Ad
Basic buffer overflow part1
- 1. BUFFER OVERFLOWS IN DEPTH Mohsen Ahmadi My motto is : "Give a man an exploit and you make him a hacker for a day ; teach a man to exploit bugs and you make him a hacker for a lifetime."
- 2. DISCLAIMER If you’re someone that wants to build exploits to partake in illegal or immoral activity, please go elsewhere
- 3. ACKNOWLEDGMENTS • Nothing worthwhile in my life could be achieved without two very important people. A huge thank you to my beautiful fiancée, CMCM, for her inexhaustible support and immeasurable inspiration And also • My Mama, Without her continually showing that every life challenge is best confronted with a grin firmly planted from ear to ear, all obstacles would be so much greater.
- 4. DON’T BEAT AROUND THE BUSH • How do exploit writers build their exploits ? • What does the process of going from detecting a possible issue to building an actual working exploit look like ? • How can you use vulnerability information to build your own exploit ? • You saw some times exploits don’t work on special type of windows OS and languages. Why? • How you can make them work on other environments? • How you can build reliable exploits? • If these kind of questions is in your head, so your in right direction.
- 5. BUILD YOUR EXPLOITS FROM SCRATCH • Our target will be “Easy RM to MP3 Converter version 2.7.3.700” • Our target OS will be Windows XP SP3 English • Our attacker machine will be Kali Linux • Our today stack overflow exploit is based on file extension which we’ll made a malicious .m3u file and feed it into program & trigger our shell code • As a security researcher try to disclose your findings first to the vendor, give them the opportunity to fix things then disclose them publically on internet & exploit sites • or may be you’re a bad guys or want to to keep the Intel for yourself
- 6. VERIFY THE BUG & REPLICATE CRASH • First of all, let’s verify that the application does indeed crash when opening a mal formatted .m3u file • Note: you can find older version of application at: • http://oldapps.com/ • http://oldversion.com/ • http://exploit-db.com • Write our poc.py to make a .m3u mal formatted file which replicate the crash for us when we feed it in our buggy application • First try with buffer size of 10000 then 20000 last 30000 • As you can see program have a good exception handling mechanism
- 7. VERIFY THE BUG – AND SEE IF IT COULD BE INTERESTING • Obviously, not every application crash can lead to an exploitation • In many cases, an application crash will not lead to exploitation, But sometimes it does • What’s the meaning of exploitation? • you want the application to do something it was not intended to do • How we can make an application do something different? • by controlling its application flow (and redirect it to somewhere else) which is under control of a CPU register name IP or PC • What is IP or PC? • IP is Instruction pointer, PC is Program counter • which is a CPU register that contains a pointer to where the next instruction that needs to be executed is located
- 8. GAP ON APPLICATION FUNCTION CALL • Suppose an application calls a function with a parameter • Before going to the function, it saves the current location in the instruction pointer why? • knows where to return when the function completes • If you can modify the value in this pointer, and point it to a location in memory that contains your own piece of code • then you can change the application flow and make it execute something different • What is shell code? • The code that you want to be executed after controlling the flow is often referred to as “shell code”
- 9. WINDOWS APPLICATIONS MEMORY COMPONENTS • CC (code segment): instructions that the processor executes • DS (data segment): variables, dynamic buffers • SS (stack segment): pass data/arguments to functions, used as space for variables • Stack started from high memory addresses & with each PUSH instruction some data goes into Top of stack which is in size of PUSHed data length • Another instruction POP which fetch 4 bytes from Top of stack and put it into a Register • If you want access to elements in stack you should use ESP register which is a pointer to top of stack (lower memory addresses)
