ATM System by image processing
Download as pptx, pdf1 like4,070 views
This document discusses biometric authentication using facial recognition technology in automated teller machines (ATMs). It provides an introduction to biometrics and how facial recognition works by measuring distinct facial features to create a unique numerical code or "faceprint". The document also outlines the process of biometric systems from data collection and transmission to decision making. It discusses some applications of biometrics like access control and benefits like increased reliability but also challenges like costs. In conclusion, it proposes using facial recognition in ATMs to provide more secure authentication while reducing fraudulent activities compared to traditional authentication methods.
1 of 20
Downloaded 66 times



















Recommended
Biometrics Technology Intresting PPT 



Biometrics Technology Intresting PPT preeti tripathi very appropiate and good ppt that u can trust , not too long or too short ppt good for college students. plzz share it.
Automatic number plate recognition (anpr)



Automatic number plate recognition (anpr)AbhishekChoudhary464889 Number Plate Recognition (NPR) is a computer vision technology that captures images of vehicles using a camera. It extracts the vehicle's number plate to identify the owner's details by matching it to a database. The system works by capturing images, preprocessing them, detecting the number plate using YOLO, recognizing the characters, and outputting the results to a database. It has benefits like saving time, reducing errors, and aiding in tracking criminals. Potential future improvements include enhancing plate recognition for different fonts/sizes and speeding up the system.
automatic number plate recognition



automatic number plate recognitionSairam Taduvai Automatic number plate recognition (ANPR) uses optical character recognition on images to read vehicle registration plates. It has seven elements: cameras, illumination, frame grabbers, computers, software, hardware, and databases. ANPR detects vehicles, captures plate images, and processes the images to recognize plates. It has advantages like improving safety and reducing crime. Applications include parking, access control, tolling, border control, and traffic monitoring.
Security



SecurityAyushiGupta3123 This document discusses biometric authentication for ATM security. It describes common ATM attacks like skimming and explains how biometric authentication works by using unique human characteristics. Various biometric modalities are described, including fingerprints, iris scans, palm veins, and facial recognition. Multimodal biometrics is presented as an accurate approach that fuses multiple biometrics to strongly authenticate users. Applications of biometrics for ATMs and other systems are mentioned along with advantages like improved security and disadvantages like increased costs. The conclusion states that multimodal biometrics provides a high level of ATM security by reducing fraudulent activities and false acceptance rates.
Digital jewellery ppt



Digital jewellery pptRithu Pudiyaveedu Digital jewelry is fashion jewelry that contains embedded computing technology. It can include pieces like earrings, a necklace, and bracelet that together function as a cell phone using Bluetooth technology. The earrings contain speakers, the necklace has a microphone, and the bracelet displays caller ID information. A Java ring can be used for security purposes by automatically unlocking doors and logging users into systems. While digital jewelry provides wireless functionality and interaction, it also has small displays, potential health risks from radiation, and high costs that limit adoption.
Mind reading computer ppt



Mind reading computer pptTarun tyagi The document discusses a seminar presentation on mind reading computers. It begins with an introduction on how people express mental states through facial expressions and gestures. It then discusses what mind reading is, how it works using sensors to measure blood oxygen levels in the brain, and the process which involves facial detection and emotional classification techniques. Applications are discussed including using it to help paralyzed people communicate and potential issues around privacy breaches. It concludes that research is underway to allow computers to respond to brain activity.
Diabetes Mellitus



Diabetes MellitusMD Abdul Haleem This document provides an overview of diabetes mellitus (DM), including the three main types (Type 1, Type 2, and gestational diabetes), signs and symptoms, complications, pathophysiology, oral manifestations, dental management considerations, emergency management, diagnosis, and treatment. DM is caused by either the pancreas not producing enough insulin or cells not responding properly to insulin, resulting in high blood sugar levels. The document compares and contrasts the characteristics of Type 1 and Type 2 DM.
Power Point Presentation on Artificial Intelligence 



Power Point Presentation on Artificial Intelligence Anushka Ghosh Its a Power Point Presentation on Artificial Intelligence.I hope you will find this helpful. Thank you.
You can also find out my another PPT on Artificial Intelligence.The link is given below--
https://www.slideshare.net/AnushkaGhosh5/ppt-presentation-on-artificial-intelligence
Anushka Ghosh
Money pad the future wallet



Money pad the future walletLeelakh Sachdeva The document summarizes a seminar report on Money-Pad, a proposed future wallet that holds digital cash and financial information rather than paper cash. Money-Pad uses biometric fingerprint recognition for secure authentication of transactions. It allows for instant clearing of funds without transaction fees or credit limits. In the future, as internet access expands globally, financial transactions may be conducted via small fingerprint recognition devices without need for physical cards or pads.
Face recognition technology - BEST PPT



Face recognition technology - BEST PPTSiddharth Modi Face recognition technology may help solve problems with identity verification by analyzing facial features instead of passwords or pins. The document outlines the key stages of face recognition systems including data acquisition, input processing, and image classification. It also discusses advantages like convenience and ease of use, as well as limitations such as an inability to distinguish identical twins. Potential applications are identified in government, security, and commercial sectors.
Voice morphing-



Voice morphing-Navneet Sharma It is a technique to modify a source speaker's speech to sound as if it was spoken by a target speaker.
Voice morphing enables speech patterns to be cloned
And an accurate copy of a person's voice can be made that can wishes to say, anything in the voice of someone else.
5 pen-pc-technology complete ppt



5 pen-pc-technology complete pptatinav242 This document describes the P-ISM (Pen-style Personal Networking Gadget Package), which was created in 2012. P-ISM allows users to use two pens to control a projected keyboard and monitor on any flat surface. It functions like a desktop computer through its CPU pen, communication pen, LED projector, virtual keyboard, digital camera, and battery. The document discusses P-ISM's history, components, functions, block diagram, working, merits such as portability, demertis like cost, and references.
Brain gate



