Authentication and Authorization in Asp.Net
Download as PPTX, PDF11 likes13,154 views
This presentation gives a little information about Why Security is important, then moving towards understanding about Authentication and Authorization and its various ways 1. Forms Authentication 2. Windows Authentication 3. Passport Authentication
1 of 20
Downloaded 479 times



















Ad
Recommended
Home Automation System using iot



Home Automation System using iotKowshik Deb This document outlines a student project to develop a low-cost home automation system using IoT. It discusses what IoT is and its applications such as smart homes. It then describes how the group will create a home automation system using a Raspberry Pi, sensors, and relays to control devices remotely via a smartphone app. Some key benefits are low-cost and flexibility, while disadvantages include potential reliability issues. The system is intended to help automate security, entertainment, and other functions in the home using an internet connection.
INTRODUCTION TO JSP,JSP LIFE CYCLE, ANATOMY OF JSP PAGE AND JSP PROCESSING



INTRODUCTION TO JSP,JSP LIFE CYCLE, ANATOMY OF JSP PAGE AND JSP PROCESSINGAaqib Hussain This document provides an introduction to Java Server Pages (JSP) including the JSP life cycle and anatomy of a JSP page. It discusses how JSP pages allow embedding Java code in HTML elements to generate dynamic web content. When a request is made to a JSP page, it is processed by a JSP container that converts the page into a Java servlet, compiles the servlet, and executes the servlet to handle the request and generate the response. The document also describes how JSP pages combine static template text and dynamic JSP elements and the translation and request processing phases of handling JSP requests.
Fake news detection project



Fake news detection projectHarshdaGhai The document describes a project to detect fake news using machine learning models. It discusses how the project classified news websites as real or fake using a combination of bag-of-words, word embeddings and feature descriptions with 87.39% accuracy. Some ways to improve the model are also provided, such as using more features in the word embeddings. Real-world applications of fake news detection include verifying news on social media during elections and detecting fake job postings.
Authentication



Authenticationprimeteacher32 Authentication is the process of verifying a user's identity by requiring them to provide credentials like a password or certificate. Common authentication methods include centralized authentication services like RADIUS, TACACS+, and Kerberos which verify credentials on a network authentication server. Firewalls can integrate with these authentication servers to provide user authentication and authorization when accessing the network.
REST & RESTful Web Services



REST & RESTful Web ServicesHalil Burak Cetinkaya An introduction to REST and RESTful web services.
You can take the course below to learn about REST & RESTful web services.
https://www.udemy.com/building-php-restful-web-services/
Comptabilite generale exercices et corriges 1



Comptabilite generale exercices et corriges 1Tanger Outlets télécharger
Envoyez-moi le lien du livre
https://www.instagram.com/a.belmoufadal/
====) [email protected]
Authentication techniques



Authentication techniquesIGZ Software house The document discusses various authentication techniques, including:
- Password-based authentication using clear text passwords, message digests of passwords, and adding randomness with challenges.
- Authentication tokens, which generate one-time passwords based on a seed value stored in the token and authentication server database.
- Multifactor authentication using passwords, biometrics, and authentication tokens or smart cards.
- Certificate-based authentication using digital certificates issued in a public key infrastructure for verifying user identities.
cloud computing architecture.pptx



cloud computing architecture.pptxSourodeepChakraborty3 This document provides an overview of cloud computing, including definitions, types, architecture, services, trends, and conclusions. It defines cloud computing as utilizing shared computing resources and information provided over the internet on demand. The document outlines the key components of cloud computing architecture including the front-end and back-end. It describes the main types of cloud computing as public, private, and hybrid and provides examples and comparisons of advantages and disadvantages. Additionally, it outlines common cloud computing services including SaaS, PaaS, and IaaS and provides diagrams to illustrate cloud computing concepts. Recent trends and a conclusion emphasizing the cost benefits of cloud computing are also presented.
Authentication & Authorization in ASPdotNet MVC



Authentication & Authorization in ASPdotNet MVCMindfire Solutions This document discusses authentication and authorization in ASP.NET MVC 4. It begins by explaining why security is important and describes different authentication and authorization techniques. It then explains what providers and membership providers are in ASP.NET and some problems with the default ASP.NET membership provider. The document introduces SimpleMembership as a better alternative and shows how to implement a SimpleMembership provider in an MVC 4 application.
Web api



Web apiSudhakar Sharma This document provides an overview of ASP.NET Web API, a framework for building RESTful web services. It discusses key REST concepts like URIs, HTTP verbs, and HATEOAS. It also compares Web API to other technologies like WCF and SOAP, noting advantages of REST such as simpler CRUD operations and standardized development methodology. The document recommends resources like a book on building REST services from start to finish with ASP.NET MVC 4 and Web API.
Json Web Token - JWT



Json Web Token - JWTPrashant Walke In this PPT, the fundamentals of what JSON Web Token (JWT), and why they are used in REST API will be explained.
Authentication vs authorization



Authentication vs authorizationFrank Victory Authentication verifies a user's identity by validating credentials like a username and password. Authorization then determines what access and permissions an authenticated user has. Authentication methods can include something you know like passwords, something you have like tokens or smartcards, or something you are like biometrics. Common authentication practices for systems include setting password policies, locking accounts after failed logins, and disabling unused accounts. Proper authentication helps implement access controls and security.
Ajax ppt



Ajax pptOECLIB Odisha Electronics Control Library This document discusses AJAX (Asynchronous JavaScript and XML). It defines AJAX as a group of interrelated web development techniques used on the client-side to create interactive web applications. AJAX allows web pages to be updated asynchronously by exchanging small amounts of data with the server without reloading the entire page. The document outlines the technologies that power AJAX like HTML, CSS, XML, JavaScript, and XMLHttpRequest and how they work together to enable asynchronous updates on web pages.
IIS



IISGiritharan V IIS (Internet Information Services) is a web server application created by Microsoft for use with Windows operating systems. It supports protocols like HTTP, HTTPS, FTP, and more. IIS has been included with Windows NT, Windows 2000, Windows Server 2003, and beyond. Newer versions of IIS have added features like support for additional authentication mechanisms, modules for extending functionality, and performance/security improvements.
What Is Express JS?



