BuildingSecurity Audits with Extended Events
0 likes2,623 views
The document discusses using Extended Events in SQL Server to perform security audits. It describes the components of Extended Events including events, actions, predicates, targets, and packages. It then provides examples of how to build audits to track logins and queries, demonstrating how to capture useful security information without invasive monitoring. Templates are shown for login and query audits that can be directed to file, ring buffer, or event stream targets.
1 of 39
Downloaded 28 times





































Ad
Recommended
Implementing Auditing in SQL Server



Implementing Auditing in SQL ServerDavid Dye This document provides an overview of implementing SQL auditing in SQL Server. It discusses creating a server audit to define how audit data is stored, creating server audit specifications to capture server-level events, and creating database audit specifications to capture database-level events for specific objects and principals. Examples are provided of creating audits using SQL Server Management Studio and Transact-SQL.
5 Amazing Reasons DBAs Need to Love Extended Events



5 Amazing Reasons DBAs Need to Love Extended EventsJason Strate Extended events provide DBAs with a powerful tool that can be used to troubleshoot and investigate SQL Server. Throughout this session, you’ll walk through five great reasons, with demos. By the end of the webcast, you’ll be itching to grab the scripts from the demos to start building your own extended event sessions today.
Icinga Camp Bangalore - Enterprise exceptions 



Icinga Camp Bangalore - Enterprise exceptions Icinga This document discusses the expectations and challenges of monitoring solutions for large enterprises with heterogeneous IT infrastructures. It notes that proprietary tools from major vendors can be costly and inflexible, causing organizations to use multiple tools. It advocates for an open-source, standards-based solution like ICINGA that provides consolidation of tools, integration, agility, automation, and cost control. Specific requirements outlined for mainframes, databases, applications, transactions, and typical enterprise components. The document calls for ICINGA to provide a standardized framework, implementation examples, and demonstration platform to effectively communicate its capabilities for large-scale enterprise monitoring.
Icinga Camp Bangalore - Icinga and Icinga Director 



Icinga Camp Bangalore - Icinga and Icinga Director Icinga This document discusses Icinga Director, a new configuration tool for Icinga 2. It aims to make configuration easy for end users by offering interfaces to other tools and avoiding writing config files. The document outlines requirements, installation, basics of templates and objects, custom data fields and lists, services, imports from external resources, and integrations. It encourages providing feedback on Icinga Director.
10 Tips to Pump Up Your Atlassian Performance



10 Tips to Pump Up Your Atlassian PerformanceAtlassian Hans and Franz are here to pump YOU up. Well, pump your Atlassian tools up, that is. Has your JIRA slowed down? Does your Confluence fall over and can't get back up? We're here to give you some tactical tips on how to take your performance to the next level. We'll reveal best practices from Atlassian support's secret arsenal, teach you how to configure JIRA, Confluence, and other products to get the most out of your system, and focus on small and easy changes that you can implement quickly.
Presto: Fast SQL on Everything



Presto: Fast SQL on EverythingDavid Phillips Presto is an open source distributed SQL query engine that was originally developed by Facebook. It allows for fast SQL queries on large datasets across multiple data sources. Presto uses various optimizations like code generation, predicate pushdown, and data layout awareness to improve query performance. It is used at Facebook and other companies for interactive analytics, batch ETL, A/B testing, and app analytics where low latency and high concurrency are important.
Redash: Open Source SQL Analytics on Data Lakes



Redash: Open Source SQL Analytics on Data LakesDatabricks Learn more about Redash from our summit keynote during this product walkthrough. Redash makes it easy to explore, query, visualize, and share data.
SPSVienna Office 365 Tenant to Tenant Migration - a complete Survial Guide



SPSVienna Office 365 Tenant to Tenant Migration - a complete Survial GuideStephan Bisser - The document discusses Office 365 tenant to tenant migration and provides guidance on scenarios companies may face when migrating tenants, such as mergers or spin-offs.
- It outlines the key components that can be migrated including Azure Active Directory, Exchange Online, SharePoint Online, and Skype for Business Online. Permissions must also be migrated.
- Third party tools are recommended for migrating components like Exchange Online and SharePoint Online due to limitations in Microsoft's native migration capabilities. Planning and testing are important to a successful migration.
Community and Java EE @ DevConf.CZ



Community and Java EE @ DevConf.CZMarkus Eisele The document discusses Java EE specifications and the Java Community Process (JCP) for developing specifications. It describes the roles of expert groups and specification leads in developing specs, as well as the reference implementation, test cases, and documentation that are produced. It also provides statistics on participation in the JCP and links to resources for getting involved in the process.
Introduction to Event Sourcing



Introduction to Event SourcingJeffrey T. Fritz Presentation slides from sessions discussing Event Source data storage and read-model projections.
Source code from demos at: https://bitbucket.org/csharpfritz/nerddinner-cqrs
The (not so) Dark Art of Atlassian Performance Tuning



The (not so) Dark Art of Atlassian Performance Tuningcolleenfry The document discusses performance tuning for Atlassian products. It covers identifying performance issues, analyzing where time is spent, and making improvements to infrastructure, Java settings, Atlassian configuration, and more. The key steps are to build a usage profile, understand what affects performance, and apply a methodical approach to find and address bottlenecks.
Can Your Mobile Infrastructure Survive 1 Million Concurrent Users?