Brain gateMayank Garg (1) Brain Gate is an electrode chip implanted in the brain that detects electrical signals from neurons and sends them to a computer to control devices.
(2) The goal of Brain Gate is to provide a fast, reliable connection between the brain of a severely disabled person and a computer to allow thought-based communication and control.
(3) Brain Gate was first tested on monkeys and rats, allowing them to control cursors and robotic arms with their minds, and was then tested on humans in 2004, allowing a paralyzed man to control a computer using only his thoughts.
EyeRing PowerPoint Presentation



EyeRing PowerPoint PresentationPriyad S Naidu 2016 Project.
A finger wore device helpful for blind people.
Used to know the color and currency and etc.,
Prepared by Ch.Durga Rao, Naidu.S.Piyadarshini.
Technical seminar on virtual smart phone



Technical seminar on virtual smart phoneAkshitha Chutke VSP will end the physical dependency of the mobile phone. VSP provides novel interaction method to seamlessly communicate with each other in a fun and intuitive way.
IoT Networking



IoT NetworkingHitesh Mohapatra This document discusses IoT networking and quality of service (QoS) for IoT networks. It begins by describing the characteristics of IoT devices such as low processing power, small size, and energy constraints. It then discusses enabling the classical Internet for IoT devices through standards developed by the IETF, including 6LoWPAN, ROLL, and CoRE. CoRE provides a framework for IoT applications and services discovery. The document concludes by examining policies for QoS in IoT networks to guarantee intended service, covering resource utilization, data timeliness, availability, and delivery.
Eye tracker based HCI

Eye tracker based HCISaswati Eye tracking is the process of measuring either the point of gaze or the motion of an eye relative to the head. An eye tracker is a device for measuring eye positions and eye movement.
Brain Computer Interfaces(BCI)



Brain Computer Interfaces(BCI)Dr. Uday Saikia 1. Introduction
2. What is BCI
3. History
4. Structure and signals
5. Architecture/Logical structure
6. Brain waves
7. Functionality
8. Future Work
9. Conclusion
10. References
Graphical password authentication



Graphical password authenticationAsim Kumar Pathak This document discusses authentication methods and focuses on graphical passwords. It begins with an overview of common authentication methods like text passwords, tokens, and biometrics. It then discusses the drawbacks of text passwords and introduces graphical passwords as an alternative. The document surveys recall-based and recognition-based graphical password techniques and provides examples like Draw-A-Secret and Passfaces. It concludes by noting the advantages of graphical passwords in usability and security but also disadvantages like longer login times and storage requirements.
Ppt on use of biomatrix in secure e trasaction



Ppt on use of biomatrix in secure e trasactionDevyani Vaidya Biometrics refers to authentication techniques that rely on measurable physiological and individual characteristics to automatically verify identity. There are two main types of biometrics: physiological, which relate to the body shape like fingerprints, retina, and face; and behavioral, which relate to behaviors like voice, handwriting, and typing patterns. Biometric systems use verification to compare a sample to a single stored template or identification to search a sample against a database of templates to resolve a person's identity. While biometrics can provide strong authentication for applications like secure banking, border control, and access control, they are not perfect and have limitations like cost, accuracy, and privacy concerns.
Atm using fingerprint



Atm using fingerprintAnIsh Kumar The document discusses using fingerprint biometrics for authentication in ATM machines. Fingerprints provide high universality, distinctiveness, permanence and performance making them suitable for biometric authentication. The technical processes of minutiae extraction from fingerprints and the biometric system workflow are described. Applications of fingerprint ATMs include added security for banking, membership verification, and food/ticket purchases. Potential disadvantages include false acceptance and rejection rates and issues with certain users. Future areas of development include improved matching algorithms and database security to further enhance fingerprint biometrics for ATM authentication.
SMART DUST



SMART DUSTKhyravdhy Tannaya Smart dust is a network of tiny sensor-enabled devices called motes that can monitor environmental conditions. Each mote contains sensors, computing power, wireless communication, and an autonomous power supply within a volume of a few millimeters. They communicate with each other and a base station using radio frequency or optical transmission. Major challenges in developing smart dust include fitting all components into a small size while minimizing energy usage. Potential applications include environmental monitoring, healthcare, security, and traffic monitoring.
Presentation on security feature of atm (2)



Presentation on security feature of atm (2)Siya Agarwal The document discusses the security features of ATM systems. It describes how ATMs work by having customers authenticate using cards and PINs. ATM security relies on crypto-processors, database security, and network security. It provides security through mechanisms like time-outs for invalid PIN entries and recognizing stolen cards. Additional security features include identity verification, data confidentiality, accountability, and audit capabilities. The document emphasizes the importance of keeping ATM cards and PINs secure and reporting any loss or theft.
Diamond chip



Diamond chipPRADEEP Cheekatla Carbon exists in many allotropes that can be used for electronics, such as diamond, graphene, carbon nanotubes, and lonsdaleite. Diamond chips are electronic chips manufactured using a diamond wafer that is doped to make it conductive. Carbon nanotubes have many desirable properties including strength, hardness, electrical and thermal conductivity, and can operate at higher temperatures than silicon chips. Potential applications of diamond chips and carbon nanotubes include information and communications technology, materials, biomedical devices, energy, transportation, and consumer goods. However, diamond chips are currently more expensive to produce than silicon chips due to the difficulty of doping the diamond structure.
Exploring the Brain Computer Interface



