AN ENHANCED HYBRID ROUTING AND CLUSTERING TECHNIQUE FOR WIRELESS SENSOR NETWORK
- 1. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 DOI: 10.5121/ijwmn.2020.12102 13 AN ENHANCED HYBRID ROUTING AND CLUSTERING TECHNIQUE FOR WIRELESS SENSOR NETWORK Hasan Al-Refai Department of Computer Science, Philadelphia University, Jordan ABSTRACT Wireless Sensor Networks (WSN) have extensively deployed in a wide range of applications. However, WSN still faces several limitations in processing capabilities, memory, and power supply of sensor nodes. It is required to extend the lifetime of WSN. Mainly this is achieved by routing protocols choosing the best transmission path in-network with desired power conservation.This cause is developing a generic protocol framework for WSNa big challenge. This work proposed a new routing technique, described as Hybrid Routing-Clustering (HRC) model. This new approach takes advantage of clustering and routing procedures defined in K-Mean clustering and AODV routing, which constituted of three phases. This development aims to achieve enhanced power conservation rate in consequence network lifetime. An extensive evaluation methodology utilized to measure the performance of the proposed model in simulated scenarios.The results categorized in terms of the average amount of packet received and power conservation rate. The Hybrid Routing-Clustering (HRC) model was determined, showed enhanced results regarding both parameters. In the end, they are comparing these results with well-known routing and well-known clustering algorithms. KEYWORDS Wireless Sensor Networks, Clustering, Routing, Power conservation, Network lifetime, AODV, K-Mean, LEACH 1. INTRODUCTION Wireless Sensor Network (WSN) is a collection of small, self-contained electromechanical devices that monitor the environmental conditions and be useful to employ in many applications such as medical, automotive safety, and space applications. There are many essential priorities to build an architectural (WSN), such as deployment, mobility, infrastructure, network topology, network size and density, connectivity, lifetime, node addressability, data aggregation, etc. Sensor nodes have several limitations, such as limited battery life, low computational capability, short radio transmission range, and small memory space. Still, the primary constraint of the nodes is their limited energy resource, which causesthe disconnection of the network. Therefore, to reduce energy usage in wireless sensor networks, many cluster-based routings have been proposed. Among those proposed, LEACH (Low Energy Adaptive Clustering Hierarchy) is a well-known cluster-based sensor network architecture, which aims to distribute energy consumption evenly to every node in a given network. This clustering technique requires a predefined number of clusters and has been developed with an assumption that the sensor nodes are uniformly distributed throughout the network (Sukhchandan Randhawa&Sushma Jain. 2019)(Tillapart et al. 2005). Moreover, (Maurya et a. 2014) stated that Low-Energy Adaptive Clustering Hierarchy (LEACH) is the first significant protocol, which consumes less amount of energy while routing the data to the base station. However, other researchers discussed this issue
- 2. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 14 in a different way (Gnanambigai et al. .2014) stated that LEACH proves to be an outwitting routing scheme ishas limitations in inheritance due to the power-consuming overhead processing and the increased number of participating nodes. Such limitations motivated the researcher to carry out this research. Numerous citations performed for the first paper released LEACH. These studies based their work principles on LEACH false assumptions, which in turn results in failure throughout their researches' works. Therefore, this research implemented and adopted a new model based on realistic values within the use of both simple routing and clustering represented in subsections (2.1.2) and (2.1.3), respectively, to clarify LEACH assumptions limitations. Therefore, this work will follow the below methodology: 1- Define the problem statement by implementing LEACH and AODV assumptions on real environments’ parameters. 2- Defining the scope of work by focusing on solving the formulated problems and issues of LEACH assumptions on real environments. 3- Proposing a new hybrid routing and clustering technique based on integrating K-Mean clustering as a clustering algorithm and simple routing i.e., AODV, as routing algorithm, to be reliable in real environments. 4- Divide the proposed technique into phases, to enhance its efficiency and ease the troubleshooting process. 5- Evaluate the proposed technique by simulating it on the real environment’s parameters using MATLAB. Besides this section, the next section reviewed some related works and current solutions for the problem under study. The proposed algorithm and its phases are discussed in the third section. The fourth section discussed the experiment and the scenarios that were implemented to prove the algorithm and the obtained results. Finally, yet importantly, the fifth section showed the conclusions and summarized the entire work. 2. TECHNICAL BACKGROUND Having mentioned the problem statement of this work in addition to our proposed solution, in this section, brief details about the techniques, schemas, and algorithms to be used in this work will be shown. Wireless Sensor Network (WSN) is an emerging network technology that provides reputable monitoring of the various environmental circumstances. One of the paramount constraints in the WSN is the scrimp energy resource. Many experimental works in WSNs are focussed on achieving energy efficacy. Many researchers focused on routing schemes as an effective Factor to achieve energy-efficient operation (Sukhchandan Randhawa&Sushma Jain. 2019), (Kaswan A., Singh V., Jana P.K. 2018), ( Amit Sarkar1 & T. Senthil Murugan. 2019), (Gnanambigai et al., 2014). designing an effective routing protocol is a critical approach for energy conservations in wireless sensor networks (Huang, & Yen, 2009).The latest algorithm of routing build and test under the assumption of uniformly distributed sensor node .although, the determines of this assumption is that it needs to be installed and condensed in some area and spares in other areas to form the scope of the ongoing monitoring process. (Baroudi et al., 2012). Wireless Sensor Network is modern technology, and it developed rapidly. Extending the lifetime of a wireless sensor network is highly recommended issues. Reduce energy consumption in the network by choosing the best transmission path in a network that is responsible for the routing
- 3. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 15 techniques (Sharma et al.,2015). Consequently, Routing protocols schemes are the main requirements for developing a model for WSNs, if the desired is power conservation. There are mainly two fields of managing the WSN environment, categorized as Clustering Algorithms and Routing Algorithms. 3. CLUSTERING OF SENSOR NODES The clustering technique has been proved to be one of the most efficient methods in this field, due to its scalability, the ability of aggregating data, minimized energy consumption, and robustness. Many protocols are categorized under the umbrella of cluster-based protocols. However, some of these protocols repeat the clustering operation at certain intervals of time, leading to a potential waste of energy. To name a few of clustering techniques in WSNs: Low-Energy Adaptive Clustering Hierarchy (LEACH) (Heinzelman et al. 2000), Hybrid Energy-Efficient Distributed clustering (HEED) (Younis & Fahmy 2004), Distributed Weight-based Energy-efficient Hierarchical Clustering protocol (DWEHC) (Ding et al. 2005), and Position-based Aggregator Node ELection protocol (PANEL) (Sukhchandan Randhawa&Sushma Jain. 2019), ( utty andSchaffer,2010). Researchers suggested that grouping the sensors into clusters will provide higher scalability, and make energy consumption more efficient, hence, prolonging the lifetime of the entire WSN. Such clusters allow for aggregation and limiting data transmission. Clustering means that nodes are divided into virtual groups according to some rules, where nodes belonging to a group can execute different functions from other nodes. When forming a cluster, a “Cluster Head”, CH, is elected and the members of such a cluster can communicate with their CH directly; then this CH can forward the aggregated data to the central base station, eventually, through other CHs (Kumar, et al.; 2014) and (Halder, & Ghosal, 2015), (Sukhchandan Randhawa&Sushma Jain. 2019). Figure 1 below shows how a clustered WSN work: Figure 1: Clustering Technique in a WSN 3.1. LEACH Algorithm The LEACH (Low-Energy Adaptive Clustering Hierarchy) clustering protocol (Heinzelman et al., 2000) was a pioneer in such methodology. In this clustering protocol, the head repeatedly rotates amongst the nodes, to balance the energy consumption. This way, energy in the nodes is reduced evenly among the nodes, and untimely battery drainage can be avoided. In this protocol, each sensor node transmits collected data to the CH, which in turn collects them and sends them
