An inconvenient truth: Evading the Ransomware Protection in windows 10 @ LeHack
- 1. An Inconvenient Truth: Evading the Ransomware Protection in Windows 10
- 2. My Profile SOYA AOYAMA Security Researcher @ Fujitsu System Integration Laboratories Ltd Organizer @ BSides Tokyo 1992 ~ 2015 software developer of Windows. 2015 ~ security researcher - 2016 AVTOKYO - 2017 BSides Las Vegas - 2018 GrrCON / ToorCon / DerbyCon / AVTOKYO - 2019 HackMiami 2018 ~ BSides Tokyo Organizer - 2018 first BSides in East Asia
- 3. My research history 2016 2017 2018 2019 Jump the AirGap Way to escalate privilege to Administrator Way to evading the ransomware protection
- 4. How to escalate privileges to administrator in latest Windows” • Basic Concept • Detail
- 5. When I execute the CompMgmtLauncher It all started...
- 6. CompMgmtLauncher.exe – does not display the UAC screen – executes with administrator privileges – loads 3rd Party dll (in Program Files folder) Which process can access Program Files folder? – Explorer.exe? Which means... UAC bypass
- 7. I searched the Explorer So...
- 8. Explorer.exe – loads OneDrive dll (in User's Folder) – can access Program Files folder I found a way to get administrator privileges Which means... UAC bypass
- 9. Basic Concept DLL Func_A() DLL Func_A() Replace the correct dll with malicious one Pass through the function to the correct dll EXE DLLMalicious DLL Call Func_A() EXE Call Func_A() Malicious DLL Call Func_A() Func_A() Func_A()?
- 10. the implementation necessary 1. Load the correct DLL and get its handle hModule = LoadLibraryEx(lpLibFileName, hFile, dwFlags); 2. Get address of each function using handle Address = GetProcAddress(hModule, lpProcName); 3. When called from EXE, call the corresponding function with the correct arguments return Address(arg1, arg2, …); To realize concept
- 11. What functions the dll has I used the dumpbin command
- 12. Only need to implement four export functions So... EXE Call LoadLibraryEx() Call DllCanUnloadNow() Call DllGetClassObject() Call DllRegisterServer() Call DllUnregisterServer() Malicious DLL Call LoadLibraryEx() Call DllCanUnloadNow() Call DllGetClassObject() Call DllRegisterServer() Call DllUnregisterServer() DllMain() DllCanUnloadNow() DllGetClassObject() DllRegisterServer() DllUnregisterServer() DLL DllMain() DllCanUnloadNow() DllGetClassObject() DllRegisterServer() DllUnregisterServer()
- 13. Describe on Microsoft web site. – HRESULT DllCanUnloadNow(void); – HRESULT DllGetClassObject(REFCLSID rclsid, REFIID riid, LPVOID *ppv); – HRESULT DllRegisterServer(void); – HRESULT DllUnregisterServer (void); Export functions API https://docs.microsoft.com/en-us/windows/desktop/api/_com/
- 14. Source Code #include <Shobjidl.h> typedef HRESULT(__stdcall *CUN)(void); typedef HRESULT(__stdcall *GCO)(REFCLSID rclsid, REFIID riid, LPVOID *ppv); typedef HRESULT(__stdcall *RS)(void); typedef HRESULT(__stdcall *US)(void); CUN CanUnloadNow; GCO GetClassObject; RS RegisterServer; US UnregisterServer; BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved) { if (DLL_PROCESS_ATTACH == ul_reason_for_call) { WCHAR dll[MAX_PATH + 1] = { 0 }; GetModuleFileName(hModule, dll, MAX_PATH); wcscat(dll, L"_"); HINSTANCE hDllInstance = ::LoadLibraryEx(dll, NULL, LOAD_WITH_ALTERED_SEARCH_PATH); CanUnloadNow = (CUN)GetProcAddress(hDllInstance, "DllCanUnloadNow"); GetClassObject = (GCO)GetProcAddress(hDllInstance, "DllGetClassObject"); RegisterServer = (RS)GetProcAddress(hDllInstance, "DllRegisterServer"); UnregisterServer = (US)GetProcAddress(hDllInstance, "DllUnregisterServer"); } return TRUE; } STDAPI DllCanUnloadNow(void) { return CanUnloadNow(); } STDAPI DllGetClassObject(REFCLSID rclsid, REFIID riid, LPVOID *ppv) { return GetClassObject(rclsid, riid, ppv); } STDAPI DllRegisterServer(void) { return RegisterServer(); } STDAPI DllUnregisterServer(void) { return UnregisterServer(); } Malicious code has been removed
