hardware, and bringing on essential new teammates like data ethicists and machine learning engineers. Software teams are also now challenged to build and maintain codebases that are intentionally not fully deterministic.
This nondeterminism can manifest in a number of surprising and oftentimes very stressful ways! Successive runs of model training may produce slight but meaningful variations. Data wrangling pipelines turn out to be extremely sensitive to the order in which transformations are applied, and require thoughtful orchestration to avoid leakage. Model hyperparameters that can be tuned independently may have mutually exclusive conditions. Models can also degrade over time, producing increasingly unreliable predictions. Moreover, open source libraries are living, dynamic things; the latest release of your team's favorite library might cause your code to suddenly behave in unexpected ways.
Put simply, as ML becomes more of an expectation than an exception in our industry, testing has never been more important! Fortunately, we are lucky to have a rich open source ecosystem to support us in our journey to build the next generation of apps in a safe, stable way. In this talk we'll share some hard-won lessons, favorite open source packages, and reusable techniques for testing ML software components.
Escaping the Black Box



Escaping the Black BoxRebecca Bilbro In machine learning, model selection is a bit more nuanced than simply picking the 'right' or 'wrong' algorithm. In practice, the workflow includes (1) selecting and/or engineering the smallest and most predictive feature set, (2) choosing a set of algorithms from a model family, and (3) tuning the algorithm hyperparameters to optimize performance. Recently, much of this workflow has been automated through grid search methods, standardized APIs, and GUI-based applications. In practice, however, human intuition and guidance can more effectively hone in on quality models than exhaustive search.
This talk presents a new open source Python library, Yellowbrick, which extends the Scikit-Learn API with a visual transfomer (visualizer) that can incorporate visualizations of the model selection process into pipelines and modeling workflow. Visualizers enable machine learning practitioners to visually interpret the model selection process, steer workflows toward more predictive models, and avoid common pitfalls and traps. For users, Yellowbrick can help evaluate the performance, stability, and predictive value of machine learning models, and assist in diagnosing problems throughout the machine learning workflow.
A Survey of Concurrency Constructs



A Survey of Concurrency ConstructsTed Leung The document provides an overview of concurrency constructs and models. It discusses threads and locks, and some of the problems with locks like manually locking/unlocking and lock ordering issues. It then covers theoretical models like actors, CSP, and dataflow. Implementation details and problems with different models are discussed. Finally, it highlights some open problems and areas for further work.
EuroSciPy 2019: Visual diagnostics at scale



EuroSciPy 2019: Visual diagnostics at scaleRebecca Bilbro The hunt for the most effective machine learning model is hard enough with a modest dataset, and much more so as our data grow! As we search for the optimal combination of features, algorithm, and hyperparameters, we often use tools like histograms, heatmaps, embeddings, and other plots to make our processes more informed and effective. However, large, high-dimensional datasets can prove particularly challenging. In this talk, we’ll explore a suite of visual diagnostics, investigate their strengths and weaknesses in face of increasingly big data, and consider how we can steer the machine learning process, not only purposefully but at scale!
Fuel Up JavaScript with Functional Programming



Fuel Up JavaScript with Functional ProgrammingShine Xavier JavaScript is the lingua franca of web development for over a decade. It has evolved tremendously along with the Web and has entrenched in modern browsers, complex Web applications, mobile development, server-side programming, and in emerging platforms like the Internet of Things.
Eventhough JavaScript has come a long way, a reinforced makeover to it will help build concurrent and massive systems that handle Big Data, IoT peripherals and many other complex eco systems. Functional Programming is the programming paradigm that could empower JavaScript to to enable more effective, robust, and flexible software development.
These days, Functional Programming is at the heart of every new generation programming technologies. The inclusion of Functional Programming in JavaScript will lead to advanced and futuristic systems.
The need of the hour is to unwrap the underlying concepts and its implementation in the software development process.
The 46th edition of FAYA:80 provides a unique opportunity for the JavaScript developers and technology enthusiasts to shed light on the functional programming paradigm and on writing efficient functional code in JavaScript.
Join us for the session to know more.
Topics Covered:
· Functional Programming Core Concepts
· Function Compositions & Pipelines
· Use of JS in Functional Programming
· Techniques for Functional Coding in JS
· Live Demo
Xbase - Implementing Domain-Specific Languages for Java



