Integrating Security into DevOps
- 1. © 2013 CloudPassage Inc. Integrating Security Into DevOps Rand Wacker VP Products @randwacker Tatiana Slater Community Manager @Turbo_Tats
- 2. © 2013 CloudPassage Inc. Agenda for Today • DevOps & Security – BFFs? • Critical components of application security • CloudPassage Halo Overview • Halo Security API Toolbox • FREE Developer Access
- 3. © 2013 CloudPassage Inc. Integrating Security Into DevOps: Automation Is Your Only Hope
- 4. © 2013 CloudPassage Inc. Why DevOps Loves Cloud
- 5. © 2013 CloudPassage Inc. Why DevOps Hates Security DB Load Balancer Auth Server App Server DB Load Balancer App Server DB dmz dmz corecore Firewal l Firewal l Waiting for Server Provisioning… Delays in Firewall Updates… Typically 6 weeks to tip up a new server
- 6. © 2013 CloudPassage Inc. Poll: Security Concerns • What is your primary concern about securing cloud applications and infrastructure? – Will slow down our pace of development/innovation – Will cost too much – We don’t have the expertise to do it – No concerns, we are actively working to secure them
- 7. © 2013 CloudPassage Inc. Cloud Complicates Security
- 8. © 2013 CloudPassage Inc. Where Do Existing Solutions Fail? Cloud Provider A www-4 www-5 www-6 Cloud Provider B www-7 www-8 www-9 www-10 Private Datacenter www-1 www-2 www-3 No Network or Hypervisor Access Multiple Cloud Environments Metered Utility Usage Cloud Provider A www-4 www-5 www-6 Temporary & Elastic Deployments
- 9. © 2013 CloudPassage Inc. Organizational Ostracism IT Operations DevOps Security Operations
- 10. © 2013 CloudPassage Inc. Critical Components of Application and Stack Security
- 11. © 2013 CloudPassage Inc. Shared Responsibility Model “…the customer should assume responsibility and management of, but not limited to, the guest operating system.. and associated application software...” “…it is possible for customers to enhance security and/or meet more stringent compliance requirements with the addition of host based firewalls, host based intrusion detection/prevention, encryption and key management.” Amazon Web Services: Overview of Security Processes AWS Shared Responsibility Model Customer Responsibility Provider Responsibility Physical Facilities Hypervisor Compute & Storage Shared Network Virtual Machine Data App Code App Framework Operating System
- 12. © 2013 CloudPassage Inc. Securing Cloud Applications Whether in a private datacenter or a public cloud, server security is your responsibility, so know your security business drivers: Compliance :: Continuity :: Brand Architect your service to solve these problems in public, private, and hybrid deployments, specifically: Perimeter & Access Control Server Integrity & Intrusion Detection
- 13. © 2013 CloudPassage Inc. Virtual Machine Secure the VM, Secure the App FWFW Provision host-based firewalls (inbound and outbound) Automate, Automate, Automate Data App Code App Framework Operating System Track sensitive data and prevent egress Continuously verify applications code is current and un-tampered Ensure application stacks are up-to-date and locked down Secure the OS services and configurations
- 14. © 2013 CloudPassage Inc. Cloud Complicates Security • Cloud app architecture more different than just being highly virtualized – Short image lifecycle, auto-scaling, “pets vs cattle” • Traditional security approaches ill-suited to self- service, automated deployments • Security orgs traditionally separate from Dev/Ops teams Security must move at speed of cloud: automated, self-service, metered
- 15. © 2013 CloudPassage Inc. Poll: Org Responsibility • Who is in your organization is responsible for securing cloud infrastructure? – Cloud provider – DevOps/application team – IT / central security team – We’re not securing our cloud infrastructure today
- 16. © 2013 CloudPassage Inc. New Approach: Security-as-a-Service
- 17. © 2013 CloudPassage Inc. Dynamic network access control Configuration and package security Account visibility & control Compromise & intrusion alerting Forensics and security analytics Integration & automation capabilities Systems in IaaS/PaaS clouds must be self- defending with highly automated controls like… How To Secure Cloud Apps
- 18. © 2013 CloudPassage Inc. Separate Security Controls Virtual Machine Data App Code App Framework OS FWFW DevOps SecOps The days of perimeter-only defenses are over!
