aclpwn - Active Directory ACL exploitation with BloodHound
5 likes11,967 views
My talk about aclpwn and Active Directory ACL exploitation as given on Hack in the Box Dubai Armory 2018.
1 of 41
Downloaded 148 times
























![fox-it.com
• Shortest path is not always the most efficient path
• Neo4j counts path length based on number of nodes
• If we have the following scenario:
• User “test” is member of group A
• Group A is member of group B
• Group B is member of group C
• Group C is member of Domain Admins
• AND user “test” has AddMember on Domain Admins
• Neo4j will see the path (Test)-[AddMember]->(Domain Admins) as shortest.
• Even if user A is effectively already a domain admin
Pathfinding with Neo4j](https://image.slidesharecdn.com/aclpwn-181204204519/85/aclpwn-Active-Directory-ACL-exploitation-with-BloodHound-25-320.jpg)















Ad
Recommended
(Ab)Using GPOs for Active Directory Pwnage



(Ab)Using GPOs for Active Directory PwnagePetros Koutroumpis Identifying privilege escalation paths within an Active Directory environment is crucial for a successful red team. Over the last few years, BloodHound has made it easier for red teamers to perform reconnaissance activities and identify these attacks paths. When evaluating BloodHound data, it is common to find ourselves having sufficient rights to modify a Group Policy Object (GPO). This level of access allows us to perform a number of attacks, targeting any computer or user object controlled by the vulnerable GPO.
In this talk we will present previous research related to GPO abuses and share a number of misconfigurations we have found in the wild. We will also present a tool that allows red teamers to target users and computers controlled by a vulnerable GPO in order to escalate privileges and move laterally within the environment.
Catch Me If You Can: PowerShell Red vs Blue



Catch Me If You Can: PowerShell Red vs BlueWill Schroeder This presentation was given at PSConfEU 2017 and covers a survey of PowerShell offensive/defensive projects.
0wn-premises: Bypassing Microsoft Defender for Identity



0wn-premises: Bypassing Microsoft Defender for IdentityNikhil Mittal This document discusses bypassing alerts from Microsoft Defender for Identity (MDI). It begins with an introduction to MDI and the types of alerts it generates. It then explores techniques for bypassing alerts during different phases of an attack like reconnaissance, credential compromise, and lateral movement. These include using alternative tools, limiting interactions with domain controllers, and complying with Kerberos policies. The document also notes techniques like silver tickets that are not detected by MDI. It concludes by acknowledging limitations of only testing alerts and not coupled defenses.
Derbycon - The Unintended Risks of Trusting Active Directory



Derbycon - The Unintended Risks of Trusting Active DirectoryWill Schroeder Given at DerbyCon 2018, this presentation covers host and Active Directory security descriptor research.
Not a Security Boundary



Not a Security BoundaryWill Schroeder 1. The document discusses breaking trusts between Active Directory forests by leveraging compromised unconstrained delegation and the "printer bug" to coerce authentication across forest boundaries.
2. It explains how a compromised server with unconstrained delegation in one forest can be used to extract ticket granting tickets (TGTs) that can then be reused to access resources in a separate, trusting forest.
3. The "printer bug" allows remotely forcing authentication and is used to extract TGTs from the separate forest to circumvent typical cross-forest security restrictions. This bypasses the assumption that forests provide a security boundary when two-way trusts exist between them.
Red Team Methodology - A Naked Look



Red Team Methodology - A Naked LookJason Lang The document provides an overview of a red team consultant's methodology for penetration testing engagements. It discusses various stages of an engagement including pre-engagement reconnaissance using tools like LinkedIn and domain research. It covers external testing techniques like NTLM brute forcing. Internal testing focuses on privileges escalation using tools like Mimikatz and movement using techniques like DLL hijacking. Reporting emphasizes providing a full narrative and findings of high quality over large quantities.
I'm in your cloud... reading everyone's email. Hacking Azure AD via Active Di...



I'm in your cloud... reading everyone's email. Hacking Azure AD via Active Di...DirkjanMollema
Azure AD is everything but a domain controller in the cloud. This talk will cover what Azure AD is, how it is commonly integrated with Active Directory and how security boundaries extend into the cloud, covering sync account password recovery, privilege escalations in Azure AD and full admin account takeovers using limited on-premise privileges.
While Active Directory has been researched for years and the security boundaries and risks are generally well documented, more and more organizations are extending their network into the cloud. A prime example of this is Office 365, which Microsoft offers through their Azure cloud. Connecting the on-premise Active Directory with the cloud introduces new attack surface both for the cloud and the on-premise directory.
This talk looks at the way the trust between Active Directory and Azure is set up and can be abused through the Azure AD Connect tool. We will take a dive into how the synchronization is set up, how the high-privilege credentials for both the cloud and Active Directory are protected (and can be obtained) and what permissions are associated with these accounts.
The talk will outline how a zero day in common setups was discovered through which on-premise users with limited privileges could take over the highest administration account in Azure and potentially compromise all cloud assets.
We will also take a look at the Azure AD architecture and common roles, and how attackers could backdoor or escalate privileges in cloud setups.
Lastly we will look at how to prevent against these kind of attacks and why your AD Connect server is perhaps one of the most critical assets in the on-premise infrastructure.
The Unintended Risks of Trusting Active Directory



The Unintended Risks of Trusting Active DirectoryWill Schroeder This presentation was given at Sp4rkCon 2018. It covers the combination of Active Directory and host-based security descriptor backdooring and the associated security implications.
Hunting for Privilege Escalation in Windows Environment



Hunting for Privilege Escalation in Windows EnvironmentTeymur Kheirkhabarov Slides from my talk at the OFFZONE 2018 conference (https://www.offzone.moscow/report/hunting-for-privilege-escalation-in-windows-environment/)
Evading Microsoft ATA for Active Directory Domination



Evading Microsoft ATA for Active Directory DominationNikhil Mittal The talk I gave at Black Hat USA 2017 on bypassing Microsoft Advanced Threat Analytics (ATA). I demonstrate techniques to bypass, avoid and attack ATA in this talk.
RACE - Minimal Rights and ACE for Active Directory Dominance



RACE - Minimal Rights and ACE for Active Directory DominanceNikhil Mittal My DEF CON 27 talk on using minimal permissions on ACLs for persistence and on demand privilege escalation in Active Directory.
You can detect PowerShell attacks



You can detect PowerShell attacksMichael Gough You can detect PowerShell attacks if you know how to audit your settings, enable, and collect.
LOG-MD
Malware Archaeology
Red Team Revenge - Attacking Microsoft ATA



Red Team Revenge - Attacking Microsoft ATANikhil Mittal Nikhil Mittal presented methods for evading detection by Microsoft Advanced Threat Analytics (ATA). ATA detects attacks by monitoring traffic to domain controllers, but can be bypassed by avoiding direct queries to the DC. Reconnaissance techniques like SPN scanning and hunting domain admin tokens on other machines go undetected. Overpass-the-hash and golden tickets can bypass ATA if the encryption type matches normal traffic. False events can also be generated by triggering unusual detections for fake users.
AMSI: How Windows 10 Plans to Stop Script-Based Attacks and How Well It Does It



AMSI: How Windows 10 Plans to Stop Script-Based Attacks and How Well It Does ItNikhil Mittal The talk I gave at Black Hat USA 2016 on Anti Malware Scan Interface. The talk looks at what good AMSI brings to Windows 10 and various methods of avoiding/bypassing it.
DerbyCon 2019 - Kerberoasting Revisited



DerbyCon 2019 - Kerberoasting RevisitedWill Schroeder Given at DerbyCon 2019, this presentation covers Kerberoasting nuances we weren't aware of until recently.
Troopers 19 - I am AD FS and So Can You



Troopers 19 - I am AD FS and So Can YouDouglas Bienstock This document provides an overview of attacking Active Directory Federation Services (AD FS). It begins with an introduction to AD FS and how it works, allowing single sign-on for applications outside of Active Directory. It then discusses how to find AD FS servers on a network and potential vulnerabilities in default configurations. The document focuses on attacking identity provider adapters and the signing certificate as ways to impersonate the AD FS server and issue unauthorized tokens. It provides technical details on decrypting the signing certificate stored in the Windows Internal Database using the Distributed Key Manager.
PSConfEU - Offensive Active Directory (With PowerShell!)