What Is Express JS?Simplilearn This Express Js tutorial will walk you through what express js is, what we can do with it, features of express js and companies that are hiring express js developers. Express Js is a Node Js framework which helps to write the API’s very efficiently. It’s a awesome framework of node js which is helping Backend development so much and it provides wide set of features to develop both web and mobile applications it is used to build single page, multipage and hybrid web applications.
REST API



REST APITofazzal Ahmed Mobile Computing & Application
Very easy to presentation of REST API
REST API very important topics
ASP.NET State management



ASP.NET State managementShivanand Arur This PPT explains about the various ways to manage the state of an asp.net web application. This PPT is for complete beginners and intermediate developers who want to know few things about Asp.net State Management. Here I have explained in brief about the various techniques we use to manage the state of our application.
User authentication



User authenticationCAS USER AUTHENTICATION
MEANS OF USER AUTHENTICATION
PASSWORD AUTHENTICATION
PASSWORD VULNERABILITIES
USE OF HASHED PASSWORDS – IN UNIX
PASSWORD CRACKING TECHNIQUES
USING BETTER PASSWORDS
TOKEN AUTHENTICATION
BIO-METRIC AUTHENTICATION
REST API and CRUD



REST API and CRUDPrem Sanil A REST API uses HTTP requests with verbs like GET, POST, PUT, and DELETE to perform CRUD (Create, Read, Update, Delete) operations on resources identified by URLs. It provides a lightweight alternative to SOAP that returns data in JSON format and HTTP response codes. Well-known codes include 200 for OK, 201 for Created, 400 for Bad Request, and 404 for Not Found. REST enables building applications and platforms that can easily integrate new interfaces over time.
Jdbc ppt



Jdbc pptsandeep54552 This document discusses Java Database Connectivity (JDBC) and the steps to connect to a database using JDBC. It provides an overview of JDBC architecture and its main components. It then outlines the key steps to connect to a database which include: 1) driver registration where the appropriate JDBC driver class is loaded, 2) defining the connection URL, 3) establishing a connection, 4) creating SQL statements, 5) executing queries and processing result sets, and 6) closing the connection. Examples are provided for connecting to MySQL and Derby databases using JDBC.
Ajax Presentation



Ajax Presentationalaa.moustafa AJAX allows asynchronous data retrieval from a server without page refreshes. It uses XMLHttpRequest objects in JavaScript to make requests to the server and update parts of the page without reloading. Common uses of AJAX include Gmail, Google Maps, and Flickr. It provides a faster and more responsive web experience compared to traditional page loads. Frameworks like AJAX.NET help implement AJAX functionality on both the client-side and server-side.
Java servlets



Java servletslopjuan This document provides an overview of Java servlets. It discusses that servlets are modules that extend request/response-oriented servers like Java web servers. Unlike applets, servlets do not have a graphical user interface. The document then covers servlet basics, uses for servlets including providing CGI script functionality and load balancing, and differences between generic and HTTP servlets. It also provides examples of simple servlets and using HTTP servlets to process web forms and handle GET and POST requests. Finally, it discusses session state maintenance using HTTP session objects.
JAVA Servlets



JAVA Servletsdeepak kumar This document provides information on servlets including:
- Servlets allow dynamic content and interaction for web applications and can be used to build search engines, e-commerce sites, and more.
- Servlets have better performance than CGI since they remain loaded in memory between requests rather than starting a new process for each request.
- Servlets follow a request-response lifecycle and provide APIs to handle HTTP requests and responses through the Servlet, HttpServletRequest, and HttpServletResponse interfaces.
MVC architecture



MVC architectureEmily Bauman The document describes the Model-View-Controller (MVC) architecture pattern for web applications. It consists of three components: the Model manages and represents the application's data, the View displays the data to the user, and the Controller handles interactions between the Model and View. Many frameworks like Spring and Ruby on Rails have adopted MVC concepts. The document then provides a specific example of using the Spring MVC framework to build a web application with the MVC pattern.
Java Servlets



Java ServletsBG Java EE Course This document provides an overview of Java servlets technology, including:
1. What Java servlets are and their main purposes and advantages such as portability, power, and integration with server APIs.
2. Key aspects of servlet architecture like the servlet lifecycle, the HttpServletRequest and HttpServletResponse objects, and how different HTTP methods map to servlet methods.
3. Examples of simple servlets that process parameters, maintain a session counter, and examples of deploying servlets in Eclipse IDE.
Client side scripting



Client side scriptingEleonora Ciceri The document discusses client-side scripting and scripts. It notes that scripts automate tasks that could otherwise be done manually. Scripts can be used in software applications, web pages, operating system shells, and more. Scripting languages make writing scripts easy and support interfaces to operating system facilities. Examples of scripting languages include JavaScript, Python, and Perl. The document then contrasts interpreters with compilers and compares how scripts and software code are developed and executed.
Express js



Express jsManav Prasad This document provides an overview of ExpressJS, a web application framework for Node.js. It discusses using Connect as a middleware framework to build HTTP servers, and how Express builds on Connect by adding functionality like routing, views, and content negotiation. It then covers basic Express app architecture, creating routes, using views with different template engines like Jade, passing data to views, and some advanced topics like cookies, sessions, and authentication.
Token Authentication in ASP.NET Core



Token Authentication in ASP.NET CoreStormpath Stormpath .NET Developer Evangelist, Nate Barbettini, presents Token Authentication with ASP.NET Core. Nate will explain how Token Authentication can be used to secure web applications built with ASP.NET Core, REST APIs, and 'unsafe' clients while supporting security best practices and even improving performance and scale.
Authentication, authorization, accounting(aaa) slides



Authentication, authorization, accounting(aaa) slidesrahul kundu Authentication, authorization, and accounting (AAA) represent the major components of network access control and security. Authentication ensures a user's identity by requiring credentials like usernames and passwords. Authorization then determines the resources and services individual users have access to based on their authentication. Accounting tracks user activity for purposes like trend analysis, billing, auditing, and capacity planning. Together these three components (authentication, authorization, accounting) provide the foundation for secure network management and administration through identity verification and access control.
Difference between authentication and authorization in asp.net



Difference between authentication and authorization in asp.netUmar Ali Authentication verifies a user's identity by having them log in, while authorization determines which resources and pages the authenticated user has access to. For example, after authenticating normal and admin users on a website, authorization would prevent normal users from accessing admin pages. Authentication occurs before authorization and verifies the user, even if anonymously, while authorization checks the user's access rights after identity is confirmed.
Ad
More Related Content
What's hot (20)
Authentication & Authorization in ASPdotNet MVC