Exploring the Brain Computer InterfaceJim McKeeth This document provides an overview of brain-computer interfaces and their applications. It discusses the science of reading brain activity through various technologies like EEG, MRI, and ultrasound. It also covers direct brain input methods such as tDCS and TMS. The document outlines several consumer brain-computer interfaces currently available and demonstrates using a brain interface to control a quadcopter. It concludes by discussing future applications of brain interfaces such as enhanced reality, thought identification, and uploading consciousness.
E-BALL TECHNOLOGY SEMINAR REPORT



E-BALL TECHNOLOGY SEMINAR REPORTVikas Kumar E-BALL TECHNOLOGY is the present evolving technology in the field of the computer-enhanced technologies.
138693 28152-brain-chips



138693 28152-brain-chipsjitendra k Singh Brain chips are implantable devices that can enhance human memory, help paralyzed patients, and be used for military purposes. They involve directly interfacing the brain with computers. Early experiments by Jose Delgado in the 1950s using electrical stimulation of animal brains helped uncover mysteries of the brain and contributed to developments in brain implant technology. More recently, researchers have linked brain cells and silicon chips electronically using tiny electrode arrays. While brain chips offer benefits like helping the blind see and paralyzed patients move, they also face challenges regarding costs, safety, and risks to personal identity and free will. Future applications may include enhancing memory, enabling new communication methods, and expanding human sensory abilities.
Screenless Display PPT Presentation



Screenless Display PPT PresentationSai Mohith A PPT presentation for technical seminar on the topic "Screenless Display"
References Used:
https://www.slideshare.net/vikasraj225/screenless-display-ppt?from_action=save
https://www.marketsandmarkets.com/Market-Reports/screenless-display-market-155203044.html
4.report (biometric security system)



4.report (biometric security system)JIEMS Akkalkuwa This document provides an introduction to biometric security systems. It discusses how biometrics has evolved from early manual criminal identification techniques to modern automated systems. It describes some of the first commercial biometric devices used over 25 years ago for timekeeping and access control. It then summarizes several common biometric modalities used in existing security systems, including fingerprint, face, signature, voice, and gait recognition.
Alaa elbeheri research_presentation 



Alaa elbeheri research_presentation alaabebe This document discusses emerging technologies related to computer inputs, outputs, and biometrics for user verification. It describes various input methods like keyboards, mice, and touch screens. It also covers output devices like screens, printers, and speakers. The document focuses on biometrics like fingerprint, facial, iris, retina, voice, signature/handwriting, and keystroke recognition. Biometrics provide automated user identification and verification by analyzing unique physiological or behavioral characteristics. Properly implemented biometrics can improve security, provide audit trails, and accurately verify identities.
More Related Content
What's hot (20)
Money pad the future wallet



Money pad the future walletLeelakh Sachdeva The document summarizes a seminar report on Money-Pad, a proposed future wallet that holds digital cash and financial information rather than paper cash. Money-Pad uses biometric fingerprint recognition for secure authentication of transactions. It allows for instant clearing of funds without transaction fees or credit limits. In the future, as internet access expands globally, financial transactions may be conducted via small fingerprint recognition devices without need for physical cards or pads.
Face recognition technology - BEST PPT



Face recognition technology - BEST PPTSiddharth Modi Face recognition technology may help solve problems with identity verification by analyzing facial features instead of passwords or pins. The document outlines the key stages of face recognition systems including data acquisition, input processing, and image classification. It also discusses advantages like convenience and ease of use, as well as limitations such as an inability to distinguish identical twins. Potential applications are identified in government, security, and commercial sectors.
Voice morphing-



Voice morphing-Navneet Sharma It is a technique to modify a source speaker's speech to sound as if it was spoken by a target speaker.
Voice morphing enables speech patterns to be cloned
And an accurate copy of a person's voice can be made that can wishes to say, anything in the voice of someone else.
5 pen-pc-technology complete ppt



5 pen-pc-technology complete pptatinav242 This document describes the P-ISM (Pen-style Personal Networking Gadget Package), which was created in 2012. P-ISM allows users to use two pens to control a projected keyboard and monitor on any flat surface. It functions like a desktop computer through its CPU pen, communication pen, LED projector, virtual keyboard, digital camera, and battery. The document discusses P-ISM's history, components, functions, block diagram, working, merits such as portability, demertis like cost, and references.
Brain gate



Brain gateMayank Garg (1) Brain Gate is an electrode chip implanted in the brain that detects electrical signals from neurons and sends them to a computer to control devices.
(2) The goal of Brain Gate is to provide a fast, reliable connection between the brain of a severely disabled person and a computer to allow thought-based communication and control.
(3) Brain Gate was first tested on monkeys and rats, allowing them to control cursors and robotic arms with their minds, and was then tested on humans in 2004, allowing a paralyzed man to control a computer using only his thoughts.
EyeRing PowerPoint Presentation



EyeRing PowerPoint PresentationPriyad S Naidu 2016 Project.
A finger wore device helpful for blind people.
Used to know the color and currency and etc.,
Prepared by Ch.Durga Rao, Naidu.S.Piyadarshini.
Technical seminar on virtual smart phone



Technical seminar on virtual smart phoneAkshitha Chutke VSP will end the physical dependency of the mobile phone. VSP provides novel interaction method to seamlessly communicate with each other in a fun and intuitive way.
IoT Networking



IoT NetworkingHitesh Mohapatra This document discusses IoT networking and quality of service (QoS) for IoT networks. It begins by describing the characteristics of IoT devices such as low processing power, small size, and energy constraints. It then discusses enabling the classical Internet for IoT devices through standards developed by the IETF, including 6LoWPAN, ROLL, and CoRE. CoRE provides a framework for IoT applications and services discovery. The document concludes by examining policies for QoS in IoT networks to guarantee intended service, covering resource utilization, data timeliness, availability, and delivery.
Eye tracker based HCI

