Application Security Logging with Splunk using Java
- 1. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. APPLICATION SECURITY LOGGING with Splunk SIEM using Java // Incomplete In-Work Draft, Please Check Again Later// robertGrupe, CISSP, CSSLP, PE, PMP tags :|: OWASP, SIEM, application security, logging, Splunk, Java 1
- 2. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Agenda: Application Security Logging • OWASP Application Security Logging • SIEM with Splunk • Java Logging • Splunk logging for Java • TCP inputs • HTTP Event Collector • Resources: Links
- 3. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. OWASP APPLICATION LOGGING
- 4. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Application Logging Purposes • Security Reasons • Identifying security incidents • Monitoring policy violations • Establishing baselines • Assisting non-repudiation controls • Providing information about problems and unusual conditions • Contributing additional application-specific data for incident investigation which is lacking in other log sources • Helping defend against vulnerability identification and exploitation through attack detection • Business Reasons • Business process monitoring e.g. sales process abandonment, transactions, connections • Anti-automation monitoring • Audit trails e.g. data addition, modification and deletion, data exports • Performance monitoring e.g. data load time, page timeouts • Compliance monitoring • Data for subsequent requests for information e.g. data subject access, freedom of information, litigation, police and other regulatory investigations • Legally sanctioned interception of data e.g application-layer wire-tapping • Other business-specific requirements
- 5. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Application Logging • When using the file system, it is preferable to use a separate partition than those used by the operating system, other application files and user generated content • For file-based logs, apply strict permissions concerning which users can access the directories, and the permissions of files within the directories • In web applications, the logs should not be exposed in web-accessible locations, and if done so, should have restricted access and be configured with a plain text MIME type (not HTML) • When using a database, it is preferable to utilize a separate database account that is only used for writing log data and which has very restrictive database , table, function and command permissions • Use standard formats over secure protocols to record and send event data, or log files, to other systems e.g. Common Log File System (CLFS), Common Event Format (CEF) over syslog, possibly Common Event Expression (CEE) in future; standard formats facilitate integration with centralised logging services • Consider separate files/tables for extended event information such as error stack traces or a record of HTTP request and response headers and bodies.
- 6. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Events to Log: Always Log • Input validation failures e.g. protocol violations, unacceptable encodings, invalid parameter names and values • Output validation failures e.g. database record set mismatch, invalid data encoding • Authentication successes and failures • Authorization (access control) failures • Session management failures e.g. cookie session identification value modification • Application errors and system events e.g. syntax and runtime errors, connectivity problems, performance issues, third party service error messages, file system errors, file upload virus detection, configuration changes • Application and related systems start-ups and shut-downs, and logging initialization (starting, stopping or pausing) • Use of higher-risk functionality e.g. network connections, addition or deletion of users, changes to privileges, assigning users to tokens, adding or deleting tokens, use of systems administrative privileges, access by application administrators, all actions by users with administrative privileges, access to payment cardholder data, use of data encrypting keys, key changes, creation and deletion of system-level objects, data import and export including screen-based reports, submission of user-generated content - especially file uploads • Legal and other opt-ins e.g. permissions for mobile phone capabilities, terms of use, terms & conditions, personal data usage consent, permission to receive marketing communications
- 7. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Events to Log: Optionally Consider • Sequencing failure • Excessive use • Data changes • Fraud and other criminal activities • Suspicious, unacceptable or unexpected behavior • Modifications to configuration • Application code file and/or memory changes
- 8. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. APPLICATION SECURITY LOGGING
- 9. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Purposes • Monitoring & Alerting • Suspicious activity • Recording User Activities • Create, read, update, delete data • Investigating • Security, privacy events • Compliance auditing: appropriate use (with retention requirements) • Federal Information Security Management Act (FISMA), • Gramm-Leach-Bliley Act (GLBA), • Health Insurance Portability and Accountability Act (HIPAA), • Payment Card Industry (PCI) • Sarbanes-Oxley Act (SOX) • External attacks, unauthorized access • Misuse of authorized access / fraud
- 10. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Application Event Logging Standards (AELS) • AELS1: • Batch, cron jobs, scheduled non-interactive tasks • Includes operating system, middleware, • AELS2: User activities • Human user actions
- 11. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. AppSec Reports • Users and Roles Report • Users Access Report
- 12. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Access Management Logging • Details • User account • Timestamp: date, time (hh:mm:ss;mm), time zone • Event • Registration • Registration Initiated • Registration Approved • Registration Denied • Log In Success • Log In Fail • Log Out • Account Locked • Account Recovery • Password Change • Password Reset
- 13. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Privileged Data Access Management Logging • Events • Association Request • Association Approved • Association Denied • Association Start • Association End
- 14. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Users and Roles Report • User Account ID • Account Status (active, locked, deleted, etc.) • Role • <User information: name, email, etc.)> • Registration Source (self, loaded, others) • Last Login (timestamp) • 1st Registered • Data Access Permissions
- 15. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. SIEM WITH SPLUNK
- 16. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. What is SIEM? • Security Information and Event Management (SIEM) • AKA SEM, SIM • Capabilities • Data aggregation • Correlation • Alerting • Dashboards • Compliance • Retention • Forensic analysis • Market solutions • IBM QRadar, • HP's ArcSight, • LogRhythm, • McAfee ESM, • SolarWinds • Splunk • Etc.