- 4. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 16 directly to the base station (which is known as the data sink), regardless of its distance. It is most efficient when the area covered by WSN is small, or when the cost of receiving data is high. Figure 2 below shows the clustering hierarchy of a WSN applying the LEACH protocol: Figure 2: LEACH Clustering LEACH works over two phases: 1- The Setup Phase (where cluster-heads are chosen) - Cluster-head selection: where the probability of a node to become a CH is calculated on timed intervals, and the CH selection is made independently by each node without consulting other nodes in the cluster to minimize overhead in cluster head establishment. This probability decreases in case a node was chosen to be a CH in previous rounds; each node during cluster head selection will generate a random number between 0 and 1. If the number is less than a calculated threshold, the node will become a cluster head. The threshold is calculated as: Where n is the current node, P is the a priori probability of this node to be selected as a CH, r is the order of the current round, and G is the set of nodes that haven’tbecomeCHs within the last 1/P rounds. - Cluster Set-Up: Each node in the WSN will broadcast a message to the rest of the nodes stating its status. These nodes will then determine the most suitableclustertheyprefertojoinbasedonthereceivedmessage’sstrength.CHs must keep their receivers ON to receive surroundingnodes’decisions. - Transmission schedule creation: the CH creates a schedule containing the number of nodes in the cluster, and then nodes send their data to the cluster head. 2. Steady-state Phase (CH manages data transmission among connected nodes) - Data transmission begins from cluster nodes to cluster heads. - Validation of received signals and aggregation of the data to be transmitted to the base station. - Data transmission from cluster heads to the base station.
- 5. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 17 Power Model of LEACH Protocol To accurately define our problem, which can formulate the motivation of this research, we have implemented the LEACH assumption on parameters from a real environment containing physical tools. However, the impact of the power model on the LEACH protocol is illustrated in figure 3. We have changed the network size in this configuration from 100x100 to 200x200 with the same number of nodes without changing the location of the sink node. It can observe that in 100x100 areas, the entire nodes are connected as well as the whole cluster heads can reach a sink node since the distance between nodes and sink node is less than 100. However, we can observe that in area 200x200, the disconnected nodes number, which cannot even reach a cluster head is larger than 50% of the total number of nodes. Moreover, 4 of the 5 selected cluster heads in different rounds could not reach a sink node. This figure shows the importance of routing in WSN. Furthermore, it explains that LEACH has many problems, which developed a motivation to solve them by proposing this algorithm. 3.2. Network Life Time for LEACH and Simple Routing After detailing the related parameters of LEACH and simple routing algorithm, we can evaluate the life-time of their nodes and the entire network, by applying their assumptions on the same parameters. Figure 4shows the CDF of the network lifetime of both of LEACH and simple routing. We can observe that under the Wi-Fi power model. Simple routing lives more than LEACH. We can observe that 80 % of nodes live more than 1800 rounds, unlike LEACH, which die in less than 1800 rounds. We also can observe the distribution in dying of nodes in LEACH. Since LEACH randomizes the dying nodes, which leads to the more fairallocation of the dead nodes and then longer life-time. However, one thing to be mentioned is that the nodes send the data even if these data did not receive from the sink node. In other words, nodes also sent if the network is disconnected. We have observed that only 819 packets have been received in the area of 300x300 using AODV, comparing with 1770 using Clustering. Moreover, to compare the lifetime between LEACH and the Routing (AODV), the disconnected rounds have been deleted from the LEACH CDF plot for area 300x300. Figure 3: Impact of the power model on LEACH protocol
- 6. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 18 Figure (4): Routing vs. ClusteringCDF (Network Lifetime) 4. RELATED WORK Several studies are carried out based on LEACH assumptions such as: (Tillapart et al., 2005;Haiming, &Sikdar, 2007; Yan et al., 2009; Huang,& Yen, 2009Baroudi, et al., 2012; Baroudi et al., 2012; Guo et al., 2012; Guo et al., 2012;Tyagi et al.; 2013;Zhang et al., 2013; Patra, Chouhan, 2013; Zhang, & Zhao, 2014;Gambhir,& Fatima, 2014;Gnanambigai et al., 2014; Sharma, & Choudhary, 2014; Maurya et al., 2014). Others are studied routing and clustering, such as, while some research works achieved good performance based on the assumption of equal initial power and/or predefined ratio in types of nodes, these mechanisms are not flexible. Besides, existed works rarely deal with cluster head distribution (Tsai & Chen, 2015). Studies that are concerned in hybrid models based on leaching like: (Tillapart et al., 2005;Zhang et al., 2013; Patra, Chouhan, 2013). (Tillapart et al., 2005) proposed a new architecture based on hybrid clustering and routing for WSNs quite similar to the proposed research model with some differences in the main parts based on. Their method relays on three parts: first, a technique termed modified subtractive clustering technique. Secondly, a technique termed an energy-aware cluster head selection. Finally, an algorithm termed coast based routing algorithm. These supposed to be performed at the base station BS because they are considered as centralized techniques, and it is showed that their proposed architecture outperforms the LEACH scheme in terms of energy conservations. (Haiming andSikdar, 2007) reduced the consumption happening to the energy throughout excluding the requirements of synchronizing TDMA. With the use of LEACH sleep-wake up based on decentralizing MAC protocol as the first step. Then, illustration for an optimal probability-obtaining framework is made, where the node becomes CH to reduce the energy consumption in the network. Firstly, the small networks are illustrated in their analysis with an assumption that the distance expected for all CHs from the sink node is similar. After that, the larger networks represented as a complement analysis of small ones; but with a conditionwhere the distance, as mentioned above, is altered not similar. The assumption, however,changed because the nodes in large networks may be farther away from the sink, which in turn required more energy to be consumed until it reaches the sink. Their resulted simulations show that their proposed method outperforms LEACH in terms of significant energy consumption, which relates to one of our research parameters that will be compared throughout the research proposed method concerning LEACH.
