Automated JavaScript Deobfuscation - PacSec 2007
0 likes1,556 views
This document discusses the need for tools and techniques to analyze malicious web content and JavaScript obfuscation, as more malware is delivered through the web. It describes Websense's approach of emulating a browser without rendering content, to allow pages to decode themselves and log all activity. This includes implementing DOM and JavaScript engines. Their system found over 124,000 infected pages from analyzing 111 million URLs in 24 hours. Limitations and other resources are also outlined.
1 of 35
Downloaded 27 times





![Obfuscation Evolution
String splitting:
“AD” + “ODB.S” + “treAM”
String encoding/escaping:
“%41u0044” + “Ox44%42u002ES” + “t%72eAM”
Closing html tags (e.g. </TEXTAREA>)
Code length dependant obfuscation:
arguments.callee.toString()
Server-side [poly|meta]-morphic obfuscation](https://image.slidesharecdn.com/automatedjavascriptdeobfuscation2007-13443236681677-phpapp02-120807021504-phpapp02/85/Automated-JavaScript-Deobfuscation-PacSec-2007-6-320.jpg)




![Coming At You Like A Spider Monkey
Integrate scripting engine(s) with our DOM to
execute scripts as they are discovered
Scripts are [mostly] safe for execution
Firefox’s SpiderMonkey JavaScript Engine
(MPL/GPL/LGPL)](https://image.slidesharecdn.com/automatedjavascriptdeobfuscation2007-13443236681677-phpapp02-120807021504-phpapp02/85/Automated-JavaScript-Deobfuscation-PacSec-2007-12-320.jpg)





















Ad
Recommended
Dev and Blind - Attacking the weakest Link in IT Security



Dev and Blind - Attacking the weakest Link in IT SecurityMario Heiderich The developer is an easy and valuable target for malicious minds. The reasons for that are numerous and hard to come by. This talk delivers examples, proof, discussion and awkward moments in a pretty special way.
Everybody hates developers – especially web developers. And why not? The cracks and crevices of their APIs and implementations are the reason that vulnerabilities in web applications are still a widespread issue – and will continue to be in the foreseeable future.
Bashing and blaming them for their wrongdoings is fun – boy, they are stupid in their mistakes! But has anyone ever dared to have an open on stage battle with an actual developer?
And who of the developers dares to face their collective nemesis – the attacker? Can there be life where matter and anti-matter collide? We will know about this soon – because this is what this talk is going to be about. Developer versus attacker – vulnerability versus defense. Be prepared for swearing, violence and people leaving the stage prematurely in tears.
Ln monitoring repositories



Ln monitoring repositoriessnyff This document discusses monitoring software repositories to detect security issues. It introduces a tool called SANZARU that analyzes commits to repositories to identify potential bugs and vulnerabilities. SANZARU works by extracting vectors from commit data, training a classifier on past issues, and then classifying new commits. Its goals are to detect security fixes, new vulnerabilities, and interesting new features. The document provides examples of issues SANZARU has found and discusses challenges in commit classification.
Ruxmon cve 2012-2661



Ruxmon cve 2012-2661snyff Louis Nyffenegger discovered a SQL injection vulnerability in ActiveRecord, the ORM used in Ruby on Rails applications. He demonstrated how to exploit it locally by creating two states (true/false) based on the response time of SQL queries with sleep commands. This allowed him to extract data bit-by-bit to retrieve the database version. He then explained how to modify the exploit to send HTTP requests to a remote vulnerable application by properly encoding the injected SQL.
Ruxmon feb 2013 what happened to rails



Ruxmon feb 2013 what happened to railssnyff Louis Nyffenegger gave a talk about the recent vulnerabilities discovered in Ruby on Rails. Several vulnerabilities allowed remote code execution by injecting malicious YAML payloads that were parsed by Rails. These issues arose due to assumptions that Rails was secure, increased scrutiny as its popularity grew, and its flexible parsing of requests. Upgrades and removing unnecessary parsers can help mitigate risks going forward.
I thought you were my friend - Malicious Markup



I thought you were my friend - Malicious MarkupMario Heiderich The document is a transcript from a talk given by Mario Heiderich at the CONFidence 2009 conference. It discusses various ways that malicious code can be embedded in markup and exploited by browsers, including through techniques like inline SVG, XML namespaces, XUL artifacts, and more. It provides examples of actual malicious code and encourages awareness of legacy browser vulnerabilities as new web standards are developed.
HTML5 - The Good, the Bad, the Ugly



HTML5 - The Good, the Bad, the UglyMario Heiderich This document provides an overview of HTML5 including its history, current status, implementation in browsers, and both benefits and security issues. It discusses how HTML5 aims to simplify and enhance usability but also introduces new vulnerabilities due to its dynamic nature forcing rapid implementation. While HTML5 enables rich content and interactivity, its inconsistencies and evolving specifications combined with a rush for browser support has resulted in buggy websites and potential for attacks like hijacking forms, stealing data, and bypassing security restrictions.
Finding Needles in Haystacks



Finding Needles in Haystackssnyff This document summarizes Louis Nyffenegger's talk on code review and capture-the-flag exercises for finding security vulnerabilities. The talk discusses different approaches to code review like grepping for bugs, following user inputs, reviewing functionality, and reading all code. It also provides tips for getting started with capture-the-flag exercises by focusing on weaknesses rather than vulnerabilities and combining issues. An example application is provided for attendees to practice on, and common weaknesses are listed that could lead to vulnerabilities like hardcoded credentials, cross-site scripting, and remote code execution.
The Ultimate IDS Smackdown



The Ultimate IDS SmackdownMario Heiderich This document summarizes a talk given by Gareth Heyes and Mario Heiderich on web security and the PHPIDS project. It describes the early challenges of detecting attacks using simple blacklists and how the project evolved to address increasingly complex obfuscated payloads. Key points discussed include the introduction of a payload canonicalizer to normalize strings before detection, ongoing challenges of new browser behaviors and standards, and the importance of an open community approach to security research.
Generic Attack Detection - ph-Neutral 0x7d8



Generic Attack Detection - ph-Neutral 0x7d8Mario Heiderich Mario Heiderich presents on generic attack detection using PHPIDS. PHPIDS uses 70 regex rules to detect attacks like XSS and SQLi by analyzing user input. It first normalizes the input, then detects patterns through a conversion and detection process, and can log or report any findings. PHPIDS aims to avoid blacklisting traps through this generic approach. Future work may include optimizing existing detection routines and adding more granular analysis techniques.
Owasp tds



Owasp tdssnyff Test-driven security involves writing security-focused test cases to test for vulnerabilities during the development process. This helps enable continuous deployment by ensuring new code does not introduce security bugs. The key aspects discussed are:
1) Having developers or security experts write test cases to validate common vulnerabilities like authentication failures, input validation, and authorization checks.
2) Involving non-technical team members like project managers in writing test cases using plain language to specify scenarios.
3) Integrating security testing into continuous integration pipelines to automatically catch issues during code reviews.
The Future of Web Attacks - CONFidence 2010



The Future of Web Attacks - CONFidence 2010Mario Heiderich This document discusses current and emerging web attacks. It notes that while cross-site scripting (XSS) and SQL injection attacks were once prevalent, modern web applications and browsers incorporate defenses against these attacks. However, the document argues that web applications and browsers are evolving in ways that enable new types of multi-layer attacks. Examples are provided of attacks that combine layers like the database management system, JavaScript execution in browsers, and HTML parsing quirks to bypass defenses. The document urges security researchers and practitioners to consider these evolving attack techniques and the growing diversity of client devices and applications.
Locking the Throne Room - How ES5+ might change views on XSS and Client Side ...



Locking the Throne Room - How ES5+ might change views on XSS and Client Side ...Mario Heiderich This document discusses using ES5 capabilities to help mitigate cross-site scripting (XSS) vulnerabilities. It summarizes the history of JavaScript and XSS, current approaches to mitigation, and limitations. It then proposes using ES5 features like Object.defineProperty to prohibit unauthorized access to DOM properties and add monitoring of property access. This could enable intrusion detection and role-based access control without impedance mismatches. Examples show freezing DOM objects to prevent tampering. Limitations include blacklisting and compatibility issues, but the approach aims to detect and prevent XSS at the client level without server-side filtering.
Locking the Throneroom 2.0



Locking the Throneroom 2.0Mario Heiderich This document summarizes Mario Heiderich's presentation titled "Locking the Throne Room - How ES5+ will change XSS and Client Side Security" given at BlueHat, Redmond 2011. The presentation discusses how new features in ECMAScript 5 (ES5), such as Object.defineProperty(), can be used to prevent cross-site scripting (XSS) attacks by locking down access to sensitive DOM properties and methods on the client-side in a tamper-resistant way. This moves XSS mitigation closer to the client where the attacks occur, avoiding issues caused by impedance mismatches between server-side filters and client-side execution. The approach could allow role-based access control and intrusion
Flash it baby!



