Application Security Architecture and Threat Modelling
Download as PPTX, PDF6 likes4,520 views
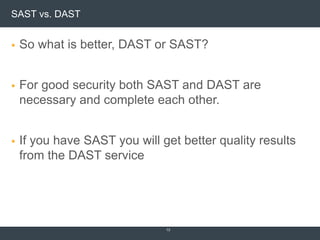
95% of attacks are against “Web Servers and Web Applications” Security Architecture and SDLC 3 Tier – Web App Architecture Would you trust the code? Traditional SDLC Secure SDLC SAST vs. DAST
1 of 50
Downloaded 233 times

















































Ad
Recommended
Static Analysis Security Testing for Dummies... and You



Static Analysis Security Testing for Dummies... and YouKevin Fealey Most enterprise application security teams have at least one Static Analysis Security Testing (SAST) tool in their tool-belt; but for many, the tool never leaves the belt. SAST tools have gotten a reputation for being slow, error-prone, and difficult to use; and out of the box, many of them are – but with a little more knowledge behind how these tools are designed, a SAST tool can be a valuable part of any security program.
In this talk, we’ll help you understand the strengths and weaknesses of SAST tools by illustrating how they trace your code for vulnerabilities. You’ll see out-of-the-box rules for commercial and open-source SAST tools, and learn how to write custom rules for the widely-used open source SAST tool, PMD. We’ll explain the value of customizing tools for your organization; and you’ll learn how to integrate SAST technologies into your existing build and deployment pipelines. Lastly, we’ll describe many of the common challenges organizations face when deploying a new security tool to security or development teams, as well as some helpful hints to resolve these issues
7 Steps to Threat Modeling



7 Steps to Threat ModelingDanny Wong Threat Modeling has become an integral part of Microsoft's SDL (Security Development Lifecycle) process
Threat Modeling And Analysis



Threat Modeling And AnalysisLalit Kale This presentation is part of one of talk, I gave in Microsoft .NET Bootcamp. The contents are slightly edited to share the information in public domain. In this presentation, I covered the significance and all related theory of Threat modeling and analysis.This presentation will be useful for software architects/Managers,developers and QAs. Do share your feedback in comments.
Application Security



Application SecurityReggie Niccolo Santos * Brief timeline on cyber attack history
* Definition
* Foundations of Security
* Definition of Terms
* Threat Modeling
* Application Vulnerability Categories
* Core Security Principles
* Web Application Security
* Risks and Risk Mitigation/Control Measures
Chapter 2 Hardware and Software



Chapter 2 Hardware and SoftwareAnjan Mahanta Hardware devices can be categorized as input, output, or storage. Internal hardware includes the central processing unit (CPU), motherboard, random access memory (RAM), read only memory (ROM), graphics card, and sound card. The CPU processes data and runs instructions. The motherboard connects components. RAM stores active programs and data, while ROM permanently stores basic instructions. External devices include monitors, keyboards, mice, printers, and cameras. Storage devices like hard disk drives and solid state drives non-volatile store data on a storage medium.
Secure Coding and Threat Modeling



Secure Coding and Threat ModelingMiriam Celi, CISSP, GISP, MSCS, MBA This document summarizes Miriam Celi's presentation on secure coding and threat modeling. The key points are:
1. Miriam Celi discussed secure coding principles and resources like CWE, CVE, and OWASP to help developers write more secure code. Threat modeling was presented as a way to identify risks and address them in the design process.
2. Threat modeling involves identifying threats, assets, and vulnerabilities in a system and making design decisions to mitigate risks. It is an iterative team activity that should be performed throughout development.
3. Resources like STRIDE, CAPEC, and Microsoft's threat modeling tool were presented to help structure the threat modeling process. Statistics on rising costs of
IT Security management and risk assessment



IT Security management and risk assessmentCAS Terminology
Security Risk Assessment
Detailed Risk Analysis Process
Asset Identification / System Characterizations
Threat Identification
Vulnerability Identification
Analyze Risks / Control Analysis
Likelihood Determination
Impact analysis / Consequence determination
Risk determination
Control Recommendation & Result Documentation
Hunting for Credentials Dumping in Windows Environment



Hunting for Credentials Dumping in Windows EnvironmentTeymur Kheirkhabarov My slides from Zero Nights 2017 talk - https://2017.zeronights.ru/report/hunting-for-credentials-dumping-in-windows-environment/
Secure coding practices



Secure coding practicesMohammed Danish Amber Secure Coding Practices - PHP.
How to safe gaurd your application from CSRF, Session Hijacking, SQLi
Cyber Threat Intelligence



Cyber Threat Intelligencemohamed nasri This document discusses cyber threat intelligence and strategies for defense. It begins with an introduction to cyber threat intelligence and discusses the cyber attack life cycle model from Lockheed Martin. It then addresses questions to consider regarding cyber threats. The document outlines threat intelligence standards and tools like STIX and TAXII, and discusses challenges with SIEM systems. It proposes architectures that incorporate threat intelligence to provide preventive, detective, and fusion capabilities. The presentation concludes with a discussion of data sources and architectures to support cyber threat analysis.
OWASP Top 10 2021 Presentation (Jul 2022)



OWASP Top 10 2021 Presentation (Jul 2022)TzahiArabov The document provides information about the OWASP Top 10 2021 list of web application security risks. It describes the top risk, A01: Broken Access Control, giving its definition, examples of vulnerabilities it can enable, prevention methods, and examples. It also summarizes the second and third top risks, A02: Cryptographic Failures and A03: Injection, in a similar manner.
Application Security - Your Success Depends on it



Application Security - Your Success Depends on itWSO2 Traditional information security mainly revolves around network and operating system (OS) level protection. Regardless of the level of security guarding those aspects, the system can be penetrated and the entire deployment can be brought down if your application's security isn't taken into serious consideration. Information security should ideally start at the application level, before network and OS level security is ensured. To achieve this, security needs to be integrated into the application at the software development phase.
In this session, Dulanja will discuss the following:
The importance of application security - why network and OS security is insufficient.
Challenges in securing your application.
Making security part of the development lifecycle.
Governance of security operation centers



Governance of security operation centersBrencil Kaimba This document provides an overview of governance of security operations centers. It discusses the impact of disruptive technologies on organizations and the need for security operations centers to manage security risks. It covers designing an effective SOC including defining threats, processes, technology and acquiring a SOC. Operating a SOC includes defining expectations, baselining normal activity, using threat intelligence and handling incidents. Qualities of analysts and measuring SOC success are also discussed. Sustainable SOC governance principles like investing in people and emphasizing teamwork are presented.
Introduction to Web Application Penetration Testing



Introduction to Web Application Penetration TestingAnurag Srivastava Web Application Pentesting
* Process to check and penetrate the security of a web application or a website
* process involves an active analysis of the application for any weaknesses, technical flaws, or vulnerabilities
* Any security issues that are found will be presented to the system owner, together with an assessment of the impact, a proposal for mitigation or a technical solution.
Security operation center (SOC)



Security operation center (SOC)Ahmed Ayman The document discusses security operation centers (SOCs) and their functions. It describes what a SOC is and its main purpose of monitoring, preventing, detecting, investigating and responding to cyber threats. It outlines the typical roles in a SOC including tier 1, 2 and 3 analysts and security engineers. It also discusses the common tools, skills needed for each role, and types of SOCs such as dedicated, distributed, multifunctional and virtual SOCs.
Penetration Testing Basics



Penetration Testing BasicsRick Wanner The document provides an overview of penetration testing basics from a presentation by The Internet Storm Center, SANS Institute, and GIAC Certification Program. It discusses the Internet Storm Center, SANS/GIAC training and certifications, common cyber threats, the methodology for penetration testing, tools used for various stages like reconnaissance, scanning, exploitation, and analysis, and the importance of reporting and mitigation strategies.
Vulnerability assessment and penetration testing



Vulnerability assessment and penetration testingAbu Sadat Mohammed Yasin This document discusses vulnerability assessment and penetration testing. It defines them as two types of vulnerability testing that search for known vulnerabilities and attempt to exploit vulnerabilities, respectively. Vulnerability assessment uses automated tools to detect known issues, while penetration testing employs hacking techniques to demonstrate how deeply vulnerabilities could be exploited like an actual attacker. Both are important security practices for identifying weaknesses and reducing risks, but require different skills and have different strengths, weaknesses, frequencies, and report outputs. Reasons for vulnerabilities include insecure coding, limited testing, and misconfigurations. The document outlines common vulnerability and attack types as well as how vulnerability assessment and penetration testing are typically conducted.
Security architecture



Security architectureDuncan Unwin This document provides an overview of how security architecture fits within enterprise architecture. It begins by noting that security architecture is a subset of enterprise architecture. It then discusses a presentation given on this topic, highlighting how security practices are often misunderstood by both IT and security professionals. The presentation explores how to better integrate security architecture with enterprise architecture frameworks and processes to ensure security priorities are properly considered throughout enterprise initiatives. It emphasizes the importance of understanding enterprise architecture, aligning security language with business needs, and using evidence-based approaches to integrate security architecture within overall enterprise architecture.
Security Training: #3 Threat Modelling - Practices and Tools



