Binary trees1
Download as PPTX, PDF5 likes1,923 views
The document discusses binary trees and binary search trees. It defines key terms like root, child, parent, leaves, height, depth. It explains tree traversal methods like preorder, inorder and postorder. It then describes binary search trees and how they store keys in a way that searching, insertion and deletion can be done efficiently in O(log n) time. It discusses implementation of operations like search, insert, delete on BSTs. It introduces balanced binary search trees like AVL trees that ensure height is O(log n) through rotations during insertions and deletions.
1 of 48
Downloaded 189 times



































![InsertionFirst, insert the new key as a new leaf just as in ordinary binary search treeThen trace the path from the new leaf towards the root. For each node x encountered, check if heights of left(x) and right(x) differ by at most 1.If yes, proceed to parent(x). If not, restructure by doing either a single rotation or a double rotation [next slide].For insertion, once we perform a rotation at a node x, we won’t need to perform any rotation at any ancestor of x.](https://image.slidesharecdn.com/binarytrees1-110225222634-phpapp02/85/Binary-trees1-37-320.jpg)











Ad
Recommended
1.5 binary search tree



1.5 binary search treeKrish_ver2 1) Tree data structures involve nodes that can have zero or more child nodes and at most one parent node. Binary trees restrict nodes to having zero, one, or two children.
2) Binary search trees have the property that all left descendants of a node are less than the node's value and all right descendants are greater. This allows efficient searching in O(log n) time.
3) Common tree operations include insertion, deletion, and traversal. Balanced binary search trees use rotations to maintain balance during these operations.
Binary Tree in Data Structure



Binary Tree in Data StructureMeghaj Mallick Binary trees are a data structure where each node has at most two children. A binary tree node contains data and pointers to its left and right child nodes. Binary search trees are a type of binary tree where nodes are organized in a manner that allows for efficient searches, insertions, and deletions of nodes. The key operations on binary search trees are searching for a node, inserting a new node, and deleting an existing node through various algorithms that traverse the tree. Common traversals of binary trees include preorder, inorder, and postorder traversals.
AVL Tree Data Structure



AVL Tree Data StructureAfaq Mansoor Khan These slides are part of a full series of slides which covers almost all the basic concepts of data structures and algorithms.
Part 12
Binary Search Tree



Binary Search Treesagar yadav Binary search trees are binary trees where all left descendants of a node are less than the node's value and all right descendants are greater. This structure allows for efficient search, insertion, and deletion operations. The document provides definitions and examples of binary search tree properties and operations like creation, traversal, searching, insertion, deletion, and finding minimum and maximum values. Applications include dynamically maintaining a sorted dataset to enable efficient search, insertion, and deletion.
Binary search tree operations



Binary search tree operationsKamran Zafar This document discusses binary search trees (BST), including:
- The definition and properties of a BST, with nodes organized based on key values.
- Common BST operations like insertion, deletion, and searching in logarithmic time.
- Advantages of BSTs like efficient searching and working compared to arrays/lists.
- Applications of BSTs in databases, dictionaries, and evaluating expressions.
- Visual examples of searching, inserting, and deleting nodes from a BST.
Trees, Binary Search Tree, AVL Tree in Data Structures 



Trees, Binary Search Tree, AVL Tree in Data Structures Gurukul Kangri Vishwavidyalaya - Faculty of Engineering and Technology The document discusses various tree data structures and algorithms related to binary trees. It begins with an introduction to different types of binary trees such as strict binary trees, complete binary trees, and extended binary trees. It then covers tree traversal algorithms including preorder, inorder and postorder traversal. The document also discusses representations of binary trees using arrays and linked lists. Finally, it explains algorithms for operations on binary search trees such as searching, insertion, deletion and rebalancing through rotations in AVL trees.
B and B+ tree



B and B+ treeAshish Arun This PPT is all about the Tree basic on fundamentals of B and B+ Tree with it's Various (Search,Insert and Delete) Operations performed on it and their Examples...
Binary search trees



Binary search treesDhananjaysinh Jhala presentation on binary search trees for the subject analysis and design of algorithms, helpful to especially GTU students and computer and IT engineers
Binary tree 



Binary tree Rajendran Binary trees are a non-linear data structure where each node has zero, one, or two child nodes. They are commonly used to represent hierarchical relationships. A binary tree has a root node at the top with child nodes below it. Binary trees can be empty or consist of a root node and left and right subtrees, which are also binary trees. They allow for efficient search, insert, and delete operations and can be represented using arrays or linked lists.
Data Structure and Algorithms Binary Search Tree



Data Structure and Algorithms Binary Search TreeManishPrajapati78 Binary search trees (BSTs) are data structures that allow for efficient searching, insertion, and deletion. Nodes in a BST are organized so that all left descendants of a node are less than the node's value and all right descendants are greater. This property allows values to be found, inserted, or deleted in O(log n) time on average. Searching involves recursively checking if the target value is less than or greater than the current node's value. Insertion follows the search process and adds the new node in the appropriate place. Deletion handles three cases: removing a leaf, node with one child, or node with two children.
Expression trees



Expression treesSalman Vadsarya The document discusses rules and algorithms for converting between postfix notation and expression trees. It provides rules for building an expression tree from postfix notation by appending nodes based on the order in the postfix list. It also provides rules for generating prefix notation by traversing the expression tree from left to right and outputting the value of each node visited. Examples are given to demonstrate converting a postfix expression to an expression tree and then to prefix notation step-by-step.
Threaded Binary Tree.pptx



Threaded Binary Tree.pptxpavankumarjakkepalli A threaded binary tree is a variant of a binary tree that stores in-order predecessor and successor pointers instead of null pointers to facilitate faster traversal without recursion or an auxiliary stack. There are two types: single-threaded stores successor pointers only, and double-threaded stores both predecessor and successor pointers. This decreases wasted space from null pointers but makes insertion and deletion more complex. Advantages include optimal memory usage and faster traversal, while disadvantages include more complex insertion/deletion and slightly more memory usage for thread indicators.
Binary search tree(bst)



Binary search tree(bst)Hossain Md Shakhawat Definition of Binary Tree, Introduction to Binary Search Tree, Binary Tree Search Algorithm, Insert a value in BST, Delete a value from BST
Binary trees