Flash it baby!Soroush Dalili This document discusses finding vulnerabilities in SWF (Flash) files. It begins with an introduction to embedding SWF files in HTML and ActionScript versions. It then covers strategies for finding SWF files on websites, as well as types of issues like XSS, data hijacking, and information disclosure. The document provides details on tools for automated and manual testing of SWF files, such as decompiling files, identifying input parameters and sinks, and techniques for bypassing protections.
Defcon CTF quals



Defcon CTF qualssnyff The document discusses preparing for and participating in the Defcon CTF qualifiers. It provides details on:
- Defcon CTF being one of the most prestigious CTF competitions, with only 10 teams qualifying. Teams get a FreeBSD box and must reverse, protect, and attack services. Points are earned through availability, reading other teams' keys, and overwriting keys.
- The qualifiers run from June 3rd to 6th, consisting of 5 categories with 5 progressively unlocked challenges each, over 53 non-stop hours. The scoreboard is a slow Java applet that can be bypassed by reversing the client class.
- One challenge involves a Ruby-based HTTP service with a vulnerable We
Vulnerabilities in data processing levels



Vulnerabilities in data processing levelsbeched This document summarizes potential vulnerabilities in how different layers of a web application process data. It discusses how each layer - including hardware, operating system, browser, network, web server, framework, application and database - accepts inputs and produces outputs that could be leveraged maliciously if not properly validated. Many real-world examples are provided of how inputs passed between layers can bypass validation checks if the layers' data processing rules are not well understood by developers. The key message is that all variables not explicitly set in code should be considered untrusted.
Static analysis for beginners



Static analysis for beginnersAntonio Costa aka Cooler_ This document discusses static analysis for beginners. It describes how to use techniques like deterministic finite automata (DFA) and parsing tools like Flex and Bison to detect issues in source code. It provides an example of using the Re2c tool to generate a lexer for rule-based detection. The document also introduces heap detective, a tool that maps heap memory usage in programs to find issues like memory leaks. Overall, it offers an overview of static analysis concepts and tools while showcasing examples from open source projects.
Abusing Java Remote Interfaces



Abusing Java Remote Interfacesjuanvazquezslides The lecture tries to summarize some interesting Java (remote) attack, and how to check / exploit them with Metasploit. The lecture doesn't focus on client attack vectors, like java sandbox abuses through applets, or click2play bypasses. It focus on remote attack vectors abusing RMI endpoints and technologies using RMI. The lecture won't only summarize some of the popular attack vectors, it also will review how to check/exploit them with Metasploit, presenting new capabilities and modules which are being added to the Metasploit Framework to support all the techniques discussed in the lecture.
Advanced JS Deobfuscation



Advanced JS DeobfuscationMinded Security This document discusses JavaScript deobfuscation techniques using abstract syntax trees (ASTs). It begins by explaining goals of JavaScript obfuscation like blocking reverse engineering and bypassing antivirus detection. Common obfuscation techniques like eval packing and JSFuck are described. The document then discusses approaches to deobfuscation including runtime execution and manual analysis. It focuses on the benefits of partial evaluation using AST traversal and subtree reduction to perform operations like constant folding and function inlining. Examples are provided of challenges in evaluating complex data structures and functions. The conclusion is that AST-based deobfuscation is difficult but can counter some obfuscation techniques through multi-pass analysis and function hoisting.
JavaScript From Hell - CONFidence 2.0 2009



JavaScript From Hell - CONFidence 2.0 2009Mario Heiderich This document summarizes Mario Heiderich's talk on obfuscated JavaScript malware. The talk covered the history of JavaScript and how it has evolved from being frowned upon due to security issues to becoming essential for modern web applications. It then discussed how JavaScript is commonly used in malware through techniques like string obfuscation, eval injection, and hiding payloads in the DOM. The talk concluded by exploring how obfuscation could become even more advanced using new JavaScript features and discussed challenges in detecting obfuscated malware.
Building Advanced XSS Vectors



Building Advanced XSS VectorsRodolfo Assis (Brute) XSS is much more than just <script>alert(1)</script>. Thousands of unique vectors can be built and more complex payloads to evade filters and WAFs. In these slides, cool techniques to bypass them are described, from HTML to javascript. See also http://brutelogic.com.br/blog
Defending against Java Deserialization Vulnerabilities



Defending against Java Deserialization VulnerabilitiesLuca Carettoni Java deserialization vulnerabilities have recently gained popularity due to a renewed interest from the security community. Despite being publicly discussed for several years, a significant number of Java based products are still affected. Whenever untrusted data is used within deserialization methods, an attacker can abuse this simple design anti-pattern to compromise your application. After a quick introduction of the problem, this talk will focus on discovering and defending against deserialization vulnerabilities. I will present a collection of techniques for mitigating attacks when turning off object serialization is not an option, and we will discuss practical recommendations that developers can use to help prevent these attacks.
Let's Talk Technical: Malware Evasion and Detection



Let's Talk Technical: Malware Evasion and DetectionJames Haughom Jr This is from my talk at IR18 geared around evasion techniques employed by malware, and detection methods for incident responders. I touch on everything from ransomware, to evasive fileless WMI malware. My goal for this talk was to teach defenders about the inner-workings and capabilities of malware, as well as some detection methods they may have not considered.
The innerHTML Apocalypse



The innerHTML ApocalypseMario Heiderich This talk introduces and discusses a novel, mostly unpublished technique to successfully attack websites that are applied with state-of-the-art XSS protection. This attack labeled Mutation-XSS (mXSS) is capable of bypassing high-end filter systems by utilizing the browser and its unknown capabilities - every single f***** one of them. We analyzed the type and number of high-profile websites and applications that are affected by this kind of attack. Several live demos during the presentation will share these impressions and help understanding, what mXSS is, why mXSS is possible and why it is of importance for defenders as well as professional attackers to understand and examine mXSS even further. The talk wraps up several years of research on this field, shows the abhorrent findings, discusses the consequences and delivers a step-by-step guide on how to protect against this kind of mayhem - with a strong focus on feasibility and scalability.
The old is new, again. CVE-2011-2461 is back!



The old is new, again. CVE-2011-2461 is back!Luca Carettoni As a part of an ongoing investigation on Adobe Flash SOP bypass techniques, we identified a vulnerability affecting old releases of the Adobe Flex SDK compiler. Further investigation traced the issue back to a well known vulnerability (CVE20112461), already patched by Adobe. Old vulnerability, let's move on? Not this time. CVE20112461 is a very interesting bug. As long as the SWF file was compiled with a vulnerable Flex SDK, attackers can still use this vulnerability against the latest web browsers and Flash plugin. Even with the most recent updates, vulnerable Flex applications hosted on your domain can be exploited. In this presentation, we will disclose the details of this vulnerability (Adobe has never released all technicalities) and we will discuss how we conducted a large scale analysis on popular websites, resulting in the identification of numerous Alexa Top 50 sites vulnerable to this bug. Finally, we will also release a custom tool and a Burp plugin capable of detecting vulnerable SWF applications. If you’re a breaker, you will learn a new technique and enjoy our exploits. If you’re a builder, you will learn how to mitigate this attack. In both cases, you can help us to eradicate CVE20112461. After all, Troopers is about making the world a safer place.
Mauro Gentile, Luca Carettoni
Comparing DOM XSS Tools On Real World Bug



Comparing DOM XSS Tools On Real World BugStefano Di Paola This document compares DOM XSS identification tools by testing them on a real-world DOM XSS vulnerability found on pastebin.com. The vulnerability involves a JavaScript file loaded from an external domain that contains complex code. Most tools had difficulty analyzing this accurately. Runtime tools that use taint analysis were best able to follow the execution flow and identify the vulnerability, while static analyzers struggled with the indirect source and produced false positives or missed it entirely.
In the DOM, no one will hear you scream



