All Things Open 2022 - State of OSS Security & Support
1 like61 views
Presentation about the latest trends in open source software including growth, life cycles, government initiatives, support, and security
1 of 27
Download to read offline


























Ad
Recommended
Software Security Assurance for DevOps



Software Security Assurance for DevOpsBlack Duck by Synopsys Understand the challenges impacting application security in DevOps, and what you can do to overcome these challenges.
Software Security Assurance for Devops



Software Security Assurance for DevopsJerika Phelps How do organizations build secure applications, given today's rapidly moving and evolving DevOps practices? Join Black Duck and our customer experts on best practices for application security in DevOps.
You’ll learn:
-New security challenges facing today’s popular DevOps and Continuous Integration (CI) practices, including managing custom code and open source risks with containers and traditional environments
-Best practices for designing and incorporating an automated approach to application security into your existing development environment
-Future development and application security challenges organizations will face and what they can do to prepare
Open source software: The infrastructure impact



Open source software: The infrastructure impactRogue Wave Software Open source software drives efficiency and innovation, but affects your application stacks and introduces new challenges to keeping them highly available and performing. Find out about the hottest open source options and how they can help your organization achieve better uptime and performance levels. We also explore the tradeoffs of using open source software, how to evaluate and assess the available types, and the potential effects on your applications and infrastructure.
Winning open source vulnerabilities without loosing your deveopers - Azure De...



Winning open source vulnerabilities without loosing your deveopers - Azure De...WhiteSource Tsaela Pinto, Director of Knowledge R&D at WhiteSource, spoke at the Azure DevOps meetup in Tel Aviv about how develpers should part in maintaining open source security
From Zero to DevSecOps: How to Implement Security at the Speed of DevOps



From Zero to DevSecOps: How to Implement Security at the Speed of DevOpsDevOps.com The traditional way of handling security issues in DevOps involves security teams analyzing vulnerabilities and opening issues/tickets, with closing the loop on resolutions being difficult. This model is changing as the cost of fixing later-stage defects rises significantly. The shift is toward DevSecOps where responsibility for application security moves to development teams. Developers are integrating security tools earlier in the software development lifecycle (SDLC) to enable a more secure-by-design approach. Effective DevSecOps requires tools that fit seamlessly into developer workflows and prioritize actual vulnerabilities over non-issues. It also demands integrating security practices into DevOps processes through agile methodologies and automation.
#OSSPARIS19 - Understanding Open Source Governance - Gilles Gravier, Wipro Li...



#OSSPARIS19 - Understanding Open Source Governance - Gilles Gravier, Wipro Li...Paris Open Source Summit Stratégie, risques liés à l'adoption de l'open source... Comment un modèle de gouvernance fort peut rendre votre parcours open source le plus efficace.
Fortify-Application_Security_Foundation_Training.pptx



Fortify-Application_Security_Foundation_Training.pptxYoisRoberthTapiadeLa This document provides an overview of application security challenges and trends. It discusses how attacks have moved to target applications directly rather than just infrastructure. It also notes that security is often an afterthought for developers focused on speed and that maturity varies. Key trends include shifting security left in the development process, addressing open source risks, and leveraging tools like machine learning. Stakeholders have different priorities around protecting the organization versus meeting deadlines. Primary use cases involve finding and fixing vulnerabilities throughout the development lifecycle. The Fortify platform aims to provide application security that scales with development needs.
Fortify-Application_Security_Foundation_Training.pptx



Fortify-Application_Security_Foundation_Training.pptxVictoriaChavesta This document provides an overview of application security and the Fortify portfolio. It discusses growing application security challenges such as attacks targeting the application layer. It also reviews key application security trends like shift left development and cloud transformation. The document outlines primary customer use cases and priorities around securing applications. Additionally, it summarizes the Fortify product offerings and how the portfolio addresses application security needs. Examples of Fortify customer success are also provided along with insights into the competitive application security market.
From Zero to DevSecOps: How to Implement Security at the Speed of DevOps 



From Zero to DevSecOps: How to Implement Security at the Speed of DevOps WhiteSource Your organization has already embraced the DevOps methodology? That’s a great start. But what about security?
It’s a fact - many organizations fear that adding security to their DevOps practices will severely slow down their development processes. But this doesn’t need to be the case.
Tune in to hear Jeff Martin, Senior Director of Product at WhiteSource and Anders Wallgren, VP of Technology Strategy at Cloudbees, as they discuss:
- Why traditional DevOps has shifted, and what this will mean
- Who should own security in the age of DevOps
- Which tools and strategies are needed to implement continuous security throughout the DevOps pipeline
Secure DevOPS Implementation Guidance



Secure DevOPS Implementation GuidanceTej Luthra The document provides an overview of secure DevOps practices including:
- Integrating security into the software development lifecycle from design through deployment.
- Using automation and continuous integration/delivery practices to continuously assess and remediate vulnerabilities.
- Implementing secure configurations for hardware and software and keeping systems updated with the latest patches.
- Performing security testing using tools that can identify vulnerabilities during the development process.
- Controlling administrative privileges and secrets management in an "infrastructure as code" environment.
CI/CD pipeline security from start to finish with WhiteSource & CircleCI



CI/CD pipeline security from start to finish with WhiteSource & CircleCIWhiteSource This document provides an agenda for a webinar on securing CI/CD pipelines from start to finish with CircleCI and WhiteSource. The agenda includes brief introductions to CircleCI and WhiteSource, an overview of CircleCI Orbs and how they can simplify integrations, a discussion of the state of open source usage and security, and a demo of WhiteSource scanning functionality directly within a CircleCI pipeline using an Orb.
Elastic's recommendation on keeping services up and running with real-time vi...



Elastic's recommendation on keeping services up and running with real-time vi...FaithWestdorp https://community.elastic.co/events/details/elastic-amer-virtual-presents-elastics-recommendation-on-keeping-services-up-and-running-with-real-time-visibility/
Open Source Insight: SCA for DevOps, DHS Security, Securing Open Source for G...



Open Source Insight: SCA for DevOps, DHS Security, Securing Open Source for G...Black Duck by Synopsys It’s an acronym-filled issue of Open Source Insight, as we look at the question of SCA (software composition analysis) and how it fits into the DevOps environment. The DHS (Department of Homeland Security) has concerning security gaps, according to its OIG (Office of Inspector General). Can the CVE (Common Vulnerabilities and Exposures) gap be closed? The GDPR (General Data Protection Regulation) is bearing down on us like a freight train, and it’s past time to include open source security into your GDPR plans.
Plus, an intro to the Open Hub community, looking at security for blockchain apps, and best practices for open source security in container environments are all featured in this week’s cybersecurity and open source security news.
You Can’t Live Without Open Source - Results from the Open Source 360 Survey



You Can’t Live Without Open Source - Results from the Open Source 360 SurveyBlack Duck by Synopsys Today, open source drives technology and development, and its worldwide adoption ranges from companies with a single employee to large corporations like Microsoft and Apple. All of these organizations rely on open source to innovate, reduce development costs, and speed time to market. Recent research reports point out that open source comprises 80% to 90% of the code in a typical application. Our Open Source 360° survey provides an update on the rapid evolution of open source development, use and management.
The 2017 Open Source 360° survey was conducted through Black Duck’s Center for Open Source Research & Innovation (COSRI), focusing on four important areas of open source – usage, risk, contributions and governance/policies. Our respondents include input from new players, established leaders, and influencers across vertical markets and communities. This range of respondents drives broad industry awareness and discussions of these key issues.
DevOps Challenges and Version Control



