Knowledge Discovery Using Data Mining
9 likes1,179 views
This document provides an overview of business intelligence technologies including knowledge discovery, the KDD process, data mining algorithms, and classification of algorithms. It discusses the KDD process steps of data cleaning, integration, selection, transformation, mining, pattern evaluation, and knowledge presentation. It also describes common data mining algorithm types like classification, regression, segmentation, association, and sequence analysis. The Apriori algorithm and Weka tool are presented as examples.
1 of 22




















Ad
Recommended
3. mining frequent patterns



3. mining frequent patternsAzad public school The document discusses frequent pattern mining and the Apriori algorithm. It introduces frequent patterns as frequently occurring sets of items in transaction data. The Apriori algorithm is described as a seminal method for mining frequent itemsets via multiple passes over the data, generating candidate itemsets and pruning those that are not frequent. Challenges with Apriori include multiple database scans and large number of candidate sets generated.
5.1 mining data streams



5.1 mining data streamsKrish_ver2 This document discusses techniques for mining data streams. It begins by defining different types of streaming data like time-series data and sequence data. It then discusses the characteristics of data streams like their huge volume, fast changing nature, and requirement for real-time processing. The key challenges in stream query processing are the unbounded memory requirements and need for approximate query answering. The document outlines several synopsis data structures and techniques used for mining data streams, including random sampling, histograms, sketches, and randomized algorithms. It also discusses architectures for stream query processing and classification of dynamic data streams.
S/MIME



S/MIMEmaria azam S/MIME (Secure Multipurpose Internet Mail Extensions) allows users to securely send emails through encryption and digital signatures. It uses public key cryptography, with algorithms like RSA and ElGamal for encryption and DSS and RSA for digital signatures. S/MIME supports encrypting the message contents, digitally signing the message, or both. It defines new MIME types to implement these security features for email. Other technologies like PGP provide similar email security functionality to S/MIME.
20. Parallel Databases in DBMS



20. Parallel Databases in DBMSkoolkampus The document discusses different types of parallelism that can be utilized in parallel database systems: I/O parallelism to retrieve relations from multiple disks in parallel, interquery parallelism to run different queries simultaneously, intraquery parallelism to parallelize operations within a single query, and intraoperation parallelism to parallelize individual operations like sort and join. It also covers techniques for partitioning relations across disks and handling skew to balance the workload.
5.2 mining time series data



5.2 mining time series dataKrish_ver2 This document discusses time-series data and methods for analyzing it. Time-series data consists of sequential values measured over time that can be analyzed to identify patterns, trends, and outliers. Key methods discussed include trend analysis to identify long-term movements, seasonal variations, and irregular components; similarity search to find similar sequences; and dimensionality reduction and transformation techniques to reduce data size before analysis or indexing.
Multimedia system, Architecture & Databases



Multimedia system, Architecture & DatabasesHarshita Ved The document discusses multimedia databases and multimedia database management systems. It defines multimedia databases as collections of related multimedia data types including text, images, audio, and video. It also describes the additional metadata that must be managed along with the actual multimedia data. Multimedia database management systems provide support for different data formats and facilitate creation, storage, retrieval, querying, and control of multimedia data.
Distributed file system



Distributed file systemAnamika Singh The document discusses key concepts related to distributed file systems including:
1. Files are accessed using location transparency where the physical location is hidden from users. File names do not reveal storage locations and names do not change when locations change.
2. Remote files can be mounted to local directories, making them appear local while maintaining location independence. Caching is used to reduce network traffic by storing recently accessed data locally.
3. Fault tolerance is improved through techniques like stateless server designs, file replication across failure independent machines, and read-only replication for consistency. Scalability is achieved by adding new nodes and using decentralized control through clustering.
Distributed Processing



Distributed ProcessingImtiaz Hussain Distributed processing is a technique where computing tasks and data are distributed across multiple computers or devices that are connected through communication facilities. A distributed system is one where components located at networked computers communicate and coordinate their actions by passing messages. Some key forms of distributed processing include centralized, decentralized, parallel, open distributed processing, and clustering. Distributed processing provides advantages like quicker response times, lower costs, improved data integrity, and resource sharing, but also poses challenges like heterogeneity, security, scalability, and failure handling.
01 Data Mining: Concepts and Techniques, 2nd ed.



01 Data Mining: Concepts and Techniques, 2nd ed.Institute of Technology Telkom The document provides an overview of data mining concepts and techniques. It introduces data mining, describing it as the process of discovering interesting patterns or knowledge from large amounts of data. It discusses why data mining is necessary due to the explosive growth of data and how it relates to other fields like machine learning, statistics, and database technology. Additionally, it covers different types of data that can be mined, functionalities of data mining like classification and prediction, and classifications of data mining systems.
multi dimensional data model



multi dimensional data modelmoni sindhu The document discusses multidimensional databases and data warehousing. It describes multidimensional databases as optimized for data warehousing and online analytical processing to enable interactive analysis of large amounts of data for decision making. It discusses key concepts like data cubes, dimensions, measures, and common data warehouse schemas including star schema, snowflake schema, and fact constellations.
Cryptography and Network Security William Stallings Lawrie Brown



Cryptography and Network Security William Stallings Lawrie BrownInformation Security Awareness Group Block ciphers like DES encrypt data in blocks and are based on the Feistel cipher structure. DES encrypts 64-bit blocks using a 56-bit key and 16 rounds of encryption. Modern cryptanalysis techniques like differential and linear cryptanalysis use statistical analysis to reveal weaknesses in block ciphers, though DES remains relatively secure against these attacks. Careful design of block ciphers, including aspects like non-linear substitution boxes and complex key scheduling, aims to provide security against cryptanalysis.
Data Hiding Techniques



Data Hiding Techniquesprashant3535 This document discusses various techniques for hiding data in the Microsoft Windows operating system. It covers logical techniques like assigning hidden and system attributes, changing file extensions and icons. It also discusses more advanced techniques like using alternate data streams that allow hiding data in files, and using class identifiers (CLSIDs) meant for special folders for regular folders to disguise hidden data. The document provides an overview of the NTFS file system used by Windows and how its alternate data stream feature can be exploited for data hiding. It also recommends some tools that can be used to detect hidden data streams.
3 Data Mining Tasks