In the DOM, no one will hear you screamMario Heiderich The document discusses the history and development of the Document Object Model (DOM) from its early implementations in 1995 to modern standards. It outlines key milestones like DOM Level 1 in 1998, the rise of JavaScript frameworks like Prototype, jQuery and MooTools in 2005-2006, and ongoing work by the W3C and WHATWG. The talk will explore security issues that can arise from the DOM's ability to convert strings to executable code and demonstrate an attack technique called DOM clobbering.
Scriptless Attacks - Stealing the Pie without touching the Sill



Scriptless Attacks - Stealing the Pie without touching the SillMario Heiderich - The document discusses scriptless attacks that can bypass traditional XSS defenses like NoScript and XSS filters by leveraging new HTML5 and CSS features.
- It presents several proof-of-concept attacks including using CSS to steal passwords, using SVG fonts to brute force CSRF tokens, and using custom fonts to leak sensitive information like passwords without using JavaScript.
- The attacks demonstrate that even without scripting, features in HTML5 and CSS can be abused to conduct traditional XSS attacks and undermine security defenses, so more work is needed to protect against side-channels and unwanted data leakage from the browser.
JScrambler Ninja challenge



JScrambler Ninja challengeAlkemiaLabs Online hacking competition sponsored by JScrambler intended to gather developers from around the world to showcase their Javascript skills in browser security and code protection.
Protecting JavaScript source code using obfuscation - OWASP Europe Tour 2013 ...



Protecting JavaScript source code using obfuscation - OWASP Europe Tour 2013 ...AuditMark The goal of code obfuscation is to delay the understanding of what a program does. It can be used, for example, in scenarios where the code contains Intellectual Property (algorithms) or when the owner wants to prevent a competitor for stealing and reusing the code. To achieve it, an obfuscation transformation translates easy to understand code into a much harder to understand form. But in order to be resilient, obfuscation transformations need also to resist automatic reversal performed using static or dynamic code analysis techniques. This presentation focuses on the specific case of JavaScript source obfuscation, main usage cases, presents some obfuscation examples and their value in providing real protection against reverse-engineering.
Ad
More Related Content
What's hot (20)
Generic Attack Detection - ph-Neutral 0x7d8



Generic Attack Detection - ph-Neutral 0x7d8Mario Heiderich Mario Heiderich presents on generic attack detection using PHPIDS. PHPIDS uses 70 regex rules to detect attacks like XSS and SQLi by analyzing user input. It first normalizes the input, then detects patterns through a conversion and detection process, and can log or report any findings. PHPIDS aims to avoid blacklisting traps through this generic approach. Future work may include optimizing existing detection routines and adding more granular analysis techniques.
Owasp tds



Owasp tdssnyff Test-driven security involves writing security-focused test cases to test for vulnerabilities during the development process. This helps enable continuous deployment by ensuring new code does not introduce security bugs. The key aspects discussed are:
1) Having developers or security experts write test cases to validate common vulnerabilities like authentication failures, input validation, and authorization checks.
2) Involving non-technical team members like project managers in writing test cases using plain language to specify scenarios.
3) Integrating security testing into continuous integration pipelines to automatically catch issues during code reviews.
The Future of Web Attacks - CONFidence 2010



The Future of Web Attacks - CONFidence 2010Mario Heiderich This document discusses current and emerging web attacks. It notes that while cross-site scripting (XSS) and SQL injection attacks were once prevalent, modern web applications and browsers incorporate defenses against these attacks. However, the document argues that web applications and browsers are evolving in ways that enable new types of multi-layer attacks. Examples are provided of attacks that combine layers like the database management system, JavaScript execution in browsers, and HTML parsing quirks to bypass defenses. The document urges security researchers and practitioners to consider these evolving attack techniques and the growing diversity of client devices and applications.
Locking the Throne Room - How ES5+ might change views on XSS and Client Side ...



Locking the Throne Room - How ES5+ might change views on XSS and Client Side ...Mario Heiderich This document discusses using ES5 capabilities to help mitigate cross-site scripting (XSS) vulnerabilities. It summarizes the history of JavaScript and XSS, current approaches to mitigation, and limitations. It then proposes using ES5 features like Object.defineProperty to prohibit unauthorized access to DOM properties and add monitoring of property access. This could enable intrusion detection and role-based access control without impedance mismatches. Examples show freezing DOM objects to prevent tampering. Limitations include blacklisting and compatibility issues, but the approach aims to detect and prevent XSS at the client level without server-side filtering.
Locking the Throneroom 2.0



Locking the Throneroom 2.0Mario Heiderich This document summarizes Mario Heiderich's presentation titled "Locking the Throne Room - How ES5+ will change XSS and Client Side Security" given at BlueHat, Redmond 2011. The presentation discusses how new features in ECMAScript 5 (ES5), such as Object.defineProperty(), can be used to prevent cross-site scripting (XSS) attacks by locking down access to sensitive DOM properties and methods on the client-side in a tamper-resistant way. This moves XSS mitigation closer to the client where the attacks occur, avoiding issues caused by impedance mismatches between server-side filters and client-side execution. The approach could allow role-based access control and intrusion
Flash it baby!



Flash it baby!Soroush Dalili This document discusses finding vulnerabilities in SWF (Flash) files. It begins with an introduction to embedding SWF files in HTML and ActionScript versions. It then covers strategies for finding SWF files on websites, as well as types of issues like XSS, data hijacking, and information disclosure. The document provides details on tools for automated and manual testing of SWF files, such as decompiling files, identifying input parameters and sinks, and techniques for bypassing protections.
Defcon CTF quals



Defcon CTF qualssnyff The document discusses preparing for and participating in the Defcon CTF qualifiers. It provides details on:
- Defcon CTF being one of the most prestigious CTF competitions, with only 10 teams qualifying. Teams get a FreeBSD box and must reverse, protect, and attack services. Points are earned through availability, reading other teams' keys, and overwriting keys.
- The qualifiers run from June 3rd to 6th, consisting of 5 categories with 5 progressively unlocked challenges each, over 53 non-stop hours. The scoreboard is a slow Java applet that can be bypassed by reversing the client class.
- One challenge involves a Ruby-based HTTP service with a vulnerable We
Vulnerabilities in data processing levels



Vulnerabilities in data processing levelsbeched This document summarizes potential vulnerabilities in how different layers of a web application process data. It discusses how each layer - including hardware, operating system, browser, network, web server, framework, application and database - accepts inputs and produces outputs that could be leveraged maliciously if not properly validated. Many real-world examples are provided of how inputs passed between layers can bypass validation checks if the layers' data processing rules are not well understood by developers. The key message is that all variables not explicitly set in code should be considered untrusted.
Static analysis for beginners



Static analysis for beginnersAntonio Costa aka Cooler_ This document discusses static analysis for beginners. It describes how to use techniques like deterministic finite automata (DFA) and parsing tools like Flex and Bison to detect issues in source code. It provides an example of using the Re2c tool to generate a lexer for rule-based detection. The document also introduces heap detective, a tool that maps heap memory usage in programs to find issues like memory leaks. Overall, it offers an overview of static analysis concepts and tools while showcasing examples from open source projects.
Abusing Java Remote Interfaces



Abusing Java Remote Interfacesjuanvazquezslides The lecture tries to summarize some interesting Java (remote) attack, and how to check / exploit them with Metasploit. The lecture doesn't focus on client attack vectors, like java sandbox abuses through applets, or click2play bypasses. It focus on remote attack vectors abusing RMI endpoints and technologies using RMI. The lecture won't only summarize some of the popular attack vectors, it also will review how to check/exploit them with Metasploit, presenting new capabilities and modules which are being added to the Metasploit Framework to support all the techniques discussed in the lecture.
Advanced JS Deobfuscation



Advanced JS DeobfuscationMinded Security This document discusses JavaScript deobfuscation techniques using abstract syntax trees (ASTs). It begins by explaining goals of JavaScript obfuscation like blocking reverse engineering and bypassing antivirus detection. Common obfuscation techniques like eval packing and JSFuck are described. The document then discusses approaches to deobfuscation including runtime execution and manual analysis. It focuses on the benefits of partial evaluation using AST traversal and subtree reduction to perform operations like constant folding and function inlining. Examples are provided of challenges in evaluating complex data structures and functions. The conclusion is that AST-based deobfuscation is difficult but can counter some obfuscation techniques through multi-pass analysis and function hoisting.
JavaScript From Hell - CONFidence 2.0 2009



