Ad
Blockchain Fundamentals for basics understanding .pdf
- 2. Prerequisite • Knowledge of at least one programming language like what are variables, data types, loops, etc. PRESENTATION TITLE 2 Code Eater
- 3. Blockchain Fundamentals 3 Why Study Blockchain ? What is Blockchain ? Blockchain Popularity Types Of Accounts Ethereum Gas Ethereum Gas Price Ethereum Gas Limit Much More Blockchain Applications What is Ethereum ? Blockchain Working Ethereum Node Code Eater
- 4. Computer Science Fundamentals Decimal Binary (1 bit) 0 0 1 1 Code Eater
- 5. Computer Science Fundamentals Decimal Binary (2 bits) 0 00 1 01 2 10 3 11 Code Eater
- 6. Computer Science Fundamentals Decimal Binary (3 bits) 0 000 1 001 2 010 3 011 4 100 5 101 6 110 7 111 Click Here – Conversion from decimal to binary Code Eater
- 7. Computer Science Fundamentals Decimal Number 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 Equivalent Hexadecimal 0 1 2 3 4 5 6 7 8 9 A B C D E F Code Eater
- 8. Computer Science Fundamentals • 1 byte = 8 bits • 1 byte = 2 hexadecimal number Code Eater
- 10. Why Blockchain ? Code Eater
- 11. Why Blockchain ? Code Eater
- 17. Big Internet Players Code Eater
- 18. Blockchain = Transparency + Decentralization Code Eater
- 21. Billion Dolar Companies (Web2) Code Eater
- 22. Billion Dollar Companies(Web3) Code Eater
- 23. Question Time Ask your doubts
- 24. What Is Blockchain ? Blockchain is a distributed immutable ledger which is completely transparent. 24 Code Eater
- 25. What is a ledger ? 25 Code Eater
- 26. What is distributed ? 26 A B C E F Code Eater
- 27. What is distributed ? A B C E F Code Eater
- 28. What is distributed ? A B C E F Code Eater
- 29. What is distributed ? A B C E F Code Eater
- 30. What is distributed ? A B C E F Code Eater
- 31. Question Time Ask your doubts
- 32. Why Blockchain become popular ? W. Scott Stornetta Stuart Harber Code Eater
- 33. USA Code Eater
- 36. Recession Nearly 9 million – Lost Job Nearly 1.8 million – Small business closed Code Eater
- 38. Code Eater
- 39. Code Eater
- 42. Movie Code Eater
- 43. Code Eater
- 44. What is distributed ? Code Eater
- 46. 46 • Bitcoin is a decentralized digital currency, without a central bank or single administrator, that can be sent from user to user on the peer- to-peer bitcoin network without the need for intermediaries. • It uses Blockchain Technology. What is Bitcoin ? Code Eater
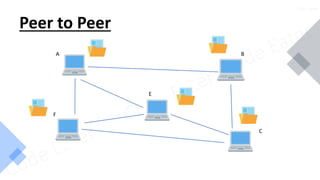
- 48. Peer to Peer A B C E F Code Eater
- 50. Ukraine Vs Russia Code Eater
- 51. Trust Code Eater
- 52. Demonstration Bitcoin Client – Click Here Code Eater
- 54. Question Time Ask your doubts Code Eater
- 56. FIR registration FIR Lodging – Click Here Code Eater
- 57. Types Of Blockchain Public Blockchain Private Blockchain Code Eater
- 61. Question Time Ask your doubts
- 62. Block Architecture Block No.-1 Data Hash:0000D8C42 Prev Hash:000000000 Genesis Block Fingerprint Code Eater
- 63. SHA256 Algorithm Document, Audio , Video etc. SHA256 5819E961F19967B4ECB242 9085E17909CFFD4DCB626 7D0067F6CAEC22150A7B1 This has 64 hexadecimal characters. Each character is of 4 bits. So in total it has 64* 4 bits i.e. 256 bits. Code Eater
- 64. SHA256 Algorithm Block No.- Data Hash: Prev Hash: SHA 256
- 65. SHA256 Algorithm Practical SHA256 Algorithm Demo Click Here Code Eater Code Eate