- 17. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Splunk Dashboards • Versions • Splunk Free caps indexing to 500MB per day, limited feature set • Splunk Enterprise for on-premises • Splunk Cloud (Google Cloud partner)
- 18. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Getting data into Splunk Enterprise • Uploading a log file via Splunk’s web interface. • Getting Splunk to monitor a local directory or file. • Splunk can index data from any network port. • HTTP • Send events directly to Splunk Enterprise rather than requiring writing to disk and installing a forwarder • Send data securely to Splunk Enterprise, with the option of an HTTPS connection and a unique token. • You expect to send data at a high volume and frequency. • TCP: syslog-ng, etc. • log to a TCP input either directly or by first logging to a file and then using a Splunk Universal Forwarder to monitor the file and send data any time the file is updated. Doing so gives you the features of the Universal Forwarder, plus added robustness from having persistent files. • SNMP • Other • FIFO queues • Scripted inputs to get data from APIs and other remote data interfaces and message queues.
- 19. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Splunk Input Considerations • Resilience • All appenders will attempt to reconnect in case of dropped connections. • Load Balancing • It's easy to set up HTTP Event Collector in a load balanced Splunk environment. • See High volume HTTP Event Collector data collection using distributed deployment for more information about your options. • For TCP inputs, you can set up a Splunk Universal Forwarder, and then have all your logging sources write to that TCP input. • Use the Universal Forwarder's load balancing features to distribute the data from there to a set of indexers. • Thread Safety • For HTTP Event Collector, Log4J, Logback, and java.util.logging adapters for HTTP Event Collector are thread-safe. • For TCP inputs, Log4J and Logback are thread-safe.
- 20. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. JAVA LOGGING
- 21. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Java Logging: Components • Package java.util.logging • Logger: data to be logged LogRecord • Log level integer (1-??) • Filter: • Handler: what to do with LogRecord • Whether and where to send • Filter: processing logic rules • Formatter: formatting of LogRecord data into string • LogManager • Level and branch hierarchy of Loggers • Others Logging Packages: Log4J, SLF4J, Apache Commons Logging, LogBack
- 22. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Java Logging: Logger • Create a Logger in each class that needs to log. • static and final: all instances of that class use the same Logger instance. • use the class name including package name as name for the Logger. • The name of the Logger to create is passed as string parameter to the Logger.getLogger() method. public class LoggingExamples { private static final Logger logger = Logger.getLogger(LoggingExamples.class.getName()); }
- 23. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Java Logging: Logger Hierarchy • To be completed
- 24. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Java Logging: Log Levels • To be completed
- 25. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Java Logging: Formatters • To be completed
- 26. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Java Logging: Filters • To be completed
- 27. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Java Logging: Handlers • To be completed
- 28. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Java Logging: LogRecord • To be completed
- 29. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Java Logging: Configuration • To be completed
- 30. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Java Logging: LogManager • To be completed
- 31. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Java Logging Example package com.example; import java.util.logging.*; public class Nose{ private static Logger logger = Logger.getLogger("com.wombat.nose"); // Obtain logger public static void main(String argv[]) { // Log FINE tracing message logger.fine("doing stuff"); try{ Wombat.sneeze(); } catch (Exception ex) { // Log the exception logger.log(Level.WARNING, "trouble sneezing", ex); } logger.fine("done"); } }
- 32. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Java Logging Reference Links • http://tutorials.jenkov.com/java-logging/logger.html • http://www.vogella.com/tutorials/Logging/article.html#over view • https://examples.javacodegeeks.com/core- java/util/logging/java-util-logging-example/ • https://docs.oracle.com/javase/8/docs/technotes/guides/lo gging/
- 33. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. SPLUNK LOGGING FOR JAVA