- 7. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 19 (Huang & Yen.2009) proposed a protocol also to reduce power consumption efficiently. This protocol called CB-DHRP. Their proposed protocol designed according to LEACH scheme with identical work principle with only one difference in single LEACH assumption. This assumption relates to the transmission range for a node and the method of formation, which used to create a routing structure. Regarding the restricted transmitting range of a node and the assist of the cluster member and CHs combination CB-DHRP builds transmission paths, which can be described with an efficient energy reservation and have the ability to send the sensed data into the sink base station BS. Their resulted simulations show that, within an available selection to CHs, CB-DHRP outperforms LEACH, ERA, and PEGASIS protocols in terms of improving network lifetime by 1.5 times better than the other protocol above does. This study is critical to our research due to the network lifetime parameter that CB-DHRP compared its performance to, concerning LEACH. To achieve power conservation, we should use the proposed hybrid self-decisive clustering technique based on Hierarchical Agglomerative Clustering and k-means algorithm, as earlier mentioned before. Such algorithms are to arrive at an optimal number of clusters for a given set of nodes distributed over the geographical area. 5. PROPOSED ALGORITHM The proposed hybrid routing-clustering (HRC) model is described in section 3.4. However, the demonstration of sensor nodes’ power, data rates, and transmission distances used within the proposed model are described in section (3.1) and (3.2). 5.1. Power Consumption Demonstration for Sensor Nodes WSN contains numerous small devices called sensor nodes, which are frequently setup randomly over a wide area for sensing and monitoring purposes to the different physical phenomena associated parameters together with environmental circumstances at different positions, and communicate with each other. However, WSN devices have various resource limitations, such as fewer memories, small clock speed, limited battery energy, and restricted computational power. Similarly, the lifetime of the network, the effectiveness of the energy, load balance, and much more scalability key issues, which considered the fundamental requirements of WSN applications (Kodali&Aravapalli, 2014). However, as explained in later sections, sensor nodes of the proposed power model are Wi-Fi enabled nodes. See table 1, which shows the consumed power to send or receive bits. These values can be found in (Halperin et al., 2010). Utilizing these values, equation (1) illustrates the required power to send while equation (2) illustrates the needed power to receive and then, listen. Table 1: Power model coefficients Variable Value Power to send (Ps) 17nJ/bit Power to listen (Pl) 12nJ/bit
- 8. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 20 𝑆𝑒𝑛𝑑𝑃𝑜𝑤𝑒𝑟 (𝑇𝑥) = 𝑃𝑠 ∗ 𝑃𝑎𝑐𝑘𝑒𝑡𝑠𝑖𝑧e (1) 𝑅𝑒𝑐𝑒𝑖𝑣𝑖𝑛𝑔𝑃𝑜𝑤𝑒𝑟 (𝑅 𝑥) = 𝑃𝑙 ∗ 𝑃𝑎𝑐𝑘𝑒𝑡𝑠𝑖𝑧𝑒 (2) 5.2. Data Rate and Transmission Distance Demonstration From observing the above equations, power does not depend on distance as in LEACH assumptions. Power depends on packet size and bit rate, as shown in (Halperin et al. 2010). In the proposed model, the first assumption of LEACH protocol, which is regarding that each sensor nodes contain an equal amount of energy, was modified, and nodes are not required to measure distances and direct their antennas. In other words, this model is implementable. Two parameter values are defined in the proposed model; first, the bit rate of sensor nodes is 50Mbps. Second, the transmission distance is constant, which is 100m and not like LEACH. 5.3. Proposed Hybrid Routing-Clustering (HRC) Model After demonstrating the power consumption, data rate, and transmission distance, the proposed protocol is described in this section. Figure 5: Flow chart of the proposed algorithm. HRC consists of three main phases. In the first phase, the sink node broadcasts a packet. Any node receives this packet will be marked as layer 1. Subsequently, the nodes in this layer will add the layer number to the packet and rebroadcasts it. Any node receives this rebroadcasted packet will be identified as layer 2. The nodes in layer 2 will continue in the same procedure until all nodes in the network receive a layer number. These two layers, in addition to the HRC, three phases will be briefly identified in the next subsections below, but after explaining briefly how this implemented system algorithm works in detail. See figure 5, which illustrates the flow chart of the proposed algorithm. Flooding Message From Sink Nodes Broadcast Message with its Layer Number Build Routing Table (Rout to the Sink) in each node Calculate Clusters Utilizing parameters from Sink Flood Message Average Nodes in clusters accoding to Location of Centroids Send Data to Cluster Heads and use table to route data to sink