- 15. File Process Low Integrity Level Medium Integrity Level High Integrity Level System Integrity Level Malicious. bat Any Folder Malicious.dllMalicious.dll Malicious. batMalicious. bat Any Folder Mechanism User executes malicious program
- 16. File %UserProfile%...OneDrive Malicious.bat Any Folder Malicious.dll FileSyncShell64.dll_ Malicious.dll FileSyncShell64.dllFileSyncShell64.dll Process Low Integrity Level Medium Integrity Level High Integrity Level System Integrity Level Malicious. bat Mechanism Malicious program replaces correct dll with itself
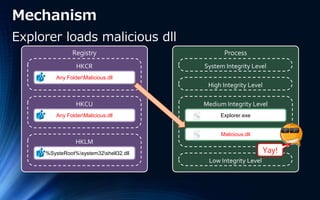
- 17. File Process Low Integrity Level Medium Integrity Level High Integrity Level System Integrity Level Explorer.exe %UserProfile%...OneDrive FileSyncShell64.dll FileSyncShell64.dll_ Any Folder Malicious.dllMalicious.dll Malicious.bat Any Folder FileSyncShell64.dllFileSyncShell64.dll Mechanism Explorer loads malicious dll
- 18. File FileSyncShell64.dll FileSyncShell64.dll_ c:Program FilesWinMerge %UserProfile%...OneDrive ShellExtensionX64.dll_ FileSyncShell64.dllFileSyncShell64.dll ShellExtensionX64.dllShellExtensionX64.dll Process Low Integrity Level Medium Integrity Level High Integrity Level System Integrity Level Explorer.exe FileSyncShell64.dll UAC bypass Mechanism Malicious program replaces correct dll with itself Need Administrator privileges
- 19. File c:Program FilesWinMerge ShellExtensionX64.dll ShellExtensionX64.dll_ %UserProfile%...OneDrive FileSyncShell64.dll FileSyncShell64.dll_ c:windowssystem32 CompMgmtLauncher.exe Process Low Integrity Level Medium Integrity Level High Integrity Level System Integrity Level Explorer.exe FileSyncShell64.dll Mechanism Malicious program executes CompMgmtLauncher
- 20. Process Medium Integrity Level High Integrity Level Explorer.exe FileSyncShell64.dll File c:Program FilesWinMerge %UserProfile%...OneDrive FileSyncShell64.dll ShellExtensionX64.dll ShellExtensionX64.dll c:windowssystem32 CompMgmtLauncher.exeCompMgmtLauncher.exe ShellExtensionX64.dll Yay! Mechanism Malicious program gets administrative privileges CompMgmtLauncher.exe Need Administrator privileges UAC bypass
- 23. I submitted a vulnerability report MSRC said…
- 24. MSRC said… can not pay the reward
- 25. ProcessFile c:Program FilesWinMerge %UserProfile%...OneDrive FileSyncShell64.dll ShellExtensionX64.dll c:windowssystem32 CompMgmtLauncher.exeCompMgmtLauncher.exe ShellExtensionX64.dll Medium Integrity Level High Integrity Level Explorer.exe FileSyncShell64.dll CompMgmtLauncher.exe ShellExtensionX64.dll Microsoft quietly fixed!! However… This issue has been fixed
- 26. May 12, 2017
- 27. May 12, 2017
- 28. Microsoft gave one answer for it
- 29. TANMAY GANACHARYA Principal Group Manager, Windows Defender Research Ransomware protection on Windows 10 For end users, the dreaded ransom note announces that ransomware has already taken their files hostage: documents, precious photos and videos, and other important files encrypted. On Windows 10 Fall Creators Update, a new feature helps stop ransomware from accessing important files in real-time, even if it manages to infect the computer. When enabled, Controlled folder access locks down folders, allowing only authorized apps to access files. https://www.microsoft.com/security/blog/2017/10/23/ stopping-ransomware-where-it-counts-protecting- your-data-with-controlled-folder-access/
- 32. The truth is …
- 34. Windows system folder is NOT protected by default.