Xbase - Implementing Domain-Specific Languages for Javameysholdt This document discusses using Xtext to implement domain-specific languages for Java. Xtext allows defining the grammar of a DSL and generates an IDE and runtime. Key points:
- Xtext generates editors, compilers/interpreters, debuggers from a DSL grammar. The grammar reuse and customization allow adapting Xtext to different needs.
- Xbase provides a reusable expression language that can be embedded in Xtext DSLs, providing features like lambda expressions, extension methods, and type inference.
- A JvmModel inference performs a model-to-model transformation to map DSL models to equivalent Java classes, providing context for linking, type system, and compilation of DSL expressions.
2CPP04 - Objects and Classes



2CPP04 - Objects and ClassesMichael Heron This is an intermediate conversion course for C++, suitable for second year computing students who may have learned Java or another language in first year.
The Little Wonders of C# 6



The Little Wonders of C# 6BlackRabbitCoder The document summarizes several new features in C# 6, including the nameof() operator, auto-property initialization, indexed initializer lists, the using static directive, method and property expressions, string interpolation, enhanced exception filtering, and the null conditional operator (?.). Some key features allow getting a string representation of an identifier with nameof(), initializing auto-properties to non-default values more easily, using indexers for initialization lists, importing static members to simplify code, string interpolation for building strings with values inline, filtering exceptions based on logical conditions, and safely accessing members and indexers of objects that may be null with the null conditional operator. Overall, the new features add syntactic sugar to help reduce boilerplate code and improve readability
Pattern Matching - at a glance



Pattern Matching - at a glanceKnoldus Inc. This document discusses pattern matching in Scala. [1] Case classes allow for convenient pattern matching by adding methods like toString and equals. [2] Pattern matching uses match expressions to select alternatives based on patterns. Common patterns include wildcards, constants, variables, constructor patterns for case classes, sequences, tuples, and typed patterns. Patterns can also be used in variable definitions and for expressions.
Java8 javatime-api



Java8 javatime-apiJini Lee - Java 8 introduced a new date and time API in the java.time package that is immutable, thread-safe, and supports multiple calendar systems.
- The API separates the concepts of date, time, and timestamps (LocalDate, LocalTime, LocalDateTime) from calendar systems and timezones (ZonedDateTime).
- The API provides methods to query, manipulate, and convert between date/time objects using static factories, instance methods, and temporal adjusters.
Introduction to Machine Learning with Spark



Introduction to Machine Learning with Sparkdatamantra Talk about implementing machine learning in Apache Spark.Presented at Bangalore Spark meetup group at Bangalore by Madhukara Phatak on 05/09/2015.
What To Leave Implicit



What To Leave ImplicitMartin Odersky This document summarizes Martin Odersky's talk on implicits in Scala. The key points are:
1. Implicits allow certain values or functions to be passed implicitly rather than explicitly as parameters. This can avoid tedious repetition when many parameters rarely change.
2. Implicits are commonly used to establish context, inject dependencies, implement type classes, and prove theorems by modeling types as theorems and programs as proofs.
3. Future changes to implicits in Scala 3 include allowing multiple implicit parameter lists, implicit by-name parameters, and implicit function types which avoid wrapping implicits in monads.
Ae31225230



Ae31225230IJERA Editor This document summarizes two GPU programming models - Accelerator and CUDA. It describes the basic steps in Accelerator programming including creating data arrays, loading them into data-parallel array objects, processing the arrays using Accelerator operations, creating a result object, and evaluating the result on a target processor. It also provides an example code showing the use of ParallelArrays and FloatParallelArray objects. The document then briefly introduces CUDA as a parallel computing platform and programming model for GPUs that provides lower and higher-level APIs.
Introduction to Spark



