BlueHat v18 || Return of the kernel rootkit malware (on windows 10)
Matt Oh, Microsoft We are seeing new technique used everyday by malware. But, it is very hard to find any impressive techniques used in the wild. Recently there was huge buzz about Detrahere malware which used internally known issues with certificate signing in Windows 10 kernel driver. Even though the certificate check bypass technique itself is very interesting, also I found that the tactics used by the malware is more impressive. Even though the malware is mainly focused on Ad-hijacking functionality through Netfilter driver installation, but it also has rootkit ability through file system driver hooking. This feels like old days coming back with various new arsenals. The rootkit detects kernel debugging settings and will destroy the system when it finds one. The unpacking process can be very challenging job, too as it uses kernel driver image hollowing technique (something similar to process hollowing) to deobfuscate itself and run unpacked code. Our patchguard doesn't seem like triggering on this action, because all the sections are pre-allocated with execute permission already. Through this talk, I want to present various techniques used by this malware focusing on the kernel level obfuscation and anti-analysis tactics. This will give us new insights on how new Windows rootkit malware might look like in the future and how detecting them from security systems and detonation systems can be a challenge.























































Recommended




























































More Related Content
What's hot (20)










































Similar to BlueHat v18 || Return of the kernel rootkit malware (on windows 10) (20)










































More from BlueHat Security Conference (20)


























































Recently uploaded (20)






































