Building an Effective Architecture for Identity and Access Management.pdf
0 likes47 views
Keycloak is an open source identity and access management solution that provides single sign-on for both legacy and new applications. It uses established standards like OAuth 2.0, OpenID Connect and SAML to securely authenticate users and manage authorization for multiple applications and services. Keycloak offers out-of-the-box features like social logins, user management, tokens and federation that make it easy to get started. It is also extensible through custom authentication mechanisms, event listeners and themes. Keycloak provides adapters to easily integrate with different frameworks and platforms.
1 of 49
Download to read offline








![[AuthZ] [AuthN]](https://image.slidesharecdn.com/buildinganeffectivearchitectureforidentityandaccessmanagement-220817005512-741fc505/85/Building-an-Effective-Architecture-for-Identity-and-Access-Management-pdf-9-320.jpg)
























![Essential Token Types
• Access Token
• Short lived [Minutes+]
• Used for accessingresources
• RefreshToken
• Long lived [Hours+]
• Used for requestingnew tokens
• ID Token
• Containsuser information(OIDC)
• Offline Token
• Long lived [Days+]
• Refreshtoken that never expires](https://image.slidesharecdn.com/buildinganeffectivearchitectureforidentityandaccessmanagement-220817005512-741fc505/85/Building-an-Effective-Architecture-for-Identity-and-Access-Management-pdf-34-320.jpg)














Ad
Recommended
ConFoo 2015 - Securing RESTful resources with OAuth2



ConFoo 2015 - Securing RESTful resources with OAuth2Rodrigo Cândido da Silva OAuth 2.0 is an open authentication and authorization protocol which enables applications to access each others data. This talk will presents how to implement the OAuth2 definitions to secure RESTful resources developed using JAX-RS in the Java EE platform.
Secure your app with keycloak



Secure your app with keycloakGuy Marom The slides from the talk I gave in Java.IL's Apr 2019 session.
These slides describe Keycloak, OAuth 2.0, OpenID and SparkBeyond's integration with Keycloak
JavaOne 2014 - Securing RESTful Resources with OAuth2



JavaOne 2014 - Securing RESTful Resources with OAuth2Rodrigo Cândido da Silva OAuth 2.0 is an open authentication and authorization protocol which enables applications to access each others data. This talk will presents how to implement the OAuth2 definitions to secure RESTful resources developed using JAX-RS in the Java EE platform.
Help! I Have An Identity Crisis: A look at various mechanisms of Single Sign On



Help! I Have An Identity Crisis: A look at various mechanisms of Single Sign OnSaloni Shah The document discusses single sign-on and identity federation standards including SAML, OAuth, and OpenID Connect. It provides an overview of the key concepts and roles for each standard. SAML uses XML and focuses on enterprise single sign-on, using three roles - identity provider, service provider, and principal. OAuth is an authorization protocol using tokens for APIs, with roles of client, resource owner, and authorization server. OpenID Connect builds on OAuth to provide single sign-on for consumers on web and mobile. Security considerations are discussed around using standards, TLS, and avoiding vulnerabilities.
Authentication in microservice systems - fsto 2017



Authentication in microservice systems - fsto 2017Dejan Glozic This document discusses authentication in microservice systems. It begins by setting the stage and introducing relevant topics. It then builds vocabulary around OAuth2, bearer tokens, JWT, and JWK. It describes authenticating micro frontends using an identity provider, leader/follower pattern, and endpoint middleware. It covers authenticating REST API microservices using bearer token validation. Finally, it addresses authenticating asynchronous messages using client credentials grants and session IDs across message brokers and web sockets. The conclusion summarizes that securing a microservice system involves securing each micro frontend, REST API, and asynchronous flow while maintaining performance and architecture abstraction.
Anil saldhana cloudidentitybestpractices



Anil saldhana cloudidentitybestpracticesAnil Saldanha This document discusses best practices for cloud identity in a JavaEE enabled PaaS environment. It covers topics like user registration, identity management, authentication, authorization, identity providers, and API access. It also demonstrates an Aerogear TODO application deployed on OpenShift that implements some of these practices. Relevant standards like JSR 351 and work from Oasis on cloud identity and authorization are also mentioned.
JDD2015: Security in the era of modern applications and services - Bolesław D...



JDD2015: Security in the era of modern applications and services - Bolesław D...PROIDEA This document discusses security challenges with modern applications and services and provides an overview of common standards and approaches. It outlines issues with traditional password-based authentication and session management in today's environment of mobile apps, microservices, and client-side applications. The document then introduces token-based security standards like SAML, JWT, OAuth2, and OpenID Connect, explaining how they address these issues through tokenization, delegation, and flexible authentication. It recommends relying on existing solutions like Keycloak that implement these standards to simplify security implementation and avoid potential vulnerabilities.
Api security 



Api security teodorcotruta API Security Teodor Cotruta discusses API security and provides an overview of key concepts. The document discusses how API security involves protecting APIs against unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction. It also outlines methods for implementing API security such as HTTP authentication, TLS, identity delegation, OAuth 1.0, OAuth 2.0, Federation, SAML, JWT, OpenID Connect, JWToken, JWSignature and JWEncryption.
Keycloak for Science Gateways - SGCI Technology Sampler Webinar



Keycloak for Science Gateways - SGCI Technology Sampler Webinarmarcuschristie Using Keycloak to Provide Authentication, Authorization, and Identity Management Services for Your Gateway
Presentation to accompany blog post: https://sciencegateways.org/-/eds-tech-blog-using-keycloak-to-provide-authentication-authorization-and-identity-management-services-for-your-gateway
Self-Service x Hashicorp Vault



Self-Service x Hashicorp VaultMartin Conraux Let's see how we can leverage on Vault capabilities to create a self-service system inside your company
SSL Everywhere!



