3 Modern Security - Secure identities to reach zero trust with AAD
- 1. Microsoft 365 Training Series: Security and Compliance
- 2. Secure identities to reach Zero Trust with Azure AD Matt Fooks Clouds in [email protected] Infrastructure Cloud Architect [email protected] Andrew Bettany MVP IT Masterclasses Ltd [email protected]
- 5. 653K1.1B17.5M Every Office 365 and Microsoft Azure customer uses Azure Active Directory Sep 2018 90%90K 450B
- 8. Conditional access Identity protectionSecure authentication
- 11. Password-less authenticationUser-friendly experienceEnterprise-grade security Hello 47M enterprises have deployed Windows Hello for Business active Windows Hello users 6.5K growth in biometric capable computers 350%
- 13. 9M+ 32M+
- 16. Azure AD Password Protection Dynamic banning of passwords based on known bad patterns and those you define. Smart Lockout to thwart bad actors trying to guess passwords. Built for hybrid environments. Unified admin experience for on-premises and cloud. Cloud intelligence to ensure strong passwords
- 18. Azure AD Conditional Access User and location Device Application Real time risk Conditional access
- 19. Corporate Network Geo-location Microsoft Cloud App SecurityMacOS Android iOS Windows Windows Defender ATP Client apps Browser apps Google ID MSA Azure AD ADFS Require MFA Allow/block access Block legacy authentication Force password reset ****** Limited access Controls Employee & Partner Users and Roles Trusted & Compliant Devices Physical & Virtual Location Client apps & Auth Method Conditions Machine learning Policies Real time Evaluation Engine Session Risk 3 40TB Effective policy
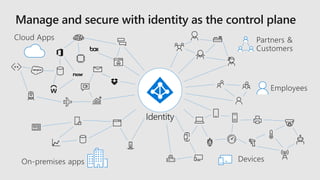
- 20. Productivity Security Timely access to the right resources The right people have the right access to resources
- 21. Identity lifecycle facilities collaboration Access lifecycle provides seamless and efficient access Privileged access lifecycle addresses risks inherent in administration Productivity Security Timely access to the right resources The right people have the right access to resources The right controls that ensure secure productivity Identity Access Admin rights
- 22. Identity lifecycle facilities collaboration Access lifecycle provides seamless and efficient access Privileged access lifecycle addresses risks inherent in administration Productivity Security Timely access to the right resources The right people have the right access to resources The right controls that ensure secure productivity Identity Access Admin rights
- 23. Azure Active Directory access reviews Manage risk and compliance for employees, guests, business partners, and contractors Audit and recertify users’ access to applications, resources, and roles Configure programs to automatically repeat complex review sequences Review current memberships Confirm which memberships to keep Remove stale memberships Request sent to users and resource owners Report status to admin Access Reviews
- 24. Azure AD Privileged Identity Management (PIM) See which users are assigned privileged roles. Enable on-demand, "just in time" administrative access. Set up approval flows for privilege activation. Get alerts and view a history of administrator activation and actions. Review administrative roles and require users to provide justification to retain membership. Manage built-in Azure Resource roles, as well as custom (RBAC) roles IntuneRoleAdministrator DevTestLabsUser SecurityReader VirtualMachineUserLogin ContosoExpensesAppModerator Management and auditing of admin roles across Azure and Office clouds
- 26. First account Compromised Domain Admin Compromised Attack Discovered Research & Preparation Attacker Undetected (Data Exfiltration) Attack Sophistication Target Active Directory (AD) & Identities Attacks not detected. Assume breach Response and Recovery • Attack operators exploit any weakness • Target information on any device or service • Attacks get automated and are industrialized • Active Directory controls access to business assets • Attackers commonly target AD and IT Admins • Time to detect an attack is very short as attacks can occur out of nowhere and might be automated • You may be under attack (or compromised) • Response requires advanced expertise and tools • Expensive and challenging to successfully recover 24-48 Hours 101+ Days
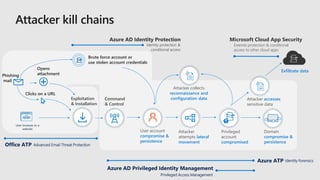
- 27. User browses to a website Phishing mail Opens attachment Clicks on a URL + Exploitation & Installation Command & Control Brute force account or use stolen account credentials User account compromise & persistence Attacker attempts lateral movement Privileged account compromised Domain compromise & persistence Attacker accesses sensitive data Exfiltrate data Azure AD Identity Protection Identity protection & conditional access Microsoft Cloud App Security Extends protection & conditional access to other cloud apps Azure ATP Azure AD Identity Protection Identity protection & conditional access Identity forensics Attacker collects reconnaissance and configuration data Office ATP Azure AD Privileged Identity Management Advanced Email Threat Protection Privileged Access Management
- 28. Microsoft Threat Protection Identities Endpoints User Data Cloud Apps Infrastructure Users and Admins Devices and Sensors Email messages and documents SaaS Applications and Data Stores Servers, Virtual Machines, Databases, Networks Intelligent Security Graph 6.5 TRILLION signals per day
- 29. Get comprehensive Identity protection An integral component of Microsoft Threat Protection Azure AD Identity Protection Azure ATP Microsoft Cloud App Security
- 30. Azure AD Identity Protection Connected intelligence Continuous detection Actionable insights Observe trillions of signals and risk events from cloud systems Apply artificial intelligence and human expertise to derive accurate insights Send alerts, self-mitigate, and automatically remediate threats Protects against 99.6% of identity attacks
- 31. A comprehensive, intelligent security solution that brings the visibility, real-time control, and security you have in your on-premises network to your cloud applications. ControlDiscover Protect Integrates with your SIEM, Identity and Access Management, DLP and Information Protection solutions
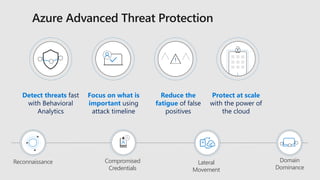
- 32. Azure Advanced Threat Protection Detect threats fast with Behavioral Analytics Focus on what is important using attack timeline Reduce the fatigue of false positives Protect at scale with the power of the cloud Reconnaissance ! ! ! Compromised Credentials Lateral Movement Domain Dominance
- 33. Conditional access Identity protectionSecure authentication
- 34. Protecting against threats can be simple Strengthen your credentials Reduce your attack surface Automate threat response Increase your awareness with auditing and monitor security alerts Enable self-help for more predictable and complete end user security https://aka.ms/securitysteps