8087 MICROPROCESSOR and diagram with definition.pdf
0 likes270 views
8087 microprocessor
1 of 33
Download to read offline

























![ FLD Source- Decrements the stack pointer by
one and copies a real number from a
stack element or memory location to the new ST.
•FLD ST(3) ;Copies ST(3) to ST.
•FLD LONG_REAL[BX] ;Number from memory
copied to ST.
FLD Destination- Copies ST to a specified stack
position or to a specified memory location .
•FST ST(2) ;Copies ST to ST(2),and increment
stack pointer.
•FST SHORT_REAL[BX] ;Copy ST to a memory at
a SHORT_REAL[BX]
28](https://image.slidesharecdn.com/8087microprocessor-240505131933-9db6895a/85/8087-MICROPROCESSOR-and-diagram-with-definition-pdf-27-320.jpg)

![ FILD Source – Integer load. Convert integer
number from memory to temporary-real
sformat and push on 8087 stack.
•FILD DWORD PTR[BX] ;Short integer from
memory at [BX].
FIST Destination- Integer store. Convert number
from ST to integer and copy to memory.
•FIST LONG_INT ;ST to memory locations named
LONG_INT.
20-Nov-10
30
www.eazynotes.com](https://image.slidesharecdn.com/8087microprocessor-240505131933-9db6895a/85/8087-MICROPROCESSOR-and-diagram-with-definition-pdf-29-320.jpg)




Ad
Recommended
Arm7 Interfacing examples 



Arm7 Interfacing examples Dr.YNM This is meant for Electronics students of SKU and other ECE students who are interested in ARM processor learning.
Architecture of 8051 microcontroller))



Architecture of 8051 microcontroller))Ganesh Ram A microcontroller is a single-chip microprocessor system consisting of a CPU, memory, and input/output ports. It can be considered a complete computer on a single chip. The 8051 was an early microcontroller developed by Intel for use in embedded systems. It had 4KB of program memory, 128 bytes of data memory, timers, counters, and I/O ports. The 8051 has separate memory spaces for program and data memory and its CPU, registers, timers and I/O ports allow it to monitor and control external devices.
Introduction to ARM LPC2148



Introduction to ARM LPC2148Veera Kumar This document provides an introduction to pins, ports, and configuring pins on the ARM LPC2148 microcontroller. It discusses pin configuration, the different ports on the LPC2148, and how to configure pins as inputs, outputs, or alternate functions using the various IO registers. It also provides an example program for blinking an LED connected to pin P1.16 to demonstrate basic pin configuration and output. The document concludes with an assignment to draw the LED blinking circuit and modify the program to blink LEDs on pins P0.16 through P0.23.
Intel 80486 Microprocessor



Intel 80486 MicroprocessorDarpan Dekivadiya The document discusses the Intel 80486 microprocessor. Some key points:
1) The 80486 is an evolutionary step up from the 80386, integrating the math coprocessor on the chip for faster performance.
2) It has an 8KB internal code and data cache, a floating point unit, and 168 pins in a pin grid array package.
3) The architecture includes address and data buses, cache control signals, and status flags in registers like the 80386. It supports protected mode with virtual memory and multitasking capabilities.
VHDL- data types



VHDL- data typesVandanaPagar1 This document provides an overview of various data types and constructs in Verilog hardware description language (HDL), including strings, identifiers, keywords, nets, registers, vectors, integers, real numbers, time, arrays, memories, and parameters. It defines each concept, provides examples of declarations and usage, and references additional resources for further reading. The key topics covered are data representation, variable types, module constructs, and modeling memory in Verilog HDL.
3.programmable interrupt controller 8259



3.programmable interrupt controller 8259MdFazleRabbi18 The document describes the Intel 8259 programmable interrupt controller chip. It contains blocks for buffering data to and from the system data bus, controlling read/write signals, storing interrupt requests in the interrupt request register, masking interrupts in the interrupt mask register, tracking interrupts being serviced in the in-service register, resolving interrupt priorities, and cascading multiple 8259 chips. The pin diagram shows inputs for interrupt requests, read/write control, an ID comparator for cascading, and an 8-bit data bus.
1347 Assembly Language Programming Of 8051



1347 Assembly Language Programming Of 8051techbed The document discusses Assembly Language Programming of the 8051 microcontroller. It covers the following key points in 3 sentences:
Assembly language uses mnemonics to represent machine code instructions and provides a lower level of programming than high-level languages. The 8051 has 8-bit registers including the accumulator register A used for arithmetic, and 4 status flags in the PSW register for carry, overflow, auxiliary carry, and parity. Assembly language programs are assembled into machine code using an assembler and can access different register banks by setting bits in the PSW register.
Ieee 488 by imran



Ieee 488 by imranTaohidur Imran IEEE 488, also known as GPIB or HP-IB, is a digital communications bus standard developed by Hewlett-Packard in the 1960s to connect electronic test and measurement devices. It uses a 24-pin connector and has 16 signal lines for bidirectional communication, bus management, and handshaking between up to 15 connected devices within a maximum distance of 20 meters. Key advantages include its simple hardware interface, ability to connect multiple devices to a single host, and support for mixing slow and fast devices. However, it also has disadvantages such as bulky connectors, lack of early command protocol standards, and high cost.
Evolution of microprocessors and 80486 Microprocessor.



Evolution of microprocessors and 80486 Microprocessor.Ritwik MG The document discusses the evolution of Intel x86 microprocessors from 80186 to 80486. It describes the key features and improvements introduced in each generation, including additional instructions, memory management capabilities, and on-chip cache in 80486. The 80486 is a 32-bit processor compatible with 80386 with enhanced performance due to its highly integrated design and 8KB internal cache. It has the same 4GB memory address space and register set as 80386 but provides faster execution through fewer clock cycles and additional instructions.
Comparison of pentium processor with 80386 and 80486



Comparison of pentium processor with 80386 and 80486Tech_MX The document compares the 80386, 80486, and Pentium processors. It discusses the limitations of the 80286 that led to the development of the 80386, which was a 32-bit processor that could address over 4GB of memory. The 80486 provided improvements like an 8KB cache and integrated floating point unit. The Pentium provided further enhancements such as separate 8KB instruction and data caches, dual integer pipelines, and branch prediction logic. It also introduced the 64-bit memory system. These changes helped significantly increase the processing power and speed of successive processor generations.
Introduction to Interrupts of 8085 microprocessor



Introduction to Interrupts of 8085 microprocessorRAKESHCHOUDHARY164857 The document discusses interrupts in microprocessors. It defines an interrupt as an asynchronous signal from an I/O device that gets the processor's attention. Interrupts can be maskable, which can be delayed, or non-maskable, which cannot. The 8085 interrupt controller supports 5 interrupt lines, including one non-maskable TRAP line. Interrupts are handled through an interrupt vector table that redirects the processor to interrupt service routines.
Register of 80386



Register of 80386aviban The document discusses the registers of the 80386 microprocessor. It describes:
1) The 80386 has eight 32-bit general purpose registers (EAX, EBX, ECX, EDX, EBP, ESP, ESI, EDI) that can be used as either 8-bit or 16-bit registers. It also has six segment registers (CS, SS, DS, ES, FS, GS).
2) The 80386 has additional registers compared to the 8086, including a 32-bit instruction pointer (EIP), status flags register (EFLAGS), and two additional segment registers (FS and GS).
3) The document provides details on the various status flags in
Machine cycles



Machine cyclesWafaAbied The document defines timing diagrams, machine cycles, and T-states. It then discusses the specific machine cycles of the 8085 microprocessor, including the opcode fetch cycle, memory read/write cycles, I/O read/write cycles, and interrupt acknowledge cycle. It provides examples of timing diagrams for various instructions like STA, INR, and discusses registers and instructions like STAX, MVI, LHLD.
8086 pin configuration



