Cryptography
Download as PPTX, PDF131 likes84,822 views
Cryptography is the science of using mathematics to encrypt and decrypt data. Cryptography enables you to store sensitive information or transmit it across insecure networks so that it cannot be read by anyone except the intended recipient.
1 of 22
Downloaded 6,199 times



















Ad
Recommended
Cryptography



CryptographyShivanand Arur This PPT explains about the term "Cryptography - Encryption & Decryption". This PPT is for beginners and for intermediate developers who want to learn about Cryptography. I have also explained about the various classes which .Net provides for encryption and decryption and some other terms like "AES" and "DES".
Cryptography.ppt



Cryptography.pptkusum sharma This document provides an overview of cryptography. It defines cryptography as the science of securing messages from attacks. It discusses basic cryptography terms like plain text, cipher text, encryption, decryption, and keys. It describes symmetric key cryptography, where the same key is used for encryption and decryption, and asymmetric key cryptography, which uses different public and private keys. It also covers traditional cipher techniques like substitution and transposition ciphers. The document concludes by listing some applications of cryptography like e-commerce, secure data, and access control.
Introduction to Cryptography



Introduction to CryptographyMd. Afif Al Mamun Cryptography is the practice of securing communication and information by converting plaintext into ciphertext. The document provides an introduction to cryptography including its history from ancient times to the present. It discusses terminology like plaintext, encryption, ciphertext, decryption, and keys. Symmetric key cryptography uses a single key for encryption and decryption while asymmetric key cryptography uses two different keys. Examples of symmetric methods are DES, 3DES, AES, and RC4, while RSA is a common asymmetric method. Applications of cryptography include ATMs, email passwords, e-payments, e-commerce, electronic voting, defense services, securing data, and access control.
Cryptography



CryptographyDarshini Parikh Cryptography is the practice and study of securing communication through techniques like encryption. It has evolved through manual, mechanical, and modern eras using computers. Cryptography aims to achieve goals like authentication, confidentiality, integrity, and non-repudiation. Common attacks include brute force, chosen plaintext, and differential power analysis. Symmetric cryptography uses a shared key while asymmetric uses public/private key pairs. Digital signatures and watermarks can authenticate documents. DRM and watermarks control digital content distribution.
Cryptography.ppt



Cryptography.pptUday Meena This document provides an overview of cryptography. It begins with basic definitions related to cryptography and a brief history of its use from ancient times to modern ciphers. It then describes different types of ciphers like stream ciphers, block ciphers, and public key cryptosystems. It also covers cryptography methods like symmetric and asymmetric algorithms. Common types of attacks on cryptosystems like brute force, chosen ciphertext, and frequency analysis are also discussed.
cryptography



cryptographyAbhijeet Singh Cryptography is the practice of securing communications through techniques like encryption and decryption. It involves constructing algorithms to protect information from adversaries and ensure data confidentiality, integrity, and authentication. The main types are transposition ciphers, which rearrange letters, and substitution ciphers, which replace letters. Modern cryptography expanded with computers to encrypt any data and uses symmetric key cryptography, where senders and receivers share a key, and public key cryptography, where they have different keys. It has many applications including ATMs, email, remote access, and smart cards.
Cryptography



Cryptographyjayashri kolekar Cryptography is the art and science of securing communication and information by encoding messages so that they are unintelligible to unauthorized parties. It involves techniques for encrypting and decrypting messages to ensure confidentiality, authentication, and integrity. The document defines key terminology related to cryptography such as encryption, decryption, plaintext, ciphertext, and cryptanalysis. It also discusses different types of cryptographic techniques including symmetric and asymmetric encryption as well as cryptographic applications and characteristics.
Cryptography



CryptographyEmaSushan Cryptography is the science of using mathematics to encrypt and decrypt data. This presentation explains about the cryptography, its history, types i.e. symmetric and asymmetric cryptography.
Cryptography



Cryptographysubodh pawar Today in modern era of internet we share some sensitive data to information transmission. but need to ensure security. So we focus on Cryptography modern technique for secure transmission of information over network.
Cryptography ppt



Cryptography pptOECLIB Odisha Electronics Control Library The internet is the internationally connected network of computer networks with addresses that are administrated by IANA
cryptography ppt free download



cryptography ppt free downloadTwinkal Harsora This document presents a seminar on cryptography. It begins with an introduction to cryptography and its purpose in ensuring confidentiality, integrity and accuracy of communications. It then defines cryptography and discusses secret key cryptography which uses a single shared key for encryption and decryption, and public key cryptography which uses separate public and private keys. The document outlines the architecture and process of cryptography, along with common cryptographic algorithms like symmetric and asymmetric key cryptography and hash functions. It also discusses different types of attacks on cryptography like cipher text only and chosen plaintext attacks. The conclusion emphasizes using the appropriate cryptographic algorithm according to the requirements for security and speed of message transmission.
6. cryptography



6. cryptography7wounders The document discusses cryptography concepts such as encryption algorithms, key management, digital signatures, and cryptanalysis attacks. It covers symmetric and asymmetric cryptographic systems as well as specific algorithms like DES, RSA, and elliptic curve cryptography. The document also examines requirements for secrecy, authenticity and properties of cryptographic systems.
Cryptography



Cryptographyprasham95 This presentation will show you the basics of cryptography.
Main topics like basic terminology,goals of cryptography,threats,types of cryptography,algorithms of cryptography,etc. are covered in this presentation.If you like this presentation please do hit the like.
Public Key Cryptosystem



Public Key CryptosystemDevakumar Kp Introduction to Public key Cryptosystems with block diagrams
Reference : Cryptography and Network Security Principles and Practice , Sixth Edition , William Stalling
Symmetric and asymmetric key



Symmetric and asymmetric keyTriad Square InfoSec Symmetric encryption uses a shared secret key between the sender and receiver to encrypt and decrypt messages. It is faster than asymmetric encryption but requires secure key exchange. Asymmetric encryption uses separate public and private keys, where the public key is used to encrypt and the private key decrypts, allowing secure communication without pre-shared keys. Common symmetric algorithms are AES and DES, while asymmetric algorithms include RSA, Diffie-Hellman, and ECDSA.
Public Key Cryptography



Public Key CryptographyGopal Sakarkar Public key cryptography uses two keys, a public key that can encrypt messages and a private key that decrypts messages. It has six components: plain text, encryption algorithm, public and private keys, ciphertext, and decryption algorithm. Some key characteristics are that it is computationally infeasible to determine the private key from the public key alone, and encryption/decryption is easy when the relevant key is known. The requirements of public key cryptography are that it is easy to generate a public-private key pair, easy to encrypt with the public key, easy for the recipient to decrypt with the private key, and infeasible to determine the private key from the public key or recover the plaintext from the ciphertext and public key alone
Cryptography



