Agile and Secure SDLC
Download as PPTX, PDF10 likes9,645 views
This document discusses implementing a secure software development lifecycle (SDLC) to improve application security. It outlines why the traditional approach of only involving security experts does not work. Instead, it proposes integrating security practices throughout each phase of the development process, including requirements, design, implementation, verification, and release. This includes training developers, conducting threat modeling and security testing, using security tools in continuous integration, and analyzing results to address issues early. The goal is to reduce security defects over time by changing developer mindsets and integrating security as applications are built.
1 of 45
Downloaded 330 times










































Ad
Recommended
Static Analysis Security Testing for Dummies... and You



Static Analysis Security Testing for Dummies... and YouKevin Fealey Most enterprise application security teams have at least one Static Analysis Security Testing (SAST) tool in their tool-belt; but for many, the tool never leaves the belt. SAST tools have gotten a reputation for being slow, error-prone, and difficult to use; and out of the box, many of them are – but with a little more knowledge behind how these tools are designed, a SAST tool can be a valuable part of any security program.
In this talk, we’ll help you understand the strengths and weaknesses of SAST tools by illustrating how they trace your code for vulnerabilities. You’ll see out-of-the-box rules for commercial and open-source SAST tools, and learn how to write custom rules for the widely-used open source SAST tool, PMD. We’ll explain the value of customizing tools for your organization; and you’ll learn how to integrate SAST technologies into your existing build and deployment pipelines. Lastly, we’ll describe many of the common challenges organizations face when deploying a new security tool to security or development teams, as well as some helpful hints to resolve these issues
DevOps to DevSecOps Journey..



DevOps to DevSecOps Journey..Siddharth Joshi Here is the small presentation on DevOps to DevSecOps Journey..
- What is DevOps and their best practices.
- Practical Scenario of DevOps practices.
- DevOps transformation Journey.
- Transition to DevSecOps and why we need it.
- Enterprise CI/CD Pipeline.
DevSecOps



DevSecOpsJoel Divekar This document discusses DevSecOps and provides information about integrating security practices into the DevOps process. It describes how DevSecOps improves upon traditional DevOps by adding security checks to code, containers, and infrastructure. These checks help detect vulnerabilities, sensitive information, and non-compliance before code is deployed. The document also introduces the open-source auditing tool Lynis, which scans servers to identify vulnerabilities and compliance issues across the operating system, network settings, authentication methods, and more.
Practical DevSecOps - Arief Karfianto



Practical DevSecOps - Arief Karfiantoidsecconf This document discusses practical DevSecOps. It begins with an agenda and introduction of the presenter. It then describes the presenter's work background and organization. The document outlines the development lifecycle, from no versioning or automation to introducing versioning, continuous integration, and automated security analysis. It discusses competing priorities between business, development, security, and operations. The rest of the document covers why automation is important, what DevOps and DevSecOps are, an example GitLab CI configuration, lessons learned, and concludes by thanking the audience.
Demystifying DevSecOps



Demystifying DevSecOpsArchana Joshi This document discusses DevSecOps, which involves infusing security practices into the development lifecycle to enable faster release cycles while maintaining security. It notes that over 53,000 cybersecurity incidents occurred in India in 2017. Implementing DevSecOps requires changes across an organization's people, processes, tools, and governance to embed security responsibilities across all teams. The typical DevSecOps pipeline shifts security left through activities like threat modeling, security testing, and monitoring throughout the development lifecycle.
Soc analyst course content v3



Soc analyst course content v3ShivamSharma909 The SOC analyst training program is meticulously designed by the subject matter experts at Infosec Train. The training program offers a deep insight into the SOC operations and workflows. It is an excellent opportunity for aspiring and current SOC analysts (L1/L2/L3) to level up their skills to mitigate business risks by effectively handling and responding to security threats.
https://www.infosectrain.com/courses/soc-analyst-expert-training/
Threat Hunting



Threat HuntingSplunk The document is a presentation on threat hunting with Splunk. It discusses threat hunting basics, data sources for threat hunting, knowing your endpoint, and using the cyber kill chain framework. It outlines an agenda that includes a hands-on walkthrough of an attack scenario using Splunk's core capabilities. It also discusses advanced threat hunting techniques and tools, enterprise security walkthroughs, and applying machine learning and data science to security.
Information Security and the SDLC



Information Security and the SDLCBDPA Charlotte - Information Technology Thought Leaders BDPA Charlotte Program Meeting
Date: 10/8/2010
Topic: Information Security and the SDLC
Presenter: Ron Clement, CISSP
Basic of SSDLC



Basic of SSDLCChitpong Wuttanan The document discusses the Secure Software Development Life Cycle (SSDLC) and provides recommendations for developers to integrate security into their processes. It recommends that developers understand common threats, perform penetration testing, implement logging of abnormal activity, secure all inputs and outputs, and consider security requirements throughout the entire development cycle from design to deployment. The document emphasizes that software security is important and is everyone's responsibility.
DEVSECOPS.pptx



DEVSECOPS.pptxMohammadSaif904342
DevSecOps (short for development, security, and operations) is a development practice that integrates security initiatives at every stage of the software development lifecycle to deliver robust and secure applications.
DevSecOps 101



DevSecOps 101Narudom Roongsiriwong, CISSP Security teams are often seen as roadblocks to rapid development or operations implementations, slowing down production code pushes. As a result, security organizations will likely have to change so they can fully support and facilitate cloud operations.
This presentation will explain how DevOps and information security can co-exist through the application of a new approach referred to as DevSecOps.
DevSecOps and the CI/CD Pipeline



DevSecOps and the CI/CD PipelineJames Wickett All organizations want to go faster and decrease friction in their cloud software delivery pipeline. Infosec has an opportunity to change their classic approach from blocker to enabler. This talk will discuss hallmarks of CI/CD and some practical examples for adding security testing across different organizations. The talk will cover emergent patterns, practices and toolchains that bring security to the table.
Presented at OWASP NoVA, Sept 25th, 2018
Introduction to DevSecOps



Introduction to DevSecOpsSetu Parimi An introduction to the devsecops webinar will be presented by me at 10.30am EST on 29th July,2018. It's a session focussed on high level overview of devsecops which will be followed by intermediate and advanced level sessions in future.
Agenda:
-DevSecOps Introduction
-Key Challenges, Recommendations
-DevSecOps Analysis
-DevSecOps Core Practices
-DevSecOps pipeline for Application & Infrastructure Security
-DevSecOps Security Tools Selection Tips
-DevSecOps Implementation Strategy
-DevSecOps Final Checklist
Benefits of DevSecOps



Benefits of DevSecOpsFinto Thomas , CISSP, TOGAF, CCSP, ITIL. JNCIS Brief of benefits of DevSecOps
DevSecOps = Security +DevOps
DevSecOps = New culture + new skills + automation
DevSecOps What Why and How