- 10. PUSH / POP • After a PUSH, ESP will point to a lower memory address • address is decremented with the size of the data that is pushed onto the stack, which is 4 bytes in case of addresses/pointers • Depending on the implementation, • Decrements usually happen before the item is placed on the stack • if ESP already points at the next free location in the stack, the decrement happens after placing data on the stack • After a POP, ESP points to a higher memory address • address is incremented by 4 bytes in case of addresses/pointers • Increments happen after an item is removed from the stack • *--ESP = value; // push • value = *ESP++; // pop
- 11. FRAME POINTER • When a function/subroutine is entered, a stack frame is created • What does it do? • keeps the parameters of the parent procedure together • pass arguments to the subroutine • Current location of stack can be accessed by ESP, but what about frame? • Current location of subroutine can be accessed by EBP (Base Pointer) • What is exactly function's stack frame? • is the area between the addresses contained in ESP, the stack pointer, and EBP, the frame pointer (base pointer in Intel terminology) • the caller must clean up the stack after the function call
- 12. INTEL X86 REGISTERS • EAX : used for performing calculations, and used to store return values from function calls. • EBX : used for storing some data • ECX : used for iterations, counts downward • EDX : It allows for more complex calculations (multiply, divide) by allowing extra data to be stored to facilitate those calculations • ESP : stack pointer • EBP : base pointer • ESI : holds location of input data, first element of an array • EDI : holds location of where result of data operation is stored, last element of an array • EIP : instruction pointer
- 13. PROCESS MEMORY • When an application is stared in a Win32 environment, a process is created and virtual memory is assigned to • User-land vs. kernel-land addresses • flat memory model • the CPU can directly/sequentially/linearly address all of the available memory locations, without having to use a segmentation/paging scheme • Besides VM when a process is created two other things is also will be create: • PEB • TEB
- 14. PEB / TEB • PEB contains all use-land parameters that are associated with process • Location main executable code • Pointer to loader data such as loaded modules/DLLs • Pointer to all information belongs to heap • TEB contains current state of live thread • Location PEB in memory • Pointer to stack of each thread • Pointer to first entry in SEH chain
- 15. MEMORY LAYOUT IN C • .text segment : of a program image / DLL is read-only, as it only contains the application code • .data segment : store global and static program variables, initialized global variables, strings, and other constants, it’s writeable • Heap segment : is used for the rest of the program variables, All of the memory in the heap is managed by allocator (and de allocator) algorithms The heap will grow towards a higher addresses
- 16. STACK (CONT.) • Stack work based on a data structure named LIFO • Stack is allocated by OS for each thread and cleared after threads finished • Stack size is fixed • Stack is pretty fast, but limited in size • Stack has two main instruction: • PUSH : put an item on the top of stack • POP : pull an item from top of stack • LIFO means that the most recent placed data(result of a PUSH instruction) is the first one that will be removed from the stack again(by a POP instruction)
- 17. STACK • Stack grows toward lower memory addresses by PUSH instruction • Stack contains local variables, function call, saved EIP, other info that does not need to be stored for a larger amount of time • What happens during a simple function call in stack? • Parameters send to function • EIP pushed onto top of stack • ESP pushed onto top of stack • Stack frame for buffers in function will be create • When function returns, POP EIP from stack and put it as Next Instruction in EIP
- 18. WHAT DOES APPLICATION EXACTLY DO? • This applications takes an argument (argv[1] and passes the argument to function do_something() • In that function, the argument is copied into a local variable that has a maximum of 128 bytes • What happens when buggy function call? • A new stack frame will be created, on top of the ‘parent’ stack • Before do_something() is called, a pointer to the argument(s) gets pushed to the stack