Security Training: #3 Threat Modelling - Practices and ToolsYulian Slobodyan This document provides an overview of threat modeling practices and tools. It begins with an introduction that defines threat modeling and outlines its benefits. It then covers threat modeling basics like principles, approaches and reasons it is avoided. The main threat modeling process is described, including creating diagrams, identifying threats and planning mitigations. Popular threat modeling tools and a demo are discussed. Standard mitigation techniques and a sample threat model appendix are also included.
Secure Design: Threat Modeling



Secure Design: Threat ModelingNarudom Roongsiriwong, CISSP Threat modeling is an approach for analyzing the security of an application. It is a structured approach that enables you to identify, quantify, and address the security risks associated with an application.
Cybersecurity Roadmap Development for Executives



Cybersecurity Roadmap Development for ExecutivesKrist Davood - Principal - CIO Secrets to managing your Duty of Care in an ever- changing world.
How well do you know your risks?
Are you keeping up with your responsibilities to provide Duty of Care?
How well are you prioritising Cybersecurity initiatives?
Liability for Cybersecurity attacks sits with Executives and Board members who may not have the right level of technical security knowledge. This session will outline what practical steps executives can take to implement a Cybersecurity Roadmap that is aligned with its strategic objectives.
Led by Krist Davood, who has spent over 28 years implementing secure mission critical systems for executives. Krist is an expert in protecting the interconnectedness of technology, intellectual property and information systems, as evidenced through his roles at The Good Guys, Court Services Victoria and Schiavello.
The seminar will cover:
• Fiduciary responsibility
• How to efficiently deal with personal liability and the threat of court action
• The role of a Cybersecurity Executive Dashboard and its ability to simplify risk and amplify informed decision making
• How to identify and bridge the gap between your Cybersecurity Compliance Rating and the threat of court action
Red Team Framework



Red Team Framework👀 Joe Gray Presented at the DEFCON27 Red Team Offensive Village on 8/10/19.
From the dawn of technology, adversaries have been present. They have ranged from criminal actors and curious children to - more modernly - nation states and organized crime. As an industry, we started to see value in emulating bad actors and thus the penetration test was born. As time passes, these engagements become less about assessing the true security of the target organization and more about emulating other penetration testers. Furthermore, these tests have evolved into a compliance staple that results in little improvement and increasingly worse emulation of bad actors.
In this presentation, we will provide a framework complementary to the Penetration Testing Execution Standard (PTES). This complementary work, the Red Team Framework (RTF), focuses on the objectives and scoping of adversarial emulation with increased focus on the perspective of the business, their threat models, and business models. The RTF borrows part of the PTES, adding emphasis on detection capabilities as well as purple team engagements. We believe this approach will better assist organizations and their defensive assets in understanding threats and building relevant detections.
SOC presentation- Building a Security Operations Center



SOC presentation- Building a Security Operations CenterMichael Nickle Presentation I used to give on the topic of using a SIM/SIEM to unify the information stream flowing into the SOC. This piece of collateral was used to help close the largest SIEM deal (Product and services) that my employer achieved with this product line.
Secure Code Review 101



Secure Code Review 101Narudom Roongsiriwong, CISSP Secure code review is probably the most effective technique to identify security bugs early in the system development lifecycle.
When used together with automated and manual penetration testing, code review can significantly increase the cost effectiveness of an application security verification effort. This presentation explain how can we start secure code review effectively.
Optimizing Security Operations: 5 Keys to Success



Optimizing Security Operations: 5 Keys to SuccessSirius Organizations are suffering from cyber fatigue, with too many alerts, too many technologies, and not enough people. Many security operations center (SOC) teams are underskilled and overworked, making it extremely difficult to streamline operations and decrease the time it takes to detect and remediate security incidents.
Addressing these challenges requires a shift in the tactics and strategies deployed in SOCs. But building an effective SOC is hard; many companies struggle first with implementation and then with figuring out how to take their security operations to the next level.
Read to learn:
--Advantages and disadvantages of different SOC models
--Tips for leveraging advanced analytics tools
--Best practices for incorporating automation and orchestration
--How to boost incident response capabilities, and measure your efforts
--How the NIST Cybersecurity Framework and CIS Controls can help you establish a strong foundation
Start building your roadmap to a next-generation SOC.
Secure coding practices



Secure coding practicesScott Hurrey This document provides an overview of secure coding practices for developers. It discusses secure design principles like defense in depth and least privilege. It also covers secure coding practices such as input validation, escaping, and HTML sanitization. The document provides examples of good and bad code related to reflecting user input, access control, and request authenticity. It also defines key security terms and outlines strategies for handling user input and encoding output.
Cyber Security Governance



Cyber Security GovernancePriyanka Aash Most organizations have good enterprise-level security policies that define their approach to maintaining, improving, and securing their information and information systems. However, once the policies are signed by senior leadership and distributed throughout the organization, significant cybersecurity governance challenges remain. In this workshop I will explain the transforming organizational security to strengthen defenses and integrate cybersecurity with the overall approach toward security governance, risk management and compliance.
NIST cybersecurity framework



NIST cybersecurity frameworkShriya Rai The NIST Cybersecurity Framework acts as a bridge between the management and Cybersecurity ecosystem.
Network Forensics and Practical Packet Analysis



Network Forensics and Practical Packet AnalysisPriyanka Aash Why Packet Analysis?
3 Phases - Analysis, Conversion & Collection
How do we do it ?
Statistics - Protocol Hierarchy
Statistics - End Points & Conversations
Practical Applications of Block Chain Technologies 



Practical Applications of Block Chain Technologies Priyanka Aash The document discusses blockchain technology and its potential practical uses. It begins by defining blockchain as a distributed digital ledger that allows participants in a network to securely record transactions without a central authority. It then provides examples of how blockchain could be used in healthcare to securely store electronic health records, enable smart contracts to automatically pay providers, and track medical devices to prevent counterfeiting. The document concludes by describing a hypothetical example where blockchain is used to give healthcare providers access to a patient's complete medical history from various sources to improve treatment while reducing redundant tests.
Ad
More Related Content
What's hot (20)
Secure coding practices



Secure coding practicesMohammed Danish Amber Secure Coding Practices - PHP.
How to safe gaurd your application from CSRF, Session Hijacking, SQLi
Cyber Threat Intelligence



Cyber Threat Intelligencemohamed nasri This document discusses cyber threat intelligence and strategies for defense. It begins with an introduction to cyber threat intelligence and discusses the cyber attack life cycle model from Lockheed Martin. It then addresses questions to consider regarding cyber threats. The document outlines threat intelligence standards and tools like STIX and TAXII, and discusses challenges with SIEM systems. It proposes architectures that incorporate threat intelligence to provide preventive, detective, and fusion capabilities. The presentation concludes with a discussion of data sources and architectures to support cyber threat analysis.
OWASP Top 10 2021 Presentation (Jul 2022)



OWASP Top 10 2021 Presentation (Jul 2022)TzahiArabov The document provides information about the OWASP Top 10 2021 list of web application security risks. It describes the top risk, A01: Broken Access Control, giving its definition, examples of vulnerabilities it can enable, prevention methods, and examples. It also summarizes the second and third top risks, A02: Cryptographic Failures and A03: Injection, in a similar manner.
Application Security - Your Success Depends on it



Application Security - Your Success Depends on itWSO2 Traditional information security mainly revolves around network and operating system (OS) level protection. Regardless of the level of security guarding those aspects, the system can be penetrated and the entire deployment can be brought down if your application's security isn't taken into serious consideration. Information security should ideally start at the application level, before network and OS level security is ensured. To achieve this, security needs to be integrated into the application at the software development phase.
In this session, Dulanja will discuss the following:
The importance of application security - why network and OS security is insufficient.
Challenges in securing your application.
Making security part of the development lifecycle.
Governance of security operation centers



Governance of security operation centersBrencil Kaimba This document provides an overview of governance of security operations centers. It discusses the impact of disruptive technologies on organizations and the need for security operations centers to manage security risks. It covers designing an effective SOC including defining threats, processes, technology and acquiring a SOC. Operating a SOC includes defining expectations, baselining normal activity, using threat intelligence and handling incidents. Qualities of analysts and measuring SOC success are also discussed. Sustainable SOC governance principles like investing in people and emphasizing teamwork are presented.
Introduction to Web Application Penetration Testing



Introduction to Web Application Penetration TestingAnurag Srivastava Web Application Pentesting
* Process to check and penetrate the security of a web application or a website
* process involves an active analysis of the application for any weaknesses, technical flaws, or vulnerabilities
* Any security issues that are found will be presented to the system owner, together with an assessment of the impact, a proposal for mitigation or a technical solution.
Security operation center (SOC)



