AppSec Tel Aviv - OWASP Top 10 For JavaScript Developers
- 1. OWASP TOP 10 For JavaScript Developers @LewisArdern
- 2. About Me • Sr. Security Consultant @ Synopsys Software Integrity Group (SIG) – Formerly Cigital • AngularSF Organizer – https://www.meetup.com/Angular-SF/ • B.Sc. in Computer Security and Ethical Hacking – Founder of http://leedshackingsociety.co.uk/ • JavaScript Enthusiast!
- 3. What is the OWASP Top 10? • 10 critical web application security risks • Common flaws and weaknesses • Present in nearly all applications Modern, evidence-based risks. Data covers 2014-2017: • 114,000 apps • 9000 bug bounties • 40 security consultancies and 1 bug bounty firm • 50+ CWEs accepted in raw data Community-chosen risks • 500 survey responses OWASP Top 10 2017 A1 Injection A2 Broken Authentication A3 Sensitive Data Exposure A4 XML External Entities (XXE) A5 Broken Access Control A6 Security Misconfiguration A7 Cross-site Scripting A8 Insecure Deserialization A9 Using Components with Known Vulnerabilities A10 Insufficient Logging and Monitoring
- 4. A1:2017 Injection The Dangers of Mixing Data and Code
- 5. Official documentation says no SQL Injection Vulnerable If: • User input includes a Mongo Query Selector: • $ne, $lt, $gt, $eq, $regex, etc. • User input is directly included into a collection method as part of the query: • find, findOne, findOneAndUpdate, etc. NoSQL Injection No SQL Injection != No Injection In NoSQL https://docs.mongodb.com/manual/faq/fundamentals/#how-does-mongodb-address-sql-or-query-injection https://docs.mongodb.com/manual/reference/operator/query/ https://docs.mongodb.com/manual/reference/method/
- 6. Query Output: Vulnerable MongoDB Login Example Injection: https://url.to/login?user=admin&pass[$ne]=
- 8. MongoDB Injection Prevention • Ensure user-input is a String inside a collection method • https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Global_Objects/String • Perform Custom Data Validation • https://github.com/hapijs/joi
- 10. • Parameterized Mechanisms • https://github.com/tediousjs/node-mssql#input-name-type-value • https://github.com/mysqljs/mysql#escaping-query-identifiers • Secure APIs • https://github.com/tediousjs/node-mssql#prepared-statements • Perform Input Validation & Output Encoding • https://dev.to/azure/pushing-left-like-a-boss-part-5-1-input-validation-output-encoding-and-parameterized- queries-2749 Injection Prevention Business Logic XML file DB Input Validation Output Encoding Parameterized query Business logicClient < Ok? =? Input Output
- 11. A2:2017 Broken Authentication Broken Authentication and Session Management
- 12. Insecure Object Comparisons • What happens if you create your own Authentication middleware?
- 13. Comparison Table Value Return SESSIONS['invalidString'] False SESSIONS[''] False SESSIONS['constructor'] True SESSIONS['hasOwnPropery'] True
- 14. What Happens When You Create an Object in JavaScript?
- 15. Exploit This issue is trivial to exploit. • Using cURL we can simply run the following command: – curl https://localhost:9000 -H "Cookie: token=constructor" • Alternatively, you can just set the document.cookie value via the browser.