Can Your Mobile Infrastructure Survive 1 Million Concurrent Users?TechWell When you’re building the next killer mobile app, how can you ensure that your app is both stable and capable of near-instant data updates? The answer: Build a backend! Siva Katir says that there’s much more to building a backend than standing up a SQL server in your datacenter and calling it a day. Since different types of apps demand different backend services, how do you know what sort of backend you need? And, more importantly, how can you ensure that your backend scales so you can survive an explosion of users when you are featured in the app store? Siva discusses the common scenarios facing mobile app developers looking to expand beyond just the device. He’ll share best practices learned while building the PlayFab and other companies’ backends. Join Siva to learn how you can ensure that your app can scale safely and affordably into the millions of concurrent users and across multiple platforms.
Docker in the Enterprise



Docker in the EnterpriseSaul Caganoff Docker right now provides great value in the enterprise but the value proposition is more about developer productivity than scale-out.
Docker benefits include resource management, environment management, continuous delivery, developer and operations collaboration, and hybrid workloads.
Take care in its introduction. Consider Docker as just part of an overall toolkit and you don't need to go "full stack" to gain value.
Introduction à Application Insights



Introduction à Application InsightsMSDEVMTL This document provides an overview of Application Insights and how to use it. It discusses what Application Insights is, what can be done with it, how to add it to an Azure subscription, and how to instrument applications manually or automatically. It also covers managing access, reading data, using analytics, and points to additional documentation. The document gives high-level information on Application Insights and demonstrates some of its basic features.
Hexagonal Architecture using Grails



Hexagonal Architecture using GrailsDavid Dawson Instead of following the normal data centric structure in Grails, this presentation describes implementing a highly decoupled, communication centric architecture in Grails.
Intro to Node.js (German)



Intro to Node.js (German)Daniel Khan This document discusses Node.js and digital transformation. It notes that Node.js is used by companies like Netflix, Tinder, and NASA. Node.js complements existing systems and its uses include authentication, authorization, data transformation, and presentation of HTML. Node.js is well-suited for modern web applications that need to gather and push real-time data from different sources to many clients. Its advantages include using JavaScript, asynchronous and non-blocking I/O, and the V8 JavaScript engine. However, it is not suitable for CPU-intensive tasks.
What is Nagios XI and how is it different from Nagios Core



What is Nagios XI and how is it different from Nagios CoreSanjay Willie Simple information for businesses on the features and functionalities of Nagios XI with focus on comparing it with Nagios Core.
Achieving cyber mission assurance with near real-time impact

Achieving cyber mission assurance with near real-time impactElasticsearch See how Elastic and ECS support the Mission Assurance Decision Support System (MADSS) program for the Navy with observability, data enrichment, and powerful search in a containerized environment. By correlating data from diverse sources using web-based services and secure, automated data transformation services, MADSS improves responsiveness, predictions, and event analysis for critical network and infrastructure outages.
Database projects within visual studio



Database projects within visual studioRonnie Hicks Using Database Projects within Visual Studio (thanks to SQL Server Data Tools) can help bridge a gap between developers who need to test their applications against database changes they need and Database Administrators who like to safeguard their servers. This slide deck was used as part of Days of Dot Net 2014 by Ronnie Hicks for his presentation, and contains useful information for getting started with database projects.
Jeremy Engle's slides from Redshift / Big Data meetup on July 13, 2017



Jeremy Engle's slides from Redshift / Big Data meetup on July 13, 2017AWS Chicago "Strategies for supporting near real time analytics, OLAP, and interactive data exploration" - Dr. Jeremy Engle, Engineering Manager Data Team at Jellyvision
Monitoring as Code - Ignite



Monitoring as Code - IgniteIcinga Icinga is a scalable and extensible monitoring system that checks resource availability, notifies users of outages, and provides metrics. It uses an object-based configuration language to define hosts, services, rules, conditions, loops and custom functions. Configurations can be imported from various sources and managed through a RESTful API or web interface. Icinga Director allows importing configurations from multiple sources, deploying them hands-free with versioning and audit logging.
The Modern Data Team for the Modern Data Stack: dbt and the Role of the Analy...



The Modern Data Team for the Modern Data Stack: dbt and the Role of the Analy...Databricks A traditional data team has roles including data engineer, data scientist, and data analyst. However, many organizations are finding success by integrating a new role – the analytics engineer. The analytics engineer develops a code-based data infrastructure that can serve both analytics and data science teams. He or she develops re-usable data models using the software engineering practices of version control and unit testing, and provides the critical domain expertise that ensures that data products are relevant and insightful. In this talk we’ll talk about the role and skill set of the analytics engineer, and discuss how dbt, an open source programming environment, empowers anyone with a SQL skillset to fulfill this new role on the data team. We’ll demonstrate how to use dbt to build version-controlled data models on top of Delta Lake, test both the code and our assumptions about the underlying data, and orchestrate complete data pipelines on Apache Spark™.
I2 - SharePoint Hybrid Search Start to Finish - Thomas Vochten



I2 - SharePoint Hybrid Search Start to Finish - Thomas VochtenSPS Paris One of the most compelling additions to a SharePoint practitioner’s toolbox is hybrid search. Although hybrid search capabilities were already around for a few years, with the introduction of the “Cloud Search Service Application” things got a lot more interesting. This demo-heavy session will focus on the technical implementation details and their prerequisites, as well as the typical hurdles that you’ll face in your first hybrid search project.
SSIS Monitoring Deep Dive