Security operation center (SOC)Ahmed Ayman The document discusses security operation centers (SOCs) and their functions. It describes what a SOC is and its main purpose of monitoring, preventing, detecting, investigating and responding to cyber threats. It outlines the typical roles in a SOC including tier 1, 2 and 3 analysts and security engineers. It also discusses the common tools, skills needed for each role, and types of SOCs such as dedicated, distributed, multifunctional and virtual SOCs.
Penetration Testing Basics



Penetration Testing BasicsRick Wanner The document provides an overview of penetration testing basics from a presentation by The Internet Storm Center, SANS Institute, and GIAC Certification Program. It discusses the Internet Storm Center, SANS/GIAC training and certifications, common cyber threats, the methodology for penetration testing, tools used for various stages like reconnaissance, scanning, exploitation, and analysis, and the importance of reporting and mitigation strategies.
Vulnerability assessment and penetration testing



Vulnerability assessment and penetration testingAbu Sadat Mohammed Yasin This document discusses vulnerability assessment and penetration testing. It defines them as two types of vulnerability testing that search for known vulnerabilities and attempt to exploit vulnerabilities, respectively. Vulnerability assessment uses automated tools to detect known issues, while penetration testing employs hacking techniques to demonstrate how deeply vulnerabilities could be exploited like an actual attacker. Both are important security practices for identifying weaknesses and reducing risks, but require different skills and have different strengths, weaknesses, frequencies, and report outputs. Reasons for vulnerabilities include insecure coding, limited testing, and misconfigurations. The document outlines common vulnerability and attack types as well as how vulnerability assessment and penetration testing are typically conducted.
Security architecture



Security architectureDuncan Unwin This document provides an overview of how security architecture fits within enterprise architecture. It begins by noting that security architecture is a subset of enterprise architecture. It then discusses a presentation given on this topic, highlighting how security practices are often misunderstood by both IT and security professionals. The presentation explores how to better integrate security architecture with enterprise architecture frameworks and processes to ensure security priorities are properly considered throughout enterprise initiatives. It emphasizes the importance of understanding enterprise architecture, aligning security language with business needs, and using evidence-based approaches to integrate security architecture within overall enterprise architecture.
Security Training: #3 Threat Modelling - Practices and Tools



Security Training: #3 Threat Modelling - Practices and ToolsYulian Slobodyan This document provides an overview of threat modeling practices and tools. It begins with an introduction that defines threat modeling and outlines its benefits. It then covers threat modeling basics like principles, approaches and reasons it is avoided. The main threat modeling process is described, including creating diagrams, identifying threats and planning mitigations. Popular threat modeling tools and a demo are discussed. Standard mitigation techniques and a sample threat model appendix are also included.
Secure Design: Threat Modeling



Secure Design: Threat ModelingNarudom Roongsiriwong, CISSP Threat modeling is an approach for analyzing the security of an application. It is a structured approach that enables you to identify, quantify, and address the security risks associated with an application.
Cybersecurity Roadmap Development for Executives



Cybersecurity Roadmap Development for ExecutivesKrist Davood - Principal - CIO Secrets to managing your Duty of Care in an ever- changing world.
How well do you know your risks?
Are you keeping up with your responsibilities to provide Duty of Care?
How well are you prioritising Cybersecurity initiatives?
Liability for Cybersecurity attacks sits with Executives and Board members who may not have the right level of technical security knowledge. This session will outline what practical steps executives can take to implement a Cybersecurity Roadmap that is aligned with its strategic objectives.
Led by Krist Davood, who has spent over 28 years implementing secure mission critical systems for executives. Krist is an expert in protecting the interconnectedness of technology, intellectual property and information systems, as evidenced through his roles at The Good Guys, Court Services Victoria and Schiavello.
The seminar will cover:
• Fiduciary responsibility
• How to efficiently deal with personal liability and the threat of court action
• The role of a Cybersecurity Executive Dashboard and its ability to simplify risk and amplify informed decision making
• How to identify and bridge the gap between your Cybersecurity Compliance Rating and the threat of court action
Red Team Framework



Red Team Framework👀 Joe Gray Presented at the DEFCON27 Red Team Offensive Village on 8/10/19.
From the dawn of technology, adversaries have been present. They have ranged from criminal actors and curious children to - more modernly - nation states and organized crime. As an industry, we started to see value in emulating bad actors and thus the penetration test was born. As time passes, these engagements become less about assessing the true security of the target organization and more about emulating other penetration testers. Furthermore, these tests have evolved into a compliance staple that results in little improvement and increasingly worse emulation of bad actors.
In this presentation, we will provide a framework complementary to the Penetration Testing Execution Standard (PTES). This complementary work, the Red Team Framework (RTF), focuses on the objectives and scoping of adversarial emulation with increased focus on the perspective of the business, their threat models, and business models. The RTF borrows part of the PTES, adding emphasis on detection capabilities as well as purple team engagements. We believe this approach will better assist organizations and their defensive assets in understanding threats and building relevant detections.
SOC presentation- Building a Security Operations Center



SOC presentation- Building a Security Operations CenterMichael Nickle Presentation I used to give on the topic of using a SIM/SIEM to unify the information stream flowing into the SOC. This piece of collateral was used to help close the largest SIEM deal (Product and services) that my employer achieved with this product line.
Secure Code Review 101



Secure Code Review 101Narudom Roongsiriwong, CISSP Secure code review is probably the most effective technique to identify security bugs early in the system development lifecycle.
When used together with automated and manual penetration testing, code review can significantly increase the cost effectiveness of an application security verification effort. This presentation explain how can we start secure code review effectively.
Optimizing Security Operations: 5 Keys to Success



Optimizing Security Operations: 5 Keys to SuccessSirius Organizations are suffering from cyber fatigue, with too many alerts, too many technologies, and not enough people. Many security operations center (SOC) teams are underskilled and overworked, making it extremely difficult to streamline operations and decrease the time it takes to detect and remediate security incidents.
Addressing these challenges requires a shift in the tactics and strategies deployed in SOCs. But building an effective SOC is hard; many companies struggle first with implementation and then with figuring out how to take their security operations to the next level.
Read to learn:
--Advantages and disadvantages of different SOC models
--Tips for leveraging advanced analytics tools
--Best practices for incorporating automation and orchestration
--How to boost incident response capabilities, and measure your efforts
--How the NIST Cybersecurity Framework and CIS Controls can help you establish a strong foundation
Start building your roadmap to a next-generation SOC.
Secure coding practices



Secure coding practicesScott Hurrey This document provides an overview of secure coding practices for developers. It discusses secure design principles like defense in depth and least privilege. It also covers secure coding practices such as input validation, escaping, and HTML sanitization. The document provides examples of good and bad code related to reflecting user input, access control, and request authenticity. It also defines key security terms and outlines strategies for handling user input and encoding output.
Cyber Security Governance



Cyber Security GovernancePriyanka Aash Most organizations have good enterprise-level security policies that define their approach to maintaining, improving, and securing their information and information systems. However, once the policies are signed by senior leadership and distributed throughout the organization, significant cybersecurity governance challenges remain. In this workshop I will explain the transforming organizational security to strengthen defenses and integrate cybersecurity with the overall approach toward security governance, risk management and compliance.
NIST cybersecurity framework



NIST cybersecurity frameworkShriya Rai The NIST Cybersecurity Framework acts as a bridge between the management and Cybersecurity ecosystem.
Viewers also liked (20)
Network Forensics and Practical Packet Analysis



Network Forensics and Practical Packet AnalysisPriyanka Aash Why Packet Analysis?
3 Phases - Analysis, Conversion & Collection
How do we do it ?
Statistics - Protocol Hierarchy
Statistics - End Points & Conversations
Practical Applications of Block Chain Technologies 



Practical Applications of Block Chain Technologies Priyanka Aash The document discusses blockchain technology and its potential practical uses. It begins by defining blockchain as a distributed digital ledger that allows participants in a network to securely record transactions without a central authority. It then provides examples of how blockchain could be used in healthcare to securely store electronic health records, enable smart contracts to automatically pay providers, and track medical devices to prevent counterfeiting. The document concludes by describing a hypothetical example where blockchain is used to give healthcare providers access to a patient's complete medical history from various sources to improve treatment while reducing redundant tests.
SOC Architecture - Building the NextGen SOC



SOC Architecture - Building the NextGen SOCPriyanka Aash Why are APTs difficult to detect
Revisit the cyber kill chain
Process orient detection
NextGen SOC Process
Building your threat mind map
Implement and measure your SOC
Security Strategy and Tactic with Cyber Threat Intelligence (CTI)



Security Strategy and Tactic with Cyber Threat Intelligence (CTI)Priyanka Aash Targeted attacks need targeted Defense
What protocol should we use for CTI information exchange?
How should we describe our indicators of compromise
Structured threat information expression (STIX)
How we can keep information within our defined trust boundaries?
Where to store IOCs?
Threat Intelligence Feeds Lifecycle
How to measure the CTI process?
Workshop on Endpoint Memory Forensics