Eye tracker based HCISaswati Eye tracking is the process of measuring either the point of gaze or the motion of an eye relative to the head. An eye tracker is a device for measuring eye positions and eye movement.
Brain Computer Interfaces(BCI)



Brain Computer Interfaces(BCI)Dr. Uday Saikia 1. Introduction
2. What is BCI
3. History
4. Structure and signals
5. Architecture/Logical structure
6. Brain waves
7. Functionality
8. Future Work
9. Conclusion
10. References
Graphical password authentication



Graphical password authenticationAsim Kumar Pathak This document discusses authentication methods and focuses on graphical passwords. It begins with an overview of common authentication methods like text passwords, tokens, and biometrics. It then discusses the drawbacks of text passwords and introduces graphical passwords as an alternative. The document surveys recall-based and recognition-based graphical password techniques and provides examples like Draw-A-Secret and Passfaces. It concludes by noting the advantages of graphical passwords in usability and security but also disadvantages like longer login times and storage requirements.
Ppt on use of biomatrix in secure e trasaction



Ppt on use of biomatrix in secure e trasactionDevyani Vaidya Biometrics refers to authentication techniques that rely on measurable physiological and individual characteristics to automatically verify identity. There are two main types of biometrics: physiological, which relate to the body shape like fingerprints, retina, and face; and behavioral, which relate to behaviors like voice, handwriting, and typing patterns. Biometric systems use verification to compare a sample to a single stored template or identification to search a sample against a database of templates to resolve a person's identity. While biometrics can provide strong authentication for applications like secure banking, border control, and access control, they are not perfect and have limitations like cost, accuracy, and privacy concerns.
Atm using fingerprint



Atm using fingerprintAnIsh Kumar The document discusses using fingerprint biometrics for authentication in ATM machines. Fingerprints provide high universality, distinctiveness, permanence and performance making them suitable for biometric authentication. The technical processes of minutiae extraction from fingerprints and the biometric system workflow are described. Applications of fingerprint ATMs include added security for banking, membership verification, and food/ticket purchases. Potential disadvantages include false acceptance and rejection rates and issues with certain users. Future areas of development include improved matching algorithms and database security to further enhance fingerprint biometrics for ATM authentication.
SMART DUST



SMART DUSTKhyravdhy Tannaya Smart dust is a network of tiny sensor-enabled devices called motes that can monitor environmental conditions. Each mote contains sensors, computing power, wireless communication, and an autonomous power supply within a volume of a few millimeters. They communicate with each other and a base station using radio frequency or optical transmission. Major challenges in developing smart dust include fitting all components into a small size while minimizing energy usage. Potential applications include environmental monitoring, healthcare, security, and traffic monitoring.
Presentation on security feature of atm (2)



Presentation on security feature of atm (2)Siya Agarwal The document discusses the security features of ATM systems. It describes how ATMs work by having customers authenticate using cards and PINs. ATM security relies on crypto-processors, database security, and network security. It provides security through mechanisms like time-outs for invalid PIN entries and recognizing stolen cards. Additional security features include identity verification, data confidentiality, accountability, and audit capabilities. The document emphasizes the importance of keeping ATM cards and PINs secure and reporting any loss or theft.
Diamond chip



Diamond chipPRADEEP Cheekatla Carbon exists in many allotropes that can be used for electronics, such as diamond, graphene, carbon nanotubes, and lonsdaleite. Diamond chips are electronic chips manufactured using a diamond wafer that is doped to make it conductive. Carbon nanotubes have many desirable properties including strength, hardness, electrical and thermal conductivity, and can operate at higher temperatures than silicon chips. Potential applications of diamond chips and carbon nanotubes include information and communications technology, materials, biomedical devices, energy, transportation, and consumer goods. However, diamond chips are currently more expensive to produce than silicon chips due to the difficulty of doping the diamond structure.
Exploring the Brain Computer Interface



Exploring the Brain Computer InterfaceJim McKeeth This document provides an overview of brain-computer interfaces and their applications. It discusses the science of reading brain activity through various technologies like EEG, MRI, and ultrasound. It also covers direct brain input methods such as tDCS and TMS. The document outlines several consumer brain-computer interfaces currently available and demonstrates using a brain interface to control a quadcopter. It concludes by discussing future applications of brain interfaces such as enhanced reality, thought identification, and uploading consciousness.
E-BALL TECHNOLOGY SEMINAR REPORT



E-BALL TECHNOLOGY SEMINAR REPORTVikas Kumar E-BALL TECHNOLOGY is the present evolving technology in the field of the computer-enhanced technologies.
138693 28152-brain-chips



138693 28152-brain-chipsjitendra k Singh Brain chips are implantable devices that can enhance human memory, help paralyzed patients, and be used for military purposes. They involve directly interfacing the brain with computers. Early experiments by Jose Delgado in the 1950s using electrical stimulation of animal brains helped uncover mysteries of the brain and contributed to developments in brain implant technology. More recently, researchers have linked brain cells and silicon chips electronically using tiny electrode arrays. While brain chips offer benefits like helping the blind see and paralyzed patients move, they also face challenges regarding costs, safety, and risks to personal identity and free will. Future applications may include enhancing memory, enabling new communication methods, and expanding human sensory abilities.
Screenless Display PPT Presentation



Screenless Display PPT PresentationSai Mohith A PPT presentation for technical seminar on the topic "Screenless Display"
References Used:
https://www.slideshare.net/vikasraj225/screenless-display-ppt?from_action=save
https://www.marketsandmarkets.com/Market-Reports/screenless-display-market-155203044.html
Similar to ATM System by image processing (20)
4.report (biometric security system)