- 17. How Do We Correctly Check? • Use crypto.timingSafeEqual(a, b) – https://nodejs.org/api/crypto.html#crypto_crypto_timingsafeequal_a_b – It provides a safe comparison and prevents timing attacks • Object.hasOwnProperty or Map.has do not check base properties – https://developer.mozilla.org/en- US/docs/Web/JavaScript/Reference/Global_Objects/Object/hasOwnProperty – https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Global_Objects/Map/has
- 18. A4:2017 XML External Entities (XXE)
- 19. XML External Entities (XXE) Injection Two examples of parsing libraries vulnerable to XXE • node-expat – 48,353 weekly downloads – Vulnerable by default – No way to configure parser to disable DTD – https://help.semmle.com/wiki/display/JS/XML+ internal+entity+expansion • libxmljs – 47,876 weekly downloads – Vulnerable if noent is set to true – https://help.semmle.com/wiki/display/JS/XML+ external+entity+expansion
- 20. XML External Entities (XXE) Vulnerable Example Libxmljs can be vulnerable to XXE https://github.com/appsecco/dvna/blob/69f46843c05613d707fa5d036e350cca37deeb19/core/appHandler.js#L235 User-input: req.files Misconfiguration: noent: true
- 21. XML Injection Prevention • Consider using a library which does not process DTDs – https://github.com/isaacs/sax-js • Use libraries with safe defaults, such as libxmljs (apart from its sax parser) – https://github.com/libxmljs/libxmljs • If entities such as & or > need to be expanded use lodash, underscore, or he – https://lodash.com/docs/4.17.11#unescape – https://underscorejs.org/#unescape – https://github.com/mathiasbynens/he • Alternatively, strict input validation/output encoding must be performed before parsing
- 22. A5:2017 Broken Access Control
- 23. Do Not Rely on Client-Side Controls • Client-side routing and authorization should only be implemented for user experience • Authentication and authorization controls implemented client-side can be bypassed • All authorization, authentication, and business logic controls must be enforced server-side: – npm packages - https://github.com/casbin/node-casbin – Frameworks - https://sailsjs.com/documentation/concepts/policies/access-control-and-permissions – Writing custom middleware:
- 24. Angular Example • Angular Route Guards are for Boolean display aesthetics https://angular.io/guide/router#milestone-5-route-guards https://nvisium.com/blog/2019/01/17/angular-for-pentesters-part-2.html
- 26. Ensure Node Is Not Running in Development Mode • NodeJS and most frameworks that run on it return verbose errors if left in development mode • When deploying to production, set the NODE_ENV variable to a value other than development to avoid verbose errors – https://expressjs.com/en/advanced/best-practice-performance.html NodeJS applications run in development mode by default
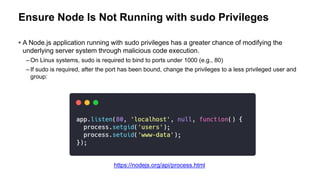
- 27. Ensure Node Is Not Running with sudo Privileges • A Node.js application running with sudo privileges has a greater chance of modifying the underlying server system through malicious code execution. – On Linux systems, sudo is required to bind to ports under 1000 (e.g., 80) – If sudo is required, after the port has been bound, change the privileges to a less privileged user and group: https://nodejs.org/api/process.html
- 28. A7:2017 Cross-Site Scripting (XSS)
- 29. XSS Is Easy To Introduce http://www.vulnerable.site#userName=<img src=x onerror='alert(document.domain)’> Script Execution:
- 30. XSS Prevention Is HARD • DOM XSS is hard to prevent in todays developer ecosystem – https://hackerone.com/reports/158853 – https://hackerone.com/reports/405191 – https://hackerone.com/reports/164821 • Each browser parses and renders HTML differently – https://www.youtube.com/watch?v=lG7U3fuNw3A – http://shazzer.co.uk • Various execution contexts and character sets – https://html5sec.org – https://github.com/cure53/XSSChallengeWiki/wiki/Puzzle-1-on-kcal.pw – http://polyglot.innerht.ml/ • Script Gadgets – https://github.com/google/security-research-pocs/tree/master/script-gadgets @LiveOverflow
- 31. Frameworks Reduce The Attack Surface Until: • Combining templating engines, third-party libraries, and frameworks – https://jsfiddle.net/015jxu8s/ • Disabling security controls – https://docs.angularjs.org/api/ng/provider/$sceProvider • Using Insecure APIs – trustAs, v-html, bypassSecurityTrust, or dangerouslySetInnerHTML • Allowing JavaScript URIs in <a href=“”></a> – https://medium.com/javascript-security/avoiding-xss-in-react-is-still-hard-d2b5c7ad9412 • Direct access to the DOM – https://angular.io/api/core/ElementRef • Server-Side Rendering – https://medium.com/node-security/the-most-common-xss-vulnerability-in-react-js-applications- 2bdffbcc1fa0 • Caching mechanisms such as $templateCache – https://docs.angularjs.org/guide/security Note: This is not an exhaustive list.