Introduction to SparkSriram Kailasam This document introduces Spark, an open-source cluster computing framework. Spark improves on Hadoop MapReduce by keeping intermediate data in memory rather than disk, speeding up iterative jobs. Spark uses resilient distributed datasets (RDDs) that can tolerate failures using lineage graphs to recompute lost data. It runs on Hadoop YARN and HDFS and is programmed using Scala, a functional programming language that supports objects, higher-order functions, and nested functions.
Simplicitly



SimplicitlyMartin Odersky This document discusses implicit function types as a way to abstract over context in programming. It proposes implicit function types as a lighter-weight alternative to type classes and the reader monad for passing implicit context parameters. Implicit function types allow context to be provided implicitly based on the expected type rather than requiring it to be passed explicitly. The document outlines the typing rules and translation to the lambda calculus for implicit function types and provides examples of their use in a conference management system and the builder pattern.
Functional programming with Scala



Functional programming with ScalaNeelkanth Sachdeva Scala is a multi-paradigm programming language that blends object-oriented and functional programming. It is designed to express common programming patterns in a concise, elegant, and type-safe way. Scala runs on the Java Virtual Machine and interoperates seamlessly with Java, but also integrates concepts from languages such as Haskell, ML and Ruby. Some key features of Scala include support for functional programming, a static type system with type inference, pattern matching, actors and immutable data structures.
Practical pairing of generative programming with functional programming.



Practical pairing of generative programming with functional programming.Eugene Lazutkin The new wave of JavaScript techniques: Practical pairing of generative programming with functional programming. Eugene Lazutkin, ClubAjax, 6/4/2013
Constructors & Destructors



Constructors & DestructorsRokonuzzaman Rony Constructors are special member functions that are called automatically when objects are created. They initialize objects and are declared with the same name as the class but without a return type. Destructors are also special member functions that are called when objects are destroyed in order to perform cleanup tasks. Copy constructors are used to initialize objects as copies of other objects and are declared with a parameter of the class type passed by reference. Constructors and destructors perform important initialization and cleanup tasks but have certain limitations like not being able to return values.
What To Leave Implicit



What To Leave ImplicitMartin Odersky - Implicit function types are a powerful way to abstract over contexts by defining types that inject implicit values into a scope. This can fundamentally change the code we write by removing boilerplate around passing implicit parameters and configurations.
- Implicit parameters are a core Scala feature that allow removing repetition through parameterization while enabling use cases like proving theorems, establishing context, and implementing type classes. Their scope may be expanded through implicit function types.
- Future Scala versions aim to tighten rules for implicit conversions while introducing features like lazy implicits, multiple implicit parameter lists, and coherence to improve the discoverability and reasoning around implicits.
Similar to Java performance (20)
Linq To The Enterprise



Linq To The EnterpriseDaniel Egan The document provides a biography and background information on Daniel N. Egan, including his roles as a Microsoft Regional Director, Microsoft MVP for ASP.Net, author, and speaker. It then outlines the topics to be covered in the presentation, including object relational mappers, language enhancements in C# and VB.Net, LINQ goals, fundamentals and usage.
EuroAD 2021: ChainRules.jl 



EuroAD 2021: ChainRules.jl Lyndon White ChainRules.jl provides extensible, AD engine-agnostic custom differentiation rules for Julia. It defines rules for Julia's standard libraries that can be used by various AD engines like Zygote and ReverseDiff. ChainRules.jl is made up of three key packages - ChainRulesCore defines the system for creating rules, ChainRules defines rules for Julia, and ChainRulesTestUtils tests rule definitions. Polymorphism in Julia poses challenges for AD rules, such as ensuring tangents have the proper structure. Future work includes better support for selective differentiation.
Mobile Developer Summit 2012, Pune