DevOps Challenges and Version ControlPerforce This document summarizes the results of a survey on DevOps challenges and version control. The survey found that the top DevOps challenges companies face are continuous integration/delivery, managing build artifacts, and managing projects, repositories and permissions. Effective version control was seen as key to overcoming these challenges. The survey showed that many teams commit code daily but have issues with integration and delivery speeds. It also found that non-source assets are increasingly stored in version control systems. The document concludes that selecting the right version control system can help solve many common DevOps challenges that companies face.
Secure application deployment in the age of continuous delivery



Secure application deployment in the age of continuous deliveryTim Mackey As presented at Open Source Open Standards (GovNet) (http://opensourceconference.co.uk/), this deck covers some of the material which operators of open source data centers and users of container and cloud technologies should be aware of when seeking to be security conscious.
Traditionally, when datacentre operators talk about application security, there has been a tendency to focus on issues related to key management, firewalls and data access. By contrast, application developers have a security focus which is more aligned with code analysis and fuzzing techniques. The reality is, secure application deployment principles extend from the infrastructure layer through the application and include how the application is deployed. With the prevalence of continuous deployment, it’s imperative to focus efforts on what attackers’ view as vulnerable; particularly in an environment where new exploits are being disclosed almost daily.
In this session we’ll present:
- How known vulnerabilities can make their way into production deployments
- How vulnerability impact is maximized
- A methodology for ensuring deployment of vulnerable code can be minimized
- A methodology to minimize the potential for vulnerable code to be redistributed
Secure application deployment in the age of continuous delivery



Secure application deployment in the age of continuous deliveryBlack Duck by Synopsys As presented by Tim Mackey, Senior Technical Evangelist at Black Duck Software, at Open Source Open Standards (GovNet) (http://opensourceconference.co.uk/), this deck covers some of the material which operators of open source data centers and users of container and cloud technologies should be aware of when seeking to be security conscious.
Traditionally, when datacentre operators talk about application security, there has been a tendency to focus on issues related to key management, firewalls and data access. By contrast, application developers have a security focus which is more aligned with code analysis and fuzzing techniques. The reality is, secure application deployment principles extend from the infrastructure layer through the application and include how the application is deployed. With the prevalence of continuous deployment, it’s imperative to focus efforts on what attackers’ view as vulnerable; particularly in an environment where new exploits are being disclosed almost daily.
In this session we’ll present:
- How known vulnerabilities can make their way into production deployments
- How vulnerability impact is maximized
- A methodology for ensuring deployment of vulnerable code can be minimized
- A methodology to minimize the potential for vulnerable code to be redistributed
The Top 3 Strategies To Reduce Your Open Source Security Risks - A WhiteSour...



The Top 3 Strategies To Reduce Your Open Source Security Risks - A WhiteSour...WhiteSource In our latest webinar with IMA, we presented The Top 3 Strategies to Reduce Your Open Source Security Risks.
OSS has taken over the enterprise: The top five OSS trends of 2015



OSS has taken over the enterprise: The top five OSS trends of 2015Rogue Wave Software It’s everywhere. From your phone to the enterprise, open source software (OSS) is running far and wide. Gartner predicts that by 2016, 99 percent of Global 2000 enterprises will use open source in mission-critical software. While it’s free, easy to find, and pushes software to the market faster, it’s vital to understand how to use OSS safely.
Join Richard Sherrard, director of product management at Rogue Wave, for a live webinar reviewing the top five OSS trends of 2015. From OSS discovery, to risk, and governance, we’ll take a deep dive into the trends we’ve noticed this year while providing you with some predictions for 2016.
In this webinar you’ll learn how to:
-Discover the OSS in your codebase to ensure that code is free of bugs, security vulnerabilities, and license conflicts
-Implement controls on OSS usage at your organization
-Create a multi-tier approach to OSS risk reduction with open source tools, static code analysis and dynamic analysis
Watch the webinar recording now: https://www.brighttalk.com/webcast/12285/164531
Linux and the Open Source- D Sarkar



Linux and the Open Source- D SarkarDipayan Sarkar The document discusses open source software. It defines open source software as software whose source code is publicly accessible and available for modification or enhancement by anyone. It then provides several benefits and reasons for using open source software, including improved security, quality, customizability, freedom from vendor lock-in, flexibility, interoperability, auditability, strong support communities, and lower costs compared to proprietary software. The document also discusses India's policy promoting the adoption of open source software by government organizations.
Pentest is yesterday, DevSecOps is tomorrow



Pentest is yesterday, DevSecOps is tomorrowAmien Harisen Rosyandino Introduction to General DevSecOps, how it differentiate with DevOps and the correlation between Agile DevOps and DevSecOps
The Growing Research that Open Source Owns the Future in Cloud



The Growing Research that Open Source Owns the Future in CloudAll Things Open Presented by: Chris Ferris & Deb Bryant
Presented at the All Things Open 2021
Raleigh, NC, USA
Raleigh Convention Center
Abstract: The latest research on open source shows the growing need and value of the skills as well as the advancement of open source in the enterprise stack. Join Deb Bryant, Senior Director, Open Source Project Office at Red Hat and Chris Ferris, CTO, Open Technologies at IBM to cover the latest global research on Open Source. Red Hat and IBM embarked on research in 2020 that have insights on the state of open source, its practitioners and its future. 65% of developers consider skills and knowledge related to underlying Open Source cloud technologies to be more beneficial to their careers, than skills related to any specific cloud. Join us to cover some of the critical questions and discoveries which showed strong support for your skills in key open source technologies. While the widespread use of free and open source software and migration to the cloud are the two most significant shifts characterizing computing in the last two decades, open source technology is still the root of that innovation. In the era of hybrid cloud, open source is maintaining and increasing its influence. Our research suggests that over the long term, recruiting skills in the most fundamental open source tools and libraries will likely provide major benefits to both professionals and their organizations.
Empowering Financial Institutions to Use Open Source With Confidence



Empowering Financial Institutions to Use Open Source With ConfidenceWhiteSource The days when financial institutions relied solemnly on proprietary code are over. Today, even the largest financial services firms have realized the benefits of using open source technology to build powerful, innovative applications at a reduced time-to-market. However, the financial services industry faces strict regulatory requirements that present it with a unique set of challenges, especially when it comes to open source usage (both consumption and contribution).
FINOS is a non-profit organization whose purpose is to accelerate collaboration and innovation in financial services through the adoption of open source software, standards and best practices. Together with WhiteSource, they are able to provide a safe environment for developers to use open source components freely and fearlessly.
Join FINOS and WhiteSource as they discuss:
The challenges of open source usage
The state of open source vulnerabilities management
How FINOS uses WhiteSource to ensure the security and IP compliance of FINOS-produced open source software
WhiteSource and FINOS: Empowering Financial Institutions to use Open Source W...



