Ad
AWS Security and Encryption
- 1. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Ric Harvey, Technical Developer Evangelist @ric__harvey AWS Security and Encryption Encrypting data at rest and in transit
- 2. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved.© 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Data classification
- 3. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Data classification Start of by classifying data based on sensitivity: • Public data = unencrypted, non-sensitive, available to everyone • Critical data = encrypted, not directly accessible from the internet, requires authorization and authentication Use resource tags to help define the policy: • “DataClassification=CRITICAL” • Integrate access with IAM policies Amazon Macie: • Macie can automatically discover, classify and protect sensitive data through machine learning
- 4. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Encrypt your data
- 5. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved.© 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Data in transit
- 6. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Data in transit AWS endpoints are HTTPS, but what can you do? • VPN connectivity to VPC • TLS application communication • ELB or CloudFront with ACM
- 7. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. • Open source SSL/TLS implementation • Small and auditable code base • Powering 100% ofTLS traffic in S3 • Automated formal verification of s2n provides critical security and safety assurance
- 8. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. AWS Certificate Manager • Protect and SecureYourWebsite • Get Certificates Easily • Managed Certificate Renewal • Secure Key Management • Centrally Manage Certificates on the AWS Cloud • Integrated with Other AWS Cloud Services • Import Third-Party Certificates • FREE!!!!
- 9. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved.© 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Data at rest
- 10. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Why encrypt? • Organizational policies • Industry or government regulations • Protect the privacy of your customers
- 11. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Key management infrastructure (KMI) Data EncryptionAlgorithm + Encryption Keys +
- 12. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. The key to encryption: Who controls the keys? • Model A:You control the encryption method and the KMI • Model B:You control the encryption algorithm and the key management but allow AWS to provide the key storage layer • Model C: AWS controls the encryption method and the entire KMI Customer Managed AWS Managed Encryption Method KMI Key Storage Key Management ModelA Encryption Method KMI Key Storage Key Management Model B Encryption Method KMI Key Storage Key Management ModelC
- 13. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved.© 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Model A You control the encryption method and the entire KMI
- 14. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon S3 • Encrypt data before you upload to S3 • Decrypt data in application as you download • Use open source or third party tools • Amazon S3 encryption Client
- 15. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon S3
- 16. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Elastic Block Store (EBS) • Block level storage network attached to an instance • Leverage most standard block level encryption tools: • Loop-AES, dm-crypt, etc • Leverage system level encryption tools: • eCryptfs, EncFs, etc • Provide the key from your own KMS • Caveat: data volumes only
- 17. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon RDS • RDS doesn’t expose the disk – transparent encryption methods don’t apply • Selective encryption of data fields in your application • Encrypted data is decrypted in your application for presentation • Use standard libs: • openSSL, Bouncy Castle, etc
- 18. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Partners
- 19. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Other services • AWS Storage Gateway • Amazon EMR
- 20. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved.© 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Model B You control the encryption algorithm and the key management but allow AWS to provide the key storage layer
- 21. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Hardware security module (HSM)
- 22. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. AWS CloudHSM • Fully managed service (Provisioning, HA, patching and backups) • Manage your own keys (FIPS 140-2 Level 3) • Integrates with industry standards • Export keys • Bring your own KMI (key rotation, access control policy)
- 23. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. AWS CloudHSM AWS CloudHSM AWS Administrator – manages the appliance You – control keys and crypto operations Amazon Virtual Private Cloud Help meet compliance requirements for data security by using a dedicated Hardware Security Module appliance with AWS. • Dedicated, single-tenant hardware device • Can be deployed as HA and load balanced • Customer use cases: • Oracle TDE • MS SQL Server TDE • Setup SSL connections • Digital Rights Management (DRM) • Document Signing