SSL Everywhere!Simon Haslam SSL, more strictly called Transport Layer Security (TLS), is a means to encrypt data that is in flight between software components, whether within your data center or between that and your end users' devices. This prevents eavesdroppers seeing confidential information, such as credit card numbers or database passwords, and ensures that components are communicating with who they they think they are. So why isn't SSL/TLS used for all electronic communications? Firstly it is, almost by definition, "slightly tricky" to configure and errors are not terribly informative when things don't work (why would you help a hacker?!). Secondly there is a performance overhead for running TLS, although with modern hardware this is probably less of a concern than it used to be.
This session describes how to configure TLS at all layers within a Fusion Middleware stack - from the front-end Oracle HTTP Server, right through to communications with the database.
This platform was first given by Simon Haslam (eProseed UK) and Jacco Landlust (ING) at the OGh Fusion Middleware Experience event in February 2016.
TALK-I-TIVE_PresentatTALK-I-TIVE_Presentation[1][1].pptxion[1][1].pptx![TALK-I-TIVE_PresentatTALK-I-TIVE_Presentation[1][1].pptxion[1][1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation11-250223062925-3471f52a-thumbnail.jpg?width=560&fit=bounds)
![TALK-I-TIVE_PresentatTALK-I-TIVE_Presentation[1][1].pptxion[1][1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation11-250223062925-3471f52a-thumbnail.jpg?width=560&fit=bounds)
![TALK-I-TIVE_PresentatTALK-I-TIVE_Presentation[1][1].pptxion[1][1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation11-250223062925-3471f52a-thumbnail.jpg?width=560&fit=bounds)
![TALK-I-TIVE_PresentatTALK-I-TIVE_Presentation[1][1].pptxion[1][1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation11-250223062925-3471f52a-thumbnail.jpg?width=560&fit=bounds)
TALK-I-TIVE_PresentatTALK-I-TIVE_Presentation[1][1].pptxion[1][1].pptxdosoro7306 TALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptx
TALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptx![TALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation1-250223062819-64690da9-thumbnail.jpg?width=560&fit=bounds)
![TALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation1-250223062819-64690da9-thumbnail.jpg?width=560&fit=bounds)
![TALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation1-250223062819-64690da9-thumbnail.jpg?width=560&fit=bounds)
![TALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation1-250223062819-64690da9-thumbnail.jpg?width=560&fit=bounds)
TALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptxdosoro7306 TALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptxTALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptxTALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptxTALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptxTALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptx
Introduction to sitecore identity



Introduction to sitecore identityGopikrishna Gujjula This document provides an overview of authentication, authorization, ASP.NET Identity, OAuth, OpenID Connect, and IdentityServer4. It discusses the evolution of user security in ASP.NET, how ASP.NET Identity works with OAuth and OpenID Connect, and the roles of an authorization server and security token service. The agenda indicates it will include a demo of IdentityServer4 configuration and use with a sample Sitecore implementation.
Adding Identity Management and Access Control to your App



Adding Identity Management and Access Control to your AppFIWARE Adding Identity Management and Access Control to your App presentation, by Alvaro Alonso & Cyril Dangerville.
Security Chapter. 1st FIWARE Summit, Málaga Dec. 13-15, 2016.
Managing your secrets in a cloud environment



Managing your secrets in a cloud environmentTaswar Bhatti Managing your secrets in a cloud environment using Azure Key Vault and HashiCorp Vault. Presentation at Update Conference Prague 2018.
Part 5 of the REAL Webinars on Oracle Cloud Native Application Development - ...



Part 5 of the REAL Webinars on Oracle Cloud Native Application Development - ...Lucas Jellema This document announces six virtual developer meetups on cloud native application development on Oracle Cloud Platform. The meetups will cover topics including cloud operations, monitoring, infrastructure as code using Terraform, and native application development. All sessions will include introductions, demonstrations, hands-on labs, and Q&A. Recordings of the sessions will be made available on YouTube. The document provides details on preparing an Oracle Cloud Infrastructure tenancy for the hands-on labs and signing up for a cloud trial.
Web API 2 Token Based Authentication



Web API 2 Token Based Authenticationjeremysbrown This document discusses token based authentication in ASP.NET Web API 2 projects. It covers the basic concepts of token authentication including the roles in OAuth 2.0 of resource owners, clients, authorization servers and resource servers. It also summarizes the different OAuth 2.0 client types, authorization grant types, and development options for implementing token authentication using OWIN middleware or DotNetOpenAuth.
SharePoint Authentication And Authorization SPTechCon San Francisco



SharePoint Authentication And Authorization SPTechCon San FranciscoLiam Cleary [MVP] This document discusses authentication and authorization in SharePoint. It begins with an overview of security concepts like authentication, which verifies a claim of identity, and authorization, which verifies permissions. It then covers authentication options in SharePoint like Windows authentication and claims-based authentication using an identity provider. The document also discusses authorization and role providers, custom identity providers, and Azure Access Control Service. It emphasizes configuring authorization correctly after authentication and expecting security issues to arise.
Building IAM for OpenStack



Building IAM for OpenStackSteve Martinelli Building IAM for OpenStack, presented at CIS (Cloud Identity Summit) 2015.
Discuss Identity Sources, Authentication, Managing Access and Federating Identities
Intro to Apache Shiro