CryptographyRutuja Solkar A brief introduction to Crytography,the various types of crytography and the advantages and disadvantages associated to using the following tyes with some part of the RSA algorithm
Cryptography and network security



Cryptography and network securitypatisa This document provides an overview of cryptography including:
1. Cryptography is the process of encoding messages to protect information and ensure confidentiality, integrity, authentication and other security goals.
2. There are symmetric and asymmetric encryption algorithms that use the same or different keys for encryption and decryption. Examples include AES, RSA, and DES.
3. Other techniques discussed include digital signatures, visual cryptography, and ways to implement cryptography like error diffusion and halftone visual cryptography.
RSA ALGORITHM



RSA ALGORITHMDr. Shashank Shetty The document summarizes the RSA encryption algorithm. It begins by explaining that RSA was developed in 1977 by Rivest, Shamir and Adleman. It then provides an example to demonstrate how RSA works step-by-step, generating keys, encrypting a message and decrypting the ciphertext. Finally, it discusses some challenges with breaking RSA encryption, including brute force attacks and mathematical attacks based on factoring the encryption keys, as well as timing attacks that aim to deduce keys based on variations in processing time.
S/MIME



S/MIMEmaria azam S/MIME (Secure Multipurpose Internet Mail Extensions) allows users to securely send emails through encryption and digital signatures. It uses public key cryptography, with algorithms like RSA and ElGamal for encryption and DSS and RSA for digital signatures. S/MIME supports encrypting the message contents, digitally signing the message, or both. It defines new MIME types to implement these security features for email. Other technologies like PGP provide similar email security functionality to S/MIME.
Cryptography



CryptographyJens Patel This document provides an overview of cryptography. It defines cryptography as the science of secret writing and discusses its use in applications like ATM cards and passwords. It describes the basic components of cryptography including plaintext, ciphertext, ciphers, keys, and algorithms. It differentiates between symmetric and asymmetric key cryptography. It provides examples of traditional and modern ciphers, including DES, AES, and RSA algorithms. In conclusion, it states that cryptography techniques help maintain data security, privacy, and integrity.
symmetric key encryption algorithms



symmetric key encryption algorithmsRashmi Burugupalli Symmetric Key Encryption Algorithms can be categorized as stream ciphers or block ciphers. Block ciphers like the Data Encryption Standard (DES) operate on fixed-length blocks of bits, while stream ciphers process messages bit-by-bit. DES is an example of a block cipher that encrypts 64-bit blocks using a 56-bit key. International Data Encryption Algorithm (IDEA) is another block cipher that uses a 128-bit key and 64-bit blocks, employing addition and multiplication instead of XOR like DES. IDEA consists of 8 encryption rounds followed by an output transformation to generate the ciphertext from the plaintext and key.
Cryptography



CryptographySagar Janagonda This document discusses cryptography and its various aspects. Cryptography is the science of securing communication and information. It involves encryption to encode data into an unreadable format and decryption to decode it. There are different types of cryptography like symmetric key, public key, and hash functions. Symmetric key uses a single key for encryption and decryption while public key uses different keys. Hash functions create a unique digest from data but the data cannot be recovered from the digest. Cryptography provides security features like authentication, privacy, integrity and non-repudiation. Keys are numerical values used in encryption algorithms. The document outlines advantages like privacy and disadvantages like the time needed for encryption and decryption.
Fundamentals of cryptography



Fundamentals of cryptographyHossain Md Shakhawat Introduction to Cryptography, Fundamentals of cryptography, Encryption, Decryption, Plaintext, Ciphertext, Public key cryptography, Secret key cryptography, steam cipher, block cipher, transposition cipher, security of cryptographic algorithm, cipher attack,
Encryption And Decryption



Encryption And DecryptionNA This document discusses encryption and decryption. It was developed by four students and submitted to their professor. The document introduces encryption as converting plaintext to ciphertext and decryption as converting ciphertext back to plaintext. It explains that encryption uses a key to scramble the plaintext and decryption uses the same key to unscramble the ciphertext to retrieve the original plaintext. The document also briefly mentions the feasibility study, methodology, purpose of providing security, and system requirements for the encryption/decryption software.
Substitution techniques



Substitution techniquesvinitha96 - Substitution techniques involve replacing the letters of plaintext with other letters, numbers or symbols. The main substitution techniques are Caesar cipher, monoalphabetic cipher, Playfair cipher and Hill cipher.
- The Caesar cipher replaces each letter with the letter three positions down the alphabet. The monoalphabetic cipher uses a single alphabetic key for the entire message. The Playfair cipher encrypts pairs of letters based on a 5x5 grid generated from a keyword. The Hill cipher encrypts blocks of letters as numerical values using a matrix-based approach.
Network security cryptography ppt



Network security cryptography pptThushara92 This document discusses network security and cryptography. It begins by defining a network and common network threats. It then discusses network security, including transit and traffic security. It covers problems and attacks like secrecy, authentication, and integrity control. The document introduces cryptography and its use in encryption and decryption to securely transmit data. It describes algorithms like RSA, substitution ciphers, and transposition ciphers. It also covers advantages and disadvantages of cryptography along with a proposed concept to strengthen encryption security.
Email security



Email securityIndrajit Sreemany Electronic mail security requires confidentiality, authentication, integrity, and non-repudiation. Privacy Enhanced Mail (PEM) and Pretty Good Privacy (PGP) provide these security services for email. PEM uses canonical conversion, digital signatures, encryption, and base64 encoding. PGP provides authentication via digital signatures and confidentiality through symmetric encryption of messages with randomly generated session keys. Secure/Multipurpose Internet Mail Extensions (S/MIME) also supports signed and encrypted email to provide security.
Introduction to Cryptography



Introduction to CryptographyPopescu Petre A short introduction to cryptography. What is public and private key cryptography? What is a Caesar Cipher and how do we decrypt it? How does RSA work?
Certification authority



Certification authorityproser tech This document discusses certificate authorities (CAs) and provides an example scenario for securing a web server using a CA. It defines a CA as an entity that issues digital certificates for use by other parties in public key infrastructure schemes. There are commercial CAs, as well as CAs run by institutions and governments. The document then describes the process a CA goes through to issue a certificate and how users can verify certificates. It provides a list of common CAs. Finally, it presents a scenario where a web server obtains a server certificate from a CA to secure its SSL port, and clients can obtain client certificates from the CA's website to access the secure site.
Ad
More Related Content
What's hot (20)
Cryptography



Cryptographysubodh pawar Today in modern era of internet we share some sensitive data to information transmission. but need to ensure security. So we focus on Cryptography modern technique for secure transmission of information over network.
Cryptography ppt