4.report (biometric security system)JIEMS Akkalkuwa This document provides an introduction to biometric security systems. It discusses how biometrics has evolved from early manual criminal identification techniques to modern automated systems. It describes some of the first commercial biometric devices used over 25 years ago for timekeeping and access control. It then summarizes several common biometric modalities used in existing security systems, including fingerprint, face, signature, voice, and gait recognition.
Alaa elbeheri research_presentation 



Alaa elbeheri research_presentation alaabebe This document discusses emerging technologies related to computer inputs, outputs, and biometrics for user verification. It describes various input methods like keyboards, mice, and touch screens. It also covers output devices like screens, printers, and speakers. The document focuses on biometrics like fingerprint, facial, iris, retina, voice, signature/handwriting, and keystroke recognition. Biometrics provide automated user identification and verification by analyzing unique physiological or behavioral characteristics. Properly implemented biometrics can improve security, provide audit trails, and accurately verify identities.
International Journal of Engineering Research and Development



International Journal of Engineering Research and DevelopmentIJERD Editor Electrical, Electronics and Computer Engineering,
Information Engineering and Technology,
Mechanical, Industrial and Manufacturing Engineering,
Automation and Mechatronics Engineering,
Material and Chemical Engineering,
Civil and Architecture Engineering,
Biotechnology and Bio Engineering,
Environmental Engineering,
Petroleum and Mining Engineering,
Marine and Agriculture engineering,
Aerospace Engineering.
J1076975



J1076975IJERD Editor This document proposes fusing eye vein and finger vein biometrics for multimodal authentication. It extracts features from eye vein and finger vein images separately, then concatenates the feature vectors. Experimental results on public databases show this technique achieves more accurate identity verification than single biometrics, with lower false rejection and acceptance rates. The fused template provides better discrimination than individual features.
2001229094(1).pptx biometrics authentication



2001229094(1).pptx biometrics authenticationMdAminulkhan1 This document discusses biometric authentication for ATMs. It begins with an introduction to biometrics and how various biometric systems like fingerprint and facial recognition are being used for real-time identification. It then addresses issues with current ATM authentication methods like card fraud and sharing of PINs. Biometric ATMs are presented as a solution by providing strong authentication without hidden card costs. The document proceeds to describe different biometric systems including fingerprint, hand, and iris scanning. It concludes by noting biometrics offers greater security than traditional methods and some countries have already implemented biometric ATMs.
best face detection technology ppt



best face detection technology pptDharmendra Prajapat Face detection technology uses computer vision and biometrics to automatically detect and identify human faces. It works by capturing a digital image, detecting and extracting a face, measuring nodal points like eye and mouth positions, and comparing these measurements to a stored database to identify the person. There are two main applications - verification like mobile face unlock, which does a one-to-one comparison, and identification like airport security, which does a one-to-many search of a database. The key purpose of face detection is for security and privacy by uniquely identifying individuals.
Biometrics verification techniques combine



Biometrics verification techniques combinesiva23143 This document proposes a multimodal biometrics payment system that combines biometrics verification techniques with hidden biometrics. It describes a system that uses fingerprint, face, and hidden biometrics like electromyograms and medical images for secure user identification and payment. The system extracts features from fingerprints and infrared images of faces for matching. It also discusses using signals from muscles or bones in medical images as hidden biometrics to prevent forgery. The document concludes that combining standard and hidden biometrics can provide robust user identification for secure payment systems.
SEMINAR ON BIOMETRIC TECHNOLOGY.1pptx.pptx



SEMINAR ON BIOMETRIC TECHNOLOGY.1pptx.pptx1A255Gauravwankar The document discusses biometric technology. It begins with a brief history of biometrics, noting that the first real biometric system was created in 1870 and fingerprints were first used for identification in 1892. It then defines biometrics as automated methods of identifying individuals based on physiological or behavioral characteristics. The document outlines the main components of a biometric system including modes of operation, typical blocks, and types of biometrics. It provides details on specific biometric technologies like fingerprint, facial, and iris recognition. The benefits, advantages and disadvantages as well as applications of biometric systems are also summarized.
Biometrics Research/Thesis Paper



Biometrics Research/Thesis PaperSumaiya Ismail Biometrics is the most secure and suitable authentication tool. It is the automated method of recognizing a person based on a physiological or behavioral characteristic. Biometric authentication is used in computer Science for verifying human identity.
International Journal of Computational Engineering Research(IJCER)



International Journal of Computational Engineering Research(IJCER)ijceronline International Journal of Computational Engineering Research(IJCER) is an intentional online Journal in English monthly publishing journal. This Journal publish original research work that contributes significantly to further the scientific knowledge in engineering and Technology.
Enhancing the Cash Point using Multimode Biometric System



Enhancing the Cash Point using Multimode Biometric Systemijtsrd Frauds attacking the automated teller machine have increased over the decade which has motivated us to use the biometrics for personal identification to procure high level of security and accuracy This paper describes a system that replaces the ATM cards and PINs by the physiological biometric face and iris authentication. In this system during enrolment the genuine users face and iris samples of are retained in the database. The process of transaction begins by getting and matching face and iris patterns. The system will automatically distinguish between real legitimate trait and fake samples. If a fake biometric is recognized a GSM module connected to the controller will message OTP by the system to the registered mobile number. After the valid OTP is entered the user can either withdraw or deposit cash or check his her balance. We have included another biometric called Palm Vien. By using Palm Vein we can access the ATM. Mr. T. Karthikeyan | Ms. Aarthi. S | Ms. Amirtha. P | Ms. Divya. R | Ms. Sowndarya. S ""Enhancing the Cash Point using Multimode Biometric System"" Published in International Journal of Trend in Scientific Research and Development (ijtsrd), ISSN: 2456-6470, Volume-3 | Issue-3 , April 2019, URL: https://www.ijtsrd.com/papers/ijtsrd21768.pdf
Paper URL: https://www.ijtsrd.com/engineering/electronics-and-communication-engineering/21768/enhancing-the-cash-point-using-multimode-biometric-system/mr-t-karthikeyan
A86eseminar on biometrics