8086 pin configurationSridari Iyer Pin Diagram of 8086 simplified
This ppt gives you a step-by-step to understand and remember the pin diagram of 8086
L10 assembly-language-programming-of-atmega328 p



L10 assembly-language-programming-of-atmega328 prsamurti This document discusses assembler programming for the Atmega328P microcontroller. It begins by explaining the language options for programming the microcontroller, including higher-level languages like C/C++ and assembly language. It describes why learning assembly language is important, particularly for understanding the microcontroller's architecture and writing optimized code. The facilities needed for assembly language programming are outlined, including a text editor, assembler, debugger/simulator, and programmer. An overview of the Atmega328P's instruction set is provided, including classifications and addressing modes. Examples of several common instructions like LDI, ADD, MOV, COM, and JMP are described.
Timer counter in arm7(lpc2148)



Timer counter in arm7(lpc2148)Aarav Soni this ppt only for beginner who want to understand concept of Timer counter operation of LPC2148 step by step.
hope it may help u.
always welcoming ur suggestion.
Microprocessor architecture-I



Microprocessor architecture-IDr.YNM This first part of PPT ,explains the basics of 8085 Microprocessor Architecture with the help of a block diagram.
ARM Microcontroller and Embedded Systems (17EC62) – ARM – 32 bit Microcontrol...



ARM Microcontroller and Embedded Systems (17EC62) – ARM – 32 bit Microcontrol...Shrishail Bhat Lecture Slides for ARM Microcontroller and Embedded Systems (17EC62) – ARM – 32 bit Microcontroller (Module 1) for VTU Students
Contents
Thumb-2 technology and applications of ARM, Architecture of ARM Cortex M3, Various Units in the architecture, Debugging support, General Purpose Registers, Special Registers, exceptions, interrupts, stack operation, reset sequence.
Textbook: Joseph Yiu, “The Definitive Guide to the ARM Cortex-M3”, 2nd Edition, Newnes (Elsevier), 2010
INTERRUPTS OF 8086 MICROPROCESSOR



INTERRUPTS OF 8086 MICROPROCESSORGurudev joshi The document discusses interrupts in computing systems. It defines an interrupt as either a hardware-generated call from an external signal or a software-generated call from an instruction. The main purposes of interrupts are to halt normal program execution and divert processing to an interrupt service routine in response to external events. It then provides details on different types of interrupts, including hardware interrupts from devices and software interrupts from instructions. It lists and describes the most common interrupt types and their associated vector numbers.
Instruction formats-in-8086



Instruction formats-in-8086MNM Jain Engineering College The document describes the instruction formats of the 8086 microprocessor. It has 1-6 byte instruction sizes with an opcode field in the first byte. The second byte contains mode, register, and register/memory fields that specify operands. It defines register codes and explains how the mode, register, and register/memory fields are used to determine operands and effective addresses. Examples show how to encode instructions like MOV, SUB, and ADD using the instruction format. Input/output instructions like IN and OUT are also described, indicating how port numbers can be immediate values or specified with the DX register.
8085-microprocessor



8085-microprocessorATTO RATHORE The 8085 microprocessor is an 8-bit microprocessor introduced in 1976 as an updated version of the 8080. It has features like multiplexed address/data bus and interrupt pins. The 8085 consists of units like the accumulator, ALU, registers, program counter, stack pointer, flags, and instruction decoder. It uses flags to indicate arithmetic results and has interrupt controls. Registers are used for data, addressing, and instructions. The timing and control unit coordinates operations using a clock. Serial I/O is also supported.
Uart



UartAditee Apurvaa The document discusses UART (Universal Asynchronous Receiver/Transmitter) communication. It describes how UARTs allow for asynchronous serial communication between devices using only 2 wires by converting parallel data to serial and vice versa. The UART communication process involves a transmitting UART adding start, stop and optionally parity bits to data before transmitting it serially bit-by-bit to a receiving UART which reconstructs the parallel data. It also discusses the TTL and RS-232 physical layer standards for UART.
8251 -USART.pptx



8251 -USART.pptxVikasMahor3 The document discusses the 8251 USART chip, which converts parallel data to serial and vice versa. It describes asynchronous and synchronous communication methods. It provides details on the architecture of the 8251 including the read/write control logic, transmitter, receiver, and modem control sections. It also discusses initializing the chip by writing control words to set the mode, baud rate, parity, and enable transmission or reception.
8086 micro processor



8086 micro processorPoojith Chowdhary The Intel 8086 is a 16-bit microprocessor that can access up to 1 MB of memory. It has two main components: the Bus Interface Unit (BIU) handles bus operations like instruction fetching and memory access, while the Execution Unit (EU) decodes and executes instructions. The BIU contains registers for the code, data, extra, and stack segments as well as an instruction queue. The EU has registers for accumulation, base, count, data, pointers, and flags, and contains an ALU and decoder. It executes instructions from the queued bytes using a pipeline architecture.
MICROPROCESSOR 8085 WITH PROGRAMS



MICROPROCESSOR 8085 WITH PROGRAMSSabin Gautam The document describes a microprocessor, which is an integrated circuit that contains the logic circuitry of a central processing unit on a single chip. It discusses the main components of a microprocessor, including the arithmetic logic unit, register array, control unit, and how they function together. It provides examples of applications for microprocessors across various fields like electronics, mechanical, electrical, medical, computers, and domestic devices. It also includes detailed diagrams and explanations of the architecture, bus structure, registers, flags, and pin descriptions of the specific 8085 microprocessor.
Embedded system and its platforms



Embedded system and its platformsMrunal Deshkar An embedded system can be thought of as a computer hardware system having software embedded in it. It is a microcontroller or microprocessor based system which is designed to perform a specific task. An embedded system has hardware, application software, and a real-time operating system (RTOS) that supervises the application software and provides mechanisms to control latencies according to a fixed plan. Embedded systems are single-functioned, tightly constrained, reactive, real-time systems based on microprocessors with limited memory that are connected and combine both hardware and software.
Math coprocessor 8087



Math coprocessor 8087Fazla Rabbi Mashrur The document discusses the Intel 8087 math coprocessor, which was designed to work alongside the Intel 8086 and 8088 processors to improve floating point calculation performance. It describes the internal architecture of the 8087 including its control unit, numeric execution unit, status register, control register, and tag register. The document also covers how the 8086 and 8087 interface together and synchronize operations.
EE2356 Microprocessor and Microcontroller Lab Manuel



EE2356 Microprocessor and Microcontroller Lab ManuelVelalar College of Engineering and Technology The document discusses assembly language programs for arithmetic operations and data conversions using an 8085 microprocessor. It includes algorithms and programs for 8-bit addition, subtraction, multiplication, and division. It also covers sorting data in ascending and descending order, finding minimum and maximum values, and performing rotate instructions. Additional programs are provided for converting between ASCII, hexadecimal, and BCD codes.
Ad
More Related Content
What's hot (20)
Ieee 488 by imran



Ieee 488 by imranTaohidur Imran IEEE 488, also known as GPIB or HP-IB, is a digital communications bus standard developed by Hewlett-Packard in the 1960s to connect electronic test and measurement devices. It uses a 24-pin connector and has 16 signal lines for bidirectional communication, bus management, and handshaking between up to 15 connected devices within a maximum distance of 20 meters. Key advantages include its simple hardware interface, ability to connect multiple devices to a single host, and support for mixing slow and fast devices. However, it also has disadvantages such as bulky connectors, lack of early command protocol standards, and high cost.
Evolution of microprocessors and 80486 Microprocessor.