3 Data Mining TasksMahmoud Alfarra Data Mining Tasks
Data mining tasks are the kind of data patterns that can be mined.
Challenges of Data Mining
Data mining application
Mining Association Rules in Large Database



Mining Association Rules in Large DatabaseEr. Nawaraj Bhandari Association rule mining is used to find interesting relationships among data items in large datasets. It can help with business decision making by analyzing customer purchasing patterns. For example, market basket analysis looks at what items are frequently bought together. Association rules use support and confidence metrics, where support is the probability an itemset occurs and confidence is the probability that a rule is correct. The Apriori algorithm is commonly used to generate association rules by first finding frequent itemsets that meet a minimum support threshold across multiple passes of the data. It then generates rules from those itemsets if they meet a minimum confidence. Association rule mining has various applications and can provide useful insights but also has computational limitations.
Language for specifying lexical Analyzer



Language for specifying lexical AnalyzerArchana Gopinath The document discusses the role and process of lexical analysis using LEX. LEX is a tool that generates a lexical analyzer from regular expression rules. A LEX source program consists of auxiliary definitions for tokens and translation rules that match regular expressions to actions. The lexical analyzer created by LEX reads input one character at a time and finds the longest matching prefix, executes the corresponding action, and places the token in a buffer.
Data mining , Knowledge Discovery Process, Classification



Data mining , Knowledge Discovery Process, ClassificationDr. Abdul Ahad Abro The document provides an overview of data mining techniques and processes. It discusses data mining as the process of extracting knowledge from large amounts of data. It describes common data mining tasks like classification, regression, clustering, and association rule learning. It also outlines popular data mining processes like CRISP-DM and SEMMA that involve steps of business understanding, data preparation, modeling, evaluation and deployment. Decision trees are presented as a popular classification technique that uses a tree structure to split data into nodes and leaves to classify examples.
Fundamentals of Database system



Fundamentals of Database systemphilipsinter This document provides an overview of database system concepts and architecture. It discusses different data models including conceptual, physical and implementation models. It also covers database languages, interfaces, utilities and centralized versus distributed (client-server) architectures. Specifically, it describes hierarchical and network data models, the three schema architecture, data independence, DBMS languages like DDL and DML, and different DBMS classifications including relational, object-oriented and distributed systems.
data generalization and summarization 



data generalization and summarization janani thirupathi This document discusses data generalization and summarization techniques. It describes how attribute-oriented induction generalizes data from low to high conceptual levels by examining attribute values. The number of distinct values for each attribute is considered, and attributes may be removed, generalized up concept hierarchies, or retained in the generalized relation. An algorithm for attribute-oriented induction takes a relational database and data mining query as input and outputs a generalized relation. Generalized data can be presented as crosstabs, bar charts, or pie charts.
Data Warehouses & Deployment By Ankita dubey



Data Warehouses & Deployment By Ankita dubeyAnkita Dubey This document contains the notes about data warehouses and life cycle for data warehouse deployment project. This can be useful for students or working professionals to gain the basic knowledge about Data warehouses.
Multimedia Database 



Multimedia Database Avnish Patel Multimedia databases store various media types like text, images, audio and video. They allow querying and retrieval of data based on content. Relational databases store multimedia as BLOBs while object-oriented databases represent multimedia as classes and objects. Challenges include large data size, different formats, and complex queries required for content-based retrieval from multimedia data. Applications include digital libraries, education, entertainment and geographic information systems.
Terminologies Used In Big data Environments,G.Sumithra,II-M.sc(computer scien...



Terminologies Used In Big data Environments,G.Sumithra,II-M.sc(computer scien...sumithragunasekaran Terminologies and its types
In-Memory Analytics
In-Database processing
Symmetric Multiprocessor system(SMP)
Massively Parallel Processing
Difference Between Parallel and Distributed Systems
Shared Nothing Architecture
Advantages of a “ shared nothing Architecture”
CAP Theorem Explained
CAP Theorem
Kdd process



Kdd processRajesh Chandra The KDD process involves several steps: data cleaning to remove noise, data integration of multiple sources, data selection of relevant data, data transformation into appropriate forms for mining, applying data mining techniques to extract patterns, evaluating patterns for interestingness, and representing mined knowledge visually. The KDD process aims to discover useful knowledge from various data types including databases, data warehouses, transactional data, time series, sequences, streams, spatial, multimedia, graphs, engineering designs, and web data.
Text data mining1



Text data mining1KU Leuven Text mining seeks to extract useful information from unstructured text documents. It involves preprocessing the text, identifying features, and applying techniques from data mining, machine learning and natural language processing to discover patterns. The core operations of text mining include analyzing distributions of concepts, identifying frequent concept sets and associations between concepts. Text mining systems aim to analyze document collections over time to identify trends, ephemeral relationships and anomalous patterns.
Tcpip services and applications



Tcpip services and applicationsOnline The document discusses several TCP/IP protocols used for communication over the internet including SMTP, HTTP, FTP, TFTP, NNTP, SNMP, POP, IMAP, and Telnet. It describes the basic functions and workflows of each protocol.
File systems versus a dbms



File systems versus a dbmsRituBhargava7 The document discusses traditional file systems and database management systems (DBMS). It provides an overview of traditional file systems, including their advantages and limitations. It then discusses DBMS, including its components, advantages like reduced data redundancy and improved data integrity, and limitations such as increased complexity. The document uses examples to illustrate key differences between traditional file systems and DBMS.
Text MIning



Text MIningPrakhyath Rai This document presents an overview of text mining. It discusses how text mining differs from data mining in that it involves natural language processing of unstructured or semi-structured text data rather than structured numeric data. The key steps of text mining include pre-processing text, applying techniques like summarization, classification, clustering and information extraction, and analyzing the results. Some common applications of text mining are market trend analysis and filtering of spam emails. While text mining allows extraction of information from diverse sources, it requires initial learning systems and suitable programs for knowledge discovery.
Web Mining & Text Mining



