Access Control Models: Controlling Resource Authorization
- 2. Access Control Models: Controlling Resource Authorization Mark Niebergall @mbniebergall
- 3. About Mark Niebergall ▪ PHP since 2005 ▪ MS degree in MIS ▪ Senior Software Engineer ▪ UPHPU President ▪ SSCP, CSSLP Certified and SME ▪ Drones, fishing, skiing, father, husband
- 4. Overview
- 5. Overview Access request flow Define applicable terminology Cover primary Access Control Models Discuss pros and cons of each model
- 11. Authentication You are who you say you are Verify identity
- 12. Subject
- 13. Subject Also known as requestor Human or non-person entity (NPE)
- 14. Subject Making request to access resource
- 17. Resource
- 18. Resource Also known as object Protected from unauthorized use
- 19. Resource Something the system has or does ▪ Data ▪ Functionality ▪ Hardware
- 22. Authorization
- 23. Authorization Allow an authenticated subject access to a resource
- 24. Authorization Allow or deny Subject action on object (CRUD)
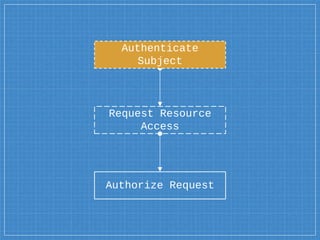
- 26. Request Resource Access Authorize Request Authenticate Subject Access Control Model
- 29. Access Control Model Dictates who gets to do what
- 30. Access Control Model Framework for making authorization decisions
- 31. Access Control Model Deciding subject access to resources
- 32. Access Control Model #4 on 2017 OWASP Top 10: Broken Access Control
- 33. Access Control Model Primary Access Control Models ▪ DAC: Discretionary ▪ MAC: Mandatory ▪ RBAC: Role Based ▪ ABAC: Attribute Based
- 35. DAC House keys
- 36. Email DAC
- 40. DAC Object owner grants permission based on subject identity Access Control List (ACL) Deny by default
- 41. DAC Subject Resource Authorization Alice Report Allow Alice Finance Deny Alice Customer Allow Bob Report Allow Bob Finance Deny Bob Customer Deny
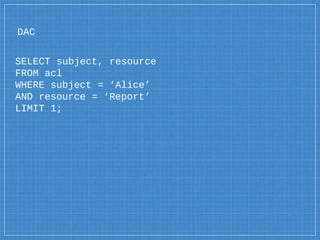
- 42. DAC SELECT is_allow FROM acl WHERE subject = ‘Alice’ AND resource = ‘Customer’ LIMIT 1;
- 43. DAC $acl = new Acl; $alice = new User(‘Alice’); $bob = new User(‘Bob’); $customer = new Resource(‘Customer’); $acl->allow($alice, $customer); $acl->deny($bob, $customer); $acl->isAllowed($alice, $customer); $acl->isAllowed($bob, $customer);
- 44. DAC Simple implementation High operational overhead Access at discretion of resource owner
- 45. DAC Questions?
- 49. MAC Blog
- 50. MAC Leveled-up character in game
- 53. MAC Object sensitivity Subject security level or clearance Write up, read down
- 54. MAC Owner sets object label System sets subject security level
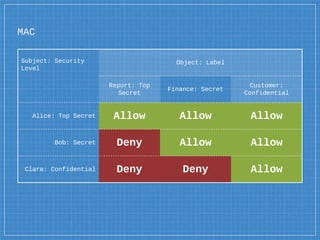
- 55. MAC Subject Security Level Object Label Top Secret Secret Confidential Top Secret Allow Allow Allow Secret Deny Allow Allow Confidential Deny Deny Allow
- 56. Subject Security Level Alice Top Secret Bob Secret Clara Confidential Object Label Report Top Secret Finance Secret Customer Confidential MAC Level Name 1 Top Secret 2 Secret
- 57. MAC Subject: Security Level Object: Label Report: Top Secret Finance: Secret Customer: Confidential Alice: Top Secret Allow Allow Allow Bob: Secret Deny Allow Allow Clara: Confidential Deny Deny Allow
- 58. MAC SELECT s.security_level FROM subject s JOIN security_level sl_s ON sl_s.name = s.name JOIN resource r ON r.resource = ‘Report’ JOIN security_level sl_r ON sl_r.name = r.name AND sl_r.level <= sl_s.level WHERE s.subject = ‘Alice’ LIMIT 1;
- 59. MAC $accessControl = new Mac; $topSecret = new Level(‘Top Secret’); $secret = new Level(‘Secret’); $alice = new User(‘Alice’); $bob = new User(‘Bob’); $finances = new Resource(‘Finances’); $accessControl->addLevel($topSecret, 1) ->addLevel($secret, 2); $accessControl->addUser($alice, $topSecret) ->addUser($bob, $secret); $accessControl->addResource($finances, $secret); $accessControl->isAllowed($alice, $finances);
- 60. MAC Multilevel security System and owner determine access No flexibility Moderate overhead
- 61. MAC Questions?