- 9. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 21 First Phase: Preparing the Nodes The sink node sends a broadcast to all nodes within its coverage area. All nodes that receive the broadcast message resend a broadcast and declare as layer one. All nodes that receive the resend broadcast are clarified as layer two and resend a broadcast, and so on. For more detailed steps on what is happening during this phase, the steps below are stated as follows: 1- Each node has a physical address. 2- Sink node knows its location in the network. 3- Sink node broadcast a MSG <sink physical address, layer 0, location, distance=0, random values = 20, 30, 40, 50>. 4- Any node receives this MSG will mark itself as Layer 1 node. They modify the received MSG as follows < Physical address, layer 1, location “sink”, distance= can be computed from equation (3), random values=20, 30, 40, 50>. 5- Each node in this layer will broadcast this MSG. If a layer one node receives this MSG, it will add the node physical address into a neighbor table like the one shown in table 2. 6- Any node which has no layer number receives these broadcast MSG will update its status to be in layer= MSG.layer+1. Subsequently, it will broadcast the MSG by modifying the following fields <Physical address, layer 2, location “sink”, distance=MSG.distance+ computed new distance, random values=20, 30, 40, 50> 7- If a node in the current layer (e.g. layer 2) receives multi-packets from nodes with layer number less than its layer number (e.g., layer 1). It will use the first packet it received to calculate the distance, and it will add the physical address in the new MSG into a gateway table for possible routing nodes. See table 3 for an example for a gateway list. 8- Any nodes receive this MSG will do the following. A- If the node in Layer 1 discards the MSG. B- If the node in Layer2 adds the Physical address into the neighbor table. C- If it has, no layer will repeat step 6 and so on. D- If multi packets from the layer add the physical address to the gateway table 9- When nodes in the last layer broadcast the MSG, no new nodes will receive the MSG; however, they will consider itself as a leaf node. Table 2: Neighbor table Physical address Mark 1 4 8 Etc.
- 10. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 22 Table 3: Gateway List Node 4 Node 7 Etc. All nodes will receive these MSGs. If a node does not receive any MSG, this means it cannot connect with any other nodes, and it should be relocated since it is disconnected from the Network. Equation (3) illustrates the Free-space propagation model (Schmidt-Eisenlohr, 2010). Any propagation model can be used. However, this one is the easiest. 𝑃𝑇(𝑑) = 𝑃𝑡 𝐺𝑡 𝐺 𝑇 𝜆2 (4𝜋)2 𝑑2 𝐿 ………………….. (3) Where: 𝑃𝑡Is the transmitted power 𝑃𝑇(𝑑)Is the received power 𝐺𝑡Is the transmitter antenna gain mostly equal to one 𝐺 𝑇Is the receiver antenna gain mostly equal to one 𝑑Is the distance between transmitter and receiver 𝜆Is the wavelength in which the communication takes place. 𝐿Is the system loss factor dependent upon line attenuation, and its equal to one. Second Phase: Clustering and Centroid In this phase, the clusters are constructed. The WSNs are consist of a number of clusters (# CHs). In this work, 100 nodes are distributed randomly in the different coverage area dimensions; 100x100, 200x200 ... 500x500. Moreover, all the nodes in this phase each (nodes in any layer greater than layer one) will perform the following steps: 1. First, compare that node’s Physical ID with all Physical IDs in its neighbor table. If it has the highest ID number, it will wait. 2. If it is the smallest Physical ID number, it will select the first random value “20” and add it to its calculated distance to be selected as a centroid. 3. It will broadcast this Physical ID number<MSG.Cluster>. Each neighbor node will receive this number anduse it to calculate their distances to the new centroid. 4. If the ID number of the node is in the middle of other nodes in the neighbor list (it is ID number is greaterthan some node’s ID and smaller than some node’s ID), it will perform the procedures described in (b) and (c) of step (8) in the first phase. If the node received <MSG.Cluster> before, it will use the second random value. Else, it will use the first one. 5. When a node receives MSG.Cluster messages from multiple nodes, it will save the distance and the node ID of this MSG. Subsequently, it will calculate the distance between its distance and the value of centroid in these MSGs. It will choose the smallest distance. 6. Each node will broadcast the cluster name it will follow. The names will be the physical address of the node sent to the MSG.cluster. 7. Nodes in the same cluster will hear these broadcasts. They will build the cluster list “table” of all nodes in the same cluster with them. 8. The node with the smallest ID “Physical address” will be the first cluster head for the first round.