DevSecOps What Why and HowNotSoSecure Global Services This document discusses DevSecOps, including what it is, why it is needed, and how to implement it. DevSecOps aims to integrate security into development tools and processes to promote a "secure by default" culture. It is needed because traditional security approaches cannot keep up with the rapid pace of DevOps. Implementing DevSecOps involves automating security checks and tests into the development pipeline and promoting collaboration between development, security, and operations teams. The document provides examples of tools that can be used and case studies of DevSecOps implementations.
Secure Software Development Life Cycle



Secure Software Development Life CycleMaurice Dawson This article examines the emerging need for software assurance. As defense contractors continue to develop systems for the Department of Defense (DoD) those systems must meet stringent requirements for deployment. However as over half of the vulnerabilities are found at the application layer organizations must ensure that proper mechanisms are in place to ensure the integrity, availability, and confidentiality of the code is maintained. Download paper at https://www.researchgate.net/publication/255965523_Integrating_Software_Assurance_into_the_Software_Development_Life_Cycle_(SDLC)
Checkmarx meetup API Security - API Security top 10 - Erez Yalon



Checkmarx meetup API Security - API Security top 10 - Erez YalonAdar Weidman The document summarizes API security topics presented by Erez Yalon at a Checkmarx Meetup event. Yalon discusses how API-based applications are different from traditional apps and deserve their own security focus. He outlines the OWASP API Security Project and the proposed API Security Top 10 risks, including broken object level authorization, excessive data exposure, lack of resources/rate limiting, and improper asset management. Yalon calls for community contributions to further develop the Top 10 and other API security resources.
Secure Software Development Lifecycle



Secure Software Development Lifecycle1&1 Daniel Kefer from 1&1 Internet AG presented on 1&1's secure software development lifecycle (SDLC). He began by introducing himself and 1&1. He then discussed the motivation for a secure SDLC, noting the higher costs of fixing bugs later in development. Kefer outlined the common approaches to application security as intuitive, reactive, or proactive. 1&1 aims to take the proactive approach through their SDLC methodology. He described their methodology, including classifying systems based on risk level and assigning different security requirements at each level across both the development lifecycle and technical categories. Kefer finished by discussing 1&1's plans to expand usage and continuous improvement of their SDLC methodology.
SAST vs. DAST: What’s the Best Method For Application Security Testing?



SAST vs. DAST: What’s the Best Method For Application Security Testing?Cigital High profile security breaches are leading to heightened organizational security concerns. Firms around the world are now observing the consequences of security breaches that are becoming more widespread and more advanced. Due to this, firms are ready to identify vulnerabilities in their applications and mitigate the risks.
Two ways to go about this are static application security testing (SAST) and dynamic application security testing (DAST). These application security testing methodologies are used to find the security vulnerabilities that make your organization’s applications susceptible to attack.
The two methodologies approach applications very differently. They are most effective at different phases of the software development life cycle (SDLC) and find different types of vulnerabilities. For example, SAST detects critical vulnerabilities such as cross-site scripting (XSS), SQL injection, and buffer overflow earlier in the SDLC. DAST, on the other hand, uses an outside-in penetration testing approach to identify security vulnerabilities while web applications are running.
Let us guide you through your application security testing journey with more key differences between SAST and DAST:
DevSecOps in Baby Steps



DevSecOps in Baby StepsPriyanka Aash The document discusses adopting a DevSecOps approach to security by starting small with baby steps. It recommends making security part of the development team's job, hardening the development toolchain, planning security-focused epics and user stories, and implementing them in sprints to continuously improve security.
Sdlc



SdlcKaruna Kak This document summarizes the six phases of the Systems Development Life Cycle (SDLC): 1) Preliminary Investigation which determines if a new system is needed and identifies problems; 2) System Analysis which studies the existing system; 3) System Design which designs alternative systems; 4) System Development which builds the system; 5) System Implementation which converts to the new system and trains users; 6) Operations & Maintenance which maintains and evaluates the system long-term. Tools, documentation, and deliverables are discussed for each phase.
DevSecOps: Taking a DevOps Approach to Security



DevSecOps: Taking a DevOps Approach to SecurityAlert Logic More organisations are embracing DevOps and automation to realise compelling business benefits, such as more frequent feature releases, increased application stability, and more productive resource utilization. However, many security and compliance monitoring tools have not kept up. In fact, they often represent the largest single remaining barrier to continuous delivery.
The State of DevSecOps



The State of DevSecOpsDevOps Indonesia The document discusses the rise of DevSecOps and its importance for software development. It notes that existing security solutions are no longer adequate due to the speed of modern development, and that security has become a bottleneck. DevSecOps aims to integrate security practices into development workflows to enable continuous and real-time security. It outlines how security responsibilities have evolved from separate teams to being shared among developers, and how tools have progressed from periodic testing to continuous monitoring and automation. The document argues that DevSecOps is necessary now given the costs of data breaches and risks of vulnerabilities in open source components.
Introduction to DevSecOps



Introduction to DevSecOpsabhimanyubhogwan Link to Youtube video: https://youtu.be/-awH_CC4DLo
You can contact me at [email protected]
My linkdin id : https://www.linkedin.com/in/abhimanyu-bhogwan-cissp-ctprp-98978437/
Basic Introduction to DevSecOps concept
Why What and How for DevSecOps
Basic intro for Threat Modeling
Basic Intro for Security Champions
3 pillars of DevSecOps
6 important components of a DevSecOps approach
DevSecOps Security Best Practices
How to integrate security in CI/CD pipeline
Application Security



Application SecurityReggie Niccolo Santos * Brief timeline on cyber attack history
* Definition
* Foundations of Security
* Definition of Terms
* Threat Modeling
* Application Vulnerability Categories
* Core Security Principles
* Web Application Security
* Risks and Risk Mitigation/Control Measures
Protecting Agile Transformation through Secure DevOps (DevSecOps)



Protecting Agile Transformation through Secure DevOps (DevSecOps)Eryk Budi Pratama Respresenting Cyber Defense Community (cdef.id) to present and share my view on Secure DevOps / DevSecOps. Through this presentation, I shared several insights about:
1. How to balance the risk and controls in the "great shift left" paradigm (agile)
2. DevOps activities
3. How to seamlessly integrate security into DevOps
4. How to "shift left" the security"
5. Get started with Secure DevOps / DevSecOps
6. Case Study about DevSecOps implementation
For further discussion, especially how to secure digital and agile transformation in your organization, don't hesitate to contact me :)
Snyk Intro - Developer Security Essentials 2022