- 66. Question Time Ask your doubts Code Eater
- 67. How Blockchain Is Formed ? Block No.-1 Data Hash:0000D8C42 Prev Hash:000000000 Block No.-2 Data Hash:00003A459 Prev Hash:0000D8C42 Block No.-3 Data Hash:00003D45F Prev Hash:00003A459 Genesis Block Code Eater
- 68. Question Time Ask your doubts
- 69. Revise Let's take a (5+2) minutes break
- 70. Bitcoin Vs Ethereum (Application Level) Block No.-1 Data Hash:0000D8C42 Prev Hash:000000000 Code Eater Code Eate
- 71. Bitcoin Vs Ethereum (Application Level) Block No.-1 Data Hash:0000D8C42 Prev Hash:000000000
- 72. Ethereum Blockchain A B E F Code Eater
- 73. Demonstration Etherscan – Click Here Code Eater
- 74. Why Bitcoin does not support apps ? Bitcoin Script – Not Turing Complete Solidity – Turing Complete Code Eater
- 75. Ethereum Gas Code Eater Code Eate
- 76. Ethereum Gas
- 78. Ethereum Gas 10 * 3 – 6 = ? Multiplication – 5 gas Subtraction – 3 gas Equal to – 3 gas Total gas –> 5 + 3 +3 = 11 Gas Opcode List - Click Here Remix IDE - Click Here Code Eater
- 79. Why Bitcoin does not support apps ? Bitcoin Script – Not Turing Complete Solidity – Turing Complete Code Eater
- 80. Question Time Ask your doubts Code Eater
- 81. Ethereum Gas Price Code Eater
- 82. Ethereum Gas Price Gas /Petrol - 10L Rupees - ? 1L – Rs.100 Rupees for 10 L = 10 * 100 = Rs.1000 Code Eater
- 83. Ethereum Gas Price 10 * 3 – 6 = ? Multiplication – 5 gas Subtraction – 3 gas Equal to – 3 gas Total gas –> 5 + 3 +3 = 11 Gas 1 Gas price = 10 gwei Total Gas price = 11 * 10 = 110 gwei Code Eater Code Eate
- 84. 84 What is Gas Price? • It is the amount the sender wants to pay per unit of gas to get the transaction mined. gasPrice is set by the sender. • Gas prices are denoted in gwei. (1 gwei = 10^-9 ETH) 1 Gas price = x gwei where x >0 • X is decided by the demand and supply in the market. Code Eater
- 85. Gas Price • The higher the gas price the faster the transaction will be mined. It just like the transaction in Bitcoin. Code Eater
- 86. Question Time Ask your doubts
- 87. Why Bitcoin does not support apps ? Bitcoin Script – Not Turing Complete Solidity – Turing Complete Code Eater
- 88. Why Bitcoin does not support apps ? A B E F Code Eater
- 89. Gas Limit • It is the maximum gas the transaction can consume. • Set by the sender. Code Eater Code Eate
- 90. 90 What is Gas Price? gasLimit > gas consumed Return the remaining gas Revert the transaction Yes No
- 91. Demonstration Etherscan – Click Here Code Eater
- 93. Question Time Ask your doubts
- 94. How To Become Part Of The Network? A B E F C
- 96. Types Of Nodes Full Node Light Node Archive node
- 97. Full Node • All states can be derived from a full node (although very old states are reconstructed from requests made to archive nodes) • Serves the network and provides data on request. • Stores full blockchain data (although this is periodically pruned so a full node does not store all state data back to genesis) • Participates in block validation, verifies all blocks and states.
- 98. Light Node • The light nodes do not participate in consensus (i.e. they cannot be miners/validators), but they can access the Ethereum blockchain with the same functionality as a full node. • Stores only the block header and depends on full node. • For low capacity devices which cannot afford to store the gigabytes of data.