WhiteSource and FINOS: Empowering Financial Institutions to use Open Source W...DevOps.com The days when financial institutions relied solemnly on proprietary code are over. Today, even the largest financial services firms have realized the benefits of using open source technology to build powerful, innovative applications at a reduced time-to-market. However, the financial services industry faces strict regulatory requirements that present it with a unique set of challenges, especially when it comes to open source usage (both consumption and contribution).
FINOS is a non-profit organization whose purpose is to accelerate collaboration and innovation in financial services through the adoption of open source software, standards and best practices. Together with WhiteSource, they are able to provide a safe environment for developers to use open source components freely and fearlessly.
Join FINOS and WhiteSource as they discuss:
The challenges of open source usage
The state of open source vulnerabilities management
How FINOS uses WhiteSource to ensure the security and IP compliance of FINOS-produced open source software
Open Source All The Things



Open Source All The ThingsAll Things Open Presented at All Things Open 2022
Presented by Andrew Zigler
Title: Open Source All The Things
Abstract: Open source software is increasingly becoming the number one choice for software developers worldwide because it's considered best in class for its improved security, extensibility and customization, and high-quality tooling. Wouldn’t it be great if your entire software development lifecycle could take place on open source software?
The good news is that it absolutely can! Modern open source tools give your development team everything they need to be productive, from initial planning to production deployment. In this session, you’ll learn how to use 100% open source software to set up a complete development pipeline that includes source code management, CI/CD, service monitoring and notifications, team communications and collaboration, project and task management, and process automation. Attendees will come away with an arsenal of tools they can deploy for their team to become more efficient at the software development process.
Target Audience:
Anyone who works on a software development team and wants to find ways to make their team more productive and facilitate better collaboration. This session is ideal for developers and technical managers who want to use open source tools to reduce context switching and increase the focus time they have to write code.
DevOps for Highly Regulated Environments



DevOps for Highly Regulated EnvironmentsDevOps.com Financial institutions, medical groups, governmental organizations, automotive companies… these types of entities all have unique and sometimes difficult-to-meet regulations. You may be required to have fine-grained auditability of your SDLC or maintain specific third-party integrations. Security models may be heightened, or certain types of compliance processes maintained. So how are we supposed to “do the DevOps” when we have so many things to worry about? In this webinar, we’ll explore some ways that you can adopt DevOps best practices and even (gasp!) thrive when building your DevOps and DevSecOps pipelines in highly-regulated industries.
SCS DevSecOps Seminar - State of DevSecOps



SCS DevSecOps Seminar - State of DevSecOpsStefan Streichsbier - Stefan Streichsbier is the CEO of GuardRails and a professional white-hat hacker who has identified severe shortcomings in security processes and technologies, leading him to create GuardRails.
- The document discusses the evolution of DevOps and increasing complexity, the state of security and how it needs to fit within modern development workflows, and introduces the concept of DevSecOps to address shortcomings and better integrate security.
- Key aspects of DevSecOps discussed include how to create, test, and monitor secure applications and empower development teams to build security in from the start rather than see it as a separate function. Automated security tools and the need to reduce noise and improve usability for developers is also
State of DevSecOps - DevSecOpsDays 2019



State of DevSecOps - DevSecOpsDays 2019Stefan Streichsbier This talk provides a brief history of how DevOps has enabled tech companies to become unicorns. Furthermore, is Security in DevOps important, who is responsible and what can teams do make security a competitive advantage.
Open Source Security and ChatGPT-Published.pdf



Open Source Security and ChatGPT-Published.pdfJavier Perez 1) ChatGPT and other AI tools allow developers to produce code more quickly and efficiently but the validity and security of generated code must still be verified by developers.
2) While AI can introduce vulnerabilities if misused, it can also help find vulnerabilities when used properly under a developer's guidance.
3) Open source security involves continuously monitoring libraries and dependencies for vulnerabilities and applying patches through practices like software bill of materials and regular scans.
Open Source North - State of OSS in Organizations



Open Source North - State of OSS in OrganizationsJavier Perez This document discusses the state of open source software usage in organizations based on a survey. Some key findings include:
- Over 76% of organizations increased their use of open source in the last year, with 40.59% increasing significantly.
- The top reasons for using open source are access to innovation, cost reduction due to no licensing fees, and reducing vendor lock-in.
- Common challenges with open source include keeping up with updates and patches, installation upgrades, and ensuring sufficient personnel experience.
- Open source usage varies by industry, with retail having the highest usage at 60% and manufacturing the lowest rate of experts at under 30%.
Ad
More Related Content
Similar to All Things Open 2022 - State of OSS Security & Support (20)
From Zero to DevSecOps: How to Implement Security at the Speed of DevOps 



From Zero to DevSecOps: How to Implement Security at the Speed of DevOps WhiteSource Your organization has already embraced the DevOps methodology? That’s a great start. But what about security?
It’s a fact - many organizations fear that adding security to their DevOps practices will severely slow down their development processes. But this doesn’t need to be the case.
Tune in to hear Jeff Martin, Senior Director of Product at WhiteSource and Anders Wallgren, VP of Technology Strategy at Cloudbees, as they discuss:
- Why traditional DevOps has shifted, and what this will mean
- Who should own security in the age of DevOps
- Which tools and strategies are needed to implement continuous security throughout the DevOps pipeline
Secure DevOPS Implementation Guidance



Secure DevOPS Implementation GuidanceTej Luthra The document provides an overview of secure DevOps practices including:
- Integrating security into the software development lifecycle from design through deployment.
- Using automation and continuous integration/delivery practices to continuously assess and remediate vulnerabilities.
- Implementing secure configurations for hardware and software and keeping systems updated with the latest patches.
- Performing security testing using tools that can identify vulnerabilities during the development process.
- Controlling administrative privileges and secrets management in an "infrastructure as code" environment.
CI/CD pipeline security from start to finish with WhiteSource & CircleCI



CI/CD pipeline security from start to finish with WhiteSource & CircleCIWhiteSource This document provides an agenda for a webinar on securing CI/CD pipelines from start to finish with CircleCI and WhiteSource. The agenda includes brief introductions to CircleCI and WhiteSource, an overview of CircleCI Orbs and how they can simplify integrations, a discussion of the state of open source usage and security, and a demo of WhiteSource scanning functionality directly within a CircleCI pipeline using an Orb.
Elastic's recommendation on keeping services up and running with real-time vi...



Elastic's recommendation on keeping services up and running with real-time vi...FaithWestdorp https://community.elastic.co/events/details/elastic-amer-virtual-presents-elastics-recommendation-on-keeping-services-up-and-running-with-real-time-visibility/
Open Source Insight: SCA for DevOps, DHS Security, Securing Open Source for G...