PSConfEU - Offensive Active Directory (With PowerShell!)Will Schroeder This talk covers PowerShell for offensive Active Directory operations with PowerView. It was given on April 21, 2016 at the PowerShell Conference EU 2016.
Carlos García - Pentesting Active Directory Forests [rooted2019]![Carlos García - Pentesting Active Directory Forests [rooted2019]](https://cdn.slidesharecdn.com/ss_thumbnails/carlosgarcia-rooted2019-pentestingactivedirectoryforests-public-190403185357-thumbnail.jpg?width=560&fit=bounds)
![Carlos García - Pentesting Active Directory Forests [rooted2019]](https://cdn.slidesharecdn.com/ss_thumbnails/carlosgarcia-rooted2019-pentestingactivedirectoryforests-public-190403185357-thumbnail.jpg?width=560&fit=bounds)
![Carlos García - Pentesting Active Directory Forests [rooted2019]](https://cdn.slidesharecdn.com/ss_thumbnails/carlosgarcia-rooted2019-pentestingactivedirectoryforests-public-190403185357-thumbnail.jpg?width=560&fit=bounds)
![Carlos García - Pentesting Active Directory Forests [rooted2019]](https://cdn.slidesharecdn.com/ss_thumbnails/carlosgarcia-rooted2019-pentestingactivedirectoryforests-public-190403185357-thumbnail.jpg?width=560&fit=bounds)
Carlos García - Pentesting Active Directory Forests [rooted2019]RootedCON The document discusses penetration testing of Active Directory forests and trusts. It begins with an introduction to forests, domains, and trust types. It then covers authentication protocols like NTLM and Kerberos across trusts. Next, it discusses techniques for enumerating trusts and mapping the trust relationships. The document outlines common attacks when domain admin privileges are available, such as using Golden Tickets and SID history exploitation. For situations without domain admin, it recommends reconnaissance of trusts and objects to map a path to privileged accounts.
ReCertifying Active Directory



ReCertifying Active DirectoryWill Schroeder "ReCertifying Active Directory was presented at BlackHat EU 2021 by Will Schroeder and Lee Christensen.
I hunt sys admins 2.0



I hunt sys admins 2.0Will Schroeder This document discusses techniques for hunting down target users on Windows domains after gaining initial access. It begins by outlining existing tools like psloggedon.exe and netsess.exe that can detect logged-in users but typically require administrator privileges. It then explores using domain data sources and PowerShell with tools like PowerView to profile and locate target users throughout the domain without administrator privileges. Various PowerShell commands like Invoke-UserHunter, Invoke-UserView, and Invoke-UserEventHunter are demonstrated for efficiently finding sessions and events associated with target users.
An ACE in the Hole - Stealthy Host Persistence via Security Descriptors



An ACE in the Hole - Stealthy Host Persistence via Security DescriptorsWill Schroeder The document discusses stealthy host persistence techniques using security descriptors. It begins with an introduction to the authors and their research focusing on offensive applications of securable objects. It then provides an overview of securable objects, access control lists, and the authors' methodology for researching new persistence primitives using various securable objects like the Service Control Manager, WinRM, DCOM, WMI namespaces, printers, and the remote registry. Case studies and demonstrations are presented for some of these objects.
Here Be Dragons: The Unexplored Land of Active Directory ACLs



Here Be Dragons: The Unexplored Land of Active Directory ACLsAndy Robbins This document summarizes information about three individuals - Andy, Rohan, and Will - who work at Specter Ops creating security tools like BloodHound. It provides details on their jobs, tool development experience, conference presentations, training experience, and Twitter accounts. It then outlines abuse primitives that can be exploited through misconfigurations in Active Directory object ACLs. Finally, it demonstrates how to use tools like PowerView, SharpHound, and BloodHound to find misconfigurations and attack paths in Active Directory.
Six Degrees of Domain Admin - BloodHound at DEF CON 24



Six Degrees of Domain Admin - BloodHound at DEF CON 24Andy Robbins This document summarizes a presentation about domain privilege escalation in Active Directory environments. It discusses how attackers can escalate privileges by chaining together access to various privileged accounts through derivative local administrator rights. It introduces the concepts of attack graphs and how the BloodHound tool uses graph theory and data collected from PowerView to map out all the potential privilege escalation paths in a domain. PowerView is presented as a stealthy method to collect the situational awareness data on users, groups, computers and permissions that BloodHound relies on to generate and analyze the attack graph.
I Have the Power(View)



I Have the Power(View)Will Schroeder This presentation covers PowerView, and offensive Active Directory enumeration tool written in PowerShell. It was given at Troopers16.
Hunting for Credentials Dumping in Windows Environment



Hunting for Credentials Dumping in Windows EnvironmentTeymur Kheirkhabarov My slides from Zero Nights 2017 talk - https://2017.zeronights.ru/report/hunting-for-credentials-dumping-in-windows-environment/
Windows Threat Hunting



Windows Threat HuntingGIBIN JOHN This document discusses techniques for threat hunting on Windows systems. It covers key areas to focus on during incident triage like processes, network connections, filesystem artifacts and logs. It also describes general hunting scenarios using threat intelligence or without intelligence. Specific techniques and artifacts discussed include the Windows Task Scheduler, ShimCache, AmCache, RecentFileCache, rogue services, timeline analysis using MFT, DLL side loading, DLL injection rootkits, autoruns, and the Wdigest credential storage downgrade attack. The document provides details on what to look for and analyze to effectively hunt for threats on Windows.
50 Shades of Sigma



50 Shades of SigmaFlorian Roth This document discusses Sigma, an open source generic rule format for detecting threats in log data. It begins by introducing the creator Florian Roth and his background in security. It then explains what Sigma is, how rules are written, and why the Sigma format was created. Key points covered include Sigma's simplicity, large rule base, and ability to work across different log analysis systems. The document also outlines future directions for Sigma such as integrating STIX indicators and sandbox event data.
Fantastic Red Team Attacks and How to Find Them



Fantastic Red Team Attacks and How to Find ThemRoss Wolf Presented at Black Hat 2019
https://www.blackhat.com/us-19/briefings/schedule/index.html#fantastic-red-team-attacks-and-how-to-find-them-16540
Casey Smith (Red Canary)
Ross Wolf (Endgame)
bit.ly/fantastic19
Abstract:
Red team testing in organizations over the last year has shown a dramatic increase in detections mapped to MITRE ATT&CK™ across Windows, Linux and macOS. However, many organizations continue to miss several key techniques that, unsurprisingly, often blend in with day-to-day user operations. One example includes Trusted Developer Utilities which can be readily available on standard user endpoints, not just developer workstations, and such applications allow for code execution. Also, XSL Script processing can be used as an attack vector as there are a number of trusted utilities that can consume and execute scripts via XSL. And finally, in addition to these techniques, trusted .NET default binaries are known to allow unauthorized execution as well, these include tools like InstallUtil, Regsvcs and AddInProcess. Specific techniques, coupled with procedural difficulties within a team, such as alert fatigue and lack of understanding with environmental norms, make reliable detection of these events near impossible.
This talk summarizes prevalent and ongoing gaps across organizations uncovered by testing their defenses against a broad spectrum of attacks via Atomic Red Team. Many of these adversary behaviors are not atomic, but span multiple events in an event stream that may be arbitrarily and inconsistently separated in time by nuisance events.
Additionally, we introduce and demonstrate the open-sourced Event Query Language for creating high signal-to-noise analytics that close these prevalent behavioral gaps. EQL is event agnostic and can be used to craft analytics that readily link evidence across long sequences of log data. In a live demonstration, we showcase powerful but easy to craft analytics that catch adversarial behavior most commonly missed in organizations today.
Top school in noida