A86eseminar on biometricsChill Chaithanya Biometrics refers to automatic identification of individuals based on physiological or behavioral characteristics. This document discusses different biometric recognition techniques such as fingerprint recognition, hand geometry recognition, iris scanning, facial recognition, signature verification, voice recognition, and keystroke dynamics. It also outlines applications of biometrics such as security for ATMs, computers, buildings, and more. Biometrics could replace the need for passwords, pins, keys and other traditional identification methods.
Facial Recognition Technology



Facial Recognition Technologypriyabratamansingh1 This document discusses facial recognition technology. It begins with an introduction to biometrics and the need for facial recognition. It then describes the process of facial recognition, including data capture, extraction of features, comparison, and matching. The key components of a facial recognition system and how it works are also outlined. Advantages include convenience and ease of use, while disadvantages relate to issues with lighting, pose, and privacy concerns. The document concludes by describing applications of facial recognition technology in government, security, banking, and other commercial sectors.
An atm with an eye



An atm with an eyeJohn Williams This document proposes an ATM system that uses facial recognition instead of cards and PINs for verification. It would work by having a camera installed on the ATM that takes a photo of the customer's face and compares it to an image stored in the bank's database associated with the account. This would provide increased security by matching a live photo to the stored image without needing a card or PIN. The document outlines the components, techniques, process and potential benefits of such a biometric-based ATM system for more reliable authentication.
face-recognition-technology-08012013131029-face-recognition-technology.doc



face-recognition-technology-08012013131029-face-recognition-technology.docAjijahamadKhaji More info jnsin thank you reconsider the report ppt
Attendance system based on face recognition using python by Raihan Sikdar



Attendance system based on face recognition using python by Raihan Sikdarraihansikdar The document discusses face recognition technology for use in an automatic attendance system. It first defines biometrics and face recognition, explaining that face recognition identifies individuals using facial features. It then covers how face recognition systems work by detecting nodal points on faces to create unique face prints. The document proposes using such a system to take student attendance in online classes during the pandemic, noting advantages like ease of use, increased security, and cost effectiveness. It provides examples of how the system would capture images, analyze features, and recognize enrolled students to record attendance automatically.
Ecrime Practical Biometric



Ecrime Practical BiometricJorge Sebastiao The document discusses various topics related to biometrics including:
1. Biometrics can be used for physical access control, ATM access, and authenticating transactions over the telephone or from home computers. Fingerprints, iris scans, and facial recognition are some common biometric technologies used.
2. Early biometrics systems from the 1880s involved precise body measurements and physical descriptions but failed by 1903. Modern biometrics use automated methods to recognize individuals based on physiological or behavioral characteristics.
3. Biometrics are part of identity management and can help with security, national security threats, accountability, and optimizing resources. However, biometrics also have limitations like environmental factors affecting performance.
Finger print ATM



Finger print ATMAnkan Biswas This document discusses using fingerprint biometrics for authentication in ATM machines. It defines ATMs and outlines issues with current identification methods like stolen cards and shared PINs. Fingerprint biometrics could solve these issues through multi-factor authentication combining cards, PINs, and fingerprints. The document then covers fingerprint patterns, how fingerprint scanners work to enroll and verify prints, and the system design of a biometric ATM including hardware and software components. Potential advantages are discussed like increased security over shared passwords, with disadvantages including higher costs.
Fingerprint detection



Fingerprint detectionMudit Mishra This is a complete report on Bio-metrics, finger print detection. It include what finger print is, how to scan and refin finger print, how the mechanism of its detection work, applications, etc
facerecognitiontechnology-131025121934-phpapp01.pdf



facerecognitiontechnology-131025121934-phpapp01.pdfPoooi2 This seminar presentation provides an overview of face recognition technology. It discusses how face recognition works by measuring nodal points on the face and creating a numerical face print. The key advantages are that face recognition is convenient, easy to use, and inexpensive compared to other biometrics. However, it cannot distinguish identical twins. The presentation outlines common applications in government (e.g. law enforcement, security), commercial (e.g. banking, access control), and concludes that costs are decreasing which will lead to more widespread deployment of face recognition technologies.
Recently uploaded (20)
UNIT-1-PPT-Introduction about Power System Operation and Control



UNIT-1-PPT-Introduction about Power System Operation and ControlSridhar191373 Power scenario in Indian grid – National and Regional load dispatching centers –requirements of good power system - necessity of voltage and frequency regulation – real power vs frequency and reactive power vs voltage control loops - system load variation, load curves and basic concepts of load dispatching - load forecasting - Basics of speed governing mechanisms and modeling - speed load characteristics - regulation of two generators in parallel.
Forensic Science – Digital Forensics – Digital Evidence – The Digital Forensi...



Forensic Science – Digital Forensics – Digital Evidence – The Digital Forensi...ManiMaran230751 Forensic Science – Digital Forensics – Digital Evidence – The Digital Forensics Process – Introduction – The
Identification Phase – The Collection Phase – The Examination Phase – The Analysis Phase – The
Presentation Phase.
Department of Environment (DOE) Mix Design with Fly Ash.