Open Source Insight: SCA for DevOps, DHS Security, Securing Open Source for G...Black Duck by Synopsys It’s an acronym-filled issue of Open Source Insight, as we look at the question of SCA (software composition analysis) and how it fits into the DevOps environment. The DHS (Department of Homeland Security) has concerning security gaps, according to its OIG (Office of Inspector General). Can the CVE (Common Vulnerabilities and Exposures) gap be closed? The GDPR (General Data Protection Regulation) is bearing down on us like a freight train, and it’s past time to include open source security into your GDPR plans.
Plus, an intro to the Open Hub community, looking at security for blockchain apps, and best practices for open source security in container environments are all featured in this week’s cybersecurity and open source security news.
You Can’t Live Without Open Source - Results from the Open Source 360 Survey



You Can’t Live Without Open Source - Results from the Open Source 360 SurveyBlack Duck by Synopsys Today, open source drives technology and development, and its worldwide adoption ranges from companies with a single employee to large corporations like Microsoft and Apple. All of these organizations rely on open source to innovate, reduce development costs, and speed time to market. Recent research reports point out that open source comprises 80% to 90% of the code in a typical application. Our Open Source 360° survey provides an update on the rapid evolution of open source development, use and management.
The 2017 Open Source 360° survey was conducted through Black Duck’s Center for Open Source Research & Innovation (COSRI), focusing on four important areas of open source – usage, risk, contributions and governance/policies. Our respondents include input from new players, established leaders, and influencers across vertical markets and communities. This range of respondents drives broad industry awareness and discussions of these key issues.
DevOps Challenges and Version Control



DevOps Challenges and Version ControlPerforce This document summarizes the results of a survey on DevOps challenges and version control. The survey found that the top DevOps challenges companies face are continuous integration/delivery, managing build artifacts, and managing projects, repositories and permissions. Effective version control was seen as key to overcoming these challenges. The survey showed that many teams commit code daily but have issues with integration and delivery speeds. It also found that non-source assets are increasingly stored in version control systems. The document concludes that selecting the right version control system can help solve many common DevOps challenges that companies face.
Secure application deployment in the age of continuous delivery



Secure application deployment in the age of continuous deliveryTim Mackey As presented at Open Source Open Standards (GovNet) (http://opensourceconference.co.uk/), this deck covers some of the material which operators of open source data centers and users of container and cloud technologies should be aware of when seeking to be security conscious.
Traditionally, when datacentre operators talk about application security, there has been a tendency to focus on issues related to key management, firewalls and data access. By contrast, application developers have a security focus which is more aligned with code analysis and fuzzing techniques. The reality is, secure application deployment principles extend from the infrastructure layer through the application and include how the application is deployed. With the prevalence of continuous deployment, it’s imperative to focus efforts on what attackers’ view as vulnerable; particularly in an environment where new exploits are being disclosed almost daily.
In this session we’ll present:
- How known vulnerabilities can make their way into production deployments
- How vulnerability impact is maximized
- A methodology for ensuring deployment of vulnerable code can be minimized
- A methodology to minimize the potential for vulnerable code to be redistributed
Secure application deployment in the age of continuous delivery



Secure application deployment in the age of continuous deliveryBlack Duck by Synopsys As presented by Tim Mackey, Senior Technical Evangelist at Black Duck Software, at Open Source Open Standards (GovNet) (http://opensourceconference.co.uk/), this deck covers some of the material which operators of open source data centers and users of container and cloud technologies should be aware of when seeking to be security conscious.
Traditionally, when datacentre operators talk about application security, there has been a tendency to focus on issues related to key management, firewalls and data access. By contrast, application developers have a security focus which is more aligned with code analysis and fuzzing techniques. The reality is, secure application deployment principles extend from the infrastructure layer through the application and include how the application is deployed. With the prevalence of continuous deployment, it’s imperative to focus efforts on what attackers’ view as vulnerable; particularly in an environment where new exploits are being disclosed almost daily.
In this session we’ll present:
- How known vulnerabilities can make their way into production deployments
- How vulnerability impact is maximized
- A methodology for ensuring deployment of vulnerable code can be minimized
- A methodology to minimize the potential for vulnerable code to be redistributed
The Top 3 Strategies To Reduce Your Open Source Security Risks - A WhiteSour...



The Top 3 Strategies To Reduce Your Open Source Security Risks - A WhiteSour...WhiteSource In our latest webinar with IMA, we presented The Top 3 Strategies to Reduce Your Open Source Security Risks.
OSS has taken over the enterprise: The top five OSS trends of 2015



OSS has taken over the enterprise: The top five OSS trends of 2015Rogue Wave Software It’s everywhere. From your phone to the enterprise, open source software (OSS) is running far and wide. Gartner predicts that by 2016, 99 percent of Global 2000 enterprises will use open source in mission-critical software. While it’s free, easy to find, and pushes software to the market faster, it’s vital to understand how to use OSS safely.
Join Richard Sherrard, director of product management at Rogue Wave, for a live webinar reviewing the top five OSS trends of 2015. From OSS discovery, to risk, and governance, we’ll take a deep dive into the trends we’ve noticed this year while providing you with some predictions for 2016.
In this webinar you’ll learn how to:
-Discover the OSS in your codebase to ensure that code is free of bugs, security vulnerabilities, and license conflicts
-Implement controls on OSS usage at your organization
-Create a multi-tier approach to OSS risk reduction with open source tools, static code analysis and dynamic analysis
Watch the webinar recording now: https://www.brighttalk.com/webcast/12285/164531
Linux and the Open Source- D Sarkar



Linux and the Open Source- D SarkarDipayan Sarkar The document discusses open source software. It defines open source software as software whose source code is publicly accessible and available for modification or enhancement by anyone. It then provides several benefits and reasons for using open source software, including improved security, quality, customizability, freedom from vendor lock-in, flexibility, interoperability, auditability, strong support communities, and lower costs compared to proprietary software. The document also discusses India's policy promoting the adoption of open source software by government organizations.
Pentest is yesterday, DevSecOps is tomorrow



Pentest is yesterday, DevSecOps is tomorrowAmien Harisen Rosyandino Introduction to General DevSecOps, how it differentiate with DevOps and the correlation between Agile DevOps and DevSecOps
The Growing Research that Open Source Owns the Future in Cloud



The Growing Research that Open Source Owns the Future in CloudAll Things Open Presented by: Chris Ferris & Deb Bryant
Presented at the All Things Open 2021
Raleigh, NC, USA
Raleigh Convention Center
Abstract: The latest research on open source shows the growing need and value of the skills as well as the advancement of open source in the enterprise stack. Join Deb Bryant, Senior Director, Open Source Project Office at Red Hat and Chris Ferris, CTO, Open Technologies at IBM to cover the latest global research on Open Source. Red Hat and IBM embarked on research in 2020 that have insights on the state of open source, its practitioners and its future. 65% of developers consider skills and knowledge related to underlying Open Source cloud technologies to be more beneficial to their careers, than skills related to any specific cloud. Join us to cover some of the critical questions and discoveries which showed strong support for your skills in key open source technologies. While the widespread use of free and open source software and migration to the cloud are the two most significant shifts characterizing computing in the last two decades, open source technology is still the root of that innovation. In the era of hybrid cloud, open source is maintaining and increasing its influence. Our research suggests that over the long term, recruiting skills in the most fundamental open source tools and libraries will likely provide major benefits to both professionals and their organizations.
Empowering Financial Institutions to Use Open Source With Confidence



Empowering Financial Institutions to Use Open Source With ConfidenceWhiteSource The days when financial institutions relied solemnly on proprietary code are over. Today, even the largest financial services firms have realized the benefits of using open source technology to build powerful, innovative applications at a reduced time-to-market. However, the financial services industry faces strict regulatory requirements that present it with a unique set of challenges, especially when it comes to open source usage (both consumption and contribution).
FINOS is a non-profit organization whose purpose is to accelerate collaboration and innovation in financial services through the adoption of open source software, standards and best practices. Together with WhiteSource, they are able to provide a safe environment for developers to use open source components freely and fearlessly.
Join FINOS and WhiteSource as they discuss:
The challenges of open source usage
The state of open source vulnerabilities management
How FINOS uses WhiteSource to ensure the security and IP compliance of FINOS-produced open source software
WhiteSource and FINOS: Empowering Financial Institutions to use Open Source W...