Workshop on Endpoint Memory ForensicsPriyanka Aash Why memory forensics?
Virtual versus Physical Memory
Type of memory dumps
Enterprise Security Architecture



Enterprise Security ArchitecturePriyanka Aash Enterprise Architecture
Enterprise Architectural Methodologies
A Brief History of Enterprise Architecture
Zachman Framework
Business Attributes
Features & Advantages
SABSA Lifecycle
SABSA Development Process
SMP Maturity Levels
Risk Analysis using open FAIR and Adoption of right Security Controls



Risk Analysis using open FAIR and Adoption of right Security ControlsPriyanka Aash Introduction to O-RA
Security challenges in E-Commerce
Control considerations
Data Breaches in Retail Environment
Risk Analysis & Taxonomy
Enterprise Security Architecture



Enterprise Security ArchitecturePriyanka Aash The document discusses enterprise architecture frameworks and how they can help DreamKart, an ecommerce company facing several IT challenges. It describes the Zachman Framework, which provides a taxonomy for organizing architecture artifacts, and TOGAF, which defines an architecture development method (ADM) process. Using Zachman's taxonomy, DreamKart could classify artifacts, ensure all stakeholder perspectives are considered, and trace business requirements to technical implementations. However, Zachman alone does not provide a process for creating new architectures. TOGAF's ADM process could guide DreamKart in developing enterprise architectures by moving from generic to specific. Using both approaches could help address DreamKart's problems.
Keynote Session : The Non - Evolution of Security



Keynote Session : The Non - Evolution of SecurityPriyanka Aash Critical Exploitable Vulnerabilities
Increased Investment Cost Per Exploit
5 Critical Attributes
Top Cureent Trends
Keynote Session : Emerging Healthcare Tech & Future Security Impact



Keynote Session : Emerging Healthcare Tech & Future Security ImpactPriyanka Aash Data Science
Virtual Reality
Augmented Reality
Fibretronics
Internet of Things
Block Chain
Security Challenges
Practical Enterprise Security Architecture 



Practical Enterprise Security Architecture Priyanka Aash This document summarizes two innovative approaches to enterprise security architecture: Google's BeyondCorp architecture and the Cloud Security Alliance's Software Defined Perimeters (SDP). BeyondCorp aims to remove network-based attacks by implementing zero-trust network access based on continuous device/user authentication and authorization. SDP uses cryptographic protocols and dynamic firewalls to create on-demand, air-gapped networks between initiating and accepting hosts. The document then discusses how organizations can implement these approaches using existing security tools and outlines steps to develop an enterprise security architecture.
Security Strategy and Tactic with Cyber Threat Intelligence (CTI)



Security Strategy and Tactic with Cyber Threat Intelligence (CTI)Priyanka Aash Implications to the Cyber World
Cyber Attacks
Dos & DDOS
Logical Attacks on ATM's
Subtypes of Cyber Threat Intelligence
Keynote Session : Kill The Password



Keynote Session : Kill The PasswordPriyanka Aash New Era Of Authentication
Password Based Attacks
How Strong is Your Password?
Validation Failure
Password Patterns
Keynote Session : Using Behavioral Psychology and Science of Habit to Change ...



Keynote Session : Using Behavioral Psychology and Science of Habit to Change ...Priyanka Aash Is Awareness Enough To Change Human Behavior?
Awarness vs Change Of Behavior
What Else Do We Need?
How To Build A New Habit?
How To Change A Habit?
From Business Architecture to Security Architecture



From Business Architecture to Security ArchitecturePriyanka Aash This document discusses transitioning from business architecture to security architecture. It provides an overview of key aspects of digital architecture like technology adoption, infrastructure management, threat modeling, and security solutions. It then discusses how a typical business architecture in the banking/finance sector (BFSI) can involve many threats across various areas. These threats need to be addressed through proper security architecture and controls. Finally, it analyzes security options for transactions and how they can help protect, defend, deter, limit exposure, detect issues, monitor activities, respond to incidents, contain damage, investigate problems, and aid recovery.
Application Threat Modeling



Application Threat ModelingPriyanka Aash This document discusses application threat modeling. It begins with introducing key terminology used in threat modeling like assets, threats, attacks, and risks. It then explains what threat modeling is and when it should be performed. The document outlines three main approaches to threat modeling: asset-centric, attacker-centric using attack trees, and system-centric. It provides examples of each approach and discusses how to identify threats, calculate risks, and plan countermeasures as part of the system-centric threat modeling process.
Security Maturity Models.



Security Maturity Models.Priyanka Aash - Maturity models provide frameworks for organizations to evaluate their security capabilities and identify areas for improvement. They allow benchmarking against peers.
- There are different types of models including progress-based models that measure advancement through levels and capability maturity models (CMM) that assess process institutionalization. Hybrid models combine aspects of both.
- Examples discussed include the Systems Security Engineering Capability Maturity Model (SSE-CMM) that evaluates security engineering practices across five levels and the CISO Platform Security Benchmarking that compares technologies adopted to peers.
Building Your Application Security Data Hub - OWASP AppSecUSA



Building Your Application Security Data Hub - OWASP AppSecUSADenim Group One of the reasons application security is so challenging to address is that it spans multiple teams within an organization. Development teams build software, security testing teams find vulnerabilities, security operations staff manage applications in production and IT audit organizations make sure that the resulting software meets compliance and governance requirements. In addition, each team has a different toolbox they use to meet their goals, ranging from scanning tools, defect trackers, Integrated Development Environments (IDEs), WAFs and GRC systems. Unfortunately, in most organizations the interactions between these teams is often strained and the flow of data between these disparate tools and systems is non-existent or tediously implemented manually.
In today’s presentation, we will demonstrate how leading organizations are breaking down these barriers between teams and better integrating their disparate tools to enable the flow of application security data between silos to accelerate and simplify their remediation efforts. At the same time, we will show how to collect the proper data to measure the performance and illustrate the improvement of the software security program. The challenges that need to be overcome to enable teams and tools to work seamlessly with one another will be enumerated individually. Team and tool interaction patterns will also be outlined that reduce the friction that will arise while addressing application security risks. Using open source products such as OWASP ZAP, ThreadFix, Bugzilla and Eclipse, a significant amount of time will also be spent demonstrating the kinds of interactions that need to be enabled between tools. This will provide attendees with practical examples on how to replicate a powerful, integrated Application Security program within their own organizations. In addition, how to gather program-wide metrics and regularly calculate measurements such as mean-time-to-fix will also be demonstrated to enable attendees to monitor and ensure the continuing health and performance of their Application Security program.
What Good is this Tool? A Guide to Choosing the Right Application Security Te...



What Good is this Tool? A Guide to Choosing the Right Application Security Te...Kevin Fealey Abstract:
Choosing the right Application Security Testing (AST) tool can be challenging for any security program, and after rolling it out, discovering the real security value it brings can be downright discouraging. No single tool can solve all of all of your security problems, but unfortunately, that is exactly how many of them are marketed. This is compounded by sales teams who convince executive leadership that security programs should be built around their tools, rather than fitting each tool within a well-planned security program. The primary takeaways from this talk are:
• An understanding the real value of each type of AST tool (SAST, DAST, IAST);
• How to leverage your tools for better security visibility and process efficiency;
• Steps to find the right tool for your security program;
• Keys to finding the best stage of the SDLC to implement each tool type within your security program;
• How to integrate new tools with your existing DevOps or Agile environments and processes
Additional Takeaways:
• Examine the strengths and limitations of SAST, DAST, and IAST tools
• Learn how to choose the right tools for your security program
• Discover how to seamlessly integrate your tools into existing DevOps and Agile environments and processes
• Provide security visibility to developers, managers, and executives by enhancing your existing technology
• Learn to use your tools to improve the efficiency of security tasks that are currently manual
SACON Orientation



SACON OrientationPriyanka Aash This document summarizes SACON, India's first security architecture conference. It discusses the need for more security architects to address issues like the halting problem and building secure systems. The CISO Platform is introduced as the world's largest collaboration platform for CISOs, with over 3000 members. It has created several decision tools to help with security technology buying, including the CPSMM benchmarking model, security taxonomy, CISO Platform Index for product ratings, and community RFP checklists. The agenda for SACON includes learning various security models in the first half and applying them through group activities and a wargame in the second half.
Ad
Similar to Application Security Architecture and Threat Modelling (20)
Understanding Application Threat Modelling & Architecture



Understanding Application Threat Modelling & ArchitecturePriyanka Aash Understanding Application Threat Modelling & Architecture
- 99% of Application has at least one vulnerability
Security in the cloud protecting your cloud apps



Security in the cloud protecting your cloud appsCenzic The document discusses security best practices for cloud applications. It notes that 75% of cyber attacks target internet applications and over 400 new vulnerabilities are discovered each month. The top vulnerabilities include cross-site scripting, SQL injection, and insecure direct object references. The document provides examples of how these vulnerabilities can be exploited by hackers and recommends best practices like input validation, output encoding, secure authentication and session management to help protect applications.
Web Application Security