SSIS Monitoring Deep DiveDavide Mauri In this session we'll see everything interesting is hidden in the SSISDB database, where you can gain a lot of insight on the outcome, the performance and the status of your SSIS Packages. I'll share everything I've learned building the SSIS Dashboard we're actually using in production and that you can test here http://ssis-dashboard.azurewebsites.net/. We’ll see the internals of SSISDB database, how we can add custom logging information and how we can use all these data in order to know exactly what happened on a specific point in time.
Anypoint platform for api



Anypoint platform for apiKrishna_in Anypoint Platform for APIs and Anypoint Data Gateway allow integration of data between legacy systems and Salesforce. Anypoint Data Gateway installs as a Salesforce app and provides a point-and-click interface to access external data sources like SAP, Oracle, and SQL from within Salesforce. It supports instant connection to external systems by configuring host, user, etc. parameters and publishing the gateway to specified entities.
TechDays NL 2016 - Building your scalable secure IoT Solution on Azure



TechDays NL 2016 - Building your scalable secure IoT Solution on AzureTom Kerkhove The Internet-of-Things was one of the big hypes in 2015 but it’s more than that – Customers want to build out their own infrastructures and act on their data.
Today we’ll look at how Microsoft Azure helps us to build scalable solutions to process events from thousands of devices in a secure manner and the challenges it has. Once the data is in the cloud we’ll also take a look at ways we can learn from our measurements.
20160317 lagom sf scala



20160317 lagom sf scalashinolajla The document discusses microservices and the Lagom framework. It provides an overview of what microservices are and the goals they aim to achieve, such as accelerating teams, reducing dependencies, and increasing application throughput. It then outlines several principles for microservices, including isolation, asynchronous APIs, immutable deployments, and exposing simplified APIs. Finally, it describes key aspects of the Lagom framework, which supports building microservices, such as its service and persistence APIs, development environment, and production environment using Lightbend Reactive Platform.
Better Search and Business Analytics at Southern Glazer’s Wine & Spirits



Better Search and Business Analytics at Southern Glazer’s Wine & SpiritsElasticsearch See how Southern Glazer’s Wine & Spirits architected their system to deliver a better search and ordering experience, plus how they centrally manage all Elasticsearch deployments on Elastic Cloud Enterprise.
Make your Azure PaaS Deployment More Safe



Make your Azure PaaS Deployment More SafeThuan Ng This presentation targets to guiding security expert and developer to protect PaaS deployment to eliminate security threats. This also introduces Threat Modeling.
Introduction to SQL Server Security



Introduction to SQL Server SecurityJason Strate This document discusses securing Microsoft SQL Server. It covers securing the SQL Server installation, controlling access to the server and databases, and validating security. Key points include using least privilege for service accounts, controlling access through logins, roles and permissions, auditing with SQL Server Audit and Policy Based Management, and services available from Pragmatic Works related to SQL Server security, training and products.
Ad
More Related Content
What's hot (20)
Community and Java EE @ DevConf.CZ



Community and Java EE @ DevConf.CZMarkus Eisele The document discusses Java EE specifications and the Java Community Process (JCP) for developing specifications. It describes the roles of expert groups and specification leads in developing specs, as well as the reference implementation, test cases, and documentation that are produced. It also provides statistics on participation in the JCP and links to resources for getting involved in the process.
Introduction to Event Sourcing



Introduction to Event SourcingJeffrey T. Fritz Presentation slides from sessions discussing Event Source data storage and read-model projections.
Source code from demos at: https://bitbucket.org/csharpfritz/nerddinner-cqrs
The (not so) Dark Art of Atlassian Performance Tuning



The (not so) Dark Art of Atlassian Performance Tuningcolleenfry The document discusses performance tuning for Atlassian products. It covers identifying performance issues, analyzing where time is spent, and making improvements to infrastructure, Java settings, Atlassian configuration, and more. The key steps are to build a usage profile, understand what affects performance, and apply a methodical approach to find and address bottlenecks.
Can Your Mobile Infrastructure Survive 1 Million Concurrent Users?



Can Your Mobile Infrastructure Survive 1 Million Concurrent Users?TechWell When you’re building the next killer mobile app, how can you ensure that your app is both stable and capable of near-instant data updates? The answer: Build a backend! Siva Katir says that there’s much more to building a backend than standing up a SQL server in your datacenter and calling it a day. Since different types of apps demand different backend services, how do you know what sort of backend you need? And, more importantly, how can you ensure that your backend scales so you can survive an explosion of users when you are featured in the app store? Siva discusses the common scenarios facing mobile app developers looking to expand beyond just the device. He’ll share best practices learned while building the PlayFab and other companies’ backends. Join Siva to learn how you can ensure that your app can scale safely and affordably into the millions of concurrent users and across multiple platforms.
Docker in the Enterprise



Docker in the EnterpriseSaul Caganoff Docker right now provides great value in the enterprise but the value proposition is more about developer productivity than scale-out.
Docker benefits include resource management, environment management, continuous delivery, developer and operations collaboration, and hybrid workloads.
Take care in its introduction. Consider Docker as just part of an overall toolkit and you don't need to go "full stack" to gain value.
Introduction à Application Insights



