Arrow ECS IBM Partner Jam - Security Update - Vicki Cooper - IBM
- 1. IBM Security Systems Arrow Business Partner Jam – Tuesday 17th July 2012 Vicki Cooper, Security Systems Sales Manager IBM Security Systems IBM Software Group UKI © 2012 IBM Corporation 1 © 2012 IBM Corporation
- 2. IBM Security Systems IT Security is a board room discussion Business Brand image Supply chain Legal Impact of Audit risk results exposure hacktivism Sony estimates HSBC data Epsilon breach TJX estimates Lulzsec 50-day Zurich potential $1B breach impacts 100 $150M class hack-at-will Insurance PLc long term discloses 24K national brands action spree impacts fined £2.275M impact – private banking settlement in Nintendo, CIA, ($3.8M) for the $171M / 100 customers release of PBS, UK NHS, loss and customers* credit / debit UK SOCA, exposure of card info Sony … 46K customer records 2 © 2012 IBM Corporation
- 3. IBM Security Systems Security leaders shared their views on how the security landscape is changing 3 Source: IBM Center for Applied Insights © 2012 IBM Corporation
- 4. IBM Security Systems Targeted Attacks Shake Businesses and Governments IBM Security X-Force® 2011 Trend and Risk Report 4 © 2012 IBM Corporation
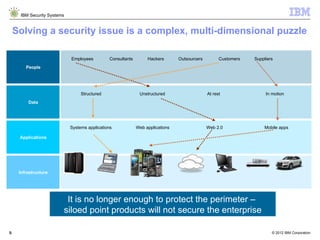
- 5. IBM Security Systems Solving a security issue is a complex, multi-dimensional puzzle Employees Consultants Hackers Outsourcers Customers Suppliers People Structured Unstructured At rest In motion Data Systems applications Web applications Web 2.0 Mobile apps Applications Infrastructure It is no longer enough to protect the perimeter – siloed point products will not secure the enterprise 5 5 © 2012 IBM Corporation
- 6. IBM Security Systems Intelligence: Leading products and services in every segment 6 © 2012 IBM Corporation
- 7. IBM Security Systems IBM’s Vision for Infrastructure Threat Protection – Roadmap Security Network Intelligence Risk Log Manager SIEM Activity Future Platform Manager Monitor Threat 2 Intelligence Vulnerability Data Malicious Websites Malware Information IP Reputation and Research Advanced Management Threat Protection 1 3 4 Platform Content Network Intrusion Web Application IBM Network and Data Anomaly Future Prevention Protection Security Security Detection 1 1Q12: Launched IBM Security Network IPS Powered by X-Force 2 2Q12: Launch X-Force IP Reputation Feed for QRadar 3 2Q12: Launch QRadar Network Anomaly Detection 7 © 2012 IBM Corporation
- 8. IBM Security Systems In this “new normal”, organizations need an intelligent view of their security posture Optimized Organizations use In Sec predictive and te u automated security lli rit ge y analytics to drive toward nc security intelligence e O Automated pt im iz ed Prr P Proficient offi o Security is layered into ic i ci the IT fabric and en en business operations Basic tt Ba Manual Organizations si employ perimeter c protection, which regulates access and feeds manual reporting Reactive Proactive 8 © 2012 IBM Corporation
- 9. IBM Security Systems Business Partner Value in the Sales Process – SVI Programme Business Partner Opportunity Sales Process Contribution Registration Identifying and qualifying new customer Identify opportunities for SWG’s products accurately captures Developing and delivering compelling value the Sell propositions, proof of concepts, etc. that result Business in customers selecting SWG’s products Partner’s contribution Providing fulfillment services such as contract in a timely Fulfill management, order management, credit risk, fashion and shipping and logistics 9 © 2012 IBM Corporation
- 10. IBM Security Systems Aligning Business Partner Incentives to Value Linked Total Identify Sell Fulfill Earning SVI Potential (Fee Payment) As normal Base Discount 5% 5%* No Change 10%+ + SMB Premium +5% +5%* No Change 20%+ OR Value Advantage Plus +10% +15% 15% 40% (Rebate) – Reward for “identify” is dependent upon qualification for “sell” – Rewards for “identify” and “sell” are independent of “fulfill” (Assuming partner – Value Advantage Plus remains as an alternative for “sell” rewards identifies, sells & – Fee payments processed immediately after software claim fulfills) 10 © 2012 IBM Corporation