Top school in noidaEdhole.com This document discusses access control mechanisms, specifically access control lists and capability lists. It provides examples of how access control lists work, including default permissions, abbreviations to shorten lists, and how conflicts are handled. It also covers capability lists, how capabilities are implemented using tags or cryptographic tickets, and the challenges of revocation for each method. Maintaining the principle of least privilege is discussed in the context of access control mechanisms.
OSMC 2016 - Monitor your infrastructure with Elastic Beats by Monica Sarbu



OSMC 2016 - Monitor your infrastructure with Elastic Beats by Monica SarbuNETWAYS Monica ist Mit-Schöpferin von Elastic Beats. Bevor sie Beats erfand, arbeitete sie als Core Developer für IPTEGO, einem Start-Up Unternehmen aus Berlin, das eine komplette Monitoring und Trouble-Shooting Solution für VoIP Netzwerke anbietet. Das Produkt wurde weltweit verkauft, und wird derzeit von großen Firmen der Telekommunikationsbranche verwendet.
Ad
More Related Content
What's hot (20)
Hunting for Privilege Escalation in Windows Environment



Hunting for Privilege Escalation in Windows EnvironmentTeymur Kheirkhabarov Slides from my talk at the OFFZONE 2018 conference (https://www.offzone.moscow/report/hunting-for-privilege-escalation-in-windows-environment/)
Evading Microsoft ATA for Active Directory Domination



Evading Microsoft ATA for Active Directory DominationNikhil Mittal The talk I gave at Black Hat USA 2017 on bypassing Microsoft Advanced Threat Analytics (ATA). I demonstrate techniques to bypass, avoid and attack ATA in this talk.
RACE - Minimal Rights and ACE for Active Directory Dominance



RACE - Minimal Rights and ACE for Active Directory DominanceNikhil Mittal My DEF CON 27 talk on using minimal permissions on ACLs for persistence and on demand privilege escalation in Active Directory.
You can detect PowerShell attacks



You can detect PowerShell attacksMichael Gough You can detect PowerShell attacks if you know how to audit your settings, enable, and collect.
LOG-MD
Malware Archaeology
Red Team Revenge - Attacking Microsoft ATA



Red Team Revenge - Attacking Microsoft ATANikhil Mittal Nikhil Mittal presented methods for evading detection by Microsoft Advanced Threat Analytics (ATA). ATA detects attacks by monitoring traffic to domain controllers, but can be bypassed by avoiding direct queries to the DC. Reconnaissance techniques like SPN scanning and hunting domain admin tokens on other machines go undetected. Overpass-the-hash and golden tickets can bypass ATA if the encryption type matches normal traffic. False events can also be generated by triggering unusual detections for fake users.
AMSI: How Windows 10 Plans to Stop Script-Based Attacks and How Well It Does It



AMSI: How Windows 10 Plans to Stop Script-Based Attacks and How Well It Does ItNikhil Mittal The talk I gave at Black Hat USA 2016 on Anti Malware Scan Interface. The talk looks at what good AMSI brings to Windows 10 and various methods of avoiding/bypassing it.
DerbyCon 2019 - Kerberoasting Revisited



DerbyCon 2019 - Kerberoasting RevisitedWill Schroeder Given at DerbyCon 2019, this presentation covers Kerberoasting nuances we weren't aware of until recently.
Troopers 19 - I am AD FS and So Can You



Troopers 19 - I am AD FS and So Can YouDouglas Bienstock This document provides an overview of attacking Active Directory Federation Services (AD FS). It begins with an introduction to AD FS and how it works, allowing single sign-on for applications outside of Active Directory. It then discusses how to find AD FS servers on a network and potential vulnerabilities in default configurations. The document focuses on attacking identity provider adapters and the signing certificate as ways to impersonate the AD FS server and issue unauthorized tokens. It provides technical details on decrypting the signing certificate stored in the Windows Internal Database using the Distributed Key Manager.
PSConfEU - Offensive Active Directory (With PowerShell!)



PSConfEU - Offensive Active Directory (With PowerShell!)Will Schroeder This talk covers PowerShell for offensive Active Directory operations with PowerView. It was given on April 21, 2016 at the PowerShell Conference EU 2016.
Carlos García - Pentesting Active Directory Forests [rooted2019]![Carlos García - Pentesting Active Directory Forests [rooted2019]](https://cdn.slidesharecdn.com/ss_thumbnails/carlosgarcia-rooted2019-pentestingactivedirectoryforests-public-190403185357-thumbnail.jpg?width=560&fit=bounds)
![Carlos García - Pentesting Active Directory Forests [rooted2019]](https://cdn.slidesharecdn.com/ss_thumbnails/carlosgarcia-rooted2019-pentestingactivedirectoryforests-public-190403185357-thumbnail.jpg?width=560&fit=bounds)
![Carlos García - Pentesting Active Directory Forests [rooted2019]](https://cdn.slidesharecdn.com/ss_thumbnails/carlosgarcia-rooted2019-pentestingactivedirectoryforests-public-190403185357-thumbnail.jpg?width=560&fit=bounds)
![Carlos García - Pentesting Active Directory Forests [rooted2019]](https://cdn.slidesharecdn.com/ss_thumbnails/carlosgarcia-rooted2019-pentestingactivedirectoryforests-public-190403185357-thumbnail.jpg?width=560&fit=bounds)
Carlos García - Pentesting Active Directory Forests [rooted2019]RootedCON The document discusses penetration testing of Active Directory forests and trusts. It begins with an introduction to forests, domains, and trust types. It then covers authentication protocols like NTLM and Kerberos across trusts. Next, it discusses techniques for enumerating trusts and mapping the trust relationships. The document outlines common attacks when domain admin privileges are available, such as using Golden Tickets and SID history exploitation. For situations without domain admin, it recommends reconnaissance of trusts and objects to map a path to privileged accounts.
ReCertifying Active Directory



ReCertifying Active DirectoryWill Schroeder "ReCertifying Active Directory was presented at BlackHat EU 2021 by Will Schroeder and Lee Christensen.
I hunt sys admins 2.0



I hunt sys admins 2.0Will Schroeder This document discusses techniques for hunting down target users on Windows domains after gaining initial access. It begins by outlining existing tools like psloggedon.exe and netsess.exe that can detect logged-in users but typically require administrator privileges. It then explores using domain data sources and PowerShell with tools like PowerView to profile and locate target users throughout the domain without administrator privileges. Various PowerShell commands like Invoke-UserHunter, Invoke-UserView, and Invoke-UserEventHunter are demonstrated for efficiently finding sessions and events associated with target users.
An ACE in the Hole - Stealthy Host Persistence via Security Descriptors



An ACE in the Hole - Stealthy Host Persistence via Security DescriptorsWill Schroeder The document discusses stealthy host persistence techniques using security descriptors. It begins with an introduction to the authors and their research focusing on offensive applications of securable objects. It then provides an overview of securable objects, access control lists, and the authors' methodology for researching new persistence primitives using various securable objects like the Service Control Manager, WinRM, DCOM, WMI namespaces, printers, and the remote registry. Case studies and demonstrations are presented for some of these objects.
Here Be Dragons: The Unexplored Land of Active Directory ACLs