WhiteSource and FINOS: Empowering Financial Institutions to use Open Source W...DevOps.com The days when financial institutions relied solemnly on proprietary code are over. Today, even the largest financial services firms have realized the benefits of using open source technology to build powerful, innovative applications at a reduced time-to-market. However, the financial services industry faces strict regulatory requirements that present it with a unique set of challenges, especially when it comes to open source usage (both consumption and contribution).
FINOS is a non-profit organization whose purpose is to accelerate collaboration and innovation in financial services through the adoption of open source software, standards and best practices. Together with WhiteSource, they are able to provide a safe environment for developers to use open source components freely and fearlessly.
Join FINOS and WhiteSource as they discuss:
The challenges of open source usage
The state of open source vulnerabilities management
How FINOS uses WhiteSource to ensure the security and IP compliance of FINOS-produced open source software
Open Source All The Things



Open Source All The ThingsAll Things Open Presented at All Things Open 2022
Presented by Andrew Zigler
Title: Open Source All The Things
Abstract: Open source software is increasingly becoming the number one choice for software developers worldwide because it's considered best in class for its improved security, extensibility and customization, and high-quality tooling. Wouldn’t it be great if your entire software development lifecycle could take place on open source software?
The good news is that it absolutely can! Modern open source tools give your development team everything they need to be productive, from initial planning to production deployment. In this session, you’ll learn how to use 100% open source software to set up a complete development pipeline that includes source code management, CI/CD, service monitoring and notifications, team communications and collaboration, project and task management, and process automation. Attendees will come away with an arsenal of tools they can deploy for their team to become more efficient at the software development process.
Target Audience:
Anyone who works on a software development team and wants to find ways to make their team more productive and facilitate better collaboration. This session is ideal for developers and technical managers who want to use open source tools to reduce context switching and increase the focus time they have to write code.
DevOps for Highly Regulated Environments



DevOps for Highly Regulated EnvironmentsDevOps.com Financial institutions, medical groups, governmental organizations, automotive companies… these types of entities all have unique and sometimes difficult-to-meet regulations. You may be required to have fine-grained auditability of your SDLC or maintain specific third-party integrations. Security models may be heightened, or certain types of compliance processes maintained. So how are we supposed to “do the DevOps” when we have so many things to worry about? In this webinar, we’ll explore some ways that you can adopt DevOps best practices and even (gasp!) thrive when building your DevOps and DevSecOps pipelines in highly-regulated industries.
SCS DevSecOps Seminar - State of DevSecOps



SCS DevSecOps Seminar - State of DevSecOpsStefan Streichsbier - Stefan Streichsbier is the CEO of GuardRails and a professional white-hat hacker who has identified severe shortcomings in security processes and technologies, leading him to create GuardRails.
- The document discusses the evolution of DevOps and increasing complexity, the state of security and how it needs to fit within modern development workflows, and introduces the concept of DevSecOps to address shortcomings and better integrate security.
- Key aspects of DevSecOps discussed include how to create, test, and monitor secure applications and empower development teams to build security in from the start rather than see it as a separate function. Automated security tools and the need to reduce noise and improve usability for developers is also
State of DevSecOps - DevSecOpsDays 2019



State of DevSecOps - DevSecOpsDays 2019Stefan Streichsbier This talk provides a brief history of how DevOps has enabled tech companies to become unicorns. Furthermore, is Security in DevOps important, who is responsible and what can teams do make security a competitive advantage.
Open Source Insight: SCA for DevOps, DHS Security, Securing Open Source for G...



Open Source Insight: SCA for DevOps, DHS Security, Securing Open Source for G...Black Duck by Synopsys
More from Javier Perez (7)
Open Source Security and ChatGPT-Published.pdf



Open Source Security and ChatGPT-Published.pdfJavier Perez 1) ChatGPT and other AI tools allow developers to produce code more quickly and efficiently but the validity and security of generated code must still be verified by developers.
2) While AI can introduce vulnerabilities if misused, it can also help find vulnerabilities when used properly under a developer's guidance.
3) Open source security involves continuously monitoring libraries and dependencies for vulnerabilities and applying patches through practices like software bill of materials and regular scans.
Open Source North - State of OSS in Organizations



Open Source North - State of OSS in OrganizationsJavier Perez This document discusses the state of open source software usage in organizations based on a survey. Some key findings include:
- Over 76% of organizations increased their use of open source in the last year, with 40.59% increasing significantly.
- The top reasons for using open source are access to innovation, cost reduction due to no licensing fees, and reducing vendor lock-in.
- Common challenges with open source include keeping up with updates and patches, installation upgrades, and ensuring sufficient personnel experience.
- Open source usage varies by industry, with retail having the highest usage at 60% and manufacturing the lowest rate of experts at under 30%.
Intro to open source - 101 presentation



Intro to open source - 101 presentationJavier Perez This document provides an overview of open-source software and how to get started with it. It discusses the history of open-source software dating back to 1955. It defines key open-source concepts like licenses, roles, and best practices for contributing. It also highlights the large open-source ecosystems existing today and the top companies contributing to open-source. The document aims to address common questions or concerns about open-source software.
Open source and AI keynote



Open source and AI keynoteJavier Perez The document discusses open source software and IBM Z. It notes that the latest innovations in areas like augmented reality, virtual reality, and artificial intelligence are all based on open source technologies. It highlights some key open source statistics like over 210 million repositories and 500,000 projects. The rest of the document focuses on encouraging open source contribution and consumption, providing examples of open source projects relevant to IBM Z, and use cases that apply machine learning to real world problems using open source tools and libraries.
SacHacks Keynote Open Source Software and IBM Z



SacHacks Keynote Open Source Software and IBM ZJavier Perez The document discusses open source software and how it relates to IBM Z. It notes that the latest innovations in areas like AI, ML and blockchain are all based on open source technologies. There are millions of open source projects, libraries, and over 50 million developers working on open source software. The document encourages both consuming and contributing to open source software and provides examples of how to get involved through activities like documentation, testing, translations and more. It also highlights several specific open source projects relevant to IBM Z.
All You need to Know about Secure Coding with Open Source Software



All You need to Know about Secure Coding with Open Source SoftwareJavier Perez This document provides an overview of secure coding with open source software. It discusses that open source software is now mainstream, used in many modern innovations. It describes what open source software is, the explosive growth of open source, and popular open source libraries and dependencies. The document outlines roles in open source projects and how to contribute. It discusses security considerations like vulnerabilities in open source libraries and the increased risk with reusing libraries. The document provides examples of popular open source projects like Angular.js and their contributions and vulnerabilities. It emphasizes the real risk is not a lack of fixes but the lack of speed in applying fixes. The importance of software composition analysis and vulnerability management for open source is highlighted.
Guide to open source 



Guide to open source Javier Perez This document provides an overview of open source software and recommendations for companies adopting open source. It discusses how open source can accelerate projects and attract talent. It profiles companies like Adobe, Netflix, Oracle, Samsung, and Microsoft that contribute to open source despite not being commonly associated with it. The document outlines how to launch an open source project, including using an open source license, README, contribution guidelines, and code of conduct. It also discusses roles in open source projects and various open source business models. The recommendations encourage companies to publish independent components on GitHub, take releases from GitHub, and create developer websites to engage with the open source community.
Ad
Recently uploaded (20)
How to Optimize Your AWS Environment for Improved Cloud Performance



How to Optimize Your AWS Environment for Improved Cloud PerformanceThousandEyes How to Optimize Your AWS Environment for Improved Cloud Performance
How Valletta helped healthcare SaaS to transform QA and compliance to grow wi...