- 36. The truth is …
- 39. apps folders allowed apps cmdExplorer Protected folders Documents Pictures PowerShell System32 Ransomware protection Mechanism
- 40. You ain’t Seen nothin' yet!
- 41. app folders allowed apps cmdExplorer Protected folders Documents Pictures PowerShell System32 Simple Idea
- 42. YAGO JESUS MICROSOFT ANTI RANSOMWARE BYPASS By default, Office executables are included in the whitelist so these programs could make changes in protected folders without restrictions. This access level is granted even if a malicious user uses OLE/COM objects to drive Office executables programmatically. So a Ransomware developer could adapt their software to use OLE objects to change / delete / encrypt files invisibly for the files owner http://www.securitybydefault.com/2018/01/microsoft-anti-ransomware-bypass-not.html
- 43. My method is …
- 45. I'll explain now
- 46. Why does Explorer load OneDrive dll? It all started ...
- 47. I searched in the registry It was found in HKEY_CLASSES_ROOT
- 48. HKCR is that merges HKLM with HKCU HKCU takes precedence from HKLM What HKEY_CLASSES_ROOT? https://docs.microsoft.com/en-us/windows/desktop/sysinfo/merged-view-of-hkey-classes-root
- 49. I found it Which dll meets the requirements?
- 50. File Process Low Integrity Level Medium Integrity Level High Integrity Level System Integrity Level Malicious. bat Any Folder Malicious.dllMalicious.dll Malicious. bat Any Folder Malicious. bat User executes malicious program Mechanism
- 51. Process Low Integrity Level Medium Integrity Level High Integrity Level System Integrity Level Malicious. bat Registry Malicious.bat HKCR Malicious.bat HKCUSoftwareClasses Malicious.bat HKLMSoftwareClasses %SysteRoot%system32shell32.dll Any FolderMalicious.dll %SysteRoot%system32shell32.dllAny FolderMalicious.dll Mechanism Malicious program writes malicious path in HKCU
- 52. Registry Malicious.bat HKCR Malicious.bat HKCU Malicious.bat HKLM Malicious.batAny FolderMalicious.dll Malicious.batAny FolderMalicious.dll Malicious.bat%SysteRoot%system32shell32.dll Process Low Integrity Level Medium Integrity Level High Integrity Level System Integrity Level Explorer.exe Malicious.dll Yay! Mechanism Explorer loads malicious dll
- 53. It’s revenge I submitted a vulnerability report MSRC said…
- 54. MSRC said… can not pay the reward
- 55. The bar for security servicing Security Boundary Security Goal Network boundary An unauthorized network endpoint cannot access or tamper with the code and data on a customer’s device. Kernel boundary A non-administrative user mode process cannot access or tamper with kernel code and data. Administrator-to-kernel is not a security boundary. Process boundary An unauthorized user mode process cannot access or tamper with the code and data of another process. AppContainer sandbox boundary An AppContainer-based sandbox process cannot access or tamper with code and data outside of the sandbox based on the container capabilities User boundary A user cannot access or tamper with the code and data of another user without being authorized. Session boundary A user logon session cannot access or tamper with another user logon session without being authorized. Web browser boundary An unauthorized website cannot violate the same-origin policy, nor can it access or tamper with the native code and data of the Microsoft Edge web browser sandbox. Virtual machine boundary An unauthorized Hyper-V guest virtual machine cannot access or tamper with the code and data of another guest virtual machine; this includes Hyper-V Isolated Containers. Virtual Secure Mode boundary Data and code within a VSM trustlet or enclave cannot be accessed or tampered with by code executing outside of the VSM trustlet or enclave. https://www.microsoft.com/en-us/msrc/windows-security-servicing-criteria
- 56. https://www.microsoft.com/en-us/msrc/windows-security-servicing-criteria Defense-in-depth security features Security feature Security Goal User Account Control (UAC) Prevent unwanted system-wide changes (files, registry, etc) without administrator consent AppLocker Prevent unauthorized applications from executing Controlled Folder Access Protect access and modification to controlled folders from apps that may be malicious Mark of the Web (MOTW) Prevent active content download from the web from elevating privileges when viewed locally Kernel Address Space Layout Randomization (KASLR) The layout of the kernel virtual address space is not predictable to an attacker (on 64-bit) Control Flow Guard (CFG) CFG protected code can only make indirect calls to valid indirect call targets Windows Defender Exploit Guard (WDEG) Allow apps to enable additional defense-in-depth exploit mitigation features that make it more difficult to exploit vulnerabilities Protected Process Light (PPL) Prevent non-administrative non-PPL processes from accessing or tampering with code and data in a PPL process via open process functions Shielded Virtual Machines Help protect a VM’s secrets and its data against malicious fabric admins or malware running on the host from both runtime and offline attacks NOT covered by active bug bounty programs User Account Control (UAC) Controlled Folder Access
- 57. How about others antimalware application?