JavaScript From Hell - CONFidence 2.0 2009Mario Heiderich This document summarizes Mario Heiderich's talk on obfuscated JavaScript malware. The talk covered the history of JavaScript and how it has evolved from being frowned upon due to security issues to becoming essential for modern web applications. It then discussed how JavaScript is commonly used in malware through techniques like string obfuscation, eval injection, and hiding payloads in the DOM. The talk concluded by exploring how obfuscation could become even more advanced using new JavaScript features and discussed challenges in detecting obfuscated malware.
Building Advanced XSS Vectors



Building Advanced XSS VectorsRodolfo Assis (Brute) XSS is much more than just <script>alert(1)</script>. Thousands of unique vectors can be built and more complex payloads to evade filters and WAFs. In these slides, cool techniques to bypass them are described, from HTML to javascript. See also http://brutelogic.com.br/blog
Defending against Java Deserialization Vulnerabilities



Defending against Java Deserialization VulnerabilitiesLuca Carettoni Java deserialization vulnerabilities have recently gained popularity due to a renewed interest from the security community. Despite being publicly discussed for several years, a significant number of Java based products are still affected. Whenever untrusted data is used within deserialization methods, an attacker can abuse this simple design anti-pattern to compromise your application. After a quick introduction of the problem, this talk will focus on discovering and defending against deserialization vulnerabilities. I will present a collection of techniques for mitigating attacks when turning off object serialization is not an option, and we will discuss practical recommendations that developers can use to help prevent these attacks.
Let's Talk Technical: Malware Evasion and Detection



Let's Talk Technical: Malware Evasion and DetectionJames Haughom Jr This is from my talk at IR18 geared around evasion techniques employed by malware, and detection methods for incident responders. I touch on everything from ransomware, to evasive fileless WMI malware. My goal for this talk was to teach defenders about the inner-workings and capabilities of malware, as well as some detection methods they may have not considered.
The innerHTML Apocalypse



The innerHTML ApocalypseMario Heiderich This talk introduces and discusses a novel, mostly unpublished technique to successfully attack websites that are applied with state-of-the-art XSS protection. This attack labeled Mutation-XSS (mXSS) is capable of bypassing high-end filter systems by utilizing the browser and its unknown capabilities - every single f***** one of them. We analyzed the type and number of high-profile websites and applications that are affected by this kind of attack. Several live demos during the presentation will share these impressions and help understanding, what mXSS is, why mXSS is possible and why it is of importance for defenders as well as professional attackers to understand and examine mXSS even further. The talk wraps up several years of research on this field, shows the abhorrent findings, discusses the consequences and delivers a step-by-step guide on how to protect against this kind of mayhem - with a strong focus on feasibility and scalability.
The old is new, again. CVE-2011-2461 is back!



The old is new, again. CVE-2011-2461 is back!Luca Carettoni As a part of an ongoing investigation on Adobe Flash SOP bypass techniques, we identified a vulnerability affecting old releases of the Adobe Flex SDK compiler. Further investigation traced the issue back to a well known vulnerability (CVE20112461), already patched by Adobe. Old vulnerability, let's move on? Not this time. CVE20112461 is a very interesting bug. As long as the SWF file was compiled with a vulnerable Flex SDK, attackers can still use this vulnerability against the latest web browsers and Flash plugin. Even with the most recent updates, vulnerable Flex applications hosted on your domain can be exploited. In this presentation, we will disclose the details of this vulnerability (Adobe has never released all technicalities) and we will discuss how we conducted a large scale analysis on popular websites, resulting in the identification of numerous Alexa Top 50 sites vulnerable to this bug. Finally, we will also release a custom tool and a Burp plugin capable of detecting vulnerable SWF applications. If you’re a breaker, you will learn a new technique and enjoy our exploits. If you’re a builder, you will learn how to mitigate this attack. In both cases, you can help us to eradicate CVE20112461. After all, Troopers is about making the world a safer place.
Mauro Gentile, Luca Carettoni
Comparing DOM XSS Tools On Real World Bug



Comparing DOM XSS Tools On Real World BugStefano Di Paola This document compares DOM XSS identification tools by testing them on a real-world DOM XSS vulnerability found on pastebin.com. The vulnerability involves a JavaScript file loaded from an external domain that contains complex code. Most tools had difficulty analyzing this accurately. Runtime tools that use taint analysis were best able to follow the execution flow and identify the vulnerability, while static analyzers struggled with the indirect source and produced false positives or missed it entirely.
In the DOM, no one will hear you scream



In the DOM, no one will hear you screamMario Heiderich The document discusses the history and development of the Document Object Model (DOM) from its early implementations in 1995 to modern standards. It outlines key milestones like DOM Level 1 in 1998, the rise of JavaScript frameworks like Prototype, jQuery and MooTools in 2005-2006, and ongoing work by the W3C and WHATWG. The talk will explore security issues that can arise from the DOM's ability to convert strings to executable code and demonstrate an attack technique called DOM clobbering.
Scriptless Attacks - Stealing the Pie without touching the Sill



Scriptless Attacks - Stealing the Pie without touching the SillMario Heiderich - The document discusses scriptless attacks that can bypass traditional XSS defenses like NoScript and XSS filters by leveraging new HTML5 and CSS features.
- It presents several proof-of-concept attacks including using CSS to steal passwords, using SVG fonts to brute force CSRF tokens, and using custom fonts to leak sensitive information like passwords without using JavaScript.
- The attacks demonstrate that even without scripting, features in HTML5 and CSS can be abused to conduct traditional XSS attacks and undermine security defenses, so more work is needed to protect against side-channels and unwanted data leakage from the browser.
Viewers also liked (20)
JScrambler Ninja challenge



JScrambler Ninja challengeAlkemiaLabs Online hacking competition sponsored by JScrambler intended to gather developers from around the world to showcase their Javascript skills in browser security and code protection.
Protecting JavaScript source code using obfuscation - OWASP Europe Tour 2013 ...



Protecting JavaScript source code using obfuscation - OWASP Europe Tour 2013 ...AuditMark The goal of code obfuscation is to delay the understanding of what a program does. It can be used, for example, in scenarios where the code contains Intellectual Property (algorithms) or when the owner wants to prevent a competitor for stealing and reusing the code. To achieve it, an obfuscation transformation translates easy to understand code into a much harder to understand form. But in order to be resilient, obfuscation transformations need also to resist automatic reversal performed using static or dynamic code analysis techniques. This presentation focuses on the specific case of JavaScript source obfuscation, main usage cases, presents some obfuscation examples and their value in providing real protection against reverse-engineering.
Ajit-Legiment_Techniques



Ajit-Legiment_Techniquesguest66dc5f This document discusses and compares classical and legitimate techniques for evading intrusion detection and prevention systems. It provides examples of using legitimate techniques like altering the command sequence and exploiting flaws to evade detection of an attack on the Microsoft Exchange Server vulnerability MS03-046. Legitimate techniques are more effective than classical methods at evading IPS/IDS because they focus on exploiting weaknesses in how the applications and protocols are analyzed rather than just obscuring network traffic patterns.
The (In)Security of Topology Discovery in Software Defined Networks



The (In)Security of Topology Discovery in Software Defined NetworksTalal Alharbi Topology Discovery is an essential service in Soft-
ware Defined Networks (SDN). Most SDN controllers use a de-
facto standard topology discovery mechanism based on OpenFlow
to identify active links in the network. This paper discusses the
security, or rather lack thereof, of the current SDN topology
discovery mechanism, and its vulnerability to link spoofing
attacks. The feasibility and impact of the attacks are verified and
demonstrated via experiments. The paper presents and evaluates
a countermeasure based on HMAC authentication.
VMRay intro video



VMRay intro videoChad Loeven VMRay Analyzer is a hypervisor-based threat detection solution that provides best-in-class analysis of malware and targeted attacks. It utilizes full hypervisor integration to allow for high performance, scalable analysis that is resistant to detection and evasion techniques. VMRay's approach leverages the hypervisor to monitor all activity within virtual machines and detect advanced persistent threats and targeted attacks that other tools may miss.
Welcome to the United States: An Acculturation Conversation



Welcome to the United States: An Acculturation ConversationSuzanne M. Sullivan This document provides an overview of a program to help prepare expatriates for living and working in the United States. The program covers understanding American culture, communicating effectively, doing business, and living in the US. It discusses American values, history, regions, diversity, and current issues. Tips are provided for adapting to a new culture and building intercultural skills to enhance work and life abroad. The objectives are to develop cultural self-awareness, knowledge of American culture, and strategies for bridging cultural differences.
Code obfuscation, php shells & more



Code obfuscation, php shells & moreMattias Geniar Code Obfuscation, PHP shells & more
What hackers do once they get passed your code - and how you can detect & fix it.
Content:
- What happens when I get hacked?
- What's code obfuscation?
- What are PHP shells?
- Show me some clever hacks!
- Prevention
- Post-hack cleanup
What is this not about:
- How can I hack a website?
- How can I DoS a website?
- How can I find my insecure code?
A combined approach to search for evasion techniques in network intrusion det...