How Valletta helped healthcare SaaS to transform QA and compliance to grow wi...Egor Kaleynik This case study explores how we partnered with a mid-sized U.S. healthcare SaaS provider to help them scale from a successful pilot phase to supporting over 10,000 users—while meeting strict HIPAA compliance requirements.
Faced with slow, manual testing cycles, frequent regression bugs, and looming audit risks, their growth was at risk. Their existing QA processes couldn’t keep up with the complexity of real-time biometric data handling, and earlier automation attempts had failed due to unreliable tools and fragmented workflows.
We stepped in to deliver a full QA and DevOps transformation. Our team replaced their fragile legacy tests with Testim’s self-healing automation, integrated Postman and OWASP ZAP into Jenkins pipelines for continuous API and security validation, and leveraged AWS Device Farm for real-device, region-specific compliance testing. Custom deployment scripts gave them control over rollouts without relying on heavy CI/CD infrastructure.
The result? Test cycle times were reduced from 3 days to just 8 hours, regression bugs dropped by 40%, and they passed their first HIPAA audit without issue—unlocking faster contract signings and enabling them to expand confidently. More than just a technical upgrade, this project embedded compliance into every phase of development, proving that SaaS providers in regulated industries can scale fast and stay secure.
Revolutionizing Residential Wi-Fi PPT.pptx



Revolutionizing Residential Wi-Fi PPT.pptxnidhisingh691197 Discover why Wi-Fi 7 is set to transform wireless networking and how Router Architects is leading the way with next-gen router designs built for speed, reliability, and innovation.
F-Secure Freedome VPN 2025 Crack Plus Activation New Version



F-Secure Freedome VPN 2025 Crack Plus Activation New Versionsaimabibi60507 Copy & Past Link 👉👉
https://dr-up-community.info/
F-Secure Freedome VPN is a virtual private network service developed by F-Secure, a Finnish cybersecurity company. It offers features such as Wi-Fi protection, IP address masking, browsing protection, and a kill switch to enhance online privacy and security .
Adobe Lightroom Classic Crack FREE Latest link 2025



Adobe Lightroom Classic Crack FREE Latest link 2025kashifyounis067 🌍📱👉COPY LINK & PASTE ON GOOGLE http://drfiles.net/ 👈🌍
Adobe Lightroom Classic is a desktop-based software application for editing and managing digital photos. It focuses on providing users with a powerful and comprehensive set of tools for organizing, editing, and processing their images on their computer. Unlike the newer Lightroom, which is cloud-based, Lightroom Classic stores photos locally on your computer and offers a more traditional workflow for professional photographers.
Here's a more detailed breakdown:
Key Features and Functions:
Organization:
Lightroom Classic provides robust tools for organizing your photos, including creating collections, using keywords, flags, and color labels.
Editing:
It offers a wide range of editing tools for making adjustments to color, tone, and more.
Processing:
Lightroom Classic can process RAW files, allowing for significant adjustments and fine-tuning of images.
Desktop-Focused:
The application is designed to be used on a computer, with the original photos stored locally on the hard drive.
Non-Destructive Editing:
Edits are applied to the original photos in a non-destructive way, meaning the original files remain untouched.
Key Differences from Lightroom (Cloud-Based):
Storage Location:
Lightroom Classic stores photos locally on your computer, while Lightroom stores them in the cloud.
Workflow:
Lightroom Classic is designed for a desktop workflow, while Lightroom is designed for a cloud-based workflow.
Connectivity:
Lightroom Classic can be used offline, while Lightroom requires an internet connection to sync and access photos.
Organization:
Lightroom Classic offers more advanced organization features like Collections and Keywords.
Who is it for?
Professional Photographers:
PCMag notes that Lightroom Classic is a popular choice among professional photographers who need the flexibility and control of a desktop-based application.
Users with Large Collections:
Those with extensive photo collections may prefer Lightroom Classic's local storage and robust organization features.
Users who prefer a traditional workflow:
Users who prefer a more traditional desktop workflow, with their original photos stored on their computer, will find Lightroom Classic a good fit.
Exceptional Behaviors: How Frequently Are They Tested? (AST 2025)



Exceptional Behaviors: How Frequently Are They Tested? (AST 2025)Andre Hora Exceptions allow developers to handle error cases expected to occur infrequently. Ideally, good test suites should test both normal and exceptional behaviors to catch more bugs and avoid regressions. While current research analyzes exceptions that propagate to tests, it does not explore other exceptions that do not reach the tests. In this paper, we provide an empirical study to explore how frequently exceptional behaviors are tested in real-world systems. We consider both exceptions that propagate to tests and the ones that do not reach the tests. For this purpose, we run an instrumented version of test suites, monitor their execution, and collect information about the exceptions raised at runtime. We analyze the test suites of 25 Python systems, covering 5,372 executed methods, 17.9M calls, and 1.4M raised exceptions. We find that 21.4% of the executed methods do raise exceptions at runtime. In methods that raise exceptions, on the median, 1 in 10 calls exercise exceptional behaviors. Close to 80% of the methods that raise exceptions do so infrequently, but about 20% raise exceptions more frequently. Finally, we provide implications for researchers and practitioners. We suggest developing novel tools to support exercising exceptional behaviors and refactoring expensive try/except blocks. We also call attention to the fact that exception-raising behaviors are not necessarily “abnormal” or rare.
EASEUS Partition Master Crack + License Code



EASEUS Partition Master Crack + License Codeaneelaramzan63 Copy & Paste On Google >>> https://dr-up-community.info/
EASEUS Partition Master Final with Crack and Key Download If you are looking for a powerful and easy-to-use disk partitioning software,
Solidworks Crack 2025 latest new + license code



Solidworks Crack 2025 latest new + license codeaneelaramzan63 Copy & Paste On Google >>> https://dr-up-community.info/
The two main methods for installing standalone licenses of SOLIDWORKS are clean installation and parallel installation (the process is different ...
Disable your internet connection to prevent the software from performing online checks during installation
Automation Techniques in RPA - UiPath Certificate



Automation Techniques in RPA - UiPath CertificateVICTOR MAESTRE RAMIREZ Automation Techniques in RPA - UiPath Certificate
Microsoft AI Nonprofit Use Cases and Live Demo_2025.04.30.pdf



Microsoft AI Nonprofit Use Cases and Live Demo_2025.04.30.pdfTechSoup In this webinar we will dive into the essentials of generative AI, address key AI concerns, and demonstrate how nonprofits can benefit from using Microsoft’s AI assistant, Copilot, to achieve their goals.
This event series to help nonprofits obtain Copilot skills is made possible by generous support from Microsoft.
What You’ll Learn in Part 2:
Explore real-world nonprofit use cases and success stories.
Participate in live demonstrations and a hands-on activity to see how you can use Microsoft 365 Copilot in your own work!
Who Watches the Watchmen (SciFiDevCon 2025)



Who Watches the Watchmen (SciFiDevCon 2025)Allon Mureinik Tests, especially unit tests, are the developers’ superheroes. They allow us to mess around with our code and keep us safe.
We often trust them with the safety of our codebase, but how do we know that we should? How do we know that this trust is well-deserved?
Enter mutation testing – by intentionally injecting harmful mutations into our code and seeing if they are caught by the tests, we can evaluate the quality of the safety net they provide. By watching the watchmen, we can make sure our tests really protect us, and we aren’t just green-washing our IDEs to a false sense of security.
Talk from SciFiDevCon 2025
https://www.scifidevcon.com/courses/2025-scifidevcon/contents/680efa43ae4f5
Douwan Crack 2025 new verson+ License code



Douwan Crack 2025 new verson+ License codeaneelaramzan63 Copy & Paste On Google >>> https://dr-up-community.info/
Douwan Preactivated Crack Douwan Crack Free Download. Douwan is a comprehensive software solution designed for data management and analysis.
Proactive Vulnerability Detection in Source Code Using Graph Neural Networks:...



