Ad
AdvisorAssist Presentation: Cloud Computing and Compliance For RIAs
- 1. Cloud Computing For RIAs: Compliance Tips And Practical IT Considerations for Registered Investment Advisors April, 2012 Confidential. For recipients use only.
- 2. What is Cloud Computing? 2 Copyright 2011 AdvisorAssist, LLC
- 3. Rationale for Cloud Computing Ease of systems and data access Lower IT costs Integration among systems 24 x 7 access Ability to supervise remote teams Share data seamlessly with clients Enhanced business continuity Stronger data redundancy …the list grows daily! Regulations are still lagging innovation, but cloud systems can be more sound and secure than in-house systems – with the right controls! 3 Copyright 2011 AdvisorAssist, LLC
- 4. Regulatory Framework for RIAs Registered Investment Advisors are required, pursuant to IA Rule 206(4)-7 to design and implement a compliance program (And YES, the CCO has responsibility for Technology!) • Rule 206(4)-7 -- Compliance Procedures and Practices (“CCO Rule”) • Rule 204-2 -- Books and Records • Rule 206(4)-2 – Custody Rules (client passwords??) • Regulation S-P • Review adequacy at least annually Advisers Act discusses the principles and expectations, but does not impose standards on how to meet them. • Often more flexibility than Exchange and FINRA rules • Email and data retention. No WORM requirement • Due diligence requirements • Privacy laws – more than Regulation S-P • Example – MA Privacy Law – specific rules if you hold private data 4 Copyright 2011 AdvisorAssist, LLC
- 5. Regulatory Framework for RIAs All firms must have Policies and Procedures that address Privacy, Data Security, Use of technology, Escalation of Issues, etc. All financial services firms must have a Business Continuity Plan. Cloud systems can make this easier. All Compliance Programs must be tested at least annually. Systems and controls must be adequately designed to protect Client interests and private information. Firms must conduct both initial and ongoing testing and due diligence of their technology and service providers. 5 Copyright 2011 AdvisorAssist, LLC
- 6. Data Protection All critical data in single location is a risk – Hackers, thieves only have to get lucky once! Implementation of access controls with roles/privileges. Complex password requirements and expiration policy. Vendor privacy and data policies? Who is the vendor to the vendor? (You need to do your due diligence.) Implementation of strong authentication and passing on vendors that have loose controls. Vendor viability – don’t bet it all on a vendor that might not be there in a month! Data location – do you know where your data resides? Is it even in the U.S? 6 Copyright 2011 AdvisorAssist, LLC
- 7. Initial Vendor Due Diligence Develop a requirements matrix • End-user needs • Technology integration and management • Compliance oversight Understand the data security model Determine location of data center(s) Ensure that there is a redundancy model in place Assess before you buy Talk to existing users of the service provider (not just the salesperson’s referrals) Consider the financial viability of providers Assess service provider’s customer service model... Are they open when you are open? 7 Copyright 2011 AdvisorAssist, LLC
- 8. Compliance Benefits of Cloud Computing Remove geography from books and records storage Supervise remote personnel and offices Monitor who is using which systems and when Control access to sensitive data Reduce input error through re-keying of data Reduce need to send private information via email Produce audit trails and redundancy models There are some risks to cloud computing. But benefits typically outweigh them. 8 Copyright 2011 AdvisorAssist, LLC
- 9. Ongoing Testing and Due Diligence Assess vendor’s attitude towards testing • SAS-70? • Test at least annually. Pick a time of year that is best for your firm. Perform a “real” test. • Data security • Business continuity • Data retention • Compliance and IT Staff TOGETHER • Document gaps, consider remediation alternatives Output = Assessment report with gaps and enhancement recommendations. 9 Copyright 2011 AdvisorAssist, LLC
- 10. Ongoing Testing and Due Diligence: What do I test? Inventory all systems and integrations. Are they reflected in your BCP Plan and IT Policies? Review the vendor’s controls and testing performed on their end (i.e., SAS-70). Any security breaches? What is their BCP Plan? Data retention. Can you find a specific client record from last week, last month or 3 years ago on random date? Data security. Ask for the API and port logs. Where is your data going? Any abnormalities during testing on that given day? User access. Which users are embracing your cloud-based systems? Any with low use? Check user’s laptops for local files. 10 Copyright 2011 AdvisorAssist, LLC