- 11. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 23 9. After each round, the nodes will change to the second cluster head in the list. Thesecond higher physical address and so on. Third Phase: Data Routing After using-mean clustering, each node is referred to as a particular cluster. The following steps are responsible for routing process accomplished in the third phase of HRC: 1- Any cluster head will wait to receive data from all nodes in its cluster “round” it will add them to one packet and rout them. 2- To route the data, the cluster head will choose one node of its gateway table randomly as the next-hop address and sends the packet to that node. 2- Cluster head can randomly choose any node from the gateway table for load balancing. 6. HRC EVALUATION (EXPERIMENTAL ENVIRONMENT) The proposed HRC model was evaluated through a set of simulation studies conducted using Matlab. Three different protocols have been considered; LEACH, simple routing, and proposed HRC. Moreover, the static distance has been embedded in LEACH to determine its impact on network connectivity. Simple routing has been simulated to be a ground truth of simple configuration without clustering. Table (4) shows the configuration used for the simulation environment. Five different scenarios were used, each with different coverage area dimensionsstaring from 100x100 and ending with 500x500. These scenarios were repeated 30 times and then averaged for accuracy. Table (4): research configuration of the simulation Environment 6.1. Research Results Results are categorized according to the average received packets and power conservation achieved by using Proposed HRC, LEACH, and Simple Routing. The comparison was based on adifferent number of rounds and several area sizes. 6.2 The Average Received Packets in HRC and Simple Routing First of all, the values of the below table have resulted. Table (5) describes the average received packets in HRC and using a simple routing approach. The average received packets are used to clarify the advances achieved in the proposed HRC in receiving a greater amount of received packets comparing to simple routing. The maximum average of the received packets was1834 packets if all nodes can reach the sink node without any routing. This can be calculated according Component Value Area Size 5 scenarios. (100x100, 200x200 …. 500x500) Number of nodes 100 Initial power in J 0.5J Number of Sink nodes 1 Packet Size 2000 Bytes Sink Node Location (50,50)
- 12. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 24 to equation (4). This value is considered as the maximum boundary of the number of transmitted packets. 𝒎𝒂𝒙𝒊𝒎𝒖𝒏𝒂𝒗𝒆𝒓𝒂𝒈𝒆𝑹𝒙𝒑𝒂𝒄𝒌𝒆𝒕𝒔 = 𝒊𝒏𝒊𝒕𝒊𝒂𝒍𝒑𝒐𝒘𝒆𝒓 ×𝒑𝒂𝒄𝒌𝒆𝒕𝒔𝒔𝒊𝒛𝒆 𝒕𝒓𝒂𝒏𝒔𝒎𝒊𝒕𝒕𝒆𝒅𝒑𝒐𝒘𝒆𝒓 ……... (4) The average packet received for simple routing was 551. The reason behind this small number of received packets is the death of nodes in the first layer. These nodes died after a few rounds because of the routing process. However, the number was increased in HRC because of clustering and compressing processes of data. Table (5): the average received Packets and simple routing: 6.3 Comparing HRC and Simple Routing A comparison between simple routing and HRC in the lifetime of the network is illustrated in figure 6. This comparison has been conducted with an area size of 200x200 m.It can be noticed that 50% of the nodes consumed their power in less than 600 rounds within the use of simple routing; however, these nodes survived until approximately 1200 rounds using HRC. Moreover, it is quite noticeable that 35% of the nodes in simple routing lived until 1800 rounds; these nodes are leaf nodes, which do not route any traffic in the network. Therefore, this provides evidence that the network dies from meddling and not in a random manner as it is assumed in LEACH. Figure 6: CDF of LEACH and Proposed HRC Figure7, the y-axis indicates Cumulative Distribution Function (CDF) measured by percentage (1=100%, 0.9 = 90% … and so on). The stability in simple routing graph between rounds (400- 600, 600-800, and 800-1800), respectively, indicate useless nodes, which still alive, but it does not route anymore. Such nodes are considered leaf nodes whose location is way far from the sink node. After round 1800, those nodes are considered to die due to lack of electricity. Simple Routing 551 HRC 1304
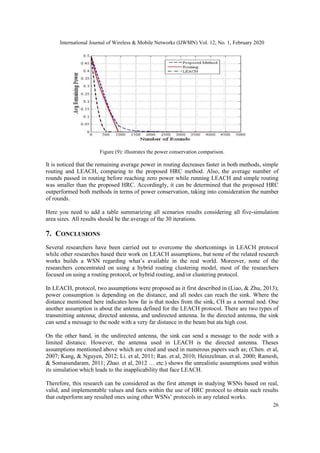
- 13. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 25 Figure 7: Network Lifetime 6.4 The Relation between HRC Layers and Area Size Figure 8: Relation between Layers and Network Size The relation between the number of layers in HRC and the area size is illustrated in figure 8. It is clear that this relationship is linear. In addition, within an area of 500x500, 8 layers are needed. This shows the limitation in the LEACH protocol, which has no routing at all. Figure (8) shows the Cumulative Distribution Function. LEACH nodes lived shorter connected time than the proposed HRC method. We also can observe that 50% of nodes died in less than 800 rounds. However, in the proposed model, 50% of nodes lived 1100 rounds. The improvement can be measured as average rounds in proposed over average rounds in LEACH, which is equal to 57.3%. As shown in the below figure. 6.5 The Power Conservation Comparison between Proposed Method, LEACH and Simple Routing A comparison of the remaining power after each round in all threeproposed methods HRC, LEACH, andsimple routing is illustrated in figure 9. This power conservation comparison has been conducted with an area size of 300x300 m. The average power after each round can be calculated as the sum of the remaining power in all nodes divided by the number of nodes.
- 14. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 26 Figure (9): illustrates the power conservation comparison. It is noticed that the remaining average power in routing decreases faster in both methods, simple routing and LEACH, comparing to the proposed HRC method. Also, the average number of rounds passed in routing before reaching zero power while running LEACH and simple routing was smaller than the proposed HRC. Accordingly, it can be determined that the proposed HRC outperformed both methods in terms of power conservation, taking into consideration the number of rounds. Here you need to add a table summarizing all scenarios results considering all five-simulation area sizes. All results should be the average of the 30 iterations. 7. CONCLUSIONS Several researchers have been carried out to overcome the shortcomings in LEACH protocol while other researches based their work on LEACH assumptions, but none of the related research works builds a WSN regarding what’s available in the real world. Moreover, none of the researchers concentrated on using a hybrid routing clustering model, most of the researchers focused on using a routing protocol, or hybrid routing, and/or clustering protocol. In LEACH, protocol, two assumptions were proposed as it first described in (Liao, & Zhu, 2013); power consumption is depending on the distance, and all nodes can reach the sink. Where the distance mentioned here indicates how far is that nodes from the sink, CH as a normal nod. One another assumption is about the antenna defined for the LEACH protocol. There are two types of transmitting antenna; directed antenna, and undirected antenna. In the directed antenna, the sink can send a message to the node with a very far distance in the beam but ata high cost. On the other hand, in the undirected antenna, the sink can send a message to the node with a limited distance. However, the antenna used in LEACH is the directed antenna. Theses assumptions mentioned above which are cited and used in numerous papers such as; (Chen. et al, 2007; Kang, & Nguyen, 2012; Li. et al, 2011; Ran. et al, 2010; Heinzelman. et al. 2000; Ramesh, & Somasundaram, 2011; Zhao. et al, 2012 … etc.) shows the unrealistic assumptions used within its simulation which leads to the inapplicability that face LEACH. Therefore, this research can be considered as the first attempt in studying WSNs based on real, valid, and implementable values and facts within the use of HRC protocol to obtain such results that outperform any resulted ones using other WSNs’ protocols in any related works.