Here Be Dragons: The Unexplored Land of Active Directory ACLsAndy Robbins This document summarizes information about three individuals - Andy, Rohan, and Will - who work at Specter Ops creating security tools like BloodHound. It provides details on their jobs, tool development experience, conference presentations, training experience, and Twitter accounts. It then outlines abuse primitives that can be exploited through misconfigurations in Active Directory object ACLs. Finally, it demonstrates how to use tools like PowerView, SharpHound, and BloodHound to find misconfigurations and attack paths in Active Directory.
Six Degrees of Domain Admin - BloodHound at DEF CON 24



Six Degrees of Domain Admin - BloodHound at DEF CON 24Andy Robbins This document summarizes a presentation about domain privilege escalation in Active Directory environments. It discusses how attackers can escalate privileges by chaining together access to various privileged accounts through derivative local administrator rights. It introduces the concepts of attack graphs and how the BloodHound tool uses graph theory and data collected from PowerView to map out all the potential privilege escalation paths in a domain. PowerView is presented as a stealthy method to collect the situational awareness data on users, groups, computers and permissions that BloodHound relies on to generate and analyze the attack graph.
I Have the Power(View)



I Have the Power(View)Will Schroeder This presentation covers PowerView, and offensive Active Directory enumeration tool written in PowerShell. It was given at Troopers16.
Hunting for Credentials Dumping in Windows Environment



Hunting for Credentials Dumping in Windows EnvironmentTeymur Kheirkhabarov My slides from Zero Nights 2017 talk - https://2017.zeronights.ru/report/hunting-for-credentials-dumping-in-windows-environment/
Windows Threat Hunting



Windows Threat HuntingGIBIN JOHN This document discusses techniques for threat hunting on Windows systems. It covers key areas to focus on during incident triage like processes, network connections, filesystem artifacts and logs. It also describes general hunting scenarios using threat intelligence or without intelligence. Specific techniques and artifacts discussed include the Windows Task Scheduler, ShimCache, AmCache, RecentFileCache, rogue services, timeline analysis using MFT, DLL side loading, DLL injection rootkits, autoruns, and the Wdigest credential storage downgrade attack. The document provides details on what to look for and analyze to effectively hunt for threats on Windows.
50 Shades of Sigma



50 Shades of SigmaFlorian Roth This document discusses Sigma, an open source generic rule format for detecting threats in log data. It begins by introducing the creator Florian Roth and his background in security. It then explains what Sigma is, how rules are written, and why the Sigma format was created. Key points covered include Sigma's simplicity, large rule base, and ability to work across different log analysis systems. The document also outlines future directions for Sigma such as integrating STIX indicators and sandbox event data.
Fantastic Red Team Attacks and How to Find Them



Fantastic Red Team Attacks and How to Find ThemRoss Wolf Presented at Black Hat 2019
https://www.blackhat.com/us-19/briefings/schedule/index.html#fantastic-red-team-attacks-and-how-to-find-them-16540
Casey Smith (Red Canary)
Ross Wolf (Endgame)
bit.ly/fantastic19
Abstract:
Red team testing in organizations over the last year has shown a dramatic increase in detections mapped to MITRE ATT&CK™ across Windows, Linux and macOS. However, many organizations continue to miss several key techniques that, unsurprisingly, often blend in with day-to-day user operations. One example includes Trusted Developer Utilities which can be readily available on standard user endpoints, not just developer workstations, and such applications allow for code execution. Also, XSL Script processing can be used as an attack vector as there are a number of trusted utilities that can consume and execute scripts via XSL. And finally, in addition to these techniques, trusted .NET default binaries are known to allow unauthorized execution as well, these include tools like InstallUtil, Regsvcs and AddInProcess. Specific techniques, coupled with procedural difficulties within a team, such as alert fatigue and lack of understanding with environmental norms, make reliable detection of these events near impossible.
This talk summarizes prevalent and ongoing gaps across organizations uncovered by testing their defenses against a broad spectrum of attacks via Atomic Red Team. Many of these adversary behaviors are not atomic, but span multiple events in an event stream that may be arbitrarily and inconsistently separated in time by nuisance events.
Additionally, we introduce and demonstrate the open-sourced Event Query Language for creating high signal-to-noise analytics that close these prevalent behavioral gaps. EQL is event agnostic and can be used to craft analytics that readily link evidence across long sequences of log data. In a live demonstration, we showcase powerful but easy to craft analytics that catch adversarial behavior most commonly missed in organizations today.
Similar to aclpwn - Active Directory ACL exploitation with BloodHound (20)
Top school in noida



Top school in noidaEdhole.com This document discusses access control mechanisms, specifically access control lists and capability lists. It provides examples of how access control lists work, including default permissions, abbreviations to shorten lists, and how conflicts are handled. It also covers capability lists, how capabilities are implemented using tags or cryptographic tickets, and the challenges of revocation for each method. Maintaining the principle of least privilege is discussed in the context of access control mechanisms.
OSMC 2016 - Monitor your infrastructure with Elastic Beats by Monica Sarbu



OSMC 2016 - Monitor your infrastructure with Elastic Beats by Monica SarbuNETWAYS Monica ist Mit-Schöpferin von Elastic Beats. Bevor sie Beats erfand, arbeitete sie als Core Developer für IPTEGO, einem Start-Up Unternehmen aus Berlin, das eine komplette Monitoring und Trouble-Shooting Solution für VoIP Netzwerke anbietet. Das Produkt wurde weltweit verkauft, und wird derzeit von großen Firmen der Telekommunikationsbranche verwendet.
OSMC 2016 | Monitor your Infrastructure with Elastic Beats by Monica Sarbu



OSMC 2016 | Monitor your Infrastructure with Elastic Beats by Monica SarbuNETWAYS Beats sind eine freundliche Armee von leichtgewichtigen Agenten die, wenn sie auf dem Server installiert sind, Betriebsdaten erfassen und sie zur Analyse an Elasticsearch senden.
Sie sammeln die Logdaten ihrer Server und erhalten so Statistiken von CPU, Disk- und Speicherauslastung. Durch regelmäßige Abfragen sammeln sie Metriken von externen Systemen wie MySQL, Docker und Zookeeper und können die Kommunikation zwischen den Servern durch sniffen der entsprechenden Netzwerkverbindungen visualisieren.
Dieser Vortrag erläutert wie Sie Beats mit Elasticsearch und Kibana in einer kompletten Open Source Monitoring Lösung kombinieren können und sie ihnen helfen ihre verzweigte Infrastruktur zu überwachen und Fehler zu beheben.
BSides SG Practical Red Teaming Workshop



BSides SG Practical Red Teaming WorkshopAjay Choudhary Practical Red Teaming is a hands-on class designed to teach participants with various techniques and tools for performing red teaming attacks. The goal of the training is to give a red teamer’s perspective to participants who want to go beyond VAPT. This intense course immerses students in a simulated enterprise environment, with multiple domains, up-to-date and patched operating systems. We will cover several phases of a Red Team engagement in depth – Local Privilege escalation, Domain Enumeration, Admin Recon, Lateral movement, Domain Admin privileges etc.
If you want to learn how to perform Red Team operations, sharpen your red teaming skillset, or understand how to defend against modern attacks, Practical Red Teaming is the course for you.
Topics :
• Red Team philosophy/overview
• Red Teaming vs Penetration Testing
• Active Directory Fundamentals – Forests, Domains, OU’s etc
• Assume Breach Methodology
• Insider Attack Simulation
• Introduction to PowerShell
• Initial access methods
• Privilege escalation methods through abuse of misconfigurations
• Domain Enumeration
• Lateral Movement and Pivoting
• Single sign-on in Active Directory
• Abusing built-in functionality for code execution
• Credential Replay
• Domain privileges abuse
• Dumping System and Domain Secrets
• Kerberos – Basics and its Fundamentals
• Kerberos Attack and Defense (Kerberoasting, Silver ticket, Golden ticket attack etc)
https://bsidessg.org/schedule/2019-ajaychoudhary-and-niteshmalviya/
Data Publication and Discovery with Globus



