Algorithm analysis basics - Seven Functions/Big-Oh/Omega/Theta
Download as ppt, pdf4 likes2,072 views
Discuss seven functions, Analysis of algorithms- Experimental Studies/Primitive operations/Asymptotic notation- Big Oh/Big-Omega/Big-Theta (Download is recommended to make the animations work)
1 of 31
Downloaded 26 times
















![Example
Algorithm arrayMax(A, n)
# operations
currentMax ← A[0] 2
for i ← 1 to n − 1 do 2n
if A[i] > currentMax then 2(n − 1)
currentMax ← A[i] 2(n − 1)
{ increment counter i } 2(n − 1)
return currentMax 1
Total 8n − 2](https://image.slidesharecdn.com/algorithmanalysisbasics-170415031048/85/Algorithm-analysis-basics-Seven-Functions-Big-Oh-Omega-Theta-19-320.jpg)












Ad
Recommended
Type Checking(Compiler Design) #ShareThisIfYouLike



Type Checking(Compiler Design) #ShareThisIfYouLikeUnited International University The purpose of types:
To define what the program should do.
e.g. read an array of integers and return a double
To guarantee that the program is meaningful.
that it does not add a string to an integer
that variables are declared before they are used
To document the programmer's intentions.
better than comments, which are not checked by the compiler
To optimize the use of hardware.
reserve the minimal amount of memory, but not more
use the most appropriate machine instructions.
Rule Based Architecture System



Rule Based Architecture SystemFirdaus Adib Rule-based systems are used as a way to store and manipulate knowledge to interpret information in a useful way. Often used in artificial intelligence applications and research.
BackTracking Algorithm: Technique and Examples



BackTracking Algorithm: Technique and ExamplesFahim Ferdous This slides gives a strong overview of backtracking algorithm. How it came and general approaches of the techniques. Also some well-known problem and solution of backtracking algorithm.
Java-java virtual machine



Java-java virtual machineSurbhi Panhalkar Java is a programming language that compiles code to bytecode that runs on a Java Virtual Machine (JVM). The JVM is an abstraction layer that executes bytecode similarly across operating systems. It includes components like the bytecode verifier, class loader, execution engine, garbage collector, and security manager. The JVM allows Java to be platform independent and "write once, run anywhere".
Java buzzwords



Java buzzwordsramesh517 java buzzwords are the features in java. These describes the overall description of java programming
Operators in java



Operators in javaThen Murugeshwari Operators in Java provide symbols that operate on arguments to produce results. The document discusses the different types of operators in Java including assignment, arithmetic, relational, logical, bitwise, and ternary operators. Examples are provided to demonstrate the usage of various operators like increment/decrement, arithmetic, relational, logical, bitwise, ternary, and instanceof operators in Java code.
Semaphores



SemaphoresMohd Arif 1) A semaphore consists of a counter, a waiting list, and wait() and signal() methods. Wait() decrements the counter and blocks if it becomes negative, while signal() increments the counter and resumes a blocked process if the counter becomes positive.
2) The dining philosophers problem is solved using semaphores to lock access to shared chopsticks, with one philosopher designated as a "weirdo" to avoid deadlock by acquiring locks in a different order.
3) The producer-consumer problem uses three semaphores - one to limit buffer size, one for empty slots, and one for locks - to coordinate producers adding to a bounded buffer
Single source Shortest path algorithm with example



Single source Shortest path algorithm with exampleVINITACHAUHAN21 The document discusses greedy algorithms and their application to solving optimization problems. It provides an overview of greedy algorithms and explains that they make locally optimal choices at each step in the hope of finding a globally optimal solution. One application discussed is the single source shortest path problem, which can be solved using Dijkstra's algorithm. Dijkstra's algorithm is presented as a greedy approach that runs in O(V2) time for a graph with V vertices. An example of applying Dijkstra's algorithm to find shortest paths from a source node in a graph is provided.
Deadlock dbms



Deadlock dbmsVardhil Patel In this presentation all concept of deadlock is included. and it explain in less slides so easy to explain.
It is also useful for study.
Directory structure



Directory structuresangrampatil81 - Directory structures organize files in a storage system and contain metadata about each file's name, location, size, and type. They allow operations like creating, searching, deleting, listing, and renaming files.
- Early systems used single-level directories with one list of all files, but this does not allow multiple files with the same name or grouping of files.
- Modern systems commonly use tree-structured directories that allow nesting files into subdirectories, making searching more efficient and allowing grouping of similar files. Directories can also be connected in acyclic graphs to enable sharing of files between directories through links.
Lexical Analysis - Compiler design 



Lexical Analysis - Compiler design Aman Sharma The document discusses the role and implementation of a lexical analyzer. It can be summarized as:
1. A lexical analyzer scans source code, groups characters into lexemes, and produces tokens which it returns to the parser upon request. It handles tasks like removing whitespace and expanding macros.
2. It implements buffering techniques to efficiently scan large inputs and uses transition diagrams to represent patterns for matching tokens.
3. Regular expressions are used to specify patterns for tokens, and flex is a common language for implementing lexical analyzers based on these specifications.
Knowledge representation



Knowledge representationAmit Kumar Rathi The document discusses different types of knowledge that may need to be represented in AI systems, including objects, events, performance, and meta-knowledge. It describes representing knowledge at two levels: the knowledge level, which describes facts, and the symbol level, where facts are represented using symbols that can be manipulated by programs. Different knowledge representation schemes are examined, including databases, semantic networks, logic, procedural representations, and choosing an appropriate level of granularity. Issues around representing sets of objects and selecting the right knowledge structure are also covered.
Loop optimization



Loop optimizationVivek Gandhi Loop optimization is a technique to improve the performance of programs by optimizing the inner loops which take a large amount of time. Some common loop optimization methods include code motion, induction variable and strength reduction, loop invariant code motion, loop unrolling, and loop fusion. Code motion moves loop-invariant code outside the loop to avoid unnecessary computations. Induction variable and strength reduction techniques optimize computations involving induction variables. Loop invariant code motion avoids repeating computations inside loops. Loop unrolling replicates loop bodies to reduce loop control overhead. Loop fusion combines multiple nested loops to reduce the total number of iterations.
Semaphore