- 99. Archive Nodes • Stores everything kept in the full node and built an archive of historical data. • Requires terabytes of diskspace. Code Eater
- 100. Types Of Accounts Externally Owned Account (EOA) Contract Account
- 101. Demonstration Etherscan – Click Here Code Eater
- 102. Question Time Ask your doubts
- 104. Why do we need blockchain? Code Eater 1. Decentralization: One of the primary reasons for using blockchain technology is to create decentralized systems. In a decentralized network, there is no central authority or intermediary to control the system, which makes it more transparent, secure, and resistant to censorship and corruption. 2. Security: Blockchain technology uses cryptographic algorithms to secure transactions and data. Every transaction on the blockchain is verified and validated by multiple participants, which makes it difficult for any unauthorized party to alter the data or steal information. 3. Transparency: Blockchain technology provides transparency by creating an immutable ledger of all transactions. This means that every participant in the network can see all the transactions that have taken place and can verify their authenticity, which promotes trust and accountability. 4. Efficiency: Blockchain technology can help reduce transaction costs and increase efficiency by eliminating intermediaries and automating processes. By removing intermediaries, transactions can be completed faster and more efficiently, which can help reduce costs and increase profits for businesses.
- 105. What is Blockchain? Code Eater Blockchain is a digital ledger technology that enables the creation of secure, transparent, and decentralized systems. A blockchain is a distributed database that is maintained by a network of computers, or nodes, rather than a central authority. Every node in the network has a copy of the database, which contains a record of every transaction that has ever occurred on the blockchain. Each transaction on the blockchain is verified and validated by multiple nodes in the network, using advanced cryptographic algorithms. Once a transaction is verified and validated, it is added to the blockchain, creating a new block in the chain. This block is then broadcast to every node in the network, and each node updates its copy of the blockchain accordingly. The blockchain is considered secure because every block in the chain is linked to the previous block, creating an unbreakable chain of transactions. Once a block is added to the blockchain, it cannot be altered or deleted, making it a tamper-proof record of all transactions that have ever occurred on the blockchain. Blockchain technology has a wide range of applications, including financial services, supply chain management, healthcare, voting systems, and more. Its potential lies in its ability to create trust, security, and transparency in various industries, while eliminating the need for intermediaries and enabling new business models.
- 106. Types of Blockchain Code Eater There are generally three types of blockchain: public, private, and hybrid. 1. Public Blockchain: A public blockchain is a decentralized blockchain network that is open to anyone to participate and access. Anyone can join the network, read, and write data. Examples of public blockchains are Bitcoin, Ethereum, and Litecoin. 2. Private Blockchain: A private blockchain is a blockchain network that is permissioned, meaning that only authorized participants can access and participate in the network. Private blockchains are typically used within organizations or among a group of known and trusted parties. Examples of private blockchains are Hyperledger Fabric, Corda, and Quorum. 3. Hybrid Blockchain: A hybrid blockchain is a combination of both public and private blockchain networks. It offers the best of both worlds, as it allows authorized participants to access and participate in the private network while also being able to interact with the public blockchain network. Examples of hybrid blockchains are Dragonchain, Aion, and Ark. In addition to these three types of blockchains, there are also other types of blockchains that are variations or modifications of the three types. For example, there are consortium blockchains that are a type of private blockchain where a group of organizations come together to jointly operate and manage the network.
- 107. Blockchain Applications Code Eater Blockchain technology has a wide range of applications across various industries. Here are four examples of how blockchain is being used: 1. Cryptocurrencies: The most well-known application of blockchain technology is the creation and use of cryptocurrencies like Bitcoin, Ethereum, and Litecoin. These digital currencies are decentralized, meaning they are not controlled by any government or financial institution, and they use blockchain technology to facilitate secure, peer-to-peer transactions. 2. Supply Chain Management: Blockchain technology is being used to improve supply chain management by creating a transparent and secure record of every transaction that occurs in the supply chain. This helps to reduce fraud, increase efficiency, and improve trust between all parties involved in the supply chain. 3. Identity Verification: Blockchain technology can be used to create secure and tamper-proof digital identities for individuals. This can help to reduce identity theft and fraud, as well as make it easier for individuals to prove their identity in a variety of contexts. 4. Smart Contracts: Smart contracts are self-executing contracts that use blockchain technology to automatically enforce the terms of a contract. This can help to reduce the need for intermediaries like lawyers and banks, as well as increase the efficiency and speed of contract execution. Smart contracts are being used in a variety of industries, including real estate, insurance, and financial services.