Data Publication and Discovery with GlobusGlobus This tutorial from the Gateways 2018 conference in Austin, TX explored the capabilities provided by Globus for assembling, describing, publishing, identifying, searching, and discovering datasets.
Apache Performance Tuning: Scaling Up



Apache Performance Tuning: Scaling UpSander Temme This is the version of my Apache Performance Tuning deck I last presented at ApacheCon, in 2008 in Amsterdam.
Introduction to Laravel Framework (5.2)



Introduction to Laravel Framework (5.2)Viral Solani This document provides an overview of the Laravel PHP framework, including why it was created, its main features and components. Some key points:
- Laravel was created to guide developers to best practices and utilizes modern PHP features. It has an active community and good documentation.
- Its major components include routing, controllers, blade templating, Eloquent ORM, authentication, queues and more. It also uses Composer for dependency management.
- Other tools in the Laravel ecosystem help with deployment (Homestead, Forge), billing (Cashier), APIs (Lumen) and more. The framework is fully-featured but aims to be easy to learn and use.
REST Api Tips and Tricks



REST Api Tips and TricksMaksym Bruner All we know that REST services are almost everywhere now and nearly all new projects use it.
But do we really know how to design proper interfaces? What are pitfalls and how to avoid them?
I did many REST service designs and have a bunch of tips and tricks you definitely would like to use.
It will save you and your team a lot of time in future.
Power on, Powershell



Power on, PowershellRoo7break This document discusses using PowerShell for penetration testing when standard tools and frameworks may not be usable due to network restrictions or lack of privileges. It provides an introduction to PowerShell and examples of how port scanning, downloading files, and other tasks could be accomplished using PowerShell scripts even in restricted environments. It also covers some of the security mechanisms in PowerShell like execution policies and how they can be bypassed to run unsigned scripts without prompts.
airflow web UI and CLI.pptx



airflow web UI and CLI.pptxVIJAYAPRABAP Airflow is a workflow management system for authoring, scheduling and monitoring workflows or pipelines. It has several key components including DAGs which define workflows as directed acyclic graphs of tasks. Operators represent individual tasks or steps while hooks allow connections to external systems. Airflow supports features like variables, cross-communication (XComs), security, CLI, and a user interface for visualizing workflows.
airflowpresentation1-180717183432.pptx



airflowpresentation1-180717183432.pptxVIJAYAPRABAP Airflow is a workflow management system for authoring, scheduling and monitoring workflows or directed acyclic graphs (DAGs) of tasks. It supports authoring workflows as Python code with built-in operators to interact with external systems and databases. Airflow has a modular architecture allowing different executors like Celery and Kubernetes. It provides features like variables, connections, XComs and service level agreements. The user interface allows visualizing and monitoring DAGs and includes data profiling capabilities. Airflow also has a command line interface and supports security features like authentication and impersonation.
Introduction to the Globus PaaS (GlobusWorld Tour - STFC)



Introduction to the Globus PaaS (GlobusWorld Tour - STFC)Globus Globus serves as a platform for building science gateways, web portals, and other applications in support of research and education. It provides identity and access management through Globus Auth as well as APIs for file transfer, search, and sharing. Developers can access these services through the Globus Python SDK or by using helper pages designed for web applications. Example applications include a modern research data portal that leverages Globus for authentication and file operations. Support resources include documentation, a helpdesk, professional services, and sample code.
Leveraging the Globus Platform (GlobusWorld Tour - UCSD)



Leveraging the Globus Platform (GlobusWorld Tour - UCSD)Globus Presented at the GlobusWorld Tour workshop at the University of California, San Diego on May 8, 2019.
Topic 3-1_More_Linux_Commands.pptx



Topic 3-1_More_Linux_Commands.pptxdulala3 1. The document provides an overview of more Linux commands and tools, including how to edit files, create users and groups, change file permissions, become the super user, install software, and use compression tools.
2. Commands covered include gedit and vi for text editing, useradd/groupadd for creating users and groups, chmod for changing file permissions, sudo for becoming the super user, apt-get for installing packages, and tar for compressing files.
3. The document also discusses concepts like file permissions represented as octal numbers, using sudo and root privileges carefully, and different methods for installing and compressing files in Linux.
Airflow presentation



Airflow presentationIlias Okacha Airflow is a workflow management system for authoring, scheduling and monitoring workflows or directed acyclic graphs (DAGs) of tasks. It has features like DAGs to define tasks and their relationships, operators to describe tasks, sensors to monitor external systems, hooks to connect to external APIs and databases, and a user interface for visualizing pipelines and monitoring runs. Airflow uses a variety of executors like SequentialExecutor, CeleryExecutor and MesosExecutor to run tasks on schedulers like Celery or Kubernetes. It provides security features like authentication, authorization and impersonation to manage access.
Defending Your "Gold"



Defending Your "Gold"Will Schroeder This presentation was given at PSConfEU and covers common privilege escalation vectors for Windows systems, as well as how to enumerate these issues with PowerUp.
The Google Chubby lock service for loosely-coupled distributed systems



The Google Chubby lock service for loosely-coupled distributed systemsRomain Jacotin The Google Chubby lock service presented in 2006 is the inspiration for Apache ZooKeeper: let's take a deep dive into Chubby to better understand ZooKeeper and distributed consensus.
Leveraging the Globus Platform (GlobusWorld Tour - Columbia University)



Leveraging the Globus Platform (GlobusWorld Tour - Columbia University)Globus The document discusses how the Globus platform can be leveraged to build science gateways, web portals, and other applications. It provides examples of how the Globus Auth, APIs, and Connect services can be used to enable authentication, file transfer, and data sharing. The Globus Python SDK and helper pages are also described as tools for developing applications that integrate Globus functionality.
Solr Recipes



Solr RecipesErik Hatcher Solr Recipes provides quick and easy steps for common use cases with Apache Solr. Bite-sized recipes will be presented for data ingestion, textual analysis, client integration, and each of Solr’s features including faceting, more-like-this, spell checking/suggest, and others.
Introduction to Globus: Research Data Management Software at the ALCF



Introduction to Globus: Research Data Management Software at the ALCFGlobus This document provides an introduction and overview of Globus, a research data management platform. It discusses how Globus can be used to move, share, discover, and reproduce data across different storage tiers and resources. Globus delivers fast and reliable big data transfer, sharing, and platform services directly from existing storage systems via software-as-a-service using existing identities, with the goal of unifying access to data across different locations and resources. The document demonstrates how Globus can be used via its web interface, command line interface, REST API, and as a platform for building other research applications and workflows.
Ad
Recently uploaded (20)
Exploring Wayland: A Modern Display Server for the Future



Exploring Wayland: A Modern Display Server for the FutureICS Wayland is revolutionizing the way we interact with graphical interfaces, offering a modern alternative to the X Window System. In this webinar, we’ll delve into the architecture and benefits of Wayland, including its streamlined design, enhanced performance, and improved security features.
PDF Reader Pro Crack Latest Version FREE Download 2025



PDF Reader Pro Crack Latest Version FREE Download 2025mu394968 🌍📱👉COPY LINK & PASTE ON GOOGLE https://dr-kain-geera.info/👈🌍
PDF Reader Pro is a software application, often referred to as an AI-powered PDF editor and converter, designed for viewing, editing, annotating, and managing PDF files. It supports various PDF functionalities like merging, splitting, converting, and protecting PDFs. Additionally, it can handle tasks such as creating fillable forms, adding digital signatures, and performing optical character recognition (OCR).
Douwan Crack 2025 new verson+ License code