Mobile Developer Summit 2012, PuneBhuvan Khanna The document provides tips for improving code performance in Java. Some key points include:
- Avoid doing unnecessary work and allocating memory if possible. Using efficient data structures and algorithms makes a bigger difference than micro-optimizations.
- Object creation has overhead so avoid creating temporary objects, especially in loops.
- Virtual method calls are more expensive than direct field access so favor the latter.
- The enhanced for loop is generally better than a basic for loop for iterating over arrays but a counted loop may be faster for performance critical code.
- Inner classes can access outer class private members through generated access methods, causing a performance hit, so favor package private access for performance critical inner class usage.
Linq 1224887336792847 9



Linq 1224887336792847 9google The document provides an overview of Daniel Egan's professional experience including his roles as a Microsoft Regional Director, Microsoft MVP for ASP.Net, Chief Architect at Odyssey Consulting Group, author, instructor, and his involvement with various .Net user groups. It then outlines topics to be covered including object relational mappers, language enhancements in VB.Net and C# 3.0, LINQ and LINQ to SQL.
Can't Dance The Lambda



Can't Dance The LambdaTogakangaroo The document discusses how lambdas can be used for various programming patterns and tasks such as mapping and reducing data, creating navigable domain-specific languages, handling events more cleanly, and abstracting common conditional and null checking logic. Lambdas offer a concise syntax for anonymous methods and can be used to make code more readable, refactorable, and maintainable compared to traditional approaches using delegates. Examples are provided for how lambdas can simplify programming patterns around asynchronous execution, expression analysis, reflection, and other tasks.
Bound and Checked



Bound and CheckedKevlin Henney The document discusses different approaches for handling out-of-bounds indexing of containers like std::vector in C++. It examines options like undefined behavior, debug checking, runtime exceptions, index remapping, and automatic resizing. The standard library uses undefined behavior for efficiency but other approaches provide safety checks or well-defined alternate behaviors.
The Uniform Access Principle



The Uniform Access PrinciplePhilip Schwarz The document discusses the Uniform Access Principle, which states that all services offered by a module should be available through a uniform notation that does not reveal whether they are implemented through storage or computation. It provides examples of how different languages do or do not follow this principle, and explains that following this principle helps avoid breaking client code when implementation details change. It also discusses how Scala supports the Uniform Access Principle for parameterless methods.
Designing Better API



Designing Better APIKaniska Mandal The document provides guidelines for designing APIs. Some key points include:
1) Each API should clearly explain what the user can achieve and how to use it. Documentation is important.
2) Consider using annotations to mark APIs as deprecated or to specify thread safety and other implementation details.
3) Use factory methods instead of constructors when possible to increase flexibility and avoid tight coupling.
4) Make implementation classes immutable to avoid side effects and threading issues.
5) Provide consistent exceptions at the appropriate level of abstraction.
Design Patterns



Design PatternsAnkit.Rustagi The document summarizes 5 design patterns: Singleton, Strategy, Decorator, Facade, and Bulk State Transition. It provides code examples and explanations of how each pattern is implemented in Apex to solve common problems like repeated object instantiation, selecting algorithms at runtime, adding temporary fields, simplifying complex classes, and performing bulk actions. The document was presented by Ankit Rustagi and covers implementing these patterns in Apex along with handling governor limits. Contact information is provided at the end for any additional questions.
Working Effectively With Legacy Perl Code



Working Effectively With Legacy Perl Codeerikmsp - Legacy Perl code is code that uses outdated practices, has no tests or documentation, and is difficult to understand and modify. It often results from organic growth over many years and developers.
- Unit testing legacy code provides safety during refactoring, speeds up development by replacing debugging, and creates regression tests. However, the code's dependencies make it difficult to isolate and test.
- Techniques like dependency injection, sprouting, monkey patching, and temporary object reblessing can help break dependencies and make legacy code more testable. Instrumentation with profilers also aids understanding the code.
Function Overloading Call by value and call by reference



Function Overloading Call by value and call by referenceTusharAneyrao1 CALL BY VALUE AND CALL BY REFERENCE
Practical catalyst