SemaphoreArafat Hossan This document discusses semaphores, which are integer variables that coordinate access to shared resources. It describes counting semaphores, which allow multiple processes to access a critical section simultaneously up to a set limit, and binary semaphores, which only permit one process at a time. Key differences are that counting semaphores can have any integer value while binary semaphores are limited to 0 or 1, and counting semaphores allow multiple slots while binary semaphores provide strict mutual exclusion. Limitations of semaphores include potential priority inversion issues and deadlocks if not used properly.
Algorithmic problem solving



Algorithmic problem solvingPrabhakaran V M This document discusses the process of algorithm design and analysis. It outlines 9 key techniques for solving problems algorithmically: 1) Understanding the problem, 2) Ascertaining computational capabilities, 3) Determining exact or approximate solutions, 4) Choosing appropriate data structures, 5) Using algorithm design techniques, 6) Specifying the algorithm, 7) Proving correctness, 8) Analyzing efficiency, and 9) Coding the algorithm. These techniques provide a systematic approach to developing procedural solutions to problems through specific instructions to obtain answers.
Interface in java



Interface in javaPhD Research Scholar This document discusses interfaces in Java. It defines an interface as a blueprint of a class that defines static constants and abstract methods. Interfaces are used to achieve abstraction and multiple inheritance in Java. They represent an "is-a" relationship. There are three main reasons to use interfaces - for abstraction, to support multiple inheritance functionality, and to achieve loose coupling. The document provides examples of interfaces, such as a Printable interface and implementations in different classes. It also demonstrates multiple inheritance using interfaces and interface inheritance.
Java interfaces



Java interfacesRaja Sekhar Java Interfaces Concept
By
N.V.Raja Sekhar Reddy
www.technolamp.co.in
Want more...
Like us @ https://www.facebook.com/Technolamp.co.in
subscribe videos @ http://www.youtube.com/user/nvrajasekhar
Sorting Algorithms



Sorting AlgorithmsPranay Neema This document discusses various sorting algorithms and their complexities. It begins by defining an algorithm and complexity measures like time and space complexity. It then defines sorting and common sorting algorithms like bubble sort, selection sort, insertion sort, quicksort, and mergesort. For each algorithm, it provides a high-level overview of the approach and time complexity. It also covers sorting algorithm concepts like stable and unstable sorting. The document concludes by discussing future directions for sorting algorithms and their applications.
Memory Management in OS



Memory Management in OSvampugani This document discusses different memory management techniques used in operating systems. It begins by describing the basic components and functions of memory. It then explains various memory management algorithms like overlays, swapping, paging and segmentation. Overlays divide a program into instruction sets that are loaded and unloaded as needed. Swapping loads entire processes into memory for execution then writes them back to disk. Paging and segmentation are used to map logical addresses to physical addresses through page tables and segment tables respectively. The document compares advantages and limitations of these approaches.
backpropagation in neural networks



backpropagation in neural networksAkash Goel Backpropagation is the algorithm that is used to train modern feed-forwards neural nets. This ppt aims to explain it succinctly.
Asymptotic notations



Asymptotic notationsNikhil Sharma The document discusses asymptotic notations that are used to describe the time complexity of algorithms. It introduces big O notation, which describes asymptotic upper bounds, big Omega notation for lower bounds, and big Theta notation for tight bounds. Common time complexities are described such as O(1) for constant time, O(log N) for logarithmic time, and O(N^2) for quadratic time. The notations allow analyzing how efficiently algorithms use resources like time and space as the input size increases.
Design and Analysis of Algorithms.pptx



Design and Analysis of Algorithms.pptxSyed Zaid Irshad This document discusses algorithms and their analysis. It defines an algorithm as a finite sequence of unambiguous instructions that terminate in a finite amount of time. It discusses areas of study like algorithm design techniques, analysis of time and space complexity, testing and validation. Common algorithm complexities like constant, logarithmic, linear, quadratic and exponential are explained. Performance analysis techniques like asymptotic analysis and amortized analysis using aggregate analysis, accounting method and potential method are also summarized.
Bruteforce algorithm



Bruteforce algorithmRezwan Siam This powerpoint slide is for educational purposes only.!
We have given our best to educate people about the basic brute-force algorithm. Best of luck.
MULTI THREADING IN JAVA



MULTI THREADING IN JAVAVINOTH R This document provides an overview of threads in Java, including:
- Threads allow for multitasking by executing multiple processes simultaneously. They are lightweight processes that exist within a process and share system resources.
- Threads can be created by extending the Thread class or implementing the Runnable interface. The run() method defines the code executed by the thread.
- Threads transition between states like new, runnable, running, blocked, and dead during their lifecycle. Methods like start(), sleep(), join(), etc. impact the thread states.
- Synchronization is used to control access to shared resources when multiple threads access methods and data outside their run() methods. This prevents issues like inconsistent data.
Forms of learning in ai



Forms of learning in aiRobert Antony Three main types of machine learning are supervised learning, unsupervised learning, and reinforcement learning. Supervised learning involves training a model using labeled input/output data where the desired outputs are provided, allowing the model to map inputs to outputs. Unsupervised learning involves discovering hidden patterns in unlabeled data and grouping similar data points together. Reinforcement learning involves an agent learning through trial-and-error interactions with a dynamic environment by receiving rewards or punishments for actions.
Remote backup system



Remote backup systemDipendraMahato3 Remote backup system allows data to be simultaneously backed up in two locations - a primary site and remote backup site. This provides high availability even if the primary site fails, as the remote backup site can take over processing after executing recovery actions. The remote site is kept synchronized with log record updates from the primary site over the internet. If the primary site fails, the remote backup site takes over processing to ensure uninterrupted transactions.
process and thread.pptx



process and thread.pptxHamzaxTv Processes provide resource ownership and protection, while threads are the unit of scheduling and execution. There are two main types of threads: user-level threads managed by applications and kernel-level threads managed by the operating system kernel. Both approaches have advantages and disadvantages related to scheduling efficiency and blocking system calls. Modern operating systems use a combined approach for maximum flexibility. Processes contain threads and manage resources, while the kernel schedules threads and handles synchronization between threads of the same process.
Genetic programming