Cryptography pptOECLIB Odisha Electronics Control Library The internet is the internationally connected network of computer networks with addresses that are administrated by IANA
cryptography ppt free download



cryptography ppt free downloadTwinkal Harsora This document presents a seminar on cryptography. It begins with an introduction to cryptography and its purpose in ensuring confidentiality, integrity and accuracy of communications. It then defines cryptography and discusses secret key cryptography which uses a single shared key for encryption and decryption, and public key cryptography which uses separate public and private keys. The document outlines the architecture and process of cryptography, along with common cryptographic algorithms like symmetric and asymmetric key cryptography and hash functions. It also discusses different types of attacks on cryptography like cipher text only and chosen plaintext attacks. The conclusion emphasizes using the appropriate cryptographic algorithm according to the requirements for security and speed of message transmission.
6. cryptography



6. cryptography7wounders The document discusses cryptography concepts such as encryption algorithms, key management, digital signatures, and cryptanalysis attacks. It covers symmetric and asymmetric cryptographic systems as well as specific algorithms like DES, RSA, and elliptic curve cryptography. The document also examines requirements for secrecy, authenticity and properties of cryptographic systems.
Cryptography



Cryptographyprasham95 This presentation will show you the basics of cryptography.
Main topics like basic terminology,goals of cryptography,threats,types of cryptography,algorithms of cryptography,etc. are covered in this presentation.If you like this presentation please do hit the like.
Public Key Cryptosystem



Public Key CryptosystemDevakumar Kp Introduction to Public key Cryptosystems with block diagrams
Reference : Cryptography and Network Security Principles and Practice , Sixth Edition , William Stalling
Symmetric and asymmetric key



Symmetric and asymmetric keyTriad Square InfoSec Symmetric encryption uses a shared secret key between the sender and receiver to encrypt and decrypt messages. It is faster than asymmetric encryption but requires secure key exchange. Asymmetric encryption uses separate public and private keys, where the public key is used to encrypt and the private key decrypts, allowing secure communication without pre-shared keys. Common symmetric algorithms are AES and DES, while asymmetric algorithms include RSA, Diffie-Hellman, and ECDSA.
Public Key Cryptography



Public Key CryptographyGopal Sakarkar Public key cryptography uses two keys, a public key that can encrypt messages and a private key that decrypts messages. It has six components: plain text, encryption algorithm, public and private keys, ciphertext, and decryption algorithm. Some key characteristics are that it is computationally infeasible to determine the private key from the public key alone, and encryption/decryption is easy when the relevant key is known. The requirements of public key cryptography are that it is easy to generate a public-private key pair, easy to encrypt with the public key, easy for the recipient to decrypt with the private key, and infeasible to determine the private key from the public key or recover the plaintext from the ciphertext and public key alone
Cryptography



CryptographyRutuja Solkar A brief introduction to Crytography,the various types of crytography and the advantages and disadvantages associated to using the following tyes with some part of the RSA algorithm
Cryptography and network security



Cryptography and network securitypatisa This document provides an overview of cryptography including:
1. Cryptography is the process of encoding messages to protect information and ensure confidentiality, integrity, authentication and other security goals.
2. There are symmetric and asymmetric encryption algorithms that use the same or different keys for encryption and decryption. Examples include AES, RSA, and DES.
3. Other techniques discussed include digital signatures, visual cryptography, and ways to implement cryptography like error diffusion and halftone visual cryptography.
RSA ALGORITHM



RSA ALGORITHMDr. Shashank Shetty The document summarizes the RSA encryption algorithm. It begins by explaining that RSA was developed in 1977 by Rivest, Shamir and Adleman. It then provides an example to demonstrate how RSA works step-by-step, generating keys, encrypting a message and decrypting the ciphertext. Finally, it discusses some challenges with breaking RSA encryption, including brute force attacks and mathematical attacks based on factoring the encryption keys, as well as timing attacks that aim to deduce keys based on variations in processing time.
S/MIME



S/MIMEmaria azam S/MIME (Secure Multipurpose Internet Mail Extensions) allows users to securely send emails through encryption and digital signatures. It uses public key cryptography, with algorithms like RSA and ElGamal for encryption and DSS and RSA for digital signatures. S/MIME supports encrypting the message contents, digitally signing the message, or both. It defines new MIME types to implement these security features for email. Other technologies like PGP provide similar email security functionality to S/MIME.
Cryptography



CryptographyJens Patel This document provides an overview of cryptography. It defines cryptography as the science of secret writing and discusses its use in applications like ATM cards and passwords. It describes the basic components of cryptography including plaintext, ciphertext, ciphers, keys, and algorithms. It differentiates between symmetric and asymmetric key cryptography. It provides examples of traditional and modern ciphers, including DES, AES, and RSA algorithms. In conclusion, it states that cryptography techniques help maintain data security, privacy, and integrity.
symmetric key encryption algorithms



symmetric key encryption algorithmsRashmi Burugupalli Symmetric Key Encryption Algorithms can be categorized as stream ciphers or block ciphers. Block ciphers like the Data Encryption Standard (DES) operate on fixed-length blocks of bits, while stream ciphers process messages bit-by-bit. DES is an example of a block cipher that encrypts 64-bit blocks using a 56-bit key. International Data Encryption Algorithm (IDEA) is another block cipher that uses a 128-bit key and 64-bit blocks, employing addition and multiplication instead of XOR like DES. IDEA consists of 8 encryption rounds followed by an output transformation to generate the ciphertext from the plaintext and key.
Cryptography



CryptographySagar Janagonda This document discusses cryptography and its various aspects. Cryptography is the science of securing communication and information. It involves encryption to encode data into an unreadable format and decryption to decode it. There are different types of cryptography like symmetric key, public key, and hash functions. Symmetric key uses a single key for encryption and decryption while public key uses different keys. Hash functions create a unique digest from data but the data cannot be recovered from the digest. Cryptography provides security features like authentication, privacy, integrity and non-repudiation. Keys are numerical values used in encryption algorithms. The document outlines advantages like privacy and disadvantages like the time needed for encryption and decryption.
Fundamentals of cryptography



Fundamentals of cryptographyHossain Md Shakhawat Introduction to Cryptography, Fundamentals of cryptography, Encryption, Decryption, Plaintext, Ciphertext, Public key cryptography, Secret key cryptography, steam cipher, block cipher, transposition cipher, security of cryptographic algorithm, cipher attack,
Encryption And Decryption



Encryption And DecryptionNA This document discusses encryption and decryption. It was developed by four students and submitted to their professor. The document introduces encryption as converting plaintext to ciphertext and decryption as converting ciphertext back to plaintext. It explains that encryption uses a key to scramble the plaintext and decryption uses the same key to unscramble the ciphertext to retrieve the original plaintext. The document also briefly mentions the feasibility study, methodology, purpose of providing security, and system requirements for the encryption/decryption software.
Substitution techniques