Proactive Vulnerability Detection in Source Code Using Graph Neural Networks:...Ranjan Baisak As software complexity grows, traditional static analysis tools struggle to detect vulnerabilities with both precision and context—often triggering high false positive rates and developer fatigue. This article explores how Graph Neural Networks (GNNs), when applied to source code representations like Abstract Syntax Trees (ASTs), Control Flow Graphs (CFGs), and Data Flow Graphs (DFGs), can revolutionize vulnerability detection. We break down how GNNs model code semantics more effectively than flat token sequences, and how techniques like attention mechanisms, hybrid graph construction, and feedback loops significantly reduce false positives. With insights from real-world datasets and recent research, this guide shows how to build more reliable, proactive, and interpretable vulnerability detection systems using GNNs.
Avast Premium Security Crack FREE Latest Version 2025



Avast Premium Security Crack FREE Latest Version 2025mu394968 🌍📱👉COPY LINK & PASTE ON GOOGLE https://dr-kain-geera.info/👈🌍
Avast Premium Security is a paid subscription service that provides comprehensive online security and privacy protection for multiple devices. It includes features like antivirus, firewall, ransomware protection, and website scanning, all designed to safeguard against a wide range of online threats, according to Avast.
Key features of Avast Premium Security:
Antivirus: Protects against viruses, malware, and other malicious software, according to Avast.
Firewall: Controls network traffic and blocks unauthorized access to your devices, as noted by All About Cookies.
Ransomware protection: Helps prevent ransomware attacks, which can encrypt your files and hold them hostage.
Website scanning: Checks websites for malicious content before you visit them, according to Avast.
Email Guardian: Scans your emails for suspicious attachments and phishing attempts.
Multi-device protection: Covers up to 10 devices, including Windows, Mac, Android, and iOS, as stated by 2GO Software.
Privacy features: Helps protect your personal data and online privacy.
In essence, Avast Premium Security provides a robust suite of tools to keep your devices and online activity safe and secure, according to Avast.
TestMigrationsInPy: A Dataset of Test Migrations from Unittest to Pytest (MSR...



TestMigrationsInPy: A Dataset of Test Migrations from Unittest to Pytest (MSR...Andre Hora Unittest and pytest are the most popular testing frameworks in Python. Overall, pytest provides some advantages, including simpler assertion, reuse of fixtures, and interoperability. Due to such benefits, multiple projects in the Python ecosystem have migrated from unittest to pytest. To facilitate the migration, pytest can also run unittest tests, thus, the migration can happen gradually over time. However, the migration can be timeconsuming and take a long time to conclude. In this context, projects would benefit from automated solutions to support the migration process. In this paper, we propose TestMigrationsInPy, a dataset of test migrations from unittest to pytest. TestMigrationsInPy contains 923 real-world migrations performed by developers. Future research proposing novel solutions to migrate frameworks in Python can rely on TestMigrationsInPy as a ground truth. Moreover, as TestMigrationsInPy includes information about the migration type (e.g., changes in assertions or fixtures), our dataset enables novel solutions to be verified effectively, for instance, from simpler assertion migrations to more complex fixture migrations. TestMigrationsInPy is publicly available at: https://github.com/altinoalvesjunior/TestMigrationsInPy.
Top 10 Client Portal Software Solutions for 2025.docx



Top 10 Client Portal Software Solutions for 2025.docxPortli Discover the top 10 client portal software solutions for 2025. Streamline communication, ensure security, and enhance client experience.
Get & Download Wondershare Filmora Crack Latest [2025]![Get & Download Wondershare Filmora Crack Latest [2025]](https://cdn.slidesharecdn.com/ss_thumbnails/revolutionizingresidentialwi-fi-250422112639-60fb726f-250429170801-59e1b240-thumbnail.jpg?width=560&fit=bounds)
![Get & Download Wondershare Filmora Crack Latest [2025]](https://cdn.slidesharecdn.com/ss_thumbnails/revolutionizingresidentialwi-fi-250422112639-60fb726f-250429170801-59e1b240-thumbnail.jpg?width=560&fit=bounds)
![Get & Download Wondershare Filmora Crack Latest [2025]](https://cdn.slidesharecdn.com/ss_thumbnails/revolutionizingresidentialwi-fi-250422112639-60fb726f-250429170801-59e1b240-thumbnail.jpg?width=560&fit=bounds)
![Get & Download Wondershare Filmora Crack Latest [2025]](https://cdn.slidesharecdn.com/ss_thumbnails/revolutionizingresidentialwi-fi-250422112639-60fb726f-250429170801-59e1b240-thumbnail.jpg?width=560&fit=bounds)
Get & Download Wondershare Filmora Crack Latest [2025]saniaaftab72555 Copy & Past Link 👉👉
https://dr-up-community.info/
Wondershare Filmora is a video editing software and app designed for both beginners and experienced users. It's known for its user-friendly interface, drag-and-drop functionality, and a wide range of tools and features for creating and editing videos. Filmora is available on Windows, macOS, iOS (iPhone/iPad), and Android platforms.
Download YouTube By Click 2025 Free Full Activated



Download YouTube By Click 2025 Free Full Activatedsaniamalik72555 Copy & Past Link 👉👉
https://dr-up-community.info/
"YouTube by Click" likely refers to the ByClick Downloader software, a video downloading and conversion tool, specifically designed to download content from YouTube and other video platforms. It allows users to download YouTube videos for offline viewing and to convert them to different formats.
Mastering Fluent Bit: Ultimate Guide to Integrating Telemetry Pipelines with ...