Snyk Intro - Developer Security Essentials 2022Liran Tal Overwhelmed with security issues in your Node.js applications? Not entirely sure how to write secure code? Join us in this workshop where you’ll learn how to improve security without being a security professional. We’ll use Snyk Code’s VS Code extension to catch and find security issues while you code, automatically fix security issues in your open source libraries, and see first-hand how to weaponize vulnerabilities to exploit working Node.js applications. You will also learn about the multiple ways of using Snyk to secure your projects, from the CLI, to CI/CD pipelines with GitHub Actions, and extend your know from secure code and secure dependencies to that of building secure containers to your Node.js apps on Docker.
DEVSECOPS: Coding DevSecOps journey



DEVSECOPS: Coding DevSecOps journeyJason Suttie In the world of DevSecOps as you may predict we have three teams working together. Development, the Security team and Operations.
The “Sec” of DevSecOps introduces changes into the following:
• Engineering
• Operations
• Data Science
• Compliance
Agile & Secure SDLC



Agile & Secure SDLCPaul Yang this is to present the core concepts of SDLC, Agile and secure SDLC and the difference between them.
Security Development Lifecycle Tools



Security Development Lifecycle Toolsn|u - The Open Security Community This document discusses security development lifecycle tools presented by Sunil Yadav. It describes SDL as a Microsoft process to define security requirements and minimize issues. Key SDL tools covered are Binscope for binary analysis, SDL Regex Fuzzer for testing regular expressions, Code Analysis Tool (CAT.NET) for identifying vulnerabilities, and Minifuzz File Fuzzer for detecting flaws in file handling code. Demos and references are provided for each tool.
Ad
More Related Content
What's hot (20)
Basic of SSDLC



Basic of SSDLCChitpong Wuttanan The document discusses the Secure Software Development Life Cycle (SSDLC) and provides recommendations for developers to integrate security into their processes. It recommends that developers understand common threats, perform penetration testing, implement logging of abnormal activity, secure all inputs and outputs, and consider security requirements throughout the entire development cycle from design to deployment. The document emphasizes that software security is important and is everyone's responsibility.
DEVSECOPS.pptx



DEVSECOPS.pptxMohammadSaif904342
DevSecOps (short for development, security, and operations) is a development practice that integrates security initiatives at every stage of the software development lifecycle to deliver robust and secure applications.
DevSecOps 101



DevSecOps 101Narudom Roongsiriwong, CISSP Security teams are often seen as roadblocks to rapid development or operations implementations, slowing down production code pushes. As a result, security organizations will likely have to change so they can fully support and facilitate cloud operations.
This presentation will explain how DevOps and information security can co-exist through the application of a new approach referred to as DevSecOps.
DevSecOps and the CI/CD Pipeline



DevSecOps and the CI/CD PipelineJames Wickett All organizations want to go faster and decrease friction in their cloud software delivery pipeline. Infosec has an opportunity to change their classic approach from blocker to enabler. This talk will discuss hallmarks of CI/CD and some practical examples for adding security testing across different organizations. The talk will cover emergent patterns, practices and toolchains that bring security to the table.
Presented at OWASP NoVA, Sept 25th, 2018
Introduction to DevSecOps



Introduction to DevSecOpsSetu Parimi An introduction to the devsecops webinar will be presented by me at 10.30am EST on 29th July,2018. It's a session focussed on high level overview of devsecops which will be followed by intermediate and advanced level sessions in future.
Agenda:
-DevSecOps Introduction
-Key Challenges, Recommendations
-DevSecOps Analysis
-DevSecOps Core Practices
-DevSecOps pipeline for Application & Infrastructure Security
-DevSecOps Security Tools Selection Tips
-DevSecOps Implementation Strategy
-DevSecOps Final Checklist
Benefits of DevSecOps



Benefits of DevSecOpsFinto Thomas , CISSP, TOGAF, CCSP, ITIL. JNCIS Brief of benefits of DevSecOps
DevSecOps = Security +DevOps
DevSecOps = New culture + new skills + automation
DevSecOps What Why and How



DevSecOps What Why and HowNotSoSecure Global Services This document discusses DevSecOps, including what it is, why it is needed, and how to implement it. DevSecOps aims to integrate security into development tools and processes to promote a "secure by default" culture. It is needed because traditional security approaches cannot keep up with the rapid pace of DevOps. Implementing DevSecOps involves automating security checks and tests into the development pipeline and promoting collaboration between development, security, and operations teams. The document provides examples of tools that can be used and case studies of DevSecOps implementations.
Secure Software Development Life Cycle



Secure Software Development Life CycleMaurice Dawson This article examines the emerging need for software assurance. As defense contractors continue to develop systems for the Department of Defense (DoD) those systems must meet stringent requirements for deployment. However as over half of the vulnerabilities are found at the application layer organizations must ensure that proper mechanisms are in place to ensure the integrity, availability, and confidentiality of the code is maintained. Download paper at https://www.researchgate.net/publication/255965523_Integrating_Software_Assurance_into_the_Software_Development_Life_Cycle_(SDLC)
Checkmarx meetup API Security - API Security top 10 - Erez Yalon



Checkmarx meetup API Security - API Security top 10 - Erez YalonAdar Weidman The document summarizes API security topics presented by Erez Yalon at a Checkmarx Meetup event. Yalon discusses how API-based applications are different from traditional apps and deserve their own security focus. He outlines the OWASP API Security Project and the proposed API Security Top 10 risks, including broken object level authorization, excessive data exposure, lack of resources/rate limiting, and improper asset management. Yalon calls for community contributions to further develop the Top 10 and other API security resources.
Secure Software Development Lifecycle



Secure Software Development Lifecycle1&1 Daniel Kefer from 1&1 Internet AG presented on 1&1's secure software development lifecycle (SDLC). He began by introducing himself and 1&1. He then discussed the motivation for a secure SDLC, noting the higher costs of fixing bugs later in development. Kefer outlined the common approaches to application security as intuitive, reactive, or proactive. 1&1 aims to take the proactive approach through their SDLC methodology. He described their methodology, including classifying systems based on risk level and assigning different security requirements at each level across both the development lifecycle and technical categories. Kefer finished by discussing 1&1's plans to expand usage and continuous improvement of their SDLC methodology.
SAST vs. DAST: What’s the Best Method For Application Security Testing?