Substitution techniquesvinitha96 - Substitution techniques involve replacing the letters of plaintext with other letters, numbers or symbols. The main substitution techniques are Caesar cipher, monoalphabetic cipher, Playfair cipher and Hill cipher.
- The Caesar cipher replaces each letter with the letter three positions down the alphabet. The monoalphabetic cipher uses a single alphabetic key for the entire message. The Playfair cipher encrypts pairs of letters based on a 5x5 grid generated from a keyword. The Hill cipher encrypts blocks of letters as numerical values using a matrix-based approach.
Network security cryptography ppt



Network security cryptography pptThushara92 This document discusses network security and cryptography. It begins by defining a network and common network threats. It then discusses network security, including transit and traffic security. It covers problems and attacks like secrecy, authentication, and integrity control. The document introduces cryptography and its use in encryption and decryption to securely transmit data. It describes algorithms like RSA, substitution ciphers, and transposition ciphers. It also covers advantages and disadvantages of cryptography along with a proposed concept to strengthen encryption security.
Email security



Email securityIndrajit Sreemany Electronic mail security requires confidentiality, authentication, integrity, and non-repudiation. Privacy Enhanced Mail (PEM) and Pretty Good Privacy (PGP) provide these security services for email. PEM uses canonical conversion, digital signatures, encryption, and base64 encoding. PGP provides authentication via digital signatures and confidentiality through symmetric encryption of messages with randomly generated session keys. Secure/Multipurpose Internet Mail Extensions (S/MIME) also supports signed and encrypted email to provide security.
Viewers also liked (20)
Introduction to Cryptography



Introduction to CryptographyPopescu Petre A short introduction to cryptography. What is public and private key cryptography? What is a Caesar Cipher and how do we decrypt it? How does RSA work?
Certification authority



Certification authorityproser tech This document discusses certificate authorities (CAs) and provides an example scenario for securing a web server using a CA. It defines a CA as an entity that issues digital certificates for use by other parties in public key infrastructure schemes. There are commercial CAs, as well as CAs run by institutions and governments. The document then describes the process a CA goes through to issue a certificate and how users can verify certificates. It provides a list of common CAs. Finally, it presents a scenario where a web server obtains a server certificate from a CA to secure its SSL port, and clients can obtain client certificates from the CA's website to access the secure site.
Steganography



SteganographyMayank Saxena This document discusses steganography, which is a method of hiding secret information within other information. It begins by providing background on the rise of the internet and the need for information security. It then explains steganography and how it differs from cryptography by not only encrypting messages but hiding their very existence. The document outlines various types of steganography, including techniques for hiding messages in text, audio, images, and video files. It notes some advantages and disadvantages of steganography and discusses the latest research on improving steganography detection.
Network security and protocols



Network security and protocolsOnline This document discusses network security and protocols. It covers internal and external threats to networks like unauthorized access, data destruction, and hacking. It also discusses ways to protect networks from these threats, including passwords, firewalls, encryption, authentication protocols, and virtual local area networks (VLANs). The document outlines concepts like cryptography, digital signatures, and authentication protocols. It also discusses firewalls, storage technologies like RAID, NAS, and SAN for fault tolerance, and tape backups.
Public key cryptography and RSA



Public key cryptography and RSAShafaan Khaliq Bhatti 1. The document discusses public-key cryptography and some of its key concepts like asymmetric encryption where each user has a public and private key.
2. It also covers applications like encryption, digital signatures, and key exchange. It notes that while public-key crypto has advantages, symmetric crypto is still important due to public-key crypto's lower speed.
3. The RSA algorithm is presented as one of the first implementations of public-key cryptography based on the difficulty of factoring large integers.
Introduction to Cryptography



Introduction to CryptographyBharat Kumar Katur This document provides an overview of cryptography concepts including encryption, decryption, symmetric and asymmetric cryptosystems. It discusses X.509 certificates, self-signed certificates, and why certificates need to be signed by a Certificate Authority. It also covers RSA and AES cryptosystems, OpenSSL functions for X509, EVP and RSA, and hybrid cryptosystems.
Steganography Project 



Steganography Project Jitu Choudhary This document provides an overview of steganography. It discusses how steganography hides messages within carriers so that the message is concealed. The document then discusses the history of steganography dating back to ancient Greece. It also discusses modern uses of steganography during the Cold War and by terrorist groups. The document outlines the objectives of the study which are to provide security during message transmission. It then discusses steganography techniques like the LSB algorithm and provides snapshots of its implementation. Finally, it discusses the results of using LSB steganography and concludes with possibilities for further enhancement.
Steganography



SteganographyNeha Sharma Steganography is the art and science of hiding messages within other non-secret text, images, or other files. It works by encoding hidden messages within carrier files like images, videos, or documents in a way that avoids attracting attention to the message itself. Common techniques for steganography include least significant bit insertion and masking and filtering. While it can be used for privacy, it has also been used by hackers, terrorists, and criminals for illegal purposes.
Network Security and Cryptography



Network Security and CryptographyAdam Reagan A brief discussion of network security and an introduction to cryptography. We end the presentation with a discussion of the RSA algorithm, and show how it works with a basic example.
types of network



types of networkZenobia Sukhia There are eight main types of computer networks: LAN, WLAN, WAN, MAN, SAN, CAN, PAN, and DAN. LAN connects devices within a short area like homes or offices. WAN covers long distances to connect computers globally, with the Internet as an example. WLAN is a wireless LAN that connects devices using radio signals instead of wires. Different network types serve various purposes at different scales from personal to worldwide.
Types of computer network



Types of computer networkAmit Shaw There are several types of computer networks:
- Local area networks (LANs) connect devices within a small geographic area like a home or office using technologies like Ethernet or WiFi.
- Metropolitan area networks (MANs) connect devices within a city using technologies like DSL or cable.
- Wide area networks (MANs) connect LANs over long distances using technologies like leased phone lines or satellites.
Steganography 



Steganography Uttam Jain The document provides an overview of steganography, including its definition, history, techniques, applications, and future scope. It discusses different types of steganography such as text, image, and audio steganography. For image steganography, it describes techniques such as LSB insertion and compares image and transform domain methods. It also provides examples of steganography tools and their usage for confidential communication and data protection.
PPT steganography



PPT steganographyparvez Sharaf This document discusses steganography, which is hiding messages within seemingly harmless carriers or covers so that no one apart from the intended recipient knows a message has been sent. It provides examples of steganography in text, images, and audio, as well as methods used for each. These include techniques like least significant bit insertion and temporal sampling rates. The document also covers steganalysis, which aims to detect hidden communications by analyzing changes in the statistical properties of covers.
AES Cryptosystem