Intro to Apache ShiroClaire Hunsaker Apache Shiro, a simple easy-to-use framework to enforce user security by Shiro PMC Chair and Stormpath CTO, Les Hazlewood.
http://shiro.apache.org
http://stormpath.com
Adding identity management and access control to your app



Adding identity management and access control to your appÁlvaro Alonso González The document discusses OAuth 2.0 and authorization. It describes OAuth 2.0 as a mechanism for applications to access restricted resources without sharing credentials. It outlines the roles in OAuth 2.0 including resource owner, resource server, client, and authorization server. It also describes the different OAuth 2.0 grant types including authorization code, implicit, resource owner password credentials, and client credentials. The document then discusses using OAuth 2.0 and PEP proxies to secure web applications and backends as well as authenticating IoT devices. It also provides an overview of key FIWARE security generic enablers for identity management, authorization, and PEP proxy functionality.
WebLogic authentication debugging



WebLogic authentication debuggingMaarten Smeets Login information and group memberships (identity) often are centrally managed in Enterprises. Many systems use this information to, for example, achieve Single Sign On (SSO) functionality. Surprisingly, access to the Weblogic Server Console and applications is often not centrally managed. I will explain why centralizing management of these identities, in addition to increased security, quickly starts reducing operational cost and even increases developer productivity. During a demonstration, I will introduce several methods for debugging authentication using an external authentication provider in order to lower the bar to apply this pattern. This technically oriented presentation is especially useful for people working in operations managing Weblogic Servers.
Shifting security left simplifying security for k8s open shift environments



Shifting security left simplifying security for k8s open shift environmentsLibbySchulze This document discusses securing secrets in Kubernetes. It describes how attackers were able to hijack cloud resources by accessing unprotected credentials stored in a Kubernetes console. It then provides recommendations for securely managing secrets, including using Conjur to establish identity for applications and enforce authorization. It outlines best practices like regularly rotating secrets and removing hard-coded credentials. The document also describes how Conjur can integrate with Kubernetes to verify application identities and issue credentials without exposing secrets.
Securing Microservices using Play and Akka HTTP



Securing Microservices using Play and Akka HTTPRafal Gancarz Going down the microservices route makes a lot of things around creating and maintaining large systems easier but it comes at a cost too, particularly associated with challenges around security. While securing monolithic applications was a relatively well understood area, the same can't be said about microservice based architectures.
This presentation covers how implementing microservices affects the security of distributed systems, outlines pros and cons of several standards and common practices and offers practical suggestions for securing microservice based systems using Play and Akka HTTP.
Securing .NET Core, ASP.NET Core applications



Securing .NET Core, ASP.NET Core applicationsNETUserGroupBern This document discusses securing .NET Core and ASP.NET Core applications. It covers authentication and authorization topics like OpenID Connect, OAuth, sessions, and HTTPS. It provides an overview of authentication flows like OAuth's resource owner credentials flow and OpenID Connect's authorization code flow. It also discusses securing single page applications, Azure managed identities, and using libraries instead of rolling your own security implementation.
FIWARE Training: Identity Management and Access Control



FIWARE Training: Identity Management and Access ControlFIWARE An online training course run by the FIWARE Foundation in conjunction with the i4Trust project and IShare Foundation. The core part of this virtual training camp (27 Jun - 01 Jul 2022) covered all the necessary skills to develop smart solutions powered by FIWARE. It introduces the basis of Digital Twin programming using NGSI-LD (the simple yet powerful open standard API enabling to publish and access digital twin data) combined with common smart data models
In addition, it covers the supplementary FIWARE technologies used to implement the rest of functions typically required when architecting a complete smart solution: Identity and Access Management (IAM) functions to secure access to digital twin data, and functions enabling the interface with IoT and 3rd systems, or the connection with different tools for processing and monitoring current and historic big data.
Extending this core part, the training camp also cover how you can easily integrate FIWARE systems with blockchain networks to create audit-proof logs of processes and ensure transparency.
Access Management for Cloud and Mobile



Access Management for Cloud and MobileForgeRock Presented by Bert Van Beeck, Technical Enablement Lead, ForgeRock at ForgeRock Open Identity Stack Summit, France 2013
Learn more about ForgeRock Access Management:
https://www.forgerock.com/platform/access-management/
Learn more about ForgeRock Identity Management:
https://www.forgerock.com/platform/identity-management/
fluke dealers in bangalore..............



fluke dealers in bangalore..............Haresh Vaswani The Fluke 925 is a vane anemometer, a handheld device designed to measure wind speed, air flow (volume), and temperature. It features a separate sensor and display unit, allowing greater flexibility and ease of use in tight or hard-to-reach spaces. The Fluke 925 is particularly suitable for HVAC (heating, ventilation, and air conditioning) maintenance in both residential and commercial buildings, offering a durable and cost-effective solution for routine airflow diagnostics.
International Journal of Distributed and Parallel systems (IJDPS)



International Journal of Distributed and Parallel systems (IJDPS)samueljackson3773 The growth of Internet and other web technologies requires the development of new
algorithms and architectures for parallel and distributed computing. International journal of
Distributed and parallel systems is a bimonthly open access peer-reviewed journal aims to
publish high quality scientific papers arising from original research and development from
the international community in the areas of parallel and distributed systems. IJDPS serves
as a platform for engineers and researchers to present new ideas and system technology,
with an interactive and friendly, but strongly professional atmosphere.
Ad
More Related Content
Similar to Building an Effective Architecture for Identity and Access Management.pdf (20)
Keycloak for Science Gateways - SGCI Technology Sampler Webinar



Keycloak for Science Gateways - SGCI Technology Sampler Webinarmarcuschristie Using Keycloak to Provide Authentication, Authorization, and Identity Management Services for Your Gateway
Presentation to accompany blog post: https://sciencegateways.org/-/eds-tech-blog-using-keycloak-to-provide-authentication-authorization-and-identity-management-services-for-your-gateway
Self-Service x Hashicorp Vault



Self-Service x Hashicorp VaultMartin Conraux Let's see how we can leverage on Vault capabilities to create a self-service system inside your company
SSL Everywhere!