- 108. What is Bitcoin? Code Eater Bitcoin is a decentralized digital currency, also known as a cryptocurrency, that operates on a peer-to-peer network without the need for a central authority or intermediary. It was created in 2009 by an anonymous individual or group of individuals using the pseudonym Satoshi Nakamoto. Bitcoin transactions are recorded on a public ledger called the blockchain, which is maintained by a network of computers, or nodes, around the world. Each transaction on the blockchain is verified and validated by multiple nodes, using advanced cryptographic algorithms. One of the key features of Bitcoin is its limited supply. The total number of bitcoins that can ever be created is capped at 21 million, which means that it is a deflationary currency. This is in contrast to fiat currencies, which are inflationary and can be printed by central authorities at will. Bitcoin can be bought and sold on cryptocurrency exchanges, and it can be used to purchase goods and services from merchants that accept it as payment. Bitcoin can also be stored in digital wallets, which can be accessed from anywhere in the world, as long as there is an internet connection. Bitcoin has gained significant adoption over the years and has inspired the creation of many other cryptocurrencies and blockchain-based applications.
- 109. What is Peer-To-Peer Network? Code Eater A peer-to-peer (P2P) network is a type of network in which each node in the network can act as both a client and a server, allowing it to share resources and information directly with other nodes without the need for a central server or intermediary. In a P2P network, each node has equal status and can initiate or respond to requests from other nodes in the network. In a P2P network, each node maintains its own copy of the data, which can be shared with other nodes in the network. This allows for distributed computing, where tasks can be divided among multiple nodes, and resources can be shared among all the nodes in the network. P2P networks are commonly used for file-sharing, where users can share files directly with other users, without the need for a central server. P2P networks are also used for distributed computing, where multiple nodes can work together to solve complex problems or perform large-scale simulations. One of the advantages of P2P networks is their scalability, as they can handle a large number of nodes without the need for a centralized infrastructure. P2P networks are also resilient to failures, as nodes can still communicate with each other even if some nodes are offline or unavailable. However, P2P networks can also be more difficult to manage and secure, as there is no central authority to oversee the network or ensure its security. As such, P2P networks require specialized protocols and security measures to ensure that data is kept safe and secure.
- 110. What is client-server model? Code Eater The client-server model is a computing architecture in which a central server provides resources, data, or services to multiple client devices. In this model, the server is responsible for managing the resources and providing access to them, while the clients are responsible for requesting and using those resources. In a client-server model, the server is typically a powerful computer or set of computers that are designed to handle a large amount of traffic and requests from multiple clients simultaneously. The clients, on the other hand, can be any type of device that can communicate with the server, such as a desktop computer, laptop, tablet, or smartphone. When a client wants to access a resource or service provided by the server, it sends a request to the server over a network connection. The server processes the request, retrieves the necessary data or resources, and sends it back to the client over the same connection. The client then uses the resources or data it received to perform a task or display information to the user. The client-server model is commonly used in many different types of applications and services, such as web browsing, email, file sharing, and database management. It is a widely used model because it provides a scalable and efficient way to share resources and services among multiple clients, while allowing the server to manage and maintain control over those resources.