AES Cryptosystemهيثم فرج Cryptography and Network security, describe and explain the AES cryptosystem, Explores mistakes in paper research
and Nmap tools.
Advanced Encryption Standard (AES) Implementaion using Java



Advanced Encryption Standard (AES) Implementaion using JavaSunil Kumar R The document describes a project report on the implementation of the AES encryption algorithm. It was submitted by two students, Sunil Kumar R and Shreekant, in partial fulfillment of the requirements for a Bachelor of Engineering degree in computer science. The project was carried out under the guidance of three faculty members at R.V. College of Engineering in Bangalore. It includes a certificate signed by the faculty confirming the students' satisfactory completion of the project.
Digital signature



Digital signatureYash Karanke The document discusses digital signatures, including how they work, their history, applications, and legal status in India. A digital signature uses public and private keys to authenticate a message sender's identity and verify that the message was not altered. It explains how digital signature certificates are issued by certified authorities and associate an individual's identity with their public and private keys. The document also addresses frequently asked questions about digital signatures, such as how they provide security, who issues them, how long they are valid for, and their legal standing.
Digital Signature



Digital Signaturenayakslideshare Digital signatures provide authenticity, integrity and non-repudiation to electronic documents by using public key infrastructure. Under PKI, each individual has a public/private key pair, and certification authorities verify and certify individuals' public keys. Digital signatures are generated by encrypting a document hash with an individual's private key and can be verified by decrypting with the corresponding public key.
Aes



AesKunal Prajapati The document discusses the Advanced Encryption Standard (AES) algorithm. AES is a symmetric block cipher that encrypts data in blocks of 128 bits using cipher keys of 128, 192, or 256 bits. It operates on a 4x4 column-major order state matrix through 10-14 rounds depending on the key size. Each round consists of four steps: byte substitution, shifting rows, mixing columns, and adding the round key. The key is expanded into a key schedule to derive a different round key for each round.
Advanced Encryption Standard (AES)



Advanced Encryption Standard (AES)Amir Masinaei This document discusses AES (Advanced Encryption Standard), a symmetric encryption algorithm. It explains the AES encryption process which involves:
1) Performing rounds of substitution, shifting rows, mixing columns and adding a round key on the plaintext
2) The number of rounds depends on the key size (10 rounds for 128-bit keys)
3) The round keys are derived from the original key through an expansion process
cns 2marks



cns 2marksilakiyadinesh This document contains definitions and explanations of various cryptographic concepts and techniques:
- It defines traffic analysis attacks, rail fence transposition, block ciphers vs stream ciphers, cryptanalysis vs brute force attacks, unconditionally secure vs computationally secure ciphers, the Caesar cipher, monoalphabetic ciphers, Playfair ciphers, one-time pads, transposition ciphers, steganography, and Feistel ciphers.
- It also explains concepts like diffusion vs confusion, the purpose of S-boxes in DES, the avalanche effect, monoalphabetic vs polyalphabetic ciphers, and criteria for evaluating AES candidates.
Ad
Similar to Cryptography (20)
Cryptography



CryptographyShafique Rehman The document discusses various topics in cryptography including encryption, decryption, symmetric and asymmetric cryptography. It defines common cryptography terms like plaintext, ciphertext, encryption, decryption. It explains different encryption techniques like transposition cipher, substitution cipher, stream cipher and block cipher. It also discusses public key cryptography and cryptanalysis. The document concludes by mentioning some techniques to implement network security using cryptography and potential constructive and destructive uses of acoustic cryptanalysis.
Pavan



Pavanpavan kumar The document discusses various topics in cryptography including encryption, decryption, symmetric and asymmetric cryptography. It defines plain text, cipher text, encryption, decryption and keys. It describes different cryptographic techniques like transposition cipher, substitution cipher, stream cipher and block cipher. It also discusses cryptanalysis, acoustic cryptanalysis and ways to prevent it like using rubber keyboards or acoustic cases. It concludes saying cryptography should be used to protect private data and communications.
Cryptography 130919084510-phpapp02(2)



Cryptography 130919084510-phpapp02(2)Vidyadhar Vijju This document summarizes different cryptography techniques for encrypting and decrypting data during transmission. It discusses symmetric cryptography which uses the same key for encryption and decryption, and asymmetric cryptography which uses a public key to encrypt and private key to decrypt. Specific techniques covered include stream ciphers which encrypt single bits, block ciphers which encrypt fixed-length blocks, transposition ciphers which change character order, and substitution ciphers which substitute plaintext with ciphertext. Public key cryptography is also introduced as using a key pair for encryption and decryption separately. In conclusion, cryptography ensures secure data transmission and transactions over networks by encrypting information.
Crpto ppt



Crpto pptAsmita Pal This document provides an overview of cryptography. It discusses security threats and goals, then defines cryptography as using mathematics to encrypt and decrypt data. It describes basic terms like plaintext, encryption, ciphertext, and decryption. The document outlines symmetric and asymmetric key cryptography, and examples of techniques like transposition ciphers, substitution ciphers, stream ciphers, and block ciphers. It concludes that cryptography should be used to implement network security and prevent data leakage through encryption and decryption techniques.
Cryptography 130919084510-phpapp02



Cryptography 130919084510-phpapp02Ravi Kashyap This document summarizes key concepts in cryptography. It discusses plaintext, encryption, ciphertext, decryption, keys, cryptanalysis, cryptographers, cryptanalysts, and cryptology. It also differentiates between symmetric and asymmetric key cryptography, and describes classical ciphers like transposition and substitution ciphers as well as modern ciphers like stream and block ciphers. It provides examples of cryptanalysis techniques like known plaintext analysis and discusses the threat of acoustic cryptanalysis. Throughout it emphasizes the importance of cryptography for network security and secure data transmission.
Computer Security (Cryptography) Ch01



Computer Security (Cryptography) Ch01Saif Kassim This document discusses computer security and network cryptography. It begins by explaining how organizations can use cryptosystems like symmetric and asymmetric encryption to protect data. Symmetric encryption is faster but requires secure key exchange, while asymmetric encryption uses public and private key pairs. The document then defines cryptography terminology and components like plaintext, ciphertext, encryption, decryption, and cryptanalysis. It describes techniques like substitution and transposition ciphers. The rest of the document discusses encryption models, algorithms, and cryptanalysis methods like ciphertext-only and known-plaintext attacks.
CISSP Certification Security Engineering-Part2



CISSP Certification Security Engineering-Part2Hamed Moghaddam Training and Tips that are very helpful to gain knowledge in the field of information Security and passing your CISSP Certification Exam.
To be CISSP Certified Please Check out the link below:
http://asmed.com/cissp-isc2/
Cryptography-Known plain text attack 



