Basic network training2
- 1. Global Technology Services, ASEAN IBM Confidential | 2013 Basic Network Training Taywin Supha Sakon Baisopon
- 2. Global Technology Services IBM ConfidentialBasic Network Training2 DAY2 - Transport Protocol - Routing • Static route • Dynamic route - RIP - EIGRP - OSPF - Wireless LAN Agenda
- 3. Global Technology Services IBM Confidential Transport Protocol Basic Network Training3
- 4. Global Technology Services IBM Confidential Transport Protocol Set of rules - for exchange control message / data End-to-End Example protocols - User Datagram Protocol (UDP) - Transmission Control Protocol (TCP) Essential Switch Command Training4
- 5. Global Technology Services IBM Confidential Port and Address IP address is the end point of identifier - source / destination On same machine (same IP) - needs identifier for each application - multiple applications (e.g. 3 ftp sessions) “Port” - 16-bit number (65,356 ports) for each IP Basic Network Training5
- 6. Global Technology Services IBM Confidential Port and Address Basic Network Training6 IP address: 158.108.1.2 • Unique connection identifier • [source IP] + [source port] • [dest. IP] + [dest. port] Web #1 [158.108.1.2:80] Web #2 [158.108.1.2:8080] Ftp [158.108.1.2:24]
- 7. Global Technology Services IBM Confidential Port and Address Known destination IP Concern Issues - destination port ? - listen port ? Port numbers have the following assigned ranges: - Numbers below 1024 are considered well-known ports numbers. - Numbers above 1024 are dynamically assigned ports numbers. Basic Network Training7
- 8. Global Technology Services IBM Confidential Well-Known Ports Basic Network Training8
- 9. Global Technology Services IBM Confidential User Datagram Protocol (UDP) Characteristics - No error detection/recovery - No flow control - No checking for existing of destination Simple services Very useful protocol Basic Network Training9
- 10. Global Technology Services IBM Confidential UDP Message Format Basic Network Training10 Total length = UDP header+ Payload ≤ 216 bytes
- 11. Global Technology Services IBM Confidential Protocol that use UDP The protocols that use UDP include: - TFTP (Trivial File Transfer Protocol) - SNMP (Simple Network Management Protocol) - DHCP (Dynamic Host Control Protocol) - DNS (Domain Name System) Basic Network Training11
- 12. Global Technology Services IBM Confidential Transmission Control Protocol (TCP) Most popular/important in Internet Reliable transport protocol Connection-oriented - need establishment - [IP+source port] ↔ [IP+destination port] - guarantee delivery / error Basic Network Training12
- 13. Global Technology Services IBM Confidential TCP Message Format Basic Network Training13
- 14. Global Technology Services IBM Confidential Three-Way Handshake Basic Network Training14 TCP is a connection-oriented protocol. TCP requires connection establishment before data transfer begins
- 15. Global Technology Services IBM Confidential Flow Control Basic Network Training15 Flow control avoids the problem of a transmitting host overflowing the buffers in the receiving host. TCP provides the mechanism for flow control by allowing the sending and receiving host to communicate. The two hosts then establish a data-transfer rate that is agreeable to both.
- 16. Global Technology Services IBM Confidential Windowing Basic Network Training16 Windowing is a flow-control mechanism. Windowing requires that the source device receive an acknowledgment from the destination after transmitting a certain amount of data.
- 17. Global Technology Services IBM Confidential Windowing Basic Network Training17
- 18. Global Technology Services IBM Confidential Protocol that use TCP The protocols that use TCP include: - File Transfer Protocol (FTP) - Hypertext Transfer Protocol (HTTP) - Simple Mail Transfer Protocol (SMTP) - Post Office Protocol (POP3) - Telnet Basic Network Training18
- 19. Global Technology Services IBM Confidential Router as a Computer Describe the basic purpose of a router – Computers that specialize in sending packets over the data network – They are responsible for interconnecting networks by selecting the best path for a packet to travel and forwarding packets to their destination Routers are the network center – Routers generally have 2 connections: • WAN connection (Connection to ISP) • LAN connection
- 20. Global Technology Services IBM Confidential Router as a Computer Data is sent in form of packets between 2 end devices Routers are used to direct packet to its destination
- 21. Global Technology Services IBM Confidential Router as a Computer Routers examine a packet’s destination IP address and determine the best path by enlisting the aid of a routing table
- 22. Global Technology Services IBM Confidential Router as a Computer Router components and their functions: – CPU - Executes operating system instructions – Random access memory (RAM) - Contains the running copy of configuration file. Stores routing table. RAM contents lost when power is off. – Read-only memory (ROM) - Holds diagnostic software used when router is powered up. Stores the router’s bootstrap program. – Non-volatile RAM (NVRAM) - Stores startup configuration. This may include IP addresses (Routing protocol, Hostname of router). – Flash memory - Contains the operating system (Cisco IOS). – Interfaces - There exist multiple physical interfaces that are used to connect network. Examples of interface types: • Ethernet / fast Ethernet interfaces • Serial interfaces • Management interfaces
- 23. Global Technology Services IBM Confidential Router as a Computer Router components
- 24. Global Technology Services IBM Confidential Router as a Computer Major phases to the router boot-up process – Test router hardware • Power-On Self Test (POST) • Execute bootstrap loader – Locate & load Cisco IOS software • Locate IOS • Load IOS – Locate & load startup configuration file or enter setup mode • Bootstrap program looks for configuration file
- 25. Global Technology Services IBM Confidential Router as a Computer Verify the router boot-up process: – The show version command is used to view information about the router during the bootup process. Information includes: • Platform model number • Image name & IOS version • Bootstrap version stored in ROM • Image file name & where it was loaded from • Number & type of interfaces • Amount of NVRAM • Amount of flash • Configuration register
- 26. Global Technology Services IBM Confidential Router as a Computer
- 27. Global Technology Services IBM Confidential Router as a Computer Router Interface is a physical connector that enables a router to send or receive packets Each interface connects to a separate network Consist of socket or jack found on the outside of a router Types of router interfaces: – Ethernet – Fastethernet – Serial – DSL – ISDN – Cable
- 28. Global Technology Services IBM Confidential Router as a Computer Two major groups of Router Interfaces – LAN Interfaces • Are used to connect router to LAN network • Has a layer 2 MAC address • Can be assigned a Layer 3 IP address • Usually consist of an RJ-45 jack – WAN Interfaces • Are used to connect routers to external networks that interconnect LANs • Depending on the WAN technology, a layer 2 address may be used • Uses a layer 3 IP address
- 29. Global Technology Services IBM Confidential Router as a Computer Routers and the Network Layer – Routers use destination IP address to forward packets • The path a packet takes is determined after a router consults information in the routing table • After router determines the best path • Packet is encapsulated into a frame • Frame is then placed on network medium in form of Bits
- 30. Global Technology Services IBM Confidential Router as a Computer Routers Operate at Layers 1, 2 & 3 – Router receives a stream of encoded bits – Bits are decoded and passed to layer 2 – Router de-encapsulates the frame – Remaining packet passed up to layer 3 • Routing decision made at this layer by examining destination IP address – Packet is then re-encapsulated & sent out outbound interface
- 31. Global Technology Services IBM Confidential Configure Devices and Apply Addresses Implementing Basic Addressing Schemes When designing a new network or mapping an existing network you must provide the following information in the form of a document: – Topology drawing that Illustrates physical connectivity – Address table that provides the following information: • Device name • Interfaces used • IP addresses • Default gateway
- 32. Global Technology Services IBM Confidential Configure Devices and Apply Addresses Basic Router Configuration – A basic router configuration should contain the following: • Router name - Host name should be unique. • Banner - At a minimum, banner should warn against unauthorized use. • Passwords - Use strong passwords. • Interface configurations - Specify interface type, IP address and subnet mask. Describe purpose of interface. Issue no shutdown command. If DCE serial interface issue clock rate command. – After entering in the basic configuration the following tasks should be completed: • Verify basic configuration and router operations. • Save the changes on a router.