Douwan Crack 2025 new verson+ License codeaneelaramzan63 Copy & Paste On Google >>> https://dr-up-community.info/
Douwan Preactivated Crack Douwan Crack Free Download. Douwan is a comprehensive software solution designed for data management and analysis.
Download Wondershare Filmora Crack [2025] With Latest![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
![Download Wondershare Filmora Crack [2025] With Latest](https://cdn.slidesharecdn.com/ss_thumbnails/neo4j-howkgsareshapingthefutureofgenerativeaiatawssummitlondonapril2024-240426125209-2d9db05d-250419-250428115407-a04afffa-thumbnail.jpg?width=560&fit=bounds)
Download Wondershare Filmora Crack [2025] With Latesttahirabibi60507 Copy & Past Link 👉👉
http://drfiles.net/
Wondershare Filmora is a video editing software and app designed for both beginners and experienced users. It's known for its user-friendly interface, drag-and-drop functionality, and a wide range of tools and features for creating and editing videos. Filmora is available on Windows, macOS, iOS (iPhone/iPad), and Android platforms.
Who Watches the Watchmen (SciFiDevCon 2025)



Who Watches the Watchmen (SciFiDevCon 2025)Allon Mureinik Tests, especially unit tests, are the developers’ superheroes. They allow us to mess around with our code and keep us safe.
We often trust them with the safety of our codebase, but how do we know that we should? How do we know that this trust is well-deserved?
Enter mutation testing – by intentionally injecting harmful mutations into our code and seeing if they are caught by the tests, we can evaluate the quality of the safety net they provide. By watching the watchmen, we can make sure our tests really protect us, and we aren’t just green-washing our IDEs to a false sense of security.
Talk from SciFiDevCon 2025
https://www.scifidevcon.com/courses/2025-scifidevcon/contents/680efa43ae4f5
Download YouTube By Click 2025 Free Full Activated



Download YouTube By Click 2025 Free Full Activatedsaniamalik72555 Copy & Past Link 👉👉
https://dr-up-community.info/
"YouTube by Click" likely refers to the ByClick Downloader software, a video downloading and conversion tool, specifically designed to download content from YouTube and other video platforms. It allows users to download YouTube videos for offline viewing and to convert them to different formats.
Interactive odoo dashboards for sales, CRM , Inventory, Invoice, Purchase, Pr...



Interactive odoo dashboards for sales, CRM , Inventory, Invoice, Purchase, Pr...AxisTechnolabs Interactive Odoo Dashboard for various business needs can provide users with dynamic, visually appealing dashboards tailored to their specific requirements. such a module that could support multiple dashboards for different aspects of a business
✅Visit And Buy Now : https://bit.ly/3VojWza
✅This Interactive Odoo dashboard module allow user to create their own odoo interactive dashboards for various purpose.
App download now :
Odoo 18 : https://bit.ly/3VojWza
Odoo 17 : https://bit.ly/4h9Z47G
Odoo 16 : https://bit.ly/3FJTEA4
Odoo 15 : https://bit.ly/3W7tsEB
Odoo 14 : https://bit.ly/3BqZDHg
Odoo 13 : https://bit.ly/3uNMF2t
Try Our website appointment booking odoo app : https://bit.ly/3SvNvgU
👉Want a Demo ?📧 [email protected]
➡️Contact us for Odoo ERP Set up : 091066 49361
👉Explore more apps: https://bit.ly/3oFIOCF
👉Want to know more : 🌐 https://www.axistechnolabs.com/
#odoo #odoo18 #odoo17 #odoo16 #odoo15 #odooapps #dashboards #dashboardsoftware #odooerp #odooimplementation #odoodashboardapp #bestodoodashboard #dashboardapp #odoodashboard #dashboardmodule #interactivedashboard #bestdashboard #dashboard #odootag #odooservices #odoonewfeatures #newappfeatures #odoodashboardapp #dynamicdashboard #odooapp #odooappstore #TopOdooApps #odooapp #odooexperience #odoodevelopment #businessdashboard #allinonedashboard #odooproducts
How to Optimize Your AWS Environment for Improved Cloud Performance



How to Optimize Your AWS Environment for Improved Cloud PerformanceThousandEyes How to Optimize Your AWS Environment for Improved Cloud Performance
Mastering Fluent Bit: Ultimate Guide to Integrating Telemetry Pipelines with ...



Mastering Fluent Bit: Ultimate Guide to Integrating Telemetry Pipelines with ...Eric D. Schabell It's time you stopped letting your telemetry data pressure your budgets and get in the way of solving issues with agility! No more I say! Take back control of your telemetry data as we guide you through the open source project Fluent Bit. Learn how to manage your telemetry data from source to destination using the pipeline phases covering collection, parsing, aggregation, transformation, and forwarding from any source to any destination. Buckle up for a fun ride as you learn by exploring how telemetry pipelines work, how to set up your first pipeline, and exploring several common use cases that Fluent Bit helps solve. All this backed by a self-paced, hands-on workshop that attendees can pursue at home after this session (https://o11y-workshops.gitlab.io/workshop-fluentbit).
Adobe Illustrator Crack FREE Download 2025 Latest Version



Adobe Illustrator Crack FREE Download 2025 Latest Versionkashifyounis067 🌍📱👉COPY LINK & PASTE ON GOOGLE http://drfiles.net/ 👈🌍
Adobe Illustrator is a powerful, professional-grade vector graphics software used for creating a wide range of designs, including logos, icons, illustrations, and more. Unlike raster graphics (like photos), which are made of pixels, vector graphics in Illustrator are defined by mathematical equations, allowing them to be scaled up or down infinitely without losing quality.
Here's a more detailed explanation:
Key Features and Capabilities:
Vector-Based Design:
Illustrator's foundation is its use of vector graphics, meaning designs are created using paths, lines, shapes, and curves defined mathematically.
Scalability:
This vector-based approach allows for designs to be resized without any loss of resolution or quality, making it suitable for various print and digital applications.
Design Creation:
Illustrator is used for a wide variety of design purposes, including:
Logos and Brand Identity: Creating logos, icons, and other brand assets.
Illustrations: Designing detailed illustrations for books, magazines, web pages, and more.
Marketing Materials: Creating posters, flyers, banners, and other marketing visuals.
Web Design: Designing web graphics, including icons, buttons, and layouts.
Text Handling:
Illustrator offers sophisticated typography tools for manipulating and designing text within your graphics.
Brushes and Effects:
It provides a range of brushes and effects for adding artistic touches and visual styles to your designs.
Integration with Other Adobe Software:
Illustrator integrates seamlessly with other Adobe Creative Cloud apps like Photoshop, InDesign, and Dreamweaver, facilitating a smooth workflow.
Why Use Illustrator?
Professional-Grade Features:
Illustrator offers a comprehensive set of tools and features for professional design work.
Versatility:
It can be used for a wide range of design tasks and applications, making it a versatile tool for designers.
Industry Standard:
Illustrator is a widely used and recognized software in the graphic design industry.
Creative Freedom:
It empowers designers to create detailed, high-quality graphics with a high degree of control and precision.
Adobe Lightroom Classic Crack FREE Latest link 2025