- 111. What is Ethereum? Code Eater Ethereum is a decentralized blockchain platform that enables the creation of smart contracts and decentralized applications (Dapps). It was launched in 2015 by Vitalik Buterin, a Canadian-Russian programmer. Like Bitcoin, Ethereum uses a blockchain to record and verify transactions, but it goes beyond Bitcoin by allowing developers to build and deploy decentralized applications on top of the blockchain. These applications can be used for a wide range of purposes, including financial services, gaming, social networks, supply chain management, and more. One of the key features of Ethereum is its smart contract functionality. Smart contracts are self-executing programs that run on the Ethereum blockchain, allowing developers to create decentralized applications that can execute code without the need for intermediaries or trusted third parties. Smart contracts can be used to automate a wide range of processes, such as the exchange of assets, the management of digital identities, and the execution of complex financial transactions. Ethereum has its own cryptocurrency, called Ether (ETH), which is used to pay for transactions and services on the network. Ether can be bought and sold on cryptocurrency exchanges, and it is used by developers to incentivize the validation of transactions and the execution of smart contracts.
- 112. Ethereum Vs Bitcoin Code Eater Ethereum and Bitcoin are both decentralized blockchain platforms that have some similarities but also some important differences. Here are some key differences between Ethereum and Bitcoin: 1. Purpose: Bitcoin was created as a decentralized digital currency, while Ethereum was designed as a platform for decentralized applications (Dapps) and smart contracts. 2. Mining Algorithm: Bitcoin uses a Proof-of-Work (PoW) mining algorithm, which requires a lot of computational power and energy to validate transactions and add new blocks to the blockchain. Ethereum currently uses PoS algorithm, which is more energy-efficient. 3. Programming Language: While Bitcoin has a limited scripting language for transactions, Ethereum allows developers to create custom smart contracts and decentralized applications using a variety of programming languages, such as Solidity, Vyper, and Rust. 4. Transaction Speed and Scalability: Ethereum is generally faster than Bitcoin when it comes to processing transactions, with an average block time of around 15 seconds compared to Bitcoin's 10 minutes. However, Ethereum is facing scalability issues, with network congestion leading to high fees and slower transaction times during periods of high demand. 5. Supply: Bitcoin has a finite supply of 21 million coins, while Ethereum does not have a fixed supply, with new Ether tokens being created through mining and transaction fees.
- 113. Turing Complete – Bitcoin vs Ethereum Code Eater Ethereum is Turing-complete, while Bitcoin is not. Turing completeness is a measure of the ability of a programming language or system to perform any computation that a Turing machine can do. A Turing machine is a hypothetical machine that can perform any computation that is algorithmically computable. Ethereum's smart contract programming language, Solidity, is Turing-complete. This means that any computation that can be performed by a Turing machine can also be performed by a smart contract on the Ethereum blockchain. In contrast, Bitcoin's scripting language is not Turing-complete. While it can perform some basic operations, such as verifying signatures and checking if a transaction output has been spent, it is not capable of performing arbitrary computations. The Turing completeness of Ethereum's smart contract system allows for the creation of more complex and sophisticated decentralized applications (dApps) on the Ethereum blockchain, such as decentralized exchanges, prediction markets, and games. However, it also introduces additional security risks, as smart contracts can potentially be vulnerable to bugs and exploits that can lead to financial losses for users.
- 114. Ethereum Gas Code Eater In the Ethereum network, "gas" refers to the unit of measurement used to calculate the amount of computational power required to execute a transaction or smart contract. Gas represents the cost of performing an operation on the Ethereum network, and it is paid for in Ether, the native cryptocurrency of the Ethereum network. Every transaction or smart contract execution in the Ethereum network requires a certain amount of gas to be used. The amount of gas required depends on the complexity of the transaction or smart contract, and the gas price is determined by the market demand and supply of gas at any given time. The gas price is denominated in Gwei, which is a fraction of an Ether. Gas prices can vary widely depending on network congestion and other factors, and users can set their own gas prices when sending transactions or executing smart contracts. If a user sets a gas price that is too low, the transaction may take longer to be confirmed or may not be confirmed at all. On the other hand, if a user sets a gas price that is too high, they may end up paying more than necessary for the transaction. In summary, gas is a measure of the computational resources required to execute transactions and smart contracts on the Ethereum network, and it is paid for in Ether at a market-determined gas price.