Authentication & Authorization in ASPdotNet MVCMindfire Solutions This document discusses authentication and authorization in ASP.NET MVC 4. It begins by explaining why security is important and describes different authentication and authorization techniques. It then explains what providers and membership providers are in ASP.NET and some problems with the default ASP.NET membership provider. The document introduces SimpleMembership as a better alternative and shows how to implement a SimpleMembership provider in an MVC 4 application.
Web api



Web apiSudhakar Sharma This document provides an overview of ASP.NET Web API, a framework for building RESTful web services. It discusses key REST concepts like URIs, HTTP verbs, and HATEOAS. It also compares Web API to other technologies like WCF and SOAP, noting advantages of REST such as simpler CRUD operations and standardized development methodology. The document recommends resources like a book on building REST services from start to finish with ASP.NET MVC 4 and Web API.
Json Web Token - JWT



Json Web Token - JWTPrashant Walke In this PPT, the fundamentals of what JSON Web Token (JWT), and why they are used in REST API will be explained.
Authentication vs authorization



Authentication vs authorizationFrank Victory Authentication verifies a user's identity by validating credentials like a username and password. Authorization then determines what access and permissions an authenticated user has. Authentication methods can include something you know like passwords, something you have like tokens or smartcards, or something you are like biometrics. Common authentication practices for systems include setting password policies, locking accounts after failed logins, and disabling unused accounts. Proper authentication helps implement access controls and security.
Ajax ppt



Ajax pptOECLIB Odisha Electronics Control Library This document discusses AJAX (Asynchronous JavaScript and XML). It defines AJAX as a group of interrelated web development techniques used on the client-side to create interactive web applications. AJAX allows web pages to be updated asynchronously by exchanging small amounts of data with the server without reloading the entire page. The document outlines the technologies that power AJAX like HTML, CSS, XML, JavaScript, and XMLHttpRequest and how they work together to enable asynchronous updates on web pages.
IIS



IISGiritharan V IIS (Internet Information Services) is a web server application created by Microsoft for use with Windows operating systems. It supports protocols like HTTP, HTTPS, FTP, and more. IIS has been included with Windows NT, Windows 2000, Windows Server 2003, and beyond. Newer versions of IIS have added features like support for additional authentication mechanisms, modules for extending functionality, and performance/security improvements.
What Is Express JS?



What Is Express JS?Simplilearn This Express Js tutorial will walk you through what express js is, what we can do with it, features of express js and companies that are hiring express js developers. Express Js is a Node Js framework which helps to write the API’s very efficiently. It’s a awesome framework of node js which is helping Backend development so much and it provides wide set of features to develop both web and mobile applications it is used to build single page, multipage and hybrid web applications.
REST API



REST APITofazzal Ahmed Mobile Computing & Application
Very easy to presentation of REST API
REST API very important topics
ASP.NET State management



ASP.NET State managementShivanand Arur This PPT explains about the various ways to manage the state of an asp.net web application. This PPT is for complete beginners and intermediate developers who want to know few things about Asp.net State Management. Here I have explained in brief about the various techniques we use to manage the state of our application.
User authentication



User authenticationCAS USER AUTHENTICATION
MEANS OF USER AUTHENTICATION
PASSWORD AUTHENTICATION
PASSWORD VULNERABILITIES
USE OF HASHED PASSWORDS – IN UNIX
PASSWORD CRACKING TECHNIQUES
USING BETTER PASSWORDS
TOKEN AUTHENTICATION
BIO-METRIC AUTHENTICATION
REST API and CRUD



REST API and CRUDPrem Sanil A REST API uses HTTP requests with verbs like GET, POST, PUT, and DELETE to perform CRUD (Create, Read, Update, Delete) operations on resources identified by URLs. It provides a lightweight alternative to SOAP that returns data in JSON format and HTTP response codes. Well-known codes include 200 for OK, 201 for Created, 400 for Bad Request, and 404 for Not Found. REST enables building applications and platforms that can easily integrate new interfaces over time.
Jdbc ppt



Jdbc pptsandeep54552 This document discusses Java Database Connectivity (JDBC) and the steps to connect to a database using JDBC. It provides an overview of JDBC architecture and its main components. It then outlines the key steps to connect to a database which include: 1) driver registration where the appropriate JDBC driver class is loaded, 2) defining the connection URL, 3) establishing a connection, 4) creating SQL statements, 5) executing queries and processing result sets, and 6) closing the connection. Examples are provided for connecting to MySQL and Derby databases using JDBC.
Ajax Presentation



Ajax Presentationalaa.moustafa AJAX allows asynchronous data retrieval from a server without page refreshes. It uses XMLHttpRequest objects in JavaScript to make requests to the server and update parts of the page without reloading. Common uses of AJAX include Gmail, Google Maps, and Flickr. It provides a faster and more responsive web experience compared to traditional page loads. Frameworks like AJAX.NET help implement AJAX functionality on both the client-side and server-side.
Java servlets



Java servletslopjuan This document provides an overview of Java servlets. It discusses that servlets are modules that extend request/response-oriented servers like Java web servers. Unlike applets, servlets do not have a graphical user interface. The document then covers servlet basics, uses for servlets including providing CGI script functionality and load balancing, and differences between generic and HTTP servlets. It also provides examples of simple servlets and using HTTP servlets to process web forms and handle GET and POST requests. Finally, it discusses session state maintenance using HTTP session objects.
JAVA Servlets



JAVA Servletsdeepak kumar This document provides information on servlets including:
- Servlets allow dynamic content and interaction for web applications and can be used to build search engines, e-commerce sites, and more.
- Servlets have better performance than CGI since they remain loaded in memory between requests rather than starting a new process for each request.
- Servlets follow a request-response lifecycle and provide APIs to handle HTTP requests and responses through the Servlet, HttpServletRequest, and HttpServletResponse interfaces.
MVC architecture



MVC architectureEmily Bauman The document describes the Model-View-Controller (MVC) architecture pattern for web applications. It consists of three components: the Model manages and represents the application's data, the View displays the data to the user, and the Controller handles interactions between the Model and View. Many frameworks like Spring and Ruby on Rails have adopted MVC concepts. The document then provides a specific example of using the Spring MVC framework to build a web application with the MVC pattern.
Java Servlets



