Ad
5- Introduction to Networking.type and general
- 2. What is a Network? A network consists of 2 or more computers connected together, and they can communicate and share resources (e.g. information)
- 3. Why Networking? • Sharing information — i.e. data communication • Do you prefer these? • Or this?
- 4. • Sharing hardware or software • Centralize administration and support • E.g. print document • E.g. Internet-based, so everyone can access the same administrative or support application from their PCs
- 5. How many kinds of Networks? • Depending on one’s perspective, we can classify networks in different ways • Based on transmission media: Wired (UTP, coaxial cables, fiber-optic cables) and Wireless • Based on network size: LAN and WAN (and MAN) • Based on management method: Peer-to-peer and Client/Server • Based on topology (connectivity): Bus, Star, Ring … : :
- 6. Local Area Networks (LANs) Characteristics of LANs: (a) Private-owned (b) Small size (c) Transmission technology, (d) Topology
- 7. Metropolitan Area Networks A metropolitan area network based on cable TV.
- 9. Wide Area Networks (WANs) Relation between hosts on LANs and the subnet. WANs are point-to-point networks WANs consist of two distinct components: Transmission lines (copper, fiber, microwave) and Switches (electronics, optics)
- 10. Uses of Computer Networks • Business Applications • Home Applications • Mobile Users • Social Issues
- 11. Two main categories: Guided ― wires, cables Unguided ― wireless transmission, e.g. radio, microwave, infrared, sound, sonar We will concentrate on guided media here: Twisted-Pair cables: Unshielded Twisted-Pair (UTP) cables Shielded Twisted-Pair (STP) cables Coaxial cables Fiber-optic cables Transmission Media
- 12. LAN and WAN Local Area Network (LAN) • Small network, short distance, A room, a floor, a building. • Limited by no. of computers and distance covered • Usually one kind of technology throughout the LAN • Serve a department within an organization • Examples: • Network inside the Student Computer Room • Network inside your home
- 13. Wide Area Network (WAN) A network that uses long-range telecommunication links to connect 2 or more LANs/computers housed in different places far apart. • Towns, states, countries Examples: • Network of our Campus • Internet WAN Student Computer Centre Your home USA
- 14. Peer-to-Peer Networks • Peer-to-peer network is also called workgroup • No hierarchy among computers all are equal • No administrator responsible for the network Peer-to-peer
- 15. Peer-to peer network A peer-to-peer network is a network where the computers act as both workstations and servers. great for small, simple, and inexpensive networks. In a strict peer-to-peer networking setup, every computer is an equal, a peer in the network. Each machine can have resources that are shared with any other machine. There is no assigned role for any particular device, and each of the devices usually runs similar software. Any device can and will send requests to any other.
- 17. • Advantages of peer-to-peer networks: • Low cost • Simple to configure • User has full accessibility of the computer • Disadvantages of peer-to-peer networks: • May have duplication in resources • Difficult to uphold security policy • Difficult to handle uneven loading • Where peer-to-peer network is appropriate: • 10 or less users • No specialized services required • Security is not an issue • Only limited growth in the foreseeable future
- 18. Clients and Servers • Network Clients (Workstation) • Computers that request network resources or services • Network Servers • Computers that manage and provide network resources and services to clients • Usually have more processing power, memory and hard disk space than clients • Run Network Operating System that can manage not only data, but also users, groups, security, and applications on the network • Servers often have a more stringent requirement on its performance and reliability
- 19. Client/Server Networking In this design, a small number of computers are designated as centralized servers and given the task of providing services to a larger number of user machines called clients.