Adobe Lightroom Classic Crack FREE Latest link 2025kashifyounis067 🌍📱👉COPY LINK & PASTE ON GOOGLE http://drfiles.net/ 👈🌍
Adobe Lightroom Classic is a desktop-based software application for editing and managing digital photos. It focuses on providing users with a powerful and comprehensive set of tools for organizing, editing, and processing their images on their computer. Unlike the newer Lightroom, which is cloud-based, Lightroom Classic stores photos locally on your computer and offers a more traditional workflow for professional photographers.
Here's a more detailed breakdown:
Key Features and Functions:
Organization:
Lightroom Classic provides robust tools for organizing your photos, including creating collections, using keywords, flags, and color labels.
Editing:
It offers a wide range of editing tools for making adjustments to color, tone, and more.
Processing:
Lightroom Classic can process RAW files, allowing for significant adjustments and fine-tuning of images.
Desktop-Focused:
The application is designed to be used on a computer, with the original photos stored locally on the hard drive.
Non-Destructive Editing:
Edits are applied to the original photos in a non-destructive way, meaning the original files remain untouched.
Key Differences from Lightroom (Cloud-Based):
Storage Location:
Lightroom Classic stores photos locally on your computer, while Lightroom stores them in the cloud.
Workflow:
Lightroom Classic is designed for a desktop workflow, while Lightroom is designed for a cloud-based workflow.
Connectivity:
Lightroom Classic can be used offline, while Lightroom requires an internet connection to sync and access photos.
Organization:
Lightroom Classic offers more advanced organization features like Collections and Keywords.
Who is it for?
Professional Photographers:
PCMag notes that Lightroom Classic is a popular choice among professional photographers who need the flexibility and control of a desktop-based application.
Users with Large Collections:
Those with extensive photo collections may prefer Lightroom Classic's local storage and robust organization features.
Users who prefer a traditional workflow:
Users who prefer a more traditional desktop workflow, with their original photos stored on their computer, will find Lightroom Classic a good fit.
How can one start with crypto wallet development.pptx



How can one start with crypto wallet development.pptxlaravinson24 This presentation is a beginner-friendly guide to developing a crypto wallet from scratch. It covers essential concepts such as wallet types, blockchain integration, key management, and security best practices. Ideal for developers and tech enthusiasts looking to enter the world of Web3 and decentralized finance.
Exceptional Behaviors: How Frequently Are They Tested? (AST 2025)



Exceptional Behaviors: How Frequently Are They Tested? (AST 2025)Andre Hora Exceptions allow developers to handle error cases expected to occur infrequently. Ideally, good test suites should test both normal and exceptional behaviors to catch more bugs and avoid regressions. While current research analyzes exceptions that propagate to tests, it does not explore other exceptions that do not reach the tests. In this paper, we provide an empirical study to explore how frequently exceptional behaviors are tested in real-world systems. We consider both exceptions that propagate to tests and the ones that do not reach the tests. For this purpose, we run an instrumented version of test suites, monitor their execution, and collect information about the exceptions raised at runtime. We analyze the test suites of 25 Python systems, covering 5,372 executed methods, 17.9M calls, and 1.4M raised exceptions. We find that 21.4% of the executed methods do raise exceptions at runtime. In methods that raise exceptions, on the median, 1 in 10 calls exercise exceptional behaviors. Close to 80% of the methods that raise exceptions do so infrequently, but about 20% raise exceptions more frequently. Finally, we provide implications for researchers and practitioners. We suggest developing novel tools to support exercising exceptional behaviors and refactoring expensive try/except blocks. We also call attention to the fact that exception-raising behaviors are not necessarily “abnormal” or rare.
Get & Download Wondershare Filmora Crack Latest [2025]![Get & Download Wondershare Filmora Crack Latest [2025]](https://cdn.slidesharecdn.com/ss_thumbnails/revolutionizingresidentialwi-fi-250422112639-60fb726f-250429170801-59e1b240-thumbnail.jpg?width=560&fit=bounds)
![Get & Download Wondershare Filmora Crack Latest [2025]](https://cdn.slidesharecdn.com/ss_thumbnails/revolutionizingresidentialwi-fi-250422112639-60fb726f-250429170801-59e1b240-thumbnail.jpg?width=560&fit=bounds)
![Get & Download Wondershare Filmora Crack Latest [2025]](https://cdn.slidesharecdn.com/ss_thumbnails/revolutionizingresidentialwi-fi-250422112639-60fb726f-250429170801-59e1b240-thumbnail.jpg?width=560&fit=bounds)
![Get & Download Wondershare Filmora Crack Latest [2025]](https://cdn.slidesharecdn.com/ss_thumbnails/revolutionizingresidentialwi-fi-250422112639-60fb726f-250429170801-59e1b240-thumbnail.jpg?width=560&fit=bounds)
Get & Download Wondershare Filmora Crack Latest [2025]saniaaftab72555 Copy & Past Link 👉👉
https://dr-up-community.info/
Wondershare Filmora is a video editing software and app designed for both beginners and experienced users. It's known for its user-friendly interface, drag-and-drop functionality, and a wide range of tools and features for creating and editing videos. Filmora is available on Windows, macOS, iOS (iPhone/iPad), and Android platforms.
Avast Premium Security Crack FREE Latest Version 2025



Avast Premium Security Crack FREE Latest Version 2025mu394968 🌍📱👉COPY LINK & PASTE ON GOOGLE https://dr-kain-geera.info/👈🌍
Avast Premium Security is a paid subscription service that provides comprehensive online security and privacy protection for multiple devices. It includes features like antivirus, firewall, ransomware protection, and website scanning, all designed to safeguard against a wide range of online threats, according to Avast.
Key features of Avast Premium Security:
Antivirus: Protects against viruses, malware, and other malicious software, according to Avast.
Firewall: Controls network traffic and blocks unauthorized access to your devices, as noted by All About Cookies.
Ransomware protection: Helps prevent ransomware attacks, which can encrypt your files and hold them hostage.
Website scanning: Checks websites for malicious content before you visit them, according to Avast.
Email Guardian: Scans your emails for suspicious attachments and phishing attempts.
Multi-device protection: Covers up to 10 devices, including Windows, Mac, Android, and iOS, as stated by 2GO Software.
Privacy features: Helps protect your personal data and online privacy.
In essence, Avast Premium Security provides a robust suite of tools to keep your devices and online activity safe and secure, according to Avast.
Solidworks Crack 2025 latest new + license code



Solidworks Crack 2025 latest new + license codeaneelaramzan63 Copy & Paste On Google >>> https://dr-up-community.info/
The two main methods for installing standalone licenses of SOLIDWORKS are clean installation and parallel installation (the process is different ...
Disable your internet connection to prevent the software from performing online checks during installation
Adobe Marketo Engage Champion Deep Dive - SFDC CRM Synch V2 & Usage Dashboards



Adobe Marketo Engage Champion Deep Dive - SFDC CRM Synch V2 & Usage DashboardsBradBedford3 Join Ajay Sarpal and Miray Vu to learn about key Marketo Engage enhancements. Discover improved in-app Salesforce CRM connector statistics for easy monitoring of sync health and throughput. Explore new Salesforce CRM Synch Dashboards providing up-to-date insights into weekly activity usage, thresholds, and limits with drill-down capabilities. Learn about proactive notifications for both Salesforce CRM sync and product usage overages. Get an update on improved Salesforce CRM synch scale and reliability coming in Q2 2025.
Key Takeaways:
Improved Salesforce CRM User Experience: Learn how self-service visibility enhances satisfaction.
Utilize Salesforce CRM Synch Dashboards: Explore real-time weekly activity data.
Monitor Performance Against Limits: See threshold limits for each product level.
Get Usage Over-Limit Alerts: Receive notifications for exceeding thresholds.
Learn About Improved Salesforce CRM Scale: Understand upcoming cloud-based incremental sync.
WinRAR Crack for Windows (100% Working 2025)



WinRAR Crack for Windows (100% Working 2025)sh607827 copy and past on google ➤ ➤➤ https://hdlicense.org/ddl/
WinRAR Crack Free Download is a powerful archive manager that provides full support for RAR and ZIP archives and decompresses CAB, ARJ, LZH, TAR, GZ, ACE, UUE, .
Societal challenges of AI: biases, multilinguism and sustainability