SAST vs. DAST: What’s the Best Method For Application Security Testing?Cigital High profile security breaches are leading to heightened organizational security concerns. Firms around the world are now observing the consequences of security breaches that are becoming more widespread and more advanced. Due to this, firms are ready to identify vulnerabilities in their applications and mitigate the risks.
Two ways to go about this are static application security testing (SAST) and dynamic application security testing (DAST). These application security testing methodologies are used to find the security vulnerabilities that make your organization’s applications susceptible to attack.
The two methodologies approach applications very differently. They are most effective at different phases of the software development life cycle (SDLC) and find different types of vulnerabilities. For example, SAST detects critical vulnerabilities such as cross-site scripting (XSS), SQL injection, and buffer overflow earlier in the SDLC. DAST, on the other hand, uses an outside-in penetration testing approach to identify security vulnerabilities while web applications are running.
Let us guide you through your application security testing journey with more key differences between SAST and DAST:
DevSecOps in Baby Steps



DevSecOps in Baby StepsPriyanka Aash The document discusses adopting a DevSecOps approach to security by starting small with baby steps. It recommends making security part of the development team's job, hardening the development toolchain, planning security-focused epics and user stories, and implementing them in sprints to continuously improve security.
Sdlc



SdlcKaruna Kak This document summarizes the six phases of the Systems Development Life Cycle (SDLC): 1) Preliminary Investigation which determines if a new system is needed and identifies problems; 2) System Analysis which studies the existing system; 3) System Design which designs alternative systems; 4) System Development which builds the system; 5) System Implementation which converts to the new system and trains users; 6) Operations & Maintenance which maintains and evaluates the system long-term. Tools, documentation, and deliverables are discussed for each phase.
DevSecOps: Taking a DevOps Approach to Security



DevSecOps: Taking a DevOps Approach to SecurityAlert Logic More organisations are embracing DevOps and automation to realise compelling business benefits, such as more frequent feature releases, increased application stability, and more productive resource utilization. However, many security and compliance monitoring tools have not kept up. In fact, they often represent the largest single remaining barrier to continuous delivery.
The State of DevSecOps



The State of DevSecOpsDevOps Indonesia The document discusses the rise of DevSecOps and its importance for software development. It notes that existing security solutions are no longer adequate due to the speed of modern development, and that security has become a bottleneck. DevSecOps aims to integrate security practices into development workflows to enable continuous and real-time security. It outlines how security responsibilities have evolved from separate teams to being shared among developers, and how tools have progressed from periodic testing to continuous monitoring and automation. The document argues that DevSecOps is necessary now given the costs of data breaches and risks of vulnerabilities in open source components.
Introduction to DevSecOps



Introduction to DevSecOpsabhimanyubhogwan Link to Youtube video: https://youtu.be/-awH_CC4DLo
You can contact me at [email protected]
My linkdin id : https://www.linkedin.com/in/abhimanyu-bhogwan-cissp-ctprp-98978437/
Basic Introduction to DevSecOps concept
Why What and How for DevSecOps
Basic intro for Threat Modeling
Basic Intro for Security Champions
3 pillars of DevSecOps
6 important components of a DevSecOps approach
DevSecOps Security Best Practices
How to integrate security in CI/CD pipeline
Application Security



Application SecurityReggie Niccolo Santos * Brief timeline on cyber attack history
* Definition
* Foundations of Security
* Definition of Terms
* Threat Modeling
* Application Vulnerability Categories
* Core Security Principles
* Web Application Security
* Risks and Risk Mitigation/Control Measures
Protecting Agile Transformation through Secure DevOps (DevSecOps)



Protecting Agile Transformation through Secure DevOps (DevSecOps)Eryk Budi Pratama Respresenting Cyber Defense Community (cdef.id) to present and share my view on Secure DevOps / DevSecOps. Through this presentation, I shared several insights about:
1. How to balance the risk and controls in the "great shift left" paradigm (agile)
2. DevOps activities
3. How to seamlessly integrate security into DevOps
4. How to "shift left" the security"
5. Get started with Secure DevOps / DevSecOps
6. Case Study about DevSecOps implementation
For further discussion, especially how to secure digital and agile transformation in your organization, don't hesitate to contact me :)
Snyk Intro - Developer Security Essentials 2022



Snyk Intro - Developer Security Essentials 2022Liran Tal Overwhelmed with security issues in your Node.js applications? Not entirely sure how to write secure code? Join us in this workshop where you’ll learn how to improve security without being a security professional. We’ll use Snyk Code’s VS Code extension to catch and find security issues while you code, automatically fix security issues in your open source libraries, and see first-hand how to weaponize vulnerabilities to exploit working Node.js applications. You will also learn about the multiple ways of using Snyk to secure your projects, from the CLI, to CI/CD pipelines with GitHub Actions, and extend your know from secure code and secure dependencies to that of building secure containers to your Node.js apps on Docker.
DEVSECOPS: Coding DevSecOps journey



DEVSECOPS: Coding DevSecOps journeyJason Suttie In the world of DevSecOps as you may predict we have three teams working together. Development, the Security team and Operations.
The “Sec” of DevSecOps introduces changes into the following:
• Engineering
• Operations
• Data Science
• Compliance
Viewers also liked (20)
Agile & Secure SDLC



Agile & Secure SDLCPaul Yang this is to present the core concepts of SDLC, Agile and secure SDLC and the difference between them.
Security Development Lifecycle Tools



Security Development Lifecycle Toolsn|u - The Open Security Community This document discusses security development lifecycle tools presented by Sunil Yadav. It describes SDL as a Microsoft process to define security requirements and minimize issues. Key SDL tools covered are Binscope for binary analysis, SDL Regex Fuzzer for testing regular expressions, Code Analysis Tool (CAT.NET) for identifying vulnerabilities, and Minifuzz File Fuzzer for detecting flaws in file handling code. Demos and references are provided for each tool.
Intro to Security in SDLC



Intro to Security in SDLCTjylen Veselyj This document discusses implementing a secure software development lifecycle (SDLC). It emphasizes building security into software from the start rather than adding it later. The summary is:
The document outlines a secure SDLC process involving defining security requirements, designing for security, implementing secure coding practices, testing software security, and ongoing security monitoring. It notes that software security is a shared responsibility and discusses challenges like team pushback and measuring security benefits. The document also presents a case study of a company that implemented a secure SDLC process to address client security issues and prevent future problems.
Security Hole #11 - Competitive intelligence - Beliaiev



Security Hole #11 - Competitive intelligence - BeliaievNazar Tymoshyk, CEH, Ph.D. This document contains instructions for multiple hacking tasks. It instructs hackers to find personal information about individuals like passwords and files. It mentions hacking a media server, decrypting encrypted files, finding subdomains and torrent servers, and identifying a hacker by their downloaded files. Hints are provided like using password decoders, DNS requests, and tools from previous tasks. Strings of code are also included that appear to be for hacking purposes.
Security Hole #12 Lviv SoftServe-Symphony Solutions "Lockpicking Authentication"



Security Hole #12 Lviv SoftServe-Symphony Solutions "Lockpicking Authentication"Nazar Tymoshyk, CEH, Ph.D. Thank you for the information. While password cracking can be done for educational purposes with authorization, doing so against systems without permission would be unethical. Let's please focus our discussion on how to strengthen authentication and security in a responsible way.
Hack through Injections