Binary treesSimratpreet Singh A binary tree is composed of nodes, where each node contains a value and references (pointers) to a left and right child node. It may be empty or have a root node from which all other nodes are reachable through unique paths. Nodes without child nodes are leaves. The size is the number of nodes, and the depth is the longest path from the root node. Binary trees can be balanced or unbalanced. Common traversals that visit each node once include preorder, inorder, and postorder, which differ in when the root node is visited among its child subtrees.
Binary search tree



Binary search treeKousalya M A binary search tree is a node-based binary tree data structure where each node contains a key and a value. Each node has references to its left and right child nodes. Common operations on a binary search tree include search, insert, preorder traversal, inorder traversal, and postorder traversal. During a search, the tree is traversed starting from the root node by comparing keys to determine whether to search in the left or right subtree. Insertion adds new nodes at leaf locations. Traversals have different orders for visiting the left subtree, root, and right subtree.
Splay Tree



Splay TreeDr Sandeep Kumar Poonia The document describes splay trees, a type of self-adjusting binary search tree. Splay trees differ from other balanced binary search trees in that they do not explicitly rebalance after each insertion or deletion, but instead perform a process called "splaying" in which nodes are rotated to the root. This splaying process helps ensure search, insert, and delete operations take O(log n) amortized time. The document explains splaying operations like zig, zig-zig, and zig-zag that rotate nodes up the tree, and analyzes how these operations affect the tree's balance over time through a concept called the "rank" of the tree.
Red Black Tree Insertion & Deletion



Red Black Tree Insertion & DeletionInternational Institute of Information Technology (I²IT) The Red Black Tree is one of the most popular implementation of sets and dictionaries. A red-black tree is a binary search tree in which each node is coloured red or black.
Binomial Heap



Binomial HeapGoa App A binomial heap is a collection of binomial trees where each node has a key, trees are heap-ordered with minimum keys at the root, and trees have different sizes. Binomial heaps support creation, finding minimum keys, merging, insertion, removal of minimum keys, decreasing keys, and removal through keeping degree, child, sibling, and parent pointers at each node and combining trees of different sizes.
Binary tree



Binary treeVanitha Chandru This document discusses binary trees and various tree traversal algorithms. It defines what a binary tree is, including nodes, roots, leaves, and siblings. It explains different types of binary tree traversals including preorder, inorder, postorder, and level order. Pseudocode is provided for algorithms to perform inorder, preorder, and postorder traversals on a binary tree. Advantages of using trees are also listed.
Binary tree



Binary treeRajendran This document discusses binary trees. It defines a binary tree as a structure containing nodes with two self-referenced fields - a left reference and a right reference. Each node can have at most two child nodes. It provides examples of common binary tree terminology like root, internal nodes, leaves, siblings, depth, and height. It also describes different ways to represent binary trees using arrays or links and their tradeoffs. Complete binary trees are discussed as an optimal structure with height proportional to log of number of nodes.
Selection sort algorithm presentation, selection sort example using power point 



Selection sort algorithm presentation, selection sort example using power point University of Science and Technology Chitttagong The slide was made for computer science student who try to easily understand selection by a easy example. if u need u can watch it.
Red black tree



Red black treeDr Sandeep Kumar Poonia The document discusses algorithms and data structures, focusing on binary search trees (BSTs). It provides the following key points:
- BSTs are an important data structure for dynamic sets that can perform operations like search, insert, and delete in O(h) time where h is the height of the tree.
- Each node in a BST contains a key, and pointers to its left/right children and parent. The keys must satisfy the BST property - all keys in the left subtree are less than the node's key, and all keys in the right subtree are greater.
- Rotations are a basic operation used to restructure trees during insertions/deletions. They involve reassigning child
Circular linked list



Circular linked listchauhankapil This document provides an introduction to circular linked lists. It explains that a circular linked list is a variation of a linked list where the first element points to the last element, forming a loop. Both singly and doubly linked lists can be made circular by having the next pointer of the last node point to the first node, and in doubly linked lists the previous pointer of the first node points to the last node. Basic operations like insert, delete, and display are supported. Memory management involves the head pointer storing the address of the first node, and each node storing the address of the next node and last node.
Quick Sort , Merge Sort , Heap Sort



Quick Sort , Merge Sort , Heap SortMohammed Hussein The document discusses various sorting algorithms that use the divide-and-conquer approach, including quicksort, mergesort, and heapsort. It provides examples of how each algorithm works by recursively dividing problems into subproblems until a base case is reached. Code implementations and pseudocode are presented for key steps like partitioning arrays in quicksort, merging sorted subarrays in mergesort, and adding and removing elements from a heap data structure in heapsort. The algorithms are compared in terms of their time and space complexity and best uses.
Tree Traversal



Tree TraversalMd. Israil Fakir Traversal is a process to visit all the nodes of a tree and may print their values too. Because, all nodes are connected via edges (links) we always start from the root (head) node. That is, we cannot randomly access a node in a tree.
Queues



QueuesLovely Professional University Queue is an abstract data structure, somewhat similar to Stacks. Unlike stacks, a queue is open at both its ends. One end is always used to insert data (enqueue) and the other is used to remove data (dequeue). Queue follows First-In-First-Out methodology, i.e., the data item stored first will be accessed first.
Tree and Binary Search tree



Tree and Binary Search treeMuhazzab Chouhadry Tree and Binary search tree in data structure.
The complete explanation of working of trees and Binary Search Tree is given. It is discussed such a way that everyone can easily understand it. Trees have great role in the data structures.
Doubly & Circular Linked Lists



Doubly & Circular Linked ListsAfaq Mansoor Khan The document discusses double and circular linked lists. It covers inserting and deleting nodes from doubly linked lists and circular linked lists. Specifically, it describes how to insert nodes at different positions in a doubly linked list, such as at the front, after a given node, at the end, and before a given node. It also explains how to delete nodes from a doubly linked list. For circular linked lists, it outlines how to insert nodes in an empty list, at the beginning, at the end, and between nodes. It also provides the steps to delete nodes from a circular linked list.
Op-Amp Fundamental



Op-Amp FundamentalGaensan An operational amplifier, also known as an op-amp, is a high-gain differential amplifier with high input impedance and low output impedance. It has two input ports (inverting and non-inverting) and one output port. Op-amps can be used in single-ended or double-ended input configurations, with the output voltage determined by the difference or average of the input voltages multiplied by the differential or common-mode gain of the amplifier. Common applications include inverting and non-inverting amplifiers. Typical specifications for the LM741 op-amp include a voltage gain of 2 million, bandwidth of 6 kHz, and common mode rejection ratio of 90 dB.
Introduction to group theory