Practical catalystdwm042 Catalyst is a web framework for Perl that allows developers to build dynamic web applications in a modular, reusable way. It utilizes common Perl techniques like Moose, DBIx::Class and Template Toolkit to handle tasks like object modeling, database access and view rendering. Catalyst applications can be built in a model-view-controller style to separate application logic, data access and presentation layers. This framework provides a standard way to write reusable code and build web UIs for tasks like system administration and automation.
Design Patterns



Design Patternsimedo.de The document discusses various design patterns including the Template Method, Strategy, Observer, Composite, Iterator, Command, Adapter, Proxy, Decorator, Singleton, Factory, Builder, Interpreter, Domain Specific Language (DSL), Meta-programming, and Convention over Configuration patterns. It provides examples and descriptions of when each pattern would be used.
Modern C++



Modern C++Richard Thomson Utah Code Camp, Spring 2016. http://utahcodecamp.com In this presentation I describe modern C++. Modern C++ assumes features introduced in the C++11/14 standard. An overview of the new features is presented and some idioms for mdoern C++ based on those features are presented.
Implementation



Implementationadil raja The document discusses various approaches to implementing object-oriented programming languages, including compilers vs interpreters, virtual method tables, inheritance, and just-in-time compilation. It covers topics like how receivers are passed as arguments, name encoding for unique method identifiers, inherited vs overridden methods, problems with multiple inheritance, bytecode interpreters, and using dispatch tables for dynamic languages. The key implementation techniques are using virtual method tables to dispatch overridden methods at runtime and just-in-time compilers that translate bytecode to native machine code for improved performance.
Concurrency and parallel in .net



Concurrency and parallel in .netMohammad Hossein Karami The document discusses various topics related to concurrency and parallelism including threads, shared state, locks, asynchronous programming, parallel processing, and reactive programming. It provides examples of using locks, reader-writer locks, thread pools, tasks, and reactive streams. It also covers challenges with concurrent programming such as race conditions, deadlocks, and debugging concurrent applications.
C# features



C# featuressagaroceanic11 The document discusses various small features and techniques in .NET called "little wonders" that can improve code readability, maintainability, and performance. It provides examples of implicit typing, auto-properties, using blocks, static class modifiers, casts, string methods, object and path helpers, Stopwatch, TimeSpan factories, operators, initializers, and extension methods. The techniques allow writing more concise and clear code to handle common tasks like property declaration, exception handling, null checking, and LINQ queries.
Patterns in Python



Patterns in Pythondn This document discusses various design patterns in Python and how they compare to their implementations in other languages like C++. It provides examples of how common patterns from the Gang of Four book like Singleton, Observer, Strategy, and Decorator are simplified or invisible in Python due to features like first-class functions and duck typing. The document aims to illustrate Pythonic ways to implement these patterns without unnecessary complexity.
Workshop - The Little Pattern That Could.pdf



Workshop - The Little Pattern That Could.pdfTobiasGoeschel The document discusses refactoring a monolithic application to follow Domain-Driven Design (DDD) and microservice principles. It provides exercises and hints to guide refactoring the codebase to use Hexagonal Architecture with separated domains, commands and queries using CQRS, and persistence-oriented repositories. Later exercises discuss improving test speed by isolating dependencies and refactoring for a serverless architecture by splitting the application into individual use cases and replacing the in-memory repository.
Salesforce integration questions



Salesforce integration questionsDebabrat Rout The document discusses transient variables in Apex. It states that declaring variables as transient reduces view state size. Transient variables cannot be saved as part of the view state and shouldn't be transmitted when a Visualforce page is rendered. It also lists some objects that are automatically transient like HttpRequest. The document then asks questions about callouts, scheduling batches, future annotations limitations, and differences between enterprise and partner WSDLs.
Ad
Recently uploaded (20)
Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...



Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...Noah Loul Artificial intelligence is changing how businesses operate. Companies are using AI agents to automate tasks, reduce time spent on repetitive work, and focus more on high-value activities. Noah Loul, an AI strategist and entrepreneur, has helped dozens of companies streamline their operations using smart automation. He believes AI agents aren't just tools—they're workers that take on repeatable tasks so your human team can focus on what matters. If you want to reduce time waste and increase output, AI agents are the next move.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
tecnologias de las primeras civilizaciones.pdf



tecnologias de las primeras civilizaciones.pdffjgm517 descaripcion detallada del avance de las tecnologias en mesopotamia, egipto, roma y grecia.
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
Big Data Analytics Quick Research Guide by Arthur Morgan



Big Data Analytics Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
HCL Nomad Web – Best Practices and Managing Multiuser Environments



HCL Nomad Web – Best Practices and Managing Multiuser Environmentspanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-and-managing-multiuser-environments/
HCL Nomad Web is heralded as the next generation of the HCL Notes client, offering numerous advantages such as eliminating the need for packaging, distribution, and installation. Nomad Web client upgrades will be installed “automatically” in the background. This significantly reduces the administrative footprint compared to traditional HCL Notes clients. However, troubleshooting issues in Nomad Web present unique challenges compared to the Notes client.
Join Christoph and Marc as they demonstrate how to simplify the troubleshooting process in HCL Nomad Web, ensuring a smoother and more efficient user experience.
In this webinar, we will explore effective strategies for diagnosing and resolving common problems in HCL Nomad Web, including
- Accessing the console
- Locating and interpreting log files
- Accessing the data folder within the browser’s cache (using OPFS)
- Understand the difference between single- and multi-user scenarios
- Utilizing Client Clocking
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
Linux Support for SMARC: How Toradex Empowers Embedded Developers



Linux Support for SMARC: How Toradex Empowers Embedded DevelopersToradex Toradex brings robust Linux support to SMARC (Smart Mobility Architecture), ensuring high performance and long-term reliability for embedded applications. Here’s how:
• Optimized Torizon OS & Yocto Support – Toradex provides Torizon OS, a Debian-based easy-to-use platform, and Yocto BSPs for customized Linux images on SMARC modules.
• Seamless Integration with i.MX 8M Plus and i.MX 95 – Toradex SMARC solutions leverage NXP’s i.MX 8 M Plus and i.MX 95 SoCs, delivering power efficiency and AI-ready performance.
• Secure and Reliable – With Secure Boot, over-the-air (OTA) updates, and LTS kernel support, Toradex ensures industrial-grade security and longevity.
• Containerized Workflows for AI & IoT – Support for Docker, ROS, and real-time Linux enables scalable AI, ML, and IoT applications.
• Strong Ecosystem & Developer Support – Toradex offers comprehensive documentation, developer tools, and dedicated support, accelerating time-to-market.
With Toradex’s Linux support for SMARC, developers get a scalable, secure, and high-performance solution for industrial, medical, and AI-driven applications.
Do you have a specific project or application in mind where you're considering SMARC? We can help with Free Compatibility Check and help you with quick time-to-market
For more information: https://www.toradex.com/computer-on-modules/smarc-arm-family
Semantic Cultivators : The Critical Future Role to Enable AI



Semantic Cultivators : The Critical Future Role to Enable AIartmondano By 2026, AI agents will consume 10x more enterprise data than humans, but with none of the contextual understanding that prevents catastrophic misinterpretations.
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
Build Your Own Copilot & Agents For Devs



Build Your Own Copilot & Agents For DevsBrian McKeiver May 2nd, 2025 talk at StirTrek 2025 Conference.
Andrew Marnell: Transforming Business Strategy Through Data-Driven Insights



Andrew Marnell: Transforming Business Strategy Through Data-Driven InsightsAndrew Marnell With expertise in data architecture, performance tracking, and revenue forecasting, Andrew Marnell plays a vital role in aligning business strategies with data insights. Andrew Marnell’s ability to lead cross-functional teams ensures businesses achieve sustainable growth and operational excellence.
Heap, Types of Heap, Insertion and Deletion



Heap, Types of Heap, Insertion and DeletionJaydeep Kale This pdf will explain what is heap, its type, insertion and deletion in heap and Heap sort
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
2025-05-Q4-2024-Investor-Presentation.pptx