- 33. Global Technology Services IBM Confidential Configure Devices and Apply Addresses
- 34. Global Technology Services IBM Confidential Configure Devices and Apply Addresses Verify Basic Router Configuration – Issue the show running-config command – Save the basic router configuration by issuing the copy running-config startup- config command – Additional commands that will enable you to further verify router configuration are: • Show running-config - Displays configuration currently in RAM • Show startup-config - Displays configuration file NVRAM • Show IP route - Displays routing table • Show interfaces - Displays all interface configurations • Show IP int brief - Displays abbreviated interface configuration information
- 35. Global Technology Services IBM Confidential Routing Table Structure Routing Table is stored in ram and contains information about: – Directly connected networks - this occurs when a device is connected to another router interface – Remotely connected networks - this is a network that is not directly connected to a particular router – Detailed information about the networks include source of information, network address & subnet mask, and Ip address of next-hop router Show ip route command is used to view a routing table
- 36. Global Technology Services IBM Confidential Routing Table Structure Adding a connected network to the routing table – Router interfaces • Each router interface is a member of a different network • Activated using the no shutdown command • In order for static and dynamic routes to exist in routing table you must have directly connected networks
- 37. Global Technology Services IBM Confidential Routing Table Structure Static routes in the routing table – Includes: network address and subnet mask and IP address of next hop router or exit interface – Denoted with the code S in the routing table – Routing tables must contain directly connected networks used to connect remote networks before static or dynamic routing can be used When to use static routes – When network only consists of a few routers – Network is connected to internet only through one ISP – Hub & spoke topology is used on a large network
- 38. Global Technology Services IBM Confidential Routing Table Structure Connected and Static routes
- 39. Global Technology Services IBM Confidential Routing Table Structure Dynamic routing protocols – Used to add remote networks to a routing table – Are used to discover networks – Are used to update and maintain routing tables Automatic network discovery – Routers are able discover new networks by sharing routing table information
- 40. Global Technology Services IBM Confidential Routing Table Structure Maintaining routing tables – Dynamic routing protocols are used to share routing information with other router & to maintain and up date their own routing table IP routing protocols - example of routing protocols include: • RIP • IGRP • EIGRP • OSPF
- 41. Global Technology Services IBM Confidential Routing Table Structure Routing Table Principles – 3 principles regarding routing tables: • Every router makes its decisions alone, based on the information it has in its routing table • Different routing table may contain different information • A routing table can tell how to get to a destination but not how to get back
- 42. Global Technology Services IBM Confidential Routing Table Structure Effects of the 3 Routing Table Principles – Packets are forwarded through the network from one router to another, on a hop by hop basis – Packets can take path “X” to a destination but return via path “Y” (Asymmetric routing)
- 43. Global Technology Services IBM Confidential Router Paths and Packet Switching Internet Protocol (IP) packet format contains fields that provide information about the packet and the sending and receiving hosts Fields that are importance for CCNA students: – Destination IP address – Source IP address – Version & TTL – IP header length – Precedence & type of service – Packet length
- 44. Global Technology Services IBM Confidential Router Paths and Packet Switching MAC Layer Frame Format MAC Frames are also divided into fields - they include: – Preamble – Start of frame delimiter – Destination MAC address – Source MAC address – Type/length – Data and pad – Frame check sequence
- 45. Global Technology Services IBM Confidential Router Paths and Packet Switching A Metric is a numerical value used by routing protocols help determine the best path to a destination – The smaller the metric value the better the path 2 types of metrics used by routing protocols are: – Hop count - this is the number of routers a packet must travel through to get to its destination – Bandwidth - this is the “speed” of a link also known as the data capacity of a link
- 46. Global Technology Services IBM Confidential Router Paths and Packet Switching Equal cost metric is a condition where a router has multiple paths to the same destination that all have the same metric To solve this dilemma, a router will use Equal Cost Load Balancing - this means the router sends packets over the multiple exit interfaces listed in the routing table.