Java ServletsBG Java EE Course This document provides an overview of Java servlets technology, including:
1. What Java servlets are and their main purposes and advantages such as portability, power, and integration with server APIs.
2. Key aspects of servlet architecture like the servlet lifecycle, the HttpServletRequest and HttpServletResponse objects, and how different HTTP methods map to servlet methods.
3. Examples of simple servlets that process parameters, maintain a session counter, and examples of deploying servlets in Eclipse IDE.
Client side scripting



Client side scriptingEleonora Ciceri The document discusses client-side scripting and scripts. It notes that scripts automate tasks that could otherwise be done manually. Scripts can be used in software applications, web pages, operating system shells, and more. Scripting languages make writing scripts easy and support interfaces to operating system facilities. Examples of scripting languages include JavaScript, Python, and Perl. The document then contrasts interpreters with compilers and compares how scripts and software code are developed and executed.
Express js



Express jsManav Prasad This document provides an overview of ExpressJS, a web application framework for Node.js. It discusses using Connect as a middleware framework to build HTTP servers, and how Express builds on Connect by adding functionality like routing, views, and content negotiation. It then covers basic Express app architecture, creating routes, using views with different template engines like Jade, passing data to views, and some advanced topics like cookies, sessions, and authentication.
Token Authentication in ASP.NET Core



Token Authentication in ASP.NET CoreStormpath Stormpath .NET Developer Evangelist, Nate Barbettini, presents Token Authentication with ASP.NET Core. Nate will explain how Token Authentication can be used to secure web applications built with ASP.NET Core, REST APIs, and 'unsafe' clients while supporting security best practices and even improving performance and scale.
Viewers also liked (20)
Authentication, authorization, accounting(aaa) slides



Authentication, authorization, accounting(aaa) slidesrahul kundu Authentication, authorization, and accounting (AAA) represent the major components of network access control and security. Authentication ensures a user's identity by requiring credentials like usernames and passwords. Authorization then determines the resources and services individual users have access to based on their authentication. Accounting tracks user activity for purposes like trend analysis, billing, auditing, and capacity planning. Together these three components (authentication, authorization, accounting) provide the foundation for secure network management and administration through identity verification and access control.
Difference between authentication and authorization in asp.net



Difference between authentication and authorization in asp.netUmar Ali Authentication verifies a user's identity by having them log in, while authorization determines which resources and pages the authenticated user has access to. For example, after authenticating normal and admin users on a website, authorization would prevent normal users from accessing admin pages. Authentication occurs before authorization and verifies the user, even if anonymously, while authorization checks the user's access rights after identity is confirmed.
Authentication Technologies



Authentication TechnologiesNicholas Davis This document provides an overview of authentication topics, including:
- Defining authentication and the three main electronic authentication factors: something you know, something you have, something you are.
- Discussing common authentication methods like usernames/passwords and their benefits and drawbacks.
- Covering other authentication methods such as one-time passwords, biometrics, digital certificates, and knowledge-based authentication.
- Identifying issues with initial credentialing and key concepts regarding the state of digital authentication.
RADIUS



RADIUSamogh_ubale RADIUS (Remote Authentication Dial In User Service) is a protocol that provides authentication, authorization and accounting functionality. It is commonly used for remote access to networks using modems or VPNs. The RADIUS protocol uses UDP and runs on ports 1812 and 1813. It operates on a client-server model where the client is typically a network access server and the server handles authentication requests from clients. RADIUS provides basic security through MD5 hashing of packets and a shared secret between clients and servers. However, it is vulnerable to sniffing and spoofing attacks.
AAA in a nutshell



AAA in a nutshellMohamed Daif This document discusses RADIUS, a protocol for authentication, authorization, and accounting. It describes key RADIUS features like its client/server model and extensibility. It explains how RADIUS operates, including how clients authenticate users and how servers can accept, reject, or challenge requests. The document also covers RADIUS accounting, shortcomings like lack of failover support, and how Diameter evolved from RADIUS to address some of these issues. It introduces SBR as a Juniper RADIUS product and describes its modular design and features like centralized management, proxy support, and 3GPP integration.
AAA & RADIUS Protocols



AAA & RADIUS ProtocolsPeter R. Egli Short overview of AAA and the RADIUS protocol.
The term AAA (say triple A) subsumes the functions used in network access to allow a user or a computer to access a network and use its resources.
AAA stands for Authentication (is the user authentic?), Authorization (what is the user allowed to do?) and Accounting (track resource usage by the user).
AAA is typically employed at network ingress points to control user's access to the network and resources.
The most prominent protocol for AAA is RADIUS (Remote Authentication Dial In User Service) which defines messages for opening and closing a network session and counting network usage (packet and byte count).
RADIUS usually works in conjunction with an LDAP server that stores the policies and user authorizations in a central repository.
Authentication(pswrd,token,certificate,biometric)



Authentication(pswrd,token,certificate,biometric)Ali Raw Authentication refers to confirming the identity of a person or entity. There are three main categories of authentication: what you know (e.g. passwords), what you have (e.g. tokens, certificates), and who you are (biometrics). Common types of authentication include password-based using user IDs and passwords, certificate-based using digital certificates, token-based using devices that generate random codes, and biometric-based using unique human characteristics like fingerprints. Each type involves validating identity by verifying identifying information against stored credentials through an authentication process.
Layer 7: Fine Grained Authorization for Web Services



Layer 7: Fine Grained Authorization for Web ServicesCA API Management This document discusses fine-grained authorization for web services. It begins by explaining the difference between fine-grained and coarse-grained authorization, and the challenges of implementing fine-grained authorization. It then discusses how to leverage existing identity infrastructure and use policy enforcement intermediaries to enforce entitlement policies. The document provides examples of how conditions can be used for fine-grained authorization requests. It also summarizes the Layer 7 SecureSpan solution, which uses a Policy Decision Point and Policy Enforcement Point to intercept requests and make authorization decisions based on policies.
Nevigation control in asp.net



Nevigation control in asp.netparallelminder This document discusses navigation controls in ASP.NET, including the use of menu, tree view and sitemap controls. It provides an overview of how to implement these controls for navigation and includes both source code view and output screen view.
Formbased authentication in asp.net



Formbased authentication in asp.netparallelminder The document discusses authentication modes in ASP.NET, including Windows, Forms, Passport, and None. Windows authentication uses IIS authentication, while Forms authentication redirects unauthorized requests to a login form. Passport authentication was deprecated by Microsoft in 2004. The document also covers how to implement form-based authentication in ASP.NET using Visual Studio by configuring authentication in web.config and adding login, access rules, and change password pages. Screenshots are provided of sample output pages for the form authentication process.
Restoring SharePoint Frontend server