A combined approach to search for evasion techniques in network intrusion det...eSAT Journals Abstract Network Intrusion Detection Systems (NIDS) whose base is signature, works on the signature of attacks. They must be updated quickly in order to prevent the system from new attacks. The attacker finds out new evasion techniques so that he should remain undetected. As the new evasion techniques are being developed it becomes difficult for NIDS to give accurate results and NIDS may fail. The key aspect of our paper is to develop a network intrusion detection system using C4.5 algorithm where Adaboost algorithm is used to classify the packet as normal packet or attack packet and also to further classify different types of attack. Apriori algorithm is used to find real time evasion and to generate rules to find intrusion These rules are further given as input to Snort intrusion detection system for detecting different attacks. Keywords: NIDS, Evasion, Apriori Algorithm, Adaboost Algorithm, Snort
Practical IoT Exploitation (DEFCON23 IoTVillage) - Lyon Yang



Practical IoT Exploitation (DEFCON23 IoTVillage) - Lyon YangLyon Yang This is a light training/presentation talk.
My name is Lyon Yang and I am an IoT hacker. I live in sunny Singapore where IoT is rapidly being deployed – in production. This walkthrough will aim to shed light on the subject of IoT, from finding vulnerabilities in IoT devices to getting shiny hash prompts.
Our journey starts with a holistic view of IoT security, the issues faced by IoT devices and the common mistakes made by IoT developers. Things will then get technical as we progress into a both ARM and MIPS exploitation, followed by a ‘hack-along-with-us’ workshop where you will be exploiting a commonly found IoT daemon. If you are new to IoT or a seasoned professional you will likely learn something new in this workshop.
https://www.iotvillage.org/#schedule
Topics in network security



Topics in network securityNasir Bhutta This document discusses various topics related to network security including Secure Socket Layer/Transport Layer Security (SSL/TLS), Virtual Private Network (VPN), firewall, malware analysis, penetration testing, and digital forensics. SSL/TLS provides security at the transport and session layers. A VPN extends private networks across public networks like the internet. Firewalls control incoming and outgoing network traffic based on rules. Malware analysis involves reverse engineering malware to understand its capabilities and behavior. Penetration testing involves authorized hacking to test security. Digital forensics applies scientific principles to the collection, examination, and analysis of digital evidence.
Bsides to 2016-penetration-testing



Bsides to 2016-penetration-testingHaydn Johnson This talk covers the Penetration Testing Execution Standard and how it differs from the standard Vulnerability Assessment.
SENIOR MATERIAL ENGINEER WITH 5 YEARS OF EXPERIENCE



SENIOR MATERIAL ENGINEER WITH 5 YEARS OF EXPERIENCESangeetha Sankaramahadev R. S. Sangeetha is seeking a dynamic and challenging role in engineering that offers career growth. She has a BE in Electronics and Instrumentation from Thangavelu Engineering College with 7 years of experience. She currently works as a Senior Material Engineer at Infoplus Technologies where she analyzes materials, monitors inventory, and coordinates with vendors. Prior, she worked as a CAD instructor and Electronics Engineer. She has expertise in master data management and handling projects for various companies.
Web attacks using obfuscated script



Web attacks using obfuscated scriptAmol Kamble Code obfuscation techniques make code unintelligible or hard to understand. They are used by software companies to protect intellectual property and by malicious actors to avoid detection from antivirus software. The document discusses different obfuscation techniques like randomization, data encoding, and logic structure obfuscation. It also covers how obfuscated scripts can be used by attackers for information loss, downloading malware, or redirecting users to malicious sites. Antivirus software tries to detect obfuscated malware using techniques like signature matching, emulation, and analyzing script behavior after deobfuscation.
On deobfuscation in practice



On deobfuscation in practiceDmitry Schelkunov The document discusses code obfuscation techniques used to protect software from piracy and malware analysis, and methods for deobfuscation. It covers common obfuscation techniques like code virtualization, code morphing, and opaque predicates. It then introduces the Ariadne engine, which can deobfuscate virtualized and morphed code using its emulator-based AIR Wave Deobfuscation Technology to calculate variable values and determine code flow. Test results showed Ariadne can effectively deobfuscate code protected by many obfuscators and protectors.
Purple teaming Cyber Kill Chain



Purple teaming Cyber Kill ChainHaydn Johnson This is the slide deck from a presention for SecTor 2016.
I spoke with Chris Gates @carnal0wnage.
The outline is:
Purple Teaming is conducting focused Red Teams with clear training objectives for the Blue Team for the ultimate goal of improving the organization’s overall security posture. The popular opinion is that Purple Teaming requires a big undertaking. This is not true and we will show practical exercises for Purple Teaming for varying levels of organizational maturity using the Cyber Kill Chain[1] as our framework.
Code obfuscation



Code obfuscationAmol Kamble This document discusses code obfuscation techniques used to protect intellectual property and hide malicious code. It describes general obfuscation methods like control transformations, computation transformations, and data abstraction obfuscation. Specific techniques are outlined like opaque predicates, inheritance modifications, variable splitting, and method inlining/cloning. Code obfuscation aims to complicate reverse engineering but cannot completely prevent it, and it decreases performance. When used judiciously, obfuscation provides some protection against theft and malware insertion.
Penetration testing dont just leave it to chance



Penetration testing dont just leave it to chanceDr. Anish Cheriyan (PhD) This presentation talks about the focus towards building security in the software development life cycle and covers details related to Reconnaissance, Scanning and Attack based test design and execution approach.
Syllabus Advanced Exploit Development 22-23 June 2013



Syllabus Advanced Exploit Development 22-23 June 2013Dan H Syllabus advanced exploit development
22-23 June 2013
- Fuzzing
- Direct Return
- Smashing Stack
- Bypass mitigation
1. ASLR (Address space layout randomization)
2. SEH (Structured Exception Handling)
3. Safe SEH (Safe Structured Exception Handling)
4. DEP (Data Execution Prevention)
Hari kedua (windows exploit) lebih mantab bro
- Heap spray
- Web browser exploitation (exploit writing for web browser)
- Metasploit Module Development
- Denial Of Service using buffer overflow vulnerability
- Shellcode Development
- Shellcode Injection
- Reporting
www.hatsecure.com
Combat the Latest Two-Factor Authentication Evasion Techniques



Combat the Latest Two-Factor Authentication Evasion TechniquesIBM Security In the wake of 2005 FFIEC regulation calling for stronger security methods, financial institutions have adopted two-factor authentication (2FA) as a means to mitigate online fraud.
Historically 2FA measures such as security questions, one time passwords, physical tokens, SMS authentications and USB tokens have been able to effectively stop fraud attacks. However, in the fast paced arms race that is the war against financial crime, cybercriminals are starting to take the upper hand by developing increasingly sophisticated techniques that bypass 2FA.
In this presentation, Ori Bach, Senior Security Strategist at IBM Trusteer demonstrates several of the 2FA beating techniques and explains how cybercriminals:
- Highjack authenticated banking sessions by directly taking over victims computers
- Make use fake overlay messages to trick victims to surrender their tokens
- Beat one time passwords sent to mobile devices
- Purchase fraud tool-kits to bypass 2FA
View the on-demand recording: https://attendee.gotowebinar.com/recording/6080887905844019714
Penetration Testing 