- 63. No antimalware application can block my malware
- 64. About the Local Hacking No rewards No researcher No secure
Editor's Notes
- #2: Bonjour tout le monde. Je m‘appelle Soya Aoyama. As I cannot speak French, I’ll give a presentation in English. In fact, I'd like to use Japanese. OK… Today’s presentation is “An Inconvenient Truth: Evading the Ransomware Protection in Windows 10” I'm very happy to give a presentation here. ⏎
- #3: First, let me introduce myself. I’m Soya Aoyama. I’m security researcher @ Fujitsu System Integration Laboratories Limited, and organizer @ B-Sides Tokyo. I’ve been working for Fujitsu more than 20 years… as Windows software developer. I wrote NDIS drivers, Bluetooth profiles, Winsock applications, and more. I’ve started security research… about 4 years ago. My first presentation was @ AV-TOKYO. It’s one of the most famous security conference in Japan, and the motto is “no drink, no hack.” So I gave a presentation while drinking. To be honest, I'd like to do the same today, but I refrain from it. ⏎
- #4: This is my research history about local hacking. In 2016, I was researching about jump the air gap. At that time, I found way to escalate privilege to Administrator. So, in 2017, I gave a presentation it at BSides Las Vegas. In Last year, I found way to evading the ransomware protection, and gave a presentation it at grrcon, toorcon, derbycon and hack Miami. This year, I found new issue, submitted CFP, and I'm here. However, I cannot talk about the issue. Because it is not fixed. I am looking forward to meeting you next year. ⏎
- #5: Next, I’d like to talk a little about way to escalate privileges to administrator. ⏎
- #6: It all started. when I execute the CompMgmtLauncher, it's running with high integrity level, and is loading ShellExtensionX64.dll. Unbelievably, it’s 3rd party dll. ⏎
- #7: CompMgmtLauncher.exe does not display the UAC screen and executes with administrator privileges. Which means... ⏎ It’s UAC bypass. And loads 3rd Party dll in Program Files Folder. ⏎ What processes can access Program Files folder? What about Explorer? ⏎
- #8: So, I searched the Explorer. Explorer is loading OneDrive dll. Unbelievably, It’s in the User’s folder. ⏎
- #9: Explorer loads OneDrive dll in User's Folder, and can access Programmer's Folder. Which means... ⏎ I found a way to get administrator privileges. ⏎
- #10: My basic concept is that replace the correct dll with malicious one. ⏎ However, if exe call the function, ⏎ malicious dll does not know it. ⏎ So, I thought that malicious dll should passthrough the function to the correct dll. ⏎
- #11: The following is the implementation necessary to realize the concept. ⏎
- #12: What functions the dll has? I checked it using the dumpbin command. ⏎ FileSysncShell64.dll has four export functions DllCanUnloadNow, DllGetClassObject, DllRegisterServer, DllUnregisterServer and one test function. ⏎ And ShellExtensionX64.dll has same four export functions. ⏎
- #13: So, only need to implement four export functions. And it's very easy. ⏎
- #14: Because the export functions API are described on Microsoft web site. ⏎
- #15: This is the source code, but malicious code has been removed. ⏎
- #16: Then, I explain detail of mechanism. ⏎ When a user executes a malicious program. For example, by targeted email attack or watering hole attack. ⏎