- 11. IBM Security Systems Marketing Support for Business Partners Generating Opportunity BP Opportunity Identification VAD Led Campaigns Mid Market Specific IBM Led -VAD Rebate Program Co-Marketing BP autonomous OnChannel BP participates in IBM Self-led and funded -& Campaign as a Service - 50/50 IBM/BP funded 75%-25% IBM/BP funded Led campaigns campaigns - VAD funds 100% Discuss with Build your Dedicated MM Check the IBM Leverage IBM your VAD on marketing plan campaigns Brand Plans, Content their 2012 plans and put only. Request visit (through IBM and where they requests via via your VAD. BluePlanner Brand Assets can support you your VAD Campaign regularly and and Pre- based on your provided you executed A-Z enquire via yr packaged contractual meet the pre- by OnChannel BP Rep if campaigns from engagement and requisites (see agency anything of IBM Brand your own slide 5) interest Marketing, on business and PW or in the marketing plans Co-Marketing Center ) 11 © 2012 IBM Corporation
- 12. IBM CONFIDENTIAL IBM Security Systems BP Certifications update – July 15th Tests put in place: – Security Sales Mastery – QRadar Technical Certification FROM TO Rational Group Tivoli Security Group AppScan I&AM ISS/Threat I&AM ISS Application Security Automation Automation Group Data Group Tivoli Endpoint Data Group Group Manager (BigFix) Tivoli Endpoint Guardium Guardium Manager (BigFix) Partners required to pass: Partners required to pass sales and technical - 1 security sales mastery and: certifications for Rational, Tivoli, Information -2 Technical Certs for each of the groups (specific to management – Sales and Tech Sales to sell the portfolio those products the want to resell (ex. 3 Sales and upwards for 8 - 10 technical - Guardium & TEM Tech Certs apply to Security auth. certifications As few as 4 total Tech Certs can earn all three authorizations. 12 © 2012 IBM Corporation
- 13. IBM Security Systems Why IBM Security: Breadth, deep expertise, integration Leadership 10+ years of leadership and innovation in Intrusion Detection/Prevention Help protect many of the largest organizations in the world Integration Integrates with other security tools such as IBM’s AppScan suite to deliver more intelligent Web application security Expertise Backed by X-Force, one of the largest security research teams 9 security research centers combined with 9 security operations centers around the world Consolidated management of hundreds of IPS sensors, as well as other security solutions 13 © 2012 IBM Corporation
- 14. IBM Security Systems ibm.com/security 14 © 2012 IBM Corporation
Editor's Notes
- #10: There are three basic areas of contribution or value that you may be compensated for …and they map directly to the essential elements of the sales process: “ Identify” – that’s finding and validating new opportunities – especially opportunities in new customers “ Sell” – taking the opportunity and running with it to close the deal – applying your sales and technical expertise to convince the customer that you have the right solution to their business problem – based, of course, on IBM software technology… “ Fulfill” – managing the order and delivery logistics to get the right products to the right customer, on time It is relatively simple to compensate our partners for the fulfillment piece of this – this is what we have always done… We know which partners deliver what, and to whom, through Passport Advantage – our customer discount system However, appropriately compensating for these other activities – Identify & Sell – is more difficult. It requires that we know who performed them. Passport Advantage can’t help us there. That’s why a secure and easily accessible deal registration system becomes a critical element of this new incentive design Deal registration systems can capture the details of a Business Partner’s contribution (who has invested time, skills, etc…) – simply, quickly and accurately - from the outset of the opportunity. So… now we are able to track who is contributing what, …and where… … let’s see how this will work in earnest – with some real numbers…