Penetration Testing RomSoft SRL Penetration testing is used to test the security of a website by simulating real attacks from outside. It identifies potential vulnerabilities to prevent harmful attacks. By understanding how attacks work, the IT team can fix issues and prevent larger attacks in the future. The presentation will demonstrate a penetration testing tool that checks the login page for security issues like authentication, redirects, and hidden code. Contact information is provided for any additional questions.
Ad
Similar to Automated JavaScript Deobfuscation - PacSec 2007 (20)
Sandboxing JS and HTML. A lession Learned



Sandboxing JS and HTML. A lession LearnedMinded Security == Abstract ==
Presented at Analysis of Security APIs
Satellite workshop of IEEE CSF
July 13th 2015, Verona, Italy
http://www.dsi.unive.it/~focardi/ASA8/#program
Browsers HTML sandbox is, by default, only protected by the "Same Origin Policy". Although this simple constraint gave companies a very flexible environment to play with, and was probably one of the key features that led the Web to success as we see it now, it is quite unsatisfactory from a security perspective. In fact, this solution does not face the problem of letting third party code access the whole data in the DOM when explicitly loaded and executed by the browser. This behaviour opens the door to malicious third party code attacks that can be achieved using either Cross Site Scripting (OWASP Top Ten Security risk #1 for many years) or second order attacks, such as malvertising software. In the past, several attempts to sandbox untrusted code have been made. In this talk we will focus on successes and failures of the most interesting open source sandboxing browser techniques.
Thug: a new low-interaction honeyclient



Thug: a new low-interaction honeyclientAngelo Dell'Aera Thug is a new low-interaction honeyclient for analyzing malicious web content and browser exploitation. It uses the Google V8 JavaScript engine and emulates different browser personalities to detect exploits. Thug analyzes content using static and dynamic analysis and logs results using MAEC format. Future work includes improving DOM emulation and JavaScript analysis to better identify vulnerabilities and exploit kits. The source code for Thug will be publicly released after the presentation.
Cross site scripting



Cross site scriptingDilan Warnakulasooriya Myself and Asanka Fernandopulle conducted corporate level workshop on Application Security. This workshop covered areas such as application security treats, secure cording practices, application penetration testing and web application exploitations. Workshop mainly consisted with practical sessions and demonstrations. You can find all the presentations here.
.Net Debugging Techniques



.Net Debugging TechniquesBala Subra The document discusses various .NET debugging techniques, including:
1. The importance of debugging and the tools available for debugging .NET applications, such as Visual Studio and Debugging Tools for Windows.
2. Basic debugging tasks like setting breakpoints, stepping through code, and examining variables and call stacks.
3. Advanced techniques like debugging managed code, threads, and memory issues.
.NET Debugging Tips and Techniques



.NET Debugging Tips and TechniquesBala Subra Debugging is an important part of the software development process that helps developers write more reliable code. There are several tools available for debugging .NET applications, including Visual Studio and Debugging Tools for Windows. Some basic debugging tasks involve setting breakpoints, stepping through code, examining variables and call stacks, and understanding memory usage and threads. Postmortem debugging techniques like dump file analysis can help debug problems that occur in production environments where live debugging is not possible.
Intro to mobile web application development



Intro to mobile web application developmentzonathen Learn all the basics of web app development including bootstrap, handlebars templates, jquery and angularjs, as well as using hybrid app deployment on a phone.
Medium Trust for Umbraco



Medium Trust for UmbracoWarren Buckley Benjamin Howarth from Code Gecko Developments discussed running Umbraco in shared hosting and what the benefits mean for businesses (both small and large) and developers.
XSS Primer - Noob to Pro in 1 hour



XSS Primer - Noob to Pro in 1 hoursnoopythesecuritydog This document provides an introduction to cross-site scripting (XSS) attacks over the course of one hour. It defines XSS and its different types (reflected, stored, DOM), discusses common injection points and payloads, and techniques for bypassing filters including encoding, evasion tricks, and tools. The goal is to teach novices the basics needed to find and exploit XSS vulnerabilities, with tips on contexts, detection, encoding, and actual attack vectors like cookie stealing.
How We Analyzed 1000 Dumps in One Day - Dina Goldshtein, Brightsource - DevOp...



How We Analyzed 1000 Dumps in One Day - Dina Goldshtein, Brightsource - DevOp...DevOpsDays Tel Aviv The document describes BrightSource Energy's process for analyzing crash dumps from their solar power plant control software. Originally, crashes were analyzed manually using debuggers like Visual Studio, which could take 10 minutes per dump and there were often dozens of dumps per day. They developed an automatic analysis workflow using the ClrMD NuGet package to analyze dumps. The script uses ClrMD to find the exception, call stack, and faulty component in each dump. It then alerts the relevant owner and creates a ticket in Redmine. This reduced analysis time from hours to seconds and allowed them to analyze around 1000 dumps in a single day.
Production Debugging at Code Camp Philly



Production Debugging at Code Camp PhillyBrian Lyttle This document provides an introduction to production debugging techniques. It discusses monitoring tools like Task Manager and Performance Monitor, debugging fundamentals like stack traces and crash dumps, protocol analysis, and remote debugging. The goal is to help developers effectively debug problems in production environments using tools that don't require a development workstation.
[CB16] Electron - Build cross platform desktop XSS, it’s easier than you thin...![[CB16] Electron - Build cross platform desktop XSS, it’s easier than you thin...](https://cdn.slidesharecdn.com/ss_thumbnails/cb16hasegawaen-161109050843-thumbnail.jpg?width=560&fit=bounds)
![[CB16] Electron - Build cross platform desktop XSS, it’s easier than you thin...](https://cdn.slidesharecdn.com/ss_thumbnails/cb16hasegawaen-161109050843-thumbnail.jpg?width=560&fit=bounds)
![[CB16] Electron - Build cross platform desktop XSS, it’s easier than you thin...](https://cdn.slidesharecdn.com/ss_thumbnails/cb16hasegawaen-161109050843-thumbnail.jpg?width=560&fit=bounds)
![[CB16] Electron - Build cross platform desktop XSS, it’s easier than you thin...](https://cdn.slidesharecdn.com/ss_thumbnails/cb16hasegawaen-161109050843-thumbnail.jpg?width=560&fit=bounds)
[CB16] Electron - Build cross platform desktop XSS, it’s easier than you thin...CODE BLUE Electron is a framework to create the desktop application on Windows,OS X, Linux easily, and it has been used to develop the popular applications such as Atom Editor, Visual Studio Code, and Slack.
Although Electron includes Chromium and node.js and allow the web application developers to be able to develop the desktop application with accustomed methods, it contains a lot of security problems such as it allows arbitrary code execution if even one DOM-based XSS exist in the application. In fact, a lot of vulnerabilities which is able to load arbitrary code in applications made with Electron have been detected and reported.
In this talk, I focus on organize and understand the security problems which tend to occur on development using Electron.
--- Yosuke Hasegawa
Secure Sky Technology Inc, Technical Adviser. Known for finding numerous vulnerablities in Internet Explorer、Mozilla Firefox and other web applications.He has also presented at Black Hat Japan 2008, South Korea POC 2008, 2010 and others.
OWASP Kansai Chapter Leader, OWASP Japan Board member.
MunichJS - 2011-04-06



MunichJS - 2011-04-06Mike West Presentation to Munich JS on 2011-04-06: covers the Munich Chrome team's privacy efforts, and argues that IndexedDB is a better mechanism than localStorage for applications of any real complexity.
HTML version up at http://20110406-munichjs.appspot.com/
C# Security Testing and Debugging



C# Security Testing and DebuggingRich Helton This document discusses various tools and techniques for security testing and debugging web applications developed in C#. It provides information on static analysis tools like FxCop and CAT.NET that can analyze source code. It also covers automated testing tools like NUnit, HTMLUnit, and Selenium that can test web applications without using a real browser. The document demonstrates how to integrate these tools into testing workflows and addresses related topics like logging, exception handling, and custom error pages.
IDA Vulnerabilities and Bug Bounty by Masaaki Chida