Introduction to group theorySt.Marys Chemistry Department This document discusses group theory and symmetry elements in chemistry. It defines symmetry elements as geometrical entities like points, lines, or planes that objects can be rotated or reflected around. Common symmetry operations are rotation, reflection, and inversion. Examples of symmetry elements include axes of rotation, planes of reflection, and centers of inversion. Several molecules like water, carbon dioxide, ethene, benzene, and ruthenium complexes are analyzed to identify their specific symmetry elements and point groups.
Ad
More Related Content
What's hot (20)
Binary tree 



Binary tree Rajendran Binary trees are a non-linear data structure where each node has zero, one, or two child nodes. They are commonly used to represent hierarchical relationships. A binary tree has a root node at the top with child nodes below it. Binary trees can be empty or consist of a root node and left and right subtrees, which are also binary trees. They allow for efficient search, insert, and delete operations and can be represented using arrays or linked lists.
Data Structure and Algorithms Binary Search Tree



Data Structure and Algorithms Binary Search TreeManishPrajapati78 Binary search trees (BSTs) are data structures that allow for efficient searching, insertion, and deletion. Nodes in a BST are organized so that all left descendants of a node are less than the node's value and all right descendants are greater. This property allows values to be found, inserted, or deleted in O(log n) time on average. Searching involves recursively checking if the target value is less than or greater than the current node's value. Insertion follows the search process and adds the new node in the appropriate place. Deletion handles three cases: removing a leaf, node with one child, or node with two children.
Expression trees



Expression treesSalman Vadsarya The document discusses rules and algorithms for converting between postfix notation and expression trees. It provides rules for building an expression tree from postfix notation by appending nodes based on the order in the postfix list. It also provides rules for generating prefix notation by traversing the expression tree from left to right and outputting the value of each node visited. Examples are given to demonstrate converting a postfix expression to an expression tree and then to prefix notation step-by-step.
Threaded Binary Tree.pptx



Threaded Binary Tree.pptxpavankumarjakkepalli A threaded binary tree is a variant of a binary tree that stores in-order predecessor and successor pointers instead of null pointers to facilitate faster traversal without recursion or an auxiliary stack. There are two types: single-threaded stores successor pointers only, and double-threaded stores both predecessor and successor pointers. This decreases wasted space from null pointers but makes insertion and deletion more complex. Advantages include optimal memory usage and faster traversal, while disadvantages include more complex insertion/deletion and slightly more memory usage for thread indicators.
Binary search tree(bst)



Binary search tree(bst)Hossain Md Shakhawat Definition of Binary Tree, Introduction to Binary Search Tree, Binary Tree Search Algorithm, Insert a value in BST, Delete a value from BST
Binary trees



Binary treesSimratpreet Singh A binary tree is composed of nodes, where each node contains a value and references (pointers) to a left and right child node. It may be empty or have a root node from which all other nodes are reachable through unique paths. Nodes without child nodes are leaves. The size is the number of nodes, and the depth is the longest path from the root node. Binary trees can be balanced or unbalanced. Common traversals that visit each node once include preorder, inorder, and postorder, which differ in when the root node is visited among its child subtrees.
Binary search tree



Binary search treeKousalya M A binary search tree is a node-based binary tree data structure where each node contains a key and a value. Each node has references to its left and right child nodes. Common operations on a binary search tree include search, insert, preorder traversal, inorder traversal, and postorder traversal. During a search, the tree is traversed starting from the root node by comparing keys to determine whether to search in the left or right subtree. Insertion adds new nodes at leaf locations. Traversals have different orders for visiting the left subtree, root, and right subtree.
Splay Tree



Splay TreeDr Sandeep Kumar Poonia The document describes splay trees, a type of self-adjusting binary search tree. Splay trees differ from other balanced binary search trees in that they do not explicitly rebalance after each insertion or deletion, but instead perform a process called "splaying" in which nodes are rotated to the root. This splaying process helps ensure search, insert, and delete operations take O(log n) amortized time. The document explains splaying operations like zig, zig-zig, and zig-zag that rotate nodes up the tree, and analyzes how these operations affect the tree's balance over time through a concept called the "rank" of the tree.
Red Black Tree Insertion & Deletion



Red Black Tree Insertion & DeletionInternational Institute of Information Technology (I²IT) The Red Black Tree is one of the most popular implementation of sets and dictionaries. A red-black tree is a binary search tree in which each node is coloured red or black.
Binomial Heap



Binomial HeapGoa App A binomial heap is a collection of binomial trees where each node has a key, trees are heap-ordered with minimum keys at the root, and trees have different sizes. Binomial heaps support creation, finding minimum keys, merging, insertion, removal of minimum keys, decreasing keys, and removal through keeping degree, child, sibling, and parent pointers at each node and combining trees of different sizes.
Binary tree



Binary treeVanitha Chandru This document discusses binary trees and various tree traversal algorithms. It defines what a binary tree is, including nodes, roots, leaves, and siblings. It explains different types of binary tree traversals including preorder, inorder, postorder, and level order. Pseudocode is provided for algorithms to perform inorder, preorder, and postorder traversals on a binary tree. Advantages of using trees are also listed.
Binary tree



Binary treeRajendran This document discusses binary trees. It defines a binary tree as a structure containing nodes with two self-referenced fields - a left reference and a right reference. Each node can have at most two child nodes. It provides examples of common binary tree terminology like root, internal nodes, leaves, siblings, depth, and height. It also describes different ways to represent binary trees using arrays or links and their tradeoffs. Complete binary trees are discussed as an optimal structure with height proportional to log of number of nodes.
Selection sort algorithm presentation, selection sort example using power point 



Selection sort algorithm presentation, selection sort example using power point University of Science and Technology Chitttagong The slide was made for computer science student who try to easily understand selection by a easy example. if u need u can watch it.
Red black tree



Red black treeDr Sandeep Kumar Poonia The document discusses algorithms and data structures, focusing on binary search trees (BSTs). It provides the following key points:
- BSTs are an important data structure for dynamic sets that can perform operations like search, insert, and delete in O(h) time where h is the height of the tree.
- Each node in a BST contains a key, and pointers to its left/right children and parent. The keys must satisfy the BST property - all keys in the left subtree are less than the node's key, and all keys in the right subtree are greater.
- Rotations are a basic operation used to restructure trees during insertions/deletions. They involve reassigning child
Circular linked list