Department of Environment (DOE) Mix Design with Fly Ash.MdManikurRahman Concrete Mix Design with Fly Ash by DOE Method. The Department of Environmental (DOE) approach to fly ash-based concrete mix design is covered in this study.
The Department of Environment (DOE) method of mix design is a British method originally developed in the UK in the 1970s. It is widely used for concrete mix design, including mixes that incorporate supplementary cementitious materials (SCMs) such as fly ash.
When using fly ash in concrete, the DOE method can be adapted to account for its properties and effects on workability, strength, and durability. Here's a step-by-step overview of how the DOE method is applied with fly ash.
"The Enigmas of the Riemann Hypothesis" by Julio Chai



"The Enigmas of the Riemann Hypothesis" by Julio ChaiJulio Chai In the vast tapestry of the history of mathematics, where the brightest minds have woven with threads of logical reasoning and flash-es of intuition, the Riemann Hypothesis emerges as a mystery that chal-lenges the limits of human understanding. To grasp its origin and signif-icance, it is necessary to return to the dawn of a discipline that, like an incomplete map, sought to decipher the hidden patterns in numbers. This journey, comparable to an exploration into the unknown, takes us to a time when mathematicians were just beginning to glimpse order in the apparent chaos of prime numbers.
Centuries ago, when the ancient Greeks contemplated the stars and sought answers to the deepest questions in the sky, they also turned their attention to the mysteries of numbers. Pythagoras and his followers revered numbers as if they were divine entities, bearers of a universal harmony. Among them, prime numbers stood out as the cornerstones of an infinite cathedral—indivisible and enigmatic—hiding their ar-rangement beneath a veil of apparent randomness. Yet, their importance in building the edifice of number theory was already evident.
The Middle Ages, a period in which the light of knowledge flick-ered in rhythm with the storms of history, did not significantly advance this quest. It was the Renaissance that restored lost splendor to mathe-matical thought. In this context, great thinkers like Pierre de Fermat and Leonhard Euler took up the torch, illuminating the path toward a deeper understanding of prime numbers. Fermat, with his sharp intuition and ability to find patterns where others saw disorder, and Euler, whose overflowing genius connected number theory with other branches of mathematics, were the architects of a new era of exploration. Like build-ers designing a bridge over an unknown abyss, their contributions laid the groundwork for later discoveries.
UNIT-4-PPT UNIT COMMITMENT AND ECONOMIC DISPATCH



UNIT-4-PPT UNIT COMMITMENT AND ECONOMIC DISPATCHSridhar191373 Statement of unit commitment problem-constraints: spinning reserve, thermal unit constraints, hydro constraints, fuel constraints and other constraints. Solution methods: priority list methods, forward dynamic programming approach. Numerical problems only in priority list method using full load average production cost. Statement of economic dispatch problem-cost of generation-incremental cost curve –co-ordination equations without loss and with loss- solution by direct method and lamda iteration method (No derivation of loss coefficients)
module 2 - Minerals and Internal Structure of Earth - ERMS.pdf



module 2 - Minerals and Internal Structure of Earth - ERMS.pdfshivamkumarsharma441 Mineral and internal structure
Video Games and Artificial-Realities.pptx



Video Games and Artificial-Realities.pptxHadiBadri1 🕹️ #GameDevs, #AIteams, #DesignStudios — I’d love for you to check it out.
This is where play meets precision. Let’s break the fourth wall of slides, together.
[HIFLUX] Lok Fitting&Valve Catalog 2025 (Eng)![[HIFLUX] Lok Fitting&Valve Catalog 2025 (Eng)](https://cdn.slidesharecdn.com/ss_thumbnails/lokfittingen-250528072439-8696f1c6-thumbnail.jpg?width=560&fit=bounds)
![[HIFLUX] Lok Fitting&Valve Catalog 2025 (Eng)](https://cdn.slidesharecdn.com/ss_thumbnails/lokfittingen-250528072439-8696f1c6-thumbnail.jpg?width=560&fit=bounds)
![[HIFLUX] Lok Fitting&Valve Catalog 2025 (Eng)](https://cdn.slidesharecdn.com/ss_thumbnails/lokfittingen-250528072439-8696f1c6-thumbnail.jpg?width=560&fit=bounds)
![[HIFLUX] Lok Fitting&Valve Catalog 2025 (Eng)](https://cdn.slidesharecdn.com/ss_thumbnails/lokfittingen-250528072439-8696f1c6-thumbnail.jpg?width=560&fit=bounds)
[HIFLUX] Lok Fitting&Valve Catalog 2025 (Eng)하이플럭스 / HIFLUX Co., Ltd. Lok Fitting, VCR Fitting, Pipe Fitting
Highway Engineering - Pavement materials



Highway Engineering - Pavement materialsAmrutaBhosale9 Bituminous binders are sticky, black substances derived from the refining of crude oil. They are used to bind and coat aggregate materials in asphalt mixes, providing cohesion and strength to the pavement.
ISO 5011 Air Filter Catalogues .pdf



ISO 5011 Air Filter Catalogues .pdf FILTRATION ENGINEERING & CUNSULTANT This presentation provides a comprehensive overview of air filter testing equipment and solutions based on ISO 5011, the globally recognized standard for performance testing of air cleaning devices used in internal combustion engines and compressors.
Key content includes:
Tesia Dobrydnia - A Leader In Her Industry



Tesia Dobrydnia - A Leader In Her IndustryTesia Dobrydnia Tesia Dobrydnia brings her many talents to her career as a chemical engineer in the oil and gas industry. With the same enthusiasm she puts into her work, she engages in hobbies and activities including watching movies and television shows, reading, backpacking, and snowboarding. She is a Relief Senior Engineer for Chevron and has been employed by the company since 2007. Tesia is considered a leader in her industry and is known to for her grasp of relief design standards.
ENERGY STORING DEVICES-Primary Battery.pdf