Cryptography-Known plain text attack amiteshg Cryptanalysis refers to analyzing encrypted messages to find weaknesses without knowing the encryption key. It involves different types of attacks like known plaintext attacks where the cryptanalyst has samples of plaintext and its encrypted version. The goal of cryptanalysis is to break security systems, while cryptographers aim to develop strong systems. Cryptanalysts use techniques like guessing plaintext to analyze encrypted messages in known plaintext attacks.
Cryptography by Durlab Kumbhakar



Cryptography by Durlab KumbhakarDurlove Kumbhakar Cryptography is the practice of hiding information to store or communicate it in a secure way. It allows for confidentiality, integrity, and authentication of messages. There are two main types: symmetric key cryptography which uses a single key for encryption and decryption, and asymmetric key cryptography which uses different public and private keys. Popular symmetric algorithms include AES and DES, while RSA is an example of an asymmetric algorithm. The seminar discussed the components, processes, and applications of cryptography as well as examples of algorithms and common attacks.
Chapter-Three Part One.pptxghgjhhjghjhjhhj



Chapter-Three Part One.pptxghgjhhjghjhjhhjShemse Shukre gjghkmnmnmnmnmnmnmnmnmnmnmnmnmnmnmnmnmnmnmnHere's an outline for a PowerPoint presentation for Day 1 and Day 2 of Module 3: Mastering Word and Advanced MS Word Techniques. You can utilize this structure to create your slides.
---
### PowerPoint Presentation: Mastering Word & Advanced MS Word Techniques
---
### Slide 1: Title Slide
- **Title**: Mastering Word & Advanced MS Word Techniques
- **Subtitle**: Module 3: Day 1 & Day 2
- **Presented by**: [Your Name]
- **Date**: [Date]
### Slide 2: Agenda
- Day 1: Mastering Word (3 hours)
- Document Structuring and Formatting
- Headers, Footers, and Page Layouts
- Using Lists and Bullets Effectively
- Day 2: Advanced MS Word Techniques (3 hours)
- Sections, Columns, and Document Layouts
- Collaboration Tools: Comments and Track Changes
- Referencing and Citations
---
## Day 1: Mastering Word
### Slide 3: Introduction to Mastering Word
- Overview of Microsoft Word.
- Importance of mastering Word in professional settings.
### Slide 4: Document Structuring and Formatting
- Importance of document structure.
- Key formatting tools (fonts, sizes, styles).
- Using styles for consistency.
### Slide 5: Structuring a Document
- Techniques for creating a well-structured document.
- Titles, subtitles, paragraphs.
- Use of headings and subheadings.
### Slide 6: Formatting Tools Overview
- Ribbon Overview: Home, Insert, Layout
- Key formatting options: Bold, Italics, Underline, and Color.
- Applying styles and themes for a professional look.
### Slide 7: Headers and Footers
- What are headers and footers?
- Steps to insert and edit headers and footers.
- Adding page numbers, document title, and date.
### Slide 8: Page Layouts
- Overview of Page Layout options.
- Setting margins, orientation, and paper size.
- Using gridlines and guides for alignment.
### Slide 9: Using Lists and Bullets Effectively
- Importance of lists and bullets in documents.
- How to create numbered and bulleted lists.
- Customizing bullet styles and list formats.
### Slide 10: Practical Exercise
- Hands-on activity: Create a structured document with headers, footers, and bullet points.
- Participants apply learned formatting techniques.
### Slide 11: Summary of Day 1
- Recap of key points covered.
- Importance of document formatting in effective communication.
---
## Day 2: Advanced MS Word Techniques
Computer Cryptography and Encryption [by: Magoiga].pptx![Computer Cryptography and Encryption [by: Magoiga].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/magoigaencryption-230526085858-fa878162-thumbnail.jpg?width=560&fit=bounds)
![Computer Cryptography and Encryption [by: Magoiga].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/magoigaencryption-230526085858-fa878162-thumbnail.jpg?width=560&fit=bounds)
![Computer Cryptography and Encryption [by: Magoiga].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/magoigaencryption-230526085858-fa878162-thumbnail.jpg?width=560&fit=bounds)
![Computer Cryptography and Encryption [by: Magoiga].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/magoigaencryption-230526085858-fa878162-thumbnail.jpg?width=560&fit=bounds)
Computer Cryptography and Encryption [by: Magoiga].pptxmagoigamtatiro1 This presentation provides a comprehensive introduction to encryption, covering various
techniques, algorithms, and best practices used to secure data and communications. Students will gain a solid understanding of the principles
and applications of cryptography, enabling them to implement robust security solutions in real world scenarios.
Evolution of Cryptography and Cryptographic techniques



Evolution of Cryptography and Cryptographic techniquesMona Rajput 1) Cryptography originated from the inherent human needs to communicate selectively and share information privately.
2) Early forms of cryptography included hieroglyphs and cipher techniques used by ancient Egyptian and Roman civilizations.
3) Modern cryptography is based on mathematical concepts from fields like number theory and uses algorithms like symmetric encryption, asymmetric encryption, hashing, and steganography to provide security services like confidentiality, integrity, authentication, and non-repudiation.
Cryptography.pptxhis document provides an overview of cryptography. It define...



Cryptography.pptxhis document provides an overview of cryptography. It define...researchcollabarator his document provides an overview of cryptography. It defines cryptography as the science of securing messages from att
Cryptography saurabh



Cryptography saurabhSaurabhChakraverty1 It is the introductory important matter about Cryptography and its implementations along with legal issues.
Day5



Day5Jai4uk This document discusses network security and honeypot techniques. It provides an overview of honeypots, including their value in learning about blackhat hacking tools and techniques. It describes different types of honeypots, including first and second generation honeypots, and how they aim to gather information while being difficult to detect. The document also briefly mentions honeynets and the Honeynet Project, an organization dedicated to honeypot research.
Iss lecture 2



Iss lecture 2Ali Habeeb This document discusses symmetric cryptography and provides an overview of symmetric cipher systems including stream ciphers like the Vernam cipher and one-time pad, as well as block ciphers like DES, Triple DES, and AES. It describes the basic components of a symmetric cipher model and the properties and modes of operation for symmetric encryption algorithms. Key topics covered include the Feistel cipher structure used by DES, the cryptanalysis of DES leading to its replacement by AES, and the advantages and disadvantages of stream and block ciphers.
CRYPTOGRAPHY AND NETWORK SECURITY



CRYPTOGRAPHY AND NETWORK SECURITYAdityaShukla141 BEGINS FROM SCRATCH TO FUTURE METHODS OF CRYPTOGRAPHY. PROVIDES A DEEP INSIGHT INTO HISTORY,USES,APPLICATION,DIFFERENT TYPES AND METHODS OF CRYPTOGRAPHY. THANK YOU
Network security Encryption



Network security EncryptionJoel Briza Symmetric encryption uses the same key for both encryption and decryption. It has five components: plaintext, encryption algorithm, secret key, ciphertext, and decryption algorithm. The security depends on keeping the key secret. Symmetric encryption is classified by the type of operations used, number of keys, and how plaintext is processed. Common symmetric algorithms like DES and AES encrypt plaintext in blocks using a substitution-permutation network structure.
Cryptography intro



Cryptography introismaelhaider Cryptography involves encrypting plaintext data into ciphertext using encryption algorithms and keys. Conventional cryptography uses a single secret key for both encryption and decryption, while public key cryptography uses separate public and private keys. The combination of these methods in hybrid cryptosystems like PGP provides both the speed of conventional encryption and the key distribution benefits of public key cryptography.
Cryptography.pptxhis document provides an overview of cryptography. It define...