Introduction à Application InsightsMSDEVMTL This document provides an overview of Application Insights and how to use it. It discusses what Application Insights is, what can be done with it, how to add it to an Azure subscription, and how to instrument applications manually or automatically. It also covers managing access, reading data, using analytics, and points to additional documentation. The document gives high-level information on Application Insights and demonstrates some of its basic features.
Hexagonal Architecture using Grails



Hexagonal Architecture using GrailsDavid Dawson Instead of following the normal data centric structure in Grails, this presentation describes implementing a highly decoupled, communication centric architecture in Grails.
Intro to Node.js (German)



Intro to Node.js (German)Daniel Khan This document discusses Node.js and digital transformation. It notes that Node.js is used by companies like Netflix, Tinder, and NASA. Node.js complements existing systems and its uses include authentication, authorization, data transformation, and presentation of HTML. Node.js is well-suited for modern web applications that need to gather and push real-time data from different sources to many clients. Its advantages include using JavaScript, asynchronous and non-blocking I/O, and the V8 JavaScript engine. However, it is not suitable for CPU-intensive tasks.
What is Nagios XI and how is it different from Nagios Core



What is Nagios XI and how is it different from Nagios CoreSanjay Willie Simple information for businesses on the features and functionalities of Nagios XI with focus on comparing it with Nagios Core.
Achieving cyber mission assurance with near real-time impact

Achieving cyber mission assurance with near real-time impactElasticsearch See how Elastic and ECS support the Mission Assurance Decision Support System (MADSS) program for the Navy with observability, data enrichment, and powerful search in a containerized environment. By correlating data from diverse sources using web-based services and secure, automated data transformation services, MADSS improves responsiveness, predictions, and event analysis for critical network and infrastructure outages.
Database projects within visual studio



Database projects within visual studioRonnie Hicks Using Database Projects within Visual Studio (thanks to SQL Server Data Tools) can help bridge a gap between developers who need to test their applications against database changes they need and Database Administrators who like to safeguard their servers. This slide deck was used as part of Days of Dot Net 2014 by Ronnie Hicks for his presentation, and contains useful information for getting started with database projects.
Jeremy Engle's slides from Redshift / Big Data meetup on July 13, 2017



Jeremy Engle's slides from Redshift / Big Data meetup on July 13, 2017AWS Chicago "Strategies for supporting near real time analytics, OLAP, and interactive data exploration" - Dr. Jeremy Engle, Engineering Manager Data Team at Jellyvision
Monitoring as Code - Ignite



Monitoring as Code - IgniteIcinga Icinga is a scalable and extensible monitoring system that checks resource availability, notifies users of outages, and provides metrics. It uses an object-based configuration language to define hosts, services, rules, conditions, loops and custom functions. Configurations can be imported from various sources and managed through a RESTful API or web interface. Icinga Director allows importing configurations from multiple sources, deploying them hands-free with versioning and audit logging.
The Modern Data Team for the Modern Data Stack: dbt and the Role of the Analy...



The Modern Data Team for the Modern Data Stack: dbt and the Role of the Analy...Databricks A traditional data team has roles including data engineer, data scientist, and data analyst. However, many organizations are finding success by integrating a new role – the analytics engineer. The analytics engineer develops a code-based data infrastructure that can serve both analytics and data science teams. He or she develops re-usable data models using the software engineering practices of version control and unit testing, and provides the critical domain expertise that ensures that data products are relevant and insightful. In this talk we’ll talk about the role and skill set of the analytics engineer, and discuss how dbt, an open source programming environment, empowers anyone with a SQL skillset to fulfill this new role on the data team. We’ll demonstrate how to use dbt to build version-controlled data models on top of Delta Lake, test both the code and our assumptions about the underlying data, and orchestrate complete data pipelines on Apache Spark™.
I2 - SharePoint Hybrid Search Start to Finish - Thomas Vochten



I2 - SharePoint Hybrid Search Start to Finish - Thomas VochtenSPS Paris One of the most compelling additions to a SharePoint practitioner’s toolbox is hybrid search. Although hybrid search capabilities were already around for a few years, with the introduction of the “Cloud Search Service Application” things got a lot more interesting. This demo-heavy session will focus on the technical implementation details and their prerequisites, as well as the typical hurdles that you’ll face in your first hybrid search project.
SSIS Monitoring Deep Dive



SSIS Monitoring Deep DiveDavide Mauri In this session we'll see everything interesting is hidden in the SSISDB database, where you can gain a lot of insight on the outcome, the performance and the status of your SSIS Packages. I'll share everything I've learned building the SSIS Dashboard we're actually using in production and that you can test here http://ssis-dashboard.azurewebsites.net/. We’ll see the internals of SSISDB database, how we can add custom logging information and how we can use all these data in order to know exactly what happened on a specific point in time.
Anypoint platform for api



Anypoint platform for apiKrishna_in Anypoint Platform for APIs and Anypoint Data Gateway allow integration of data between legacy systems and Salesforce. Anypoint Data Gateway installs as a Salesforce app and provides a point-and-click interface to access external data sources like SAP, Oracle, and SQL from within Salesforce. It supports instant connection to external systems by configuring host, user, etc. parameters and publishing the gateway to specified entities.
TechDays NL 2016 - Building your scalable secure IoT Solution on Azure