Evolution of microprocessors and 80486 Microprocessor.Ritwik MG The document discusses the evolution of Intel x86 microprocessors from 80186 to 80486. It describes the key features and improvements introduced in each generation, including additional instructions, memory management capabilities, and on-chip cache in 80486. The 80486 is a 32-bit processor compatible with 80386 with enhanced performance due to its highly integrated design and 8KB internal cache. It has the same 4GB memory address space and register set as 80386 but provides faster execution through fewer clock cycles and additional instructions.
Comparison of pentium processor with 80386 and 80486



Comparison of pentium processor with 80386 and 80486Tech_MX The document compares the 80386, 80486, and Pentium processors. It discusses the limitations of the 80286 that led to the development of the 80386, which was a 32-bit processor that could address over 4GB of memory. The 80486 provided improvements like an 8KB cache and integrated floating point unit. The Pentium provided further enhancements such as separate 8KB instruction and data caches, dual integer pipelines, and branch prediction logic. It also introduced the 64-bit memory system. These changes helped significantly increase the processing power and speed of successive processor generations.
Introduction to Interrupts of 8085 microprocessor



Introduction to Interrupts of 8085 microprocessorRAKESHCHOUDHARY164857 The document discusses interrupts in microprocessors. It defines an interrupt as an asynchronous signal from an I/O device that gets the processor's attention. Interrupts can be maskable, which can be delayed, or non-maskable, which cannot. The 8085 interrupt controller supports 5 interrupt lines, including one non-maskable TRAP line. Interrupts are handled through an interrupt vector table that redirects the processor to interrupt service routines.
Register of 80386



Register of 80386aviban The document discusses the registers of the 80386 microprocessor. It describes:
1) The 80386 has eight 32-bit general purpose registers (EAX, EBX, ECX, EDX, EBP, ESP, ESI, EDI) that can be used as either 8-bit or 16-bit registers. It also has six segment registers (CS, SS, DS, ES, FS, GS).
2) The 80386 has additional registers compared to the 8086, including a 32-bit instruction pointer (EIP), status flags register (EFLAGS), and two additional segment registers (FS and GS).
3) The document provides details on the various status flags in
Machine cycles



Machine cyclesWafaAbied The document defines timing diagrams, machine cycles, and T-states. It then discusses the specific machine cycles of the 8085 microprocessor, including the opcode fetch cycle, memory read/write cycles, I/O read/write cycles, and interrupt acknowledge cycle. It provides examples of timing diagrams for various instructions like STA, INR, and discusses registers and instructions like STAX, MVI, LHLD.
8086 pin configuration



8086 pin configurationSridari Iyer Pin Diagram of 8086 simplified
This ppt gives you a step-by-step to understand and remember the pin diagram of 8086
L10 assembly-language-programming-of-atmega328 p



L10 assembly-language-programming-of-atmega328 prsamurti This document discusses assembler programming for the Atmega328P microcontroller. It begins by explaining the language options for programming the microcontroller, including higher-level languages like C/C++ and assembly language. It describes why learning assembly language is important, particularly for understanding the microcontroller's architecture and writing optimized code. The facilities needed for assembly language programming are outlined, including a text editor, assembler, debugger/simulator, and programmer. An overview of the Atmega328P's instruction set is provided, including classifications and addressing modes. Examples of several common instructions like LDI, ADD, MOV, COM, and JMP are described.
Timer counter in arm7(lpc2148)



Timer counter in arm7(lpc2148)Aarav Soni this ppt only for beginner who want to understand concept of Timer counter operation of LPC2148 step by step.
hope it may help u.
always welcoming ur suggestion.
Microprocessor architecture-I



Microprocessor architecture-IDr.YNM This first part of PPT ,explains the basics of 8085 Microprocessor Architecture with the help of a block diagram.
ARM Microcontroller and Embedded Systems (17EC62) – ARM – 32 bit Microcontrol...



ARM Microcontroller and Embedded Systems (17EC62) – ARM – 32 bit Microcontrol...Shrishail Bhat Lecture Slides for ARM Microcontroller and Embedded Systems (17EC62) – ARM – 32 bit Microcontroller (Module 1) for VTU Students
Contents
Thumb-2 technology and applications of ARM, Architecture of ARM Cortex M3, Various Units in the architecture, Debugging support, General Purpose Registers, Special Registers, exceptions, interrupts, stack operation, reset sequence.
Textbook: Joseph Yiu, “The Definitive Guide to the ARM Cortex-M3”, 2nd Edition, Newnes (Elsevier), 2010
INTERRUPTS OF 8086 MICROPROCESSOR



INTERRUPTS OF 8086 MICROPROCESSORGurudev joshi The document discusses interrupts in computing systems. It defines an interrupt as either a hardware-generated call from an external signal or a software-generated call from an instruction. The main purposes of interrupts are to halt normal program execution and divert processing to an interrupt service routine in response to external events. It then provides details on different types of interrupts, including hardware interrupts from devices and software interrupts from instructions. It lists and describes the most common interrupt types and their associated vector numbers.
Instruction formats-in-8086



Instruction formats-in-8086MNM Jain Engineering College The document describes the instruction formats of the 8086 microprocessor. It has 1-6 byte instruction sizes with an opcode field in the first byte. The second byte contains mode, register, and register/memory fields that specify operands. It defines register codes and explains how the mode, register, and register/memory fields are used to determine operands and effective addresses. Examples show how to encode instructions like MOV, SUB, and ADD using the instruction format. Input/output instructions like IN and OUT are also described, indicating how port numbers can be immediate values or specified with the DX register.
8085-microprocessor



8085-microprocessorATTO RATHORE The 8085 microprocessor is an 8-bit microprocessor introduced in 1976 as an updated version of the 8080. It has features like multiplexed address/data bus and interrupt pins. The 8085 consists of units like the accumulator, ALU, registers, program counter, stack pointer, flags, and instruction decoder. It uses flags to indicate arithmetic results and has interrupt controls. Registers are used for data, addressing, and instructions. The timing and control unit coordinates operations using a clock. Serial I/O is also supported.
Uart



UartAditee Apurvaa The document discusses UART (Universal Asynchronous Receiver/Transmitter) communication. It describes how UARTs allow for asynchronous serial communication between devices using only 2 wires by converting parallel data to serial and vice versa. The UART communication process involves a transmitting UART adding start, stop and optionally parity bits to data before transmitting it serially bit-by-bit to a receiving UART which reconstructs the parallel data. It also discusses the TTL and RS-232 physical layer standards for UART.
8251 -USART.pptx



8251 -USART.pptxVikasMahor3 The document discusses the 8251 USART chip, which converts parallel data to serial and vice versa. It describes asynchronous and synchronous communication methods. It provides details on the architecture of the 8251 including the read/write control logic, transmitter, receiver, and modem control sections. It also discusses initializing the chip by writing control words to set the mode, baud rate, parity, and enable transmission or reception.
8086 micro processor



8086 micro processorPoojith Chowdhary The Intel 8086 is a 16-bit microprocessor that can access up to 1 MB of memory. It has two main components: the Bus Interface Unit (BIU) handles bus operations like instruction fetching and memory access, while the Execution Unit (EU) decodes and executes instructions. The BIU contains registers for the code, data, extra, and stack segments as well as an instruction queue. The EU has registers for accumulation, base, count, data, pointers, and flags, and contains an ALU and decoder. It executes instructions from the queued bytes using a pipeline architecture.
MICROPROCESSOR 8085 WITH PROGRAMS



MICROPROCESSOR 8085 WITH PROGRAMSSabin Gautam The document describes a microprocessor, which is an integrated circuit that contains the logic circuitry of a central processing unit on a single chip. It discusses the main components of a microprocessor, including the arithmetic logic unit, register array, control unit, and how they function together. It provides examples of applications for microprocessors across various fields like electronics, mechanical, electrical, medical, computers, and domestic devices. It also includes detailed diagrams and explanations of the architecture, bus structure, registers, flags, and pin descriptions of the specific 8085 microprocessor.
Embedded system and its platforms



Embedded system and its platformsMrunal Deshkar An embedded system can be thought of as a computer hardware system having software embedded in it. It is a microcontroller or microprocessor based system which is designed to perform a specific task. An embedded system has hardware, application software, and a real-time operating system (RTOS) that supervises the application software and provides mechanisms to control latencies according to a fixed plan. Embedded systems are single-functioned, tightly constrained, reactive, real-time systems based on microprocessors with limited memory that are connected and combine both hardware and software.
Similar to 8087 MICROPROCESSOR and diagram with definition.pdf (20)
Math coprocessor 8087