Circular linked listchauhankapil This document provides an introduction to circular linked lists. It explains that a circular linked list is a variation of a linked list where the first element points to the last element, forming a loop. Both singly and doubly linked lists can be made circular by having the next pointer of the last node point to the first node, and in doubly linked lists the previous pointer of the first node points to the last node. Basic operations like insert, delete, and display are supported. Memory management involves the head pointer storing the address of the first node, and each node storing the address of the next node and last node.
Quick Sort , Merge Sort , Heap Sort



Quick Sort , Merge Sort , Heap SortMohammed Hussein The document discusses various sorting algorithms that use the divide-and-conquer approach, including quicksort, mergesort, and heapsort. It provides examples of how each algorithm works by recursively dividing problems into subproblems until a base case is reached. Code implementations and pseudocode are presented for key steps like partitioning arrays in quicksort, merging sorted subarrays in mergesort, and adding and removing elements from a heap data structure in heapsort. The algorithms are compared in terms of their time and space complexity and best uses.
Tree Traversal



Tree TraversalMd. Israil Fakir Traversal is a process to visit all the nodes of a tree and may print their values too. Because, all nodes are connected via edges (links) we always start from the root (head) node. That is, we cannot randomly access a node in a tree.
Queues



QueuesLovely Professional University Queue is an abstract data structure, somewhat similar to Stacks. Unlike stacks, a queue is open at both its ends. One end is always used to insert data (enqueue) and the other is used to remove data (dequeue). Queue follows First-In-First-Out methodology, i.e., the data item stored first will be accessed first.
Tree and Binary Search tree



Tree and Binary Search treeMuhazzab Chouhadry Tree and Binary search tree in data structure.
The complete explanation of working of trees and Binary Search Tree is given. It is discussed such a way that everyone can easily understand it. Trees have great role in the data structures.
Doubly & Circular Linked Lists



Doubly & Circular Linked ListsAfaq Mansoor Khan The document discusses double and circular linked lists. It covers inserting and deleting nodes from doubly linked lists and circular linked lists. Specifically, it describes how to insert nodes at different positions in a doubly linked list, such as at the front, after a given node, at the end, and before a given node. It also explains how to delete nodes from a doubly linked list. For circular linked lists, it outlines how to insert nodes in an empty list, at the beginning, at the end, and between nodes. It also provides the steps to delete nodes from a circular linked list.
Selection sort algorithm presentation, selection sort example using power point 



Selection sort algorithm presentation, selection sort example using power point University of Science and Technology Chitttagong
Viewers also liked (6)
Op-Amp Fundamental



Op-Amp FundamentalGaensan An operational amplifier, also known as an op-amp, is a high-gain differential amplifier with high input impedance and low output impedance. It has two input ports (inverting and non-inverting) and one output port. Op-amps can be used in single-ended or double-ended input configurations, with the output voltage determined by the difference or average of the input voltages multiplied by the differential or common-mode gain of the amplifier. Common applications include inverting and non-inverting amplifiers. Typical specifications for the LM741 op-amp include a voltage gain of 2 million, bandwidth of 6 kHz, and common mode rejection ratio of 90 dB.
Introduction to group theory



Introduction to group theorySt.Marys Chemistry Department This document discusses group theory and symmetry elements in chemistry. It defines symmetry elements as geometrical entities like points, lines, or planes that objects can be rotated or reflected around. Common symmetry operations are rotation, reflection, and inversion. Examples of symmetry elements include axes of rotation, planes of reflection, and centers of inversion. Several molecules like water, carbon dioxide, ethene, benzene, and ruthenium complexes are analyzed to identify their specific symmetry elements and point groups.
Data structures



Data structuresSaurabh Mishra This document provides an overview of data structures and algorithms. It introduces common linear data structures like stacks, queues, and linked lists. It discusses the need for abstract data types and different data types. It also covers implementing stacks as a linked list and common stack operations. Key applications of stacks include function call stacks which use a LIFO structure to remember the order of function calls and returns.
Operational Amplifier Part 1



Operational Amplifier Part 1Mukesh Tekwani Introduction to operational Amplifier. For A2 level physics (CIE). Discusses characteristics of op amp, inverting and non inverting amplifier, and voltage follower, and transfer characetristics, virtual earth , etc
Data Structure



Data StructureKarthikeyan A K The binary search is faster than the sequential search. The complexity of binary search is O(log n) whereas the complexity of a sequential search is O(n). Stacks are used to evaluate algebraic or arithmetic expressions using prefix or postfix notations. Heap sort involves creating a max heap from the array and then replacing the root with the last element and rebuilding the heap for the remaining elements, repeating this process to sort the entire array.
DATA STRUCTURES



DATA STRUCTURESbca2010 This document provides information about Dream Valley College for Girls Centre for Educational Excellence. It includes an index and presentation on data structures covering topics like arrays, linked lists, queues, trees, and graphs. The presentation was presented by Harish Sir and includes definitions, examples, and diagrams to explain each data structure concept.
Ad
Similar to Binary trees1 (20)
data structures module III & IV.pptx



data structures module III & IV.pptxrani marri Binary trees and binary search trees are discussed. Binary trees have nodes with at most two children, while binary search trees have the additional property that for every node, all keys in its left subtree are smaller than the node's key and all keys in its right subtree are larger. Common tree operations like searching, insertion, and deletion can be performed in O(log n) time on balanced binary search trees. AVL trees are discussed as one way to balance binary search trees through rotations.
Review session2



Review session2NEEDY12345 The document discusses binary search trees and their properties. It explains that a binary search tree is a binary tree where every node's left subtree contains values less than the node's value and the right subtree contains greater values. Operations like search, insert, delete can be done in O(h) time where h is the height of the tree. The height is O(log n) for balanced trees but can be O(n) for unbalanced trees. The document also provides examples of using a binary search tree to sort a set of numbers in O(n log n) time by building the BST and doing an inorder traversal.
lecture 13



lecture 13sajinsc The document discusses red-black trees, which are binary search trees augmented with node colors to guarantee a height of O(log n). It describes the properties that red-black trees must satisfy, including that every node is red or black, leaves are black, and if a node is red its children are black. It then proves that these properties ensure the height is O(log n) by showing a subtree has at least 2^bh - 1 nodes, where bh is the black-height. Finally, it notes that common operations like search, insert and delete run in O(log n) time on red-black trees.
Red Black Trees