2025-05-Q4-2024-Investor-Presentation.pptxSamuele Fogagnolo Cloudflare Q4 Financial Results Presentation
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
Ad
Java performance
- 1. Jan 2010 Java Performance Quest for Speed Rajesuwer P Singaravelu
- 2. Discussed here are subtle changes that could make a difference. Minor gains, of say 2ms, could be significant if you are performing 100K operations to serve a request. Architectural patterns are not considered here. Introduction
- 3. Introduction - Know Your Application Different applications have different performance characteristics and bottlenecks. Performance varies across different hardware, operating systems, compilers and virtual machines.
- 4. Performance - Cousins Equally important are: Code Quality Maintainability Readability
- 5. Performance - Architecture Poor performance built into your app? Heavy use of the object-oriented paradigm (many layers of superclasses and subclasses) Simple tuning won t do. Re-design application or parts of it. Keep performance in mind when designing your applications.
- 6. Performance - Algorithm Use efficient algorithms. Do you use O(n2) bubblesort algorithm or a much more efficient O(n log n) quicksort ?
- 7. Tech Tips
- 8. Avoid Creating Objects Object creation is never free. This has gotten better over years, but allocating memory is always more expensive than not allocating memory. Reuse objects where possible.
- 9. Short Circuit Perform a cheap test before an expensive one if (s1 == s2 || s1.equals(s2))
- 10. Wrappers Wrapper classes come with overhead- time and space Watch out for autoboxing Consider Efficient Alternatives: If you need to add int-s to a list or map, consider using TIntArrayList, TIntObjectHashMap and such from trove library.
- 11. Prefer Concrete Over Interface Suppose you have a HashMap object. You can declare it as a HashMap or as a generic Map: Map myMap1 = new HashMap() vs HashMap myMap2 = new HashMap() Which is better? Calling through an interface reference can take longer than a call through a concrete reference. If you have chosen a HashMap because it fits what you're doing, there is little value in calling it a Map. Given the availability of IDEs that refactor your code for you, there's not much value in calling it a Map even if you're not sure where the code is headed. (Again, though, public APIs are an exception: a good API usually trumps small performance concerns.)
- 12. Prefer Static Over Virtual Make methods static If you don t need access to object s fields Can be faster Doesn't require a virtual method table indirection, so can be faster. Also good practice Method signature conveys that calling the method can’t/doesn’t alter the object's state.
- 13. (Avoid) Internal Getters/Setters Use i = this.var Instead of i = getVar() Especially inside loops. Which is expensive- method call or instance variable lookup?
- 14. Cache Field Lookups Accessing object fields is much slower than accessing local variables. Instead of: for (int i=0; i<this.mCount; i++) dumpItem(this.mItems[i]); Write: int count = this.mCount; Item[] items = this.mItems; for (int i = 0; i < count; i++) dumpItems(items[i]);
- 15. Enhanced For Loop - Use Caution For ArrayList, use: for(int i=0; i < count; i++){ list.get(i); } instead of: for(String s: list){ .. } For other collections the for-each loop will be equivalent to explicit iterator usage.
- 16. Synchronization Avoid synchronized methods if you can. If you can't, synchronizing on methods rather than on code blocks is slightly faster.
- 17. Exception Use exceptions where you really need them. Have a high basic cost, & their presence can hurt compiler analysis.
- 18. Using API classes Use Java API classes when they offer native machine performance that you can't match using Java. For example, arraycopy() is much faster than using a loop to copy an array of any significant size.
- 19. Avoid expensive constructs Sometimes Java constructs are so expensive that it can be worth making your data structures or code a little more complex to work around the problem. For example, you can add a type id number to objects to avoid paying the cost of an instanceof (this also allows you to use the result in a switch). Similarly, in a long inheritance tree you can avoid casting by including a method that returns a value of the type you would otherwise cast to.
- 20. Avoid expensive data structures Expensive Java data structures can be replaced with simpler ones at the cost of some extra code complexity. For example, it can be up to twice as expensive to access a two-dimensional array as a one-dimensional array, due to the extra indirections.