- 15. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 27 Due to that end, this research has adopted a new model proposed in this research work based on realistic values rather than LEACH assumptions to overcome thelimitation found in LEACH and to introduce a new model represented in HRC. REFERENCES: [1] Al Basset Almamou, A., Wrede, R., Kumar, P., Labiod, H., & Schiller, J. (2009). Performance evaluation of routing protocols in a Real-World WSN. Information Infrastructure Symposium, 2009. GIIS'09.Global, 1-5.Retrievedfrom http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=5307052&isnumber=5307032 [2] Baroudi, U., Al-Roubaiey, A., Mekid, S., &Bouhraoua, A. (2012). The Impact of Sensor Node Distribution on Routing Protocols Performance: A Comparitive Study. IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom),1714- 1720. [3] Chen, H., Wu, C., Chu, Y., Cheng, C., & Tsai, L. (2007). Energy Residue Aware (ERA) Clustering Algorithm for Leach-based Wireless Sensor Networks. Conference: Systems and Networks Communications. [4] Gajjar, S., Dasgupta, K., Pradhan, S., &Vala, K. (2012). Lifetime improvement of LEACH protocol for Wireless Sensor Network. 2012 Nirma University International Conference on Engineering (NUiCONE),1-6.Retrievedfrom http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6493233&isnumber=6493172 [5] Gambhir, S., & Fatima, N. (2014). Op-LEACH: An Optimized LEACH Method for Busty Traffic in WSNs. Fourth International Conference in Advanced Computing & Communication Technologies (ACCT), 222-229. [6] Gnanambigai, J., Rengarajan, N., &Prarthana, R. (2014). An analytical approach for quadrant based leach: An energy efficient routing protocol for WSNs. 2nd International Conference on Devices, Circuits and Systems (ICDCS), 1-6. Retrieved from http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6926117&isnumber=6926115 [7] Guo, L., Xie, Y., Yang, C., & Jing, Z. (2010). Improvement on LEACH by combining Adaptive Cluster Head Election and Two-hop transmission.2010 International Conference on Machine Learning and Cybernetics (ICMLC), 4, 1678-1683. [8] Halperin, D., Greenstein, B., Sheth, A., &Wetherall, D. (2010). Demystifying 802.11n Power Consumption. Proceeding HotPower'10 Proceedings of the 2010 International Conference on Power Aware Computing and Systems, 1(1). [9] Haiming, Y., &Sikdar, B. (2007). Optimal Cluster Head Selection in the LEACH Architecture. IEEE International in Performance, Computing, and Communications Conference, 93-100. [10] Heinzelman, W., Chandrakasan, A., &Balakrishnan, H. (2000). Energy-Efficient Communication Protocol for Wireless MicrosensorNetworks.Proceedings of the 33rd Hawaii International Conference on System Sciences. [11] Huang, J., & Yen, P. (2009). CB-DHRP: A Cluster-Based Directed Hierarchical Routing Protocol for wireless sensor networks.International Symposium in Autonomous Decentralized Systems, 1-6. [12] Javaid, N., Waseem, M., Khan, Z., Qasim, U., Latif, K., &Javaid, A. (2013). ACH: Away cluster heads scheme for Energy Efficient Clustering Protocols in WSNs. Saudi International in Electronics, Communications and Photonics Conference (SIECPC), 1-4. Retrieved from http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6550972&isnumber=6550724 [13] Kang, S., & Nguyen, T. (2012). Distance Based Thresholds for Cluster Head Selection in Wireless Sensor Networks. IEEE COMMUNICATIONS LETTERS, 16(9), 1396-1399. [14] Kumar, G., Mehra, H., Seth, A., Radhakrishnan, P., Hemavathi, N., &Sudha, S. (2014). An hybrid clustering algorithm for optimal clusters in Wireless sensor networks. IEEE Students' Conference on Electrical, Electronics and Computer Science (SCEECS), 1-6. Retrieved from http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6804442&isnumber=6804412 [15] Li, Y., Yu, N., Zhang, W., & Zhao, W. (2011). Enhancing the performance of LEACH protocol in wireless sensor networks. IEEE Conference: Computer Communications Workshops. [16] Liao, Q., & Zhu, H. (2013). An Energy Balanced Clustering Algorithm Based on LEACH Protocol. Proceedings of the 2nd International Conference On Systems Engineering and Modeling.
- 16. International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020 28 [17] Maurya, P., Kaur, A., &Choudhary, R. (2014). Behavior analysis of LEACH protocol. International Conference on Parallel, Distributed and Grid Computing (PDGC), 68-71. Retrieved from http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=7030717&isnumber=7030698 [18] Ramesh, K., &Somasundaram, K. (2011). A COMPARATIVE STUDY OF CLUSTERHEAD SELECTION ALGORITHMS IN WIRELESS SENSOR NETWORKS. International Journal of Computer Science & Engineering Survey, 2(4), 153-164. [19] Ran, G., Zhang, H., & Gong, S. (2010). Improving on LEACH Protocol of Wireless Sensor Networks Using Fuzzy Logic. Journal of Information & Computational Science, 7(3), 767-775. [20]Sharma, I., Singh, R., &Khurana, M. (2015). Comparative study of LEACH, LEACH-C and PEGASIS routing protocols for wireless sensor network. International Conference on Advances in Computer Engineering and Applications (ICACEA), 842-846. Retrieved from http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=7164821&isnumber=7164643 [21] Sharma, S., &Choudhary, S. (2014). Heterogeneous multi-hop LEACH routing protocol. International Conference on Green Computing Communication and Electrical Engineering (ICGCCEE), 1-6. Retrieved from http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6922249&isnumber=6920919 [22] Schmidt-Eisenlohr, F. (2010). Interference in Vehicle-to-vehicle Communication Networks: Analysis, Modelling, Simulation and Assessment (p. 149). KIT Scientific Publishing. ISBN: 9783866445710 [23] Tillapart, P., Thammarojsakul, S., Thumthawatworn, T., &Santiprabhob, P. (2005). An Approach to Hybrid Clustering and Routing in Wireless Sensor Networks. 