- 34. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. 0. Download Splunk logging for Java • Current version 1.5.2 (2016-10-11) • http://dev.splunk.com/view/splunk-logging-java/SP-CAAAE7R • Requirements • Oracle Java SE Development Kit (JDK) 7 or later. • Splunk Enterprise • http://www.splunk.com/download • Splunk logging for Java • JAR • http://dev.splunk.com/goto/loggingjavajar
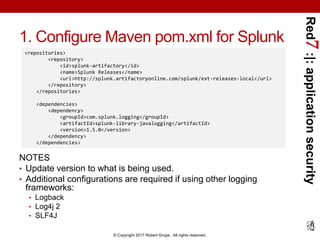
- 35. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. 1. Configure Maven pom.xml for Splunk NOTES • Update version to what is being used. • Additional configurations are required if using other logging frameworks: • Logback • Log4j 2 • SLF4J <repositories> <repository> <id>splunk-artifactory</id> <name>Splunk Releases</name> <url>http://splunk.artifactoryonline.com/splunk/ext-releases-local</url> </repository> </repositories> <dependencies> <dependency> <groupId>com.splunk.logging</groupId> <artifactId>splunk-library-javalogging</artifactId> <version>1.5.0</version> </dependency> </dependencies>
- 36. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. SPLUNK LOGGING FOR JAVA HTTP
- 37. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. HTTP Logging to Splunk HTTP Event Collector 1. Add Splunk logging for Java library to your project 2. Add your preferred logging library (java.util.logging, Logback, Log4j 2) to your project. 3. Make sure HTTP Event Collector is enabled on your Splunk Enterprise Instance and that you have a valid token. For more information, see “About Event Collector Tokens” in Use HTTP Event Collector in the Getting Data In Manual. 4. Configure your Java loggers to use the HTTP Event Collector. 5. Use your Java loggers to log events
- 38. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. HTTP 2. Configure Splunk • Splunk administrator • Enable HTTP Event Collector • http://docs.splunk.com/Documentation/Splunk/latest/Data/UsetheHTTP EventCollector • Optional attributes: • The Splunk index for events. • The Splunk source value to assign to the events. • The Splunk sourcetype value to assign to the events. • Event batching parameters: interval, maximum number of events, and maximum size of events. • Provide to Java App Developer • The hostname and port of the Splunk Enterprise or Splunk Cloud server • Default port number for HTTP Event Collector is 8088, but may be different • Valid, enabled HTTP Event Collector token • Identifies your Java app to HTTP Event Collector.
- 39. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. HTTP 3. Java Application Configuration • Specify jdklogging.properties to your program by passing the following to the Java executable • Customize jdklogging.properties file • Bare-minimum version below [refer to slide notes for more info]: • Includes just the url, level, and token properties, plus the disableCertificateValidation property. • Doesn’t include optional source, sourcetype, batch_interval, batch_size_bytes, batch_size_count, and index. Need to customize XML configuration file for your setup. - Djava.util.logging.config.file=/path/to/jdklogging.properties %user_logger_name%.level = INFO %user_logger_name%.handlers = com.splunk.logging.HttpEventCollectorLoggingHandler com.splunk.logging.HttpEventCollectorLoggingHandler.url = %scheme%://%host%:%port% com.splunk.logging.HttpEventCollectorLoggingHandler.level = INFO com.splunk.logging.HttpEventCollectorLoggingHandler.token = %user_httpeventcollector_token% com.splunk.logging.HttpEventCollectorLoggingHandler.disableCertificateValidation=true
- 40. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. HTTP 4. Java Application Coding • Though HTTP Event Collector accepts only JSON-formatted event data packets, the event data payload can be any format, as long as it is surrounded by curly brackets. • If you log a sequence of events that contains invalid events, it will process until it hits the first invalid event, and then return an error. package com.example; import java.util.logging.*; import com.splunk.logging.*; // create a logger by using the getLogger method of the Logger class Logger logger = Logger.getLogger(loggerName); // add code to log data at the appropriate levels logger.info("This is a test event for Logback test"); logger.error("This is a test error for Logback test");
- 41. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. HTTP Splunk Event Collector Classes • HttpAppender • Creates logging events to send to HTTP Event Collector. • For all loggers except Logback. • HttpLogbackAppender • Creates logging events to send to HTTP Event Collector using Logback. • HttpInputHandler • Exports logging events to HTTP Event Collector. • HttpInputLoggingErrorHandler • HTTP Event Collector error handler to which your application can subscribe to catch error responses from the Splunk server. • HttpInputLoggingEventInfo • Container for event data. • // HttpInputEventSender // • internal helper class that is used by the other classes in the library. Do not use.