Genetic programmingMeghna Singh Genetic programming is an evolutionary algorithm that uses principles of natural selection and genetics to automatically generate computer programs to solve problems. It works by generating an initial population of random programs, evaluating their performance on the task, and breeding new programs through genetic operations like crossover and mutation. The fittest programs are selected to pass their traits to the next generation, while less fit programs are removed. This process is repeated until an optimal program is found. Genetic programming represents programs as syntax trees and evolves these trees to find solutions without requiring the programmer to specify the form or structure of the solution.
3 analysis.gtm



3 analysis.gtmNatarajan Angappan This document discusses algorithm analysis and asymptotic notation. It introduces algorithms for computing prefix averages in arrays. One algorithm runs in quadratic time O(n^2) by applying the definition directly. A more efficient linear time O(n) algorithm is also presented that maintains a running sum. Asymptotic analysis determines the worst-case running time of an algorithm as a function of the input size using big-O notation. This provides an analysis of algorithms that is independent of implementation details and hardware.
Ad
More Related Content
What's hot (20)
Deadlock dbms



Deadlock dbmsVardhil Patel In this presentation all concept of deadlock is included. and it explain in less slides so easy to explain.
It is also useful for study.
Directory structure



Directory structuresangrampatil81 - Directory structures organize files in a storage system and contain metadata about each file's name, location, size, and type. They allow operations like creating, searching, deleting, listing, and renaming files.
- Early systems used single-level directories with one list of all files, but this does not allow multiple files with the same name or grouping of files.
- Modern systems commonly use tree-structured directories that allow nesting files into subdirectories, making searching more efficient and allowing grouping of similar files. Directories can also be connected in acyclic graphs to enable sharing of files between directories through links.
Lexical Analysis - Compiler design 



Lexical Analysis - Compiler design Aman Sharma The document discusses the role and implementation of a lexical analyzer. It can be summarized as:
1. A lexical analyzer scans source code, groups characters into lexemes, and produces tokens which it returns to the parser upon request. It handles tasks like removing whitespace and expanding macros.
2. It implements buffering techniques to efficiently scan large inputs and uses transition diagrams to represent patterns for matching tokens.
3. Regular expressions are used to specify patterns for tokens, and flex is a common language for implementing lexical analyzers based on these specifications.
Knowledge representation



Knowledge representationAmit Kumar Rathi The document discusses different types of knowledge that may need to be represented in AI systems, including objects, events, performance, and meta-knowledge. It describes representing knowledge at two levels: the knowledge level, which describes facts, and the symbol level, where facts are represented using symbols that can be manipulated by programs. Different knowledge representation schemes are examined, including databases, semantic networks, logic, procedural representations, and choosing an appropriate level of granularity. Issues around representing sets of objects and selecting the right knowledge structure are also covered.
Loop optimization



Loop optimizationVivek Gandhi Loop optimization is a technique to improve the performance of programs by optimizing the inner loops which take a large amount of time. Some common loop optimization methods include code motion, induction variable and strength reduction, loop invariant code motion, loop unrolling, and loop fusion. Code motion moves loop-invariant code outside the loop to avoid unnecessary computations. Induction variable and strength reduction techniques optimize computations involving induction variables. Loop invariant code motion avoids repeating computations inside loops. Loop unrolling replicates loop bodies to reduce loop control overhead. Loop fusion combines multiple nested loops to reduce the total number of iterations.
Semaphore



SemaphoreArafat Hossan This document discusses semaphores, which are integer variables that coordinate access to shared resources. It describes counting semaphores, which allow multiple processes to access a critical section simultaneously up to a set limit, and binary semaphores, which only permit one process at a time. Key differences are that counting semaphores can have any integer value while binary semaphores are limited to 0 or 1, and counting semaphores allow multiple slots while binary semaphores provide strict mutual exclusion. Limitations of semaphores include potential priority inversion issues and deadlocks if not used properly.
Algorithmic problem solving



Algorithmic problem solvingPrabhakaran V M This document discusses the process of algorithm design and analysis. It outlines 9 key techniques for solving problems algorithmically: 1) Understanding the problem, 2) Ascertaining computational capabilities, 3) Determining exact or approximate solutions, 4) Choosing appropriate data structures, 5) Using algorithm design techniques, 6) Specifying the algorithm, 7) Proving correctness, 8) Analyzing efficiency, and 9) Coding the algorithm. These techniques provide a systematic approach to developing procedural solutions to problems through specific instructions to obtain answers.
Interface in java



Interface in javaPhD Research Scholar This document discusses interfaces in Java. It defines an interface as a blueprint of a class that defines static constants and abstract methods. Interfaces are used to achieve abstraction and multiple inheritance in Java. They represent an "is-a" relationship. There are three main reasons to use interfaces - for abstraction, to support multiple inheritance functionality, and to achieve loose coupling. The document provides examples of interfaces, such as a Printable interface and implementations in different classes. It also demonstrates multiple inheritance using interfaces and interface inheritance.
Java interfaces



Java interfacesRaja Sekhar Java Interfaces Concept
By
N.V.Raja Sekhar Reddy
www.technolamp.co.in
Want more...
Like us @ https://www.facebook.com/Technolamp.co.in
subscribe videos @ http://www.youtube.com/user/nvrajasekhar
Sorting Algorithms



Sorting AlgorithmsPranay Neema This document discusses various sorting algorithms and their complexities. It begins by defining an algorithm and complexity measures like time and space complexity. It then defines sorting and common sorting algorithms like bubble sort, selection sort, insertion sort, quicksort, and mergesort. For each algorithm, it provides a high-level overview of the approach and time complexity. It also covers sorting algorithm concepts like stable and unstable sorting. The document concludes by discussing future directions for sorting algorithms and their applications.
Memory Management in OS



Memory Management in OSvampugani This document discusses different memory management techniques used in operating systems. It begins by describing the basic components and functions of memory. It then explains various memory management algorithms like overlays, swapping, paging and segmentation. Overlays divide a program into instruction sets that are loaded and unloaded as needed. Swapping loads entire processes into memory for execution then writes them back to disk. Paging and segmentation are used to map logical addresses to physical addresses through page tables and segment tables respectively. The document compares advantages and limitations of these approaches.
backpropagation in neural networks



backpropagation in neural networksAkash Goel Backpropagation is the algorithm that is used to train modern feed-forwards neural nets. This ppt aims to explain it succinctly.
Asymptotic notations