TechDays NL 2016 - Building your scalable secure IoT Solution on AzureTom Kerkhove The Internet-of-Things was one of the big hypes in 2015 but it’s more than that – Customers want to build out their own infrastructures and act on their data.
Today we’ll look at how Microsoft Azure helps us to build scalable solutions to process events from thousands of devices in a secure manner and the challenges it has. Once the data is in the cloud we’ll also take a look at ways we can learn from our measurements.
20160317 lagom sf scala



20160317 lagom sf scalashinolajla The document discusses microservices and the Lagom framework. It provides an overview of what microservices are and the goals they aim to achieve, such as accelerating teams, reducing dependencies, and increasing application throughput. It then outlines several principles for microservices, including isolation, asynchronous APIs, immutable deployments, and exposing simplified APIs. Finally, it describes key aspects of the Lagom framework, which supports building microservices, such as its service and persistence APIs, development environment, and production environment using Lightbend Reactive Platform.
Better Search and Business Analytics at Southern Glazer’s Wine & Spirits



Better Search and Business Analytics at Southern Glazer’s Wine & SpiritsElasticsearch See how Southern Glazer’s Wine & Spirits architected their system to deliver a better search and ordering experience, plus how they centrally manage all Elasticsearch deployments on Elastic Cloud Enterprise.
Similar to BuildingSecurity Audits with Extended Events (20)
Make your Azure PaaS Deployment More Safe



Make your Azure PaaS Deployment More SafeThuan Ng This presentation targets to guiding security expert and developer to protect PaaS deployment to eliminate security threats. This also introduces Threat Modeling.
Introduction to SQL Server Security



Introduction to SQL Server SecurityJason Strate This document discusses securing Microsoft SQL Server. It covers securing the SQL Server installation, controlling access to the server and databases, and validating security. Key points include using least privilege for service accounts, controlling access through logins, roles and permissions, auditing with SQL Server Audit and Policy Based Management, and services available from Pragmatic Works related to SQL Server security, training and products.
Visual Studio LightSwitch (Beta 1) Overview



Visual Studio LightSwitch (Beta 1) OverviewSteve Lange Visual Studio LightSwitch allows developers to quickly create professional, data-centric business applications. It provides pre-configured screen templates and pre-written code to build the basic application functionality faster. LightSwitch applications can access existing data sources like SQL Server and SharePoint. The applications are made up of projects containing data entities, screens, queries, and other resources. Developers can customize and extend LightSwitch applications through code. LightSwitch applications can be deployed to the desktop, browser, or cloud.
Are you Ready to Rumble? Let's Migrate Some Jira Data



Are you Ready to Rumble? Let's Migrate Some Jira DataAtlassian Migrating data from one Jira or Confluence to another can be frustrating and painful if not planned properly. We've managed 40+ successful migrations over the last 6 years at Cisco, and want to share the tips and tricks we learned along the way.
Discover how we handled the migration of Jira and Confluence instances with the right mix of people, processes, and tools. Get a look at our own code and migration questionnaire to help your own future migrations.
EA - Enterprise Integration Introduction



EA - Enterprise Integration IntroductionPraveen Pandey With this series of presentation, I am trying to cover aspect of Enterprise Integration Enterprise Integration is one of important component of Enterprise Architecture. It this slide, trying to explain what is Enterprise Integration and cover all topic in details in future slides.
System Integration is corner stone of today's Digital Era.
The Process of software applications does not lie only in Functionality that provides themselves, but ability to communicate with one another.
Bridging the Gap: Analyzing Data in and Below the Cloud



Bridging the Gap: Analyzing Data in and Below the CloudInside Analysis The Briefing Room with Dean Abbott and Tableau Software
Live Webcast July 23, 2013
http://www.insideanalysis.com
Today’s desire for analytics extends well beyond the traditional domain of Business Intelligence. That’s partly because business users are realizing the value of mixing and matching all kinds of data, from all kinds of sources. One emerging market driver is Cloud-based data, and the desire companies have to analyze this data cohesively with their on-premise data sets.
Register for this episode of The Briefing Room to learn from Analyst Dean Abbott, who will explain how the ability to access data in the cloud can play a critical role for generating business value from analytics. He’ll be briefed by Ellie Fields of Tableau Software who will tout Tableau’s latest release, which includes native connectors to cloud-based applications like Salesforce.com, Amazon Redshift, Google Analytics and BigQuery. She’ll also demonstrate how Tableau can combine cloud data with other data sources, including spreadsheets, databases, cubes and even Big Data.
Finding Security a Home in a DevOps World



Finding Security a Home in a DevOps WorldShannon Lietz Presented this talk at DevOps Summit in 2015 to a DevOps community. Discovered that security is new to most DevOps teams and this was a very good discussion.
EDB Executive Presentation 101515



EDB Executive Presentation 101515Pierre Fricke This document discusses how organizations can transform their database management systems (DBMS) to drive customer engagement and innovation initiatives. It argues that moving from expensive, proprietary DBMS to open-source PostgreSQL can free up 35-80% of IT budgets. This "found money" can then be invested in customer-focused applications, analytics, mobile, and other technologies to strengthen brands and avoid competitive threats. The document presents EnterpriseDB as a partner that can help organizations migrate to their PostgreSQL-based database platform for security, performance, compatibility with other databases, and enterprise-level support.
MongoDB in the Middle of a Hybrid Cloud and Polyglot Persistence Architecture