- 115. Ethereum Gas Price Code Eater The Ethereum gas price refers to the cost of executing a transaction or smart contract on the Ethereum network. It is denominated in "gwei," which is a fraction of an Ether. Gas price is determined by the supply and demand of computational resources needed to execute a transaction or smart contract at a given time. When there is high demand for computational resources on the network, gas prices tend to go up, and when there is low demand, gas prices tend to go down. Users can set their own gas prices when submitting a transaction or smart contract to the Ethereum network. If a user sets a gas price that is too low, the transaction may not be confirmed by the network, or it may take a long time to be confirmed. If a user sets a gas price that is too high, they may end up overpaying for the transaction. Gas prices are typically expressed in gwei per unit of gas. For example, a gas price of 20 gwei per unit of gas means that the user is willing to pay 20 gwei for each unit of computational resources needed to execute the transaction or smart contract. In summary, the Ethereum gas price is the cost of executing a transaction or smart contract on the Ethereum network, and it is determined by the market supply and demand of computational resources needed for the execution. Users can set their own gas prices based on their willingness to pay for the computational resources.
- 116. Ethereum Gas Limit Code Eater The Ethereum gas limit is a parameter in the Ethereum network that determines the maximum amount of gas that can be used in a single block. Gas refers to the computational resources needed to execute a transaction or smart contract on the Ethereum network. The gas limit is set by the miners on the network and is adjusted periodically based on the demand for computational resources. If the gas limit is set too low, it may not be enough to execute all the transactions and smart contracts in a block, resulting in an incomplete block. On the other hand, if the gas limit is set too high, it may result in wasted resources and longer block times. The gas limit is an important factor in determining the cost of executing transactions and smart contracts on the Ethereum network. The total cost of executing a transaction or smart contract is calculated by multiplying the gas price (the amount of Ether paid per unit of gas) by the amount of gas used. Therefore, a higher gas limit means that more complex and resource-intensive transactions can be executed, but it also means that the transaction or contract will be more expensive. In summary, the Ethereum gas limit is the maximum amount of gas that can be used in a single block on the Ethereum network, set by the miners on the network. It is an important factor in determining the cost and efficiency of executing transactions and smart contracts on the network.
- 117. Ethereum Gas Limit and Turing Complete Code Eater The Turing completeness of Ethereum is related to the Ethereum gas limit because it places a computational burden on the network. Since Ethereum is Turing-complete, it is capable of running arbitrary code, including potentially resource- intensive programs. This means that a poorly designed or malicious smart contract could potentially consume a large amount of computational resources and slow down the entire network. To prevent this from happening, Ethereum has implemented a gas limit. Gas is the unit of computation on the Ethereum network, and each transaction or smart contract execution requires a certain amount of gas to be paid by the user. The gas limit is the maximum amount of gas that can be used in a block, which is a collection of transactions that are processed together on the Ethereum network. The gas limit serves as a way to limit the amount of computational resources that a single transaction or smart contract execution can consume. If a transaction or smart contract execution exceeds the gas limit, it will fail and the user will lose the gas they paid. Therefore, the gas limit is a crucial mechanism for maintaining the stability and security of the Ethereum network. It ensures that the network is not overwhelmed by resource-intensive computations, while also incentivizing developers to write efficient and optimized smart contracts.
- 118. Types of Nodes Code Eater In Ethereum, there are several types of nodes, including: 1. Full Nodes: A full node in Ethereum is a node that stores the complete copy of the Ethereum blockchain and validates all transactions and smart contracts. It communicates with other nodes on the network to synchronize the blockchain data and maintains a full copy of the state of the network. 2. Light Nodes: A light node in Ethereum is a node that stores only a portion of the blockchain data and relies on full nodes to validate transactions and smart contracts. Light nodes are useful for users who don't have the storage or bandwidth capacity to run a full node. 3. Archive Nodes: An archive node in Ethereum is a node that stores not only the current state of the Ethereum network but also every historical state of the network. This makes it possible to access data from any point in time on the Ethereum blockchain.