- 19. OVERFLOW FROM DEBUGGER POINT OF VIEW
- 20. STACK IN EACH PHASE
- 22. SHORT STORY • After the strcpy(), the function ends • The function epilog kicks in • Basically, it will move ESP back to the location where saved EIP was stored, and it will issue a RET • It will take the pointer (AAAA or 0×41414141 in our case, since it got overwritten), and will jump to that address. • So you control EIP
- 23. HOOK A DEBUGGER TO PROGRAM • state of the stack (and value of registers such as the instruction pointer, stack pointer etc.) • My preferred debugger for exploit development is ImmunityDBG • http://debugger.immunityinc.com/register.html • Or you can use ollyDBG, WinDBG • winDBG is default debugger which Microsoft packaged it in a bundle SDK, WDK • You can download it from: • http://www.microsoft.com/whdc/devtools/debugging/default.mspx • But it’s in command-line & for beginners it’s too soon
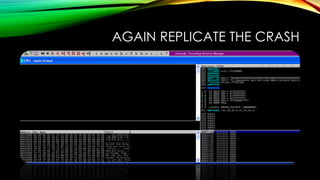
- 24. AGAIN REPLICATE THE CRASH
- 25. EIP OFFSET• We know that EIP is located somewhere between 20000 and 30000 bytes from the beginning of the buffer • We’ll create a file that contains 25000 A’s and another 5000 B’s • We have overwritten EIP with BBBB and we can also see our buffer in ESP • Metasploit has a nice tool to assist us with calculating the offset • ./pattern_create.rb 5000
- 26. CALCULATE OFFSET • Let’s use a second metasploit tool now, to calculate the exact length of the buffer before writing into EIP • That’s the buffer length needed to overwrite EIP. • So if you create a file with 25000+1094 A’s, and then add 4 B’s (42 42 42 42 in hex) EIP should contain 42 42 42 42. We also know that ESP points at data from our buffer, so we’ll add some C’s after overwriting EIP.
- 27. HOST THE SHELLCODE (CONT.) • In order to crash the application, we have written 26064 A’s into memory, we have written a new value into the saved EIP field (ret), and we have written a bunch of C’s. • When the application crashes, take a look at the registers and dump all of them • If you can see your buffer (either the A’s or the C’s) in one of the registers, then you may be able to replace those with shellcode and jump to that location • we would put our shellcode instead of the C’s and we tell EIP to go to the ESP address
- 28. HOST THE SHELLCODE (CONT.) • We don’t know if first ‘C’ in our buffer is the first one which we can see in ESP? • What we would conclude from this experiment? • ESP starts at the 5th character of our pattern, and not the first character • After the pattern string, we see “A’s”. These A’s most likely belong to the first part of the buffer (26101 A’s), so we may also be able to put our shellcode in the first part of the buffer (before overwriting RET) • What we have? • Control over EIP (execution flow) • an area where we can write our code • a register that directly points at our code, at address 0x000ff730
- 29. HOST THE SHELLCODE (CONT.) • Now what we want to to do? • build real shellcode • tell EIP to jump to the address of the start of the shellcode. We can do this by overwriting EIP with 0x000ff730 Our buffer will be : “A”*26064+”x30xf7x0fx00”+”x90”*25+”xcc”+”x90”*25
- 31. RELIABLE JUMP • we cannot just overwrite EIP with a direct memory address such as 000ff730 It’s not a good idea because it would not be reliable, and it’s not a good idea because it contains a ‘x00’ byte • What is reliable way? • find a function that will jump to that register • Using application DLLs (load modules in PEB) • the addresses used by these dll’s are pretty static • Search for all commands ‘jmp esp’ in all loaded modules
- 32. GET SHELLCODE AND FINALIZE THE EXPLOIT • We’ll use msfpayload for generating our shellcode
- 33. SHELL ENCODING
- 35. ANY QUESTION?!
- 36. THANK YOU


















![WHAT DOES APPLICATION EXACTLY DO?
• This applications takes an argument (argv[1] and passes the argument to
function do_something()
• In that function, the argument is copied into a local variable that has a
maximum of 128 bytes
• What happens when buggy function call?
• A new stack frame will be created, on top of the ‘parent’ stack
• Before do_something() is called, a pointer to the argument(s) gets pushed to the
stack](https://image.slidesharecdn.com/basicbufferoverflowpart1-170401115809/85/Basic-buffer-overflow-part1-18-320.jpg)