Asymptotic notationsNikhil Sharma The document discusses asymptotic notations that are used to describe the time complexity of algorithms. It introduces big O notation, which describes asymptotic upper bounds, big Omega notation for lower bounds, and big Theta notation for tight bounds. Common time complexities are described such as O(1) for constant time, O(log N) for logarithmic time, and O(N^2) for quadratic time. The notations allow analyzing how efficiently algorithms use resources like time and space as the input size increases.
Design and Analysis of Algorithms.pptx



Design and Analysis of Algorithms.pptxSyed Zaid Irshad This document discusses algorithms and their analysis. It defines an algorithm as a finite sequence of unambiguous instructions that terminate in a finite amount of time. It discusses areas of study like algorithm design techniques, analysis of time and space complexity, testing and validation. Common algorithm complexities like constant, logarithmic, linear, quadratic and exponential are explained. Performance analysis techniques like asymptotic analysis and amortized analysis using aggregate analysis, accounting method and potential method are also summarized.
Bruteforce algorithm



Bruteforce algorithmRezwan Siam This powerpoint slide is for educational purposes only.!
We have given our best to educate people about the basic brute-force algorithm. Best of luck.
MULTI THREADING IN JAVA



MULTI THREADING IN JAVAVINOTH R This document provides an overview of threads in Java, including:
- Threads allow for multitasking by executing multiple processes simultaneously. They are lightweight processes that exist within a process and share system resources.
- Threads can be created by extending the Thread class or implementing the Runnable interface. The run() method defines the code executed by the thread.
- Threads transition between states like new, runnable, running, blocked, and dead during their lifecycle. Methods like start(), sleep(), join(), etc. impact the thread states.
- Synchronization is used to control access to shared resources when multiple threads access methods and data outside their run() methods. This prevents issues like inconsistent data.
Forms of learning in ai



Forms of learning in aiRobert Antony Three main types of machine learning are supervised learning, unsupervised learning, and reinforcement learning. Supervised learning involves training a model using labeled input/output data where the desired outputs are provided, allowing the model to map inputs to outputs. Unsupervised learning involves discovering hidden patterns in unlabeled data and grouping similar data points together. Reinforcement learning involves an agent learning through trial-and-error interactions with a dynamic environment by receiving rewards or punishments for actions.
Remote backup system



Remote backup systemDipendraMahato3 Remote backup system allows data to be simultaneously backed up in two locations - a primary site and remote backup site. This provides high availability even if the primary site fails, as the remote backup site can take over processing after executing recovery actions. The remote site is kept synchronized with log record updates from the primary site over the internet. If the primary site fails, the remote backup site takes over processing to ensure uninterrupted transactions.
process and thread.pptx



process and thread.pptxHamzaxTv Processes provide resource ownership and protection, while threads are the unit of scheduling and execution. There are two main types of threads: user-level threads managed by applications and kernel-level threads managed by the operating system kernel. Both approaches have advantages and disadvantages related to scheduling efficiency and blocking system calls. Modern operating systems use a combined approach for maximum flexibility. Processes contain threads and manage resources, while the kernel schedules threads and handles synchronization between threads of the same process.
Genetic programming



Genetic programmingMeghna Singh Genetic programming is an evolutionary algorithm that uses principles of natural selection and genetics to automatically generate computer programs to solve problems. It works by generating an initial population of random programs, evaluating their performance on the task, and breeding new programs through genetic operations like crossover and mutation. The fittest programs are selected to pass their traits to the next generation, while less fit programs are removed. This process is repeated until an optimal program is found. Genetic programming represents programs as syntax trees and evolves these trees to find solutions without requiring the programmer to specify the form or structure of the solution.
Similar to Algorithm analysis basics - Seven Functions/Big-Oh/Omega/Theta (20)
3 analysis.gtm



3 analysis.gtmNatarajan Angappan This document discusses algorithm analysis and asymptotic notation. It introduces algorithms for computing prefix averages in arrays. One algorithm runs in quadratic time O(n^2) by applying the definition directly. A more efficient linear time O(n) algorithm is also presented that maintains a running sum. Asymptotic analysis determines the worst-case running time of an algorithm as a function of the input size using big-O notation. This provides an analysis of algorithms that is independent of implementation details and hardware.
Data Structures- Part2 analysis tools



Data Structures- Part2 analysis toolsAbdullah Al-hazmy This document discusses algorithm analysis tools. It explains that algorithm analysis is used to determine which of several algorithms to solve a problem is most efficient. Theoretical analysis counts primitive operations to approximate runtime as a function of input size. Common complexity classes like constant, linear, quadratic, and exponential time are defined based on how quickly runtime grows with size. Big-O notation represents the asymptotic upper bound of a function's growth rate to classify algorithms.
Lec1



Lec1Nikhil Chilwant The document discusses data structures and algorithms. It defines key concepts like algorithms, programs, data structures, and asymptotic analysis. It explains how to analyze algorithms to determine their efficiency, including analyzing best, worst, and average cases. Common notations for describing asymptotic running time like Big-O, Big-Omega, and Big-Theta are introduced. The document provides examples of analyzing sorting algorithms like insertion sort and calculating running times. It also discusses techniques for proving an algorithm's correctness like assertions and loop invariants.
Data Structures and Algorithms Lecture 2: Analysis of Algorithms, Asymptotic ...