- 119. Ethereum Accounts Code Eater In Ethereum, there are two types of accounts: externally owned accounts (EOAs) and contract accounts. 1. Externally Owned Accounts (EOAs): An EOA is an account that is controlled by a private key and represents an individual or organization on the Ethereum network. EOAs are used to store and transfer Ether and other ERC-20 tokens. Each EOA has an Ethereum address, which is a 20-byte hexadecimal string that serves as the identifier for the account. 2. Contract Accounts: A contract account in Ethereum is an account that is controlled by a smart contract. Contract accounts are created when a smart contract is deployed to the Ethereum network. The contract account can hold Ether or other tokens, and the smart contract code defines the rules for how the funds can be transferred or accessed. Each contract account has a unique Ethereum address, just like an EOA. The main difference between EOAs and contract accounts is that EOAs are controlled by a private key, while contract accounts are controlled by a smart contract. EOAs can only hold Ether and other tokens, while contract accounts can hold Ether, tokens, and other assets that are represented by the smart contract code.
- 120. What is geth? Code Eater Geth (short for "go-ethereum") is one of the most popular client implementations of the Ethereum protocol. It is written in the Go programming language and is developed by the Ethereum Foundation. Geth is used to connect to the Ethereum network, synchronize with the blockchain, and interact with smart contracts and dApps. It is a command-line tool that can be run on a local machine or on a remote server. Some of the key features of Geth include: 1. Node management: Geth allows users to create and manage Ethereum nodes, which are used to connect to the Ethereum network. 2. Blockchain synchronization: Geth synchronizes with the Ethereum blockchain, ensuring that the node has the latest copy of the blockchain. 3. Smart contract deployment: Geth allows users to deploy and interact with smart contracts on the Ethereum network. Part 1 of 2
- 121. What is geth? Code Eater 4. Mining: Geth supports mining, which is the process of adding new blocks to the blockchain and earning ether as a reward. 5. Web3 API: Geth provides a Web3 API that allows developers to build decentralized applications that interact with the Ethereum network. Overall, Geth is an essential tool for developers, miners, and anyone else who wants to participate in the Ethereum ecosystem. Its robust feature set and active development community make it a reliable and widely used client implementation of the Ethereum protocol. Part 2 of 2
- 122. What is opcode? Code Eater In computer science, an opcode (short for "operation code") is a basic instruction that specifies an operation to be performed by a computer processor. Opcodes are used in machine language and assembly language programming, which are low-level programming languages that are directly executed by the processor. Each opcode represents a specific operation that the processor can perform, such as adding two numbers, moving data from one memory location to another, or jumping to a different part of the program. Opcodes are typically represented as binary values that are encoded into the machine language instructions. Programmers use opcodes to write programs that can be executed by a computer. Higher-level programming languages, such as C, Java, and Python, use compilers to translate their code into machine language, which consists of sequences of opcodes and operands. In summary, an opcode is a fundamental building block of machine language and assembly language programming that represents a specific operation that a computer processor can perform.
- 123. What is Ethereum opcode? Code Eater In Ethereum, there are two types of accounts: externally owned accounts (EOAs) and contract accounts. 1. Externally Owned Accounts (EOAs): An EOA is an account that is controlled by a private key and represents an individual or organization on the Ethereum network. EOAs are used to store and transfer Ether and other ERC-20 tokens. Each EOA has an Ethereum address, which is a 20-byte hexadecimal string that serves as the identifier for the account. 2. Contract Accounts: A contract account in Ethereum is an account that is controlled by a smart contract. Contract accounts are created when a smart contract is deployed to the Ethereum network. The contract account can hold Ether or other tokens, and the smart contract code defines the rules for how the funds can be transferred or accessed. Each contract account has a unique Ethereum address, just like an EOA. The main difference between EOAs and contract accounts is that EOAs are controlled by a private key, while contract accounts are controlled by a smart contract. EOAs can only hold Ether and other tokens, while contract accounts can hold Ether, tokens, and other assets that are represented by the smart contract code.
- 124. Thank you Instagram - @codeeater21 LinkedIn - www.linkedin.com/in/kshitijWeb3 Twitter - @KshitijWeb3 Code Eater