- 24. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved.© 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Model C AWS controls the encryption method and the entire KMI
- 25. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. AWS Key Management Service (KMS) • Provision and use keys with AWS Services • Send data to the service to encrypt and decrypt • Centralized access • Auditable • Integrates natively with other AWS services: • EBS, S3, Redshift • Low latency and Highly availability
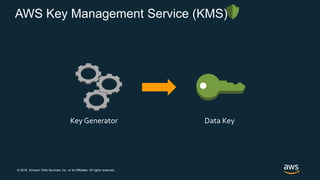
- 26. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. AWS Key Management Service (KMS) Key Generator Data Key
- 27. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. AWS Key Management Service (KMS) PlainText Data Data Key + Encrypted Data
- 28. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. AWS Key Management Service (KMS) Existing Key Encryption Key + Encrypted Data Key Data Key
- 29. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. AWS Key Management Service (KMS) +Encrypted Data Key Encrypted Data AWS Storage Services
- 30. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon S3 • Server-side encryption • Server-side encryption using customer provided keys (SSE-C) • Server-side encryption using KMS +
- 31. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Elastic Block Store (EBS) • Select a KMS key when creating the volume • Instance makes call to KMS • KMS uses master key to generate volume key • Key is stored in memory to encrypt and decrypt data • Volumes and Snapshots are encrypted
- 32. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon RDS • RDS can create encrypted EBS volumes too! • Full disk encryption for database volumes • Data stored at rest on the volume, database snapshots, automated backups, and read replicas are all encrypted
- 33. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. $aws ssmget-parameter –nameMyParameter { "Parameter": { "Type": "SecureString", "Name": "MyParameter", "Value": "AQECAHgnOkMROh5LaLXkA4j0+…… " } } $aws ssmget-parameter –nameMyParameter --with-decryption { "Parameter": { "Type": "SecureString", "Name": "MyParameter", "Value": ”secret_value" } } AWS Systems Manager Parameter Store aws ssm put-parameter --name MyParameter --value "secret_value" --type SecureString • Manage and store application secrets to be consumed by your application • Integrates with KMS
- 34. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Redshift • Amazon Redshift uses a four-tier, key-based architecture for encryption. The architecture consists of data encryption keys, a database key, a cluster key, and a master key • Data encryption keys encrypt data blocks in the cluster. Each data block is assigned a randomly-generated AES-256 key. These keys are encrypted by using the database key for the cluster • The cluster key encrypts the database key for the Amazon Redshift cluster • You can use AWS KMS, AWS CloudHSM, or an external hardware security module (HSM) to manage the clusterkey
- 35. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon EMR • S3DistCP moves large amounts of data from S3 into HDFS • Supports the ability to use SSE with S3 • No additional cost
- 36. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Other services • AWS Storage Gateway • Amazon Glacier
- 37. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Resources Amazon Macie – https://aws.amazon.com/macie/ AWS Cloud HSM – https://aws.amazon.com/cloudhsm/ AWS KMS - https://aws.amazon.com/kms/ S2n - https://github.com/awslabs/s2n AWS Certificate Manager: https://aws.amazon.com/certificate-manager/
- 38. © 2018, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Thank you! Ric Harvey, Technical Developer Evangelist @ric__harvey
Editor's Notes
- #5: Lots of options to give you full control and flexibility, from fully managed solutions to solutions where you bring your own key and encrypt data before its sent to AWS. s2n is the open source TLS implementation that’s now handling 100% of traffic for S3
- #6: Covered in depth in the Best practices webinar
- #7: All AWS service endpoints are HTTPS When looking at connectivity for management or data transfer to and from your VPC consider using a VPN to secure communications If you have applications that send data between them You should use TLS to secure the connection. AWS Certificate Manager = ACM can generate , deploy and manage certs for you You can also secure external communications into you applications via ELB/ALB and CloudFront and use ACM to manage the certificate. It’s also possible to bring your own SSL cert and key to use.
- #9: Elastic Load Balancers, Amazon CloudFront distributions, or APIs for Amazon API Gateway. AWS Certificate Manager also works with AWS Elastic Beanstalk and AWSCloudFormation to help you manage certificates and use them with yourapplications in the AWS Cloud.
- #11: Organizational policies, or industry or government regulations, might require the use of encryption at rest to protect your data. The flexible nature of Amazon Web Services(AWS) allows you to choose from a variety of different options that meet your needs.