Cryptography.pptxhis document provides an overview of cryptography. It define...researchcollabarator
Ad
Recently uploaded (20)
Handling Multiple Choice Responses: Fortune Effiong.pptx



Handling Multiple Choice Responses: Fortune Effiong.pptxAuthorAIDNationalRes INTRO TO STATISTICS
INTRO TO SPSS INTERFACE
CLEANING MULTIPLE CHOICE RESPONSE DATA WITH EXCEL
ANALYZING MULTIPLE CHOICE RESPONSE DATA
INTERPRETATION
Q & A SESSION
PRACTICAL HANDS-ON ACTIVITY
Ultimate VMware 2V0-11.25 Exam Dumps for Exam Success



Ultimate VMware 2V0-11.25 Exam Dumps for Exam SuccessMark Soia Boost your chances of passing the 2V0-11.25 exam with CertsExpert reliable exam dumps. Prepare effectively and ace the VMware certification on your first try
Quality dumps. Trusted results. — Visit CertsExpert Now: https://www.certsexpert.com/2V0-11.25-pdf-questions.html
Presentation on Tourism Product Development By Md Shaifullar Rabbi



Presentation on Tourism Product Development By Md Shaifullar RabbiMd Shaifullar Rabbi Presentation on Tourism Product Development By Md Shaifullar Rabbi, Assistant Manager- SABRE Bangladesh.
Political History of Pala dynasty Pala Rulers NEP.pptx



Political History of Pala dynasty Pala Rulers NEP.pptxArya Mahila P. G. College, Banaras Hindu University, Varanasi, India. The Pala kings were people-protectors. In fact, Gopal was elected to the throne only to end Matsya Nyaya. Bhagalpur Abhiledh states that Dharmapala imposed only fair taxes on the people. Rampala abolished the unjust taxes imposed by Bhima. The Pala rulers were lovers of learning. Vikramshila University was established by Dharmapala. He opened 50 other learning centers. A famous Buddhist scholar named Haribhadra was to be present in his court. Devpala appointed another Buddhist scholar named Veerdeva as the vice president of Nalanda Vihar. Among other scholars of this period, Sandhyakar Nandi, Chakrapani Dutta and Vajradatta are especially famous. Sandhyakar Nandi wrote the famous poem of this period 'Ramcharit'.
How to Set warnings for invoicing specific customers in odoo



How to Set warnings for invoicing specific customers in odooCeline George Odoo 16 offers a powerful platform for managing sales documents and invoicing efficiently. One of its standout features is the ability to set warnings and block messages for specific customers during the invoicing process.
Operations Management (Dr. Abdulfatah Salem).pdf



Operations Management (Dr. Abdulfatah Salem).pdfArab Academy for Science, Technology and Maritime Transport This version of the lectures is provided free of charge to graduate students studying the Operations Management course at the MBA level.
Metamorphosis: Life's Transformative Journey



Metamorphosis: Life's Transformative JourneyArshad Shaikh *Metamorphosis* is a biological process where an animal undergoes a dramatic transformation from a juvenile or larval stage to a adult stage, often involving significant changes in form and structure. This process is commonly seen in insects, amphibians, and some other animals.
K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schools



K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schoolsdogden2 Algebra 1 is often described as a “gateway” class, a pivotal moment that can shape the rest of a student’s K–12 education. Early access is key: successfully completing Algebra 1 in middle school allows students to complete advanced math and science coursework in high school, which research shows lead to higher wages and lower rates of unemployment in adulthood.
Learn how The Atlanta Public Schools is using their data to create a more equitable enrollment in middle school Algebra classes.
How to Subscribe Newsletter From Odoo 18 Website



How to Subscribe Newsletter From Odoo 18 WebsiteCeline George Newsletter is a powerful tool that effectively manage the email marketing . It allows us to send professional looking HTML formatted emails. Under the Mailing Lists in Email Marketing we can find all the Newsletter.
The ever evoilving world of science /7th class science curiosity /samyans aca...



The ever evoilving world of science /7th class science curiosity /samyans aca...Sandeep Swamy The Ever-Evolving World of
Science
Welcome to Grade 7 Science4not just a textbook with facts, but an invitation to
question, experiment, and explore the beautiful world we live in. From tiny cells
inside a leaf to the movement of celestial bodies, from household materials to
underground water flows, this journey will challenge your thinking and expand
your knowledge.
Notice something special about this book? The page numbers follow the playful
flight of a butterfly and a soaring paper plane! Just as these objects take flight,
learning soars when curiosity leads the way. Simple observations, like paper
planes, have inspired scientific explorations throughout history.
One Hot encoding a revolution in Machine learning



One Hot encoding a revolution in Machine learningmomer9505 A brief introduction to ONE HOT encoding a way to communicate with machines
pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulse



pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulsesushreesangita003 what is pulse ?
Purpose
physiology and Regulation of pulse
Characteristics of pulse
factors affecting pulse
Sites of pulse
Alteration of pulse
for BSC Nursing 1st semester
for Gnm Nursing 1st year
Students .
vitalsign
LDMMIA Reiki Master Spring 2025 Mini Updates



LDMMIA Reiki Master Spring 2025 Mini UpdatesLDM Mia eStudios As of Mid to April Ending, I am building a new Reiki-Yoga Series. No worries, they are free workshops. So far, I have 3 presentations so its a gradual process. If interested visit: https://www.slideshare.net/YogaPrincess
https://ldmchapels.weebly.com
Blessings and Happy Spring. We are hitting Mid Season.
How to track Cost and Revenue using Analytic Accounts in odoo Accounting, App...