2005 IEEE in Aerospace Conference, 1- 8. [24] Tran, S., & Yang, T. (2007). OCO: Optimized Communication & Organization for Target Tracking in Wireless Sensor Networks. University of Houston. [25] Tsai, M., & Chen, Y. (2015). A Virtual Cluster Head Election Scheme for Energy-Efficient Routing in Wireless Sensor Networks. 3rd International Conference in Future Internet of Things and Cloud (FiCloud), 341-348. [26] Tyagi, S., Gupta, S., Tanwar, S., & Kumar, N. (2013). EHE-LEACH: Enhanced heterogeneous LEACH protocol for lifetime enhancement of wireless SNs. International Conference on Advances in Computing, Communications and Informatics (ICACCI), 1485-1490. Retrieved from http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6637399&isnumber=6637135 [27] Yan, L., Pan, W., Luo, B., Liu, J., &Xu, M. (2009). Communication protocol based on optical low- energy-adaptive-clustering-hierarchy (O-LEACH) for hybrid optical wireless sensor networks. Communications and Photonics Conference and Exhibition (ACP), 1-6. Retrieved from http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=5405443&isnumber=5405166 [28] Zhang, J., Mao, Z., &Jia, R. (2013). Study on hybrid modelling approach for gold cyanidation leaching process. 25th Chinese in Control and Decision Conference (CCDC), 1557-1561. Retrieved from http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6561176&isnumber=6560882 [29] Zhao, F., Xu, Y., & Li, R. (2012). Improved LEACH Routing Communication Protocol for a Wireless Sensor Network. International Journal of Distributed Sensor Networks, 1, 1-6. [30] Zhao, W., & Zhang, L. (2014). Analysis and research of improved LEACH routing protocol for pressure sensor based on WSN. Cyberspace Technology (CCT 2014), International Conference, 1-6. [31] Sukhchandan Randhawa & Sushma Jain (2019). MLBC: Multi-objective Load Balancing Clustering technique in Wireless Sensor Networks. Journal of Applied Soft Computing. ELSEVIER. Volume 74, January 2019, Pages 66-89. [32] Kaswan A., Singh V., Jana P.K. (2018). A multi-objective and PSO based energy efficient path design for mobile sink in wireless sensor networks. Pervasive Mob. Comput., 46 , pp. 122-136 [33] Amit Sarkar1 & T. Senthil Murugan. (2019). Cluster head selection for energy efficient and delay-less routing in wireless sensor network. Wireless Netw (2019) 25:303–320. Springer.













![International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020
27
Due to that end, this research has adopted a new model proposed in this research work based on
realistic values rather than LEACH assumptions to overcome thelimitation found in LEACH and
to introduce a new model represented in HRC.
REFERENCES:
[1] Al Basset Almamou, A., Wrede, R., Kumar, P., Labiod, H., & Schiller, J. (2009). Performance
evaluation of routing protocols in a Real-World WSN. Information Infrastructure Symposium, 2009.
GIIS'09.Global, 1-5.Retrievedfrom
http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=5307052&isnumber=5307032
[2] Baroudi, U., Al-Roubaiey, A., Mekid, S., &Bouhraoua, A. (2012). The Impact of Sensor Node
Distribution on Routing Protocols Performance: A Comparitive Study. IEEE 11th International
Conference on Trust, Security and Privacy in Computing and Communications (TrustCom),1714-
1720.
[3] Chen, H., Wu, C., Chu, Y., Cheng, C., & Tsai, L. (2007). Energy Residue Aware (ERA) Clustering
Algorithm for Leach-based Wireless Sensor Networks. Conference: Systems and Networks
Communications.
[4] Gajjar, S., Dasgupta, K., Pradhan, S., &Vala, K. (2012). Lifetime improvement of LEACH protocol
for Wireless Sensor Network. 2012 Nirma University International Conference on Engineering
(NUiCONE),1-6.Retrievedfrom
http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6493233&isnumber=6493172
[5] Gambhir, S., & Fatima, N. (2014). Op-LEACH: An Optimized LEACH Method for Busty Traffic in
WSNs. Fourth International Conference in Advanced Computing & Communication Technologies
(ACCT), 222-229.
[6] Gnanambigai, J., Rengarajan, N., &Prarthana, R. (2014). An analytical approach for quadrant based
leach: An energy efficient routing protocol for WSNs. 2nd International Conference on Devices,
Circuits and Systems (ICDCS), 1-6. Retrieved from
http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6926117&isnumber=6926115
[7] Guo, L., Xie, Y., Yang, C., & Jing, Z. (2010). Improvement on LEACH by combining Adaptive
Cluster Head Election and Two-hop transmission.2010 International Conference on Machine Learning
and Cybernetics (ICMLC), 4, 1678-1683.
[8] Halperin, D., Greenstein, B., Sheth, A., &Wetherall, D. (2010). Demystifying 802.11n Power
Consumption. Proceeding HotPower'10 Proceedings of the 2010 International Conference on Power
Aware Computing and Systems, 1(1).
[9] Haiming, Y., &Sikdar, B. (2007). Optimal Cluster Head Selection in the LEACH Architecture. IEEE
International in Performance, Computing, and Communications Conference, 93-100.
[10] Heinzelman, W., Chandrakasan, A., &Balakrishnan, H. (2000). Energy-Efficient Communication
Protocol for Wireless MicrosensorNetworks.Proceedings of the 33rd Hawaii International Conference
on System Sciences.
[11] Huang, J., & Yen, P. (2009). CB-DHRP: A Cluster-Based Directed Hierarchical Routing Protocol for
wireless sensor networks.International Symposium in Autonomous Decentralized Systems, 1-6.
[12] Javaid, N., Waseem, M., Khan, Z., Qasim, U., Latif, K., &Javaid, A. (2013). ACH: Away cluster
heads scheme for Energy Efficient Clustering Protocols in WSNs. Saudi International in Electronics,
Communications and Photonics Conference (SIECPC), 1-4. Retrieved from
http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6550972&isnumber=6550724
[13] Kang, S., & Nguyen, T. (2012). Distance Based Thresholds for Cluster Head Selection in Wireless
Sensor Networks. IEEE COMMUNICATIONS LETTERS, 16(9), 1396-1399.