Data Structures and Algorithms Lecture 2: Analysis of Algorithms, Asymptotic ...TechVision8 This document discusses analyzing the running time of algorithms. It introduces pseudocode as a way to describe algorithms, primitive operations that are used to count the number of basic steps an algorithm takes, and asymptotic analysis to determine an algorithm's growth rate as the input size increases. The key points covered are using big-O notation to focus on the dominant term and ignore lower-order terms and constants, and analyzing two algorithms for computing prefix averages to demonstrate asymptotic analysis.
Data Structures and Agorithm: DS 22 Analysis of Algorithm.pptx



Data Structures and Agorithm: DS 22 Analysis of Algorithm.pptxRashidFaridChishti Data Structures and Agorithm: DS 22 Analysis of Algorithm.pptx
Data Structure & Algorithms - Mathematical



Data Structure & Algorithms - Mathematicalbabuk110 This document discusses various mathematical notations and asymptotic analysis used for analyzing algorithms. It covers floor and ceiling functions, remainder function, summation symbol, factorial function, permutations, exponents, logarithms, Big-O, Big-Omega and Theta notations. It provides examples of calculating time complexity of insertion sort and bubble sort using asymptotic notations. It also discusses space complexity analysis and how to calculate the space required by an algorithm.
DS Unit-1.pptx very easy to understand..



DS Unit-1.pptx very easy to understand..KarthikeyaLanka1 The document discusses algorithms, including their definition, properties, analysis of time and space complexity, and examples of recursion and iteration. It defines an algorithm as a finite set of instructions to accomplish a task. Properties include inputs, outputs, finiteness, definiteness, and effectiveness. Time complexity is analyzed using big-O notation, while space complexity considers static and variable parts. Recursion uses function calls to solve sub-problems, while iteration uses loops. Examples include factorial calculation, GCD, and Towers of Hanoi solved recursively.
Algorithm Analysis



Algorithm AnalysisMegha V The document discusses various methods for analyzing algorithms, including analyzing running time complexity and rate of growth. It covers asymptotic notations like Big O, Big Omega, and Big Theta notation for describing upper bounds, lower bounds, and tight bounds of an algorithm's running time. Various time complexities like constant, logarithmic, linear, quadratic, and exponential are provided with examples. The analysis of different algorithm control structures like loops, nested loops, if-else statements, and switches are also discussed.
AlgorithmAnalysis2.ppt



AlgorithmAnalysis2.pptREMEGIUSPRAVEENSAHAY This document provides an overview of algorithm analysis and asymptotic notation. It discusses analyzing algorithms based on problem size and using Big-O notation to characterize runtime. Specifically, it introduces the concepts of best, worst, and average case analysis. It also covers properties of Big-O, like how operations combine asymptotically. Examples analyze the runtime of prefix averages algorithms and solving recursive equations using repeated substitution or telescoping. Finally, it discusses abstract data types and how to design new data types through specification, application, and implementation.
Algorithm And analysis Lecture 03& 04-time complexity.



Algorithm And analysis Lecture 03& 04-time complexity.Tariq Khan This document discusses algorithm efficiency and complexity analysis. It defines key terms like algorithms, asymptotic complexity, Big O notation, and different complexity classes. It provides examples of analyzing time complexity for different algorithms like loops, nested loops, and recursive functions. The document explains that Big O notation allows analyzing algorithms independent of machine or input by focusing on the highest order term as the problem size increases. Overall, the document introduces methods for measuring an algorithm's efficiency and analyzing its time and space complexity asymptotically.
Algorithm chapter 2



Algorithm chapter 2chidabdu The document discusses the framework for analyzing the efficiency of algorithms by measuring how the running time and space requirements grow as the input size increases, focusing on determining the order of growth of the number of basic operations using asymptotic notation such as O(), Ω(), and Θ() to classify algorithms based on their worst-case, best-case, and average-case time complexities.
lecture 1



lecture 1sajinsc The document discusses algorithms and algorithm analysis. It provides examples to illustrate key concepts in algorithm analysis including worst-case, average-case, and best-case running times. The document also introduces asymptotic notation such as Big-O, Big-Omega, and Big-Theta to analyze the growth rates of algorithms. Common growth rates like constant, logarithmic, linear, quadratic, and exponential functions are discussed. Rules for analyzing loops and consecutive statements are provided. Finally, algorithms for two problems - selection and maximum subsequence sum - are analyzed to demonstrate algorithm analysis techniques.
Algorithms required for data structures(basics like Arrays, Stacks ,Linked Li...



Algorithms required for data structures(basics like Arrays, Stacks ,Linked Li...DebiPrasadSen An algorithm is a well-defined computational procedure that takes input values and produces output values. It has several key properties including being well-defined, producing the correct output for any possible input, and terminating after a finite number of steps. When analyzing algorithms, asymptotic complexity is important as it measures how processing requirements grow with increasing input size. Common complexity classes include constant O(1), logarithmic O(log n), linear O(n), quadratic O(n^2), and exponential O(2^n) time. For large inputs, slower asymptotic growth indicates better performance.
Ad
More from Priyanka Rana (19)
Insertion & Selection Sort - using Priority Queues



Insertion & Selection Sort - using Priority QueuesPriyanka Rana Elaboration of sorting applications of Priority Queues using Insertion Sort and Selection Sort, with animations and their running times justifications
Scrum values



Scrum valuesPriyanka Rana The document discusses the five core values of Scrum: focus, courage, openness, commitment, and respect. It explains that these values are important for the health and success of Scrum teams. Focus values concentrating efforts on a few important tasks at a time to deliver work sooner. Courage values undertaking challenges and admitting imperfections with transparency. Openness values openly expressing concerns and collaborating. Commitment values having control over work with dedication to quality, collaboration, learning, and goals. Respect values regarding others with diverse backgrounds and opinions to strengthen the team.
Usability testing 



Usability testing Priyanka Rana Slides talk about complete process of usability testing, extensively discusses usability components, phases of usability testing process and significance of designing with empathy
Content package - Mobile computing



Content package - Mobile computingPriyanka Rana The document discusses Content Providers and Content Resolvers in Android. Content Providers allow access to application data from other applications through a common interface, while enforcing security. Content Resolvers provide a global instance to query Content Providers and resolve requests by directing them to the proper Content Provider based on authority. Content Providers abstract the underlying data source and define security permissions, and Content Resolvers handle CRUD operations on behalf of applications.
Scrum retrospective 



Scrum retrospective Priyanka Rana The sprint retrospective is a meeting that occurs at the end of each sprint cycle in Scrum. The purpose is for the team to inspect how the last sprint went and identify improvements for the next sprint. Key elements include discussing what went well, what went wrong, and what could be improved. The retrospective is collaborative, involving the whole team, and helps the team improve its processes and build ownership over outcomes.
Convergent divergent thinking & wireframeprototyping