IDA Vulnerabilities and Bug Bounty by Masaaki ChidaCODE BLUE IDA Pro is an advanced disassembler software and often used in vulnerability research and malware analysis. IDA Pro is used to analyse software behavior in detail, if there was a vulnerability and the user is attacked not only can it have impact in a social sense but also impact legal proceedings. In this presentation I will discuss the vulnerabilities found and attacks leveraging the vulnerabilities and Hex-rays's remediation process and dialogue I had with them.
http://codeblue.jp/en-speaker.html#MasaakiChida
EN - BlackHat US 2009 favorite XSS Filters-IDS and how to attack them.pdf



EN - BlackHat US 2009 favorite XSS Filters-IDS and how to attack them.pdfGiorgiRcheulishvili This document discusses various cross-site scripting (XSS) evasion techniques and evaluates the effectiveness of popular XSS filters and intrusion detection systems (IDS), including ModSecurity, PHP-IDS, and Internet Explorer 8. It provides examples of how attacks can bypass these defenses by exploiting Unicode encoding, HTML/JavaScript tricks, and other methods. The author argues that most filters are ineffective at blocking all XSS variations and recommends ways to strengthen XSS filtering.
Introduction to Node.js



Introduction to Node.jsAaron Rosenberg Node.js is a JavaScript runtime built on Chrome's V8 JavaScript engine. It allows JavaScript to be run on the server-side and is well-suited for real-time, event-driven applications due to its asynchronous and non-blocking I/O model. It was created in 2009 by Ryan Dahl who was frustrated by the limitations of JavaScript in the server-side. Node.js uses an event loop that handles asynchronous callbacks and a single thread model to achieve scalable performance. Many large companies like Uber, LinkedIn, and Netflix use Node.js for applications that require real-time features or high throughput.
Beyond HTML: Tools for Building Web 2.0 Apps



Beyond HTML: Tools for Building Web 2.0 AppsMarcos Caceres A simple introduction to the main kinds of "Web 2.0" Apps, and some of the tools a developer can use to build them.
DotNet Introduction



DotNet IntroductionWei Sun The document discusses various topics related to .NET Framework and C#. It provides definitions of concepts like framework, CLR, and comparisons between C# and other languages. It also includes code examples in C# and Java for calculating directory size recursively. Quizzes are included to test understanding.
(In)Security Implication in the JS Universe



(In)Security Implication in the JS UniverseStefano Di Paola JavaScript is the most widely used language cross platforms. This talk will analyze the security concerns from past to present with a peek to the future of this important language. This talk was presented as Keynote at CyberCamp Espana 2014.
Web security: Securing Untrusted Web Content in Browsers



Web security: Securing Untrusted Web Content in BrowsersPhú Phùng This document summarizes a seminar on securing untrusted web content at browsers. It discusses how 92% of websites use JavaScript, which can pose security issues if third-party scripts are malicious or compromised. The seminar presents an approach using lightweight self-protecting JavaScript that enforces security policies without browser modifications. This is done by sandboxing untrusted code execution and intercepting API calls according to enforcement rules defined in policy files. Real-world attacks are also examined that were carried out by injecting malicious code into third-party scripts on major websites.
Ad
More from Stephan Chenette (11)
Landing on Jupyter



Landing on JupyterStephan Chenette Jupyter notebooks can be a valuable tool for data-driven storytelling in security operations. They allow presenting real-time insights in a sequential narrative format, unlike static presentations. Examples shown include using notebooks to: (1) demonstrate current security posture against threats and identify gaps to obtain budget support; (2) provide detection coverage details to operations to improve security; and (3) prove improvement over time while highlighting remaining gaps. Notebooks anticipate questions, incorporate visual data, and enable credible, evidence-based decision making for improved security.
2013 Toorcon San Diego Building Custom Android Malware for Penetration Testing



2013 Toorcon San Diego Building Custom Android Malware for Penetration TestingStephan Chenette In this presentation Stephan will discuss some recent research that emerged he was asked to build malicious applications that bypassed custom security controls. He will walk through some of the basics of reversing malicious apps for android as well as common android malware techniques and methodologies. From the analysis of the wild android malware, he will discuss techniques and functionality to include when penetration testing against 3rd-party android security controls.
BIO
Stephan Chenette is the Director of Security Research and Development at IOActive where he conducts ongoing research to support internal and external security initiatives within the IOActive Labs. Stephan has been in involved in security research for the last 10 years and has presented at numerous conferences including: Blackhat, CanSecWest, RSA, EkoParty, RECon, AusCERT, ToorCon, SecTor, SOURCE, OWASP, B-Sides and PacSec. His specialty is in writing research tools for both the offensive and defensive front as well as investigating next generation emerging threats. He has released public analyses on various vulnerabilities and malware. Prior to joining IOActive, Stephan was the head security researcher at Websense for 6 years and a security software engineer for 4 years working in research and product development at eEye Digital Security.
Building Custom Android Malware BruCON 2013



Building Custom Android Malware BruCON 2013Stephan Chenette An expert in custom Android malware for penetration testing discussed building custom malware to bypass security controls. The speaker outlined their methodology which included researching existing malware techniques, probing the environment, uploading unmodified malware, and creating altered versions to evade detection. The talk covered functionality like autostarting, collecting device data, and communicating with command and control servers. Various scenarios were proposed like using vulnerable libraries or requesting all permissions to test security controls.
B-Sides Seattle 2012 Offensive Defense



B-Sides Seattle 2012 Offensive DefenseStephan Chenette 2012 B-Sides and ToorCon Talk Offensive Defense
Blog Post - http://blog.ioactive.com/2013/01/offensive-defense.html
Cyber-criminals have had back-end infrastructures equivalent to Virus Total to test if malware and exploits are effective against AV scanners for many years, thus showing that attackers are proactively avoiding detection when building malware. In this day of age malicious binaries are generated on demand by server-side kits when a victim visits a malicious web page, making reliance solely on hash based solutions inadequate. In the last 15 years detection techniques have evolved in an attempt to keep up with attack trends. In the last few years security companies have looked for supplemental solutions such as the use of machine learning to detect and mitigate attacks against cyber criminals. Let's not pretend attackers can't bypass each and every detection technique currently deployed. Join me as I present and review current detection methods found in most host and network security solutions found today. We will re-review the defense in depth strategy while keeping in mind that a solid security strategy consists of forcing an attacker to spend as much time and effort while needing to know a variety of skills and technologies in order to successfully pull off the attack. In the end I hope to convince you that thinking defensively requires thinking offensively.
The Future of Automated Malware Generation



The Future of Automated Malware GenerationStephan Chenette The document discusses the current and future states of automated malware generation and malware defense techniques. It describes how malware distribution networks currently work and trends showing rising malware samples. The future of malware defense is proposed to apply more machine learning and statistical techniques to model malware behaviors and attributes in order to handle growing sample volumes. This would involve training machine learning classifiers on features identified by human experts to classify and cluster malware more effectively.
Detecting Web Browser Heap Corruption Attacks - Stephan Chenette, Moti Joseph...



Detecting Web Browser Heap Corruption Attacks - Stephan Chenette, Moti Joseph...Stephan Chenette This document summarizes a presentation on detecting web browser heap corruption attacks. The presentation focuses on research into detecting these attacks and an internal tool called "xmon" that is part of a larger system for detecting malicious web content. The document provides background on heap corruption vulnerabilities and exploits, and how techniques like heap spraying and heap feng shui have increased the reliability of such exploits. It then describes xmon's methods for generic detection of exploit techniques through actions like patching virtual function calls and hooking structured exception handlers.
Web Wreck-utation - CanSecWest 2008



Web Wreck-utation - CanSecWest 2008Stephan Chenette The document discusses how reputation systems are increasingly being exploited by spammers and malicious actors online. It notes that the most visited websites are being used to host malicious content, as these sites generally have good reputations. Attackers are able to compromise legitimate domains and inject malicious code through techniques like IFRAME injections. The document also discusses how email reputation systems can be exploited, such as by using free webmail services to send spam. Domain reputation is touched on as well, noting how domain tasting undermines the signal of domain age. Overall, the document outlines how reputation, while helpful for security, is not foolproof and can be manipulated or hijacked by malicious parties.
The Ultimate Deobfuscator - ToorCON San Diego 2008