Math coprocessor 8087Fazla Rabbi Mashrur The document discusses the Intel 8087 math coprocessor, which was designed to work alongside the Intel 8086 and 8088 processors to improve floating point calculation performance. It describes the internal architecture of the 8087 including its control unit, numeric execution unit, status register, control register, and tag register. The document also covers how the 8086 and 8087 interface together and synchronize operations.
EE2356 Microprocessor and Microcontroller Lab Manuel



EE2356 Microprocessor and Microcontroller Lab ManuelVelalar College of Engineering and Technology The document discusses assembly language programs for arithmetic operations and data conversions using an 8085 microprocessor. It includes algorithms and programs for 8-bit addition, subtraction, multiplication, and division. It also covers sorting data in ascending and descending order, finding minimum and maximum values, and performing rotate instructions. Additional programs are provided for converting between ASCII, hexadecimal, and BCD codes.
8086 microprocessor



8086 microprocessorsavitamhaske The 8086 microprocessor was introduced in 1978 as the first 16-bit microprocessor. It operated at speeds between 5-10 MHz and contained 29,000 transistors. The 8086 included a Bus Interface Unit to fetch instructions and data from memory as well as an Execution Unit to decode and execute instructions. It had general purpose registers like AX, BX, CX, and DX that could be used individually as 8-bit registers or in pairs as 16-bit registers. The 8086 also included segment registers, flag registers, and supported features like an instruction queue and conditional/control flags.
Introduction of 8086 micro processor .



Introduction of 8086 micro processor .Siraj Ahmed The 8086 CPU is a 16-bit microprocessor with a 16-bit data bus, 20-bit address bus, and includes an ALU, BIU, and EU. The BIU fetches instructions and data from memory using segment registers and address pointers, while the EU decodes and executes instructions using general purpose registers like AX, BX, CX, DX, and flags. Memory is divided into segments of up to 64KB that can overlap. The 8086 supports various addressing modes to access memory locations.
Microprocessor Architecture.pptx



Microprocessor Architecture.pptxCaptain Price The document discusses the architecture of the 8086 microprocessor. It describes the various functional blocks including the computational unit, internal storage, instruction decoding unit, and timing and control unit. It also explains the bus interface unit and execution unit that fetch and execute instructions, respectively. Finally, it provides details about the different registers used by the 8086 like the segment registers, flag register, and general purpose registers.
Math Co-processor 8087



Math Co-processor 8087Prothoma Diteeya The 8087 was the first math coprocessor designed by Intel to pair with the 8086 and 8088 processors. It was built to speed up floating point calculations by freeing up the CPU's time and resources. The 8087 introduced 60 new instructions beginning with "F" and contained an control unit and numerical execution unit. It connected to the 8086 via address-data bus lines, status lines, and interrupt/request signals to process floating point operations simultaneously while allowing the CPU to focus on other tasks.
Lab manual mp



Lab manual mpHarshitParkar6677 The document outlines the syllabus for an Introduction to Microprocessors lab course. The syllabus includes topics such as studying the 8085 and 8086 microprocessor systems, developing programs to find the largest/smallest number, convert temperatures, compute squares, and sort numbers, and interfacing components like RAM, keyboard controllers, DMA controllers, and UARTs/USARTs to microprocessors. The document then provides details on studying the 8085 microprocessor system including its architecture, address and data buses, control signals, and functional description. It also provides details on studying the 8086 microprocessor system including its features, pin descriptions, and operating modes.
architecture memory interfacing



architecture memory interfacingShamsul Huda all about architecture and memory interfacing. This is the most important lecture for microprocessor.
In computer science you must known about this lecture.
8086 microprocessor



8086 microprocessorVEERA BOOPATHY E i. The 8086 microprocessor is a 16-bit processor with 16-bit data bus and 20-bit address bus, allowing it to access up to 1 MB of memory space.
ii. It has 14 internal 16-bit registers used for storing data and addressing memory, including the Accumulator (AX), Base (BX), Count (CX), and Data (DX) registers.
iii. The 8086 uses a Harvard architecture with separate buses for instructions and data, allowing it to fetch instructions simultaneously with data processing for improved performance.
8051 Microcontroller



8051 MicrocontrollerNitin Ahire The document discusses the 8051 microcontroller. It provides a brief history, stating that the 8051 was introduced by Intel in 1981 and was the original member of the MCS-51 microcontroller family. It then describes some key aspects of the 8051, including that it combines a CPU, RAM, ROM, I/O ports, and timers on a single chip.
8051 microcontrolle rclass1



8051 microcontrolle rclass1Xavier Institute of Engineering, Mumbai The document discusses the 8051 microcontroller. It provides a brief history, stating that the 8051 was introduced by Intel in 1981 and was the original member of the MCS-51 microcontroller family. It then describes some key aspects of the 8051, including that it combines a CPU, RAM, ROM, I/O ports, and timers on a single chip.
8051 (microcontroller)class1



8051 (microcontroller)class1Nitin Ahire The 8051 microcontroller combines the CPU, RAM, ROM, I/O ports, and timers onto a single chip. It was introduced by Intel in 1981 as an 8-bit microcontroller called the 8051. The 8051 has 4KB of program memory, 128 bytes of RAM, 32 I/O lines, and two timers. It helped popularize embedded systems by providing these components in a single package with low power consumption.
8085 microprocessor(1)



8085 microprocessor(1)Reevu Pal The document describes the 8085 microprocessor. It provides details on the architecture of the 8085 microprocessor including its pin configuration, address and data buses, control signals, interrupts, and block diagram. It also discusses the instruction set of the 8085 which includes data transfer, arithmetic, logical, and branching instructions. Programming models involving registers, flags, stacks, counters, and delays are explained. An example of a traffic light control system using the 8085 is also provided.
ECE 310 22232 Unit II.pptx



ECE 310 22232 Unit II.pptxAkhilNameirakpam The document describes the pin diagram and internal architecture of the 8086 microprocessor, a 16-bit processor with a 16-bit data bus, 20-bit address bus, and registers including general purpose, pointer, base, index, and segment registers. It also provides details on the pins for address, data, control signals, interrupts and their functions. The pin diagram and architecture of the 8086 is compared to the older 8085 8-bit microprocessor.
8085 instruction-set part 1



8085 instruction-set part 1RENUKASHIRBAVIKAR1 This document describes the instruction set of the 8085 microprocessor. It includes descriptions of various instruction groups such as data transfer instructions, arithmetic instructions, logical instructions, branch instructions, stack instructions, I/O instructions, and machine control instructions. Diagrams are provided explaining the program status word register flags and addressing modes used by the 8085 instruction set. Examples of specific instructions like MVI, LXI, and PUSH are also referenced.
8087 COPROCESSOR connection with 8086 and other processors



8087 COPROCESSOR connection with 8086 and other processorsDrVikasMahor The document discusses the architecture and operation of numeric coprocessors used with Intel x86 processors. It describes the 8087, 80287, and later coprocessors and their compatibility with processors like the 8086, 80286, 80386 etc. The key components of the 8087 coprocessor are described, including its 8-register stack, control and status registers, and numeric execution unit. The document also covers the circuit connections and synchronization between the x86 CPU and its numeric coprocessor to ensure proper data transfer and instruction execution.
8086 Architecture, Pin diagram, Addressing modes (3).pdf



8086 Architecture, Pin diagram, Addressing modes (3).pdfYHarika2 bdsihkjnlm;xl,';.z,s/mw.n,bmvnvxbnkm,.s.,/m.nbx
3 organization of intel 8086