- 32. Signal Creates a Lot of Noise What happens if you bypass React controls for insecure use? Source: https://ivan.barreraoro.com.ar/wp-content/uploads/2018/05/poc1.mp4?_=1
- 33. What Went Wrong? Signal developers utilized dangerouslySetInnerHTML for phone and desktop leading to RCE in the desktop and Cross-Site Scripting (XSS) in iOS/Android https://github.com/signalapp/Signal-Desktop/commit/4e5c8965ff72576a9e20850dd30d9985f4073192#diff-f8bba204372da85d8cceed81278b7eecL114
- 34. General Prevention Techniques • Libraries and frameworks for automatic output encoding and sanitization: – Pug, Mustache, EJS – Angular, React ,Vue – secure-filters • Sanitization for HTML, MathML and SVG with DOMPurify – https://github.com/cure53/DOMPurify • Default to safe APIs – innerText – encodeURI Templating Engine HTML Output Mustache {{code}} <b>Input</b> Jade/Pug #{code} <b>Input</b> EJS <%=code%> <b>Input</b> Caution: Always use the correct encoding context, in the correct order.
- 35. • Create a strong Content Security Policy (CSP) – https://speakerdeck.com/lweichselbaum/csp-a-successful-mess-between-hardening-and-mitigation – https://twitter.com/LewisArdern/status/1112926476498698240 – https://csp.withgoogle.com • Experiment with Trusted Types – https://developers.google.com/web/updates/2019/02/trusted-types Apply Defence In Depth Strategies
- 36. A9:2017 Using Components with Known Vulnerabilities
- 37. Security Issues with Third-Party Components • Perform a security audit against 3rd party code • If you find a security issue, notify the project maintainer – https://github.blog/2019-05-23-introducing-new-ways-to-keep-your-code-secure/#open-source-security • Use automated tools to audit dependencies in your CI/CD pipeline: Example Command npm https://docs.npmjs.com/cli/audit npm audit --fix yarn https://yarnpkg.com/en/docs/cli/audit yarn audit --fix bower https://www.npmjs.com/package/auditjs auditjs --bower bower.json Client-Side JavaScript https://github.com/retirejs/retire.js/ retire --js /path/ Node.js Open-Source https://snyk.io/test/ snyk test
- 38. Examples of Components with Known Vulnerabilities • Prototype Pollution In Lodash: CVE-2018-3721 in Lodash impact in some cases was denial of service (DoS), Remote Code Execution (RCE), and even bypass security controls. • Directory Traversal in Next.js: CVE-2018-6184 in Next.js allowed for arbitrary read of the file system • Cross-Site-Scripting (XSS) in Next.js: CVE-2018-18282 in Next.js allowed for XSS on the /_error page • Privilege Escalation in auth0-js: CVE 2018-6873 in auth0-js did not validate JWT audience which allowed for Privilege Escalation • Arbitrary Command Injection in Kibana: CVE-2018-17246 in Kibana allowed for arbitrary command execution in the Console Plugin. These are examples of popular components with known vulnerabilities:
- 39. Mitigation Techniques • Maintain a technology assets inventory to track components and dependencies – https://medium.com/uber-security-privacy/code-provenance-application-security-77ebfa4b6bc5 – https://yarnpkg.com/lang/en/docs/cli/why/ and https://yarnpkg.com/lang/en/docs/cli/list – https://docs.npmjs.com/cli/ls.html – https://bower.io/docs/api/#list • Review the inventory on a regular basis for known vulnerabilities • Track known risks and vulnerabilities in the environment • Develop a process to update, and regression test external components • Pin Dependency versions where possible – Reduce the risk of another event-stream affecting your organization – https://docs.npmjs.com/files/shrinkwrap.json – https://yarnpkg.com/lang/en/docs/yarn-lock Track use of outdated third-party components and update where necessary:
- 40. Thank you! Email: [email protected] Website: https://ardern.io Twitter: https://twitter.com/LewisArdern GitHub: https://github.com/LewisArdern LinkedIn: https://www.linkedin.com/in/lewis-ardern-83373a40 Bonus Slides Available Online* https://github.com/LewisArdern/ConferenceTalks/tree/master/OWASP%20Top%2010
- 41. OWASP Top 10 https://www.owasp.org/index.php/Category:OWAS P_Top_Ten_Project OWASP Application Security Verification Standard https://www.owasp.org/index.php/Category:OWAS P_Application_Security_Verification_Standard_Pro ject OWASP Proactive Controls https://www.owasp.org/index.php/OWASP_Proacti ve_Controls OWASP Testing Guide https://www.owasp.org/index.php/OWASP_Testing _Project OWASP Cheat Sheet Series https://www.owasp.org/index.php/OWASP_Cheat_ Sheet_Series BSIMM https://www.bsimm.com/ https://www.owasp.org/index.php/OWASP_SAMM _Project SafeCode https://safecode.org Microsoft Agile SDL https://www.microsoft.com/en- us/SDL/discover/sdlagile.aspx Recommended Reading:
- 43. Cheat Sheets & Best Practices https://cheatsheets.pragmaticwebsecurity.com/cheatsheets/angularOWASPtop10.pdf https://github.com/i0natan/nodebestpractices
- 44. Recommended Open Source Analysis Tools Products that perform JavaScript data flow analysis: • Coverity Scan • LGTM Tools that look for areas of interest: • Tarnish • JSHint • JSLint • ESLint – Code Climate - nodesecurity plugin • TSLint – tslint-config-security – tslint-angular-security Tools that look for known issues in JavaScript libraries: • Retire.js • npm audit • yarn audit • GitHub • Snyk • auditjs Tools that deobfuscate JavaScript: • Closure Compiler • JStillery • Unminify • Jsnice • jsdetox • prepack.io Referencing only projects that are either open-source or scan open-source:
- 45. ESLint Security Rules • ESLint can help identify security issues • Default security rule configs – NodeJS https://github.com/nodesecurity/eslint-config-nodesecurity – VanillaJS https://github.com/mozfreddyb/eslint-config-scanjs – AngularJS https://github.com/LewisArdern/eslint-plugin-angularjs-security-rules – React https://github.com/yannickcr/eslint-plugin-react#list-of-supported-rules • Security rules – eslint-plugin-scanjs – eslint-plugin-security – eslint-plugin-react – eslint-plugin-angularjs-security – eslint-plugin-no-wildcard-postmessage – eslint-plugin-no-unsafe-innerhtml – vue/no-v-html – eslint-plugin-prototype-pollution-security-rules





![Query Output:
Vulnerable MongoDB Login Example
Injection:
https://url.to/login?user=admin&pass[$ne]=](https://image.slidesharecdn.com/appsectelavivowasptop1030minutes-190531140010/85/AppSec-Tel-Aviv-OWASP-Top-10-For-JavaScript-Developers-6-320.jpg)






![Comparison Table
Value Return
SESSIONS['invalidString'] False
SESSIONS[''] False
SESSIONS['constructor'] True
SESSIONS['hasOwnPropery'] True](https://image.slidesharecdn.com/appsectelavivowasptop1030minutes-190531140010/85/AppSec-Tel-Aviv-OWASP-Top-10-For-JavaScript-Developers-13-320.jpg)