- 47. Global Technology Services IBM Confidential Router Paths and Packet Switching Path determination is a process used by a router to pick the best path to a destination One of 3 path determinations results from searching for the best path – Directly connected network – Remote network – No route determined
- 48. Global Technology Services IBM Confidential Router Paths and Packet Switching Switching Function of Router is the process used by a router to switch a packet from an incoming interface to an outgoing interface on the same router – A packet received by a router will do the following: • Strips off layer 2 headers • Examines destination IP address located in Layer 3 header to find best route to destination • Re-encapsulates layer 3 packet into layer 2 frame • Forwards frame out exit interface
- 49. Global Technology Services IBM Confidential Router Paths and Packet Switching As a packet travels from one networking device to another – The Source and Destination IP addresses NEVER change – The Source & Destination MAC addresses CHANGE as packet is forwarded from one router to the next – TTL field decrement by one until a value of zero is reached at which point router discards packet (prevents packets from endlessly traversing the network)
- 50. Global Technology Services IBM Confidential Router Paths and Packet Switching Path determination and switching function details. PC1 wants to send something to PC 2. – Step 1 - PC1 encapsulates packet into a frame - frame contains R1’s destination MAC address
- 51. Global Technology Services IBM Confidential Router Paths and Packet Switching Step 2 - R1 receives Ethernet frame – R1 sees that destination MAC address matches its own MAC – R1 then strips off Ethernet frame – R1 Examines destination IP – R1 consults routing table looking for destination IP – After finding destination IP in routing table, R1 now looks up next hop IP address – R1 re-encapsulates IP packet with a new Ethernet frame – R1 forwards Ethernet packet out Fa0/1 interface
- 52. Global Technology Services IBM Confidential Router Paths and Packet Switching
- 53. Global Technology Services IBM Confidential Router Paths and Packet Switching Step 3 - Packet arrives at R2 – R2 receives Ethernet frame – R2 sees that destination MAC address matches its own MAC – R2 then strips off Ethernet frame – R2 Examines destination IP – R2 consults routing table looking for destination IP – After finding destination IP in routing table, R2 now looks up next hop IP address – R2 re-encapsulates IP packet with a new data link frame – R2 forwards Ethernet packet out S0/0 interface
- 54. Global Technology Services IBM Confidential Router Paths and Packet Switching Step 4 - Packet arrives at R3 – R3 receives PPP frame – R3 then strips off PPP frame – R3 Examines destination IP – R3 consults routing table looking for destination IP – After finding destination IP in routing table, R3 is directly connected to destination via its fast Ethernet interface – R3 re-encapsulates IP packet with a new Ethernet frame – R3 forwards Ethernet packet out Fa0/0 interface Step 5 - IP packet arrives at PC2 - frame is decapsulated and processed by upper layer protocols
- 55. Global Technology Services IBM Confidential General Role of the Router Functions of a Router – Best Path Selections – Forwarding packets to destination Introducing the Topology – 3 1800 series routers connected via WAN links – Each router connected to a LAN represented by a switch and a PC
- 56. Global Technology Services IBM Confidential General Role of the Router Connections of a Router for WAN – A router has a DB-60 port that can support 5 different cabling standards Connections of a Router for Ethernet – 2 types of connectors can be used: Straight through and Cross-over • Straight through used to connect: – Switch-to-Router, Switch-to-PC, Router-to-Server, Hub-to-PC, Hub- to-Server • Cross-over used to connect: – Switch-to-Switch, PC-to-PC, Switch-to-Hub, Hub-to-Hub, Router-to- Router
- 57. Global Technology Services IBM Confidential Routing Table and CDP Protocol Purpose of the debug ip routing command – Allows you to view changes that the router performs when adding or removing routes. – Example: • R2#debug ip routing • IP routing debugging is on
- 58. Global Technology Services IBM Confidential Routing Table and CDP Protocol To configure an Ethernet interface – Example: • R2(config)#interface fastethernet 0/0 • R2(config-if)#ip address 172.16.1.1 255.255.255.0 • R2(config-if)#no shutdown
- 59. Global Technology Services IBM Confidential Routing Table and CDP Protocol When a router only has its interfaces configured & no other routing protocols are configured then: – The routing table contains only the directly connected networks – Only devices on the directly connected networks are reachable
- 60. Global Technology Services IBM Confidential Routing Table and CDP Protocol
- 61. Global Technology Services IBM Confidential Routing Table and CDP Protocol Checking each route in turn – The ping command is used to check end to end connectivity
- 62. Global Technology Services IBM Confidential Routing Table and CDP Protocol Purpose of CDP – A layer 2 cisco proprietary tool used to gather information about other directly connected Cisco devices. Concept of neighbors – 2 types of neighbors: • Layer 3 neighbors • Layer 2 neighbors
- 63. Global Technology Services IBM Confidential Routing Table and CDP Protocol CDP show commands – Show cdp neighbors command • Displays the following information: – Neighbor device ID – Local interface – Holdtime value, in seconds – Neighbor device capability code – Neighbor hardware platform – Neighbor remote port ID – Show cdp neighbors detail command • Useful in determining if an IP address configuration error
- 64. Global Technology Services IBM Confidential Routing Table and CDP Protocol Disabling CDP – To disable CDP globally use the following command • Router(config)#no cdp run
- 65. Global Technology Services IBM Confidential Static Routes with Exit Interfaces Purpose of a static route – A manually configured route used when routing from a network to a stub network
- 66. Global Technology Services IBM Confidential Static Routes with Exit Interfaces IP route command – To configure a static route use the following command: ip route – Example: • Router(config)# ip route network-address subnet-mask {ip-address | exit- interface }
- 67. Global Technology Services IBM Confidential Static Routes with Exit Interfaces Dissecting static route syntax – ip route - Static route command – 172.16.1.0 – Destination network address – 255.255.255.0 - Subnet mask of destination network – 172.16.2.2 - Serial 0/0/0 interface IP address on R2, which is the "next-hop" to this network
- 68. Global Technology Services IBM Confidential Static Routes with Exit Interfaces Configuring routes to 2 or more remote networks – Use the following commands for R1 • R1(config)#ip route 192.168.1.0 255.255.255.0 172.16.2.2 • R1(config)#ip route 192.168.2.0 255.255.255.0 172.16.2.2
- 69. Global Technology Services IBM Confidential Static Routes with Exit Interfaces Zinin’s 3 routing principles – Principle 1: “Every router makes its decision alone, based on the information it has in its own routing table.” – Principle 2: “The fact that one router has certain information in its routing table does not mean that other routers have the same information.” – Principle 3: “Routing information about a path from one network to another does not provide routing information about the reverse, or return path.”
- 70. Global Technology Services IBM Confidential Static Routes with Exit Interfaces Modifying Static routes – Existing static routes cannot be modified. The old static route must be deleted by placing no in front of the ip route – Example: • no ip route 192.168.2.0 255.255.255.0 172.16.2.2 – A new static route must be rewritten in the configuration
- 71. Global Technology Services IBM Confidential Static Routes with Exit Interfaces Verifying the Static Route Configuration – Use the following commands • Step 1 show running-config • Step 2 verify static route has been entered correctly • Step 3 show ip route • Step 4 verify route was configured in routing table • Step 5 issue ping command to verify packets can reach destination and that Return path is working
- 72. Global Technology Services IBM Confidential Static Routes with Exit Interfaces Ethernet interfaces and ARP – If a static route is configured on an Ethernet link and packet is sent to the next-hop router then… • The destination MAC address will be the address of the next hop’s Ethernet interface • This is found by the router consulting the ARP table • If an entry isn’t found then an ARP request will be sent out
- 73. Global Technology Services IBM Confidential Summary and Default Route Summarizing routes reduces the size of the routing table. Route summarization is the process of combining a number of static routes into a single static route.