SSL Everywhere!Simon Haslam SSL, more strictly called Transport Layer Security (TLS), is a means to encrypt data that is in flight between software components, whether within your data center or between that and your end users' devices. This prevents eavesdroppers seeing confidential information, such as credit card numbers or database passwords, and ensures that components are communicating with who they they think they are. So why isn't SSL/TLS used for all electronic communications? Firstly it is, almost by definition, "slightly tricky" to configure and errors are not terribly informative when things don't work (why would you help a hacker?!). Secondly there is a performance overhead for running TLS, although with modern hardware this is probably less of a concern than it used to be.
This session describes how to configure TLS at all layers within a Fusion Middleware stack - from the front-end Oracle HTTP Server, right through to communications with the database.
This platform was first given by Simon Haslam (eProseed UK) and Jacco Landlust (ING) at the OGh Fusion Middleware Experience event in February 2016.
TALK-I-TIVE_PresentatTALK-I-TIVE_Presentation[1][1].pptxion[1][1].pptx![TALK-I-TIVE_PresentatTALK-I-TIVE_Presentation[1][1].pptxion[1][1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation11-250223062925-3471f52a-thumbnail.jpg?width=560&fit=bounds)
![TALK-I-TIVE_PresentatTALK-I-TIVE_Presentation[1][1].pptxion[1][1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation11-250223062925-3471f52a-thumbnail.jpg?width=560&fit=bounds)
![TALK-I-TIVE_PresentatTALK-I-TIVE_Presentation[1][1].pptxion[1][1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation11-250223062925-3471f52a-thumbnail.jpg?width=560&fit=bounds)
![TALK-I-TIVE_PresentatTALK-I-TIVE_Presentation[1][1].pptxion[1][1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation11-250223062925-3471f52a-thumbnail.jpg?width=560&fit=bounds)
TALK-I-TIVE_PresentatTALK-I-TIVE_Presentation[1][1].pptxion[1][1].pptxdosoro7306 TALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptxTALK-I-TIVE_Presentation[1][1].pptx
TALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptx![TALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation1-250223062819-64690da9-thumbnail.jpg?width=560&fit=bounds)
![TALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation1-250223062819-64690da9-thumbnail.jpg?width=560&fit=bounds)
![TALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation1-250223062819-64690da9-thumbnail.jpg?width=560&fit=bounds)
![TALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptx](https://cdn.slidesharecdn.com/ss_thumbnails/talk-i-tivepresentation1-250223062819-64690da9-thumbnail.jpg?width=560&fit=bounds)
TALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptxdosoro7306 TALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptxTALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptxTALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptxTALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptxTALK-I-TIVE_Presensadsdasdasdasdasdasdastation[1].pptx
Introduction to sitecore identity



Introduction to sitecore identityGopikrishna Gujjula This document provides an overview of authentication, authorization, ASP.NET Identity, OAuth, OpenID Connect, and IdentityServer4. It discusses the evolution of user security in ASP.NET, how ASP.NET Identity works with OAuth and OpenID Connect, and the roles of an authorization server and security token service. The agenda indicates it will include a demo of IdentityServer4 configuration and use with a sample Sitecore implementation.
Adding Identity Management and Access Control to your App



Adding Identity Management and Access Control to your AppFIWARE Adding Identity Management and Access Control to your App presentation, by Alvaro Alonso & Cyril Dangerville.
Security Chapter. 1st FIWARE Summit, Málaga Dec. 13-15, 2016.
Managing your secrets in a cloud environment



Managing your secrets in a cloud environmentTaswar Bhatti Managing your secrets in a cloud environment using Azure Key Vault and HashiCorp Vault. Presentation at Update Conference Prague 2018.
Part 5 of the REAL Webinars on Oracle Cloud Native Application Development - ...



Part 5 of the REAL Webinars on Oracle Cloud Native Application Development - ...Lucas Jellema This document announces six virtual developer meetups on cloud native application development on Oracle Cloud Platform. The meetups will cover topics including cloud operations, monitoring, infrastructure as code using Terraform, and native application development. All sessions will include introductions, demonstrations, hands-on labs, and Q&A. Recordings of the sessions will be made available on YouTube. The document provides details on preparing an Oracle Cloud Infrastructure tenancy for the hands-on labs and signing up for a cloud trial.
Web API 2 Token Based Authentication



Web API 2 Token Based Authenticationjeremysbrown This document discusses token based authentication in ASP.NET Web API 2 projects. It covers the basic concepts of token authentication including the roles in OAuth 2.0 of resource owners, clients, authorization servers and resource servers. It also summarizes the different OAuth 2.0 client types, authorization grant types, and development options for implementing token authentication using OWIN middleware or DotNetOpenAuth.
SharePoint Authentication And Authorization SPTechCon San Francisco