- #12: Encryption requires three components Data to encrypt An encryption algorithm (such as AES) Encryption keys to be used in conjunction with the data and algorithm Choosing the right algorithm is important but storing the keys safely and securely and protecting them from unauthorized use is critical Managing keys is often done using KMI. It has two main components, a storage layer to protect the plain text keys and a management layer that authorizes key usage
- #13: AWS gives you flexibility for encryption and its important to understand who has access to what. This means you can use different methods depending on data classification and either leverage the tool set AWS offers or bring your own. Lets look at three different models of encryption on AWS Model A: Bring your own encryption, full control doesn’t have to exist inside AWS (onprem) Model B: You use cloudHSM to store the keys but in your software you control the management of the keys and the encryption method Model C: AWS handles the heavy lifting of KMI systems for you via AWS Key Management Service KMS
- #14: This physical location of the KMI and the encryption method can be outside of AWS or in an Amazon Elastic Compute Cloud (Amazon EC2) instance you own. The encryption method can be a combination of open-source tools, AWS SDKs, or third-party software and/or hardware. You have full control over the KMI and the encryption method, AWS has no access and can not perform encryption or decryption on your behalf. Lets look how you’d use this model with different AWS servcies
- #15: You encrypt data using any method you want before you upload it to amazon S3 Many languages include many cryptographic libs (bouncy castle and open SSL are two common ones) AWS also has an alternative: Amazon S3 encryption client which is an open source set of API’s embedded in the AWS SDK. It allows you to supply the key from your KMI to encrypt and decrypt the data. If you are using the AWS encryption client on premise AWS never has access to your Keys or unencrypted data.
- #16: You encrypt data using any method you want before you upload it to amazon S3 Many languages include many cryptographic libs (bouncy castle and open SSL are two common ones) AWS also has an alternative: Amazon S3 encryption client which is an open source set of API’s embedded in the AWS SDK. It allows you to supply the key from your KMI to encrypt and decrypt the data. If you are using the AWS encryption client on premise AWS never has access to your Keys or unencrypted data.
- #18: Consider how you want data queries to work Design your data so that range data for searches doesn’t look up encrypted data in order to get useful results
- #19: CipherCloud Voltage Security
- #22: An HSM is a dedicated storage and data processing device that performs cryptographic operations using keys on the device. An HSM typically provides tamper evidence, or resistance, to protect keys from unauthorized use. A software-based authorization layer controls who can administer the HSM and which users or applications can use which keys within the HSM. AWS CloudHSM – fully managed (patching, HA, backups) - $1.47 per hour you can manage your own encryption keys using FIPS 140-2 Level 3 validated HSMs flexibility to integrate with your applications using industry-standardAPIs, such as PKCS#11, Java Cryptography Extensions (JCE), and MicrosoftCryptoNG (CNG) libraries CloudHSM is also standards-compliant and enables you to export all of your keys to most other commercially-available HSMs
- #23: AWS CloudHSM – fully managed (patching, HA, backups) - $1.47 per hour you can manage your own encryption keys using FIPS 140-2 Level 3 validated HSMs flexibility to integrate with your applications using industry-standardAPIs, such as PKCS#11, Java Cryptography Extensions (JCE), and MicrosoftCryptoNG (CNG) libraries CloudHSM is also standards-compliant and enables you to export all of your keys to most other commercially-available HSMs A HSM can store key material and perform encryption and decryption
- #24: Apps must be able to access the CLoudHSM in the VPC For the highest level of HA we recommend deploying multiple CLoudHSM’s across AZ’s or with an on prem SafeNet Luna appliance. AWS manages and monitors the HSM appliances, but does not have access to the keys. In fact, if you lose the access to your credentials, AWS can’t help you recover your key material. You can recover from your own backup if you have a backup with the required credentials.
- #26: Master keys are provisioned like in HSM’s and are never exported from the service New!!!!! KMS is now fips 140-2 validated https://aws.amazon.com/blogs/security/aws-key-management-service-now-offers-fips-140-2-validated-cryptographic-modules-enabling-easier-adoption-of-the-service-for-regulated-workloads/
- #27: A data key is generated by the AWS service at the time you request your data to be encrypted.
- #28: Data key is used to encrypt your data
- #29: The data key is then encrypted with a key-encrypting key unique to the service storing your data.
- #30: The encrypted data key and encrypted data are then stored by the AWS storage service on your behalf The key-encrypting keys are storage and managed separately from the data and data keys Strict access controls are placed on encryption keys designed to prevent unauthorized use by AWS employees. When you decrypt the reverse or the above process is started,
- #31: Server-side encryption: set an API flag and data is encrypted by AWS before its written to disk, bonus is that keys are periodically rotated and managed by S3. NO EXTRA cost Server-side encryption customer keys: Use your own generated AES-256 key, S3 encrypts the data and store the encrypted file and deletes the key from its systems. You need to supply the key when retrieving the data. Server-side encryption with KMS: By selecvting a KMS master key KMS generates a data encryption key (example above). S3 encrypts the object by requesting the plaintext object key from KMS and once its finishes deletes the key. The encrypted object and encrypted data key are then stored in S3
- #32: Volume key is returned in plain text to ec2 instance