Convergent divergent thinking & wireframeprototypingPriyanka Rana This document discusses convergent and divergent thinking processes involved in creativity. It defines divergent thinking as generating many novel ideas through techniques like brainstorming, journaling, and mind mapping. Convergent thinking is described as analyzing ideas to find the best solution using logic and decision making strategies. The document provides examples of divergent and convergent learning activities and explains the differences between wireframes and prototypes, with wireframes focusing on content structure and prototypes adding interactivity details.
Sketching&storyboarding



Sketching&storyboardingPriyanka Rana Slides talk about importance & guidelines of sketching and story boarding. It discusses two approaches about "getting the design right" or getting the right design". Steps and Do's/Dont's of storyboarding
Building better prototype



Building better prototypePriyanka Rana types of requirements, types of users, user characteristics, conceptual model and components (metaphor/analogies)
Mobile presence & location based marketing



Mobile presence & location based marketingPriyanka Rana Slides talk about value of mobile marketing , various tools and technologies that support mobile marketing along with discussion of location-based marketing.
User friendliness of website



User friendliness of websitePriyanka Rana Slides talk about "must have" user friendliness features of a website that makes it search engine
friendly and favorite of ts users.
E-commerce Marketing & advertising



E-commerce Marketing & advertisingPriyanka Rana Illustration of various types of Online marketing with examples.Slides talk about search engine marketing, display ads, affiliate marketing, lead generation marketing, native marketing, email marketing etc.
E commerce business proposal



E commerce business proposalPriyanka Rana Includes brief description about components of E-commerce business plan and introduction of E-commerce presence map
E-strategic Management-1



E-strategic Management-1Priyanka Rana E-strategic management involves the formulation and implementation of major goals and initiatives based on an assessment of internal and external environments. E-strategy is the process of creating or modifying a business model for e-business through a sustainable and financially viable model. E-business is the business use of the internet that provides a business benefit like increased revenue or reduced costs. E-commerce involves digital transactions between organizations and individuals using the internet, while e-business refers to digitally enabling internal firm processes and systems. Unique features of e-commerce technology include ubiquity, global reach, universal standards, richness, interactivity, information density, personalization, social technology, and omnichannel experiences.
Maps&hash tables



Maps&hash tablesPriyanka Rana Describes Map data structure, its methods and implementation using Hash tables & linked list along with their running time. Hash table components, bucket Array and hash function. Collision handing strategies: Separate chaining, Linear probing, quadratic probing, double hashing.
Ordered Maps and corresponding binary search
Heaps & Adaptable priority Queues



Heaps & Adaptable priority QueuesPriyanka Rana Slides cover understanding heap, heap properties, representation of heap, up-heap and down heap bubbling followed by Adaptable priority queues, list and heap implementation of priority queues.
Priority queues



Priority queuesPriyanka Rana Describes basic understanding of priority queues, their applications, methods, implementation with sorted/unsorted list, sorting applications with insertion sort and selection sort with their running times.
Trees - Non Linear Data Structure



Trees - Non Linear Data StructurePriyanka Rana Slides cover definition of tree data structure with examples, related terminologies, accessors methods, query methods, generic methods, traversal algorithms (preorder, postorder, inorder) traversal, Binary tree, Binary tree implementation using linked list and array, Binary search
Recursion - Algorithms and Data Structures



Recursion - Algorithms and Data StructuresPriyanka Rana Discuss different types of recursion with examples.
Linear/Binary/Multiple recursion
(Download is recommended to make the animations work)
Linked list



Linked listPriyanka Rana Slides give the basic introduction of linked list, doubly linked list, circular linked list and operations related to it. It has animations, Download is recommended in order to make best out of animations
(Download is recommended to make the animations work)
Ad
Recently uploaded (20)
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
Technology Trends in 2025: AI and Big Data Analytics



Technology Trends in 2025: AI and Big Data AnalyticsInData Labs At InData Labs, we have been keeping an ear to the ground, looking out for AI-enabled digital transformation trends coming our way in 2025. Our report will provide a look into the technology landscape of the future, including:
-Artificial Intelligence Market Overview
-Strategies for AI Adoption in 2025
-Anticipated drivers of AI adoption and transformative technologies
-Benefits of AI and Big data for your business
-Tips on how to prepare your business for innovation
-AI and data privacy: Strategies for securing data privacy in AI models, etc.
Download your free copy nowand implement the key findings to improve your business.
Canadian book publishing: Insights from the latest salary survey - Tech Forum...



Canadian book publishing: Insights from the latest salary survey - Tech Forum...BookNet Canada Join us for a presentation in partnership with the Association of Canadian Publishers (ACP) as they share results from the recently conducted Canadian Book Publishing Industry Salary Survey. This comprehensive survey provides key insights into average salaries across departments, roles, and demographic metrics. Members of ACP’s Diversity and Inclusion Committee will join us to unpack what the findings mean in the context of justice, equity, diversity, and inclusion in the industry.
Results of the 2024 Canadian Book Publishing Industry Salary Survey: https://publishers.ca/wp-content/uploads/2025/04/ACP_Salary_Survey_FINAL-2.pdf
Link to presentation recording and transcript: https://bnctechforum.ca/sessions/canadian-book-publishing-insights-from-the-latest-salary-survey/
Presented by BookNet Canada and the Association of Canadian Publishers on May 1, 2025 with support from the Department of Canadian Heritage.
Webinar - Top 5 Backup Mistakes MSPs and Businesses Make .pptx



Webinar - Top 5 Backup Mistakes MSPs and Businesses Make .pptxMSP360 Data loss can be devastating — especially when you discover it while trying to recover. All too often, it happens due to mistakes in your backup strategy. Whether you work for an MSP or within an organization, your company is susceptible to common backup mistakes that leave data vulnerable, productivity in question, and compliance at risk.
Join 4-time Microsoft MVP Nick Cavalancia as he breaks down the top five backup mistakes businesses and MSPs make—and, more importantly, explains how to prevent them.
tecnologias de las primeras civilizaciones.pdf



tecnologias de las primeras civilizaciones.pdffjgm517 descaripcion detallada del avance de las tecnologias en mesopotamia, egipto, roma y grecia.
TrsLabs - AI Agents for All - Chatbots to Multi-Agents Systems