- 11. Getting Started in the Cloud Identify your business goals Develop a work plan Identify possible solutions Evaluate the viability and integration options Assemble the implementation team Refine the plan into a roadmap to success 11 Copyright 2011 AdvisorAssist, LLC
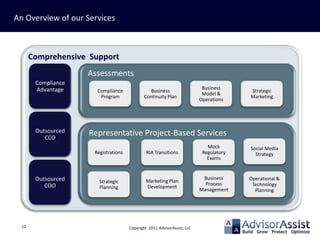
- 12. An Overview of our Services Comprehensive Support Assessments Compliance Advantage Business Compliance Business Strategic Model & Program Continuity Plan Marketing Operations Outsourced Representative Project-Based Services CCO Mock Social Media Registrations RIA Transitions Regulatory Strategy Exams Outsourced Business Operational & Strategic Marketing Plan COO Process Technology Planning Development Management Planning 12 Copyright 2011 AdvisorAssist, LLC
- 13. Solutions across the Investment Advisor Lifecycle Start Up or Transitioning Established Advisors Advisors • SEC & State Registration • Ongoing Compliance Support • RIA Transitions • SEC to State Transition • Operations & Technology • Mock SEC & State Exam Planning • Social Media Program Design • Marketing Planning & • Compliance Program Design Advertising Review • Strategic Planning • Business Development Planning • Outsourced CCO • Outsourced COO 13 Copyright 2011 AdvisorAssist, LLC
- 14. Leadership Biographies Christopher E. Winn Founder and Managing Principal Chris has over 17 years of asset management industry experience, with a focus on regulatory compliance, investment management operations, distribution and technology matters. Chris founded AdvisorAssist to help close the increasing gap in support for small and medium advisory firms. As the financial burden for compliance and business support for advisors has increased significantly over the past decade, many providers have simply tried to force big firm policies, controls and systems on small firms. There is a better way. Chris serves as an Advisory Board member for several investment management and technology firms. Prior to founding AdvisorAssist, Chris was a Co- founder and Managing Principal of MainStay Consulting Group, LLC, a strategy and compliance consulting firm serving the needs of investment advisors, fund complexes and private investment firms. Before founding MainStay, Chris was the Chief Operating Officer and Chief Compliance Officer for Open Investing, Inc., a registered investment advisor and its affiliated RIA, AdvisorNow, Inc. Prior to serving as COO/CCO, Chris was as an Associate Director in the Investment Management Consulting Practice of Navigant Consulting, an international compliance, forensic and litigation support consulting firm. At Navigant, Chris led regulatory compliance teams in assessing the effectiveness of the design and implementation of compliance programs pursuant to Rule 206(4)-7 of the Investment Advisers Act of 1940, Rule 38a-1 of the Investment Company Act of 1940, and other federal securities laws. Chris has served in several leadership roles within investment advisory firms, including Chief Compliance Officer, Chief Operating Officer, Assistant Treasurer (Mutual Funds), Vice President of Product Distribution, Vice President/Head of Business Operations, and Vice President Operations and Compliance. Chris started his career focusing on operational and regulatory challenges for investment advisors, investment companies and their service providers. 14 Copyright 2011 AdvisorAssist, LLC
- 15. Leadership Biographies Brian R. Lauzon, CFA Managing Principal Brian has over 18 years experience in the investment industry with specific expertise in firm management, strategic and operational planning, institutional and retail distribution and product management. His background spans across all non-investment functions within the investment advisory firm and his experience encompasses several asset classes (equities, fixed income, alternative investments) and distribution channels. Prior to joining AdvisorAssist, Brian ran a start-up hedge fund advisory firm where he was responsible for leading the firm’s non-investment functions, including strategic management, operations, marketing and finance. Prior to this, Brian was Equity Chief Operating Officer at Delaware Investments where he was responsible for project leadership and process development within their equity franchise. His efforts integrated a broad range of functional activities including: investment process/performance evaluation, risk management, legal, compliance, finance and operations. In 2009, Brian led Delaware’s efforts in the formation of a new global hedge fund offering. Previously, Brian was a partner and member of the management committee at Merganser Capital, an institutional fixed income advisory firm. He led Merganser’s distribution and client service efforts during a period of rapid organizational growth and change. Brian graduated from Villanova University and received an MBA with honors from The Wharton School of the University of Pennsylvania. He currently serves on the board of the CFA Society of Philadelphia. 15 Copyright 2011 AdvisorAssist, LLC