3 organization of intel 8086ELIMENG The document describes the organization and architecture of the Intel 8086 microprocessor. It discusses the register organization including general purpose registers, segment registers, and flag register. It also describes the segmented memory addressing scheme, physical address calculation, and instruction queue. The key components of the 8086 architecture including the bus interface unit and execution unit are summarized.
physical_address segmentation.pdf



physical_address segmentation.pdfSwapnil511014 The 8086 microprocessor launched by Intel in 1978 is a 16-bit microprocessor with a 16-bit data bus and 20-bit address bus, allowing it to access up to 1MB of memory. It has two main units - the Bus Interface Unit which handles read/write operations, and the Execution Unit which performs decoding and execution. The 8086 uses memory segmentation to divide the 1MB memory into 64KB segments to overcome the limitation of 16-bit registers. It can have four segments active at a time - code, stack, data, and extra segments.
Ad
More from MalligaarjunanN (20)
English article power point presentation eng.pptx



English article power point presentation eng.pptxMalligaarjunanN Articles are words that indicate a noun without describing it. There are two types of articles: definite ("the") and indefinite ("a", "an"). Articles modify nouns and anything acting as a noun. A compound noun is a noun made up of two or more existing words, such as "snowstorm".
Digital principle and computer design Presentation (1).pptx



Digital principle and computer design Presentation (1).pptxMalligaarjunanN This document discusses the Hardware Description Language (HDL) VHDL. It provides an overview of VHDL, including that it is used to describe and simulate digital circuits, and is an IEEE standard. The key elements of VHDL are then described - entities define input/output ports, architectures describe how the circuit operates, and configurations define how designs are linked together. Examples of each element are provided. Finally, it briefly discusses VHDL modeling styles and objects like constants, variables, and signals.
Technical English grammar and tenses.pptx



Technical English grammar and tenses.pptxMalligaarjunanN The document discusses different verb tenses in English. It defines what tense is and explains that tense is used to indicate the time of an action or state expressed by the verb. It then provides definitions and examples of simple present, present continuous, present perfect, past, past continuous, future, and other tenses including how they are formed and the time or duration they refer to.
Polymorphism topic power point presentation li.pptx



Polymorphism topic power point presentation li.pptxMalligaarjunanN Polymorphism exists widely in Python. Operators like addition can work with different data types like integers, strings, lists, tuples, and dictionaries by supporting polymorphic "add" operations for each type. Methods like repr() also demonstrate polymorphism by converting data to strings in type-appropriate ways, such as converting an integer to its string representation. While Python supports advanced OOP features like operator overloading and multiple inheritance, it does not enforce strict encapsulation with private and public access modifiers, preferring simple syntax instead.
Chemistry iconic bond topic chem ppt.pptx



Chemistry iconic bond topic chem ppt.pptxMalligaarjunanN This document discusses ionic bonds, including what they are, how they are formed between atoms, and the types of ions involved. Ionic bonds are formed through the complete transfer of electrons from one atom to another, creating positively charged cations and negatively charged anions. There are two types of ions that make up ionic bonds - cations, which are positively charged, and anions, which are negatively charged. Simple diagrams are used to illustrate ionic bond formation.
C programming DOC-20230723-WA0001..pptx



C programming DOC-20230723-WA0001..pptxMalligaarjunanN C programming is a course presented by Soundarya.s, a student with roll number 73152213091 studying in the 1st year of CSE-'B' program at K.S.R. College of Engineering. The document appears to be an introduction for a presentation on C programming given by the student.
Chemistry fluorescent topic chemistry.pptx



Chemistry fluorescent topic chemistry.pptxMalligaarjunanN Fluorescence is a chemistry presentation by Varna N.S., a student with registration number 7352214052 studying electrical and electronics engineering. The presentation includes a graph showing the fluorescence phenomenon.
C programming power point presentation c ppt.pptx



C programming power point presentation c ppt.pptxMalligaarjunanN The document discusses random access files in C programming. It defines random access files as files that allow non-sequential reading and writing of data without reading all preceding data. It describes functions like fseek(), ftell(), and rewind() that enable random access. It provides examples of using ftell() to get a file size and fseek() to modify part of a file's contents. It discusses the syntax for creating random access files and advantages like faster access to specific data points compared to sequential access files.
Inheritance_Polymorphism_Overloading_overriding.pptx



Inheritance_Polymorphism_Overloading_overriding.pptxMalligaarjunanN 1. Inheritance allows one class to inherit properties from another class, creating a parent-child relationship between classes.
2. Polymorphism means a function can behave differently depending on its parameters. Method overloading and operator overloading are examples of polymorphism.
3. Overriding occurs when a child class replaces a method in the parent class that shares the same name and parameters. This allows the child class method to perform differently than the parent.
Python programming file handling mhhk.pptx



Python programming file handling mhhk.pptxMalligaarjunanN Files allow data to be persistently stored beyond a program's lifetime. The basic file operations in Python are open, close, read, and write. To open a file, the open() function is used, specifying the filename, mode (such as read 'r', write 'w', or append 'a'), and returning a file object. The file object's close() method finalizes any buffered operations when closing the file. Reading from an open file returns its contents as a sequence of lines, while writing clears the file's existing contents if opened in 'w' mode, or appends to the end if in 'a' mode.
Computer organisation and architecture updated unit 2 COA ppt.pptx



Computer organisation and architecture updated unit 2 COA ppt.pptxMalligaarjunanN The document describes the basic processing unit (CPU) of a computer. It discusses how the CPU fetches, decodes, and executes machine language instructions in 5 steps: 1) fetch instruction, 2) decode and read registers, 3) execute (e.g. ALU operation), 4) access memory or ALU result, 5) write to register. It details the hardware components that perform these steps, including the register file, ALU, and data path. The CPU coordinates operations to perform tasks specified by programs through sequential instruction execution, branching, and waiting for memory as needed.
Data structures trees and graphs - Heap Tree.pptx



Data structures trees and graphs - Heap Tree.pptxMalligaarjunanN The document discusses heap data structures, which are specialized binary trees used to implement priority queues. Heaps have the properties that a parent node's value is always greater than or equal to its children's values (for max heaps) or less than or equal (for min heaps). The key operations on heaps are insertion and deletion of elements, which require pushing nodes up or down the tree to maintain the ordering property. Heaps enable efficient implementations of priority queue operations and are used in algorithms like Dijkstra's and Prim's algorithms.
Data structures trees and graphs - AVL tree.pptx



Data structures trees and graphs - AVL tree.pptxMalligaarjunanN The document discusses AVL trees, which are self-balancing binary search trees. It describes how AVL trees maintain a balance factor of -1, 0, or 1 through rotations. It covers insertion, deletion, and the different types of rotations performed to balance the tree. Examples are provided to illustrate insertion, deletion, and the resulting rotations. AVL trees provide logarithmic time performance for operations by keeping the tree height balanced.
Data structures trees - B Tree & B+Tree.pptx



Data structures trees - B Tree & B+Tree.pptxMalligaarjunanN B-Trees and B+ Trees are data structures used to store large amounts of data on disks when it cannot all fit in main memory. They allow for efficient multilevel indexing and reduce disk access times compared to other balanced trees like AVL trees by keeping the tree height low. B-Trees have multiple keys in each node and store data pointers in internal and leaf nodes, while B+ Trees only store data pointers in leaf nodes. B+ Trees provide faster searches and easier insertion/deletion compared to B-Trees. Both are commonly used in database systems and file systems to efficiently organize and retrieve large blocks of indexed data from secondary storage.
Computer organisation and architecture .