- 74. Global Technology Services IBM Confidential Summary and Default Route Configuring a summary route – Step 1: Delete the current static route – Step 2: Configure the summary static route – Step 3: Verify the new static route
- 75. Global Technology Services IBM Confidential Summary and Default Route Default Static Route – This is a route that will match all packets. Stub routers that have a number of static routes all exiting the same interface are good candidates for a default route. • Like route summarization this will help reduce the size of the routing table. Configuring a default static route – Similar to configuring a static route. Except that destination IP address and subnet mask are all zeros. – Example: • Router(config)#ip route 0.0.0.0 0.0.0.0 [exit-interface | ip-address ].
- 76. Global Technology Services IBM Confidential Summary and Default Route Static routes and subnet masks – The routing table lookup process will use the most specific match when comparing destination IP address and subnet mask Default static routes and subnet masks – Since the subnet mask used on a default static route is 0.0.0.0 all packets will match
- 77. Global Technology Services IBM Confidential Static Routes and Packet Forwarding Packet forwarding with static routes (recall Zinin’s 3 routing principles) Router 1 – Packet arrives on R1’s Fastethernet 0/0 interface – R1 does not have a route to the destination network, 192.168.2.0/24 – R1 uses the default static route
- 78. Global Technology Services IBM Confidential Static Routes and Packet Forwarding Packet forwarding with static routes (recall Zinin’s 3 routing principles) Router 2 – The packet arrives on the Serial 0/0/0 interface on R2 – R2 has a static route to 192.168.2.0/24 out Serial0/0/1
- 79. Global Technology Services IBM Confidential Static Routes and Packet Forwarding Packet forwarding with static routes. (recall Zinin’s 3 routing principles) Router 3 – The packet arrives on the Serial0/0/1 interface on R3 – R3 has a connected route to 192.168.2.0/24 out Fastethernet 0/1
- 80. Global Technology Services IBM Confidential Static Routes and Packet Forwarding Troubleshooting a Missing Route Tools that can be used to isolate routing problems include: – Ping - tests end to end connectivity – Traceroute - used to discover all of the hops (routers) along the path between 2 points – Show IP route - used to display routing table & ascertain forwarding process – Show ip interface brief - used to show status of router interfaces – Show cdp neighbors detail - used to gather configuration information about directly connected neighbors
- 81. Global Technology Services IBM Confidential Static Routes and Packet Forwarding Solving a Missing Route Finding a missing or mis-configured route requires methodically using the correct tools – Start with PING - if ping fails then use traceroute to determine where packets are failing to arrive Issue: show ip route to examine routing table – If there is a problem with a mis-configured static route remove the static route then reconfigure the new static route
- 82. Global Technology Services IBM Confidential Dynamic Routing Protocols Function(s) of Dynamic Routing Protocols: – Dynamically share information between routers. – Automatically update routing table when topology changes. – Determine best path to a destination.
- 83. Global Technology Services IBM Confidential Dynamic Routing Protocols The purpose of a dynamic routing protocol is to: – Discover remote networks – Maintaining up-to-date routing information – Choosing the best path to destination networks – Ability to find a new best path if the current path is no longer available
- 84. Global Technology Services IBM Confidential Dynamic Routing Protocols Components of a routing protocol – Algorithm • In the case of a routing protocol algorithms are used for facilitating routing information and best path determination – Routing protocol messages • These are messages for discovering neighbors and exchange of routing information
- 85. Global Technology Services IBM Confidential Dynamic Routing Protocols Advantages of static routing – It can backup multiple interfaces/networks on a router – Easy to configure – No extra resources are needed – More secure Disadvantages of static routing – Network changes require manual reconfiguration – Does not scale well in large topologies
- 86. Global Technology Services IBM Confidential Classifying Routing Protocols Dynamic routing protocols are grouped according to characteristics. Examples include: – RIP – IGRP – EIGRP – OSPF – IS-IS – BGP Autonomous System is a group of routers under the control of a single authority.
- 87. Global Technology Services IBM Confidential Classifying Routing Protocols Types of routing protocols: – Interior Gateway Protocols (IGP) – Exterior Gateway Protocols (EGP)
- 88. Global Technology Services IBM Confidential Classifying Routing Protocols Interior Gateway Routing Protocols (IGP) – Used for routing inside an autonomous system & used to route within the individual networks themselves – Examples: RIP, EIGRP, OSPF Exterior Routing Protocols (EGP) – Used for routing between autonomous systems – Example: BGPv4
- 89. Global Technology Services IBM Confidential Classifying Routing Protocols IGP: Comparison of Distance Vector & Link State Routing Protocols - Distance vector – Routes are advertised as vectors - of distance & direction – Incomplete view of network - topology – Generally, periodic - updates - Link state – Complete view of network - topology is created – Updates are not - periodic -
- 90. Global Technology Services IBM Confidential Classifying Routing Protocols
- 91. Global Technology Services IBM Confidential Classifying Routing Protocols Classful routing protocols – Do NOT send subnet mask in routing updates Classless routing protocols – Do send subnet mask in routing updates
- 92. Global Technology Services IBM Confidential Classifying Routing Protocols Convergence is defined as when all routers’ routing tables are at a state of consistency
- 93. Global Technology Services IBM Confidential Routing Protocols Metrics Metric – A value used by a routing protocol to determine which routes are better than others
- 94. Global Technology Services IBM Confidential Routing Protocols Metrics Metrics used in IP routing protocols – Bandwidth – Cost – Delay – Hop count – Load – Reliability
- 95. Global Technology Services IBM Confidential Routing Protocols Metrics The Metric Field in the Routing Table Metric used for each routing protocol – RIP - hop count – IGRP & EIGRP - Bandwidth (used by default), Delay (used by default), Load, Reliability – IS-IS & OSPF - Cost, Bandwidth (Cisco’s implementation)
- 96. Global Technology Services IBM Confidential Routing Protocols Metrics Load balancing – This is the ability of a router to distribute packets among multiple same cost paths
- 97. Global Technology Services IBM Confidential Administrative Distance of a Route Purpose of a metric – It’s a calculated value used to determine the best path to a destination Purpose of Administrative Distance – It’s a numeric value that specifies the preference of a particular route
- 98. Global Technology Services IBM Confidential Administrative Distance of a Route Identifying the Administrative Distance (AD) in a routing table – It is the first number in the brackets in the routing table