- 16. Leadership Biographies Gregory A. Brown Principal Greg has over 9 years of industry experience, focused primarily on consulting in regulatory matters including the evaluation and implementation of compliance policies and procedures and providing business advisory services to assess the operational and regulatory risks for various investment industry organizations. His background includes work with registered investment advisors, mutual funds, hedge funds, and service providers. His expertise includes evaluating business activities, developing risk assessments for policies, procedures and related internal controls, writing compliance policies and procedures, identifying best practices and conflicts of interest, and developing risk-based compliance monitoring programs. Greg’s experience also includes assisting clients with SEC enforcement actions, and a variety of litigation and forensic accounting matters including standard of care in fund administration, recreating fund financial statements, and assisting with violations to the securities laws. Prior to his career in consulting, Greg worked at the U.S. Securities and Exchange Commission for two years where he participated on compliance examinations of financial services companies and investigations of various entities and individuals related to violations of the securities laws. His experience includes examinations of investment advisors and investment companies operations, books and records, and procedures for safeguarding securities and business methodology. Mr. Brown was responsible for conducting interviews with personnel and preparing necessary schedules, materials, and evaluations to formulate conclusions regarding compliance with regulatory requirements. His investigations included work on various financial fraud matters involving complex accounting issues, earnings management schemes, improper hedge accounting, Ponzi schemes, market timing, market manipulation and various other matters. Greg graduated from Boston University and earned an MA in economics and a BA in economics and applied mathematics. He is currently a CFA Level II candidate as well as a member of CFA Institute and the Boston Security Analysts Society. 16 Copyright 2011 AdvisorAssist, LLC
- 17. Leadership Biographies Jack O’Hara Vice President & National Sales Director Jack is responsible for achieving the company’s business development goals. He has over 20 years of financial services industry experience in developing and executing sales and marketing strategies. Jack’s resume includes leadership positions at Broadridge Financial Solutions, Philadelphia Stock Exchange, and as an Advisor and Registered Rep at Morgan Stanley and PNC Bank. More recently Jack was in charge of sales for an early-stage software vendor serving the investment management sector and developed the strategy that led the company to a market leadership position. Jack is a graduate of The Wharton School of the University of Pennsylvania, and currently involved with the Wharton Small Business Development Center. Prior to joining AdvisorAssist, Jack was the initial Vice President of Sales for an early-stage software vendor serving investment management firms and was responsible for the marketing and sales strategy. While in this role, Jack developed a business development strategy that expanded the target market to include retail advisory firms and led the company into a market leadership position. Jack’s resume also includes leadership positions at Broadridge Financial Solutions, Philadelphia Stock Exchange, and as a Registered Rep and Advisor at Morgan Stanley and PNC Bank. Jack is a graduate of the Wharton School at the University of Pennsylvania and current member of the Wharton Small Business Development Center. 17 Copyright 2011 AdvisorAssist, LLC




















































![[Webinar] - Using RPA to Accelerate the Benefits from Shared Services](https://cdn.slidesharecdn.com/ss_thumbnails/webinar-usingrpatoacceleratethebenefitsfromsharedservices-200529082716-thumbnail.jpg?width=560&fit=bounds)






