SharePoint Authentication And Authorization SPTechCon San FranciscoLiam Cleary [MVP] This document discusses authentication and authorization in SharePoint. It begins with an overview of security concepts like authentication, which verifies a claim of identity, and authorization, which verifies permissions. It then covers authentication options in SharePoint like Windows authentication and claims-based authentication using an identity provider. The document also discusses authorization and role providers, custom identity providers, and Azure Access Control Service. It emphasizes configuring authorization correctly after authentication and expecting security issues to arise.
Building IAM for OpenStack



Building IAM for OpenStackSteve Martinelli Building IAM for OpenStack, presented at CIS (Cloud Identity Summit) 2015.
Discuss Identity Sources, Authentication, Managing Access and Federating Identities
Intro to Apache Shiro



Intro to Apache ShiroClaire Hunsaker Apache Shiro, a simple easy-to-use framework to enforce user security by Shiro PMC Chair and Stormpath CTO, Les Hazlewood.
http://shiro.apache.org
http://stormpath.com
Adding identity management and access control to your app



Adding identity management and access control to your appÁlvaro Alonso González The document discusses OAuth 2.0 and authorization. It describes OAuth 2.0 as a mechanism for applications to access restricted resources without sharing credentials. It outlines the roles in OAuth 2.0 including resource owner, resource server, client, and authorization server. It also describes the different OAuth 2.0 grant types including authorization code, implicit, resource owner password credentials, and client credentials. The document then discusses using OAuth 2.0 and PEP proxies to secure web applications and backends as well as authenticating IoT devices. It also provides an overview of key FIWARE security generic enablers for identity management, authorization, and PEP proxy functionality.
WebLogic authentication debugging



WebLogic authentication debuggingMaarten Smeets Login information and group memberships (identity) often are centrally managed in Enterprises. Many systems use this information to, for example, achieve Single Sign On (SSO) functionality. Surprisingly, access to the Weblogic Server Console and applications is often not centrally managed. I will explain why centralizing management of these identities, in addition to increased security, quickly starts reducing operational cost and even increases developer productivity. During a demonstration, I will introduce several methods for debugging authentication using an external authentication provider in order to lower the bar to apply this pattern. This technically oriented presentation is especially useful for people working in operations managing Weblogic Servers.
Shifting security left simplifying security for k8s open shift environments



Shifting security left simplifying security for k8s open shift environmentsLibbySchulze This document discusses securing secrets in Kubernetes. It describes how attackers were able to hijack cloud resources by accessing unprotected credentials stored in a Kubernetes console. It then provides recommendations for securely managing secrets, including using Conjur to establish identity for applications and enforce authorization. It outlines best practices like regularly rotating secrets and removing hard-coded credentials. The document also describes how Conjur can integrate with Kubernetes to verify application identities and issue credentials without exposing secrets.
Securing Microservices using Play and Akka HTTP



Securing Microservices using Play and Akka HTTPRafal Gancarz Going down the microservices route makes a lot of things around creating and maintaining large systems easier but it comes at a cost too, particularly associated with challenges around security. While securing monolithic applications was a relatively well understood area, the same can't be said about microservice based architectures.
This presentation covers how implementing microservices affects the security of distributed systems, outlines pros and cons of several standards and common practices and offers practical suggestions for securing microservice based systems using Play and Akka HTTP.
Securing .NET Core, ASP.NET Core applications



Securing .NET Core, ASP.NET Core applicationsNETUserGroupBern This document discusses securing .NET Core and ASP.NET Core applications. It covers authentication and authorization topics like OpenID Connect, OAuth, sessions, and HTTPS. It provides an overview of authentication flows like OAuth's resource owner credentials flow and OpenID Connect's authorization code flow. It also discusses securing single page applications, Azure managed identities, and using libraries instead of rolling your own security implementation.
FIWARE Training: Identity Management and Access Control



FIWARE Training: Identity Management and Access ControlFIWARE An online training course run by the FIWARE Foundation in conjunction with the i4Trust project and IShare Foundation. The core part of this virtual training camp (27 Jun - 01 Jul 2022) covered all the necessary skills to develop smart solutions powered by FIWARE. It introduces the basis of Digital Twin programming using NGSI-LD (the simple yet powerful open standard API enabling to publish and access digital twin data) combined with common smart data models
In addition, it covers the supplementary FIWARE technologies used to implement the rest of functions typically required when architecting a complete smart solution: Identity and Access Management (IAM) functions to secure access to digital twin data, and functions enabling the interface with IoT and 3rd systems, or the connection with different tools for processing and monitoring current and historic big data.
Extending this core part, the training camp also cover how you can easily integrate FIWARE systems with blockchain networks to create audit-proof logs of processes and ensure transparency.
Access Management for Cloud and Mobile



Access Management for Cloud and MobileForgeRock Presented by Bert Van Beeck, Technical Enablement Lead, ForgeRock at ForgeRock Open Identity Stack Summit, France 2013
Learn more about ForgeRock Access Management:
https://www.forgerock.com/platform/access-management/
Learn more about ForgeRock Identity Management:
https://www.forgerock.com/platform/identity-management/
Recently uploaded (20)
fluke dealers in bangalore..............



fluke dealers in bangalore..............Haresh Vaswani The Fluke 925 is a vane anemometer, a handheld device designed to measure wind speed, air flow (volume), and temperature. It features a separate sensor and display unit, allowing greater flexibility and ease of use in tight or hard-to-reach spaces. The Fluke 925 is particularly suitable for HVAC (heating, ventilation, and air conditioning) maintenance in both residential and commercial buildings, offering a durable and cost-effective solution for routine airflow diagnostics.
International Journal of Distributed and Parallel systems (IJDPS)