TrsLabs - AI Agents for All - Chatbots to Multi-Agents SystemsTrs Labs AI Adoption for Your Business
AI applications have evolved from chatbots
into sophisticated AI agents capable of
handling complex workflows. Multi-agent
systems are the next phase of evolution.
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Build 3D Animated Safety Induction - Tech EHS



Build 3D Animated Safety Induction - Tech EHSTECH EHS Solution Train Smarter, Not Harder – Let 3D Animation Lead the Way!
Discover how 3D animation makes inductions more engaging, effective, and cost-efficient.
Check out the slides to see how you can transform your safety training process!
Slide 1: Why 3D animation changes the game
Slide 2: Site-specific induction isn’t optional—it’s essential
Slide 3: Visitors are most at risk. Keep them safe
Slide 4: Videos beat text—especially when safety is on the line
Slide 5: TechEHS makes safety engaging and consistent
Slide 6: Better retention, lower costs, safer sites
Slide 7: Ready to elevate your induction process?
Can an animated video make a difference to your site's safety? Let's talk.
Transcript: Canadian book publishing: Insights from the latest salary survey ...



Transcript: Canadian book publishing: Insights from the latest salary survey ...BookNet Canada Join us for a presentation in partnership with the Association of Canadian Publishers (ACP) as they share results from the recently conducted Canadian Book Publishing Industry Salary Survey. This comprehensive survey provides key insights into average salaries across departments, roles, and demographic metrics. Members of ACP’s Diversity and Inclusion Committee will join us to unpack what the findings mean in the context of justice, equity, diversity, and inclusion in the industry.
Results of the 2024 Canadian Book Publishing Industry Salary Survey: https://publishers.ca/wp-content/uploads/2025/04/ACP_Salary_Survey_FINAL-2.pdf
Link to presentation slides and transcript: https://bnctechforum.ca/sessions/canadian-book-publishing-insights-from-the-latest-salary-survey/
Presented by BookNet Canada and the Association of Canadian Publishers on May 1, 2025 with support from the Department of Canadian Heritage.
Web and Graphics Designing Training in Rajpura



Web and Graphics Designing Training in RajpuraErginous Technology Web & Graphics Designing Training at Erginous Technologies in Rajpura offers practical, hands-on learning for students, graduates, and professionals aiming for a creative career. The 6-week and 6-month industrial training programs blend creativity with technical skills to prepare you for real-world opportunities in design.
The course covers Graphic Designing tools like Photoshop, Illustrator, and CorelDRAW, along with logo, banner, and branding design. In Web Designing, you’ll learn HTML5, CSS3, JavaScript basics, responsive design, Bootstrap, Figma, and Adobe XD.
Erginous emphasizes 100% practical training, live projects, portfolio building, expert guidance, certification, and placement support. Graduates can explore roles like Web Designer, Graphic Designer, UI/UX Designer, or Freelancer.
For more info, visit erginous.co.in , message us on Instagram at erginoustechnologies, or call directly at +91-89684-38190 . Start your journey toward a creative and successful design career today!
TrsLabs Consultants - DeFi, WEb3, Token Listing



TrsLabs Consultants - DeFi, WEb3, Token ListingTrs Labs Enter the world of web3 with experienced strategic partner.
Open your business to new opportunities.
Reimagine How You and Your Team Work with Microsoft 365 Copilot.pptx



Reimagine How You and Your Team Work with Microsoft 365 Copilot.pptxJohn Moore M365 Community Conference 2025 Workshop on Microsoft 365 Copilot
AI 3-in-1: Agents, RAG, and Local Models - Brent Laster



AI 3-in-1: Agents, RAG, and Local Models - Brent LasterAll Things Open Presented at All Things Open RTP Meetup
Presented by Brent Laster - President & Lead Trainer, Tech Skills Transformations LLC
Talk Title: AI 3-in-1: Agents, RAG, and Local Models
Abstract:
Learning and understanding AI concepts is satisfying and rewarding, but the fun part is learning how to work with AI yourself. In this presentation, author, trainer, and experienced technologist Brent Laster will help you do both! We’ll explain why and how to run AI models locally, the basic ideas of agents and RAG, and show how to assemble a simple AI agent in Python that leverages RAG and uses a local model through Ollama.
No experience is needed on these technologies, although we do assume you do have a basic understanding of LLMs.
This will be a fast-paced, engaging mixture of presentations interspersed with code explanations and demos building up to the finished product – something you’ll be able to replicate yourself after the session!
Unlocking Generative AI in your Web Apps



Unlocking Generative AI in your Web AppsMaximiliano Firtman Slides for the session delivered at Devoxx UK 2025 - Londo.
Discover how to seamlessly integrate AI LLM models into your website using cutting-edge techniques like new client-side APIs and cloud services. Learn how to execute AI models in the front-end without incurring cloud fees by leveraging Chrome's Gemini Nano model using the window.ai inference API, or utilizing WebNN, WebGPU, and WebAssembly for open-source models.
This session dives into API integration, token management, secure prompting, and practical demos to get you started with AI on the web.
Unlock the power of AI on the web while having fun along the way!
TrsLabs - Leverage the Power of UPI Payments



TrsLabs - Leverage the Power of UPI PaymentsTrs Labs Revolutionize your Fintech growth with UPI Payments
"Riding the UPI strategy" refers to leveraging the Unified Payments Interface (UPI) to drive digital payments in India and beyond. This involves understanding UPI's features, benefits, and potential, and developing strategies to maximize its usage and impact. Essentially, it's about strategically utilizing UPI to promote digital payments, financial inclusion, and economic growth.
Enterprise Integration Is Dead! Long Live AI-Driven Integration with Apache C...