Restoring SharePoint Frontend serverparallelminder 1. The SharePoint frontend server was missing the default SharePoint site on port 80 after installing CRM.
2. The document provides steps to restore the SharePoint site by running the configuration wizard, disconnecting from the existing farm, reconnecting to the farm and specifying the database and passphrase settings.
3. After completing the steps, the SharePoint 80 port site was restored and the administrator was able to access it again.
Asp.net membership anduserroles_ppt



Asp.net membership anduserroles_pptShivanand Arur This document provides an overview of membership and user roles in ASP.NET. It discusses authentication and authorization, and how membership providers and role providers allow ASP.NET applications to manage user accounts and roles. Membership providers like SQLMembershipProvider abstract the data source for user accounts. Role providers similarly manage user roles and role-based authorization. The document provides code samples for configuring these providers in ASP.NET applications.
Authentication and Authorization Architecture in the MEAN Stack



Authentication and Authorization Architecture in the MEAN StackFITC This document discusses authentication and authorization architecture in browser applications. It covers authenticating and authorizing clients to protect them from outsiders and each other. It discusses using cookies versus tokens to maintain state and different authentication providers like Passport. It also discusses authorizing by role, resource, or custom and setting up API routes and restricting access by object or post-query filtering. The client side uses Angular to handle login and check authorization status before accessing resources. Templates can show/hide elements based on authorization.
Master Pages In Asp.net



Master Pages In Asp.netparallelminder The document discusses master pages in ASP.NET. Master pages allow you to create a consistent layout for pages in an application. A single master page defines look, feel and standard behavior for all or groups of pages. The master page uses the @Master directive instead of the @Page directive. ContentPlaceHolder controls are included to define areas for content on individual pages. Master pages provide advantages like centralized common functionality, easy creation of reusable controls across pages, and fine-grained control over page layout.
Asp Net Advance Topics



Asp Net Advance TopicsAli Taki This document provides an overview of several advanced ASP.Net topics including localization, ASP.Net providers, validation controls, user controls, AJAX, caching, and LINQ. It discusses how to configure localization for different cultures and regions. It also explains the various membership, role, and profile providers and how to implement them to connect to data sources like SQL Server. Finally, it covers how to use and customize ASP.Net web parts and the different web parts modes.
The Three Musketeers (Authentication, Authorization, Accounting)



The Three Musketeers (Authentication, Authorization, Accounting)Sarah Conway The document discusses authentication, authorization and accounting (AAA) in PostgreSQL. It provides an overview of the AAA model and covers topics like authentication methods, user accounts, SSL configuration, and authorization files like pg_hba.conf and postgresql.conf. Specific configuration options for authentication timeouts, SSL certificates and other security settings are also examined.
Ch3 server controls



Ch3 server controlsMadhuri Kavade ASP.NET provides many server controls that generate HTML elements and simplify web development, including basic controls that map to HTML tags, more advanced controls that generate complex output, and specialized controls for tasks like validation, navigation, and data binding. Server controls inherit from classes in the .NET Framework and have properties and events that make them easier to work with compared to standard HTML elements. ASP.NET offers a variety of server controls to handle common tasks and interface elements on web forms.
Master pages ppt



Master pages pptIblesoft This document provides an overview and introduction to using master pages in ASP.NET. It discusses how master pages define common content and placeholders that content pages can fill with their own specific content. Master pages allow developers to build templates that contribute shared code and content to other pages on a site, enabling visual inheritance where content pages inherit appearance from master pages.
Radius server,PAP and CHAP Protocols



Radius server,PAP and CHAP ProtocolsDhananjay Aloorkar Brief information about Radius server,PAP and CHAP protocols which commonly stands for authentication, authorization and accounting.
Master pages



Master pagesteach4uin Master pages in ASP.NET allow you to create a consistent layout for all pages in an application. A master page defines the common elements like navigation, headers and footers. It contains content placeholders that content pages can fill. When a content page is requested, it merges with the associated master page to produce the output. This allows separation of design and content while ensuring a uniform appearance.
Ad
Similar to Authentication and Authorization in Asp.Net (20)
SharePoint Saturday The Conference DC - Are you who you say you are share poi...



SharePoint Saturday The Conference DC - Are you who you say you are share poi...Liam Cleary [MVP] Liam Cleary presents on authentication and authorization in SharePoint. He defines authentication as verifying a claim of identity, while authorization is verifying permissions. With claims-based authentication in SharePoint 2010, users are authenticated through security tokens from an identity provider and authorized via claims. The sign-in process involves the user being redirected to the identity provider, which issues a security token then passed to SharePoint. Real-world authentication requires considering external users, single sign-on, and cross-site authentication.
Y U No OAuth, Using Common Patterns to Secure Your Web Applications



Y U No OAuth, Using Common Patterns to Secure Your Web ApplicationsJason Robert Identity is one of the most critical components in all web applications. When not designed correctly, it can lead to security holes, code duplication, and maintenance nightmares. By leveraging technologies like OAuth 2.0, OpenID Connect, and JSON Web Tokens, you can build a robust security model that is scalable across all of your projects. In this session, we will take a dive into the most popular identity solutions that are available today and discuss how they can be utilized by your ASP.NET Core web applications.
Claim based authentaication



Claim based authentaicationSean Xiong Claim based authentication provides a solution to common problems with user authentication across multiple websites. It allows an identity provider like Google or Facebook to authenticate a user and issue tokens containing claims like user details. Applications can then request specific claims from an identity provider through a selector. The identity provider signs the token and applications can verify the signature to trust the identity provider. This avoids the need for each application to implement its own authentication and allows users to reuse their login from an identity provider on multiple applications.
Y U No OAuth?!?



