NSClient Workshop: 04 Protocols
- 3. Active Passive Realtime Future Everyx minute Everyx minute Onlyon errors Onlyon errors For eachservice For mostservices Onlyon errors Onlyon errors Verychatty Verychatty Lesschatty Not chatty NRPE NRPE (ish) NSCA NSCA check_nt(ish) NRDP REST REST REST REST NSCP NSCP NSCP NSCP
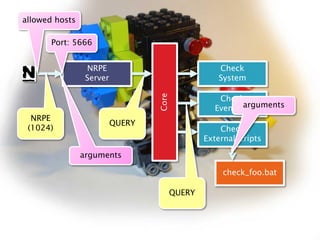
- 5. NRPE Server Core Check System Check EventLog Check ExternalScripts check_foo.bat QUERY NRPE (1024) QUERY Port: 5666 allowedhosts arguments arguments
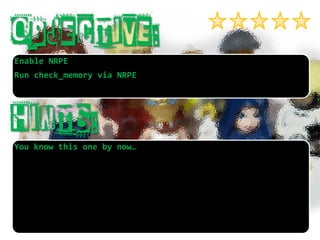
- 10. You know this one by now… Enable NRPE Run check_memoryvia NRPE
- 11. Enable NRPE Run check_memoryvia NRPE nscphelp nscpnrpehelp # Dontforgetto (re)start NSClient++
- 12. Enable NRPE Run check_memoryvia NRPE nscphelp nscpnrpehelp # Dontforgetto (re)start NSClient++ nscpnrpe--help nscpnrpeinstall --help
- 13. Enable NRPE Run check_memoryvia NRPE nscpnrpeinstall --insecure true --allowed-hosts 127.0.0.1 --arguments safe check_nrpe--insecure--host 127.0.0.1 --command check_memory
- 15. Scheduler Core Check System Check EventLog Check ExternalScripts check_foo.bat NSCA (512) QUERY Target: nsca address port password encryption commands interval Etc… NSCAClient Notification
- 17. UsingNSCA
- 18. 3:2 EnableNSCA
- 19. Setup a check_cpucheck every 5 seconds. Send the result via NSCA to localhost:5667 No encryption, password=test
- 20. Setup a check_cpucheck every 5 seconds. Send the result via NSCA to localhost:5667 No encryption, password=test Enable, Schedulerand NSCAClient Firstadda schedule Thenconfiguredefault target
- 21. Setup a check_cpucheck every 5 seconds. Send the result via NSCA to localhost:5667 No encryption, password=test Enable, Schedulerand NSCAClient Firstadda schedule /settings/scheduler/schedules Thenconfiguredefault target /settings/NSCA/client/targets/default
- 22. Setup a check_cpucheck every 5 seconds. Send the result via NSCA to localhost:5667 No encryption, password=test nscptest --settings nsca_server.ini nscptest --settings nsca_client.ini
- 24. WEB Server Core Check System Check EventLog Check ExternalScripts check_foo.bat QUERY HTTP QUERY Port: 8443, 8080allowedhosts arguments
- 25. curl--insecure --header "password: PASSWORD“ https://localhost:8443/query/QUERY?ARGScurl--insecure --header "password: PASSWORD“ https://localhost:8443/query/check_cpu?show-all
- 26. UsingREST
- 27. 3:3 UseREST
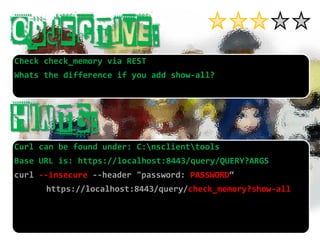
- 28. Curl can be found under: C:nsclienttools Base URL is: https://localhost:8443/query/QUERY?ARGS Check check_memoryvia REST Whatsthe differenceifyouaddshow-all?
- 29. Check check_memoryvia REST Whatsthe differenceifyouaddshow-all? Curl can be found under: C:nsclienttools Base URL is: https://localhost:8443/query/QUERY?ARGS Enable web server and set the password (see previous lab) Then use curl
- 30. Check check_memoryvia REST Whatsthe differenceifyouaddshow-all? Curl can be found under: C:nsclienttools Base URL is: https://localhost:8443/query/QUERY?ARGS Enable web server and set the password (see previous lab) Then use curl Don’t forget: --insecure, --header "password: PASSWORD“
- 31. Check check_memoryvia REST Whatsthe differenceifyouaddshow-all? Curl can be found under: C:nsclienttools Base URL is: https://localhost:8443/query/QUERY?ARGScurl --insecure --header "password: PASSWORD“ https://localhost:8443/query/check_memory?show-all