ASIC Implementation of Triple Data Encryption Algorithm (3DES)
The Triple DES Encryption is a data encryption algorithm which will be used to protect confidential data against unauthorized access. This algorithm can be used to encrypt and decrypt files, which applies the triple data encryption standard (3DES). The project is designed to enhance the security of data stored inside the devices. It enhances the privacy of the user and also able to protect user’s identity. Anyone who wants to read the data file inside the device needs to have the right keys in order to decrypt the file. Businesses may use it to protect corporate secrets, governments use it to secure classified information, and many individuals use it to protect personal information to guard against things like identity theft. The 3DES algorithm makes this design unique and important since it is hard to break. This project is more appropriate for an ASIC design because the project needed to be customized to implement a chip with application-specific logic for a particular use. This kind of task is more suitable for the ASIC rather than microcontroller since microcontroller usually needs more time delay and consumes much more power than ASIC design.The Triple DES Encryptor will track all bytes being transferred to a certain device and then applies bitwise operation for the encryption/decryption algorithm. FPGA will be used to off load the encryption algorithm onto the FPGA from the Atom/Linux, then the block that does the encryption will have to write over the Avalon bus to the FPGA.





















Recommended




























































More Related Content
What's hot (20)












































Viewers also liked (20)






































Similar to ASIC Implementation of Triple Data Encryption Algorithm (3DES) (20)










































Recently uploaded (20)




















ASIC Implementation of Triple Data Encryption Algorithm (3DES)
- 1. Triple DES Team members: Junjie Wang, Xiao Xiao, Zhuofan Li, Ming Huen Lee 1
- 2. Overview - What is 3DES? Users are able encrypt / decrypt data in a secure way Prevent hacking into important data Algorithm applies Data Encryption Standard (DES) 3 times Ciphertext = EK3(DK2(EK1(plaintext))) Each DES has 16 rounds of processing -> Encrypted with 56-bit key Appropriate for ASIC design Less time delay Consume less power Data will send through avalon bus to the FPGA 2
- 6. Fixed Success Criteria 1. Test benches exist for all top level components and the entire design. The test benches for the entire design can be demonstrated or documented to cover all of the functional requirements given in the design specific success criteria. (2 pts/Achieved) 2. Entire design synthesizes completely, without any inferred latches, timing arcs, and, sensitivity list warnings (4 pts/Achieved) 3. Source and mapped version of the complete design behave the same for all test cases. The mapped version simulates without timing errors except at time zero (2 pts/Achieved) 4. A complete IC layout is produced that passes all geometry and connectivity checks (2 pts) 5. The entire design complies with targets for area, pin count, throughput (if applicable), and clock rate. (2pts) 6
- 7. Fixed Criteria 1 & 2 7
- 11. Design Specific Success Criteria 1. Demonstrate by utilizing a know, working 3DES online tool that the output of the design both encrypts and decrypts according to the 3DES algorithm. (1 point/Achieved) 2. Demonstrate by simulation of verilog test benches that the complete design is able to utilize pipelining.(1 point/Achieved) 3. Demonstrate by simulation of verilog test benches that the complete design is able to successfully implement 3DES encryption (2 points/Achieved) 4. Demonstrate by simulation of verilog test benches that the complete design is able to successfully implement 3DES decryption. (2 points/Achieved) 5. Demonstrate that the complete design is able to dump data from atom to FPGA using C code for Avalon-Bus. (2 points/Achieved) 11
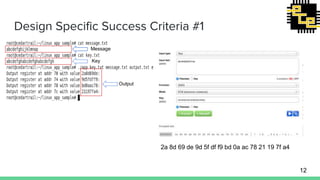
- 12. Design Specific Success Criteria #1 2a 8d 69 de 9d 5f df f9 bd 0a ac 78 21 19 7f a4 Message Key Output 12
- 13. Design Specific Success Criteria #2 New data input every 8 clock cycles when dataready is high 13
- 14. Design Specific Success Criteria #2 cont. Apply Triple DES algorithm using pipelining with same keys Input data 1 Input data 2 Encrypted data 1 Encrypted data 2 Encrypted data 1 Encrypted data 2 Decrypted data 1 Decrypted data 2 14
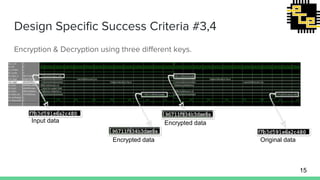
- 15. Design Specific Success Criteria #3,4 Encryption & Decryption using three different keys. Input data Encrypted data Encrypted data Original data 15
- 16. Design Specific Success Criteria #5 Output Input Next_enable 16
- 17. Quartus Report Area on the FPGA FPGA CLOCK 17
- 18. Conclusion Challenges: Develop an efficient algorithm for pipelining process FPGA (communication with atom) Time Management Approaches differently: Use the SDRAM on the FPGA Improvement: Expand the key size of the Triple DES to make it more secure 18
- 19. Appendix: One Round of Processing in DES 19
- 20. Appendix: One Round of Processing in DES 20
- 21. Appendix: 16 Rounds DES 21
- 22. Appendix: 16 Rounds DES 22
- 23. Appendix: Key Schedule Algorithm (KSA) 23