International Journal of Distributed and Parallel systems (IJDPS)samueljackson3773 The growth of Internet and other web technologies requires the development of new
algorithms and architectures for parallel and distributed computing. International journal of
Distributed and parallel systems is a bimonthly open access peer-reviewed journal aims to
publish high quality scientific papers arising from original research and development from
the international community in the areas of parallel and distributed systems. IJDPS serves
as a platform for engineers and researchers to present new ideas and system technology,
with an interactive and friendly, but strongly professional atmosphere.
Data Structures_Introduction to algorithms.pptx



Data Structures_Introduction to algorithms.pptxRushaliDeshmukh2 Concept of Problem Solving, Introduction to Algorithms, Characteristics of Algorithms, Introduction to Data Structure, Data Structure Classification (Linear and Non-linear, Static and Dynamic, Persistent and Ephemeral data structures), Time complexity and Space complexity, Asymptotic Notation - The Big-O, Omega and Theta notation, Algorithmic upper bounds, lower bounds, Best, Worst and Average case analysis of an Algorithm, Abstract Data Types (ADT)
"Feed Water Heaters in Thermal Power Plants: Types, Working, and Efficiency G...



"Feed Water Heaters in Thermal Power Plants: Types, Working, and Efficiency G...Infopitaara A feed water heater is a device used in power plants to preheat water before it enters the boiler. It plays a critical role in improving the overall efficiency of the power generation process, especially in thermal power plants.
🔧 Function of a Feed Water Heater:
It uses steam extracted from the turbine to preheat the feed water.
This reduces the fuel required to convert water into steam in the boiler.
It supports Regenerative Rankine Cycle, increasing plant efficiency.
🔍 Types of Feed Water Heaters:
Open Feed Water Heater (Direct Contact)
Steam and water come into direct contact.
Mixing occurs, and heat is transferred directly.
Common in low-pressure stages.
Closed Feed Water Heater (Surface Type)
Steam and water are separated by tubes.
Heat is transferred through tube walls.
Common in high-pressure systems.
⚙️ Advantages:
Improves thermal efficiency.
Reduces fuel consumption.
Lowers thermal stress on boiler components.
Minimizes corrosion by removing dissolved gases.
Data Structures_Searching and Sorting.pptx



Data Structures_Searching and Sorting.pptxRushaliDeshmukh2 Sorting Order and Stability in Sorting.
Concept of Internal and External Sorting.
Bubble Sort,
Insertion Sort,
Selection Sort,
Quick Sort and
Merge Sort,
Radix Sort, and
Shell Sort,
External Sorting, Time complexity analysis of Sorting Algorithms.
RICS Membership-(The Royal Institution of Chartered Surveyors).pdf



RICS Membership-(The Royal Institution of Chartered Surveyors).pdfMohamedAbdelkader115 Glad to be one of only 14 members inside Kuwait to hold this credential.
Please check the members inside kuwait from this link:
https://www.rics.org/networking/find-a-member.html?firstname=&lastname=&town=&country=Kuwait&member_grade=(AssocRICS)&expert_witness=&accrediation=&page=1
Introduction to FLUID MECHANICS & KINEMATICS



Introduction to FLUID MECHANICS & KINEMATICSnarayanaswamygdas Fluid mechanics is the branch of physics concerned with the mechanics of fluids (liquids, gases, and plasmas) and the forces on them. Originally applied to water (hydromechanics), it found applications in a wide range of disciplines, including mechanical, aerospace, civil, chemical, and biomedical engineering, as well as geophysics, oceanography, meteorology, astrophysics, and biology.
It can be divided into fluid statics, the study of various fluids at rest, and fluid dynamics.
Fluid statics, also known as hydrostatics, is the study of fluids at rest, specifically when there's no relative motion between fluid particles. It focuses on the conditions under which fluids are in stable equilibrium and doesn't involve fluid motion.
Fluid kinematics is the branch of fluid mechanics that focuses on describing and analyzing the motion of fluids, such as liquids and gases, without considering the forces that cause the motion. It deals with the geometrical and temporal aspects of fluid flow, including velocity and acceleration. Fluid dynamics, on the other hand, considers the forces acting on the fluid.
Fluid dynamics is the study of the effect of forces on fluid motion. It is a branch of continuum mechanics, a subject which models matter without using the information that it is made out of atoms; that is, it models matter from a macroscopic viewpoint rather than from microscopic.
Fluid mechanics, especially fluid dynamics, is an active field of research, typically mathematically complex. Many problems are partly or wholly unsolved and are best addressed by numerical methods, typically using computers. A modern discipline, called computational fluid dynamics (CFD), is devoted to this approach. Particle image velocimetry, an experimental method for visualizing and analyzing fluid flow, also takes advantage of the highly visual nature of fluid flow.
Fundamentally, every fluid mechanical system is assumed to obey the basic laws :
Conservation of mass
Conservation of energy
Conservation of momentum
The continuum assumption
For example, the assumption that mass is conserved means that for any fixed control volume (for example, a spherical volume)—enclosed by a control surface—the rate of change of the mass contained in that volume is equal to the rate at which mass is passing through the surface from outside to inside, minus the rate at which mass is passing from inside to outside. This can be expressed as an equation in integral form over the control volume.
The continuum assumption is an idealization of continuum mechanics under which fluids can be treated as continuous, even though, on a microscopic scale, they are composed of molecules. Under the continuum assumption, macroscopic (observed/measurable) properties such as density, pressure, temperature, and bulk velocity are taken to be well-defined at "infinitesimal" volume elements—small in comparison to the characteristic length scale of the system, but large in comparison to molecular length scale
Level 1-Safety.pptx Presentation of Electrical Safety