The Ultimate Deobfuscator - ToorCON San Diego 2008Stephan Chenette The document discusses techniques for deobfuscating malicious JavaScript code. It describes how code is often obfuscated to hide malicious behavior. It then summarizes different approaches that have been used for deobfuscation such as replacing functions like document.write. However, these approaches can be detected. The document proposes hooking directly into the browser as the "ultimate deobfuscator" to monitor functions like document.write and eval to see their actual behavior. It describes hooking browser DLLs to monitor this behavior and provides an example of deobfuscating malicious code using this technique.
Script Fragmentation - Stephan Chenette - OWASP/RSA 2008



Script Fragmentation - Stephan Chenette - OWASP/RSA 2008Stephan Chenette ERA 2008 - Stephan Chenette, Presentation on Script Fragmentation attack
Abstract: This presentation will introduce a new web-based attack vector which utilizes client-side scripting to fragment malicious web content.
This involves distributing web exploits in a asynchronous manner to evade signature detection. Similar to TCP fragmentation attacks, which are still an issue in current IDS/IPS products, This attack vector involves sending any web exploit in fragments and uses the already existing components within the web browser to reassemble and execute the exploit.
Our presentation will discuss this attack vector used to evade both gateway and client side detection. We will show several proof of concepts containing common readily available web exploits.
Fireshark - Brucon 2010



Fireshark - Brucon 2010Stephan Chenette This document summarizes a presentation on the web forensics and analysis tool Fireshark. It discusses how Fireshark allows automated browsing and passive logging of connection data, source content, JavaScript calls and page links to help analyze malicious websites and mass injection attacks. Specific use cases covered include analyzing website architectures, redirection chains, and profiling compromised content. The document also provides examples of analyzing real injection campaigns using Fireshark to gain insights into exploitation techniques and patterns used by attackers on the web.
Watchtowers of the Internet - Source Boston 2012



Watchtowers of the Internet - Source Boston 2012Stephan Chenette Watchtowers of the Internet: Analysis of Outbound Malware Communication, Stephan Chenette, Principal Security Researcher, (@StephanChenette) & Armin Buescher, Security Researcher
With advanced malware, targeted attacks, and advanced persistent threats, it’s not IF but WHEN a persistant attacker will penetrate your network and install malware on your company’s network and desktop computers. To get the full picture of the threat landscape created by malware, our malware sandbox lab runs over 30,000 malware samples a day. Network traffic is subsequently analyzed using heuristics and machine learning techniques to statistically score any outbound communication and identify command & control, back-channel, worm-like and other types of traffic used by malware.
Our talk will focus on the setup of the lab, major malware families as well as outlier malware, and the statistics we have generated to give our audience an exposure like never before into the details of malicious outbound communication. We will provide several tips, based on our analysis to help you create a safer and more secure network.
Stephan Chenette is a principal security researcher at Websense Security Labs, specializing in research tools and next generation emerging threats. In this role, he identifies and implements exploit and malcode detection techniques.
Armin Buescher is a Security Researcher and Software Engineer experienced in strategic development of detection/prevention technologies and analysis tools. Graduated as Dipl.-Inf. (MSc) with thesis on Client Honeypot systems. Interested in academic research work and published author of security research papers.
Automated JavaScript Deobfuscation - PacSec 2007
- 1. Spiffy: Automated JavaScript Deobfuscation Stephan Chenette Alex Rice Principle Security Researcher Sr. Security Researcher
- 2. Malcode analysis Current malcode research is focused on binary analysis. Multiple tools to assist researchers in analysis. IDA OllyDbg Fact: More delivery of malware is moving to the web. A new set of skills and tools are required.
- 3. What you know… What you need to know… Malicious binary analysis Languages: Assembly, C, C++, vb, delphi, etc. Concepts: PE file format, win32 function usage, unpacking, anti- disassembling tricks, etc. Tools: IDA, OllyDbg, PEiD, Imprec Malicious web content analysis Languages: (D)HTML, VBScript, JavaScript, Perl/Python/Ruby Concepts: HTTP Protocol, XMLHTTPRequest, Document Object Model (DOM), Browser Security Models, JSON, Tools: ???
- 4. Those Who Forget History Are Doomed to Repeat It Malcode authors will protect malicious web content the same way they protected malicious binaries. Signature evasion Anti-analysis techniques Pain in the #*&#$! for all researchers!!
- 5. Unpacking and anti-debugging Packing/Protecting/Anti-reversing Compression, Encryption, CRC protection Anti-debugging Virtualization detection Anti-emulation XOR stubs
- 6. Obfuscation Evolution String splitting: “AD” + “ODB.S” + “treAM” String encoding/escaping: “%41u0044” + “Ox44%42u002ES” + “t%72eAM” Closing html tags (e.g. </TEXTAREA>) Code length dependant obfuscation: arguments.callee.toString() Server-side [poly|meta]-morphic obfuscation
- 8. What we actually see…
- 9. Our Approach Emulation: a browser without a browser… HTML Parser DOM Implementation Scripting Engine(s)/Interpreter(s) Allow the page to decode itself Don’t render content, just log everything!
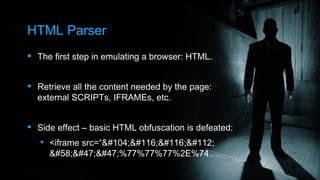
- 10. HTML Parser The first step in emulating a browser: HTML. Retrieve all the content needed by the page: external SCRIPTs, IFRAMEs, etc. Side effect – basic HTML obfuscation is defeated: <iframe src=“http ://%77%77%77%2E%74….
- 11. A Little DOM, Please Modern browsers are dynamic, so our emulator must also be. Implement Document Object Model Attempting to detect all instances of an element by simply parsing static HTML is not enough…. createElement(‘IFRAME’);
- 12. Coming At You Like A Spider Monkey Integrate scripting engine(s) with our DOM to execute scripts as they are discovered Scripts are [mostly] safe for execution Firefox’s SpiderMonkey JavaScript Engine (MPL/GPL/LGPL)
- 13. The Missing Pieces Implement all of the objects/functions that the browser provides: Native JavaScript Browser Supplied eval() alert() String.fromCharCode() document.write() escape() location.href Math.random() window.status Few internal tweaks to mimic JScript (IE) e.g., arguments.callee.toString()
- 26. Automated Usage Integrated with our miners Lots and lots of tuning … (Dec ’06) 100,000,000+ URLs analyzed every 24 hrs Even after the initial decoding, string matching is still futile: “AD” + “ODB.S” + “treAM”
- 27. New Technique, New Signatures Detect specific DOM element + attribute combinations 1. New <OBJECT> created 2. <OBJECT>.classid = “BD96C556-65A3….” 3. <OBJECT>.CreateObject(“adodb.stream”) Can still match “old fashion” signatures *inside* document.write() and eval() calls
- 28. 24 Hours – 111M URLs 124,232 Infected (0.11%)
- 29. Limitations – JavaScript Only? Other Languages? Same concepts apply! VBScript vbscript.dll under WinE! Currently working on experimental version ActionScript Partially implemented when Adobe open sourced the engine; now part of Mozilla’s Tamarin Project
- 30. Limitations – variable is not defined! Attackers can potentially use intentional errors to prevent code execution Identical input/output is very important Easy: document.width Hard: window.open() Really hard: XMLHTTPRequest Centralized verbose error logging!
- 31. Limitations – Denial of Service JS_SetBranchCallback Look familiar? Separate thread monitoring execution time
- 32. Limitations – User Interaction Malicious code could potentially rely upon a user’s action before execution begins We implemented some basic event handling: body – onload window – focus document – onmouse___ Not foolproof!
- 33. CaffeineMonkey Ben Feinstein & Daniel Peck @ SecureWorks Released Open Source Excellent tool for manual reverse engineering of obfuscation; needs HTML/DOM! Promising research that attempts to identify malicious activity based on behavior, not static signatures. http://secureworks.com/research/tools/caffeinemonkey.html
- 34. Other Resources Tutorials from ISC, excellent starting point http://handlers.sans.org/dwesemann/decode/ Jose Nazario’s CanSecWest presentation http://www.cansecwest.com/slides07/csw07-nazario.pdf Websense Blogs http://www.websense.com/securitylabs/blog/blog.php?BlogID=86 http://www.websense.com/securitylabs/blog/blog.php?BlogID=98 http://www.websense.com/securitylabs/blog/blog.php?BlogID=142
- 35. The End Stephan Chenette Alex Rice Principle Security Researcher Sr .Security Researcher schenette || websense com arice || websense com