Y U No OAuth?!?Jason Robert This document discusses authentication methods for securing web applications using identity providers. It provides an overview of the progression of user management from "roll your own" authentication to using OAuth 2.0 and OpenID Connect. Specific grant types like Authorization Code, Implicit Flow, and Hybrid Flow are described for authenticating different application types like native/legacy apps, server-side web apps, and single-page apps. Choosing an identity provider depends on factors like ecosystem, cloud provider, and control requirements. Popular options discussed include Active Directory, Auth0, Azure AD, Google, etc.
SharePoint Authentication And Authorization SPTechCon San Francisco



SharePoint Authentication And Authorization SPTechCon San FranciscoLiam Cleary [MVP] This document discusses authentication and authorization in SharePoint. It begins with an overview of security concepts like authentication, which verifies a claim of identity, and authorization, which verifies permissions. It then covers authentication options in SharePoint like Windows authentication and claims-based authentication using an identity provider. The document also discusses authorization and role providers, custom identity providers, and Azure Access Control Service. It emphasizes configuring authorization correctly after authentication and expecting security issues to arise.
Creating a Sign On with Open id connect



Creating a Sign On with Open id connectDerek Binkley The document discusses OpenID Connect, which is a standard for identity authentication built on OAuth 2.0. It describes the basic steps in OpenID Connect including the client requesting authentication, the authorization server authenticating the user and obtaining consent, returning an authorization code to the client, the client exchanging the code for an ID token and access token, and validating the ID token. It also addresses challenges with maintaining session state across a distributed architecture and strategies for addressing those challenges like embedding an iframe to check login status with the authorization server.
Securing SharePoint Apps with OAuth



Securing SharePoint Apps with OAuthKashif Imran This document discusses securing SharePoint apps using OAuth authentication. It provides an overview of app authentication in SharePoint 2013, including the use of OAuth and app principals. The key points covered are:
- SharePoint 2013 supports app authentication using OAuth or on-premise using security token service.
- Apps are assigned a principal that is used to manage app permissions separately from user permissions.
- The OAuth workflow involves apps obtaining access tokens from Azure Access Control Service to make calls to SharePoint on behalf of users.
- App principals must be registered both with SharePoint and ACS, and include a client ID, client secret, and redirect URL.
Authentication Models



Authentication ModelsRaj Chanchal This document provides an overview of authentication mechanisms on Windows, including Kerberos, Active Directory, digital certificates, biometrics, and .NET identity objects. It also discusses upcoming technologies like CardSpace and OpenID that aim to improve single sign-on authentication across multiple systems and online applications. The document concludes that with the evolution of open standards, the goal of a trustworthy single sign-on experience across the web is becoming closer to reality.
Security asp.net application



Security asp.net applicationZAIYAUL HAQUE This document provides an overview of security in ASP.NET applications. It discusses authentication, which verifies a user's identity, and authorization, which determines what authorized users are allowed to do. Authentication can be done through forms, Windows, or Passport authentication. Authorization uses roles to group users and access rules to allow or deny access to pages. Security settings are configured in the web.config file. The document also discusses SSL and how it encrypts data in transit for secure connections.
Introduction to Web Security



Introduction to Web SecurityKamil Lelonek Web security involves authentication, which verifies a user's identity, and authorization, which determines what resources a user can access. Traditionally, session-based authentication stored data on the server-side, but modern stateless authentication uses tokens passed in requests. Cookies and tokens maintain state at the client-side in a stateless manner. Libraries can help with authorization rules, roles, and multi-factor authentication.
Kerberos-PKI-Federated identity



Kerberos-PKI-Federated identityWAFAA AL SALMAN Kerberos is an authentication protocol that allows nodes communicating over an untrusted network to verify each other's identity. It uses symmetric encryption and a trusted third party called the Key Distribution Center (KDC) to authenticate users and services. The KDC issues credentials called tickets that grant access to trusted services across the network. Kerberos provides single sign-on by generating session keys that allow access to multiple services without re-authenticating. It is built into major operating systems and enables secure authentication over an insecure network like the internet.
AbedElilahElmahmoumP1.pptx



AbedElilahElmahmoumP1.pptxAbedElElahElMHMOOM A Perfect Presentation to Describe Authentication and Authorization and how it is used in Web Application Security. Definitions and implementation and full example of how it works.
NIC 2014 Modern Authentication for the Cloud Era



NIC 2014 Modern Authentication for the Cloud EraMorgan Simonsen 1. The document provides an introduction to modern authentication methods for cloud applications, focusing on claims-based identity.
2. Claims-based identity uses an abstraction layer where claims about a subject are issued in security tokens by an identity provider and can be verified by a relying party.
3. The document discusses examples of implementing claims-based identity on-premises using Active Directory Federation Services (ADFS) and in the cloud using Azure Active Directory (WAAD) as identity providers.
SharePoint Saturday Austin - Share point authentication and authorization



SharePoint Saturday Austin - Share point authentication and authorizationLiam Cleary [MVP] Liam Cleary gave a presentation on SharePoint authentication and authorization. He began with definitions of security, authentication, and authorization. He then discussed different authentication options in SharePoint like claims authentication and using membership and role providers. He also covered identity providers, authorization, and best practices like using Active Directory groups and claims-based authorization. The presentation provided an overview of key authentication and authorization concepts in SharePoint.
Combat Passwords on Post-Its with Multi-Factor Authentication for IBM i



Combat Passwords on Post-Its with Multi-Factor Authentication for IBM iPrecisely Stories of data breaches caused by stolen or guessed passwords have increased scrutiny around login practices. Requiring even more complex passwords is not recommended as users struggle to remember them – and write them down.
Multi-factor authentication has become best practice for strengthening login security and is now required by regulations such as the latest PCI Data Security Standard, the New York Department of Financial Services’ Cybersecurity Regulation (23 NYCRR 500) and more. Watch this webinar to learn how multi-factor authentication can be implemented for IBM i users to strengthen security and meet compliance requirements.
You’ll learn:
• What true multi-factor authentication really is
• Authentication options and tradeoffs
• Tips on implementing multi-factor authentication for IBM i
Microsoft Teams community call - February 2020



Microsoft Teams community call - February 2020Microsoft 365 Developer In this month's call, Loki Meyburg, Program Manager for Microsoft Teams discusses single sign-on (SS0) in Microsoft Teams, including:
-What is single sign-on (SSO)
-Authentication in 2019
-Single sign-on for Teams tabs today!
-Getting starting with SSO
Watch the recording here - https://youtu.be/91Sb5lz3STI
Web security



Web securityPadam Banthia Web-security with the help of J2EE(Java Enterprise Edition) Cryptography
Authentication of Internet
JDD2015: Security in the era of modern applications and services - Bolesław D...