Computer organisation and architecture .MalligaarjunanN The document discusses pipelining in processors. It begins by explaining that pipelining overlaps the execution of instructions to improve performance. It then describes the basic concept of dividing instruction execution into stages connected in a pipeline. It provides details on the stages in a five-stage pipeline model and how instructions can be fetched and executed in an overlapped, pipelined manner. However, it notes pipelining issues can occur if there are dependencies between instructions. It discusses different types of hazards and techniques like forwarding, stalling, and branch prediction that are used to handle hazards in pipelined processors.
Python programming variables and comment



Python programming variables and commentMalligaarjunanN This document discusses functions in Python. It defines what a function is and provides the basic syntax for defining a function using the def keyword. It also covers function parameters, including required, keyword, default, and variable-length arguments. The document explains how to call functions and discusses pass by reference vs pass by value. Additionally, it covers anonymous functions, function scope, and global vs local variables.
pythoncommentsandvariables-231016105804-9a780b91 (1).pptx



pythoncommentsandvariables-231016105804-9a780b91 (1).pptxMalligaarjunanN # Python uses the # symbol to denote single-line comments. Comments are ignored by Python and can be used to explain code. Multiline comments are not directly supported but can be written by using # on each line or using multiline strings that are not assigned to variables. The input() function allows user input and returns a string while print() displays output to the console. These functions can be combined to create interactive programs that collect and output user-provided information.
Python programming - Functions and list and tuples



Python programming - Functions and list and tuplesMalligaarjunanN - A function is a block of reusable code that takes in parameters, performs an action, and returns a value. Functions provide modularity and code reusability.
- Functions in Python are defined using the def keyword followed by the function name and parameters in parentheses. The code block is indented and can return a value. Parameters can have default values.
- Functions can take positional arguments, keyword arguments, and variable length arguments. Parameters are passed by reference, so changes inside the function also affect the variables outside.
- Anonymous functions called lambdas are small single expression functions defined with the lambda keyword. They do not have a name and cannot contain multiple expressions or statements.
Ad
Recently uploaded (20)
Microsoft Office 365 Crack Latest Version 2025?



Microsoft Office 365 Crack Latest Version 2025?yousfhashmi786 COPY PASTE LInK >>
https://click4pc.com/after-verification-click-go-to-download-page/
— Microsoft 365 (Office) is a powerful application designed to centralize all of your commonly used Office and Microsoft 365 applications in one ...
Oxygen Concentrators | Medical Machine Equipment



Oxygen Concentrators | Medical Machine Equipmentblueredblue74 Oxygen concentrators are essential medical devices designed to provide supplemental oxygen to individuals with respiratory conditions.
>parallel desktop Crack Latest Free 2025 | PPT



>parallel desktop Crack Latest Free 2025 | PPTyousfhashmi786 ➤ ►🌍📺📱👉 Click Here to Download Link 100% Working
Link https://click4pc.com/after-verification-click-go-to-download-page/
Parallel Desktop Crack is sincerely some of the existing first-class VM software. It carries Mac OS and a laptop with very cheap-cost specs.
Download Capcut Pro 5.7.1.2152 Crack Latest Version | PPT



Download Capcut Pro 5.7.1.2152 Crack Latest Version | PPTyousfhashmi786 COPY PASTE LInK >>
https://click4pc.com/after-verification-click-go-to-download-page/
The latest CapCut Pro 2025 crack version for PC brings exciting updates and features that enhance your video editing experience. With its advanced video editing ...
荷兰代尔夫特理工大学毕业证书文凭定制TUDelft成绩单定制



荷兰代尔夫特理工大学毕业证书文凭定制TUDelft成绩单定制Taqyea 靠谱制作荷兰毕业证代尔夫特理工大学成绩单!【q微1954292140】帮您解决在荷兰代尔夫特理工大学未毕业难题(Technische Universiteit Delft)文凭购买、毕业证购买、大学文凭购买、大学毕业证购买、买文凭、日韩文凭、英国大学文凭、美国大学文凭、澳洲大学文凭、加拿大大学文凭(q微1954292140)新加坡大学文凭、新西兰大学文凭、爱尔兰文凭、西班牙文凭、德国文凭、教育部认证,买毕业证,毕业证购买,买大学文凭,购买日韩毕业证、英国大学毕业证、美国大学毕业证、澳洲大学毕业证、加拿大大学毕业证(q微1954292140)新加坡大学毕业证、新西兰大学毕业证、爱尔兰毕业证、西班牙毕业证、德国毕业证,回国证明,留信网认证,留信认证办理,学历认证。从而完成就业。代尔夫特理工大学毕业证办理,代尔夫特理工大学文凭办理,代尔夫特理工大学成绩单办理和真实留信认证、留服认证、代尔夫特理工大学学历认证。学院文凭定制,代尔夫特理工大学原版文凭补办,扫描件文凭定做,100%文凭复刻。
特殊原因导致无法毕业,也可以联系我们帮您办理相关材料:
1:在代尔夫特理工大学挂科了,不想读了,成绩不理想怎么办???
2:打算回国了,找工作的时候,需要提供认证《TUDelft成绩单购买办理代尔夫特理工大学毕业证书范本》【Q/WeChat:1954292140】Buy Technische Universiteit Delft Diploma《正式成绩单论文没过》有文凭却得不到认证。又该怎么办???荷兰毕业证购买,荷兰文凭购买,
3:回国了找工作没有代尔夫特理工大学文凭怎么办?有本科却要求硕士又怎么办?
主营项目:
1、真实教育部国外学历学位认证《荷兰毕业文凭证书快速办理代尔夫特理工大学学历认证定购》【q微1954292140】《论文没过代尔夫特理工大学正式成绩单》,教育部存档,教育部留服网站100%可查.
2、办理TUDelft毕业证,改成绩单《TUDelft毕业证明办理代尔夫特理工大学学位证书电子图在线定制服务》【Q/WeChat:1954292140】Buy Technische Universiteit Delft Certificates《正式成绩单论文没过》,代尔夫特理工大学Offer、在读证明、学生卡、信封、证明信等全套材料,从防伪到印刷,从水印到钢印烫金,高精仿度跟学校原版100%相同.
3、真实使馆认证(即留学人员回国证明),使馆存档可通过大使馆查询确认.
4、留信网认证,国家专业人才认证中心颁发入库证书,留信网存档可查.
《代尔夫特理工大学录取通知书offer在线制作荷兰毕业证书办理TUDelft学历证书申请》【q微1954292140】学位证1:1完美还原海外各大学毕业材料上的工艺:水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠。文字图案浮雕、激光镭射、紫外荧光、温感、复印防伪等防伪工艺。
【q微1954292140】办理代尔夫特理工大学毕业证(TUDelft毕业证书)成绩单水印【q微1954292140】代尔夫特理工大学offer/学位证、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作【q微1954292140】Buy Technische Universiteit Delft Diploma购买美国毕业证,购买英国毕业证,购买澳洲毕业证,购买加拿大毕业证,以及德国毕业证,购买法国毕业证(q微1954292140)购买荷兰毕业证、购买瑞士毕业证、购买日本毕业证、购买韩国毕业证、购买新西兰毕业证、购买新加坡毕业证、购买西班牙毕业证、购买马来西亚毕业证等。包括了本科毕业证,硕士毕业证。
荷兰文凭代尔夫特理工大学成绩单,TUDelft毕业证【q微1954292140】办理荷兰代尔夫特理工大学毕业证(TUDelft毕业证书)【q微1954292140】文凭代尔夫特理工大学offer/学位证办学位证、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决代尔夫特理工大学学历学位认证难题。
荷兰文凭购买,荷兰文凭定制,荷兰文凭补办。专业在线定制荷兰大学文凭,定做荷兰本科文凭,【q微1954292140】复制荷兰Technische Universiteit Delft completion letter。在线快速补办荷兰本科毕业证、硕士文凭证书,购买荷兰学位证、代尔夫特理工大学Offer,荷兰大学文凭在线购买。高仿真还原荷兰文凭证书和外壳,定制荷兰代尔夫特理工大学成绩单和信封。修改成绩单分数电子版TUDelft毕业证【q微1954292140】办理荷兰代尔夫特理工大学毕业证(TUDelft毕业证书)【q微1954292140】毕业证成绩单信封等材料最强攻略代尔夫特理工大学offer/学位证学历认证失败怎么办、留信官方学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作。帮你解决代尔夫特理工大学学历学位认证难题。
如果您在英、加、美、澳、欧洲等留学过程中或回国后:
1、在校期间因各种原因未能顺利毕业《TUDelft成绩单工艺详解》【Q/WeChat:1954292140】《Buy Technische Universiteit Delft Transcript快速办理代尔夫特理工大学教育部学历认证书毕业文凭证书》,拿不到官方毕业证;
2、面对父母的压力,希望尽快拿到;
3、不清楚认证流程以及材料该如何准备;
4、回国时间很长,忘记办理;
5、回国马上就要找工作《正式成绩单代尔夫特理工大学毕业证成绩单购买》【q微1954292140】《原版高仿成绩单TUDelft挂科处理解决方案》办给用人单位看;
6、企事业单位必须要求办理的;
7、需要报考公务员、购买免税车、落转户口、申请留学生创业基金。
pharmacology.pdffffffffffffffffffffffffff