- 21. Know your switches When the numbers are close together, uses a fast direct lookup. When the numbers are further apart, uses a slower search through a table. This is particularly important if you're trying to replace a sequence of if statements with a switch.
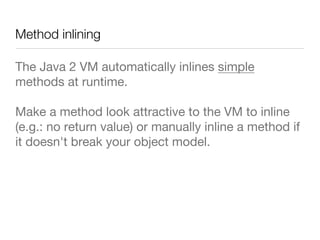
- 22. Method inlining The Java 2 VM automatically inlines simple methods at runtime. Make a method look attractive to the VM to inline (e.g.: no return value) or manually inline a method if it doesn't break your object model.
- 23. Enums Enums are very convenient, but unfortunately can be painful when size and speed matter. On first use, the class initializer invokes the <init> method on objects representing each of the enumerated values. Each object gets its own static field, and the full set is stored in an array (a static field called "$VALUES"). That's a lot of code and data, just for three integers.
- 24. Use Package Scope with Inner Classes Inner class is a totally separate class (behind the scenes). To make direct access to parent class private members, the compiler generates a couple of synthetic methods. The inner-class code calls these static methods whenever it needs to access the private members of enclosing class. Translation: members accessed through accessor methods instead of directly. (accessors are slower than direct field accesses) Remedy: declare members accessed by inner classes to have package scope, rather than private scope. Flip-side: other classes in the same package can access too; runs counter to the standard OO practice.
- 25. Replacing API classes Sometimes API classes do more than you need -with a corresponding increase in execution time You can write specialized versions that do less but run faster.
- 26. Overriding API methods Performance problems with a Java API method? Define a subclass, override that method with your own (hopefully more efficient) version.
- 27. Strength Reduction Use cheaper operations in place of expensive ones. ‣ += instead of ...=...+... result in fewer byte code instructions. ‣ Make a 1D array variable that points to the row, if repeatedly accessing elements in a single row of a 2D array ‣ Shifts instead of multiplication by powers of two ‣ Multiplication instead of exponentiation, etc. / mathematical optimizations of this type generally have little benefit unless you are using a just-in-time compiler /
- 28. Variable allocation For desperate optimizers only. The first four numeric variables or arguments in a method are accessed using via shorter bytecode instructions, although only three are usable in non-static methods. If you declare your most frequently-used variables first (e.g., loop indices), the inner bytecode loops of your methods will be marginally shorter and possibly faster. Note that although the number of bytecodes for the inner loop is the same, the length of the bytecode has decreased.
- 29. Common subexpression elimination If an expensive expression (for example, the result of a method call) is used more than once within a block of code, calculate it once and put it into a temporary variable for subsequent reuse. double d = a * Math.sqrt(c); double tmp = Math.sqrt(c); double e = b * Math.sqrt(c); double d = a * tmp; double e = b * tmp;
- 30. Loop invariant code motion If an expression inside a loop doesn't change after the loop is entered (i.e. it's invariant), calculate the value of the expression outside the loop and assign it to a temporary variable. Then use the temporary variable within the loop. Note that we could also treat array.length as a loop invariant.
- 31. Use the right algorithms & data structures Don't use an O(n2) bubblesort algorithm to sort a thousand elements when there's an O(n log n) quicksort available. Similarly, don't store a thousand items in an array that requires an O(n) search when you could use an O(log n) binary tree, or an O(1) Java hash table.
- 32. Wholesale is Cheaper Perform operations in bulk instead of one at a time. DB access in loop: Optimize SQL to perform in one bulk access (not same as executeBatch() )
- 33. Closing Notes To write good, efficient code: Understand what the code you write really does. Make deliberate choice, not inadvertent side effect: If you really want to allocate an iterator, by all means use enhanced for loop syntax on a List; just make it a deliberate choice. Build performance into your application; then make it better. Always think carefully about what your code is doing, and be on the lookout for ways to speed it up.
- 34. quest for speed continues...