Web Application SecurityAbdul Wahid The document summarizes key points about web application security vulnerabilities and how to address them. It discusses common vulnerabilities like parameter manipulation, cross-site scripting, and SQL injection that occur due to improper validation of user input. It emphasizes the importance of validating all user input on the server-side to prevent attacks, and not storing sensitive values in cookies or hidden form fields that can be manipulated by attackers.
Security Compliance Web Application Risk Management



Security Compliance Web Application Risk ManagementMarco Morana The document discusses the rise of threat analysis and fall of compliance in mitigating web application security risks. It argues that while regulatory compliance aims to improve security, many compliant organizations have still suffered major data breaches. The document advocates applying threat modeling techniques like attack tree analysis to understand likely cybercrime threats and how they could exploit vulnerabilities. This helps identify targeted security measures to implement in applications and architecture.
Security Best Practices



Security Best PracticesClint Edmonson Overview of the Microsoft Security Development Lifecycle and industry best practices for secure software development.
Novinky F5



Novinky F5MarketingArrowECS_CZ Prezentace ze semináře "Novinky F5 Networks"
Praha, 12.9.2018
Prezentovali Filip Kolář a Radovan Gibala, F5 Networks
Are you fighting_new_threats_with_old_weapons



Are you fighting_new_threats_with_old_weaponsBhargav Modi The document discusses the need for web application firewalls to protect against modern web application attacks. It notes that traditional network firewalls and intrusion prevention systems are inadequate because they operate at the network layer and do not understand the application layer protocols used in web applications. The document promotes the Cyberoam web application firewall as a solution, highlighting its positive security model using an intuitive website flow detector to learn normal application behavior and block deviations without signatures. It also lists features such as protection against attacks like SQL injection, monitoring and reporting, and help with PCI compliance.
Scaling Web 2.0 Malware Infection



Scaling Web 2.0 Malware InfectionWayne Huang Given at TRISC 2010, Grapevine, Texas.
http://www.trisc.org/speakers/aditya_sood/#p
The talk sheds light on the new trends of web based malware. Technology and Insecurity goes hand in hand. With the advent of new attacks and techniques the distribution of malware through web has been increased tremendously. Browser based exploits mainly Internet Explorer have given a birth to new world of malware infection. The attackers spread malware elegantly by exploiting the vulnerabilities and drive by downloads. The infection strategies opted by attackers like malware distribution through IFRAME injections and Search Engine Optimization. In order to understand the intrinsic behavior of these web based malware a typical analysis is required to understand the logic concept working behind these web based malwares. It is necessary to dissect these malwares from bottom to top in order to control the devastating behavior. The talk will cover structured methodologies and demonstrate the static, dynamic and behavioral analysis of web malware including PCAP analytics. Demonstrations will prove the fact and necessity of web malware analysis.
TRISC 2010 - Grapevine , Texas



TRISC 2010 - Grapevine , TexasAditya K Sood This document discusses strategies for distributing malware through web-based attacks. It begins by explaining malware anatomy and trends, then outlines over 10 strategies that malware authors use to infect websites and spread to users, including drive-by downloads, search engine poisoning, social media applications and messages. It also provides a case study of how malware infected a security company's website through an obfuscated JavaScript file. The document emphasizes how malware authors are constantly evolving techniques to evade detection.
Information security



Information securitySathyanarayana Panduranga An overview of threats to enterprise applications and data. Anatomy of some threats. The CIA triad. Web application vulnerabilities.
Layer 7 Technologies: Web Services Hacking And Hardening



Layer 7 Technologies: Web Services Hacking And HardeningCA API Management Adam Vincent, Layer 7 Federal Technical Director looks at concepts and tools used for Web services security
OWASP Top 10 And Insecure Software Root Causes



OWASP Top 10 And Insecure Software Root CausesMarco Morana This document discusses common web application vulnerabilities and their root causes. It provides an overview of the OWASP Top 10 list of vulnerabilities, describing each vulnerability type, how attackers exploit them, examples of insecure code that enables the vulnerabilities, and recommendations for secure coding practices to prevent the vulnerabilities. Specific vulnerabilities covered include cross-site scripting, SQL injection, malicious file execution, insecure direct object references, cross-site request forgery, and information leakage from error handling. The document emphasizes the importance of following secure coding standards and input validation to prevent vulnerabilities.
Seceon’s Comprehensive Cybersecurity Platform - Seceon.pptx



Seceon’s Comprehensive Cybersecurity Platform - Seceon.pptxCompanySeceon Seceon’s aiXDR solution discovers and remediates a comprehensive list of threats, exploits, attacks, suspicious activities, and non-conformance/non-compliance items, including Zero-Day and advanced malware with sophisticated evasive techniques. The Table below is an indicative subset of the exhaustive threat models implemented in the product.
Discovering the Value of Verifying Web Application Security Using IBM Rationa...



Discovering the Value of Verifying Web Application Security Using IBM Rationa...Alan Kan The document discusses a workshop on web application security using IBM Rational AppScan. It introduces the importance of securing web applications and provides an overview of common vulnerabilities like cross-site scripting and SQL injection. The workshop aims to help attendees understand application security risks and how to use AppScan to automate vulnerability scanning and analysis. Hands-on labs are included to demonstrate AppScan's vulnerability detection capabilities.
Asegurarme de la Seguridad?, Un Vistazo al Penetration Testing



Asegurarme de la Seguridad?, Un Vistazo al Penetration TestingSoftware Guru Sesión presentada en SG Virtual 11a. edición.
Por: Gilberto Sánchez.
En esta charla veremos ¿qué es el Penetration Testing?, ¿Porque hacerlo?, los tipos de Pen testing que existen, además veremos el pre-ataque, ataque y el post-ataque así como los estándares que existen en la actualidad..
Ceh certified ethical hacker



Ceh certified ethical hackerbestip This 5-day Certified Ethical Hacker training course teaches students how to scan, test, hack, and secure their own systems by learning the techniques used by hackers. The course covers topics like footprinting, scanning, enumeration, system hacking, viruses, sniffers, denial of service attacks, session hijacking, web server hacking, web application vulnerabilities, password cracking, SQL injection, and wireless and cryptography attacks. The goal is to help security professionals and network administrators enhance cybersecurity by thinking like an attacker in order to defend systems from real-world threats.
Website hacking and prevention (All Tools,Topics & Technique )



Website hacking and prevention (All Tools,Topics & Technique )Jay Nagar This document discusses the Heartbleed vulnerability in OpenSSL and its potential impacts. Heartbleed is a bug in the OpenSSL cryptography library that exposes the contents of the server's memory, including private keys and user session cookies. An attacker can exploit Heartbleed to steal sensitive data from vulnerable servers or impersonate services. The vulnerability had widespread implications because OpenSSL is used to secure a majority of websites. While patching servers and changing passwords addressed direct theft of information, Heartbleed also weakened the security of encrypted communications and online identities.
ASMC 2017 - Martin Vliem - Security < productivity < security: syntax ...



ASMC 2017 - Martin Vliem - Security < productivity < security: syntax ...PlatformSecurityManagement In deze sessie geeft Martin Vliem een overzicht van uitdagingen en trends rondom informatiebeveiliging [security] [ cybersecurity] in relatie tot de digitale transformatie onderliggend aan Het Nieuwe Werken. Hij licht de belangrijkste bedreigingen toe, gaat in op de risico’s en illustreert hoe organisaties een betere balans kunnen vinden tussen productiviteit en beveiliging.
ASMC 2017 - Martin Vliem - Security < productivity < security: syntax ...