Web Mining & Text MiningHemant Sharma Web mining is the application of data mining techniques to extract knowledge from web data, including web content, structure, and usage data. Web content mining analyzes text, images, and other unstructured data on web pages using natural language processing and information retrieval. Web structure mining examines the hyperlinks between pages to discover relationships. Web usage mining applies data mining methods to server logs and other web data to discover patterns of user behavior on websites. Text mining aims to extract useful information from unstructured text documents using techniques like summarization, information extraction, categorization, and sentiment analysis.
Storage system architecture



Storage system architectureChristalin Nelson The document provides an overview of storage system architecture, including:
- The storage system environment consists of hosts, connectivity components, and storage devices.
- Host environments include physical components like CPUs, memory, and I/O devices, as well as logical components like applications, operating systems, file systems, and device drivers.
- Connectivity carries read/write commands and data between hosts and storage, using buses, ports, cables and protocols.
Segmentación 



Segmentación laury2295 Este documento describe el perfil de una mujer colombiana entre 25 y 40 años que es ama de casa en Bogotá. Ella disfruta cocinar para su familia, administrar el presupuesto doméstico y consumir productos de buena calidad y alimentos saludables. Le gusta pasar tiempo con su familia, amigas y realizar actividades como cocinar y ver televisión.
Ad
More Related Content
What's hot (20)
01 Data Mining: Concepts and Techniques, 2nd ed.



01 Data Mining: Concepts and Techniques, 2nd ed.Institute of Technology Telkom The document provides an overview of data mining concepts and techniques. It introduces data mining, describing it as the process of discovering interesting patterns or knowledge from large amounts of data. It discusses why data mining is necessary due to the explosive growth of data and how it relates to other fields like machine learning, statistics, and database technology. Additionally, it covers different types of data that can be mined, functionalities of data mining like classification and prediction, and classifications of data mining systems.
multi dimensional data model



multi dimensional data modelmoni sindhu The document discusses multidimensional databases and data warehousing. It describes multidimensional databases as optimized for data warehousing and online analytical processing to enable interactive analysis of large amounts of data for decision making. It discusses key concepts like data cubes, dimensions, measures, and common data warehouse schemas including star schema, snowflake schema, and fact constellations.
Cryptography and Network Security William Stallings Lawrie Brown



Cryptography and Network Security William Stallings Lawrie BrownInformation Security Awareness Group Block ciphers like DES encrypt data in blocks and are based on the Feistel cipher structure. DES encrypts 64-bit blocks using a 56-bit key and 16 rounds of encryption. Modern cryptanalysis techniques like differential and linear cryptanalysis use statistical analysis to reveal weaknesses in block ciphers, though DES remains relatively secure against these attacks. Careful design of block ciphers, including aspects like non-linear substitution boxes and complex key scheduling, aims to provide security against cryptanalysis.
Data Hiding Techniques



Data Hiding Techniquesprashant3535 This document discusses various techniques for hiding data in the Microsoft Windows operating system. It covers logical techniques like assigning hidden and system attributes, changing file extensions and icons. It also discusses more advanced techniques like using alternate data streams that allow hiding data in files, and using class identifiers (CLSIDs) meant for special folders for regular folders to disguise hidden data. The document provides an overview of the NTFS file system used by Windows and how its alternate data stream feature can be exploited for data hiding. It also recommends some tools that can be used to detect hidden data streams.
3 Data Mining Tasks



3 Data Mining TasksMahmoud Alfarra Data Mining Tasks
Data mining tasks are the kind of data patterns that can be mined.
Challenges of Data Mining
Data mining application
Mining Association Rules in Large Database



Mining Association Rules in Large DatabaseEr. Nawaraj Bhandari Association rule mining is used to find interesting relationships among data items in large datasets. It can help with business decision making by analyzing customer purchasing patterns. For example, market basket analysis looks at what items are frequently bought together. Association rules use support and confidence metrics, where support is the probability an itemset occurs and confidence is the probability that a rule is correct. The Apriori algorithm is commonly used to generate association rules by first finding frequent itemsets that meet a minimum support threshold across multiple passes of the data. It then generates rules from those itemsets if they meet a minimum confidence. Association rule mining has various applications and can provide useful insights but also has computational limitations.
Language for specifying lexical Analyzer



Language for specifying lexical AnalyzerArchana Gopinath The document discusses the role and process of lexical analysis using LEX. LEX is a tool that generates a lexical analyzer from regular expression rules. A LEX source program consists of auxiliary definitions for tokens and translation rules that match regular expressions to actions. The lexical analyzer created by LEX reads input one character at a time and finds the longest matching prefix, executes the corresponding action, and places the token in a buffer.
Data mining , Knowledge Discovery Process, Classification



Data mining , Knowledge Discovery Process, ClassificationDr. Abdul Ahad Abro The document provides an overview of data mining techniques and processes. It discusses data mining as the process of extracting knowledge from large amounts of data. It describes common data mining tasks like classification, regression, clustering, and association rule learning. It also outlines popular data mining processes like CRISP-DM and SEMMA that involve steps of business understanding, data preparation, modeling, evaluation and deployment. Decision trees are presented as a popular classification technique that uses a tree structure to split data into nodes and leaves to classify examples.
Fundamentals of Database system



Fundamentals of Database systemphilipsinter This document provides an overview of database system concepts and architecture. It discusses different data models including conceptual, physical and implementation models. It also covers database languages, interfaces, utilities and centralized versus distributed (client-server) architectures. Specifically, it describes hierarchical and network data models, the three schema architecture, data independence, DBMS languages like DDL and DML, and different DBMS classifications including relational, object-oriented and distributed systems.
data generalization and summarization 



data generalization and summarization janani thirupathi This document discusses data generalization and summarization techniques. It describes how attribute-oriented induction generalizes data from low to high conceptual levels by examining attribute values. The number of distinct values for each attribute is considered, and attributes may be removed, generalized up concept hierarchies, or retained in the generalized relation. An algorithm for attribute-oriented induction takes a relational database and data mining query as input and outputs a generalized relation. Generalized data can be presented as crosstabs, bar charts, or pie charts.
Data Warehouses & Deployment By Ankita dubey