- 99. Global Technology Services IBM Confidential Administrative Distance of a Route Dynamic Routing Protocols
- 100. Global Technology Services IBM Confidential Administrative Distance of a Route Directly connected routes – Have a default AD of 0 Static Routes – Administrative distance of a static route has a default value of 1
- 101. Global Technology Services IBM Confidential Administrative Distance of a Route Directly connected routes – Immediately appear in the routing table as soon as the interface is configured
- 102. Global Technology Services IBM Confidential RIPv1 RIP Message Format RIP header - divided into 3 fields – Command field – Version field – Must be zero Route Entry - composed of 3 fields – Address family identifier – IP address – Metric
- 103. Global Technology Services IBM Confidential RIPv1 RIP Operation – RIP uses 2 message types: • Request message – This is sent out on startup by each RIP enabled interface – Requests all RIP enabled neighbors to send routing table • Response message – Message sent to requesting router containing routing table
- 104. Global Technology Services IBM Confidential RIPv1 IP addresses initially divided into classes – Class A – Class B – Class C RIP is a classful routing protocol – Does not send subnet masks in routing updates
- 105. Global Technology Services IBM Confidential RIPv1 Administrative Distance – RIP’s default administrative distance is 120
- 106. Global Technology Services IBM Confidential Basic RIPv1 Configuration A typical topology suitable for use by RIPv1 includes: – Three router set up – No PCs attached to LANs – Use of 5 different IP subnets
- 107. Global Technology Services IBM Confidential Basic RIPv1 Configuration Router RIP Command – To enable RIP enter: • Router rip at the global configuration prompt • Prompt will look like R1(config-router)#
- 108. Global Technology Services IBM Confidential Basic RIPv1 Configuration Specifying Networks – Use the network command to: • Enable RIP on all interfaces that belong to this network • Advertise this network in RIP updates sent to other routers every 30 seconds
- 109. Global Technology Services IBM Confidential Verification and Troubleshooting Show ip Route To verify and troubleshoot routing – Use the following commands: • show ip route • show ip protocols • debug ip rip
- 110. Global Technology Services IBM Confidential Verification and Troubleshooting show ip protocols command – Displays routing protocol configured on router
- 111. Global Technology Services IBM Confidential Verification and Troubleshooting Debug ip rip command – Used to display RIP routing updates as they are happening
- 112. Global Technology Services IBM Confidential Verification and Troubleshooting Passive interface command – Used to prevent a router from sending updates through an interface – Example: • Router(config-router)#passive-interface interface-type interface-number
- 113. Global Technology Services IBM Confidential Verification and Troubleshooting Passive interfaces
- 114. Global Technology Services IBM Confidential Similarities between RIPv1 & RIPv2 – Use of timers to prevent routing loops – Use of split horizon or split horizon with poison reverse – Use of triggered updates – Maximum hop count of 15
- 115. Global Technology Services IBM Confidential EIGRP Roots of EIGRP: IGRP – Developed in 1985 to overcome RIPv1’s limited hop count – Distance vector routing protocol – Metrics used by IGRP • Bandwidth (used by default) • Delay (used by default) • Reliability • Load – Discontinued support starting with IOS 12.2(13)T & 12.2(R1s4)S
- 116. Global Technology Services IBM Confidential EIGRP EIGRP Message Format EIGRP Header – Data link frame header - contains source and destination MAC address – IP packet header - contains source & destination IP address – EIGRP packet header - contains AS number – Type/Length/Field - data portion of EIGRP message
- 117. Global Technology Services IBM Confidential EIGRP EIGRP packet header contains: – Opcode field – Autonomous System number EIGRP Parameters contain: – Weights – Hold time
- 118. Global Technology Services IBM Confidential EIGRP Reliable Transport Protocol (RTP) Purpose of RTP – Used by EIGRP to transmit and receive EIGRP packets Characteristics of RTP – Involves both reliable & unreliable delivery of EIGRP packet • Reliable delivery requires acknowledgment from destination • Unreliable delivery does not require an acknowledgement from destination – Packets can be sent • Unicast • Multicast – Using address 224.0.0.10
- 119. Global Technology Services IBM Confidential EIGRP EIGRP’s 5 Packet Types Hello packets – Used to discover & form adjacencies with neighbors
- 120. Global Technology Services IBM Confidential EIGRP Update packets – Used to propagate routing information
- 121. Global Technology Services IBM Confidential EIGRP Query packets – Used by DUAL for searching for networks – Can use Unicast or Multicast Reply packets – Reply packet – Can use Unicast only Acknowledgement packets – Used to acknowledge receipt of update, query & reply packets
- 122. Global Technology Services IBM Confidential EIGRP Purpose of Hello Protocol – To discover & establish adjacencies with neighbor routers Characteristics of hello protocol – Time interval for sending hello packet • Most networks it is every 5 seconds • Multipoint non broadcast multi- access networks – Unicast every 60 seconds – Holdtime • This is the maximum time router should wait before declaring a neighbor down • Default holdtime – 3 times hello interval
- 123. Global Technology Services IBM Confidential EIGRP EIGRP Bounded Updates – EIGRP only sends update when there is a change in route status – Partial update • A partial update includes only the route information that has changed – the whole routing table is NOT sent – Bounded update • When a route changes, only those devices that are impacted will be notified of the change – EIGRP’s use of partial bounded updates minimizes use of bandwidth
- 124. Global Technology Services IBM Confidential EIGRP Diffusing Update Algorithm (DUAL) – Purpose • EIGRP’s primary method for preventing routing loops – Advantage of using DUAL • Provides for fast convergence time by keeping a list of loop-free backup routes
- 125. Global Technology Services IBM Confidential EIGRP Administrative Distance (AD) – Defined as the trustworthiness of the source route EIGRP default administrative distances – Summary routes = 5 – Internal routes = 90 – Imported routes = 170
- 126. Global Technology Services IBM Confidential EIGRP Authentication – EIGRP can • Encrypt routing information • Authenticate routing information
- 127. Global Technology Services IBM Confidential Basic EIGRP Configuration Autonomous System (AS) & Process IDs – This is a collection of networks under the control of a single authority (reference RFC 1930) – AS Numbers are assigned by IANA – Entities needing AS numbers • ISP • Internet Backbone prodiers • Institutions connecting to other institutions using AS numbers
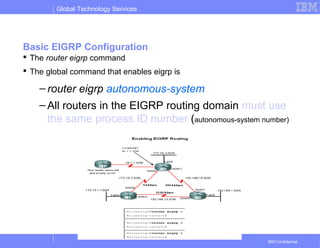
- 128. Global Technology Services IBM Confidential Basic EIGRP Configuration EIGRP autonomous system number actually functions as a process ID Process ID represents an instance of the routing protocol running on a router Example – Router(config)#router • eigrp autonomous-system