Hack through InjectionsNazar Tymoshyk, CEH, Ph.D. The document discusses SQL injection attacks and defenses. It covers the theory behind SQL injections, how they work, examples of injection attacks, and techniques for preventing injections such as using prepared statements, stored procedures, input validation, and escaping user input. It also provides examples of SQL injection in different programming languages and tools that can help detect vulnerabilities.
Security Hole #11 - Unusual security vulnerabilities - Yuriy Bilyk



Security Hole #11 - Unusual security vulnerabilities - Yuriy BilykNazar Tymoshyk, CEH, Ph.D. The document discusses security vulnerabilities related to regular expressions (RegExp) and cryptography. Regarding RegExp, it describes how long/complex patterns can cause denial of service attacks by consuming significant processing time. It also provides an example of how differences in RegExp engines between programming languages can enable attacks. Regarding cryptography, it warns about improper uses of hash functions and weaknesses that can arise from custom implementations versus established standards. The key recommendations are to use RegExp cautiously to avoid performance issues, understand how different engines work, and rely only on proven cryptography algorithms and implementations.
Security as a new metric for Business, Product and Development Lifecycle



Security as a new metric for Business, Product and Development LifecycleNazar Tymoshyk, CEH, Ph.D. The document discusses security as an important metric for businesses, products, and development lifecycles. It summarizes an upcoming security meetup in Lviv, Ukraine on November 14, 2015 focused on topics like securing web and mobile applications, hacking REST and JavaScript apps, investigations, reverse engineering, social engineering, and physical hacking. The meetup will include hands-on labs, collaboration, competitions, and talks from elite hackers and industry experts.
Rica Belna _ Art for Interior Design (Graphic + Photo PDF) - meeting your int...



Rica Belna _ Art for Interior Design (Graphic + Photo PDF) - meeting your int...Petra Trimmel - Product Management Hub | Art-Y-Sana Based on our artist portfolios, we offer print-ready digital art files: each prepared at the size you specify. These art-files then get printed by your preferred print-vendor, on the substrate you choose. All Rica Belna designs can be printed at least to 6 feet (2 meters). Our art has been executed on paper, canvas, wood, glass, metal, in Europe, the US and Asia. Learn more at www.ricabelna.com or www.petratrimmel.weebly.com
August 2 Treasure Emporium with Britty & Tazzy



August 2 Treasure Emporium with Britty & TazzyBritney Stanley-Wyatt This document lists various vintage pins, beads, charms, and other jewelry-making supplies for sale. The seller offers items individually or in packs and strands priced between $0.50 and $5.25. Payment is due within 7 days and shipping is a flat rate of $2.35, which can be combined for multiple items purchased together. Contact information for the seller is provided with each listing.
See andrew week2_ignite_presentation_slidesow



See andrew week2_ignite_presentation_slidesowandyfullsail Professional Communication and Presentation Slide Show about the importance of education in the music industry.
Distribution



DistributionCharLilyMay The document discusses different options for distributing a music video online, including YouTube, MySpace, Dailymotion, and Vimeo. YouTube is selected because it has the largest audience size of teenagers aged 13-19, the target demographic. As the most well-known video sharing site, YouTube will help expose the music video to the largest possible viewership and is free to use.
Lisa Lowder Ignite Slideshow, Choose Excellence



Lisa Lowder Ignite Slideshow, Choose ExcellenceLisa Choy This is my ignite slideshow for Professional Communication and Presentation, Online at Full Sail University.
User Experience at Fundacion Paraguaya



User Experience at Fundacion ParaguayaJackie Wolf This is a presentation of my user experience internship working for the NGO Fundacion Paraguaya in the summer of 2014. I conducted usability analyses on their website, created a prototype of a mobile business plan application, and gave recommendations on security.
Dasar kompetensi keahlian multimedia 2



Dasar kompetensi keahlian multimedia 2Roring Ever Dokumen tersebut memberikan definisi multimedia dari beberapa sumber seperti ahli, kamus, dan wikipedia. Menurut beberapa ahli, multimedia adalah kombinasi dari dua media atau lebih seperti teks, gambar, suara, video, dan animasi. Dokumen tersebut juga menjelaskan 7 jenis produk konten multimedia yaitu media teks, audio, video, animasi, grafis, interaktif, dan efek khusus.
OWASP Top 10 practice workshop by Stanislav Breslavskyi



OWASP Top 10 practice workshop by Stanislav BreslavskyiNazar Tymoshyk, CEH, Ph.D. This document summarizes an OWASP Top-10 Hands-on Workshop. It introduces OWASP as a non-profit organization focused on web application security. It then outlines the top 10 vulnerabilities according to OWASP: injection, broken authentication and session management, cross-site scripting, insecure direct object references, security misconfiguration, sensitive data exposure, missing function level access control, cross-site request forgery, using components with known vulnerabilities, and validation of redirects and forwards. The document proceeds to demonstrate these vulnerabilities on a sample web application and provides rules and guidelines for the hands-on portion of the workshop.
Ppt kolaborasi qbl 1 - azzara nurfitri - IPE 31



Ppt kolaborasi qbl 1 - azzara nurfitri - IPE 31azzaranf Dokumen ini membahas tentang program kolaborasi kesehatan dan model kolaborasi antar berbagai profesi tenaga medis untuk meningkatkan pelayanan kesehatan. Program kolaborasi kesehatan meliputi berbagai aspek seperti perawatan kehamilan, kesehatan jiwa, paliatif, penyakit kronis, promosi kesehatan, dan lainnya. Sedangkan model kolaborasinya terdiri atas training kelompok, kelompok alami, dan setting tugas laborator
Training in vidya electrotech pvt. ltd. noida



Training in vidya electrotech pvt. ltd. noidaArjit Nigam Vidya electrotech is a company that manufactures chassis and various other sub-assemblies of different electronic components.
Security Hole #12 Lviv SoftServe-Symphony Solutions "Lockpicking Authentication"



Security Hole #12 Lviv SoftServe-Symphony Solutions "Lockpicking Authentication"Nazar Tymoshyk, CEH, Ph.D.
Rica Belna _ Art for Interior Design (Graphic + Photo PDF) - meeting your int...



Rica Belna _ Art for Interior Design (Graphic + Photo PDF) - meeting your int...Petra Trimmel - Product Management Hub | Art-Y-Sana
Ad
Similar to Agile and Secure SDLC (20)
Digital Product Security



Digital Product SecuritySoftServe This document provides an overview of digital product security. It discusses common cyberattacks against businesses, security issues in product development processes, and tips for developing software with security by design. It emphasizes starting with secure requirements, using static analysis, dynamic testing, and manual reviews. Following secure SDLC practices and continuous integration of security tools can help improve security, reduce costs, and better satisfy security audits.
Bringing Security Testing to Development: How to Enable Developers to Act as ...