pharmacology.pdffffffffffffffffffffffffffanooshaazam312 Pulmonary delivery of biologics (insulin, vaccines, mRNA)
Definition and Purpose
Pulmonary Delivery: Involves administering biologics directly to the lungs via inhalation.
Goal: To achieve rapid absorption into the bloodstream, enhance bioavailability, and improve therapeutic outcomes.
Types of Biologics
• Insulin: Used for diabetes management; inhaled insulin can provide a non-invasive alternative to injections.
• Vaccines: Pulmonary delivery of vaccines (e.g., mRNA vaccines) can stimulate local and systemic immune responses.
• mRNA Therapeutics: Inhalable mRNA formulations can be used for gene therapy and vaccination, allowing for direct delivery to lung cells.
Advantages
• Non-Invasive: Reduces the need for needles, improving patient comfort and compliance.
• Rapid Onset: Direct absorption through the alveolar membrane can lead to quicker therapeutic effects.
• Targeted Delivery: Focuses treatment on the lungs, which is beneficial for respiratory diseases.
Future Directions
• Personalized Medicine: Potential for tailored therapies based on individual patient needs and responses.
• Combination Therapies: Exploring the use of pulmonary delivery for combination therapies targeting multiple diseases.
Gene therapy via inhalation
Definition and Purpose
• Gene Therapy: A technique that involves introducing, removing, or altering genetic material within a patient’s cells to treat or prevent disease.
• Inhalation Delivery: Administering gene therapies directly to the lungs through inhalation, targeting respiratory diseases and conditions.
Mechanism of Action
• Aerosolized Vectors: Utilizes viral or non-viral vectors (e.g., liposomes, nanoparticles) to deliver therapeutic genes to lung cells.
• Cell Uptake: Once inhaled, the vectors penetrate the alveolar epithelium and deliver genetic material to target cells.
Advantages
• Localized Treatment: Direct delivery to the lungs can enhance therapeutic effects while minimizing systemic side effects.
• Non-Invasive: Inhalation is less invasive than traditional injection methods, improving patient compliance.
• Rapid Onset: Potential for quicker therapeutic effects due to direct absorption in the pulmonary system.
Personalized inhaler systems with sensors
• Smart Inhalers: Devices with sensors that track usage and technique.
• Real-Time Monitoring: Connect to apps for data on adherence and inhalation patterns.
• Tailored Treatment: Adjusts medication based on individual usage data.
• Patient Engagement: Provides feedback and reminders to empower self-management.
• Improved Outcomes: Enhances adherence and reduces exacerbations in respiratory conditions.
• Future Potential: May integrate with other health data and use AI for predictive insights.
Sustained-Release Nano Formulations
Definition: Nanoscale drug delivery systems that release therapeutic agents over an extended period.
Components: Made from polymers, lipids, or inorganic materials that encapsulate drugs.
Mechanism:
Wondershare Filmora Crack Free Download Latest 2025



Wondershare Filmora Crack Free Download Latest 2025yousfhashmi786 ➤ ►🌍📺📱👉 Click Here to Download Link 100% Working Link
https://click4pc.com/after-verification-click-go-to-download-page/
Wondershare Filmora is an very impressive video editing software. It allows you to edit and convert videos and share them on a variety of different hosting ...
ppt untuk seminar proposal dan persiapannya



ppt untuk seminar proposal dan persiapannyaRasidinmamakidin ppt untuk seminar proposal dan persiapannya
Introduction-to-Robotics-PowerPoint-Presentation-on-Robotics (1).ppt



Introduction-to-Robotics-PowerPoint-Presentation-on-Robotics (1).pptAshaManjhi A common structure is to start with an introduction that grabs their attention, states your purpose, and outlines your agenda. Then, you move on to the body of your presentation, where you explain your robotics project, its objectives, methods, results, and implications.14 Mar 2024
Adobe Illustrator CC Crack Version 2025?