- 42. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. SPLUNK LOGGING FOR JAVA TCP
- 43. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. TCP: Logging to Splunk TCP inputs 1. Add the Splunk logging for Java library to your project 1. Maven pom.xml 2. Add the logging library to your project 1. java.util.logging (or Logback, Log4j 2) 3. Open a TCP input on Splunk Enterprise 1. to write log events 4. Configure your logging system 5. Use SplunkCimLogEvent class to generate log entries
- 44. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. TCP 2. Configure Splunk • Splunk Enterprise Administrator • Add a network input using Splunk Web • Add a network input using the CLI • Change restricted hosts on a TCP network input • Add a network input using inputs.conf • Documentation • http://docs.splunk.com/Documentation/Splunk/latest/Data/Monitorn etworkports
- 45. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. TPC 3. Java Application Configuration • specify java.util.logging SocketHandler as the default handler. • Set the default logging level for the root logger. • Create a logger called splunk.logger, • set its level to INFO • specify SocketHandler as its logger. • Configure the SocketHandler to write to TCP port localhost:15000. • Control the logging format using SimpleFormatter class, with syntax defined on the definition page for the Formatter class • Put the following in jdklogging.properties ... • Specify jdklogging.properties to your program by passing the following to the Java executable:
- 46. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. TPC 4. Java Application Coding package com.example; import java.util.logging.*; import com.splunk.logging.SplunkCimLogEvent; logger.info(new SplunkCimLogEvent("Event name", "event-id") {{ addField("name", "value"); addThrowableWithStacktrace(ex); setAuthAction("deny"); }});
- 47. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. TCP Splunk Input Classes • SplunkCimLogEvent: • Events contain key-value pairs, properly formatted and quoted for logging with any of Java's standard logging libraries (Logback, Log4j 2, and java.util.logging) and indexing by Splunk Enterprise. SplunkCimLogEvent has convenience methods to set the fields defined in the standard Splunk Common Information Model (CIM). • TcpAppender: • Writes logging events to a TCP Input. • Extends from the ch.qos.logback.core.AppenderBase<E> class, because Logback does not ship with a usable appender for TCP socket
- 48. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. RESOURCES
- 49. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Resources • OWASP Application Logging • https://www.owasp.org/index.php/Logging_Cheat_Sheet • Java Logging • Documentation: https://docs.oracle.com/javase/8/docs/technotes/guides/logging/ • API: https://docs.oracle.com/javase/8/docs/api/java/util/logging/package- summary.html • Splunk logging for Java • http://dev.splunk.com/view/splunk-logging-java/SP-CAAAE2K
- 50. Red7:|:applicationsecurity © Copyright 2017 Robert Grupe. All rights reserved. Finis • This Presentation & Further Resources • www. rgrupe.com • Questions, suggestions, & requests • Robert Grupe, CISSP, CSSLP, PE, PMP • [email protected] • +1.314.278.7901
Editor's Notes
- #22: Documentation @ https://docs.oracle.com/javase/8/docs/technotes/guides/logging/
- #35: http://dev.splunk.com/view/splunk-logging-java/SP-CAAAE3P
- #38: http://dev.splunk.com/view/splunk-logging-java/SP-CAAAE7M
- #44: http://dev.splunk.com/view/splunk-logging-java/SP-CAAAE3R































![Red7:|:applicationsecurity
© Copyright 2017 Robert Grupe. All rights reserved.
Java Logging Example
package com.example;
import java.util.logging.*;
public class Nose{
private static Logger logger = Logger.getLogger("com.wombat.nose"); // Obtain logger
public static void main(String argv[]) { // Log FINE tracing message
logger.fine("doing stuff");
try{
Wombat.sneeze();
} catch (Exception ex) { // Log the exception
logger.log(Level.WARNING, "trouble sneezing", ex);
}
logger.fine("done");
}
}](https://image.slidesharecdn.com/red7splunkapplicationsecurityloggingjava20170423-170424015249/85/Application-Security-Logging-with-Splunk-using-Java-31-320.jpg)






![Red7:|:applicationsecurity
© Copyright 2017 Robert Grupe. All rights reserved.
HTTP 3. Java Application Configuration
• Specify jdklogging.properties to your program by passing the
following to the Java executable
• Customize jdklogging.properties file
• Bare-minimum version below [refer to slide notes for more info]:
• Includes just the url, level, and token properties, plus the
disableCertificateValidation property.
• Doesn’t include optional source, sourcetype, batch_interval,
batch_size_bytes, batch_size_count, and index.
Need to customize XML configuration file for your setup.
- Djava.util.logging.config.file=/path/to/jdklogging.properties
%user_logger_name%.level = INFO
%user_logger_name%.handlers = com.splunk.logging.HttpEventCollectorLoggingHandler
com.splunk.logging.HttpEventCollectorLoggingHandler.url = %scheme%://%host%:%port%
com.splunk.logging.HttpEventCollectorLoggingHandler.level = INFO
com.splunk.logging.HttpEventCollectorLoggingHandler.token = %user_httpeventcollector_token%
com.splunk.logging.HttpEventCollectorLoggingHandler.disableCertificateValidation=true](https://image.slidesharecdn.com/red7splunkapplicationsecurityloggingjava20170423-170424015249/85/Application-Security-Logging-with-Splunk-using-Java-39-320.jpg)