Data Warehouses & Deployment By Ankita dubeyAnkita Dubey This document contains the notes about data warehouses and life cycle for data warehouse deployment project. This can be useful for students or working professionals to gain the basic knowledge about Data warehouses.
Multimedia Database 



Multimedia Database Avnish Patel Multimedia databases store various media types like text, images, audio and video. They allow querying and retrieval of data based on content. Relational databases store multimedia as BLOBs while object-oriented databases represent multimedia as classes and objects. Challenges include large data size, different formats, and complex queries required for content-based retrieval from multimedia data. Applications include digital libraries, education, entertainment and geographic information systems.
Terminologies Used In Big data Environments,G.Sumithra,II-M.sc(computer scien...



Terminologies Used In Big data Environments,G.Sumithra,II-M.sc(computer scien...sumithragunasekaran Terminologies and its types
In-Memory Analytics
In-Database processing
Symmetric Multiprocessor system(SMP)
Massively Parallel Processing
Difference Between Parallel and Distributed Systems
Shared Nothing Architecture
Advantages of a “ shared nothing Architecture”
CAP Theorem Explained
CAP Theorem
Kdd process



Kdd processRajesh Chandra The KDD process involves several steps: data cleaning to remove noise, data integration of multiple sources, data selection of relevant data, data transformation into appropriate forms for mining, applying data mining techniques to extract patterns, evaluating patterns for interestingness, and representing mined knowledge visually. The KDD process aims to discover useful knowledge from various data types including databases, data warehouses, transactional data, time series, sequences, streams, spatial, multimedia, graphs, engineering designs, and web data.
Text data mining1



Text data mining1KU Leuven Text mining seeks to extract useful information from unstructured text documents. It involves preprocessing the text, identifying features, and applying techniques from data mining, machine learning and natural language processing to discover patterns. The core operations of text mining include analyzing distributions of concepts, identifying frequent concept sets and associations between concepts. Text mining systems aim to analyze document collections over time to identify trends, ephemeral relationships and anomalous patterns.
Tcpip services and applications



Tcpip services and applicationsOnline The document discusses several TCP/IP protocols used for communication over the internet including SMTP, HTTP, FTP, TFTP, NNTP, SNMP, POP, IMAP, and Telnet. It describes the basic functions and workflows of each protocol.
File systems versus a dbms



File systems versus a dbmsRituBhargava7 The document discusses traditional file systems and database management systems (DBMS). It provides an overview of traditional file systems, including their advantages and limitations. It then discusses DBMS, including its components, advantages like reduced data redundancy and improved data integrity, and limitations such as increased complexity. The document uses examples to illustrate key differences between traditional file systems and DBMS.
Text MIning



Text MIningPrakhyath Rai This document presents an overview of text mining. It discusses how text mining differs from data mining in that it involves natural language processing of unstructured or semi-structured text data rather than structured numeric data. The key steps of text mining include pre-processing text, applying techniques like summarization, classification, clustering and information extraction, and analyzing the results. Some common applications of text mining are market trend analysis and filtering of spam emails. While text mining allows extraction of information from diverse sources, it requires initial learning systems and suitable programs for knowledge discovery.
Web Mining & Text Mining



Web Mining & Text MiningHemant Sharma Web mining is the application of data mining techniques to extract knowledge from web data, including web content, structure, and usage data. Web content mining analyzes text, images, and other unstructured data on web pages using natural language processing and information retrieval. Web structure mining examines the hyperlinks between pages to discover relationships. Web usage mining applies data mining methods to server logs and other web data to discover patterns of user behavior on websites. Text mining aims to extract useful information from unstructured text documents using techniques like summarization, information extraction, categorization, and sentiment analysis.
Storage system architecture



Storage system architectureChristalin Nelson The document provides an overview of storage system architecture, including:
- The storage system environment consists of hosts, connectivity components, and storage devices.
- Host environments include physical components like CPUs, memory, and I/O devices, as well as logical components like applications, operating systems, file systems, and device drivers.
- Connectivity carries read/write commands and data between hosts and storage, using buses, ports, cables and protocols.
Cryptography and Network Security William Stallings Lawrie Brown



Cryptography and Network Security William Stallings Lawrie BrownInformation Security Awareness Group
Viewers also liked (20)
Segmentación 



Segmentación laury2295 Este documento describe el perfil de una mujer colombiana entre 25 y 40 años que es ama de casa en Bogotá. Ella disfruta cocinar para su familia, administrar el presupuesto doméstico y consumir productos de buena calidad y alimentos saludables. Le gusta pasar tiempo con su familia, amigas y realizar actividades como cocinar y ver televisión.
Propiedad civil y propiedad agraria modificado



Propiedad civil y propiedad agraria modificadoMillalaidelis El documento describe las diferencias entre la propiedad civil y la propiedad agraria. La propiedad civil corresponde al titular de la tierra según el título de propiedad, mientras que la propiedad agraria está en manos de quien trabaja la tierra aunque no tenga título. La propiedad agraria tiene una función social de producción para la colectividad y está regulada por la ley de tierras, a diferencia de la propiedad civil regulada por el código civil.
Marilin del Carmen Lopez



Marilin del Carmen LopezMarilin del Carmen Lopez La persona desea mejorarse a sí misma como ciudadana, hija, hermana y persona en todas las facetas de su vida. Sus objetivos incluyen prepararse adquiriendo conocimientos, destacarse por sus méritos y esfuerzos para lograr mejores cosas a lo largo de su vida, y ser una buena hija, madre, esposa y profesional formada en valores para cumplir con sus objetivos de convertirse en una emprendedora, profesional y futura abogada de la República.
Nh



