Achieving Visible Security at Scale with the NIST Cybersecurity Framework
- 1. Aspect Security | 9175 Guilford Road, Suite 300 | Columbia, MD 21046 | www.aspectsecurity.com Achieving Visible Security at Scale with the NIST Cybersecurity Framework SRCE Workshop Atlanta, GA Nov 17, 2015
- 2. Application security that just works ABOUT US KEVIN FEALEY Principal Consultant & Practice Lead Automation & Integration Services 7 years Cybersec experience, @secfealz ©2015 Aspect Security. All Rights Reserved 2 TONY MILLER Principal Consultant & Practice Lead Application Program Services 10 years Cybersec experience, @tjmmgd
- 3. Application security that just works ABOUT YOU Government, Private Sector? AppSec Team, Risk Managers? Used Cybersecurity Framework? ©2015 Aspect Security. All Rights Reserved 3
- 4. Application security that just works APPLICATION SECURITY VS. NETWORK SECURITY ©2015 Aspect Security. All Rights Reserved 4 Application Layer – Attacker sends attacks inside valid HTTP requests. – Custom code is tricked into doing something it should not. – Security requires software development expertise, not signatures. Network Layer – Firewall, hardening, patching, IDS, and SSL/TLS cannot detect or stop attacks inside HTTP requests. – Security relies on signature databases. Firewall Firewall Databases LegacySystems WebServices Directories HumanResrcs Billing Custom Code APPLICATION ATTACK NetworkLayerApplicationLayer Accounts Finance Administration Transactions Communication KnowledgeMgmt E-Commerce Bus.Functions Hardened OS Web Server App Server
- 5. Application security that just works OWASP TOP TEN: COMMON VULNERABILITIES ©2015 Aspect Security. All Rights Reserved 5 1. Injection Flaws 2. Broken Account and Session Management 3. Cross-Site Scripting Flaws 4. Direct Object References 5. Web/Application Server Misconfigurations 6. Sensitive Data Exposure 7. Broken Access Control 8. Cross-Site Request Forgery 9. Using Components with Known Vulnerabilities 10. Unvalidated Redirects and Forwards
- 6. Application security that just works STANDARD SDLC Requirements Design DevelopTest Maintain ©2015 Aspect Security. All Rights Reserved 6 Security Testing
- 7. Application security that just works CURRENT PIPELINE ©2015 Aspect Security. All Rights Reserved 7 Development Pipeline Security Pipeline Production Pipeline Manual Security Activities 1-2 week duration Prone to human error Late in the SDLC
- 8. Application security that just works MANUAL SECURITY REVIEWS ©2015 Aspect Security. All Rights Reserved 8 Development Security Testing Production Business Stakeholders Risks
- 9. Application security that just works FUTURE PIPELINE (IE. WHAT IS APPSEC AUTOMATION?) Automate: ©2015 Aspect Security. All Rights Reserved 9 Development Pipeline Security Pipeline Production Pipeline Tasks that do not require security intelligence Verification of security policies/requirements Vulnerability testing Correlation and reporting Development, Security, and Operations collaborate early and often
- 10. Application security that just works APPSEC AUTOMATION PROGRAM DEPENDENCIES •What are our assets?Application Inventory •When is automated detection insufficient?Identify Risk Thresholds •What do we expect from our assets? Standard Security Requirements •How can we maximize our automation capabilities and mitigate risk? Common Security Controls •How will we support our developers? Developer Training and Support •How will we prioritize and fix issues we identify? Vulnerability Management Program •How will feedback be generated and integrated back? Continuous Improvement Process ©2015 Aspect Security. All Rights Reserved 10
- 11. Application security that just works APPSEC AUTOMATION PROGRAM DEPENDENCIES •What are our assets?Application Inventory •When is automated detection insufficient?Identify Risk Thresholds •What do we expect from our assets? Standard Security Requirements •How can we maximize our automation capabilities and mitigate risk? Common Security Controls •How will we support our developers? Developer Training and Support •How will we prioritize and fix issues we identify? Vulnerability Management Program •How will feedback be generated and integrated back? Continuous Improvement Process ©2015 Aspect Security. All Rights Reserved 11 • How can we effectively scale our security program to achieve business goals at a more rapid pace? AppSec Automation Program
- 12. Application security that just works CYBERSECURITY FRAMEWORK 3.2 Software Security Program Review ©2015 Aspect Security. All Rights Reserved 12 Define the Scope Analyze Threats Current Capability Assess Risks and Gaps Capability Goals Improvement Initiatives Execute Initiatives 1 2 3 4 5 6 7
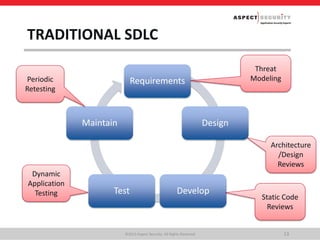
- 13. Application security that just works TRADITIONAL SDLC Requirements Design DevelopTest Maintain ©2015 Aspect Security. All Rights Reserved 13 Dynamic Application Testing Threat Modeling Architecture /Design Reviews Static Code Reviews Periodic Retesting
- 14. Application security that just works CHALLENGES OF DEV-OPS/AGILE Requirements & Design Phases Hardly accommodated Development to Deployment Highly compressed timeframes Traditional Testing Cycles Can’t accommodate stunning speed So, how do we integrate security? ©2015 Aspect Security. All Rights Reserved 14
- 15. Application security that just works SECURE DEV-OPS/AGILE MODEL Proactive Lifecycle Continuous Monitoring Developer Training Local Security SME Program Operational Security Team Secure Code & Architecture Standards Targeted Security Activities (small scope) Risk-Based Security Assurance Model Standardized Security Controls Components Self-Service Model Utilizing Automation Feedback Loop Via Stories/Features ©2015 Aspect Security. All Rights Reserved 15
- 16. Thank you! ©2015 Aspect Security. All Rights Reserved Kevin Fealey & Tony Miller [email protected] [email protected]