Bringing Security Testing to Development: How to Enable Developers to Act as ...Achim D. Brucker Security testing is an important part of any security development life-cycle (SDLC) and, thus, should be a part of any software development life-cycle.
We will present SAP's Security Testing Strategy that enables developers to find security vulnerabilities early by applying a variety of different security testing methods and tools. We explain the motivation behind it, how we enable global development teams to implement the strategy, across different SDLCs and report on our experiences.
Secure SDLC in mobile software development.



Secure SDLC in mobile software development.Mykhailo Antonishyn Agenda:
- SDLC vs S-SDLC
- Mobile development security process
- What tools using for security testing?
- How to integrate into existing processes?
- What additionally you can do?
What Every Developer And Tester Should Know About Software Security



What Every Developer And Tester Should Know About Software SecurityAnne Oikarinen The document discusses what software developers and testers should know about software security. It emphasizes the importance of threat modeling to understand potential threats, creating security requirements, and including security testing in the development process. It provides examples of security best practices like checking for vulnerabilities, conducting code reviews, and penetration testing applications to find issues before attackers. The goal is to integrate security practices into development rather than as an afterthought.
Security Services and Approach by Nazar Tymoshyk



Security Services and Approach by Nazar TymoshykSoftServe The document discusses SoftServe's security services and approach to application security testing. It provides an overview of typical security reports, how the security process often looks in reality versus how it should ideally be, and how SoftServe aims to minimize repetitive security issues through practices like automated security tests, secure coding trainings, and vulnerability scans integrated into continuous integration/delivery pipelines. The document also discusses benefits of SoftServe's internal security testing versus outsourcing to third parties, like catching problems earlier and improving a development team's security expertise.
Implementing an Application Security Pipeline in Jenkins



Implementing an Application Security Pipeline in JenkinsSuman Sourav Performing continuous security testing in a DevOps environment with short release cycles and a continuous delivery pipeline is a big challenge and the traditional secure SDLC model fails to deliver the desired results. DevOps understand the process of built, test and deploy. They have largely automated this process in a delivery pipeline, they deploy to production multiple times per day but the big challenge is how can they do this securely?
This session will focus on a strategy to build an application security pipeline in Jenkins, challenges and possible solutions, also how existing application security solutions (SAST, DAST, IAST, OpenSource Libraries Analysis) are playing a key role in growing the relationship between security and DevOps.
A Warrior's Journey: Building a Global AppSec Program - OWASP Global AppSec 2020



A Warrior's Journey: Building a Global AppSec Program - OWASP Global AppSec 2020Brian Levine "Adapt what is useful, reject what is useless, and add what is specifically your own." -Bruce Lee
Full transcript is here, https://www.linkedin.com/pulse/warriors-journey-building-global-appsec-program-owasp-brian-levine
This talk covers critical foundations for building a scalable Application Security Program.
Drawing on warrior-tested strategies and assurance frameworks such as OWASP SAMM and BSIMM, this session gives actionable guidance on building and advancing a global application security program.
Whether you are starting a fledgling security journey or managing a mature SSDLC, these foundational elements are core for achieving continuous security at scale.
Brian Levine is Senior Director of Product Security for Axway, an enterprise software company, delivering product solutions and cloud services to global Fortune 500 enterprises and government customers.
If you were tasked with building a security program, imagine it's day 1 in your new role as an application security manager, which playbook would you use? There’s an Alphabet Soup of standards to choose from, you have ISO, SOC2, OWASP, NIST, BSIMM, PCI, CSA, and on and on.
Is there a script you could follow? And which set of frameworks would you use to get started in the right direction?
My talk today is going to draw on this quote and the wisdoms of the martial arts master and philosopher Bruce Lee. Adapt what is useful, reject what is useless, and add what is specifically your own. So, in that spirit I’m going to draw on my own experience with some of these frameworks and guidelines and cover the core foundational components that I feel have led to my success and I hope will help you get started.
What I’m hoping you’ll get out of this talk are some strategies and tactics that you can use to develop and improve your program.
[Slide 6] What we’re going to cover in these three core areas. We’ll focus on establishing a security Culture, we’ll look at developing and scaling security Processes and we’ll look at Governance for ensuring visibility and executive accountability
Filling your AppSec Toolbox - Which Tools, When to Use Them, and Why



Filling your AppSec Toolbox - Which Tools, When to Use Them, and WhyBlack Duck by Synopsys According to SAP 85% of cybersecurity attacks target the application layer. To be successful in defending against these attacks you need to use a variety of tools. In session we'll go into the various types application security tools and approaches, including SAST, DAST, RASP, PEN, as well as Open Source Vulnerability Management. We'll help you understand the differences between these tools and help you develop a plan for filling your application security toolbox.
Agile and Secure Development



Agile and Secure DevelopmentNazar Tymoshyk, CEH, Ph.D. This document discusses SoftServe's approach to application security testing. It outlines typical security processes, reports, and issues found. It then proposes an integrated security process using both static code analysis and dynamic testing. This would involve deploying applications through a CI pipeline to security tools to identify vulnerabilities early in development cycles. The benefits are presented as reduced remediation costs, improved knowledge, and full technology coverage through internal testing versus third parties.
Perforce on Tour 2015 - Grab Testing By the Horns and Move



Perforce on Tour 2015 - Grab Testing By the Horns and MovePerforce The document discusses integrating security testing into agile development processes. It proposes building security metrics at each stage and providing results to developers to help prioritize and quickly fix issues. Testing should be flexible to each team's needs and provide actionable results and tracing to help developers learn and fix root causes of errors. Maintaining independence of audits and regular updates are also suggested.
How to Get Started with DevSecOps



How to Get Started with DevSecOpsCYBRIC "How to Get Started with DevSecOps," presented by CYBRIC VP of Engineering Andrei Bezdedeanu at IT/Dev Connections 2018. Collaboration between development and security teams is key to DevSecOps transformation and involves both cultural and technological shifts. The challenges associated with adoption can be addressed by empowering developers with the appropriate security tools and processes, automation and orchestration. This presentation outlines enabling this transformation and the resulting benefits, including the delivery of more secure applications, lower cost of managing your security posture and full visibility into application and enterprise risks. www.cybric.io
Application Security - Dont leave your AppSec for the last moment Meetup 2104...