Nhmiguel alejandro navarro tovar El documento describe los diferentes tipos de gráficos y sus componentes. Define gráfico y gráfica como la representación de datos numéricos mediante recursos gráficos. Explica que un gráfico contiene identificación, título, cuerpo y pie. Luego describe diagramas de barras, sectores, pictogramas, mapas temáticos e histograma y poligonos de frecuencias como tipos de gráficos. Muestra un ejemplo de diagrama de barras sobre el peso de 65 personas adultas.
essential newborn care



essential newborn careBernadette Corral Essential newborn care (ENC) involves basic care practices during the first hours, days, and weeks of life to ensure newborns remain healthy. ENC includes immediate care at birth, care during the first day, and up to 28 days. Key ENC interventions are clean childbirth, cord care, preventing newborn infection, thermal protection, early and exclusive breastfeeding started within 1 hour of birth, initiation of breathing and resuscitation, and identification and management of newborn hypo/hyperthermia and asphyxia. All newborns have four basic needs - to breathe normally, be protected, be warm, and be fed. Keeping newborns warm after delivery through practices like kangaroo mother care
Comala Unamaravilla



Comala UnamaravillaVive Colima Comala es un pequeño pueblo a 6 km de Colima que fue declarado área de monumento histórico en 1988. El nombre Comala proviene del náhuatl y significa "lugar de comales". El pueblo se caracteriza por sus casas blancas de adobe, artesanías de madera y máscaras de Suchitlán. También ofrece paisajes naturales como la laguna María, bosques y los volcanes Nevado de Colima y Volcán de Fuego, ubicados a pocos kilómetros.
Social Studies Web Sites & Technology



Social Studies Web Sites & TechnologyGlenn Wiebe This document discusses the importance and benefits of using technology in education. It provides examples of how games can promote learning by appealing to human brain functions and encouraging collaboration. While filters may seem useful, being proactive and learning from students is emphasized. A variety of online resources for educators are listed, including tools for creating and sharing content. The overall message is that technology, when used effectively, can greatly enhance learning.
Prevencion de los trastornos de la conducta alimenticia



Prevencion de los trastornos de la conducta alimenticiaGabriela Calva Hernandez Trastornos como la bulimia y la anorexia nerviosas, son, por desgracia, cada día más frecuentes
en la juventud actual y afectan de una manera más importante a las jóvenes.
Esta «Guía Práctica para la Prevención de los Trastornos de la Conducta Alimentaria» constituye
un documento indispensable hoy en la formación de monitores y directores de tiempo
libre, voluntarios y profesionales, así como de cuantos mediadores, agentes sociales y animadores
socioculturales trabajan con la juventud.
La Guía se ha orientado a su formación con una metodología práctica, y pretende la prevención
de los trastornos de la alimentación mediante el estudio de las causas y las acciones
que se pueden llevar a cabo para la mejora de la nutrición y alimentación, la imagen corporal, el
autoconcepto y autoestima, o la asertividad y las habilidades sociales de los jóvenes.
Rethinking SQL for Big Data with Apache Drill



Rethinking SQL for Big Data with Apache DrillMapR Technologies This document provides an overview of Apache Drill and how it enables ad-hoc querying and analysis of structured and unstructured data stored in Hadoop. Some key points:
1) Apache Drill allows for schema-free SQL queries against data in HDFS, HBase, Hive and other data sources, empowering self-service data exploration and "zero-day" analytics.
2) Drill's queries can handle complex, nested data through features like automatic schema discovery, repeated value support, and SQL extensions.
3) Examples show how Drill provides a familiar SQL interface and tooling to analyze JSON, text and other file formats to gain insights from large volumes of real-time data.
Kimaru-Muchai - Communication Channels used in dissemination of soil fertilit...



Kimaru-Muchai - Communication Channels used in dissemination of soil fertilit...CIALCA Presentation delivered at the CIALCA international conference 'Challenges and Opportunities to the agricultural intensification of the humid highland systems of sub-Saharan Africa'. Kigali, Rwanda, October 24-27 2011.
Czytelniczo językowa impreza dla fanów książki „igrzyska...



Czytelniczo językowa impreza dla fanów książki „igrzyska...bibliotekaszkolnag3 Reading event based on Hunger Games
Modeling the operation of a general insurance company with system dynamics ap...



Modeling the operation of a general insurance company with system dynamics ap...Peyman Haghighattalab مجموعه اسلایدهای مربوط به ارائه ی پایان نامه ی کارشناسی ارشد رشته ی سیستم های اقتصادی اجتماعی دانشگاه صنعتی شریف با موضوع "مدل سازی عملکرد یک شرکت بیمه ی عمومی با رویکرد دینامیک سیستم ها"
6.2.15 Christa Evans Rogers Resume 



6.2.15 Christa Evans Rogers Resume Christa Evans Rogers This document is a resume for Christa Evans Rogers. It summarizes her experience as an Investor Relations Project Manager and independent contractor conducting legal discovery. She has over 3 years of experience in investor relations for an oil and gas company, including preparing presentations, managing earnings reports and calls, and interfacing with analysts and investors. She also has experience in public relations, community outreach, and legal work. The resume lists her education, skills, licenses and involvement in professional organizations.
Next greatest generation 2011



Next greatest generation 2011Glenn Wiebe The document discusses how the next generation is different due to changes in technology, politics, and information. It notes how Obama's 2008 campaign raised large amounts of money through small donations and social media. It also discusses how businesses and information are constantly changing in this digital age, with examples like free music downloads and edited books. The key message is that the world is rapidly changing and parents need to help kids learn using any tools that work.
Los tainos, primeros pobladores de las Antillas Mayores 



Los tainos, primeros pobladores de las Antillas Mayores rosam24 Características de los primeros habitantes de las Antillas Mayores, su forma de vida, actividades económicas, su arte y medios de comunicación.
Modeling the operation of a general insurance company with system dynamics ap...