- 129. Global Technology Services IBM Confidential Basic EIGRP Configuration The router eigrp command The global command that enables eigrp is – router eigrp autonomous-system – All routers in the EIGRP routing domain must use the same process ID number (autonomous-system number)
- 130. Global Technology Services IBM Confidential Basic EIGRP Configuration The Network Command Functions of the network command – Enables interfaces to transmit & receive EIGRP updates – Includes network or subnet in EIGRP updates Example – Router(config-router)#network network-address
- 131. Global Technology Services IBM Confidential Basic EIGRP Configuration The network Command with a Wildcard Mask – This option is used when you want to configure EIGRP to advertise specific subnets – Example • Router(config-router)#network network-address [wildcard-mask]
- 132. Global Technology Services IBM Confidential Basic EIGRP Configuration Verifying EIGRP – EIGRP routers must establish adjacencies with their neighbors before any updates can be sent or received – Command used to view neighbor table and verify that EIGRP has established adjacencies with neighbors is • show ip eigrp neighbors
- 133. Global Technology Services IBM Confidential EIGRP The show ip protocols command is also used to verify that EIGRP is enabled
- 134. Global Technology Services IBM Confidential Basic EIGRP Configuration Examining the Routing Table – The show ip route command is also used to verify EIGRP – EIGRP routes are denoted in a routing table by the letter “D” – By default , EIGRP automatically summarizes routes at major network boundary
- 135. Global Technology Services IBM Confidential EIGRP Metric Calculation EIGRP Composite Metric & the K Values – EIGRP uses the following values in its composite metric • Bandwidth, delay, reliability, and load – The composite metric used by EIGRP • Formula used has values K1 K5 – K1 & K3 = 1 – all other K values = 0 -
- 136. Global Technology Services IBM Confidential EIGRP Metric Calculation Use the sh ip protocols command to verify the K values
- 137. Global Technology Services IBM Confidential Introduction to OSPF Background of OSPF – Began in 1987 – 1989 OSPFv1 released in RFC 1131 – This version was experimental & never deployed – 1991 OSPFv2 released in RFC 1247 – 1998 OSPFv2 updated in RFC 2328 – 1999 OSPFv3 published in RFC 2740
- 138. Global Technology Services IBM Confidential Introduction to OSPF OSPF Packet Types
- 139. Global Technology Services IBM Confidential Introduction to OSPF Hello Protocol OSPF Hello Packet – Purpose of Hello Packet • Discover OSPF neighbors & establish adjacencies • Advertise guidelines on which routers must agree to become neighbors • Used by multi-access networks to elect a designated router and a backup designated router
- 140. Global Technology Services IBM Confidential Introduction to OSPF Hello Packets continued – Contents of a Hello Packet router ID of transmitting router OSPF Hello Intervals – Usually multicast (224.0.0.5) – Sent every 30 seconds for NBMA segments OSPF Dead Intervals – This is the time that must transpire before the neighbor is considered down – Default time is 4 times the hello interval
- 141. Global Technology Services IBM Confidential Introduction to OSPF Hello protocol packets contain information that is used in electing – Designated Router (DR) • DR is responsible for updating all other OSPF routers – Backup Designated Router (BDR) • This router takes over DR’s responsibilities if DR fails
- 142. Global Technology Services IBM Confidential Introduction to OSPF OSPF Link-state Updates – Purpose of a Link State Update (LSU) • Used to deliver link state advertisements – Purpose of a Link State Advertisement (LSA) • Contains information about neighbors & path costs
- 143. Global Technology Services IBM Confidential Introduction to OSPF OSPF Algorithm OSPF routers build & maintain link-state database containing LSA received from other routers – Information found in database is utilized upon execution of Dijkstra SPF algorithm – SPF algorithm used to create SPF tree – SPF tree used to populate routing table
- 144. Global Technology Services IBM Confidential Introduction to OSPF Administrative Distance – Default Administrative Distance for OSPF is 110
- 145. Global Technology Services IBM Confidential Introduction to OSPF OSPF Authentication – Purpose is to encrypt & authenticate routing information – This is an interface specific configuration – Routers will only accept routing information from other routers that have been configured with the same password or authentication information
- 146. Global Technology Services IBM Confidential Basic OSPF Configuration Topology used for this chapter – Discontiguous IP addressing scheme – Since OSPF is a classless routing protocol the subnet mask is configured in
- 147. Global Technology Services IBM Confidential Basic OSPF Configuration The router ospf command To enable OSPF on a router use the following command – R1(config)#router ospf process-id – Process id • A locally significant number between 1 and 65535 • This means it does not have to match other OSPF routers
- 148. Global Technology Services IBM Confidential Basic OSPF Configuration OSPF network command – Requires entering: • network address • wildcard mask - the inverse of the subnet mask • area-id - area-id refers to the OSPF area – OSPF area is a group of routers that share link state information – Example: Router(config-router)#network network-address wildcard-ask area area-id
- 149. Global Technology Services IBM Confidential Basic OSPF Configuration Router ID – This is an IP address used to identify a router – 3 criteria for deriving the router ID • Use IP address configured with OSPF router-id command – Takes precedence over loopback and physical interface addresses • If router-id command not used then router chooses highest IP address of any loopback interfaces • If no loopback interfaces are configured then the highest IP address on any active interface is used
- 150. Global Technology Services IBM Confidential Basic OSPF Configuration OSPF Router ID Commands used to verify current router ID – Show ip protocols – Show ip ospf – Show ip ospf interface
- 151. Global Technology Services IBM Confidential Basic OSPF Configuration OSPF Router ID Router ID & Loopback addresses – Highest loopback address will be used as router ID if router-id command isn’t used – Advantage of using loopback address • The loopback interface cannot fail OSPF stability The OSPF router-id command – Introduced in IOS 12.0 – Command syntax • Router(config)#router ospfprocess-id • Router(config-router)#router-id ip-address Modifying the Router ID – Use the command Router#clear ip ospf process
- 152. Global Technology Services IBM Confidential Basic OSPF Configuration Verifying OSPF Use the show ip ospf command to verify & trouble shoot OSPF networks Command will display the following: – Neighbor adjacency • No adjacency indicated by – Neighboring router’s Router ID is not displayed – A state of full is not displayed • Consequence of no adjacency – No link state information exchanged – Inaccurate SPF trees & routing tables
- 153. Global Technology Services IBM Confidential Basic OSPF Configuration Command Description Show ip protocols Displays OSPF process ID, router ID, networks router is advertising & administrative distance Show ip ospf Displays OSPF process ID, router ID, OSPF area information & the last time SPF algorithm calculated Show ip ospf interface Displays hello interval and dead interval Verifying OSPF - Additional Commands