ENERGY STORING DEVICES-Primary Battery.pdfTAMILISAI R ENERGY STORING DEVICES
Batteries -Introduction – Cells – Batteries –Types of Batteries- Primary batteries – silver button cell
Air Filter Flat Sheet Media-Catalouge-Final.pdf



Air Filter Flat Sheet Media-Catalouge-Final.pdf FILTRATION ENGINEERING & CUNSULTANT This presentation provides a detailed overview of air filter testing equipment, including its types, working principles, and industrial applications. Learn about key performance indicators such as filtration efficiency, pressure drop, and particulate holding capacity. The slides highlight standard testing methods (e.g., ISO 16890, EN 1822, ASHRAE 52.2), equipment configurations (such as aerosol generators, particle counters, and test ducts), and the role of automation and data logging in modern systems. Ideal for engineers, quality assurance professionals, and researchers involved in HVAC, automotive, cleanroom, or industrial filtration systems.
DIGITAL ELECTRONICS: UNIT-III SYNCHRONOUS SEQUENTIAL CIRCUITS



DIGITAL ELECTRONICS: UNIT-III SYNCHRONOUS SEQUENTIAL CIRCUITSSridhar191373 Latches, Flip flops – SR, JK, T, D, Master/Slave FF– operation and excitation tables, Triggering of FF, Analysis and design of clocked sequential circuits – Design - Moore/Mealy models, state minimization, state assignment, circuit implementation – Design of Counters- Ripple Counters, Synchronous Counter, Ring Counters, Shift registers, Universal Shift Register- HDL Models of Sequential Circuits.
ATM System by image processing
- 1. SHAHABUL ISLAM B.TECH C.S.E (6’th SEM) Guided BY : Mr. SHAILESH PATEL COMPUTER SCIENCE & ENGINEERING
- 2. o INTRODUCTION o ATM o IMAGE PROCESSING o BIOMETRIC o HOW IT WORK o APPLICATION o ADVANTAGES o DISADVANTAGES o CONCLUSION o REFERENCE
- 3. The present generation security issue is consider the basic TCP/IP encryption and the other factor that are provided by the network . but there was lack of consistent identification of individual then the newly develop technology “ BIOMETRIC “ biometric can be defined as recognizing and identifying a person based on “ physiological “ or” behavioral” characteristic .
- 4. o An automated teller machine (ATM) is a computerized telecommunications device that provides the customers of a financial institution with access to financial transactions in a public space without the need for a human clerk or bank teller. o In ATMs, the customer is identified by inserting a plastic ATM card with a magnetic stripe or a plastic smartcard with a chip, that contains a unique card number and some security information
- 5. o It is defined in the “real world”, is considered to be a function of two real variables, for example, a (X,Y) with a as the amplitude (e.g. brightness) of the image at the real coordinate position (X,Y). o An image is considered to contain sub-images referred to as regions-of-interest
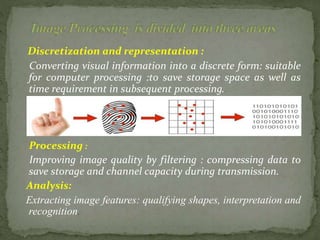
- 6. Discretization and representation : Converting visual information into a discrete form: suitable for computer processing :to save storage space as well as time requirement in subsequent processing. Processing : Improving image quality by filtering : compressing data to save storage and channel capacity during transmission. Analysis: Extracting image features: qualifying shapes, interpretation and recognition.
- 7. o A biometric is a unique, measurable characteristic of a human being that can be used to automatically recognize an individual or verify an individual’s identity. o Biometrics can measure both physiological and behavioral characteristics. o Physiological Biometrics :- This biometrics is based on measurements and data derived from direct measurement of a part of the human body. o Behavioral Biometrics :- this biometrics is based on measurements and data derived from an action.
- 8. PHYSIOLOGICAL a. Finger-scan b. Facial Recognition c. Iris-scan d. Retina-scan e. Hand-scan BEHAVIORAL a. Voice-scan b. Signature-scan c. Keystroke-scan
- 10. DATA COLLECTION TRANSMISSION SIGNAL PROCESSING DATA STORAGE DICISION
- 11. DECISION FLOW CHART OF A BIOMETRIC SYSTEM AQUIRED BIOMATRIC SAMPLE FEAUTER EXTRACTION MATCHING DATABASE
- 12. o Facial recognition uses a software known as facelt ie. based on ability to recognize face and measure various features of face. o Every face has distinct peaks, valleys that make up facial features facelt identifies this landmarks as nodal points. o These nodal points are measured creating a numerical code called face print representing face in database
- 14. o TIME AND ATTENDANCE SYSTEM o AIRPORTS o LIBRARIES o PC ACCESS
- 15. o Increase of reliability and identification quality, while reducing FAR (False Acceptance Rate) error rates. o A variety of identifiers that can be used together or separately. o Useful for senior citizens and rural people
- 16. o Noise: unwanted disturbance(in single modal system ) o Cost (w.r.t instruments) o Time Consuming
- 17. Biometrics provides a higher level of security ,we thus develop an ATM model that is more reliable in providing security by using facial recognition software, which avoids the various attacks in ATM system and fraudulent activities are reduced. The chance given for hackers to make use of fake biometrics to act as an authorized user is strictly avoided, which makes the ATM system more secure. But the cost spend to design and implement this type of system is higher when compared to the existing ATM system.
- 18. o . http ://airccj.org/CSCP/vol2/csit2316.pdf o http://citeseer.ist.psu.edu/viewdoc/summary o T. Kanade. Computer Recognition of Human o Faces o www.inttlelix.com- Application of face o recognition o ehwww.u.es/ ccwintco/uploads/e/ eb /PFC- IonMarques.pdf