- #17: ⏎ Malicious program renames correct dll. ⏎ And copies itself. ⏎
- #18: When the system restart, ⏎ Explorer loads malicious dll ⏎
- #19: It’s same process, but this time need administrator privileges, because it’s Program Files folder. However, Explorer can access it. ⏎ So, malicious program can rename correct dll to another. ⏎ And copies itself. ⏎
- #20: ⏎ Further, executes the CompMgmtLauncher. ⏎
- #21: The CompMgmtLauncher has UAC bypass, ⏎ So, executes by high integrity level. ⏎ And loads malicious dll. ⏎ A malicious program has get the administrator privileges ⏎
- #22: I have a demonstration video. Please watch it. ⏎
- #23: Then, Microsoft has the bug bounty program. I thought this issue is very dangerous, and I wanted a little pocket money, so… ⏎
- #24: I submitted a vulnerability report to MSRC. MSRC said… ⏎
- #25: “this does not meet the bar for security servicing” ⏎ So, can not pay the reward. ⏎
- #26: However… ⏎ This issue has been fixed. Microsoft quietly fixed like CompMgmtLauncher executes with medium integrity level. Microsoft must not have paid the reward ⏎
- #27: Let’s move on to the next topic. May 12, 2017… What happen? Do you remember? ⏎
- #28: It’s a day of cyber-attack by WannaCry. It caused tremendous damage all of the world. ⏎
- #29: Microsoft gave one answer for it. ⏎
- #30: It’s ransomware protection. That fall, Microsoft implemented it on Windows 10 Fall Creators Update. ⏎
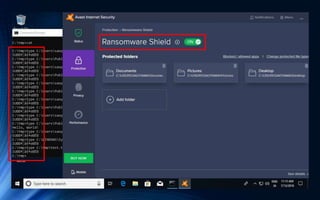
- #31: This is ransomware protection screen. Ransomware protection has Controlled folder access. However it’s off by default. If turn on it, ⏎ “protected folders” and “allow an app through Controlled folder access” are displayed. Let’s look each item. ⏎
- #32: First, here is “protected folders”. Administrator can add folder he wants, and there are folders protected by default. Documents, Pictures, Videos, Music, Desktop and Favorites. Just a moment. There is a strange phrase. ⏎ Windows system folders are protected by default. Usually system folder is “c:\windows\system32”, but there is not include in this list. ⏎
- #33: What is the truth? I’ll show you in demonstration from now.
- #34: I have a demonstration video. Please watch it. ⏎
- #35: The truth is… ⏎ Windows system folder is not protected by default. ⏎
- #36: Next, here is “Allow an app through Controlled folder access”. Administrator can add applications that can access “Protected folders”. However, there is no default list. Just a moment. There is a strange phrase too. ⏎ “Apps determined by Microsoft as friendly are always allowed”. What does friendly? ⏎
- #37: What is the truth? I’ll show you in demonstration from now.
- #38: I have a demonstration video. Please watch it. ⏎
- #39: The truth is… ⏎ Microsoft only knows. ⏎
- #40: This is ransomware protection mechanism. All applications can access all folders by default. When administrator enables the ransomware protection, ⏎ allowed apps can access protected folders, but the others apps cannot access its. ⏎
- #41: You ain’t Seen nothin' yet! Now, I found a vulnerability of “Ransomware protection”. ⏎
- #42: My idea is very simple. If we can inject malware into allowed apps, ⏎ We can access “protected folders”. And there is Explorer here. ⏎
- #43: There was similar research. Yago’s idea is using Microsoft Office. ⏎
- #44: This time I used a different method. I’ll show you in demonstration from now.