- 154. Global Technology Services IBM Confidential Basic OSPF Configuration Examining the routing table Use the show ip route command to display the routing table – An “O’ at the beginning of a route indicates that the router source is OSPF – Note OSPF does not automatically summarize at major network boundaries
- 155. Global Technology Services IBM Confidential OSPF Metric OSPF uses cost as the metric for determining the best route – The best route will have the lowest cost – Cost is based on bandwidth of an interface • Cost is calculated using the formula – 108 / bandwidth – Reference bandwidth • Defaults to 100Mbps • Can be modified using • Auto-cost reference-bandwidth command
- 156. Global Technology Services IBM Confidential OSPF Metric COST of an OSPF route – Is the accumulated value from one router to the next
- 157. Global Technology Services IBM Confidential Basic OSPF Configuration Modifying the Cost of a link Both sides of a serial link should be configured with the same bandwidth – Commands used to modify bandwidth value • Bandwidth command – Example: Router(config-if)#bandwidthbandwidth-kbps • ip ospf cost command – allows you to directly specify interface cost – Example: R1(config)#interface serial 0/0/0 – R1(config-if)#ip ospf cost 1562 -
- 158. Global Technology Services IBM Confidential OSPF and Multiaccess Networks Challenges in Multiaccess Networks OSPF defines five network types: – Point-to-point – Broadcast Multiaccess – Nonbroadcast Multiaccess (NBMA) – Point-to-multipoint – Virtual links
- 159. Global Technology Services IBM Confidential OSPF in Multiaccess Networks 2 challenges presented by multiaccess networks – Multiple adjacencies – Extensive LSA flooding
- 160. Global Technology Services IBM Confidential OSPF in Multiaccess Networks Extensive flooding of LSAs – For every LSA sent out there must be an acknowledgement of receipt sent back to transmitting router – Consequence: lots of bandwidth consumed and chaotic traffic
- 161. Global Technology Services IBM Confidential OSPF in Multiaccess Networks Solution to LSA flooding issue is the use of – Designated router (DR) – Backup designated router (BDR) DR & BDR selection – Routers are elected to send & receive LSA Sending & Receiving LSA – DR others send LSAs via multicast 224.0.0.6 to DR & BDR – DR forward LSA via multicast address 224.0.0.5 to all other routers
- 162. Global Technology Services IBM Confidential OSPF in Multiaccess Networks DR/BDR Election Process – DR/BDR elections DO NOT occur in point to point networks
- 163. Global Technology Services IBM Confidential OSPF in Multiaccess Networks DR/BDR elections will take place on multiaccess networks as shown below
- 164. Global Technology Services IBM Confidential OSPF in Multiaccess Networks Criteria for getting elected DR/BDR 1. DR: Router with the highest OSPF interface priority 2. BDR: Router with the second highest OSPF interface priority 3. If OSPF interface priorities are equal, the highest router ID is used to break the tie
- 165. Global Technology Services IBM Confidential OSPF in Multiaccess Networks OSPF Interface Priority Manipulating the DR/BDR election process continued – Use the ip ospf priority interface command. – Example:Router(config-if)#ip ospf priority {0 - 255} • Priority number range 0 to 255 – 0 means the router cannot become the DR or BDR – 1 is the default priority value
- 166. Global Technology Services IBM Confidential Wireless LAN Basic Network Training166
- 167. Global Technology Services IBM Confidential Wireless LAN Standards • 802.11 applies to wireless devices operating within a 1 to 2 Mbps range. • 802.11b transmission capabilities to 11 Mbps • 802.11a covers WLAN devices operating in the 5 GHZ transmission band and is capable of supplying data throughput of 54 Mbps • 802.11g provides the same throughout as 802.11a but with backwards compatibility for 802.11b devices Essential Switch Command Training167
- 168. Global Technology Services IBM Confidential Unlicensed Frequency Bands Basic Network Training168
- 169. Global Technology Services IBM Confidential Three Wireless Technologies Basic Network Training169
- 170. Global Technology Services IBM Confidential Wireless Devices Basic Network Training170
- 171. Global Technology Services IBM Confidential What is WLAN RF Technology? • Data send over the air wave. • Two-way radio communication (half duplex) • Same radio frequency for sending and receiving. • No licensing required for wireless products. Basic Network Training171
- 172. Global Technology Services IBM Confidential 2.4 GHz Channel Set Basic Network Training172
- 173. Global Technology Services IBM Confidential Channel- 2.4 GHz Basic Network Training173 • 11 Channels – each channel 22 MHz wide so there are 3 non- overlapping channels (1, 6, 11). • 3 access points can occupy same area.
- 174. Global Technology Services IBM Confidential WLAN Design Channel Reuse Basic Network Training174
- 175. Global Technology Services IBM Confidential Adaptive Rate Selection Basic Network Training175
- 176. Global Technology Services IBM Confidential WLAN Building Blocks • Service Set Identifier (SSID) is the name of a wireless local area network (WLAN). All wireless devices on a WLAN must employ the same SSID in ord er to communicate with each other. • Independent Basic Service Set (IBSS) Basic Network Training176
- 177. Global Technology Services IBM Confidential Wireless LAN Basic Network Training177
- 178. Global Technology Services IBM Confidential Roaming Basic Network Training178
- 179. Global Technology Services IBM Confidential Method of WEP Authentication • The first authentication process is the open system. This is an open connectivity standard in which only the SSID must match. • The second process is the shared key. This process requires the use of Wireless Equivalency Protocol (WEP) encryption. Basic Network Training179
- 180. Global Technology Services IBM Confidential Wireless Security Basic Network Training180 WPA WPA2 Enterprise mode Authentication: 802.1x/EAP Encryption: TKIP/MIC Authentication: 802.1x/EAP Encryption: AES-CCMP Personal mode Authentication: PSK Encryption: TKIP/MIC Authentication: PSK Encryption: AES-CCMP
- 181. Global Technology Services IBM Confidential Transport Protocol Basic Network Training181
- 182. Global Technology Services IBM ConfidentialEssential Switch Command Training182
- 183. Global Technology Services IBM Confidential Catalyst 2960 LED Indicators Basic Network Training183 1 SYST LED 5 Speed LED 2 RPS LED 6 PoE LED1 3 Status LED 7 Mode button 4 Duplex LED 8 Port LEDs
- 184. Global Technology Services IBM ConfidentialBasic Network Training184
- 185. Global Technology Services IBM ConfidentialBasic Network Training185
- 186. Global Technology Services IBM ConfidentialBasic Network Training186
- 187. Global Technology Services IBM ConfidentialBasic Network Training187
- 188. Global Technology Services IBM ConfidentialBasic Network Training188
- 189. Global Technology Services IBM ConfidentialBasic Network Training189
- 190. Global Technology Services IBM ConfidentialBasic Network Training190
- 191. Global Technology Services IBM ConfidentialBasic Network Training191