- 21. Advantages of client/server networks • Facilitate resource sharing – centrally administrate and control • Facilitate system backup and improve fault tolerance • Enhance security – only administrator can have access to Server • Support more users – difficult to achieve with peer-to-peer networks Disadvantages of client/server networks • High cost for Servers • Need expert to configure the network • Introduce a single point of failure to the system
- 22. Network topology A topology is a way of “laying out” the network. Topologies can be either physical or logical. Physical topologies describe how the cables are run. Logical topologies describe how the network messages travel
- 23. Topology ― 3 basic types • How so many computers are connected together? Bus Topology Ring Topology Star Topology Hub
- 24. • Bus Topology • Simple and low-cost • A single cable called a trunk (backbone, segment) • Only one computer can send messages at a time • Passive topology - computer only listen for, not regenerate data • Star Topology • Each computer has a cable connected to a single point • More cabling, hence higher cost • All signals transmission through the hub; if down, entire network down • Depending on the intelligence of hub, two or more computers may send message at the same time
- 25. How to construct a network with Bus / Star Topology? Star Topology Bus Topology BNC T-Connector Coaxial cable Network Card
- 26. • Ring Topology • Every computer serves as a repeater to boost signals • Typical way to send data: • Token passing • only the computer who gets the token can send data • Disadvantages • Difficult to add computers • More expensive • If one computer fails, whole network fails T T T dat a T dat a T dat a T dat a T dat a T dat a T Ack T Ack T Ack T Ack T
- 27. Network topology (cont.) Bus (can be both logical and physical) Star (physical only) Ring (can be both logical and physical) Mesh (can be both logical and physical)
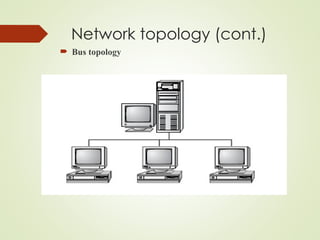
- 28. Network topology (cont.) Bus A bus is the simplest physical topology. It consists of a single cable that runs to every workstation This topology uses the least amount of cabling, but also covers the shortest amount of distance. it is difficult to add a workstation
- 29. Network topology (cont.) Each computer shares the same data and address path. With a logical bus topology, messages pass through the trunk, and each workstation checks to see if the message is addressed to itself. If the address of the message matches the workstation’s address, the network adapter copies the message to the card’s on-board memory. if any one of the cables breaks, the entire network is disrupted. Therefore, it is very expensive to maintain.
- 30. Network topology (cont.) Bus topology
- 31. Network topology (cont.) Star Topology A physical star topology branches each network device off a central device called a hub, making it very easy to add a new workstation. Also, if any workstation goes down it does not affect the entire network. (But, as you might expect, if the central device goes down, the entire network goes down.) Some types of Ethernet and ARCNet use a physical star topology. gives an example of the organization of the star network.
- 32. Network topology (cont.) Star Topology
- 33. Network topology (cont.) Star topologies are easy to install. A cable is run from each workstation to the hub. The hub is placed in a central location in the office. Star topologies are more expensive to install than bus networks, because there are several more cables that need to be installed, plus the cost of the hubs that are needed.
- 34. Network topology (cont.) Ring Each computer connects to two other computers, joining them in a circle creating a unidirectional path where messages move workstation to workstation. Each entity participating in the ring reads a message, then regenerates it and hands it to its neighbor on a different network cable. The ring makes it difficult to add new computers. Unlike a star topology network, the ring topology network will go down if one entity is removed from the ring. Physical ring topology systems don’t exist much anymore, mainly because the hardware involved was fairly expensive and the fault tolerance was very low.
- 35. Network topology (cont.) Ring Topology
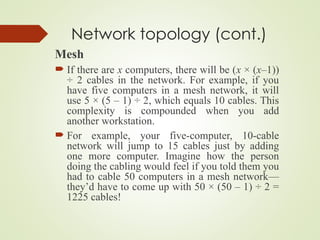
- 36. Network topology (cont.) Mesh The mesh topology is the simplest logical topology in terms of data flow, but it is the most complex in terms of physical design. In this physical topology, each device is connected to every other device This topology is rarely found in LANs, mainly because of the complexity of the cabling.
- 37. Network topology (cont.) Mesh If there are x computers, there will be (x × (x–1)) ÷ 2 cables in the network. For example, if you have five computers in a mesh network, it will use 5 × (5 – 1) ÷ 2, which equals 10 cables. This complexity is compounded when you add another workstation. For example, your five-computer, 10-cable network will jump to 15 cables just by adding one more computer. Imagine how the person doing the cabling would feel if you told them you had to cable 50 computers in a mesh network— they’d have to come up with 50 × (50 – 1) ÷ 2 = 1225 cables!
- 38. Network topology (cont.) Because of its design, the physical mesh topology is very expensive to install and maintain. Cables must be run from each device to every other device. The advantage you gain from it is its high fault tolerance.
- 39. Network topology (cont.) Mesh Topology
- 40. Network topology (cont.) Advantages and Disadvantages of Network Topologies Topology Advantages Disadvantages Bus Cheap. Easy to install. Difficult to reconfigure. Break in bus disables entire network. Star Cheap. Easy to install. Easy to reconfigure. Fault tolerant. More expensive than bus. Ring Efficient. Easy to install. Reconfiguration difficult. Very expensive. Mesh Simplest. Most fault tolerant. Reconfiguration extremely difficult. Extremely expensive. Very complex.