Level 1-Safety.pptx Presentation of Electrical SafetyJoseAlbertoCariasDel Level 1-Safety.pptx Presentation of Electrical Safety
The Gaussian Process Modeling Module in UQLab



The Gaussian Process Modeling Module in UQLabJournal of Soft Computing in Civil Engineering We introduce the Gaussian process (GP) modeling module developed within the UQLab software framework. The novel design of the GP-module aims at providing seamless integration of GP modeling into any uncertainty quantification workflow, as well as a standalone surrogate modeling tool. We first briefly present the key mathematical tools on the basis of GP modeling (a.k.a. Kriging), as well as the associated theoretical and computational framework. We then provide an extensive overview of the available features of the software and demonstrate its flexibility and user-friendliness. Finally, we showcase the usage and the performance of the software on several applications borrowed from different fields of engineering. These include a basic surrogate of a well-known analytical benchmark function; a hierarchical Kriging example applied to wind turbine aero-servo-elastic simulations and a more complex geotechnical example that requires a non-stationary, user-defined correlation function. The GP-module, like the rest of the scientific code that is shipped with UQLab, is open source (BSD license).
some basics electrical and electronics knowledge



some basics electrical and electronics knowledgenguyentrungdo88 This chapter discribe about common electrical divices such as passive component, the internaltional system unit and international system prefixes.
Process Parameter Optimization for Minimizing Springback in Cold Drawing Proc...



Process Parameter Optimization for Minimizing Springback in Cold Drawing Proc...Journal of Soft Computing in Civil Engineering In tube drawing process, a tube is pulled out through a die and a plug to reduce its diameter and thickness as per the requirement. Dimensional accuracy of cold drawn tubes plays a vital role in the further quality of end products and controlling rejection in manufacturing processes of these end products. Springback phenomenon is the elastic strain recovery after removal of forming loads, causes geometrical inaccuracies in drawn tubes. Further, this leads to difficulty in achieving close dimensional tolerances. In the present work springback of EN 8 D tube material is studied for various cold drawing parameters. The process parameters in this work include die semi-angle, land width and drawing speed. The experimentation is done using Taguchi’s L36 orthogonal array, and then optimization is done in data analysis software Minitab 17. The results of ANOVA shows that 15 degrees die semi-angle,5 mm land width and 6 m/min drawing speed yields least springback. Furthermore, optimization algorithms named Particle Swarm Optimization (PSO), Simulated Annealing (SA) and Genetic Algorithm (GA) are applied which shows that 15 degrees die semi-angle, 10 mm land width and 8 m/min drawing speed results in minimal springback with almost 10.5 % improvement. Finally, the results of experimentation are validated with Finite Element Analysis technique using ANSYS.
Development of MLR, ANN and ANFIS Models for Estimation of PCUs at Different ...



Development of MLR, ANN and ANFIS Models for Estimation of PCUs at Different ...Journal of Soft Computing in Civil Engineering Passenger car unit (PCU) of a vehicle type depends on vehicular characteristics, stream characteristics, roadway characteristics, environmental factors, climate conditions and control conditions. Keeping in view various factors affecting PCU, a model was developed taking a volume to capacity ratio and percentage share of particular vehicle type as independent parameters. A microscopic traffic simulation model VISSIM has been used in present study for generating traffic flow data which some time very difficult to obtain from field survey. A comparison study was carried out with the purpose of verifying when the adaptive neuro-fuzzy inference system (ANFIS), artificial neural network (ANN) and multiple linear regression (MLR) models are appropriate for prediction of PCUs of different vehicle types. From the results observed that ANFIS model estimates were closer to the corresponding simulated PCU values compared to MLR and ANN models. It is concluded that the ANFIS model showed greater potential in predicting PCUs from v/c ratio and proportional share for all type of vehicles whereas MLR and ANN models did not perform well.
railway wheels, descaling after reheating and before forging



railway wheels, descaling after reheating and before forgingJavad Kadkhodapour railway wheels, descaling after reheating and before forging
Fort night presentation new0903 pdf.pdf.



Fort night presentation new0903 pdf.pdf.anuragmk56 This is the document of fortnight review progress meeting
15th International Conference on Computer Science, Engineering and Applicatio...



15th International Conference on Computer Science, Engineering and Applicatio...IJCSES Journal #computerscience #programming #coding #technology #programmer #python #computer #developer #tech #coder #javascript #java #codinglife #html #code #softwaredeveloper #webdeveloper #software #cybersecurity #linux #computerengineering #webdevelopment #softwareengineer #machinelearning #hacking #engineering #datascience #css #programmers #pythonprogramming
Process Parameter Optimization for Minimizing Springback in Cold Drawing Proc...



Process Parameter Optimization for Minimizing Springback in Cold Drawing Proc...Journal of Soft Computing in Civil Engineering
Development of MLR, ANN and ANFIS Models for Estimation of PCUs at Different ...