ASMC 2017 - Martin Vliem - Security < productivity < security: syntax ...PlatformSecurityManagement
Ad
More from Priyanka Aash (20)
Keynote : Presentation on SASE Technology



Keynote : Presentation on SASE TechnologyPriyanka Aash Secure Access Service Edge (SASE) solutions are revolutionizing enterprise networks by integrating SD-WAN with comprehensive security services. Traditionally, enterprises managed multiple point solutions for network and security needs, leading to complexity and resource-intensive operations. SASE, as defined by Gartner, consolidates these functions into a unified cloud-based service, offering SD-WAN capabilities alongside advanced security features like secure web gateways, CASB, and remote browser isolation. This convergence not only simplifies management but also enhances security posture and application performance across global networks and cloud environments. Discover how adopting SASE can streamline operations and fortify your enterprise's digital transformation strategy.
Keynote : AI & Future Of Offensive Security



Keynote : AI & Future Of Offensive SecurityPriyanka Aash In the presentation, the focus is on the transformative impact of artificial intelligence (AI) in cybersecurity, particularly in the context of malware generation and adversarial attacks. AI promises to revolutionize the field by enabling scalable solutions to historically challenging problems such as continuous threat simulation, autonomous attack path generation, and the creation of sophisticated attack payloads. The discussions underscore how AI-powered tools like AI-based penetration testing can outpace traditional methods, enhancing security posture by efficiently identifying and mitigating vulnerabilities across complex attack surfaces. The use of AI in red teaming further amplifies these capabilities, allowing organizations to validate security controls effectively against diverse adversarial scenarios. These advancements not only streamline testing processes but also bolster defense strategies, ensuring readiness against evolving cyber threats.
Redefining Cybersecurity with AI Capabilities



Redefining Cybersecurity with AI CapabilitiesPriyanka Aash In this comprehensive overview of Cisco's latest innovations in cybersecurity, the focus is squarely on resilience and adaptation in the face of evolving threats. The discussion covers the imperative of tackling Mal information, the increasing sophistication of insider attacks, and the expanding attack surfaces in a hybrid work environment. Emphasizing a shift towards integrated platforms over fragmented tools, Cisco introduces its Security Cloud, designed to provide end-to-end visibility and robust protection across user interactions, cloud environments, and breaches. AI emerges as a pivotal tool, from enhancing user experiences to predicting and defending against cyber threats. The blog underscores Cisco's commitment to simplifying security stacks while ensuring efficacy and economic feasibility, making a compelling case for their platform approach in safeguarding digital landscapes.
Demystifying Neural Networks And Building Cybersecurity Applications



Demystifying Neural Networks And Building Cybersecurity ApplicationsPriyanka Aash In today's rapidly evolving technological landscape, Artificial Neural Networks (ANNs) have emerged as a cornerstone of artificial intelligence, revolutionizing various fields including cybersecurity. Inspired by the intricacies of the human brain, ANNs have a rich history and a complex structure that enables them to learn and make decisions. This blog aims to unravel the mysteries of neural networks, explore their mathematical foundations, and demonstrate their practical applications, particularly in building robust malware detection systems using Convolutional Neural Networks (CNNs).
Finetuning GenAI For Hacking and Defending



Finetuning GenAI For Hacking and DefendingPriyanka Aash Generative AI, particularly through the lens of large language models (LLMs), represents a transformative leap in artificial intelligence. With advancements that have fundamentally altered our approach to AI, understanding and leveraging these technologies is crucial for innovators and practitioners alike. This comprehensive exploration delves into the intricacies of GenAI, from its foundational principles and historical evolution to its practical applications in security and beyond.
(CISOPlatform Summit & SACON 2024) Kids Cyber Security .pdf



(CISOPlatform Summit & SACON 2024) Kids Cyber Security .pdfPriyanka Aash (CISOPlatform Summit & SACON 2024) Kids Cyber Security .pdf
(CISOPlatform Summit & SACON 2024) Regulation & Response In Banks.pdf



(CISOPlatform Summit & SACON 2024) Regulation & Response In Banks.pdfPriyanka Aash CISOPlatform Summit and SACON 2024 | 30 May
(CISOPlatform Summit & SACON 2024) Cyber Insurance & Risk Quantification.pdf



(CISOPlatform Summit & SACON 2024) Cyber Insurance & Risk Quantification.pdfPriyanka Aash CISOPlatform Summit and SACON 2024 | 30 May
(CISOPlatform Summit & SACON 2024) Workshop _ Most Dangerous Attack Technique...



(CISOPlatform Summit & SACON 2024) Workshop _ Most Dangerous Attack Technique...Priyanka Aash CISOPlatform Summit and SACON 2024 | 30 May
(CISOPlatform Summit & SACON 2024) Keynote _ Power Digital Identities With AI...



(CISOPlatform Summit & SACON 2024) Keynote _ Power Digital Identities With AI...Priyanka Aash CISOPlatform Summit and SACON 2024 | 30 May
(CISOPlatform Summit & SACON 2024) Digital Personal Data Protection Act.pdf



(CISOPlatform Summit & SACON 2024) Digital Personal Data Protection Act.pdfPriyanka Aash CISOPlatform Summit and SACON 2024 | 30 May
(CISOPlatform Summit & SACON 2024) Gen AI & Deepfake In Overall Security.pdf



(CISOPlatform Summit & SACON 2024) Gen AI & Deepfake In Overall Security.pdfPriyanka Aash CISOPlatform Summit and SACON 2024 | 30 May
(CISOPlatform Summit & SACON 2024) Incident Response .pdf



(CISOPlatform Summit & SACON 2024) Incident Response .pdfPriyanka Aash CISOPlatform Summit and SACON 2024 | 30 May
(CISOPlatform Summit & SACON 2024) Orientation by CISO Platform_ Using CISO P...



(CISOPlatform Summit & SACON 2024) Orientation by CISO Platform_ Using CISO P...Priyanka Aash CISOPlatform Summit and SACON 2024 | 30 MayCISOPlatform Summit and SACON 2024 | 30 May
Digital Personal Data Protection (DPDP) Practical Approach For CISOs



Digital Personal Data Protection (DPDP) Practical Approach For CISOsPriyanka Aash Key Discussion Pointers:
1. Introduction to Data Privacy
- What is data privacy
- Privacy laws around the globe
- DPDPA Journey
2. Understanding the New Indian DPDPA 2023
- Objectives
- Principles of DPDPA
- Applicability
- Rights & Duties of Individuals
- Principals
- Legal implications/penalties
3. A practical approach to DPDPA compliance
- Personal data Inventory
- DPIA
- Risk treatment
Verizon Breach Investigation Report (VBIR).pdf



Verizon Breach Investigation Report (VBIR).pdfPriyanka Aash The Verizon Breach Investigation Report (VBIR) is an annual report analyzing cybersecurity incidents based on real-world data. It categorizes incidents and identifies emerging trends, threat actors, motivations, attack vectors, affected industries, common attack patterns, and recommendations. Each report provides the latest insights and data to give organizations a global perspective on evolving cyber threats.
Top 10 Security Risks .pptx.pdf



Top 10 Security Risks .pptx.pdfPriyanka Aash The document summarizes the top 10 cybersecurity risks presented to the board of directors of a manufacturing company. It discusses each risk such as insider threats, cloud security, ransomware attacks, third party risks, and data security. For each risk, it provides the current posture in terms of controls, compliance level, and planned improvements. The CISO and other leaders such as the managing director, finance director, and chief risk officer attended the presentation.
Simplifying data privacy and protection.pdf



Simplifying data privacy and protection.pdfPriyanka Aash 1) Data is growing exponentially which increases the risk and impact of data breaches, while compliance requirements are also becoming more stringent.
2) IBM Security Guardium helps customers address this by discovering, classifying, and protecting sensitive data across platforms and simplifying compliance.
3) It detects threats in real-time, increases data security accuracy, and reduces the time spent on audits and issue remediation, helping customers minimize the impact of potential data breaches and address local compliance requirements.
Generative AI and Security (1).pptx.pdf



Generative AI and Security (1).pptx.pdfPriyanka Aash Generative AI and Security Testing discusses generative AI, including its definition as a subset of AI focused on generating content similar to human creations. The document outlines the evolution of generative AI from artificial neural networks to modern models like GPT, GANs, and VAEs. It provides examples of different types of generative AI like text, image, audio, and video generation. The document proposes potential uses of generative AI like GPT for security testing tasks such as malware generation, adversarial attack simulation, and penetration testing assistance.
Recently uploaded (20)
How Can I use the AI Hype in my Business Context?



How Can I use the AI Hype in my Business Context?Daniel Lehner 𝙄𝙨 𝘼𝙄 𝙟𝙪𝙨𝙩 𝙝𝙮𝙥𝙚? 𝙊𝙧 𝙞𝙨 𝙞𝙩 𝙩𝙝𝙚 𝙜𝙖𝙢𝙚 𝙘𝙝𝙖𝙣𝙜𝙚𝙧 𝙮𝙤𝙪𝙧 𝙗𝙪𝙨𝙞𝙣𝙚𝙨𝙨 𝙣𝙚𝙚𝙙𝙨?
Everyone’s talking about AI but is anyone really using it to create real value?
Most companies want to leverage AI. Few know 𝗵𝗼𝘄.
✅ What exactly should you ask to find real AI opportunities?
✅ Which AI techniques actually fit your business?
✅ Is your data even ready for AI?
If you’re not sure, you’re not alone. This is a condensed version of the slides I presented at a Linkedin webinar for Tecnovy on 28.04.2025.
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...



IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...organizerofv IEDM 2024 Tutorial2
Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...



Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...Impelsys Inc. Impelsys provided a robust testing solution, leveraging a risk-based and requirement-mapped approach to validate ICU Connect and CritiXpert. A well-defined test suite was developed to assess data communication, clinical data collection, transformation, and visualization across integrated devices.
Heap, Types of Heap, Insertion and Deletion



Heap, Types of Heap, Insertion and DeletionJaydeep Kale This pdf will explain what is heap, its type, insertion and deletion in heap and Heap sort
Build Your Own Copilot & Agents For Devs



Build Your Own Copilot & Agents For DevsBrian McKeiver May 2nd, 2025 talk at StirTrek 2025 Conference.
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Linux Professional Institute LPIC-1 Exam.pdf



Linux Professional Institute LPIC-1 Exam.pdfRHCSA Guru Introduction to LPIC-1 Exam - overview, exam details, price and job opportunities
HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungen



HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungenpanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-und-verwaltung-von-multiuser-umgebungen/
HCL Nomad Web wird als die nächste Generation des HCL Notes-Clients gefeiert und bietet zahlreiche Vorteile, wie die Beseitigung des Bedarfs an Paketierung, Verteilung und Installation. Nomad Web-Client-Updates werden “automatisch” im Hintergrund installiert, was den administrativen Aufwand im Vergleich zu traditionellen HCL Notes-Clients erheblich reduziert. Allerdings stellt die Fehlerbehebung in Nomad Web im Vergleich zum Notes-Client einzigartige Herausforderungen dar.
Begleiten Sie Christoph und Marc, während sie demonstrieren, wie der Fehlerbehebungsprozess in HCL Nomad Web vereinfacht werden kann, um eine reibungslose und effiziente Benutzererfahrung zu gewährleisten.
In diesem Webinar werden wir effektive Strategien zur Diagnose und Lösung häufiger Probleme in HCL Nomad Web untersuchen, einschließlich
- Zugriff auf die Konsole
- Auffinden und Interpretieren von Protokolldateien
- Zugriff auf den Datenordner im Cache des Browsers (unter Verwendung von OPFS)
- Verständnis der Unterschiede zwischen Einzel- und Mehrbenutzerszenarien
- Nutzung der Client Clocking-Funktion
Drupalcamp Finland – Measuring Front-end Energy Consumption



Drupalcamp Finland – Measuring Front-end Energy ConsumptionExove How to measure web front-end energy consumption using Firefox Profiler. Presented in DrupalCamp Finland on April 25th, 2025.
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...



AI Changes Everything – Talk at Cardiff Metropolitan University, 29th April 2...Alan Dix Talk at the final event of Data Fusion Dynamics: A Collaborative UK-Saudi Initiative in Cybersecurity and Artificial Intelligence funded by the British Council UK-Saudi Challenge Fund 2024, Cardiff Metropolitan University, 29th April 2025
https://alandix.com/academic/talks/CMet2025-AI-Changes-Everything/
Is AI just another technology, or does it fundamentally change the way we live and think?
Every technology has a direct impact with micro-ethical consequences, some good, some bad. However more profound are the ways in which some technologies reshape the very fabric of society with macro-ethical impacts. The invention of the stirrup revolutionised mounted combat, but as a side effect gave rise to the feudal system, which still shapes politics today. The internal combustion engine offers personal freedom and creates pollution, but has also transformed the nature of urban planning and international trade. When we look at AI the micro-ethical issues, such as bias, are most obvious, but the macro-ethical challenges may be greater.
At a micro-ethical level AI has the potential to deepen social, ethnic and gender bias, issues I have warned about since the early 1990s! It is also being used increasingly on the battlefield. However, it also offers amazing opportunities in health and educations, as the recent Nobel prizes for the developers of AlphaFold illustrate. More radically, the need to encode ethics acts as a mirror to surface essential ethical problems and conflicts.
At the macro-ethical level, by the early 2000s digital technology had already begun to undermine sovereignty (e.g. gambling), market economics (through network effects and emergent monopolies), and the very meaning of money. Modern AI is the child of big data, big computation and ultimately big business, intensifying the inherent tendency of digital technology to concentrate power. AI is already unravelling the fundamentals of the social, political and economic world around us, but this is a world that needs radical reimagining to overcome the global environmental and human challenges that confront us. Our challenge is whether to let the threads fall as they may, or to use them to weave a better future.
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
HCL Nomad Web – Best Practices and Managing Multiuser Environments



HCL Nomad Web – Best Practices and Managing Multiuser Environmentspanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-and-managing-multiuser-environments/
HCL Nomad Web is heralded as the next generation of the HCL Notes client, offering numerous advantages such as eliminating the need for packaging, distribution, and installation. Nomad Web client upgrades will be installed “automatically” in the background. This significantly reduces the administrative footprint compared to traditional HCL Notes clients. However, troubleshooting issues in Nomad Web present unique challenges compared to the Notes client.
Join Christoph and Marc as they demonstrate how to simplify the troubleshooting process in HCL Nomad Web, ensuring a smoother and more efficient user experience.
In this webinar, we will explore effective strategies for diagnosing and resolving common problems in HCL Nomad Web, including
- Accessing the console
- Locating and interpreting log files
- Accessing the data folder within the browser’s cache (using OPFS)
- Understand the difference between single- and multi-user scenarios
- Utilizing Client Clocking
Andrew Marnell: Transforming Business Strategy Through Data-Driven Insights