JDD2015: Security in the era of modern applications and services - Bolesław D...PROIDEA This document discusses security challenges with modern applications and services and provides an overview of common standards and approaches. It outlines issues with traditional password-based authentication and session management in today's environment of mobile apps, microservices, and client-side applications. The document then introduces token-based security standards like SAML, JWT, OAuth2, and OpenID Connect, explaining how they address these issues through tokenization, delegation, and flexible authentication. It recommends relying on existing solutions like Keycloak that implement these standards to simplify security implementation and avoid potential vulnerabilities.
SCWCD : Secure web : CHAP : 7



SCWCD : Secure web : CHAP : 7Ben Abdallah Helmi 7.1 Identify which attribute scopes are thread-safe:
Local variables
Instance variables
Class variables
Request attributes
Session attributes
Context attributes
7.2 Identify correct statements about differences between the multithreaded and single-threaded servlet models.
7.3 Identify the interface used to declare that a servlet must use the single thread model.
SCWCD : Secure web



SCWCD : Secure webBen Abdallah Helmi
6.1 Identify correct descriptions or statements about the security issues:
Authentication
authorization
Data integrity
Auditing
Malicious code
Website attacks
6.2 Identify the deployment descriptor element names, and their structure, that declare the following:
A security constraint
A web resource
The login configuration
A security role
6.3 Given authentication type: BASIC, DIGEST, FORM, and CLIENT-CERT, identify the correct definition of its mechanism.
Ad
Recently uploaded (20)
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
Buckeye Dreamin' 2023: De-fogging Debug Logs



Buckeye Dreamin' 2023: De-fogging Debug LogsLynda Kane Slide Deck from Buckeye Dreamin' 2023: De-fogging Debug Logs which went over how to capture and read Salesforce Debug Logs
Automation Dreamin' 2022: Sharing Some Gratitude with Your Users



Automation Dreamin' 2022: Sharing Some Gratitude with Your UsersLynda Kane Slide Deck from Automation Dreamin'2022 presentation Sharing Some Gratitude with Your Users on creating a Flow to present a random statement of Gratitude to a User in Salesforce.
Big Data Analytics Quick Research Guide by Arthur Morgan



Big Data Analytics Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
"Rebranding for Growth", Anna Velykoivanenko



"Rebranding for Growth", Anna VelykoivanenkoFwdays Since there is no single formula for rebranding, this presentation will explore best practices for aligning business strategy and communication to achieve business goals.
Hands On: Create a Lightning Aura Component with force:RecordData



Hands On: Create a Lightning Aura Component with force:RecordDataLynda Kane Slide Deck from the 3/26/2020 virtual meeting of the Cleveland Developer Group presentation on creating a Lightning Aura Component using force:RecordData.
Drupalcamp Finland – Measuring Front-end Energy Consumption



Drupalcamp Finland – Measuring Front-end Energy ConsumptionExove How to measure web front-end energy consumption using Firefox Profiler. Presented in DrupalCamp Finland on April 25th, 2025.
Buckeye Dreamin 2024: Assessing and Resolving Technical Debt



Buckeye Dreamin 2024: Assessing and Resolving Technical DebtLynda Kane Slide Deck from Buckeye Dreamin' 2024 presentation Assessing and Resolving Technical Debt. Focused on identifying technical debt in Salesforce and working towards resolving it.
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...



AI EngineHost Review: Revolutionary USA Datacenter-Based Hosting with NVIDIA ...SOFTTECHHUB I started my online journey with several hosting services before stumbling upon Ai EngineHost. At first, the idea of paying one fee and getting lifetime access seemed too good to pass up. The platform is built on reliable US-based servers, ensuring your projects run at high speeds and remain safe. Let me take you step by step through its benefits and features as I explain why this hosting solution is a perfect fit for digital entrepreneurs.
Automation Dreamin': Capture User Feedback From Anywhere



Automation Dreamin': Capture User Feedback From AnywhereLynda Kane Slide Deck from Automation Dreamin' 2022 presentation Capture User Feedback from Anywhere
Network Security. Different aspects of Network Security.



Network Security. Different aspects of Network Security.gregtap1 Network Security. Different aspects of Network Security.
Dev Dives: Automate and orchestrate your processes with UiPath Maestro



Dev Dives: Automate and orchestrate your processes with UiPath MaestroUiPathCommunity This session is designed to equip developers with the skills needed to build mission-critical, end-to-end processes that seamlessly orchestrate agents, people, and robots.
📕 Here's what you can expect:
- Modeling: Build end-to-end processes using BPMN.
- Implementing: Integrate agentic tasks, RPA, APIs, and advanced decisioning into processes.
- Operating: Control process instances with rewind, replay, pause, and stop functions.
- Monitoring: Use dashboards and embedded analytics for real-time insights into process instances.
This webinar is a must-attend for developers looking to enhance their agentic automation skills and orchestrate robust, mission-critical processes.
👨🏫 Speaker:
Andrei Vintila, Principal Product Manager @UiPath
This session streamed live on April 29, 2025, 16:00 CET.
Check out all our upcoming Dev Dives sessions at https://community.uipath.com/dev-dives-automation-developer-2025/.
TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...



TrustArc Webinar: Consumer Expectations vs Corporate Realities on Data Broker...TrustArc Most consumers believe they’re making informed decisions about their personal data—adjusting privacy settings, blocking trackers, and opting out where they can. However, our new research reveals that while awareness is high, taking meaningful action is still lacking. On the corporate side, many organizations report strong policies for managing third-party data and consumer consent yet fall short when it comes to consistency, accountability and transparency.
This session will explore the research findings from TrustArc’s Privacy Pulse Survey, examining consumer attitudes toward personal data collection and practical suggestions for corporate practices around purchasing third-party data.
Attendees will learn:
- Consumer awareness around data brokers and what consumers are doing to limit data collection
- How businesses assess third-party vendors and their consent management operations
- Where business preparedness needs improvement
- What these trends mean for the future of privacy governance and public trust
This discussion is essential for privacy, risk, and compliance professionals who want to ground their strategies in current data and prepare for what’s next in the privacy landscape.
"Client Partnership — the Path to Exponential Growth for Companies Sized 50-5...



"Client Partnership — the Path to Exponential Growth for Companies Sized 50-5...Fwdays Why the "more leads, more sales" approach is not a silver bullet for a company.
Common symptoms of an ineffective Client Partnership (CP).
Key reasons why CP fails.
Step-by-step roadmap for building this function (processes, roles, metrics).
Business outcomes of CP implementation based on examples of companies sized 50-500.
How Can I use the AI Hype in my Business Context?