BlueHat v18 || Return of the kernel rootkit malware (on windows 10)
- 1. Return of the kernel rootkit malware (on Windows 10) Matt Oh ([email protected]) Microsoft ‹#›
- 2. Whoami? • Microsoft WDATP research team • EDR, Blueteam • Special interests in new exploit and malware technique • Reverse engineer • Tearing down exploits, malware • Use the knowledge for better defense tactics/strategy • 1-day researcher • DarunGrim – opensource binary diffing tool ‹#›
- 3. Rootkits: Subverting the Windows Kernel • Rootkits: Subverting the Windows Kernel was published in 2005 • This is the reference for Windows rootkits • Many techniques were used by malware in the wild (DKOM, SSDT hooks) 2
- 4. Windows driver signing requirements https://docs.microsoft.com/en-us/windows-hardware/drivers/install/kernel-mode- code-signing-policy--windows-vista-and-later- • The Windows rootkit era ended with the release of Windows Vista, mainly due to Windows signing requirements and Kernel Patch Protection (aka KPP, PatchGuard) • Now malware authors need to overcome signing requirement • Only very advanced actors used rootkits so far (Equation, Duqu2, etc) 3
- 5. Zacinlo ad fraud operation • Bitdefender reported Zacinlo Ad Fraud operation in June of 2018 • Microsoft detection – Trojan:Win64/Detrahere • Seemed very usual until it mentioned “digitally signed rootkit” • The report focused on the ad fraud aspects of the malware • This presentation will focus on the rootkit aspects of the Zacinlo malware 4
- 6. Detrahere: low detections • It is believed that the threat has been running since early 2012 • According to VirusTotal, Malwarebytes identified the rootkit component of this threat as early as September 2017 • Low detection rates (6/67) until June 2018 5
- 7. Detrahere: Stealthiness+Persistency • The threat was under the radar for a long time • It infects other executable to propagate • The infected file will run the original executable after infecting victim machine • It installs a kernel driver that loads additional payload drivers from the hidden file system • The rootkit component blocks visibility into the related malware files using hidden file system • It registered it as a shutdown handler and also put itself in the early phase of driver loading order • Remediation can be challenging because it installs a shutdown handler to reinstall itself for persistency 6
- 8. Components Name Functionality Descriptions DriverProtect Shutdown handler registration Register a shutdown handler to regain persistence when the service is removed Hidden file system Hide file contents of the malware files Anti- analysis/debugging Block security products and analysts tools process launch and check for attached kernel debugger User-mode process USB file infection When a USB drive is connected, all PE files on it will be infected Network traffic injection Modify network traffic and inject Ad Fraud C&C Connect to C&C servers Netfilter2 Network traffic injection (driver) Provides driver-level support for network traffic injection which will be used by user-mode process udiskMgr Anti-remediation Blocks security products and analysts tools process launch Blocks some files creation (ex. FIXLISTS.TXT) used by a system recovery tool 7
- 10. USB file infection: threat delivery mechanism 9
- 11. USB file infection: threat delivery mechanism • Bitdefender report focused on one case where malware is delivered through fake VPN client. • In reality, the threat can spread through USB infections. When a user inserts a USB drive into the infected machine, the rootkit component will infect the PE files on the USB drive • Probably the VPN client found by Bitdefender might be infected in the first place. 10
- 12. File infection Verified: Signed Signing date: 2:45 AM 7/16/2016 Publisher: Microsoft Windows Company: Microsoft Corporation Description: Notepad Product: Microsoft« Windows« Operating System Prod version: 10.0.14393.0 File version: 10.0.14393.0 (rs1_release.160715-1616) MachineType: 64-bit Verified: Unsigned Link date: 5:24 AM 11/21/2017 Publisher: n/a Company: Microsoft Corporation Description: Notepad Product: Microsoft« Windows« Operating System Prod version: 10.0.14393.0 File version: 10.0.14393.0 (rs1_release.160715-1616) MachineType: 32-bit Infection The file becomes unsigned and the machine type becomes 32-bit because the malware only has a 32-bit infector. The original 64-bit file will run by this infector later after being extracted from resource section of the infected file. 11
- 13. Original PE file is inserted as a resource 12
- 14. Running original PE payload 13
- 15. Running the infected executable 14
- 17. Stolen and revoked certificate Countersignatures are missing – no way to verify validity of the certificate Stolen and revoked certificate 16
- 18. And expired • The certificate used for this driver was issued to “Handan City Congtai District LiKang Daily Goods Department” and was revoked • The malware performs system time change to sign this driver on-the- fly to generate expired certificate intentionally • For compatibility reasons, Windows will accept this certificate thinking it was previously generated for legacy driverExpired valid time range 17
- 19. Mitigations • Windows 10 S mode will prevent loading of these drivers • More strict driver requirements: • Windows Defender Application Control policy (Device Guard) • SecureBoot + HVCI (Memory Integrity) + VBS • More of anti-rootkit, exploit approach 18
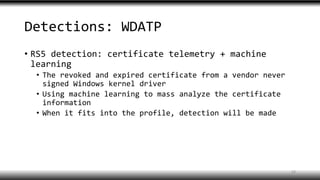
- 20. Detections: WDATP • RS5 detection: certificate telemetry + machine learning • The revoked and expired certificate from a vendor never signed Windows kernel driver • Using machine learning to mass analyze the certificate information • When it fits into the profile, detection will be made 19
- 21. Variant drivers • Searching VTI (Virus Total Intelligence) will return thousands of files with revoked certificate from “Handan City Congtai District LiKang Daily Goods Department” • These are all variants files generated by the infector 20
- 22. Variant drivers Variants are basically same except some padded bytes 21
- 23. Persistence 22
- 25. Shutdown handler registration • The DriverProtect component will register its main infection routine as a shutdown handler • With next reboot, the threat will be persistent • Traditional remediation fails because it doesn’t have control over this handler 24
- 26. Shutdown handler registration • This routine shows how the shutdown handler is registered • Remediation is extremely tricky • The system will be re-infected with each reboot of the system unless the resident kernel driver is unloaded 25
- 28. Group order list • The DriverProtect kernel module is in very early stages of the driver loading order • Will affect following security product related drivers detection attempts 27
- 29. Windows Defender Offline • Windows Defender Offline can provide offline remediation capability • When threat is detected, WDO will: • Guide through offline remediation process • Cut down the reloading of the rootkit modules 28