Andrew Marnell: Transforming Business Strategy Through Data-Driven InsightsAndrew Marnell With expertise in data architecture, performance tracking, and revenue forecasting, Andrew Marnell plays a vital role in aligning business strategies with data insights. Andrew Marnell’s ability to lead cross-functional teams ensures businesses achieve sustainable growth and operational excellence.
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
Application Security Architecture and Threat Modelling
- 1. Security Architecture and Threat Modelling Nilanjan De Devesh Bhatt
- 2. 95% of attacks are against “Web Servers and Web Applications”
- 3. Average 35 No of vulnerabilities in a website 52%of data breaches happen through Web Applications of Application has atleast one vulnerability 41 High 3 3 5 9 Mediu m Low The Scorecard 90% of hacking incidents are not reported 99% 82% of web applications have at least 1 High/Critical Vulnerability Business Logic Flaws are the most neglected vulnerabilities Source: IViZ blog
- 5. USER AGENTS User Agent / Client. Browser, BOT, Program Sends Requests like GET, POST, HEAD, PUT, DELETE WEB SERVERS ● Web Server listens for requests ● Has interpreters to understand PHP/ASP.net ● Talks to the database ● Has TCP ports in listening mode Database Server MySQL, MSSQL, Oracle 3 Tier – Web App Architecture
- 6. Web App Architecture – Data View Web Client Data Store Web Server Trusted Code Running on server Web Service Un-trusted Input hitting the server from the client, data stores, web services.
- 7. Would you trust the code? Operating System and Shell Web Server + Interpreter (PHP/ASP.net) Trusted Code
- 8. Traditional SDLC It’s too late!! We won’t meet our security standards.. Production Deadline Development + QA Pen Testing 189 Vulnerabilities Security is taken care of only at the end of the SDLC
- 9. Secure SDLC Production Deadline Development + QA + Security Pen Testing 12 Vulnerabilities Security is implemented during the SW development. • We can achieve application security • We save development time $$
- 10. Enabling S-SDLC Source Repository Build Management System Static Analysis Tool Team City Jenkins Hudson Bamboo TFS SVN GIT Etc. Developers Team Leaders / Security team Production
- 11. Cost to find/fix a defect during integration/system test is 15-90 times higher than at design/coding Time & Cost Code Inspection Integration Testing System TestingStatic analysis tools find defects and design flaws “in phase” Unit Testing Design Coding QA Production Scan sources with checkmarx Scan binaries SAST vs. DAST
- 12. SAST vs. DAST Dynamic Application Security Testing (DAST) - Can be performed only at the end of dev. - More layers covered - Not compete coverage (it is random). - Results not shown in the code Static Application Security Testing (SAST) - Can be performed from the beginning of the SDLC - Covers only the application code - Covers all the application code - Results are shown inside the code - Has more false positive results 12
- 13. SAST vs. DAST So what is better, DAST or SAST? For good security both SAST and DAST are necessary and complete each other. If you have SAST you will get better quality results from the DAST service 13
- 14. SAST Scanning SAST vendors scan binaries - Need compilation environment - Need compliable code.. have to wait SAST vendors scanning pure source code - Uses the virtual compiler technology - No need for compilation environment - Can scan from day one - Scan takes longer System is more flexible can customize the system for less FP results. 14
- 15. Threat Modelling
- 17. Threat Modelling
- 18. Common Types of Attack Connection Fails Organizational Attacks Restricted Data Accidental Breaches in Security Automated Attacks Hackers Viruses, Trojan Horses, and Worms Denial of Service (DoS) DoS
- 19. Types of Threats Spoofed packets, etc. Buffer overflows, illicit paths, etc. SQL injection, XSS, input tampering, etc. Network Host Application Threats against the network Threats against the host Threats against the application
- 20. Threats Against the Network Threat Examples Information gathering Port scanning Using trace routing to detect network topologies Using broadcast requests to enumerate subnet hosts Eavesdropping Using packet sniffers to steal passwords Denial of service (DoS) SYN floods ICMP echo request floods Malformed packets Spoofing Packets with spoofed source addresses http://msdn.microsoft.com/library/en-us/dnnetsec/html/THCMCh15.asp? frame=true#c15618429_004
- 21. Threats Against the Host Threat Examples Arbitrary code execution Buffer overflows in ISAPI DLLs (e.g., MS01-033) Directory traversal attacks (MS00-078) File disclosure Malformed HTR requests (MS01-031) Virtualized UNC share vulnerability (MS00-019) Denial of service (DoS) Malformed SMTP requests (MS02-012) Malformed WebDAV requests (MS01-016) Malformed URLs (MS01-012) Brute-force file uploads Unauthorized access Resources with insufficiently restrictive ACLs Spoofing with stolen login credentials Exploitation of open ports and protocols Using NetBIOS and SMB to enumerate hosts Connecting remotely to SQL Server
- 22. Threats Against the Application Threat Examples SQL injection Including a DROP TABLE command in text typed into an input field Cross-site scripting Using malicious client-side script to steal cookies Hidden-field tampering Maliciously changing the value of a hidden field Eavesdropping Using a packet sniffer to steal passwords and cookies from traffic on unencrypted connections Session hijacking Using a stolen session ID cookie to access someone else's session state Identity spoofing Using a stolen forms authentication cookie to pose as another user Information disclosure Allowing client to see a stack trace when an unhandled exception occurs
- 23. Threat Modeling Structured approach to identifying, quantifying, and addressing threats Essential part of development process
- 24. The Threat Modeling Process Identify assets Document architecture Decompose application Identify threats Document threats Rate threats 1 2 3 4 5 6
- 25. Identifying Assets What is it that you want to protect? Private data (e.g., customer list) Proprietary data (e.g., intellectual property) Potentially injurious data (e.g., credit card numbers, decryption keys) These also count as "assets" Integrity of back-end databases Integrity of the Web pages (no defacement) Integrity of other machines on the network Availability of the application
- 26. Documenting Architecture Define what the app does and how it's used Users view pages with catalog items Users perform searches for catalog items Users add items to shopping carts Users check out Diagram the application Show subsystems Show data flow List assets
- 27. Example Bob Alice Bill Asset #4 Asset #1 Asset #2 Asset #3 Asset #5 Asset #6 IIS ASP.NET Web Server Login State Main Database Server Firewall
- 28. Decomposing the App Refine the architecture diagram Show authentication mechanisms Show authorization mechanisms Show technologies (e.g., DPAPI) Diagram trust boundaries Identify entry points Begin to think like an attacker Where are my vulnerabilities? What am I going to do about them?
- 29. Example Bob Alice Bill IIS ASP.NET Web Server Database Server Trust Forms Authentication URL Authorization DPAPI Windows Authentication Firewall Login State Main
- 30. Identifying Threats Method #1: Threat lists Start with laundry list of possible threats Identify the threats that apply to your app Method #2: STRIDE Categorized list of threat types Identify threats by type/category Optionally draw threat trees Root nodes represent attacker's goals Trees help identify threat conditions
- 31. STRIDE S T R I D Tampering Repudiation Information disclosure Denial of service Can an attacker gain access using a false identity? Can an attacker modify data as it flows through the application? If an attacker denies doing something, can we prove he did it? Can an attacker gain access to private or potentially injurious data? Can an attacker crash or reduce the availability of the system? E Elevation of privilege Can an attacker assume the identity of a privileged user? Spoofing
- 32. Documenting Threats Theft of Auth Cookies by Eavesdropping on Connection Threat target Connections between browsers and Web server Risk Attack techniques Attacker uses sniffer to monitor traffic Countermeasures Use SSL/TLS to encrypt traffic Document threats using a template Theft of Auth Cookies via Cross-Site Scripting Threat target Vulnerable application code Risk Attack techniques Attacker sends e-mail with malicious link to users Countermeasures Validate input; HTML-encode output
- 33. Rating Threats Simple model DREAD model Greater granularization of threat potential Rates (prioritizes) each threat on scale of 1-15 Developed and widely used by Microsoft Risk = Probability * Damage Potential 1-10 Scale 1 = Least probable 10 = Most probable 1-10 Scale 1 = Least damage 10 = Most damage
- 34. DREAD D R E A D Reproducibility Exploitability Affected users Discoverability What are the consequences of a successful exploit? Would an exploit work every time or only under certain circumstances? How skilled must an attacker be to exploit the vulnerability? How many users would be affected by a successful exploit? How likely is it that an attacker will know the vulnerability exists? Damage potential
- 35. Example Threat D R E A D Sum Auth cookie theft (eavesdropping) 3 2 3 2 3 13 Auth cookie theft (XSS) 3 2 2 2 3 12 Potential for damage is high (spoofed identities, etc.) Cookie can be stolen any time, but is only useful until expired Anybody can run a packet sniffer; XSS attacks require moderate skill All users could be affected, but in reality most won't click malicious links Easy to discover: just type a <script> block into a field Prioritized Risks
- 36. Produce software that’s secure by design Improve designs the same way we’ve improved code Because attackers think differently Creator blindness/new perspective Why Threat Model
- 37. Diagram Elements - Examples •People •Other systems •Microsoft.com •etc… •Function call •Network traffic •Etc.… •DLLs •EXEs •Components •Services •Web Services •Assemblies •etc… •Database •File •Registry •Shared Memory •Queue/Stack •etc.… External entity Process Data Flow Data Store Trust Boundary •Process boundary •File system
- 38. Add trust boundaries that intersect data flows Points/surfaces where an attacker can interject Machine boundaries, privilege boundaries, integrity boundaries are examples of trust boundaries Threads in a native process are often inside a trust boundary, because they share the same rights and access Processes talking across a network always have a trust boundary Diagrams: Trust Boundaries
- 39. Context Diagram Very high-level; entire component / product / system Level 1 Diagram High level; single feature / scenario Level 2 Diagram Low level; detailed sub-components of features Level 3 Diagram More detailed Rare to need more layers, except in huge projects or when you’re drawing more trust boundaries Diagram layers
- 40. Castle Service Local User Castle Config Feedback Join/Leave Castle Remote Castle A Real Context Diagram
- 41. Castle Service Explorer (or rundll32) SSDP SSDP Remote Castle Service Registry LSA SAM Local User Shacct Get acct info Feedback Manage Castle Join, leave, Set users props Set acct info Read Castle info Set psswd Set acct info Feedback Get machine password Cache Castle info Query users props Query other Castle info Publish this Castle info Manage Castle Get acct info Get version info Set version info 1 2 3 4 5 6 7 8 9 10 A Real DFD
- 42. Understanding the threats Threat Property Definition Example Spoofing Authentication Impersonating something or someone else. Pretending to be any of billg, xbox.com or a system update Tampering Integrity Modifying data or code Modifying a game config file on disk, or a packet as it traverses the network Repudiation Non-repudiation Claiming to have not performed an action “I didn’t cheat!” Information Disclosure Confidentiality Exposing information to someone not authorized to see it Reading key material from an app Denial of Service Availability Deny or degrade service to users Crashing the web site, sending a packet and absorbing seconds of CPU time, or routing packets into a black hole Elevation of Privilege Authorization Gain capabilities without proper authorization Allowing a remote internet user to run commands is the classic example, but running kernel code from lower trust levels is also EoP
- 43. Different threats affect each type of element Process Data Store S T R I D E Element ? Dataflow External Entity
- 44. Castle Service Explorer (or rundll32) SSDP SSDP Remote Castle Service Registry LSA SAM Local User Shacct Get acct info Feedback Manage Castle Join, leave, Set users props Set acct info Read Castle info Set psswd Set acct info Feedback Get machine password Cache Castle info Query users props Query other Castle info Publish this Castle info Manage Castle Get acct info Get version info Set version info 1 2 3 4 5 6 7 8 9 10 A Real Level-0 DFD (Castle) TID TID TID TID STRIDE STRIDE Etc…
- 45. Address each threat Four ways to address threats: Redesign to eliminate Apply standard mitigations Invent new mitigations Riskier Accept vulnerability in design Address each threat! Mitigate
- 46. Validate the whole TM Does diagram match final code? Are threats enumerated? Minimum: STRIDE per element that touches a trust boundary Has Test reviewed the model? Created appropriate test plans Tester approach often finds issues with TM, or details Is each threat mitigated? Are mitigations done right Validating Threat Models
- 47. End exercise
- 48. Uncover Security Design Flaws Using the STRIDE Approach http://msdn.microsoft.com/msdnmag/issues/06/11/ThreatModeling/default.asp x http://msdn.microsoft.com/en-us/magazine/cc700352.aspx http://msdn.microsoft.com/en-us/magazine/2009.01.securitybriefs.aspx http://msdn.microsoft.com/en-us/security/cc448120.aspx References
- 49. Something to think about Password analysis from the rockyou.com data revealed The most common password was; 123456 30% passwords were less than 6 characters 60% passwords were a limited set of alphanumeric (A-Z, a-z, 0-9) characters 23,000 passwords were set to; rockyou
- 50. Thank You!!