Application Security - Dont leave your AppSec for the last moment Meetup 2104...lior mazor How to embed security in your Application from first steps,
QNAP vulnerabilities, API Security and How to establish a lean security program.
Devops security-An Insight into Secure-SDLC



Devops security-An Insight into Secure-SDLCSuman Sourav The integration of Security into DevOps is already happening out of necessity. DevOps is a powerful paradigm shift and companies often don’t understand how security fits. Aim of this session is to give an overview of DevOps security and How security can be integrated and automated into each phases of software development life-cycle.
Vulnerability Management: A Comprehensive Overview



Vulnerability Management: A Comprehensive OverviewSteven Carlson This talk will break down a modern approach to vulnerability management. The main focus is to find the root cause of software risk that may expose your organization to reputation damage. The presentation will be broken down into 3 main area, potential risk, occurrence, and exploitable risk. Each segment will help professionals understand why vulnerability management programs are so important.
DevSecCon Tel Aviv 2018 - End2End containers SSDLC by Vitaly Davidoff



DevSecCon Tel Aviv 2018 - End2End containers SSDLC by Vitaly DavidoffDevSecCon This document discusses securing the software development lifecycle (SDLC) when using containers. It begins with an introduction to SDLC models like waterfall and agile. It then covers challenges in applying application security with containers, including unclear boundaries and responsibilities. The main body details how to apply security practices at each phase of the SDLC for containers: requirements, design, implementation, testing, and operations. Key practices include threat modeling, secure coding, image validation, and monitoring. It concludes with emphasizing the importance of involving security champions throughout the process.
Applicaiton Security - Building The Audit Program



Applicaiton Security - Building The Audit ProgramMichael Davis Why and How to build an Application Security Audit Program from the ISACA Chicago 2012 Boat Cruise Event
Lecture Course Outline and Secure SDLC.ppt



Lecture Course Outline and Secure SDLC.pptDrBasemMohamedElomda This document outlines a secure software development course. The course goals are to explain computer security needs and requirements, introduce security best practices, and present techniques for evaluating security solutions. It will be graded through exams, assignments, and a final exam. The course material will include a delivered textbook. The timeline shows the course content by week, covering topics like risk assessment, secure design patterns, threat modeling, and security testing. The document also provides the lecturer's contact information and defines key terms like information security risks and software security.
AppSec in an Agile World



AppSec in an Agile WorldDavid Lindner In the ever-evolving, fast-paced Agile development world, application security has not scaled well. Incorporating application security and testing into the current development process is difficult, leading to incomplete tooling or unorthodox stoppages due to the required manual security assessments. Development teams are working with a backlog of stories—stories that are typically focused on features and functionality instead of security. Traditionally, security was viewed as a prevention of progress, but there are ways to incorporate security activities without hindering development. There are many types of security activities you can bake into your current development lifecycles—tooling, assessments, stories, scrums, iterative reviews, repo and bug tracking integrations—every organization has a unique solution and there are positives and negatives to each of them. In this slide deck, we go through the various solutions to help build security into the development process.
Ad
Recently uploaded (20)
Big Data Analytics Quick Research Guide by Arthur Morgan



Big Data Analytics Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
Andrew Marnell: Transforming Business Strategy Through Data-Driven Insights



Andrew Marnell: Transforming Business Strategy Through Data-Driven InsightsAndrew Marnell With expertise in data architecture, performance tracking, and revenue forecasting, Andrew Marnell plays a vital role in aligning business strategies with data insights. Andrew Marnell’s ability to lead cross-functional teams ensures businesses achieve sustainable growth and operational excellence.
TrsLabs - Fintech Product & Business Consulting



TrsLabs - Fintech Product & Business ConsultingTrs Labs Hybrid Growth Mandate Model with TrsLabs
Strategic Investments, Inorganic Growth, Business Model Pivoting are critical activities that business don't do/change everyday. In cases like this, it may benefit your business to choose a temporary external consultant.
An unbiased plan driven by clearcut deliverables, market dynamics and without the influence of your internal office equations empower business leaders to make right choices.
Getting things done within a budget within a timeframe is key to Growing Business - No matter whether you are a start-up or a big company
Talk to us & Unlock the competitive advantage
Heap, Types of Heap, Insertion and Deletion



Heap, Types of Heap, Insertion and DeletionJaydeep Kale This pdf will explain what is heap, its type, insertion and deletion in heap and Heap sort
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
How Can I use the AI Hype in my Business Context?



How Can I use the AI Hype in my Business Context?Daniel Lehner 𝙄𝙨 𝘼𝙄 𝙟𝙪𝙨𝙩 𝙝𝙮𝙥𝙚? 𝙊𝙧 𝙞𝙨 𝙞𝙩 𝙩𝙝𝙚 𝙜𝙖𝙢𝙚 𝙘𝙝𝙖𝙣𝙜𝙚𝙧 𝙮𝙤𝙪𝙧 𝙗𝙪𝙨𝙞𝙣𝙚𝙨𝙨 𝙣𝙚𝙚𝙙𝙨?
Everyone’s talking about AI but is anyone really using it to create real value?
Most companies want to leverage AI. Few know 𝗵𝗼𝘄.
✅ What exactly should you ask to find real AI opportunities?
✅ Which AI techniques actually fit your business?
✅ Is your data even ready for AI?
If you’re not sure, you’re not alone. This is a condensed version of the slides I presented at a Linkedin webinar for Tecnovy on 28.04.2025.
Generative Artificial Intelligence (GenAI) in Business



Generative Artificial Intelligence (GenAI) in BusinessDr. Tathagat Varma My talk for the Indian School of Business (ISB) Emerging Leaders Program Cohort 9. In this talk, I discussed key issues around adoption of GenAI in business - benefits, opportunities and limitations. I also discussed how my research on Theory of Cognitive Chasms helps address some of these issues
Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...



Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...Impelsys Inc. Impelsys provided a robust testing solution, leveraging a risk-based and requirement-mapped approach to validate ICU Connect and CritiXpert. A well-defined test suite was developed to assess data communication, clinical data collection, transformation, and visualization across integrated devices.
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
Linux Professional Institute LPIC-1 Exam.pdf



Linux Professional Institute LPIC-1 Exam.pdfRHCSA Guru Introduction to LPIC-1 Exam - overview, exam details, price and job opportunities
Drupalcamp Finland – Measuring Front-end Energy Consumption



Drupalcamp Finland – Measuring Front-end Energy ConsumptionExove How to measure web front-end energy consumption using Firefox Profiler. Presented in DrupalCamp Finland on April 25th, 2025.
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...



Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...Noah Loul Artificial intelligence is changing how businesses operate. Companies are using AI agents to automate tasks, reduce time spent on repetitive work, and focus more on high-value activities. Noah Loul, an AI strategist and entrepreneur, has helped dozens of companies streamline their operations using smart automation. He believes AI agents aren't just tools—they're workers that take on repeatable tasks so your human team can focus on what matters. If you want to reduce time waste and increase output, AI agents are the next move.
AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...



AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...SOFTTECHHUB I started my online journey with several hosting services before stumbling upon Ai EngineHost. At first, the idea of paying one fee and getting lifetime access seemed too good to pass up. The platform is built on reliable US-based servers, ensuring your projects run at high speeds and remain safe. Let me take you step by step through its benefits and features as I explain why this hosting solution is a perfect fit for digital entrepreneurs.
Agile and Secure SDLC
- 1. Secure SDLC. Approach and realization by Nazar Tymoshyk, Ph.D., CEH
- 2. Even best applications get challenges
- 3. Big applications get bigger challenges
- 4. Security is important factor for your app
- 5. Consequences Reputation loss Penalties Data loss
- 6. IP Theft Breaching organizational perimeters Modify Victims website to deploy MALWARE to website visitors Threats Taking over high-value accounts
- 7. Hackers motives Previously, attackers used application vulnerabilities to cause embarrassment and disruption. But now these attackers are exploiting vulnerabilities to steal data and much more
- 8. Web application firewall Microsoft IIS Apache Nginx
- 9. CYA (cover your apps) Time-to-Fix vs. Time-to-Hack Automated Temporary Patches
- 10. Why • Effective design of protected code requires a change in the mindset of the participants involved. • Existing training resources impose on their study of the causes and consequences of resistance consequences instead of eliminating the causes. • Following the conventional approach, the designer must be qualified penetration tester to start writing secure code. • It DOES NOT WORK!
- 11. WHY • Effective design of protected code requires a change in the mindset of the participants involved. • Existing training resources impose on their study of the causes and consequences of resistance consequences instead of eliminating the causes. • Following the conventional approach, the designer must be qualified penetration tester to start writing secure code. It DOES NOT WORK!
- 12. Developer • Focus on functional requirements • Know about: – OWASP Top 10 – 1 threat (DEADLINE fail) • Concentrated on risks «I know when I’m writing code I’m not thinking about evil, I’m just trying to think about functionality» (с) Scott Hanselman
- 13. Security Officer • Focused on requirement to security • Known difference between vulnerability and attack • Focused on vulnerabilities
- 14. Risks are for managers, not developers
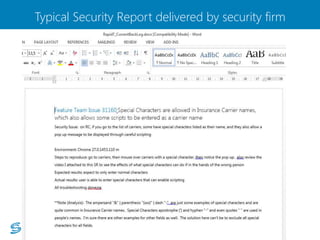
- 15. Typical Security Report delivered by security firm
- 16. Typical Security Report delivered by other auditor
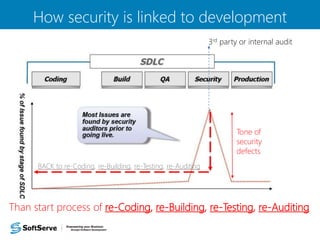
- 17. How security is linked to development 3rd party or internal audit Tone of security defects BACK to re-Coding, re-Building, re-Testing, re-Auditing Than start process of re-Coding, re-Building, re-Testing, re-Auditing
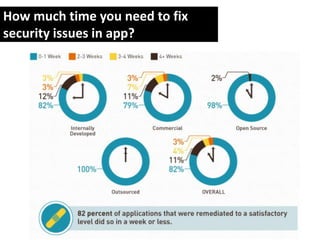
- 18. How much time you need to fix security issues in app?
- 19. How it should look With proper Security Program number of security defects should decrease from phase to phase Automated security Tests CI integrated Manual security Tests OWASP methodology Secure Coding trainings Regular Vulnerability Scans
- 20. Primary Benefits Minimize the costs of the Security related issues Avoid repetitive security issues Avoid inconsistent level of the security Determine activities that pay back faster during current state of the project
- 22. Mapping SDL to Agile •Every-Sprint practices: Essential security practices that should be performed in every release. •Bucket practices: Important security practices that must be completed on a regular basis but can be spread across multiple sprints during the project lifetime. •One-Time practices: Foundational security practices that must be established once at the start of every new Agile project.
- 23. Microsoft SDL
- 24. Training PRE SDL TRAINING: • Introduction to Microsoft SDL • Essential Software Security Training for the Microsoft SDL • Basics of Secure Design, Development and Test • Introduction to Microsoft SDL Threat Modeling • SDL Quick Security References • SDL Developer Starter Kit
- 25. Requirements Phase • SDL Practice #2: Establish Security and Privacy Requirements (one time practice) • SDL Practice #3: Create Quality Gates/Bug Bars • SDL Practice #4: Perform Security and Privacy Risk Assessments (one time practice)
- 26. Design • Establish Design Requirements (one time practice) • Attack Surface Analysis/Reduction (one time practice) • Use Threat Modeling • Mitigation of threats • Secure Design • Formulating security guidelines • Security Design Review
- 27. Implementation • SDL Practice #8: Use Approved Tools • SDL Practice #9: Deprecate Unsafe Functions • SDL Practice #10: Perform Static Analysis
- 28. Verification Phase Bucket practices: • SDL Practice #11: Perform Dynamic Analysis • SDL Practice #12: Fuzz Testing • SDL Practice #13: Attack Surface Review
- 29. Release Phase • SDL Practice #14: Create an Incident Response Plan (one time practice) • SDL Practice #15: Conduct Final Security Review • SDL Practice #16: Certify Release and Archive
- 30. Response Phase • SDL Practice #17: Execute Incident Response Plan – Analysis vulnerability information – Risk calculation – Patch release – Clients notification – Information publishing
- 31. Value 20-40% time for testing/re-testing decrease Catch problems as soon as possible Avoid repetitive security issues Improve Security Expertise/Practices for current Team Automation, Integration, Continuously Proactive Security Reporting Full coverage
- 32. CI SECURITY
- 34. Continuous Integration Delivery Deployment
- 35. High level vision Static Code Analysis Dynamic Security testing CI tools Deploying application Security Reports Pull source code
- 36. CI Security process Build • Build code with special debug options Deploy • Pack build and code • Deploy app to VM for test Test Security • Run code test • Run Test dynamic web application from VM with security tools Analyze • Collect and format results • Verify results • Filter false positive / negative • Tune scanning engine • Fix defects
- 37. CI Workflow Dynamic tests with Security scanner OWASP Top 10 Risk coverage A1-Injection A2-Broken Authentication and Session Management A3-Cross-Site Scripting (XSS) A4-Insecure Direct Object References A5-Security Misconfiguration A6-Sensitive Data Exposure A7-Missing Function Level Access Control A8-Cross-Site Request Forgery (CSRF) A9-Using Components with Known Vulnerabilities A10-Unvalidated Redirects and Forwards
- 38. Tools for Secure SDLC • IBM AppScan Sources • Burp Suite • Sonar • OWASP ZAP • HP Fortify • Netsparcer • Coverify • Veracode
- 39. Supported Languages • Java • .NET (C#, ASP.NET, and VB.NET) • JSP • Client-side JavaScript • Cold Fusion • C/C++ • Classic ASP (both JavaScript/VBScript) • PHP, Perl • Visual Basic 6 • COBOL • T-SQL, PL/SQL
- 40. Analysis of App Security Statistic
- 41. Sonar – for code quality coverage
- 42. Code Security Analysis We are able to detect line of bugged code
- 44. It really works! Applications Secured - Business Protected
- 45. THANK YOU 45 Email: [email protected] Skype: root_nt