MongoDB in the Middle of a Hybrid Cloud and Polyglot Persistence ArchitectureMongoDB The Sage Data Cloud enables next-generation cloud and mobile services via a Hybrid Cloud and Polyglot Persistence Architecture. Come learn how MongoDB and other cloud data stores make this a reality, and get an insight into our learnings and operations.
SharePoint Online vs. On-Premise



SharePoint Online vs. On-PremiseEvan Hodges SharePoint Online vs. On-Premise document compares Microsoft SharePoint Online to an on-premise SharePoint implementation. Some key differences include SharePoint Online having higher security but more limited customization options compared to on-premise which has more robust features but requires managing security. Migrating to SharePoint Online can provide cost savings on licensing and infrastructure but requires planning to address limitations in areas like search and administration interfaces. The document provides considerations for law firms evaluating moving to SharePoint Online.
The Hacking Games - Security vs Productivity and Operational Efficiency 20230119



The Hacking Games - Security vs Productivity and Operational Efficiency 20230119lior mazor Nowadays data-driven products in the cloud are delivered faster, IT resources become more responsive and productive with lower costs and higher performance for data operations.
Causing Cyber Security risks involved in accessing sensitive data and regulatory compliance requirements.
Nuts and Bolts of Building Compliance Process with Nintex and SharePoint 2013



Nuts and Bolts of Building Compliance Process with Nintex and SharePoint 2013Netwoven Inc. Compliance has become very rigorous and you need a system that can handle all the old processes, as well as any new ones that are initiated. Watch the webinar presented by the experts at Netwoven and Nintex. Here are some key takeaways from the session:
• Critical corporate compliance issues you can address today
• Overview of Microsoft SharePoint & Nintex software compliance features
• Get insights on how to make your applications include compliance reporting
• Best practices for common corporate compliance solutions development
ISS Capstone - Martinez Technology Consulting and Cedar Hills Church Security...



ISS Capstone - Martinez Technology Consulting and Cedar Hills Church Security...Robert Conti Jr. This document summarizes the results of a security audit conducted by Martinez Technology Consulting for COVERT Security Systems. The audit included assessing physical security, wireless networks, servers, workstations, and policies. Wireless networks were found to use outdated and insecure encryption methods. Servers had weak password policies and lacked patching. The network used an unsegmented flat design without central management. Several recommendations were provided to address issues, including implementing Active Directory, wireless encryption upgrades, firewalls, logging, backup solutions, and physical access controls. The findings highlighted the need for COVERT to continually evolve their security practices.
Directions Asia Unlocking New Integration Potential for d365 BC with Event ...



Directions Asia Unlocking New Integration Potential for d365 BC with Event ...Wagner Silveira Session co-presented with Tharanga Chandrasekara (Business Solution MVP) at Directions ASIA 2019
Reactive or event driven programming allow systems to have access to the correct data at the correct time. By using a BC extension and the AL language in conjunction with Azure Event Grid, you can benefit from this powerful publisher/subscriber engine to notify systems of changes in your data – as they happen - so you can enable faster business processes across your enterprise.
In this session Tharanga Chandrasekara (Business Solutions MVP) and Wagner Silveira (Azure MVP) will show you how to implement a generic extension that allows you to publish events into Azure Event Grid, and how you can use Azure Integration Services to subscribe to those events and take action.
Sukumar Nayak-Agile-DevOps-Cloud Management



Sukumar Nayak-Agile-DevOps-Cloud ManagementSukumar Nayak The document provides an overview of Agile, DevOps and Cloud Management from a security, risk management and audit compliance perspective. It discusses how the IT industry paradigm is shifting towards microservices, containers, continuous delivery and cloud platforms. DevOps is described as development and operations engineers participating together in the entire service lifecycle. Key differences in DevOps include changes to configuration management, release and change management, and event monitoring. Factors for DevOps success include culture, collaboration, eliminating waste, unified processes, tooling and automation.
Company Profile - NPC with TIBCO Spotfire solution 



Company Profile - NPC with TIBCO Spotfire solution Sirinporn Setworaya Discover the concept of 'on-the-fly' analysis with TIBCO Spotfire based on effortless of coding program for combining different types of file, cut cost of increasing in DB warehouse while DB growing, and real time analysis for digital era.
GIB2021 - Dan Probert - BizTalk Migrator Deep Dive



GIB2021 - Dan Probert - BizTalk Migrator Deep Diveprobertdaniel Slides from my BizTalk Migrator Deep Dive session at Global Integration Bootcamp 2021 session on Feb 27th 2021. This session gave more details about Microsoft's migration tool, how to get it, how to use it, and how it works plus demos of using it for various scenarios.
Aiim Seminar - SharePoint Crossroads May 23 - Bending but Not Breaking - Spea...