How to track Cost and Revenue using Analytic Accounts in odoo Accounting, App...Celine George Analytic accounts are used to track and manage financial transactions related to specific projects, departments, or business units. They provide detailed insights into costs and revenues at a granular level, independent of the main accounting system. This helps to better understand profitability, performance, and resource allocation, making it easier to make informed financial decisions and strategic planning.
Social Problem-Unemployment .pptx notes for Physiotherapy Students



Social Problem-Unemployment .pptx notes for Physiotherapy StudentsDrNidhiAgarwal Unemployment is a major social problem, by which not only rural population have suffered but also urban population are suffered while they are literate having good qualification.The evil consequences like poverty, frustration, revolution
result in crimes and social disorganization. Therefore, it is
necessary that all efforts be made to have maximum.
employment facilities. The Government of India has already
announced that the question of payment of unemployment
allowance cannot be considered in India
How to Customize Your Financial Reports & Tax Reports With Odoo 17 Accounting



How to Customize Your Financial Reports & Tax Reports With Odoo 17 AccountingCeline George The Accounting module in Odoo 17 is a complete tool designed to manage all financial aspects of a business. Odoo offers a comprehensive set of tools for generating financial and tax reports, which are crucial for managing a company's finances and ensuring compliance with tax regulations.
Multi-currency in odoo accounting and Update exchange rates automatically in ...



Multi-currency in odoo accounting and Update exchange rates automatically in ...Celine George Most business transactions use the currencies of several countries for financial operations. For global transactions, multi-currency management is essential for enabling international trade.
Political History of Pala dynasty Pala Rulers NEP.pptx



Political History of Pala dynasty Pala Rulers NEP.pptxArya Mahila P. G. College, Banaras Hindu University, Varanasi, India.
Operations Management (Dr. Abdulfatah Salem).pdf



Operations Management (Dr. Abdulfatah Salem).pdfArab Academy for Science, Technology and Maritime Transport
Cryptography
- 1. Presented By : Shibani Sarangi IT Branch, Regd no. 1001289324 Guided By : Prof. X 1
- 3. 3 Cryptography is the science of using mathematics to encrypt and decrypt data. Cryptography enables you to store sensitive information or transmit it across insecure networks so that it cannot be read by anyone except the intended recipient.
- 4. 4 Plaintext: Data that can be read and understood without any special measures. Encryption: The method of disguising plaintext in such a way as to hide its substance is called encryption. Cipher text: Encrypting plaintext results in unreadable gibberish called cipher text. Decryption: The process of reverting cipher text to its original plaintext is called decryption. Key: some secret piece of information
- 5. 5 Cryptanalysis: The art of breaking ciphers, i.e. retrieving the plaintext without knowing the proper key. Cryptographers: People who do cryptography Cryptanalysts: Practitioners of cryptanalysis. Cryptology: The branch of mathematics that studies the mathematical foundations of cryptographic methods.
- 6. 6
- 7. 7 For “secret writing” To establish a shared secret when other people (eavesdroppers) are listening. TYPES Mainly classified into two types : 1. Symmetric key cryptography 2. Asymmetric key cryptography
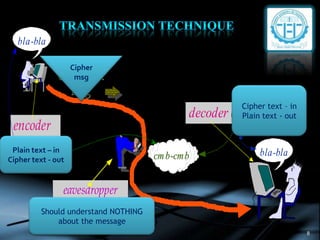
- 8. 8 encoder decoder (plaintext in - ciphertext out) ciphertextciphertext msgmsg (ciphertext in - plaintext out) (should understand nothingnothing about the msg) eavesdropper bla-blabla-bla cmbcmb--cmbcmb bla-blabla-bla Cipher msg Plain text – in Cipher text - out Should understand NOTHING about the message Cipher text – in Plain text - out
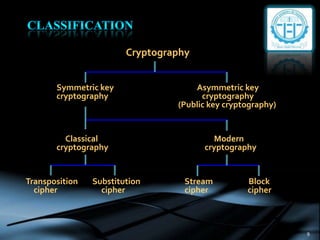
- 9. Cryptography Symmetric key Asymmetric key cryptography cryptography (Public key cryptography) Classical Modern cryptography cryptography Transposition Substitution Stream Block cipher cipher cipher cipher 9
- 11. 11 In classical cryptography, a transposition cipher changes one character from the plaintext to another i.e. the order of the characters is changed.
- 12. 12 Substitution cipher is a method of encryption by which units of plaintext are substituted with ciphertext according to a regular system.
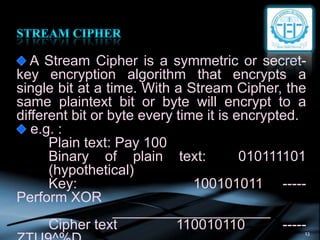
- 13. 13 A Stream Cipher is a symmetric or secret- key encryption algorithm that encrypts a single bit at a time. With a Stream Cipher, the same plaintext bit or byte will encrypt to a different bit or byte every time it is encrypted. e.g. : Plain text: Pay 100 Binary of plain text: 010111101 (hypothetical) Key: 100101011 ----- Perform XOR ____________________ Cipher text 110010110 -----
- 14. 14 Block cipher technique involves encryption of one block of text at a time .Decryption also takes one block of encrypted text at a time. Length of the block is usually 64 or 128 bits. e.g. : Plain text: four and five Four and five Key Key Key wvfa ast wvfa ---
- 15. 15 Public key cryptography is an asymmetric scheme that uses a Pair of keys for encryption: a Public key, which encrypts data, and a corresponding Private key (secret key) for decryption.
- 16. 16 Cryptanalysis refers to the study of ciphers, cipher text, or cryptosystems (that is, to secret code systems) with a view to finding weaknesses in them that will permit retrieval of the plain text from the cipher text, without necessarily knowing the key or the algorithm. This is known as breaking the cipher, cipher text, or cryptosystem. Unlike cryptography which is a clearly
- 17. 17 Known - plain text analysis Chosen – plain text analysis (Differential cryptanalysis) Cipher text - only analysis Man – in – the - middle attack
- 18. 18 It is a side channel attack which exploits sounds emitted by computers or machines. Modern acoustic cryptanalysis mostly focuses on sounds emitted by computer keyboards and internal computer components Historically it has also been applied to impact printers and electromechanical cipher machines.
- 19. 19 Use rubber keyboard or virtual keyboards to prevent keystroke sounds. Use acoustic printers. Use Acoustic case for CPU.
- 20. 20 Cryptography, being an art of encrypting and decrypting confidential information and private messages, should be implemented in the network security to prevent any leakage and threat. It can be done by using any of these techniques discussed above for fortifying the personal data transmission as well as for secure transaction. Acoustic cryptanalysis, being an art of
- 21. Yang, Sarah (14 September 2005), "Researchers recover typed text using audio recording of keystrokes", UC Berkeley News. Adi Shamir & Eran Tromer. "Acoustic cryptanalysis". Blavatnik School of Computer Science, Tel Aviv University. Retrieved 1 November 2011. http://en.wikipedia.org/wiki/Cryptography 21
- 22. 22