Enterprise Integration Is Dead! Long Live AI-Driven Integration with Apache C...Markus Eisele We keep hearing that “integration” is old news, with modern architectures and platforms promising frictionless connectivity. So, is enterprise integration really dead? Not exactly! In this session, we’ll talk about how AI-infused applications and tool-calling agents are redefining the concept of integration, especially when combined with the power of Apache Camel.
We will discuss the the role of enterprise integration in an era where Large Language Models (LLMs) and agent-driven automation can interpret business needs, handle routing, and invoke Camel endpoints with minimal developer intervention. You will see how these AI-enabled systems help weave business data, applications, and services together giving us flexibility and freeing us from hardcoding boilerplate of integration flows.
You’ll walk away with:
An updated perspective on the future of “integration” in a world driven by AI, LLMs, and intelligent agents.
Real-world examples of how tool-calling functionality can transform Camel routes into dynamic, adaptive workflows.
Code examples how to merge AI capabilities with Apache Camel to deliver flexible, event-driven architectures at scale.
Roadmap strategies for integrating LLM-powered agents into your enterprise, orchestrating services that previously demanded complex, rigid solutions.
Join us to see why rumours of integration’s relevancy have been greatly exaggerated—and see first hand how Camel, powered by AI, is quietly reinventing how we connect the enterprise.
Algorithm analysis basics - Seven Functions/Big-Oh/Omega/Theta
- 1. Algorithms and Data Structures Algorithm analysis By- Priyanka
- 2. Session 4 is about Seven Functions Analysis of algorithms
- 3. 1. Constant Function Simplest function: f(n) = c (some fixed constant) Value of n doesn’t matter. Ex: adding two numbers, assigning variable, comparing two numbers
- 4. 2. Logarithm Function f (n) = logb n for some constant b > 1 This function is defined: x = logbn if and only if bx = n Value b is known as the base of the logarithm. log n = log2 n.
- 5. Rules for algorithms Given real numbers a , c > 0, and b , d > 1, we have If b = 2, we either use log n, or lg n.
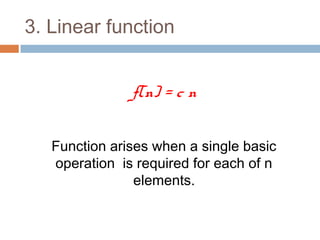
- 6. 3. Linear function f(n) = c n Function arises when a single basic operation is required for each of n elements.
- 7. 4. N- log- N function f(n) = n logn Grows faster than the linear function. Slower than the quadratic function.
- 8. 5. Quadratic function f(n) = n2 For nested loops, where combined operations of inner and outer loop gives n*n = n2.
- 9. 6. Cubic Function & Other Polynomials f(n) = n3 Comparatively less frequent
- 10. 7. Exponential Function f(n) = bn b is a positive constant, called as the base. n is the argument and called as the exponent. Also called as exponent function.
- 11. Analysis of algorithm Analysis of algorithm means: Predicting the amount of resources that the algorithm requires.
- 13. Analysis of algorithms Experimental Studies Primitive Operations Asymptotic Notation
- 14. Experimental Studies Running time of implemented algorithm is calculated by: Executing it on various test inputs. Recording the actual time spent in each execution. Using the System.curent Time Millis () method.
- 15. Experimental Studies (cont.) Steps : 1. Write a program implementing the algorithm. 2. Run the program with inputs of varying size and composition. 3. Use a system call to get running time measure. 4. Plot the results. 5. Perform a statistical analysis.
- 17. Limitations of Experimental analysis Need limited set of test inputs. Need same hardware and software environments. have to fully implement and execute an algorithm.
- 18. Primitive operations Set of primitive operations: 1. Assigning a value to a variable. 2. Calling a method. 3. Performing an arithmetic operation (for example, adding two numbers). 4. Comparing two numbers. 5. Indexing into an array. 6. Following an object reference. 7. Returning from a method.
- 19. Example Algorithm arrayMax(A, n) # operations currentMax ← A[0] 2 for i ← 1 to n − 1 do 2n if A[i] > currentMax then 2(n − 1) currentMax ← A[i] 2(n − 1) { increment counter i } 2(n − 1) return currentMax 1 Total 8n − 2
- 20. Estimating Running Time Algorithm arrayMax executes 8n − 2 primitive operations in the worst case. Define: a = Time taken by the fastest primitive operation b = Time taken by the slowest primitive operation Let T(n) be worst-case time of arrayMax. Then a (8n − 2) ≤ T(n) ≤ b(8n − 2) Hence, the running time T(n) is bounded by two linear functions.
- 21. Asymptotic Notation Uses mathematical notation for functions. Disregards constant factors. n refer to a chosen measure of the input “size”. Focus attention on the primary "big-picture" aspects in a running time function.
- 22. Asymptotic Notation(cont.) Big-Oh Notation Big-Omega Notation Big-Theta Notation
- 23. Big – Oh Notation Given functions are f(n) and g(n) f(n) is O(g(n)) if there are positive constants c>0 and n0 ≥1 such that f(n) ≤ cg(n) for n ≥ n0
- 24. Big – Oh Notation (cont.) Example: 2n + 10 is O(n) 2n + 10 ≤ cn (c − 2) n ≥ 10 n ≥ 10/(c − 2) Pick c = 3 and n0 = 10
- 25. Big – Oh Notation (cont.) Example: the function n2 is not O(n) n2 ≤ cn n ≤ c The above inequality cannot be satisfied since c must be a constant
- 27. Big – Omega Notation Given functions are f(n) and g(n) f(n) is Ω(g(n)) if there are positive constants c>0 and n0 ≥1 such that f(n) ≥ cg(n) for n ≥ n0
- 28. Big – Omega Notation(cont.) Example : the function 5n2 is Ω(n2) 5n2 ≥ c n2 5n ≥ c n c = 5 and n0 = 1
- 29. Big – Theta Notation Given functions are f(n) and g(n) f(n) is Θ(g(n)) if f(n) is O(g(n)) and f(n) is Ω(g(n)) , that is, there are real constants c’> 0 and c’’ >0 and n0 ≥1 such that c’ g(n) ≤ f(n) ≤ c’’ g(n) for n ≥ n0
- 30. Big – Theta Notation(cont.) Example : 3nlog n + 4n + 5logn is Θ(n log n). Justification: 3nlogn ≤ 3nlogn + 4n + 5logn ≤ (3+4+5)nlog n for n ≥ 2
- 31. Thank You