Development of MLR, ANN and ANFIS Models for Estimation of PCUs at Different ...Journal of Soft Computing in Civil Engineering
Ad
Building an Effective Architecture for Identity and Access Management.pdf
- 1. Building an Effective Architecture for Identity and Access Management JorgeAlvarez [email protected] GitHub: @jealvarez Twitter: @edlask8
- 2. Disclaimer The point of views, thoughts and opinions expressed in this presentation belongs only to the presenter and not necessarily to the presenter’s employer, organization, committee or other group or individual.
- 3. About Me
- 4. Agenda • Challenges • Keycloak Overview • Why shouldI use Keycloak? • CoreConcepts • TechnologyStack • Server Architecture • Single Sign-on/ Single Logout • Tokens • Calling Backing Services • Supported Platforms • Demo • Summary • Bibliography
- 5. Challenges
- 7. The old way • Securing monolithic web application relatively easy • Username and Password • Credentials verified against table in database • HTTP Session stores in security context User Interface Logic Data
- 8. The new way • Multiple applications • Multiple variants of each application • Multiple services • Multiple logins • Multiple databases • Multiple devices
- 13. Are you lookingfor a single sign-on solutionthatenables you to secure newor legacy applicationsandeasilyuse federatedidentityproviders such as socialnetworks?
- 14. You should look at Keycloak
- 17. Project • Java based AuthN and AuthZ server • Started in 2013 • Current Version 11.0.3 • ~ Every 5 weeks • Commercial Offering Available • Red Hat SSO • Have you logged into developers.redhat.com or www.openshift.com? • Community • 400+ Contributors • Very robust, good documentation, many examples
- 18. Why should I use Keycloak?
- 19. Features (1/3) • Support multiple database engines Adaptability • Social networking logins • Federation • LDAP • Active Directory • Adapters for different frameworks • Spring • NodeJS • NetCore • … Integration
- 20. Features (2/3) • Clustering Scalability • Keycloak Service Provider Interface • Enables to implement your own authenticatoror federator Extensibility • Session management • Force logouts • Determine how many sessions your system currently has Centralization Features
- 21. Features (3/3)
- 22. Core Concepts
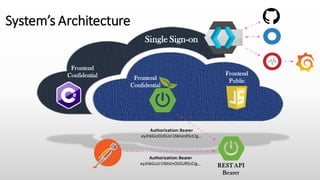
- 24. Technology Stack
- 25. Technology Stack Admin Console ❖ AngularJS ❖ React ❖ PatternFly ❖ Bootstrap Keycloak Server ❖ WildFly ❖ JPA ❖ RestEasy ❖ Freemarker ❖ Arquillian ❖ Infinispan
- 27. Keycloak 2 Keycloak1 SSO Protocols Protocol Mapper Infinispan Events Social Login User Storage JPA User Federation Realm Clients, Users, AuthN, AuthZ, Policies, … Account Login Identity Brokering Sessions Realms Settings … Replication Infinispan HTTP Endpoint
- 28. Single Sign-on How it works?
- 29. Single Sign-on • Login only once to access all applications SSO • OpenID Connect • Build on top of OAuth2 Standardized Protocols • Logouts can be propagated to applications Support for Single Logout
- 30. Tokens are associatedwith a session Unauthenticated User Unauthenticated user accesses to Application 1 Application redirectsto Keycloak 2 User submits credentials 2.1 Credentials 2.2 Keycloak creates SSO Session and Emits Cookies Generates Code and redirects the user back to the Application 3 Application exchangesCode to Tokens 4 Application verifies receivedTokens 5 User is signed-in to the application 6 1 2.2 2.1 5 3 2 4 6
- 31. Generates Code Keycloak detects SSO Session 9 Authenticated User … Authenticateduse accesses other application 7 Other application redirects user to Keycloak to sign-in 8 Other application exchangescode for tokens 10 Other application verifies receivedtokens 11 7 11 9 8 10 12 Redirectsto other application Tokens are associatedwith a session User is signed-in to the other application 12
- 32. Keycloak creates logout request to another application 3 Single Logout User initiates logout 1 Application creates logoutrequest to Keycloak 2 Keycloak terminates session 4 2 4 1 Application returns response logout to Keycloak 3.1 Applicationsdo logout 5 2.1 3.1 3 5 5 Keycloak returns response logout to the application 2.1
- 33. Tokens Overview
- 34. Essential Token Types • Access Token • Short lived [Minutes+] • Used for accessingresources • RefreshToken • Long lived [Hours+] • Used for requestingnew tokens • ID Token • Containsuser information(OIDC) • Offline Token • Long lived [Days+] • Refreshtoken that never expires
- 35. Keycloak Tokens • OAuth2 / OpenID Connect • Signed self-contained JWT • Claims • Key-Value Pairs + User Information + Metadata • Issued by Keycloak • Signed with Realm Private Key • Verified with Realm • Realm Public Key • Limited lifespan • Can be revoked
- 36. JSON Web Tokens <header-base64>. <payload-base64>. <signature-base64> Note Base64 means Encoding Encoding != Encryption
- 38. The backend looks up the Realm Public Key in cache with the kid from the JWT 3 Calling Backend Services Authenticateduse accesses to the application 1 Application uses the access token in the http header to access to the backend 2 The backend verifies signature of the access token with the Realm Public Key 4 2 4 1 The backend grants access and returns data 5 If not found, then fetch Public Key with kid from Keycloak 3.1 Keycloak returnsRealm Public Key 3.2 The applicationcan displaythe data 6 Authorization:Bearer eyJhbGciOiJSUzI1NiIsInR5cCIg… 5 3 3.1 3.2 6 kid public key access token data User can access to the data 7 7
- 44. Summary
- 45. Summary (1/2) • Unzip and Run • Docker Images So easy to get started with • Single Sign-on • Single Logout • Federation • User Management • Social Logins • … Provides many features out of the box
- 46. Summary (2/2) Build on proven a robust standards • OAuth 2.0 • OpenID Connect 1.0 • SAML2.0 Extensible • Custom • Authenticationmechanisms • Event Listeners • Themes • … Easy to integrate • Adapters available for different frameworks …
- 47. Bibliography
- 49. Email: [email protected] Github: @jealvarez Twitter: @edlask8