- 64. RBAC User roles on a computer
- 66. RBAC LARPing
- 68. RBAC Role A Role B Role C Role D Subject Role Resource
- 69. RBAC Subject assigned to role Role granted access to resource
- 70. RBAC Subject Role Alice Accounting Alice Orders Bob Payroll Clara Orders Clara Reporting Role Resource Accounting Finance Accounting Reports Orders Inventory Orders Shipments Payroll Finance
- 71. RBAC SELECT sr.subject, rr.resource FROM subject_role sr JOIN role_resource rr ON rr.subject = sr.subject AND rr.role = sr.role WHERE sr.subject = ‘Alice’ AND rr.resource = ‘Report’ LIMIT 1;
- 72. RBAC $accessControl = new Rbac; $accounting = new Role(‘Accounting’); $ordering = new Role(‘Ordering’); $alice = new User(‘Alice’); $bob = new User(‘Bob’); $inventory = new Resource(‘Inventory’); $accessControl->addRole($accounting) ->addRole($ordering); $accessControl->addUser($alice) ->addUser($bob); $accessControl->addResource($inventory); $accessControl->addUserToRole($alice, $accounting); $accessControl->addResourceToRole($inventory, $ordering); $accessControl->isAllowed($alice, $ordering); $accessControl->isAllowed($bob, $inventory);
- 74. RBAC Very common Lower overhead More scalable
- 75. RBAC Questions?
- 77. ABAC Electronic key card system
- 78. ABAC Credit card with monitoring
- 81. ABAC Conditional authorization based on attributes
- 83. ABAC Subject Action Resource Environment Policy
- 84. ABAC Subject Action Environment Resource Access Manager Create Region A Customer Allow Manager Update Region B Customer Deny Data Entry Create Region A Any Hour Customer Allow Data Entry Create Region B Day Shift Customer Allow Data Entry Create Region B After hours Customer Deny
- 85. ABAC Subject attributes Action attributes Resource attributes Environment attributes
- 86. ABAC Subject attributes ▪ Who ▪ Where ▪ Roles ▪ Affiliation ▪ Clearance
- 87. ABAC Action attributes ▪ Create, POST ▪ Read, GET ▪ Update, PUT ▪ Delete, DELETE ▪ Execute
- 88. ABAC Resource attributes ▪ Type ▪ Owner ▪ Classification
- 89. ABAC Environment attributes ▪ Time ▪ Network ▪ Operating system ▪ Encryption method
- 90. ABAC Policy Enforcement Point (PEP) Policy Decision Point (PDP) PEP sends authorization request to PDP
- 91. ABAC Gartner predicts 70% of all businesses will use ABAC by 2020 Keeps eyes on ABAC
- 92. ABAC Attempt to standardize ABAC policies into XML format is mostly dead, eXtensible Access Control Markup Language (XACML)
- 93. ABAC Refined access Meets demand for more advanced access control API access control
- 94. ABAC Typically start with RBAC implementation and then build onto it with policies Custom implementation so no example
- 95. ABAC Questions?
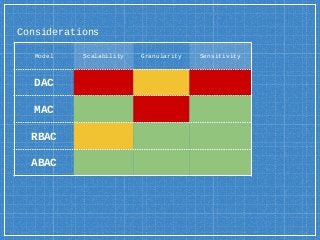
- 98. Considerations Model Scalability Granularity Sensitivity DAC MAC RBAC ABAC
- 99. Implementation Considerations Use cases for application Sensitivity of resources Scalability of model Granularity requirements
- 100. Implementation Considerations Existing frameworks and projects APIs, external interfaces
- 102. Review
- 103. Review
- 104. Review DAC: simple, high overhead, ACL MAC: user and resource classification RBAC: most common, role driven, smaller overhead ABAC: most advanced, policy driven
- 105. Review Operational overhead vs authorization needs Consider current implementation Consider future implementation
- 106. Credits
- 107. CREDITS ▪ NIST publication on ABAC http://nvlpubs.nist.gov/nistpubs/specialpublications/NI ST.sp.800-162.pdf ▪ ABAC for ZF2 https://github.com/Eye4web/Eye4webZf2Abac/blob/master/d ocs/README.md ▪ Presentation template by SlidesCarnival ▪ Axiomatics webinar, May 2014 http://www.slideshare.net/Axiomatics/attribute-based-ac cess-control-for-data-protection-webinar-may-8 ▪ OWASP https://www.owasp.org/index.php/Category:OWASP_Top_Ten_ Project