Aiim Seminar - SharePoint Crossroads May 23 - Bending but Not Breaking - Spea...Bill England At the AIIM SharePoint seminar in DC this past may, Buildingi presented out experience moving a Project Knowledge Center (PKC) .Net application to SharePoint, and were joined by Joanna Elazrak from Microsoft who spoke on 'Using SharePoint for Microsoft Records Management'.
Cybersecurity Legos - We're all part of something bigger



Cybersecurity Legos - We're all part of something biggerBen Boyd Presentation by Ben Boyd during the 2018 Northwest Arkansas Community College Cyber Security Awareness Symposium.
Building a Cyber Security program is more than just technology or architecture. Managing Cyber Risk is the duty of anyone with a digital asset.
Alexis R 



Alexis R Hilary Ip AI can analyze activity data like emails, meetings, calls and tasks to generate insights about relationships. It identifies important moments in communications and extracts relevant details. These insights are then made actionable by recommending specific next steps based on the context. For example, if pricing is discussed, it may suggest replying with a price list. Relationship insights allow users to better understand connections between people and how they collaborate over time.
Ad
More from Jason Strate (20)
Accelerating Business Intelligence Solutions with Microsoft Azure pass



Accelerating Business Intelligence Solutions with Microsoft Azure passJason Strate Business Intelligence (BI) solutions need to move at the speed of business. Unfortunately, roadblocks related to availability of resources and deployment often present an issue. What if you could accelerate the deployment of an entire BI infrastructure to just a couple hours and start loading data into it by the end of the day. In this session, we'll demonstrate how to leverage Microsoft tools and the Azure cloud environment to build out a BI solution and begin providing analytics to your team with tools such as Power BI. By end of the session, you'll gain an understanding of the capabilities of Azure and how you can start building an end to end BI proof-of-concept today.
The Plan Cache Whisperer - Performance Tuning SQL Server



The Plan Cache Whisperer - Performance Tuning SQL ServerJason Strate Execution plans tell SQL Server how to execute queries. If you listen closely, execution plans can also tell you when performance-tuning opportunities exist in your environment. By listening to your queries, you can understand how SQL Server is operating and gain insight into how your environment is functioning. In this session, learn how to use XQuery to browse and search the plan cache, enabling you to find potential performance issues and opportunities to tune your queries. In addition, learn how a performance issue on a single execution plan can be used to find similar issues on other execution plans, enabling you to scale up your performance tuning effectiveness. You can use this information to help reduce issues related to parallelism, shift queries from using scans to using seek operations, or discover exactly which queries are using which indexes. All this and more is readily available through the plan cache.
Strategies for SQL Server Index Analysis



Strategies for SQL Server Index AnalysisJason Strate Properly managing indexes for a database is a common use in many environments. When reviewing an index, should it have a single or multiple columns? Should the table be a heap, a clustered index or clustered columnstore index? These considerations are often at the forefront when analyzing your indexes. In this session, we'll look at easy methods for identifying new indexes, we'll review patterns for index consolidation, and discuss how and when to remove indexes. At the end, you'll have a strategy that helps design indexes to improve performance.
Leveraging Cloud for the Modern SQL Developer



Leveraging Cloud for the Modern SQL DeveloperJason Strate In the past, developing a database was a simple affair where you built and deployed the database for a server down the hall in your datacenter, or in some cases to a server under someone's desk. While those good ole days were a much more simple time, they were quite limiting in how a database could be deployed and there were much fewer options for ensuring stability and performance. Today, SQL Developers have many more options for deployment including the services provided through Windows Azure. In this session, we'll dive into what you need to know to start developing databases with Windows Azure and discuss the value that cloud delivery can provide to your database development.
http://pragmaticworks.com/LearningCenter/FreeTrainingWebinars/PastWebinars.aspx?ResourceId=640
Getting Started with Windows Azure and SQL Databases



Getting Started with Windows Azure and SQL DatabasesJason Strate The Microsoft Windows Azure platform provides service-based offerings for your data needs. These include services from file storage to SQL databases that are scalable to your specific needs. Regardless of the size of your data platform, Windows Azure has options that fit to your business needs. In this session, we'll discuss the Windows Azure platform and discuss how the SQL Database and other services enhance and extend your data platform. By session end, you'll understand how Windows Azure is able to fit into your environment and be ready to start using Windows Azure.
http://pragmaticworks.com/LearningCenter/FreeTrainingWebinars/PastWebinars.aspx?ResourceId=639
5 SQL Server Indexing Myths



5 SQL Server Indexing MythsJason Strate There are many "best practices" around that help people decide how to index databases. Having these practices can help alleviate the time that it takes to design an indexing strategy for a database. These practices can be of great use, except when they are wrong. Join us in this session, as we discuss some common myths associated with indexes and then dive into the myths to demonstrate how they can be debunked. At the end of the session, you'll know a few more things about indexes and leave armed with scripts that can help you debunk these myths on your own.
http://pragmaticworks.com/LearningCenter/FreeTrainingWebinars/PastWebinars.aspx?ResourceId=654
Introduction to Columnstore Indexes



Introduction to Columnstore IndexesJason Strate Columnstore indexes were first introduced in SQL Server 2012. Columnstore indexes provide the ability to flip-over your indexes from column-based to row-based, leading to dramatic changes in the storage and performance of your data. In this session, we'll review the basic concepts of columnstore indexes and look at the changes coming to them in SQL Server 2014
Introduction to Clustered Indexes and Heaps



Introduction to Clustered Indexes and HeapsJason Strate It's the age old question, do I put a clustered index on the table or leave it as a heap? While a simple question, this can have serious impacts on the performance of the table in queries. In this session, we'll review the basics of both clustered indexes and heaps; identifying key differences and cases where you might choose one over another.
The Flavors of Non-Clustered Indexes