Red Black TreesVarun Mahajan The document discusses red-black trees, which are self-balancing binary search trees. It describes the basic operations on dynamic sets like search, insert, and delete. It then explains the properties and structure of red-black trees, including that they ensure height is O(log n) through coloring nodes red or black. The insert and fixup algorithms are shown to maintain these properties and run in O(log n) time, providing efficient search tree operations.
Skiena algorithm 2007 lecture05 dictionary data structure trees



Skiena algorithm 2007 lecture05 dictionary data structure treeszukun This document discusses dictionaries and binary search trees. It describes the basic operations for dictionaries like search, insert, delete, min, max, successor, and predecessor. It then explains how to implement these operations using binary search trees. The time complexity of each operation is O(h) where h is the height of the tree, which can be O(lg n) for a balanced tree but O(n) in the worst case for an unbalanced tree. Balanced search trees like red-black trees and AVL trees help guarantee O(lg n) time for operations.
Binary Search Tree



Binary Search TreeAdityaK92 The document defines common tree terminology and describes trees and binary trees. It discusses tree traversal methods including preorder, inorder, and postorder traversal. It also covers binary search trees, including their representation, properties, and common operations like searching, insertion, deletion, finding the minimum/maximum, and finding predecessors and successors. Key operations on binary search trees like searching, insertion, and deletion run in O(h) time where h is the tree height.
Trees



TreesAnkit Sharma The document discusses binary search trees and their operations. It covers definitions of binary search trees, how to search, find the minimum/maximum keys, insert and delete nodes. It then discusses AVL trees, which are self-balancing binary search trees where the heights of the left and right subtrees of every node differ by at most one. It explains rotations needed during insertions and deletions to maintain balance in AVL trees.
Binary Search Tree



Binary Search TreeZafar Ayub A binary search tree (BST) is a binary tree where the value of each node is greater than all values in its left subtree and less than all values in its right subtree. This property allows efficient search, insert, and delete operations in O(logN) time. To search a BST, the algorithm starts at the root and recursively checks if the target value is equal to, less than, or greater than the value of the current node to determine if it proceeds to the left or right child. Insertion finds the appropriate position to add a new node by recursively comparing its value to ancestors' values.
Data structures and Algorithm analysis_Lecture4.pptx



Data structures and Algorithm analysis_Lecture4.pptxAhmedEldesoky24 This document defines and explains binary search trees (BSTs). It defines key BST terms like root, leaf nodes, and height. It also outlines common BST operations like search, insertion, deletion, finding the minimum/maximum elements, and tree traversals. Search, minimum/maximum, and traversal operations have linear time complexity based on tree height, while insertion and deletion are O(h) where h is the tree height. The document uses examples to illustrate BST concepts and operations.
Cinterviews Binarysearch Tree



Cinterviews Binarysearch Treecinterviews The document discusses binary trees and binary search trees. It defines key concepts like nodes, children, parents, leaves, height, and tree traversal. It explains that binary search trees allow searching, insertion, and deletion in O(log N) time by enforcing the property that all left descendants of a node are less than the node and all right descendants are greater. The operations of searching, insertion, deletion and their time complexities are outlined for binary search trees.
Trees in data structure



Trees in data structureAnusruti Mitra This document provides information about different tree data structures including binary trees, binary search trees, AVL trees, red-black trees, splay trees, and B-trees. Binary search trees allow for fast searching and maintain an ordered structure. AVL and red-black trees are self-balancing binary search trees that ensure fast search, insert, and delete times by keeping the tree balanced. B-trees are multiway search trees that allow for efficient storage and retrieval of data in databases and file systems.
7 chapter4 trees_binary



7 chapter4 trees_binarySSE_AndyLi The document discusses binary trees and their implementation. It defines a binary tree as a tree where each node has at most two children. Binary trees are implemented by having each node store the data and pointers to its left and right children. The document also discusses traversing binary trees using preorder, postorder and inorder traversals and provides examples of using these traversals to list files in a directory and calculate their total size. Expression trees are given as an example of binary trees, where leaves are operands and internal nodes are operators. Algorithms are provided to construct expression trees from postfix notation.
CS-102 BST_27_3_14.pdf



CS-102 BST_27_3_14.pdfssuser034ce1 Binary search trees have the property that all values in the left subtree of a node are smaller than the node's value and all values in the right subtree are larger. They allow for efficient search, insertion, and deletion operations that take O(log n) time on average for a balanced tree with n nodes. However, standard binary search trees may become unbalanced over time, affecting performance. Various self-balancing binary search tree data structures, such as AVL trees and red-black trees, use tree rotations during insertions and deletions to maintain height balance.
CS-102 BST_27_3_14v2.pdf



CS-102 BST_27_3_14v2.pdfssuser034ce1 Binary search trees have the following key properties:
1. Each node contains a value.
2. The left subtree of a node contains only values smaller than the node's value.
3. The right subtree of a node contains only values larger than the node's value.
Binary search trees allow for efficient insertion and search operations in O(log n) time due to their structure. Deletion may require rebalancing the tree to maintain the binary search tree properties.
mitochondria moment and super computer integration.ppt



mitochondria moment and super computer integration.pptAMMAD45 The document discusses binary search trees, which are binary trees that store keys in nodes such that all keys in the left subtree of a node are less than the node's key and all keys in the right subtree are greater. This property allows searching, insertion, and deletion operations to be performed efficiently in O(log N) time on average. The document covers tree terminology, traversal methods, and implementations of searching, inserting, deleting, finding the minimum/maximum keys, and maintaining the binary search tree properties during operations.
Tree.pptx



Tree.pptxworldchannel This document discusses tree data structures and binary search trees. It begins by defining linear and non-linear data structures, with trees being a non-linear structure. It then defines general tree terminology like root, child, parent, leaves, etc. It describes tree traversal methods like preorder, inorder and postorder. It also discusses binary search trees and basic BST operations like insertion, deletion and searching. Finally, it discusses how BSTs can be used for sorting by inserting elements into a BST and then performing an inorder traversal.
bst.ppt



bst.pptplagcheck This document discusses binary search trees. It begins by explaining what trees and binary trees are. It then describes key properties of binary search trees like their height and how every node's key is greater than all keys in its left subtree and less than keys in its right subtree. The document outlines common binary search tree operations like searching, insertion, deletion and traversal. It explains how each operation takes O(height of the tree) time since they involve traversing down a path in the tree from the root.
Balance tree. Short overview