- 30. Windows Defender Offline • WDO will be able to remove the threat • WDO is a special Defender service where Defender runs scanning from clean OS image from WINRE (Windows Recovery) partition • Once system reboots, the kernel malicious drivers clean up itself, before any AV scans. 29
- 33. Anti-analysis tools • Process creation callback • Also CreateProcess callback is installed by DriverProtect to prevent some analysis tools • WorkItem queue is used to terminate the process from the callback 32
- 34. Anti-analysis tools • Image load callback • Usual analyst tools are prohibited from launching on the target system from LoadImage callback installed by DriverProtect module. 33
- 35. Anti-detection • Monitor Kernel Driver Loading • If security product related kernel drivers are loaded, it will nop out the entry point (xor eax, eax; ret) 34
- 36. Anti-detection • Disable ProcessCreateCallbacks and FLT callbacks • The anti-analysis code will enumerate PspCreateProcessNotifyCallback and FLT driver routines • If it is registered by a security products, it will put nop return instructions over the callback • The determination logic for security products include driver path comparison and driver PE header scanning for version information 35
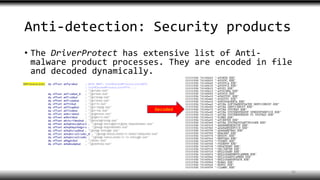
- 37. Anti-detection: Security products • The DriverProtect has extensive list of Anti- malware product processes. They are encoded in file and decoded dynamically. Decoded 36
- 38. Anti-detection: Security products • Scanning happens upon PE header • ReadFile -> ScanSecurityProductPatterns 37
- 39. Anti-debugging: Kernel debugger check • The rootkit checks whether kernel debugger is enabled • If enabled, it will call KeBugCheck. 38
- 40. Anti-analysis: obfuscations • Some rootkit kernel images are obfuscated in file (VMProtect) • When it is loaded in the kernel, it will unpack itself with original contents • It will not create new +RWX kernel memory, but will use existing section memory to de- obfuscate itself
- 41. Interfering with recovery tool • If any process tries to write contents to FIXLIST.TXT, the contents will be replaced with NULLs. • FIXLIST.TXT is used by Farbar Recovery Scan Tool 40
- 43. Hidden file system – loading components 42
- 45. Hidden file system • The DriverProtect module installs filter driver module to limit access to it’s components • The other core drivers (netfilter2 and udiskMgr) will be directly loaded from the DriverProtect itself • Security products’ operation in user-mode will have limited visibility into the core files because they are loaded from hidden file location 44
- 46. Hidden file system • DriverProtect will filter out access to protected files (malware components). • Security products run in userspace will fail to access malware components • The file contents inside protected storage is broken PE and will patched up when loaded into memory • It is implemented as filtering driver 45
- 47. Hidden file system • The rootkit drivers show missing files • When DriverProtect driver runs, it will: • Prevent access to the real file contents on the file system • The components reside on the hidden location have intentionally broken PE header • Act as a proxy and load the real contents from the protected storage after modifying the contents to be a valid PE file 46
- 48. WDATP visibility into driver loading • Even though the file never touches the file system, WDATP still detects the driver loading activity • DriverProtect protection only works against user-mode tools • WDATP sensor works in kernel level 47
- 49. Hidden file system • Through this Filter driver, the malware components are protected from investigations and false information on path is provided to the system. This will confuse security products and analysis tools. • Ex) C:windowssystem32sncibkt.exe image is actually C:WindowsSystem32spsatrmsncibkt.exe 48
- 52. Network traffic injection – netfilter2.sys There is a MITM kernel component that are written based upon commercial netfilter2 driver code from netfiltersdk.com 51
- 53. Netfilter2 – transparent proxy The filter driver provides functionality to inject packets on the fly. https://netfiltersdk.com/nfsdk.html 52
- 54. Network traffic injection – netfilter2.sys • The netfilter2.sys driver will be loaded with random names through hidden file system • It looks like this netfilter2.sys has close similarity to the NetFilterSDK.com provided one • We believe the attackers have access to the netfilter2.sys source code • The source code is commercially available 53
- 55. Adding new root certificate • The malicious user-mode component will add new root certificate • Used to hijack HTTPS sessions on the system 54 Installed root certificate
- 56. Conclusion • Detrahere (Zacinlo) is a threat that intercepts network traffic on a machine to inject ads • It has multiple self-protection mechanisms • Hidden file system to hide core drivers • Anti-analysis/debug/detection • It abuses feature in Windows driver verification to load kernel drivers using revoked certificate • WDATP has a good visibility into the detailed behaviors from the threat • WDO can be used to remediate the threat overriding persistence mechanism 55
- 57. C&C Servers IP Description 119.28.136.132:80 (gpt5.com) ASN: 132203 City: Beijing State: Beijing Country: China Organization: TENCENT CLOUD COMPUTING (BEIJING) CO. LTD. 104.193.88.77:80 (www.baidu.com) ASN: 55967 City: Cupertino State: California Country: United States Organization: BAIDU USA LLC 211.159.220.234:80 (adxco.cn) ASN: 45090 City: Beijing State: Beijing Country: China Organization: TENCENT CLOUD COMPUTING (BEIJING) CO. LTD. 119.28.137.94:8080 (www.user2best.com) ASN: 132203 City: Beijing State: Beijing Country: China Organization: TENCENT CLOUD COMPUTING (BEIJING) CO. LTD. 56
- 58. IOCs SHA1 SHA256 Filename Defender/descriptions deb585177e3fb4a935ca177260b02 714ab511353 5edeba23daabdeaaefea7d0ba3c15 3a8db07363a16c659cd120e3aa998 1f485b setup.exe Infector 954e690318768729b2e825622c883 b803fcb8433 bf57248c47bb1fc44bafad7bb257d 1e03e04128d847e5d895a05ec83ce a5bd27 C:WindowsSystem32spsatrmsncibk t.exe Trojan:Win64/Detrahere 94ec03ad3168a1b8bead60555f062 9b9186e00e6 8f0d55b54ddccf97ea798b40fc0a9 21f59010e5f02118251438ffcf79f 19847a C:windowssystem32sncibktsvc.exe NULL filled file 86218530d9043ff51e1d581a96e89 140820c8fcb d9fcc3554d657d68c94001438ebce 24842cec393ad97d3789a30c07426 1519ad C:WindowsSystem32spsatrmsncibk t.sys VirTool:Win64/Detrahere 0cbe4787b9a25bdbd8978e477d1d4 bcbe06ae341 fcbce0027b85069790b25b08444ac c4ebcb24567d6f461e63ca20f067e 7284e6 bfilps.sys Trojan:Win64/Detrahere.S 1cb1f70a120a61ee9c97d8f7c5ba6 e9ea8674e51 78ac863f8ccea5cd81a3361c203ba 792379735ba5a311d8607f1f1e587 2edb2d lsswzcgj.sys Trojan:Win64/Detrahere.S 9258b5d3a559ed02a4afaf0dd8079 820ebff3bc8 c86de08ac277735e62bef81a30685 36b43cccf8f278e6cd59e50a6a887 4c4973 rtdsuxz.exe Trojan:Win32/Detrahere.B !dr 69d209cb78d8e37de47bc697169f6 bb7de4fa738 69d209cb78d8e37de47bc697169f6 bb7de4fa738 notepad.exe Trojan:Win32/Detrahere.B !dr 57