- 19. © 2013 CloudPassage Inc. Integrate & Automate Compute Grid CloudPassa geHalo www-4 Halo www-3 www-1 Halo Halo www-2 Halo DevOps Automation Security Monitoring
- 20. © 2013 CloudPassage Inc. CloudPassage Halo Overview
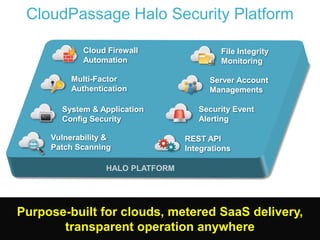
- 21. © 2013 CloudPassage Inc. CloudPassage Halo Security Platform Server Account Managements Security Event Alerting File Integrity Monitoring REST API Integrations Cloud Firewall Automation System & Application Config Security Multi-Factor Authentication Vulnerability & Patch Scanning Purpose-built for clouds, metered SaaS delivery, transparent operation anywhere
- 22. © 2013 CloudPassage Inc. Basic Halo Architecture Halo Halo Daemon • Ultra light-weight agent • Installed on server images • Automatically provisioned Halo Daemon www-1 www-1 Halo Grid • Elastic compute grid • Hosted by CloudPassage • Diverts 95% or more of analytics cycles from VM daemons Halo Grid
- 23. © 2013 CloudPassage Inc. www-1 Halo Compute Grid User Portal CloudPassage Halo Policies, Commands, Reports https RESTful API Gateway https www-1 Halo Web UI + REST API Light-weight agent Grid performs analytics SaaS delivery mysql-1 Halo bigdata-1 Cloud or Data Center Halo
- 24. © 2013 CloudPassage Inc. private cloud virtualized or bare metal center Single pane of glass across cloud deployments • Scales and bursts with dynamic cloud environments • Not dependent on chokepoints, static networks or fixed IPs • Agnostic to location, hypervisor or hardware Designed for Portability public cloud Consistent Security Controls Consistent Security Controls
- 25. © 2013 CloudPassage Inc. Quick Halo Demo
- 26. © 2013 CloudPassage Inc. We all love integration, right? Introducing: Halo Security API Toolbox
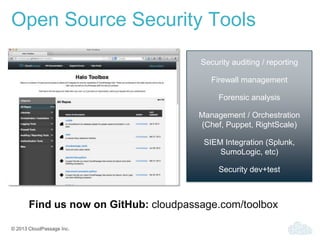
- 27. © 2013 CloudPassage Inc. Open Source Security Tools Security auditing / reporting Firewall management Forensic analysis Management / Orchestration (Chef, Puppet, RightScale) SIEM Integration (Splunk, SumoLogic, etc) Security dev+test Find us now on GitHub: cloudpassage.com/toolbox
- 28. © 2013 CloudPassage Inc. Imports Halo events into Splunk, Sumo Logic, or other logging / SIEM tools Compute Grid CloudPassa geHalo www-4 Halo www-3 www-1 Halo Halo www-2 Halo
- 29. © 2013 CloudPassage Inc. Imports Halo events into Splunk, Sumo Logic, or other logging / SIEM tools
- 30. © 2013 CloudPassage Inc. Adds or removes IP addresses via API to an IP zone that is used in a Halo firewall policy
- 31. © 2013 CloudPassage Inc. Adds or removes IP addresses via API to an IP zone that is used in a Halo firewall policy Load Balancer Halo F W App Server Halo F W App Server Halo F W DB Master Halo F W public cloud
- 32. © 2013 CloudPassage Inc.
- 33. © 2013 CloudPassage Inc. Easily sends the cryptographic checksum of a suspected compromised file to Virus Total for comparison with other reported cases of known malware.
- 34. © 2013 CloudPassage Inc. Want to contribute? github.com/cloudpassage Six-month free developer account
- 35. © 2013 CloudPassage Inc. Free Developer Access Halo Professional Developer Account Server integrity & Intrusion detection Firewall management & two- factor access Full API access 6 months free service for developer accounts Available now: cloudpassage.com/OSCON
- 36. © 2013 CloudPassage Inc. Wrapping Up
- 37. © 2013 CloudPassage Inc. Summary • Real application security is more than just firewalls, patches, and SSH • In the new DevOps and cloud world, security responsibility is shared • Security automation to maintain agility and self- service These days, everyone is a target and security is everyone’s responsibility
- 38. Thank You! Open Source Security Tools: cloudpassage.com/Toolbox 6 Months Free Halo Service: cloudpassage.com/OSCON Discuss more: @cloudpassage #CloudSec
Editor's Notes
- #20: JSON formattedBi-directional
- #29: For example, we’ve got the Halo Event Connector. We can detect a lot of security events with Halo through our Configuration Security Monitoring, File Integrity Monitoring and our Security Events module, and a lot of our customers need those to feed into tools that they use to manage logs across their environment. So, we wrote a script and some documentation to make that easier. We started with our direct partners, but the script can easily work with many other tools. We’ve made it available open-source so our customers can change it to fit their needs and integrate with whatever tool they need to use. https://support.cloudpassage.com/entries/22030408-Intro-to-the-Halo-API
- #30: For example, we’ve got the Halo Event Connector. We can detect a lot of security events with Halo through our Configuration Security Monitoring, File Integrity Monitoring and our Security Events module, and a lot of our customers need those to feed into tools that they use to manage logs across their environment. So, we wrote a script and some documentation to make that easier. We started with our direct partners, but the script can easily work with many other tools. We’ve made it available open-source so our customers can change it to fit their needs and integrate with whatever tool they need to use. https://support.cloudpassage.com/entries/22030408-Intro-to-the-Halo-API