How Can I use the AI Hype in my Business Context?Daniel Lehner 𝙄𝙨 𝘼𝙄 𝙟𝙪𝙨𝙩 𝙝𝙮𝙥𝙚? 𝙊𝙧 𝙞𝙨 𝙞𝙩 𝙩𝙝𝙚 𝙜𝙖𝙢𝙚 𝙘𝙝𝙖𝙣𝙜𝙚𝙧 𝙮𝙤𝙪𝙧 𝙗𝙪𝙨𝙞𝙣𝙚𝙨𝙨 𝙣𝙚𝙚𝙙𝙨?
Everyone’s talking about AI but is anyone really using it to create real value?
Most companies want to leverage AI. Few know 𝗵𝗼𝘄.
✅ What exactly should you ask to find real AI opportunities?
✅ Which AI techniques actually fit your business?
✅ Is your data even ready for AI?
If you’re not sure, you’re not alone. This is a condensed version of the slides I presented at a Linkedin webinar for Tecnovy on 28.04.2025.
Leading AI Innovation As A Product Manager - Michael Jidael



Leading AI Innovation As A Product Manager - Michael JidaelMichael Jidael Unlike traditional product management, AI product leadership requires new mental models, collaborative approaches, and new measurement frameworks. This presentation breaks down how Product Managers can successfully lead AI Innovation in today's rapidly evolving technology landscape. Drawing from practical experience and industry best practices, I shared frameworks, approaches, and mindset shifts essential for product leaders navigating the unique challenges of AI product development.
In this deck, you'll discover:
- What AI leadership means for product managers
- The fundamental paradigm shift required for AI product development.
- A framework for identifying high-value AI opportunities for your products.
- How to transition from user stories to AI learning loops and hypothesis-driven development.
- The essential AI product management framework for defining, developing, and deploying intelligence.
- Technical and business metrics that matter in AI product development.
- Strategies for effective collaboration with data science and engineering teams.
- Framework for handling AI's probabilistic nature and setting stakeholder expectations.
- A real-world case study demonstrating these principles in action.
- Practical next steps to begin your AI product leadership journey.
This presentation is essential for Product Managers, aspiring PMs, product leaders, innovators, and anyone interested in understanding how to successfully build and manage AI-powered products from idea to impact. The key takeaway is that leading AI products is about creating capabilities (intelligence) that continuously improve and deliver increasing value over time.
Authentication and Authorization in Asp.Net
- 2. Topics – Authentication and Authorization 1. INTRODUCTION Why Security is important in today’s world? Different Ways to secure your Website / Application 2. What is IIS? and How to install and host an ASP.NET Website? 3. What is Authentication? 4. What is Authorization? 5. What is an Identity Object? 6. What is a Principal Object?
- 3. Topics – Authentication and Authorization • Different ways of Authentication : Forms Authentication. Using Cookies Cookieless Windows Authentication. Passport Authentication.
- 4. Introduction – Why Security is Important? 1. Security is one of the most important part of any Website or a Web Application. 2. Hackers are waiting out there for us and use various ways to exploit a website / web-application. 3. Hacker can attack in many ways. Brute Force Sniffers Spoofing Social Engineering SQL Injection
- 6. Introduction - Different Ways to Secure your Application Design your Application well. Encrypting the Data while storing. Input Validation. Forcing Users for Strong Passwords. Authentication and Authorization.
- 7. What is Internet Information Service(IIS)? • IIS is one of the most powerful Web Server developed by Microsoft to host ASP.NET Websites or Applications. • Its responsibility is to give a Response back to the Request sent by the Client. How does IIS work?
- 8. What is Authentication? • Dictionary meaning of “Authentication” is to “Check someone’s genuineness” • In ASP.NET – Authentication means the same. It is a process where you check a person’s credentials. • Example – Facebook, Yahoo, Gmail. What is Authorization? • Providing access to resource based on User’s role. • Authentication always preceeds Authorization
- 10. What is an Identity Object? • An Identity Object is an Object which stores information about an Authenticated User. • Contains 2 types of Objects “WindowsIdentity” and “GenericIdentity” What is a Principal Object? • A Principal Object is an Object that basically defines the roles of the Authenticated User. • Principal Object encapsulates the Identity Object.
- 12. Forms Authentication • Forms Authentication is nothing but a Cookie based Authentication where a Cookie is stored on the Client’s machine. • It makes use of a Custom Form to accept User’s Credentials. • Credentials are validated with the information stored in a specific source. • Advantage – – It is the simplest way of authenticating Users for websites and applications. – User does not have to login again and again to the same application.
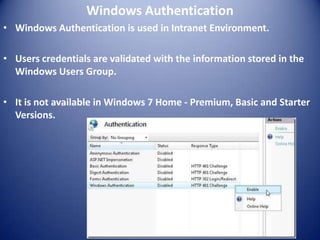
- 14. Windows Authentication • Windows Authentication is used in Intranet Environment. • Users credentials are validated with the information stored in the Windows Users Group. • It is not available in Windows 7 Home - Premium, Basic and Starter Versions.
- 15. Types of Windows Authentication 1. Anonymous Authentication – It does not authenticates the User. 2. Basic Authentication – User is authenticated and information is sent in BASE-64 Encoded format. 3. Digest Authentication – Works like Basic Authentication, but sends information in an encrypted format. 4. Integrated Windows Authentication – It either uses the NTLM or Kerberos type for authentication.
- 16. Working process of NTLM – Also know as Challenge-Response Process
- 17. Authentication using Kerberos Mechanism Authentication using Kerberos, contains 3 main components. Authentication Service (AS) Validates the Username and Password and sends a simple ticket. Ticket Granting Server (TGT) The Client sends the Ticket to the TGT, which sends a Service Ticket. Service Broker (SB) The SB, generates the Connection and creates Session for the User to use the Application
- 18. 2 1 1 2
- 19. Passport Authentication • User’s Credentials are authenticated using the Microsoft’s websites (Windows Live, Hotmail). • User’s are sent to the Microsoft’s Login page for authentication. • User is not authorized. • Developer does not require to create his own Custom Login Form. • For using the Passport Authentication service, you will have to download the .Net Passport SDK and will also need to register the Application using the .Net Service Manager.
- 20. THANK YOU