Mastering Fluent Bit: Ultimate Guide to Integrating Telemetry Pipelines with ...Eric D. Schabell It's time you stopped letting your telemetry data pressure your budgets and get in the way of solving issues with agility! No more I say! Take back control of your telemetry data as we guide you through the open source project Fluent Bit. Learn how to manage your telemetry data from source to destination using the pipeline phases covering collection, parsing, aggregation, transformation, and forwarding from any source to any destination. Buckle up for a fun ride as you learn by exploring how telemetry pipelines work, how to set up your first pipeline, and exploring several common use cases that Fluent Bit helps solve. All this backed by a self-paced, hands-on workshop that attendees can pursue at home after this session (https://o11y-workshops.gitlab.io/workshop-fluentbit).
Adobe Illustrator Crack FREE Download 2025 Latest Version



Adobe Illustrator Crack FREE Download 2025 Latest Versionkashifyounis067 🌍📱👉COPY LINK & PASTE ON GOOGLE http://drfiles.net/ 👈🌍
Adobe Illustrator is a powerful, professional-grade vector graphics software used for creating a wide range of designs, including logos, icons, illustrations, and more. Unlike raster graphics (like photos), which are made of pixels, vector graphics in Illustrator are defined by mathematical equations, allowing them to be scaled up or down infinitely without losing quality.
Here's a more detailed explanation:
Key Features and Capabilities:
Vector-Based Design:
Illustrator's foundation is its use of vector graphics, meaning designs are created using paths, lines, shapes, and curves defined mathematically.
Scalability:
This vector-based approach allows for designs to be resized without any loss of resolution or quality, making it suitable for various print and digital applications.
Design Creation:
Illustrator is used for a wide variety of design purposes, including:
Logos and Brand Identity: Creating logos, icons, and other brand assets.
Illustrations: Designing detailed illustrations for books, magazines, web pages, and more.
Marketing Materials: Creating posters, flyers, banners, and other marketing visuals.
Web Design: Designing web graphics, including icons, buttons, and layouts.
Text Handling:
Illustrator offers sophisticated typography tools for manipulating and designing text within your graphics.
Brushes and Effects:
It provides a range of brushes and effects for adding artistic touches and visual styles to your designs.
Integration with Other Adobe Software:
Illustrator integrates seamlessly with other Adobe Creative Cloud apps like Photoshop, InDesign, and Dreamweaver, facilitating a smooth workflow.
Why Use Illustrator?
Professional-Grade Features:
Illustrator offers a comprehensive set of tools and features for professional design work.
Versatility:
It can be used for a wide range of design tasks and applications, making it a versatile tool for designers.
Industry Standard:
Illustrator is a widely used and recognized software in the graphic design industry.
Creative Freedom:
It empowers designers to create detailed, high-quality graphics with a high degree of control and precision.
Ad
All Things Open 2022 - State of OSS Security & Support
- 1. Image by Gerd Altmann from Pixabay Image by Gerd Altmann from Pixabay Javier Perez Chief Evangelist & Sr. Director Product Management, OpenLogic by Perforce The State of Open Source Software, Security & Support
- 2. Nice To Meet You! Chief Evangelist & Sr. Director Product Management @jperezp_bos javierperez.mozello.com www.linkedin.com/in/javierperez Javier Perez
- 3. 2.1M + 1,034 packages per day 504K + 157 packages per day 355K + 87 packages per day 410K + 276 packages per day 328K + 150 packages per day 173K + 15 packages per day Source: Oct 28, 2022 www.modulecounts.com
- 5. Has your organization increased the use of open source software over the last year? Yes Yes, significantly Remain the same Reduced the use of open source 41% 36% 22% 1.6% YES 77%
- 6. Open Source Support Open Source in Organizations & Government Open Source Security
- 7. Open Source SDLC Trends • Smaller Releases • CI/CD, Testing & Security Scan Automation • Reduced Number of Supported Releases • Reduced Long-Term Support • Challenging to maintain older versions • Backporting patches • Time consuming • Regression testing Constant Updates Shorter LTS
- 8. Release Cadence Long-Term Support and End-of-Life • AngularJS EOL • CentOS • Extended Support beyond LTS?
- 11. Risks of Ignoring End-of-Life • Unpatched CVEs means an ongoing and compounding risk of exploit • Incompatibility with newer software • No-compliance (internal policy or industry compliance) • Becoming more complex to upgrade or migrate in the future, more support required • Self Support Cost: Development resources away from their jobs, expertise required
- 12. Open Source Support Challenges Keeping up with updates & patches Installation upgrades & configuration Personnel experience & proficiency
- 13. • Constant releases and apply security patches • End-of-life versions Vulnerability Vulnerability Discovered Vulnerability Fixed Vulnerability Vulnerability Discovered Vulnerability Fixed Vulnerability V1.0.0 V1.0.1 V1.0.2 Keeping Up With Updates and Patches Example: OpenSSL releasing 3.0.7 today
- 14. Increased Awareness Open Source Security Today • Identify Inventory: Software Bill of Materials (SBOM) • Security Scans: Vulnerability Detection • Apply Fixes: Patches
- 15. • Open source libraries reusability • Depending on the Programming Language libraries can have up to 1000’s of dependencies • A real risk for all software when there are vulnerabilities in dependencies Dependencies and Vulnerabilities * Sources: graphcommons.com
- 16. Education Open Source Software Security Mobilization Plan Risk Assessment Top 10K OSS Digital Signatures Move to Memory Safe Languages Incident Response Team Coordinated Public Disclosure Code Reviews Top 200 OSS Industry Data Sharing SBOM Everywhere Enhance Package Management
- 17. ISO/IEC 5230 Open Chain Standard • Organization Level License Compliance for every OSS artifact • Documented process • SBOM verification • Open source community engagement License Risk
- 18. Open Source and US Government White House Executive Order on Improving Cybersecurity - Working Groups H.R. 7667 Medical Device Security Bill – Vulnerability detection and SBOMs directive The Federal Trade Commission (FTC) advise companies to patch Log4J – Legal Action
- 19. Open Source and US Government Cybersecurity and Infrastructure Security Agency (CISA) – Binding directive making vulnerability disclosure mandatory National Security Strategy - Aligning with Orgs & OSS US Senate Securing Open Source Software Act – Best practices assessment framework, OSPO, and hire OSS experts
- 20. Open Source Maturity in Organizations Desired Position /Efforts Time Consumers Adopting (cost, time, or modernize) Deploying and complying with licenses Participants Limited contributions to open source Increased use & adoption, business-critical Contributor Contributions to open source projects Investment in open source technologies Leader Launching new open projects & initiatives Establishing Open Source Program Office
- 21. Maturity in Organizations by the Numbers Retail has the highest OSS Usage at 60% Manufacturing with the Lowest Rate of Experts 30% Banking, Insurance, Financial Services with most Innersources 19% Healthcare and Pharma with the Highest Rate of OSPOs 21% * Sources: 2022 State of Open Source Report
- 22. Open Source Jobs Report Source: The Linux Foundation OSS Jobs Report 93% Of Employers with difficulty finding talent with OSS Skills 77% of orgs are growing their use of cloud-native technologies Most on demand skills: Cloud/Container Technology, Linux, DevOps/GitOps, Cybersecurity, AI/ML, Web Technologies 81% of open source professionals plan to add certifications
- 23. Key Takeaways § Open source release life cycles, EOL and LTS are constantly changing § Lessons from CentOS and AngularJS EOL § OSS communities work on security, the key is to keep up with updates and patches § There’s more Open Source Security Awareness and Government participation
- 24. Has your organization increased the use of open source software over the last year? Yes Yes, significantly 41% 36% YES 77%
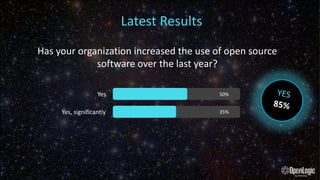
- 25. Has your organization increased the use of open source software over the last year? Yes Yes, significantly 50% 35% YES 85% Latest Results
- 26. www.research.net/r/state-of-oss Participate in the 2023 State of Open Source
- 27. Thank You! Chief Evangelist & Sr. Director Product Management @jperezp_bos javierperez.mozello.com www.linkedin.com/in/javierperez Javier Perez