Balance tree. Short overviewElifTech Short overview of balance tree: Data Structures, Binary search tree, BST Problem, Self Balancing BST, Usage, Red Black Trees, Red Black Insertion, AVL Tree, Rotations, B-Tree
Ad
More from Saurabh Mishra (7)
Sorting2



Sorting2Saurabh Mishra The document discusses various sorting algorithms and their time complexities, including:
1) Quicksort, which has an average case time complexity of O(n log n) but a worst case of O(n^2). It works by recursively partitioning an array around a pivot element.
2) Heapsort, which also has a time complexity of O(n log n). It uses a binary heap to extract elements in sorted order.
3) Counting sort and radix sort, which can sort in linear time O(n) when the input has certain properties like a limited range of values or being represented by a small number of digits.
Sorting



SortingSaurabh Mishra Insertion sort and merge sort are discussed. Insertion sort works by inserting elements in the proper position one by one. Its worst case time is O(N^2). Merge sort uses a divide and conquer approach to sort elements. It divides the list into halves, recursively sorts the halves, and then merges the sorted halves. Merging two sorted lists takes linear time. The overall time for merge sort is O(N log N). Heaps are discussed as a way to implement priority queues. A heap has the heap property where a node is always less than its children. This allows finding the minimum element and deleting it to take O(log N) time.
Searching



SearchingSaurabh Mishra Depth-first search (DFS) is a graph search algorithm that explores all nodes that are reachable from the starting node by traversing edges in a depth-first manner. It uses a stack to remember to explore the neighbor of the current node before backtracking. The algorithm marks nodes as visited as it traverses the graph and can detect cycles.
Presentation1



Presentation1Saurabh Mishra The document describes the process of depth-first search (DFS) on a graph using an adjacency list representation. It shows the recursive DFS algorithm by stepping through an example graph with 8 nodes. At each step, it marks the currently visited node as visited, marks the predecessors, and makes recursive calls to visit neighboring unvisited nodes. This traces out the DFS tree, showing how the structure captures the recursive calls. It concludes that DFS finds valid paths in the graph and runs in O(V+E) time like breadth-first search when using an adjacency list.
Graps 2



Graps 2Saurabh Mishra The document discusses breadth-first search (BFS) algorithms for graphs. It explains that BFS runs in O(n^2) time on adjacency matrices due to checking all elements in each row, but in O(n+m) time on adjacency lists where m is the number of edges. It then describes how to modify BFS to record the shortest path between nodes using a predecessor array. The rest of the document provides examples of how BFS works and applications such as finding connected components and directed acyclic graphs.
Graphs



GraphsSaurabh Mishra Graphs are useful tools for modeling problems and consist of vertices and edges. Breadth-first search (BFS) is an algorithm that visits the vertices of a graph starting from a source vertex and proceeding to visit neighboring vertices first, before moving to neighbors that are further away. BFS uses a queue to efficiently traverse the graph and discover all possible paths from the source to other vertices, identifying the shortest paths in an unweighted graph. The time complexity of BFS on an adjacency list representation is O(n+m) where n is the number of vertices and m is the number of edges.
Trees



TreesSaurabh Mishra The document discusses deletion operations in B+ trees. It explains that deleting a key from a leaf node may cause the leaf to have too few keys, requiring a merge with a sibling leaf. If the sibling also has too few keys, their parent node may need to be split or merged to maintain the B+ tree properties. The process of replacing deleted internal keys and potentially merging/splitting nodes is similar to the insertion procedure.
Recently uploaded (20)
Big Data Analytics Quick Research Guide by Arthur Morgan



Big Data Analytics Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...



Massive Power Outage Hits Spain, Portugal, and France: Causes, Impact, and On...Aqusag Technologies In late April 2025, a significant portion of Europe, particularly Spain, Portugal, and parts of southern France, experienced widespread, rolling power outages that continue to affect millions of residents, businesses, and infrastructure systems.
Special Meetup Edition - TDX Bengaluru Meetup #52.pptx



Special Meetup Edition - TDX Bengaluru Meetup #52.pptxshyamraj55 We’re bringing the TDX energy to our community with 2 power-packed sessions:
🛠️ Workshop: MuleSoft for Agentforce
Explore the new version of our hands-on workshop featuring the latest Topic Center and API Catalog updates.
📄 Talk: Power Up Document Processing
Dive into smart automation with MuleSoft IDP, NLP, and Einstein AI for intelligent document workflows.
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat The MCP (Model Context Protocol) is a framework designed to manage context and interaction within complex systems. This SlideShare presentation will provide a detailed overview of the MCP Model, its applications, and how it plays a crucial role in improving communication and decision-making in distributed systems. We will explore the key concepts behind the protocol, including the importance of context, data management, and how this model enhances system adaptability and responsiveness. Ideal for software developers, system architects, and IT professionals, this presentation will offer valuable insights into how the MCP Model can streamline workflows, improve efficiency, and create more intuitive systems for a wide range of use cases.
Complete Guide to Advanced Logistics Management Software in Riyadh.pdf



Complete Guide to Advanced Logistics Management Software in Riyadh.pdfSoftware Company Explore the benefits and features of advanced logistics management software for businesses in Riyadh. This guide delves into the latest technologies, from real-time tracking and route optimization to warehouse management and inventory control, helping businesses streamline their logistics operations and reduce costs. Learn how implementing the right software solution can enhance efficiency, improve customer satisfaction, and provide a competitive edge in the growing logistics sector of Riyadh.
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
Build Your Own Copilot & Agents For Devs



Build Your Own Copilot & Agents For DevsBrian McKeiver May 2nd, 2025 talk at StirTrek 2025 Conference.
TrsLabs - Fintech Product & Business Consulting



TrsLabs - Fintech Product & Business ConsultingTrs Labs Hybrid Growth Mandate Model with TrsLabs
Strategic Investments, Inorganic Growth, Business Model Pivoting are critical activities that business don't do/change everyday. In cases like this, it may benefit your business to choose a temporary external consultant.
An unbiased plan driven by clearcut deliverables, market dynamics and without the influence of your internal office equations empower business leaders to make right choices.
Getting things done within a budget within a timeframe is key to Growing Business - No matter whether you are a start-up or a big company
Talk to us & Unlock the competitive advantage
Drupalcamp Finland – Measuring Front-end Energy Consumption