Societal challenges of AI: biases, multilinguism and sustainabilityJordi Cabot Towards a fairer, inclusive and sustainable AI that works for everybody.
Reviewing the state of the art on these challenges and what we're doing at LIST to test current LLMs and help you select the one that works best for you
Ad
aclpwn - Active Directory ACL exploitation with BloodHound
- 1. fox-it.com Dirk-jan Mollema @_dirkjan Aclpwn.py – Active Directory ACL exploitation with BloodHound
- 2. fox-it.com - Lives in The Netherlands - Hacker / Red Teamer / Researcher @ Fox-IT since 2016 - Previously freelance webdeveloper - Author of several Active Directory tools: - mitm6 - ldapdomaindump - BloodHound.py - Co-author of ntlmrelayx - Blogs on dirkjanm.io - Tweets stuff on @_dirkjan Whoami
- 3. fox-it.com • What are ACLs • Common ACL abuse paths • aclpwn.py concepts • Using aclpwn.py Contents
- 4. fox-it.com • https://github.com/ANSSI-FR/AD-control-paths (Emmanuel Gras and Lucas Bouillot from ANSSI – 2014) • “An ACE up the Sleeve” – BH USA 2017 (by @_wald0 and @harmj0y) • BloodHound (@_wald0, @harmj0y and @CptJesus) Abusing ACLs – prior work
- 5. fox-it.com What are ACLs – the short version
- 6. fox-it.com • In Active Directory, an ACL defines who can do what on an object • Objects: • Users • Groups • Computers • Domain(s) What are ACLs – the short version
- 7. fox-it.com • Access Control List • SACL – used for auditing access • DACL – used for defining who has what access on an object • DACL exists of ACEs • Access Control Entries What are ACLs - Terminology
- 9. fox-it.com ACLs are hard (2) ??? ?????
- 10. fox-it.com ACLs are hard (3) ??? !!!
- 11. fox-it.com • Even some default ACLs are too complex for the UI to display • We can’t realistically expect sysadmins to keep track of ACLs or to fully understand their impact • Especially not if they are inherited or nested • Tooling is needed! ACLs are hard!
- 12. fox-it.com • BloodHound 1.3 introduced the ACL update • Makes it easy to identify ACLs • Identify them with SharpHound.exe -c ACL • Not yet supported in BloodHound.py (but work in progress) Mapping ACLs with BloodHound Source: https://wald0.com/?p=112
- 13. fox-it.com ACL abuse – case studies
- 14. fox-it.com • By default “Exchange Windows Permissions” has wide-reaching privileges in the domain • Including WriteDacl on the Domain object • Allows any Exchange Server to grant DCSync privileges • Effectively: local admin on Exchange Server = Domain Admin Bad ACLs – Case study 1: Exchange Sources: - https://www.specterops.io/assets/resources/an_ace_up_the_sleeve.pdf - https://github.com/gdedrouas/Exchange-AD-Privesc - https://blog.fox-it.com/2018/04/26/escalating-privileges-with-acls-in-active-directory/
- 15. fox-it.com Bad ACLs – Case study 1: Exchange
- 16. fox-it.com • No need to run anything on the Exchange server • Just dump hashes of machine account and feed them to aclpwn.py • Aclpwn.py will pass-the-hash and gain privileges • DCSync with secretsdump.py (impacket) Bad ACLs – Case study 1: Exchange
- 17. fox-it.com • ADPREP in Server 2016 introduces an “Enterprise Key Admins” group • This group has full control over the Domain object (before v1709) • Allows Account Operators to obtain DCSync privileges Bad ACLs – Case study 2: Enterprise key admins Sources: - https://secureidentity.se/adprep-bug-in-windows-server-2016/ - My lab ☺
- 18. fox-it.com Bad ACLs – Case study 2: Enterprise key admins
- 19. fox-it.com WriteDacl on Domain object => DCSync privileges
- 21. fox-it.com • PowerSploit (https://github.com/PowerShellMafia/PowerSploit) • Manual exploitation only • Can be confusing if there are multiple steps in the chain • Complex to use with machine accounts or pass-the-hash • Invoke-AclPwn (https://github.com/fox-it/Invoke-ACLPwn) • Automated pathfinding • Parses SharpHound output on host (slow) • Limited scenario’s • Complex to use with machine accounts or pass-the-hash Existing ACL exploitation tools and their limitations
- 22. fox-it.com • Direct integration with BloodHound and the Neo4j graph database • Supports any reversible ACL based attack chain • Advanced pathfinding to find the most efficient paths • Support for exploitation with NTLM hashes (pass-the-hash) • Saves restore state, easy rollback of changes • Can be run via a SOCKS tunnel • Written in Python (2.7 and 3.5+), so OS independent aclpwn.py
- 23. fox-it.com • Find an exploitation path • Start at a user/computer • End at a group or domain • aclpwn.py finds the most efficient path • Objects are modified to obtain the required access • After action on objectives is achieved, path is walked in reverse and privileges are restored aclpwn.py - the concept
- 25. fox-it.com • Shortest path is not always the most efficient path • Neo4j counts path length based on number of nodes • If we have the following scenario: • User “test” is member of group A • Group A is member of group B • Group B is member of group C • Group C is member of Domain Admins • AND user “test” has AddMember on Domain Admins • Neo4j will see the path (Test)-[AddMember]->(Domain Admins) as shortest. • Even if user A is effectively already a domain admin Pathfinding with Neo4j
- 26. fox-it.com Solution: weighed paths Weight: 0 Weight: 1
- 27. fox-it.com • Either calculated manually (faster but less accurate, may miss paths) • Or discovered using the Dijkstra algorithm (slower, but more accurate) • Different weights for different modification parameters Weighed paths
- 28. fox-it.com • Shortest only: • Dijkstra: Pathfinding methods
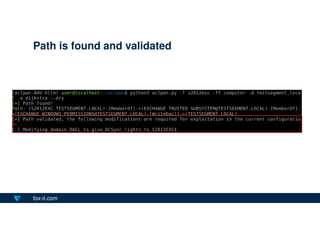
- 29. fox-it.com Path is found and validated
- 30. fox-it.com Example: escalating from account operators
- 31. fox-it.com Example: escalating from account operators
- 32. fox-it.com • ForceChangePassword: • We have the right to change the user’s password • Not easily possible to restore afterwards (only with dcshadow or setntlm) • Not supported for now • Solution: split the path, perform password reset manually • WriteOwner: • Seems to be limited to set the owner to your own user • Not possible to restore right now • Needs more investigation Non-supported edges and limitations
- 33. fox-it.com • Aclpwn will remember state during exploitation • Possible to restore all operations using --restore option • Different restore strategies Restore operation
- 36. fox-it.com • Audit your ACLs! • Use BloodHound • Remove dangerous ACLs (for example Exchange) • Restrict permission delegation • Admin on Exchange Server => Domain Admin • Admin on Azure AD connect host => Domain Admin • Resetting password of high privilege users => Domain Admin • Managing groups with high privileges => Domain Admin Defending against ACL attacks
- 37. fox-it.com • Monitor for ACL changes • Use SACLs to generate events for important object modifications • Use event logging to monitor DACL changes • See: https://blog.fox-it.com/2018/04/26/escalating-privileges-with- acls-in-active-directory/ Defending against ACL attacks
- 39. fox-it.com • ACL attacks are still relatively unknown • But present in almost every Active Directory • You don’t need a Domain Admin session to pwn the domain • More tooling will (hopefully) raise awareness for this issue Conclusions
- 40. fox-it.com • Online at https://github.com/fox-it/aclpwn.py • Follow me on Twitter to keep up-to-date with my work (@_dirkjan) • I’ll be demo-ing aclpwn.py this afternoon tomorrow morning • Feel free to drop by for any questions! ☺ Get the tools
- 41. fox-it.com Dirk-jan Mollema Aclpwn.py – Active Directory ACL exploitation with BloodHound