Adobe Illustrator CC Crack Version 2025?yousfhashmi786 ➤ ►🌍📺📱👉 Click Here to Download Link 100% Working Link
https://click4pc.com/after-verification-click-go-to-download-page/
Adobe Illustrator Crack is a professional vector graphics design software used by graphic designers, illustrators, and artists to create .
8087 MICROPROCESSOR and diagram with definition.pdf
- 1. 2 Compatible Processor and Coprocessor Processors 1. 8086 & 8088 2. 80286 3. 80386DX 4. 80386SX 5. 80486DX 6. 80486SX Coprocessors 1. 8087 2. 80287,80287XL 3. 80287,80387DX 4. 80387SX 5. It is Inbuilt 6. 80487SX
- 2. INTRODUCTION 8087 was the first math coprocessor for 16-bit processors designed by Intel. It was built to pair with 8086 and 8088. The purpose of 8087 was to speed up the computations involving floating point calculations. Addition, subtraction, multiplication and division of simple numbers is not the coprocessor’s job. It does all the calculations involving floating point numbers like scientific calculations and algebraic functions. 3
- 3. INTRODUCTION By having a coprocessor, which performs all the calculations, it can free up a lot of CPU’s time. This would allow the CPU to focus all of its resources on the other functions it has to perform. This increases the overall speed and performance of the entire system. This coprocessor introduced about 60 new instructions available to the programmer. All the mnemonics begin with “F” to differentiate them from the standard 8086 instructions. For e.g.: in contrast to ADD/MUL, 8087 provide FADD/FMUL. 4
- 4. INTRODUCTION Math coprocessor is also called as: Numeric Processor Extension (NPX) Numeric Data Processor (NDP) Floating Point Unit (FPU) 5
- 5. ARCHITECTURE OF 8087 8087 coprocessor is designed to operate with 8086 microprocessor. The microprocessor and coprocessor can execute their respective instructions simultaneously. Microprocessor interprets and executes the normal instruction set and the coprocessor interprets and executes only the coprocessor instructions. All the coprocessor instructions are ESC instructions, i.e. they start with “F”. 6
- 7. ARCHITECTURE OF 8087 The internal structure of 8087 coprocessor is divided into two major sections: Control Unit (CU) Numerical Execution Unit (NEU) 8
- 8. CONTROL UNIT (CU) It interfaces coprocessor to the microprocessor system bus. It also synchronize the operation of the coprocessor and the microprocessor. This unit has a Control Word, Status Word and Data Buffer. If an instruction is ESC instruction, then coprocessor executes it. If not, then microprocessor executes. 9
- 9. NUMERIC EXECUTION UNIT (NEU) This unit is responsible for executing all coprocessor instructions. It has an 8 register stack that holds the operands for instructions and result of instructions. The stack contains 8 registers that are 80-bits wide. Numeric data is transferred inside the coprocessor in two parts: 64-bit mantissa bus 16-bit exponent bus 10
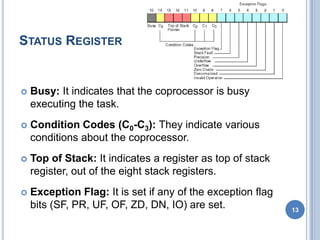
- 11. STATUS REGISTER Status Register tells the overall status of 8087 coprocessor. It is a 16-bit register. It is accessed by executing the FSTSW instruction. This instruction stores the contents of status register into memory. Once the status is stored in memory, the bit positions of the status register can be examined. 12
- 12. STATUS REGISTER Busy: It indicates that the coprocessor is busy executing the task. Condition Codes (C0-C3): They indicate various conditions about the coprocessor. Top of Stack: It indicates a register as top of stack register, out of the eight stack registers. Exception Flag: It is set if any of the exception flag bits (SF, PR, UF, OF, ZD, DN, IO) are set. 13
- 13. STATUS REGISTER Stack Fault: It is not available in 8087. It is active only in 80387 and above. Precision: It indicates that the result has exceeded the selected precision. Underflow: It tells if the result is too small to fit in a register. Overflow: It tells if the result is too large to fit in a register. 14
- 14. STATUS REGISTER Zero Divide: It indicates that you try to divide a non-zero value by zero. Denormalized: It indicates that at least one of the operand is de-normalized. Invalid Operation: It indicates an invalid operation. For e.g.: pushing more than eight items onto the stack, attempting to pop an item off an empty stack or taking the square root of a negative number. 15
- 16. CONTROL REGISTER Control Register controls the operating modes of 8087. It is also a 16-bit register. It performs rounding control and precision control. It is also used to do masking and unmasking of the exception bits that correspond to the rightmost six bits of the status register. FLDCW instruction is used to load the value into control register. 17
- 17. CONTROL REGISTER Rounding Control: It determines the type of rounding or truncating to be done. 00=Round to nearest or even 01=Round down towards minus infinity 10=Round up towards plus infinity 11=Chop or truncate towards zero Precision Control: It sets the precision of the result. 00=Single precision (short) 01=Reserved 10=Double precision (long) 11=Extended precision (temporary) Exception Masks: It determines that whether an error effects the exception bits in the status register. If it is one, then the corresponding error is ignored. If it is zero and the corresponding error occurs, then it generates an interrupt, and the corresponding bit in status register is set. 18
- 18. TAG REGISTER 19 Tag Values: 00 = Valid 01 = Zero 10 = Invalid 11 = Empty TAG 7 TAG 6 TAG 5 TAG 4 TAG 3 TAG 2 TAG 1 TAG 0
- 19. TAG REGISTER Tag Register is used to indicate the contents of each register in the stack. There are total 8 tags (Tag 0 to Tag 7) in this register and each tag uses 2 bits to represent a value. Therefore, it is a 16-bit register. 20 Tag Values: 00 = Valid 01 = Zero 10 = Invalid 11 = Empty TAG 7 TAG 6 TAG 5 TAG 4 TAG 3 TAG 2 TAG 1 TAG 0
- 20. PIN DIAGRAM OF 8087 21 8 0 8 7 GND GND CLK NC NC AD0 AD1 AD2 AD3 AD4 AD5 AD6 AD7 AD8 AD9 AD10 AD11 AD12 AD13 AD14 VCC AD15 A16/S3 A17/S4 A18/S5 A19/S6 BHE/S7 RQ/GT1 INT RQ/GT0 NC NC S2 S1 S0 QS0 QS1 BUSY READY RESET
- 21. INTERFACING OF 8086 AND 8087 Multiplexed address-data bus lines are connected directly from 8086 to 8087. The status lines and the queue status lines are connected directly from 8086 to 8087. The Request/Grant (RQ/GT0 and RQ/GT1) signals of 8087 are connected to RQ/GT0 and RQ/GT1 of 8086. BUSY signal of 8087 is connected to TEST pin of 8086. 22
- 22. EXCEPTION HANDLING The 8087 detects six different types of exception conditions that occur during instruction execution. These will cause an interrupt if unmasked and interrupts are enabled. 1) INVALID OPERATION 2) OVERFLOW 3) ZERO DIVISOR 4) UNDERFLOW 5) DENORMALIZED OPERAND 6) INEXACT RESULT 23
- 23. SYNCHRONIZATION BETWEEN 8086 AND 8087 24 Escape Activate Test Pin Execute 8086 Instruction Wait Deactivate Test Pin Monitor 8086 Wake up Co-processor Wakeup 8086 8086 8087
- 24. DATA TYPES Internally, all data operands are converted to the 80-bit temporary real format. We have 3 types. •Integer data type •Packed BCD data type •Real data type 25
- 25. INSTRUCTION SET The 8087 instruction mnemonics begins with the letter F which stands for Floating point and distinguishes from 8086. The 8087 detects an error condition usually called an exception when it executing an instruction it will set the bit in its Status register. Types I. DATA TRANSFER INSTRUCTIONS. II. ARITHMETIC INSTRUCTIONS. III. COMPARE INSTRUCTIONS. 20-Nov-10 26 www.eazynotes.com
- 26. DATA TRANSFERS INSTRUCTIONS REAL TRANSFER FLD Load real FST Store real FSTP Store real and pop FXCH Exchange registers INTEGER TRANSFER FILD Load integer FIST Store integer FISTP Store integer and pop 27
- 27. FLD Source- Decrements the stack pointer by one and copies a real number from a stack element or memory location to the new ST. •FLD ST(3) ;Copies ST(3) to ST. •FLD LONG_REAL[BX] ;Number from memory copied to ST. FLD Destination- Copies ST to a specified stack position or to a specified memory location . •FST ST(2) ;Copies ST to ST(2),and increment stack pointer. •FST SHORT_REAL[BX] ;Copy ST to a memory at a SHORT_REAL[BX] 28
- 28. FXCH Destination – Exchange the contents of ST with the contents of a specified stack element. •FXCH ST(5) ;Swap ST and ST(5) 20-Nov-10 29 www.eazynotes.com
- 29. FILD Source – Integer load. Convert integer number from memory to temporary-real sformat and push on 8087 stack. •FILD DWORD PTR[BX] ;Short integer from memory at [BX]. FIST Destination- Integer store. Convert number from ST to integer and copy to memory. •FIST LONG_INT ;ST to memory locations named LONG_INT. 20-Nov-10 30 www.eazynotes.com
- 30. ARITHMETIC INSTRUCTIONS. FOUR BASIC ARITHMETIC FUNCTIONS: ADDITION, SUBTRACTION, MULTIPLICATION, AND DIVISION Addition FADD Add real FADDP Add real and pop FIADD Add integer Subtraction FSUB Subtract real FSUBP Subtract real and pop FISUB Subtract integer 31
- 31. Multiplication FMUL Multiply real FMULP Multiply real and pop FIMUL Multiply integer Advanced FABS Absolute value FCHS Change sign FPREM Partial remainder FPRNDINT Round to integer FSCALE Scale FSQRT Square root FXTRACT Extract exponent and mantissa. 20-Nov-10 32 www.eazynotes.com
- 32. FADD ST(3), ST ;Add ST to ST(3), result in ST(3) •FADD ST,ST(4) ;Add ST(4) to ST, result in ST. •FADD ;ST + ST(1), pop stack result at ST •FADDP ST(1) ;Add ST(1) to ST. Increment stack pointer so ST(1) become ST. •FSUB ST(2), ST ;ST(2)=ST(2) – ST. •FSUB Rate ;ST=ST – real no from memory. •FSUB ;ST=( ST(1) – ST) FSUBP - Subtract ST from specified stack element and put result in specified stack element .Then increment the pointer by one. •FSUBP ST(1) ;ST(1)-ST. ST(1) becomes new ST 33
- 33. COMPARE INSTRUCTIONS. FCOM Compare real FCOMP Compare real and pop FCOMPP Compare real and pop twice FICOM Compare integer FICOMP Compare integer and pop FTST Test ST against +0.0 FXAM Examine ST Transcendental Instruction. 34