Drupalcamp Finland – Measuring Front-end Energy ConsumptionExove How to measure web front-end energy consumption using Firefox Profiler. Presented in DrupalCamp Finland on April 25th, 2025.
Cyber Awareness overview for 2025 month of security



Cyber Awareness overview for 2025 month of securityriccardosl1 Cyber awareness training educates employees on risk associated with internet and malicious emails
UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager API



UiPath Community Berlin: Orchestrator API, Swagger, and Test Manager APIUiPathCommunity Join this UiPath Community Berlin meetup to explore the Orchestrator API, Swagger interface, and the Test Manager API. Learn how to leverage these tools to streamline automation, enhance testing, and integrate more efficiently with UiPath. Perfect for developers, testers, and automation enthusiasts!
📕 Agenda
Welcome & Introductions
Orchestrator API Overview
Exploring the Swagger Interface
Test Manager API Highlights
Streamlining Automation & Testing with APIs (Demo)
Q&A and Open Discussion
Perfect for developers, testers, and automation enthusiasts!
👉 Join our UiPath Community Berlin chapter: https://community.uipath.com/berlin/
This session streamed live on April 29, 2025, 18:00 CET.
Check out all our upcoming UiPath Community sessions at https://community.uipath.com/events/.
Into The Box Conference Keynote Day 1 (ITB2025)



Into The Box Conference Keynote Day 1 (ITB2025)Ortus Solutions, Corp This is the keynote of the Into the Box conference, highlighting the release of the BoxLang JVM language, its key enhancements, and its vision for the future.
IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...



IEDM 2024 Tutorial2_Advances in CMOS Technologies and Future Directions for C...organizerofv IEDM 2024 Tutorial2
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
Linux Professional Institute LPIC-1 Exam.pdf



Linux Professional Institute LPIC-1 Exam.pdfRHCSA Guru Introduction to LPIC-1 Exam - overview, exam details, price and job opportunities
AI and Data Privacy in 2025: Global Trends



AI and Data Privacy in 2025: Global TrendsInData Labs In this infographic, we explore how businesses can implement effective governance frameworks to address AI data privacy. Understanding it is crucial for developing effective strategies that ensure compliance, safeguard customer trust, and leverage AI responsibly. Equip yourself with insights that can drive informed decision-making and position your organization for success in the future of data privacy.
This infographic contains:
-AI and data privacy: Key findings
-Statistics on AI data privacy in the today’s world
-Tips on how to overcome data privacy challenges
-Benefits of AI data security investments.
Keep up-to-date on how AI is reshaping privacy standards and what this entails for both individuals and organizations.
Splunk Security Update | Public Sector Summit Germany 2025



Splunk Security Update | Public Sector Summit Germany 2025Splunk Splunk Security Update
Sprecher: Marcel Tanuatmadja
HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungen



HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungenpanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-und-verwaltung-von-multiuser-umgebungen/
HCL Nomad Web wird als die nächste Generation des HCL Notes-Clients gefeiert und bietet zahlreiche Vorteile, wie die Beseitigung des Bedarfs an Paketierung, Verteilung und Installation. Nomad Web-Client-Updates werden “automatisch” im Hintergrund installiert, was den administrativen Aufwand im Vergleich zu traditionellen HCL Notes-Clients erheblich reduziert. Allerdings stellt die Fehlerbehebung in Nomad Web im Vergleich zum Notes-Client einzigartige Herausforderungen dar.
Begleiten Sie Christoph und Marc, während sie demonstrieren, wie der Fehlerbehebungsprozess in HCL Nomad Web vereinfacht werden kann, um eine reibungslose und effiziente Benutzererfahrung zu gewährleisten.
In diesem Webinar werden wir effektive Strategien zur Diagnose und Lösung häufiger Probleme in HCL Nomad Web untersuchen, einschließlich
- Zugriff auf die Konsole
- Auffinden und Interpretieren von Protokolldateien
- Zugriff auf den Datenordner im Cache des Browsers (unter Verwendung von OPFS)
- Verständnis der Unterschiede zwischen Einzel- und Mehrbenutzerszenarien
- Nutzung der Client Clocking-Funktion
What is Model Context Protocol(MCP) - The new technology for communication bw...