[14] Kumar, G., Mehra, H., Seth, A., Radhakrishnan, P., Hemavathi, N., &Sudha, S. (2014). An hybrid
clustering algorithm for optimal clusters in Wireless sensor networks. IEEE Students' Conference on
Electrical, Electronics and Computer Science (SCEECS), 1-6. Retrieved from
http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6804442&isnumber=6804412
[15] Li, Y., Yu, N., Zhang, W., & Zhao, W. (2011). Enhancing the performance of LEACH protocol in
wireless sensor networks. IEEE Conference: Computer Communications Workshops.
[16] Liao, Q., & Zhu, H. (2013). An Energy Balanced Clustering Algorithm Based on LEACH Protocol.
Proceedings of the 2nd International Conference On Systems Engineering and Modeling.](https://image.slidesharecdn.com/02-200311093852/85/AN-ENHANCED-HYBRID-ROUTING-AND-CLUSTERING-TECHNIQUE-FOR-WIRELESS-SENSOR-NETWORK-15-320.jpg)
![International Journal of Wireless & Mobile Networks (IJWMN) Vol. 12, No. 1, February 2020
28
[17] Maurya, P., Kaur, A., &Choudhary, R. (2014). Behavior analysis of LEACH protocol. International
Conference on Parallel, Distributed and Grid Computing (PDGC), 68-71. Retrieved from
http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=7030717&isnumber=7030698
[18] Ramesh, K., &Somasundaram, K. (2011). A COMPARATIVE STUDY OF CLUSTERHEAD
SELECTION ALGORITHMS IN WIRELESS SENSOR NETWORKS. International Journal of
Computer Science & Engineering Survey, 2(4), 153-164.
[19] Ran, G., Zhang, H., & Gong, S. (2010). Improving on LEACH Protocol of Wireless Sensor Networks
Using Fuzzy Logic. Journal of Information & Computational Science, 7(3), 767-775.
[20]Sharma, I., Singh, R., &Khurana, M. (2015). Comparative study of LEACH, LEACH-C and PEGASIS
routing protocols for wireless sensor network. International Conference on Advances in Computer
Engineering and Applications (ICACEA), 842-846. Retrieved from
http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=7164821&isnumber=7164643
[21] Sharma, S., &Choudhary, S. (2014). Heterogeneous multi-hop LEACH routing protocol. International
Conference on Green Computing Communication and Electrical Engineering (ICGCCEE), 1-6.
Retrieved from
http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6922249&isnumber=6920919
[22] Schmidt-Eisenlohr, F. (2010). Interference in Vehicle-to-vehicle Communication Networks: Analysis,
Modelling, Simulation and Assessment (p. 149). KIT Scientific Publishing. ISBN: 9783866445710
[23] Tillapart, P., Thammarojsakul, S., Thumthawatworn, T., &Santiprabhob, P. (2005). An Approach to
Hybrid Clustering and Routing in Wireless Sensor Networks. 2005 IEEE in Aerospace Conference, 1-
8.
[24] Tran, S., & Yang, T. (2007). OCO: Optimized Communication & Organization for Target Tracking in
Wireless Sensor Networks. University of Houston.
[25] Tsai, M., & Chen, Y. (2015). A Virtual Cluster Head Election Scheme for Energy-Efficient Routing in
Wireless Sensor Networks. 3rd International Conference in Future Internet of Things and Cloud
(FiCloud), 341-348.
[26] Tyagi, S., Gupta, S., Tanwar, S., & Kumar, N. (2013). EHE-LEACH: Enhanced heterogeneous
LEACH protocol for lifetime enhancement of wireless SNs. International Conference on Advances in
Computing, Communications and Informatics (ICACCI), 1485-1490. Retrieved from
http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6637399&isnumber=6637135
[27] Yan, L., Pan, W., Luo, B., Liu, J., &Xu, M. (2009). Communication protocol based on optical low-
energy-adaptive-clustering-hierarchy (O-LEACH) for hybrid optical wireless sensor networks.
Communications and Photonics Conference and Exhibition (ACP), 1-6. Retrieved from
http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=5405443&isnumber=5405166
[28] Zhang, J., Mao, Z., &Jia, R. (2013). Study on hybrid modelling approach for gold cyanidation
leaching process. 25th Chinese in Control and Decision Conference (CCDC), 1557-1561. Retrieved
from http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6561176&isnumber=6560882
[29] Zhao, F., Xu, Y., & Li, R. (2012). Improved LEACH Routing Communication Protocol for a Wireless
Sensor Network. International Journal of Distributed Sensor Networks, 1, 1-6.
[30] Zhao, W., & Zhang, L. (2014). Analysis and research of improved LEACH routing protocol for
pressure sensor based on WSN. Cyberspace Technology (CCT 2014), International Conference, 1-6.
[31] Sukhchandan Randhawa & Sushma Jain (2019). MLBC: Multi-objective Load Balancing Clustering
technique in Wireless Sensor Networks. Journal of Applied Soft Computing. ELSEVIER. Volume 74,
January 2019, Pages 66-89.
[32] Kaswan A., Singh V., Jana P.K. (2018). A multi-objective and PSO based energy efficient path design
for mobile sink in wireless sensor networks. Pervasive Mob. Comput., 46 , pp. 122-136
[33] Amit Sarkar1 & T. Senthil Murugan. (2019). Cluster head selection for energy efficient and delay-less
routing in wireless sensor network. Wireless Netw (2019) 25:303–320. Springer.](https://image.slidesharecdn.com/02-200311093852/85/AN-ENHANCED-HYBRID-ROUTING-AND-CLUSTERING-TECHNIQUE-FOR-WIRELESS-SENSOR-NETWORK-16-320.jpg)

































































![[HIFLUX] High Pressure Tube Support Catalog 2025](https://cdn.slidesharecdn.com/ss_thumbnails/tubesupporten-250529073613-16c22974-thumbnail.jpg?width=560&fit=bounds)