- #45: I have a demonstration video. Please watch it. ⏎
- #46: My method is… ⏎ I'll explain now. ⏎
- #47: It all started… I wondered why can Explorer load OneDrive dll, because the folder different every version. ⏎
- #48: So, I searched in the registry. It was found in HKCR. ⏎
- #49: HKCR is that merges HKLM with HKCU, And HKCU takes precedence from HKLM. Which means... If the explorer loads a dll, and its path is written to HKLM, we can make Explorer load a malicious dll. ⏎
- #50: Which dll meets the requirements? I found it. It’s shell32.dll ⏎
- #51: Then, I explain detail of mechanism. ⏎ When a user executes a malicious program. ⏎
- #52: ⏎ Usually, it reflects the path of shell32.dll in HKLM to HKCR. ⏎ However, when malicious program writes malicious path in HKCU, it reflects to HKCR. ⏎
- #53: When the system restart, ⏎ Explorer loads malicious dll ⏎ Yay! ⏎
- #54: It’s revenge. Payback time. I submitted a vulnerability report to MSRC again. MSRC said… ⏎
- #55: “this does not meet the bar for security servicing”. ⏎ So, can not pay the reward. ⏎
- #56: I searched the bar for security servicing on Microsoft web site. Certainly, it’s not meets. ⏎
- #57: Moreover, UAC and Controlled Folder Access are NOT covered by active bug bounty programs. I give up getting rewards. ⏎
- #58: I understand that Microsoft thinking. Then, how about others anti-malware application? ⏎
- #59: This is a Market share of Windows anti-malware application vendors. There are Avast, ESET, Malwarebytes, McAfee, and more. ⏎ I checked these. ⏎
- #60: First. Avast Internet Security has ⏎ the “Ransomware Shield”. But ⏎ my malicious dll was able to encrypt the text file… without being blocked. ⏎
- #61: Next. ESET Smart security has ⏎ the “Ransomware Shield”. But ⏎ it is the same result. ⏎
- #62: Next. Malwarebytes Premium has ⏎ the “Ransomware Protection”. But ⏎ it is the same result. ⏎
- #63: Next. McAfee has ⏎ the “Ransomware Interceptor”. But ⏎ it is the same result. ⏎
- #64: As far as I’ve checked, anti-malware applications cannot block my malware. ⏎
- #65: Finally, It’s conclusion. Microsoft does not admit vulnerability and not pay rewards. ⏎ Well then, nobody researches it. ⏎ Which means, it’s not secure. ⏎ It’s time to start taking local hacking seriously. ⏎
- #66: OK, my presentation is over. Merci beaucoup.













![Source Code
#include <Shobjidl.h>
typedef HRESULT(__stdcall *CUN)(void);
typedef HRESULT(__stdcall *GCO)(REFCLSID rclsid, REFIID riid, LPVOID *ppv);
typedef HRESULT(__stdcall *RS)(void);
typedef HRESULT(__stdcall *US)(void);
CUN CanUnloadNow;
GCO GetClassObject;
RS RegisterServer;
US UnregisterServer;
BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved)
{
if (DLL_PROCESS_ATTACH == ul_reason_for_call) {
WCHAR dll[MAX_PATH + 1] = { 0 };
GetModuleFileName(hModule, dll, MAX_PATH);
wcscat(dll, L"_");
HINSTANCE hDllInstance = ::LoadLibraryEx(dll, NULL, LOAD_WITH_ALTERED_SEARCH_PATH);
CanUnloadNow = (CUN)GetProcAddress(hDllInstance, "DllCanUnloadNow");
GetClassObject = (GCO)GetProcAddress(hDllInstance, "DllGetClassObject");
RegisterServer = (RS)GetProcAddress(hDllInstance, "DllRegisterServer");
UnregisterServer = (US)GetProcAddress(hDllInstance, "DllUnregisterServer");
}
return TRUE;
}
STDAPI DllCanUnloadNow(void) { return CanUnloadNow(); }
STDAPI DllGetClassObject(REFCLSID rclsid, REFIID riid, LPVOID *ppv) { return GetClassObject(rclsid, riid, ppv); }
STDAPI DllRegisterServer(void) { return RegisterServer(); }
STDAPI DllUnregisterServer(void) { return UnregisterServer(); }
Malicious code has been removed](https://image.slidesharecdn.com/localhack2-190710014746/85/An-inconvenient-truth-Evading-the-Ransomware-Protection-in-windows-10-LeHack-14-320.jpg)