What is Model Context Protocol(MCP) - The new technology for communication bw...Vishnu Singh Chundawat
Binary trees1
- 1. Binary Trees,Binary Search Trees
- 2. TreesLinear access time of linked lists is prohibitiveDoes there exist any simple data structure for which the running time of most operations (search, insert, delete) is O(log N)?
- 3. TreesA tree is a collection of nodesThe collection can be empty(recursive definition) If not empty, a tree consists of a distinguished node r (the root), and zero or more nonempty subtrees T1, T2, ...., Tk, each of whose roots are connected by a directed edge from r
- 4. Some TerminologiesChild and parentEvery node except the root has one parent A node can have an arbitrary number of childrenLeavesNodes with no children Siblingnodes with same parent
- 5. Some TerminologiesPathLengthnumber of edges on the pathDepthof a nodelength of the unique path from the root to that nodeThe depth of a tree is equal to the depth of the deepest leafHeight of a nodelength of the longest path from that node to a leafall leaves are at height 0The height of a tree is equal to the height of the rootAncestor and descendantProper ancestor and proper descendant
- 7. Binary TreesA tree in which no node can have more than two childrenThe depth of an “average” binary tree is considerably smaller than N, eventhough in the worst case, the depth can be as large as N – 1.
- 8. Example: Expression TreesLeaves are operands (constants or variables)The other nodes (internal nodes) contain operatorsWill not be a binary tree if some operators are not binary
- 9. Tree traversalUsed to print out the data in a tree in a certain orderPre-order traversalPrint the data at the rootRecursively print out all data in the left subtreeRecursively print out all data in the right subtree
- 10. Preorder, Postorder and InorderPreorder traversalnode, left, rightprefix expression++a*bc*+*defg
- 11. Preorder, Postorder and InorderPostorder traversalleft, right, nodepostfix expressionabc*+de*f+g*+Inorder traversalleft, node, right.infix expressiona+b*c+d*e+f*g
- 12. Preorder
- 13. Postorder
- 14. Preorder, Postorder and Inorder
- 15. Binary TreesPossible operations on the Binary Tree ADTparentleft_child, right_childsiblingroot, etcImplementationBecause a binary tree has at most two children, we can keep direct pointers to them
- 16. compare: Implementation of a general tree
- 17. Binary Search TreesStores keys in the nodes in a way so that searching, insertion and deletion can be done efficiently.Binary search tree propertyFor every node X, all the keys in its left subtree are smaller than the key value in X, and all the keys in its right subtree are larger than the key value in X
- 18. Binary Search TreesA binary search treeNot a binary search tree
- 19. Binary search treesAverage depth of a node is O(log N); maximum depth of a node is O(N)Two binary search trees representing the same set:
- 20. Implementation
- 21. Searching BSTIf we are searching for 15, then we are done.If we are searching for a key < 15, then we should search in the left subtree.If we are searching for a key > 15, then we should search in the right subtree.
- 23. Searching (Find)Find X: return a pointer to the node that has key X, or NULL if there is no such nodeTime complexityO(height of the tree)
- 24. Inorder traversal of BSTPrint out all the keys in sorted orderInorder: 2, 3, 4, 6, 7, 9, 13, 15, 17, 18, 20
- 25. findMin/ findMaxReturn the node containing the smallest element in the treeStart at the root and go left as long as there is a left child. The stopping point is the smallest elementSimilarly for findMaxTime complexity = O(height of the tree)
- 26. insertProceed down the tree as you would with a findIf X is found, do nothing (or update something)Otherwise, insert X at the last spot on the path traversedTime complexity = O(height of the tree)
- 27. deleteWhen we delete a node, we need to consider how we take care of the children of the deleted node.This has to be done such that the property of the search tree is maintained.
- 28. deleteThree cases:(1) the node is a leafDelete it immediately(2) the node has one childAdjust a pointer from the parent to bypass that node
- 29. delete(3) the node has 2 childrenreplace the key of that node with the minimum element at the right subtree delete the minimum element Has either no child or only right child because if it has a left child, that left child would be smaller and would have been chosen. So invoke case 1 or 2.Time complexity = O(height of the tree)
- 30. AVL-Trees
- 31. Balanced binary treeThe disadvantage of a binary search tree is that its height can be as large as N-1This means that the time needed to perform insertion and deletion and many other operations can be O(N) in the worst caseWe want a tree with small heightA binary tree with N node has height at least(log N) Thus, our goal is to keep the height of a binary search tree O(log N)Such trees are called balanced binary search trees. Examples are AVL tree, red-black tree.
- 32. AVL treeHeight of a nodeThe height of a leaf is 1. The height of a null pointer is zero.The height of an internal node is the maximum height of its children plus 1Note that this definition of height is different from the one we defined previously (we defined the height of a leaf as zero previously).
- 33. AVL treeAn AVL tree is a binary search tree in whichfor every node in the tree, the height of the left and right subtrees differ by at most 1.AVL property violated here
- 34. AVL treeLet x be the root of an AVL tree of height hLet Nh denote the minimum number of nodes in an AVL tree of height hClearly, Ni≥ Ni-1 by definitionWe haveBy repeated substitution, we obtain the general formThe boundary conditions are: N1=1 and N2 =2. This implies that h = O(log Nh).Thus, many operations (searching, insertion, deletion) on an AVL tree will take O(log N) time.
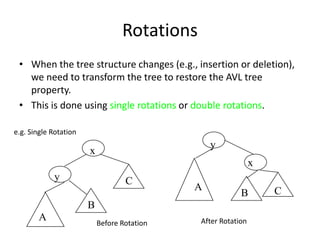
- 35. RotationsWhen the tree structure changes (e.g., insertion or deletion), we need to transform the tree to restore the AVL tree property.This is done using single rotations or double rotations.yxACBe.g. Single RotationxyCBAAfter RotationBefore Rotation
- 36. RotationsSince an insertion/deletion involves adding/deleting a single node, this can only increase/decrease the height of some subtree by 1Thus, if the AVL tree property is violated at a node x, it means that the heights of left(x) ad right(x) differ by exactly 2.Rotations will be applied to x to restore the AVL tree property.
- 37. InsertionFirst, insert the new key as a new leaf just as in ordinary binary search treeThen trace the path from the new leaf towards the root. For each node x encountered, check if heights of left(x) and right(x) differ by at most 1.If yes, proceed to parent(x). If not, restructure by doing either a single rotation or a double rotation [next slide].For insertion, once we perform a rotation at a node x, we won’t need to perform any rotation at any ancestor of x.
- 38. Insertion Let x be the node at which left(x) and right(x) differ by more than 1Assume that the height of x is h+3There are 4 casesHeight of left(x) is h+2 (i.e. height of right(x) is h)Height of left(left(x)) is h+1 single rotate with left childHeight of right(left(x)) is h+1 double rotate with left childHeight of right(x) is h+2 (i.e. height of left(x) is h)Height of right(right(x)) is h+1 single rotate with right childHeight of left(right(x)) is h+1 double rotate with right childNote: Our test conditions for the 4 cases are different from the code shown in the textbook. These conditions allow a uniform treatment between insertion and deletion.
- 39. Single rotationThe new key is inserted in the subtree A. The AVL-property is violated at x height of left(x) is h+2 height of right(x) is h.
- 40. Single rotationThe new key is inserted in the subtree C. The AVL-property is violated at x.Single rotation takes O(1) time.Insertion takes O(log N) time.
- 41. 3144810.83558341x AVL Tree5Cy8BA0.8Insert 0.8After rotation
- 42. Double rotationThe new key is inserted in the subtree B1 or B2. The AVL-property is violated at x.x-y-z forms a zig-zag shapealso called left-right rotate
- 43. Double rotationThe new key is inserted in the subtree B1 or B2. The AVL-property is violated at x.also called right-left rotate
- 44. xCy3Az43.58143.5B55833415 AVL Tree8Insert 3.5After Rotation1
- 45. An Extended Example33222442211133Fig 1335Fig 4Fig 2Fig 31Fig 5Fig 6Insert 3,2,1,4,5,6,7, 16,15,14Single rotationSingle rotation
- 46. 22444Fig 8Fig 755667337311222445566Fig 10Fig 95Fig 1133111Single rotationSingle rotation
- 47. 4447715316316316222Fig 12Fig 131566657Fig 1455111Double rotation
- 48. 4461415161533161422Fig 15Fig 167657511Double rotation