Modeling the operation of a general insurance company with system dynamics ap...Peyman Haghighattalab
Ad
Similar to Knowledge Discovery Using Data Mining (20)
Introducing new AIOps innovations in Oracle 19c - San Jose AICUG



Introducing new AIOps innovations in Oracle 19c - San Jose AICUGSandesh Rao The document discusses Oracle's use of machine learning for autonomous database services. It provides an overview of Oracle's machine learning tools and algorithms, including how they are used for applications like anomaly detection and predictive queries. It also describes Oracle's machine learning notebook interface within the Autonomous Data Warehouse Cloud for building and deploying machine learning models.
IRJET- Classification of Pattern Storage System and Analysis of Online Shoppi...



IRJET- Classification of Pattern Storage System and Analysis of Online Shoppi...IRJET Journal This document discusses classifying patterns from online shopping data using data mining techniques. It proposes using the Apriori algorithm to mine frequent patterns from transaction data stored in a data warehouse. Patterns mined from the data warehouse using Apriori would then be stored in a pattern warehouse. This would allow users to view product details and related patterns when browsing items online. The system aims to efficiently analyze large amounts of user data to discover useful patterns for improving the online shopping experience.
Data Mining with SQL Server 2008



Data Mining with SQL Server 2008Peter Gfader This document provides an overview of a SQL Server 2008 for Business Intelligence short course. It discusses the course instructor's background and specialties. The course will cover creating a data warehouse, OLAP cubes, and reports. It will also discuss data mining concepts like why it's used, common algorithms, and include a hands-on lab. Data mining algorithms that will be covered include classification, clustering, decision trees, and neural networks.
UNIT - 1 Part 2: Data Warehousing and Data Mining



UNIT - 1 Part 2: Data Warehousing and Data MiningNandakumar P DBMS Schemas for Decision Support , Star Schema, Snowflake Schema, Fact Constellation Schema, Schema Definition, Data extraction, clean up and transformation tools.
Data Mining methodology 



Data Mining methodology rebeccatho The most widely used Cross Industry Standard Process for Data Mining methodology is used to develop predictive analytical models.
Azure Machine Learning



Azure Machine LearningMostafa A presentation covers how data science is connected to build effective machine learning solutions. How to build end to end solutions in Azure ML. How to build, model, and evaluate algorithms in Azure ML.
Nose Dive into Apache Spark ML



Nose Dive into Apache Spark MLAhmet Bulut This document discusses Apache Spark machine learning (ML) workflows for recommendation systems using collaborative filtering. It describes loading rating data from users on items into a DataFrame and splitting it into training and test sets. An ALS model is fit on the training data and used to make predictions on the test set. The root mean squared error is calculated to evaluate prediction accuracy.
MS SQL SERVER: Introduction To Datamining Suing Sql Server



MS SQL SERVER: Introduction To Datamining Suing Sql Serversqlserver content Data mining involves analyzing large datasets to discover patterns. It can be used to better understand systems by studying trends and patterns in vast amounts of data. Data mining uses classification, clustering, association, and regression algorithms to organize data and discover patterns. The data mining process involves data collection, cleaning, transformation, modeling, and assessment. Examples of data mining applications include customer relationship management, enterprise resource planning, and web log analysis.
MS Sql Server: Introduction To Datamining Suing Sql Server



MS Sql Server: Introduction To Datamining Suing Sql ServerDataminingTools Inc Data mining involves analyzing large datasets to discover patterns. It can be used to better understand systems by studying trends and patterns in vast amounts of data. Data mining uses classification, clustering, association, and regression algorithms to organize data and discover patterns. The data mining process involves data collection, cleaning, transformation, modeling, and assessment. Examples of data mining applications include customer relationship management, enterprise resource planning, and analyzing web server logs.
What is OLAP -Data Warehouse Concepts - IT Online Training @ Newyorksys



What is OLAP -Data Warehouse Concepts - IT Online Training @ NewyorksysNEWYORKSYS-IT SOLUTIONS NEWYORKSYSTRAINING are destined to offer quality IT online training and comprehensive IT consulting services with complete business service delivery orientation.
Data science technology overview



Data science technology overviewSoojung Hong This document provides an overview of data science technology. It discusses big data technologies for storing, processing, and managing large amounts of data. It also covers machine learning technologies like supervised and unsupervised learning algorithms. Finally, it discusses visualization techniques for analyzing and communicating insights from big data, including tag clouds, clustergrams, and spatial information flows.
Data Mining & Data Warehousing Lecture Notes



Data Mining & Data Warehousing Lecture NotesFellowBuddy.com FellowBuddy.com is an innovative platform that brings students together to share notes, exam papers, study guides, project reports and presentation for upcoming exams.
We connect Students who have an understanding of course material with Students who need help.
Benefits:-
# Students can catch up on notes they missed because of an absence.
# Underachievers can find peer developed notes that break down lecture and study material in a way that they can understand
# Students can earn better grades, save time and study effectively
Our Vision & Mission – Simplifying Students Life
Our Belief – “The great breakthrough in your life comes when you realize it, that you can learn anything you need to learn; to accomplish any goal that you have set for yourself. This means there are no limits on what you can be, have or do.”
Like Us - https://www.facebook.com/FellowBuddycom
Data Mining based on Hashing Technique



Data Mining based on Hashing Techniqueijtsrd Data Mining is an important aspect for any business. Most of the management level decisions are based on the process of Data Mining. One of such aspect is the association between different sale products i.e. what is the actual support of a product respected to the other product. This concept is called Association Mining. According to this concept we define the process of estimating the sale of one product respective to the other product. We are proposing an association rule based on the concept of Hardware support. In this concept we first maintain the database and compare it with systolic array after this a pruning process is being performed to filter the database and to remove the rarely used items. Finally the data is indexed according to hashing technique and the decision is performed in terms of support count. Krishan Rohilla | Shabnam Kumari | Reema"Data Mining based on Hashing Technique" Published in International Journal of Trend in Scientific Research and Development (ijtsrd), ISSN: 2456-6470, Volume-1 | Issue-4 , June 2017, URL: http://www.ijtsrd.com/papers/ijtsrd82.pdf http://www.ijtsrd.com/computer-science/data-miining/82/data-mining-based-on-hashing-technique/krishan-rohilla
Data mining