- 192. Global Technology Services IBM ConfidentialBasic Network Training192
- 193. Global Technology Services IBM ConfidentialBasic Network Training193
- 194. Global Technology Services IBM ConfidentialBasic Network Training194
- 195. Global Technology Services IBM ConfidentialBasic Network Training195
- 196. Global Technology Services IBM Confidential Starting on CISCO router Basic Network Training196
- 197. Global Technology Services IBM ConfidentialEssential Switch Command Training197
- 198. Global Technology Services IBM ConfidentialBasic Network Training198
- 199. Global Technology Services IBM ConfidentialBasic Network Training199
- 200. Global Technology Services IBM ConfidentialBasic Network Training200
- 201. Global Technology Services IBM ConfidentialBasic Network Training201
- 202. Global Technology Services IBM ConfidentialBasic Network Training202
- 203. Global Technology Services IBM ConfidentialBasic Network Training203
- 204. Global Technology Services IBM ConfidentialBasic Network Training204
- 205. Global Technology Services IBM ConfidentialBasic Network Training205
- 206. Global Technology Services IBM ConfidentialBasic Network Training206
- 207. Global Technology Services IBM ConfidentialBasic Network Training207
- 208. Global Technology Services IBM ConfidentialBasic Network Training208
- 209. Global Technology Services IBM Confidential Basic network command Base on CISCO product Basic Network Training209
- 210. Global Technology Services IBM Confidential Ping Command This command usually used to check active connection between computer or server. Ping sends out a packet to a designated network computer and measures its response time. The target or other computer will respond and return a signal to determine the quality of connection to other site or another computer. Essential Switch Command Training210
- 211. Global Technology Services IBM Confidential Traceroute (tracert) command Tracert (traceroute) is another command adopted from Unix system. Actually when you try to open facebook.com or google.com in your browser, you ask your computer to go to that address through hopping into a few router address. Basic Network Training211
- 212. Global Technology Services IBM Confidential Nslookup command Helps to diagnose the Domain Name System (DNS) infrastructure and comes with a number of sub-commands. Resolve name to IP Address, IP Address to name, and other records on domain name. Basic Network Training212
- 213. Global Technology Services IBM Confidential ipconfig command ipconfig used to display the TCP/IP network configuration values. To view switches for ipconfig use ipconfig /? command for help - /all : show all information for all TCP/IP network - /release : release specified adapter if you got IP address from DHCP server. - /renew : renew and ask for new IP address from DHCP server. - /flushdns : clear all DNS local cache - /displaydns : displaying what do you have in your local DNS cache. Basic Network Training213
- 214. Global Technology Services IBM Confidential ipconfig command Basic Network Training214
- 215. Global Technology Services IBM Confidential Basic network troubleshooting Base on CISCO product Basic Network Training215
- 216. Global Technology Services IBM Confidential Determining Route Source and Destination Basic Network Training216
- 217. Global Technology Services IBM Confidential Determining L2 and L3 Address Basic Network Training217
- 218. Global Technology Services IBM Confidential Introduction to Network Testing Basic Network Training218
- 219. Global Technology Services IBM Confidential Testing by OSI Layer 1 • Broken cables • Disconnected cables • Cables connected to the wrong ports • Intermittent cable connection • Wrong cables used for the task at hand (must use rollovers, crossover cables, and straight-through cables correctly) • Devices turned off Basic Network Training219
- 220. Global Technology Services IBM Confidential Testing by OSI Layer 2 • Improperly configured serial interfaces • Improperly configured Ethernet interfaces • Improper encapsulation set (HDLC is default for serial interfaces) • Improper clockrate settings on serial interfaces • Network interface card (NIC) problems Basic Network Training220
- 221. Global Technology Services IBM Confidential Testing by OSI Layer 3 • Routing protocol not enabled • Wrong routing protocol enabled • Incorrect IP addresses • Incorrect subnet masks Basic Network Training221
- 222. Global Technology Services IBM Confidential Layer 3 Troubleshooting Using Ping Basic Network Training222
- 223. Global Technology Services IBM Confidential Testing Application Layer Using Telnet Basic Network Training223
- 224. Global Technology Services IBM Confidential Troubleshooting Using Traceroute Basic Network Training224
- 225. Global Technology Services IBM ConfidentialBasic Network Training225 Communication Cable Technologies
- 226. Global Technology Services IBM ConfidentialBasic Network Training226 Cable Technology •Data communication is accomplished with electromagnetic energy •A combination of electrical and magnetic fields vibrating in relation to each other •Includes power, voice, radio waves, infrared light, visible light, ultraviolet light, and X, gamma, and cosmic rays.
- 227. Global Technology Services IBM Confidential Q & A Basic Network Training227






![Global Technology Services
IBM Confidential
Port and Address
Basic Network Training6
IP address: 158.108.1.2
• Unique connection identifier
• [source IP] + [source port]
• [dest. IP] + [dest. port]
Web #1 [158.108.1.2:80]
Web #2 [158.108.1.2:8080]
Ftp [158.108.1.2:24]](https://image.slidesharecdn.com/basicnetworktraining-day2-170707073440/85/Basic-network-training2-6-320.jpg)





![Global Technology Services
IBM Confidential
Transmission Control Protocol (TCP)
Most popular/important in Internet
Reliable transport protocol
Connection-oriented
- need establishment
- [IP+source port] ↔ [IP+destination port]
- guarantee delivery / error
Basic Network Training12](https://image.slidesharecdn.com/basicnetworktraining-day2-170707073440/85/Basic-network-training2-12-320.jpg)






























































![Global Technology Services
IBM Confidential
Summary and Default Route
Default Static Route
– This is a route that will match all packets. Stub routers that have a number of
static routes all exiting the same interface are good candidates for a default
route.
• Like route summarization this will help reduce the size of the routing
table.
Configuring a default static route
– Similar to configuring a static route. Except that destination IP address and
subnet mask are all zeros.
– Example:
• Router(config)#ip route 0.0.0.0 0.0.0.0 [exit-interface | ip-address ].](https://image.slidesharecdn.com/basicnetworktraining-day2-170707073440/85/Basic-network-training2-75-320.jpg)






















































![Global Technology Services
IBM Confidential
Basic EIGRP Configuration
The network Command with a Wildcard Mask
– This option is used when you want to configure
EIGRP to advertise specific subnets
– Example
• Router(config-router)#network network-address [wildcard-mask]](https://image.slidesharecdn.com/basicnetworktraining-day2-170707073440/85/Basic-network-training2-131-320.jpg)































































