Data miningheba_ahmad - Data mining involves discovering novel patterns from large databases using algorithms and computers. It aims to find hidden patterns in datasets by analyzing attribute correlations.
- Common data mining tasks include classification, regression, clustering, association analysis, and anomaly detection. These can be used to solve problems like product recommendations, student enrollment predictions, and fraud detection.
- The key steps in data mining typically involve data preparation, exploration, model development, and result interpretation. Association rule mining is commonly used and aims to find relationships between variables in large datasets.
data mining



data miningmanasa polu This document provides an introduction to data mining. It defines data mining as the process of extracting knowledge from large amounts of data. The document outlines the typical steps in the knowledge discovery process including data cleaning, transformation, mining, and evaluation. It also describes some common challenges in data mining like dealing with large, high-dimensional, heterogeneous and distributed data. Finally, it summarizes several common data mining tasks like classification, association analysis, clustering, and anomaly detection.
Data meets AI - AICUG - Santa Clara



Data meets AI - AICUG - Santa ClaraSandesh Rao The document discusses Oracle's initiatives around machine learning and artificial intelligence. It provides an overview of Oracle's machine learning tools and technologies, including Oracle Machine Learning for Python (OML4Py) and the cx_Oracle package. It also discusses Oracle's Autonomous Database and how applied machine learning is used to implement AIOps. The presentation covers common machine learning algorithms, modeling workflows, and Oracle's offerings like the Autonomous Data Warehouse Cloud and upcoming Oracle AI Platform Cloud Service.
Credit card fraud detection using python machine learning



Credit card fraud detection using python machine learningSandeep Garg This document provides an overview of machine learning tools, technologies, and the data preparation process. It discusses collecting and selecting relevant data, data visualization, labeling data for supervised learning, and transforming raw data into a tidy format. The document also covers various data preprocessing techniques, including data cleaning, formatting, handling missing values and outliers, smoothing, aggregation, generalization, and data reduction methods. The goal of these preprocessing steps is to prepare raw data into a structured format suitable for machine learning modeling.
Ad
Recently uploaded (20)
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
How analogue intelligence complements AI



How analogue intelligence complements AIPaul Rowe
Artificial Intelligence is providing benefits in many areas of work within the heritage sector, from image analysis, to ideas generation, and new research tools. However, it is more critical than ever for people, with analogue intelligence, to ensure the integrity and ethical use of AI. Including real people can improve the use of AI by identifying potential biases, cross-checking results, refining workflows, and providing contextual relevance to AI-driven results.
News about the impact of AI often paints a rosy picture. In practice, there are many potential pitfalls. This presentation discusses these issues and looks at the role of analogue intelligence and analogue interfaces in providing the best results to our audiences. How do we deal with factually incorrect results? How do we get content generated that better reflects the diversity of our communities? What roles are there for physical, in-person experiences in the digital world?
Splunk Security Update | Public Sector Summit Germany 2025



Splunk Security Update | Public Sector Summit Germany 2025Splunk Splunk Security Update
Sprecher: Marcel Tanuatmadja
Linux Support for SMARC: How Toradex Empowers Embedded Developers



Linux Support for SMARC: How Toradex Empowers Embedded DevelopersToradex Toradex brings robust Linux support to SMARC (Smart Mobility Architecture), ensuring high performance and long-term reliability for embedded applications. Here’s how:
• Optimized Torizon OS & Yocto Support – Toradex provides Torizon OS, a Debian-based easy-to-use platform, and Yocto BSPs for customized Linux images on SMARC modules.
• Seamless Integration with i.MX 8M Plus and i.MX 95 – Toradex SMARC solutions leverage NXP’s i.MX 8 M Plus and i.MX 95 SoCs, delivering power efficiency and AI-ready performance.
• Secure and Reliable – With Secure Boot, over-the-air (OTA) updates, and LTS kernel support, Toradex ensures industrial-grade security and longevity.
• Containerized Workflows for AI & IoT – Support for Docker, ROS, and real-time Linux enables scalable AI, ML, and IoT applications.
• Strong Ecosystem & Developer Support – Toradex offers comprehensive documentation, developer tools, and dedicated support, accelerating time-to-market.
With Toradex’s Linux support for SMARC, developers get a scalable, secure, and high-performance solution for industrial, medical, and AI-driven applications.
Do you have a specific project or application in mind where you're considering SMARC? We can help with Free Compatibility Check and help you with quick time-to-market
For more information: https://www.toradex.com/computer-on-modules/smarc-arm-family
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptx



DevOpsDays Atlanta 2025 - Building 10x Development Organizations.pptxJustin Reock Building 10x Organizations with Modern Productivity Metrics
10x developers may be a myth, but 10x organizations are very real, as proven by the influential study performed in the 1980s, ‘The Coding War Games.’
Right now, here in early 2025, we seem to be experiencing YAPP (Yet Another Productivity Philosophy), and that philosophy is converging on developer experience. It seems that with every new method we invent for the delivery of products, whether physical or virtual, we reinvent productivity philosophies to go alongside them.
But which of these approaches actually work? DORA? SPACE? DevEx? What should we invest in and create urgency behind today, so that we don’t find ourselves having the same discussion again in a decade?
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...



TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...TrustArc Most consumers believe they’re making informed decisions about their personal data—adjusting privacy settings, blocking trackers, and opting out where they can. However, our new research reveals that while awareness is high, taking meaningful action is still lacking. On the corporate side, many organizations report strong policies for managing third-party data and consumer consent yet fall short when it comes to consistency, accountability and transparency.
This session will explore the research findings from TrustArc’s Privacy Pulse Survey, examining consumer attitudes toward personal data collection and practical suggestions for corporate practices around purchasing third-party data.
Attendees will learn:
- Consumer awareness around data brokers and what consumers are doing to limit data collection
- How businesses assess third-party vendors and their consent management operations
- Where business preparedness needs improvement
- What these trends mean for the future of privacy governance and public trust
This discussion is essential for privacy, risk, and compliance professionals who want to ground their strategies in current data and prepare for what’s next in the privacy landscape.
Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...



Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...Noah Loul Artificial intelligence is changing how businesses operate. Companies are using AI agents to automate tasks, reduce time spent on repetitive work, and focus more on high-value activities. Noah Loul, an AI strategist and entrepreneur, has helped dozens of companies streamline their operations using smart automation. He believes AI agents aren't just tools—they're workers that take on repeatable tasks so your human team can focus on what matters. If you want to reduce time waste and increase output, AI agents are the next move.
UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager API



UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager APIUiPathCommunity Join this UiPath Community Berlin meetup to explore the Orchestrator API, Swagger interface, and the Test Manager API. Learn how to leverage these tools to streamline automation, enhance testing, and integrate more efficiently with UiPath. Perfect for developers, testers, and automation enthusiasts!
📕 Agenda
Welcome & Introductions
Orchestrator API Overview
Exploring the Swagger Interface
Test Manager API Highlights
Streamlining Automation & Testing with APIs (Demo)
Q&A and Open Discussion
Perfect for developers, testers, and automation enthusiasts!
👉 Join our UiPath Community Berlin chapter: https://community.uipath.com/berlin/
This session streamed live on April 29, 2025, 18:00 CET.
Check out all our upcoming UiPath Community sessions at https://community.uipath.com/events/.
Big Data Analytics Quick Research Guide by Arthur Morgan



Big Data Analytics Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
Linux Professional Institute LPIC-1 Exam.pdf



Linux Professional Institute LPIC-1 Exam.pdfRHCSA Guru Introduction to LPIC-1 Exam - overview, exam details, price and job opportunities
AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...



AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...SOFTTECHHUB I started my online journey with several hosting services before stumbling upon Ai EngineHost. At first, the idea of paying one fee and getting lifetime access seemed too good to pass up. The platform is built on reliable US-based servers, ensuring your projects run at high speeds and remain safe. Let me take you step by step through its benefits and features as I explain why this hosting solution is a perfect fit for digital entrepreneurs.
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
Knowledge Discovery Using Data Mining
- 1. CmpE 274 –Business Intelligence Technologies.
- 2. Jinal Shah (ID-005242095) Sohel Dadia (ID-005177251) Ankit Khera (ID-005226495) Riddhi shah(ID-005359513) Vivek Modi(Id-005208581) Parth Vora (ID-005169100)
- 3. --Knowledge Discovery?? --KDD Process --Data Mining Algorithms --Different forms of Mining Models --Classification of Algorithms --Weka --DEMO -- Questions??????
- 4. It is a process of searching knowledge from data and it focuses on the high level application of various data mining methods. It main goal is mining information from raw data in the context of large databases. It makes use of different data mining algorithms to extract information.
- 5. KDD is used in machine learning, pattern-recognition, databases , AI, MIS and lot of other applications. It does the transformation according to the measures and thresholds. It also takes in to account the preprocessing, sub-sampling, and transformation of the database if required.
- 6. 1. Data Cleaning 2. Data Integration 3. Data Selection 4. Data transformation 5. Data Mining 6. Pattern Evaluation 7. Knowledge Presentation
- 8. The data mining algorithm is the mechanism that creates mining models. To create a model, an algorithm first analyzes a set of data, looking for specific patterns and trends. The algorithm then uses the results of this analysis to define the parameters of the mining model.
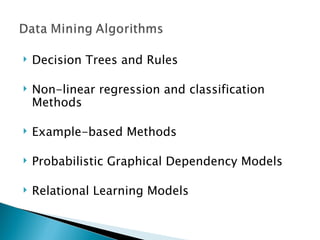
- 9. Decision Trees and Rules Non-linear regression and classification Methods Example-based Methods Probabilistic Graphical Dependency Models Relational Learning Models
- 10. A set of rules that describe how products are grouped together in a transaction. A decision tree that predicts whether a particular customer will buy a product. A mathematical model that forecasts sales. A set of clusters that describe how the cases in a dataset are related.
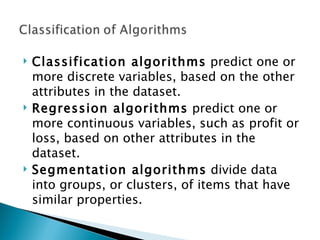
- 11. Classification algorithms predict one or more discrete variables, based on the other attributes in the dataset. Regression algorithms predict one or more continuous variables, such as profit or loss, based on other attributes in the dataset. Segmentation algorithms divide data into groups, or clusters, of items that have similar properties.
- 12. Association algorithms find correlations between different attributes in a dataset. The most common application of this kind of algorithm is for creating association rules, which can be used in a market basket analysis. Sequence analysis algorithms summarize frequent sequences or episodes in data, such as a Web path flow.
- 13. Apriori Algorithm :- is a classic algorithm for learning association rules. Apriori is designed to operate on databases containing transactions (for example, collections of items bought by customers, or details of a website frequentation). Apriori uses breadth-first search and a hash tree structure to count candidate item sets efficiently.
- 14. What is Weka ? Weka is a collection of machine learning algorithms for data mining tasks. Why Weka ? Open Source. The algorithms can either be applied directly to a dataset or called from your own Java code.
- 15. It contains tools for data pre-processing, classification, regression, clustering, association rules, and visualization. It is also well-suited for developing new machine learning schemes.
- 16. Java 1.4 (or later) is required to run Weka 3.4.x and older versions. The developer versions, starting with 3.5.3, also require Java 5.0. Platform : Windows/ Linux
- 21. http://www.cs.waikato.ac.nz/ml/weka/ http://msdn2.microsoft.com/En-US/library/ms175595.aspx http://en.wikipedia.org/wiki/Apriori_algorithm Text book “Data Mining” by Jiawei Han and Micheline Kamber