The Flavors of Non-Clustered IndexesJason Strate A non-clustered index is just another way to get to data. Add in a couple columns and off you go. Not too much to think about, just fire and forget. But it’s not really that easy. Non-clustered indexes have a number of various ways in which they can be built and designed that can have significant impacts on performance. In this session we’ll look at what can go into a non-clustered index. We will explore what you can put into a non-clustered index and what you can expect back out from performance.
Necessary Evils, Building Optimized CRUD Procedures



Necessary Evils, Building Optimized CRUD ProceduresJason Strate Every developer loves them and a lot of DBAs hate them. But there are many and valid reasons for creating generic SELECT, INSERT, UPDATE, and DELETE procedures. In this session, we’ll go through designing CRUD procedures that utilize new and existing SQL features to create CRUD procedures that are optimized for performance.
How Do Non-Clustered Indexes Improve Performance?



How Do Non-Clustered Indexes Improve Performance?Jason Strate We've all heard the mantra about the importance of clustered indexes, but what about non-clustered indexes? Do you really need non-clustered indexes or are they just something that consultants recommend to increase their billable hours? In this session, we'll investigate the various flavors of non-clustered indexes and how they can be used to provide significant performance improvements.
Choosing Your Clustered Index



Choosing Your Clustered IndexJason Strate We often hear that you should always have clustered indexes on your tables. What's left off of this discussion is the how to choose the columns for this index. Should it be the primary key? Or some other column or set of columns? Having the wrong key column(s) in the clustered index can lead to performance problems, possibly worse than having no clustered index on the table at all. In this session, we'll review common patterns for selecting clustered indexes and how to determine which pattern you need. Also, we'll look at how to analyze tables to help select the best clustered index for every table.
http://www.jasonstrate.com/go/20131010-IX/
5 ways to improve performance through indexing



5 ways to improve performance through indexingJason Strate The document discusses 5 ways to improve database performance through indexing: 1) addressing lookup imbalance by moving clustered indexes or adding included columns, 2) reducing scans on large indexes by adding alternative indexes, 3) using filtered indexes to improve performance on queries involving a subset of rows, 4) addressing missing index recommendations to optimize queries, and 5) indexing foreign keys to avoid performance issues during DML operations.
The Side Effect of NOLOCK



The Side Effect of NOLOCKJason Strate This document discusses the side effects of using NOLOCK hints in SQL queries. It notes that NOLOCK is not an acceptable way to fix locking issues and risks corrupting data. The document recommends researching SNAPSHOT ISOLATION as an alternative and provides contact information for Jason Strate, a database architect, who discusses locking and isolation levels on his website.
Discovering the plan cache (sql sat175)



Discovering the plan cache (sql sat175)Jason Strate This document discusses exploring the SQL Server plan cache. It begins with an overview of the plan cache and how it stores execution plans. It then covers various methods for viewing the plan cache, including using dynamic management objects. The document demonstrates how to interpret plan cache contents, including the showplan XML structure. It shows scenarios and demos related to missing indexes, parameter sniffing, physical operators, and key lookups. The document emphasizes that the plan cache contains valuable performance information and techniques for accessing it.
What are you waiting for? (#SQLSat211)



What are you waiting for? (#SQLSat211)Jason Strate The document discusses wait statistics and wait types in SQL Server. It provides an overview of defining, viewing, collecting and reviewing wait data using dynamic management views and wait statistics. It also simplifies the SQL Server execution model using a grocery store checkout line analogy. Specific wait types are explained such as CXPACKET, OLEDB, PAGEIOLATCH_X, PAGELATCH_X and LATCH_X. Guidelines and potential resolutions are provided for analyzing and addressing top wait events.
Discovering the plan cache (#SQLSat211)



Discovering the plan cache (#SQLSat211)Jason Strate The document discusses discovering and analyzing the plan cache in SQL Server. It covers viewing the plan cache, the structure of showplan XML, and demonstrates scenarios and techniques for querying the plan cache including identifying missing indexes, parameter sniffing issues, and physical operator details. The goal is to help attendees leverage the plan cache to troubleshoot performance issues and tune queries.
Discovering the Plan Cache (#SQLSat 206)



Discovering the Plan Cache (#SQLSat 206)Jason Strate The document discusses viewing and analyzing the plan cache in SQL Server. It covers viewing the plan cache, exploring the structure of showplan XML, and demonstrating methods to query the plan cache through demos. The goals are to discuss the plan cache, explore it, demonstrate querying methods, and demonstrate performance tuning concepts.
A Function by Any Other Name is a Function



A Function by Any Other Name is a FunctionJason Strate This document discusses user defined functions in SQL Server and their performance impacts. It identifies purposes for creating user defined functions, discusses the different types including scalar, inline, and multi-statement functions. It demonstrates the performance impact of each type of function through examples and benchmarks. Scalar functions have linear performance effects while inline and multi-statement functions allow for more complex logic but can introduce duplication of access. In summary, functions provide benefits like consolidation and reuse but their performance impact depends on the type and how they are used.
What are you waiting for



What are you waiting forJason Strate This document discusses wait statistics and wait analysis in SQL Server. It defines waits as occurring when a process requests a resource that is unavailable. It provides an overview of wait types categorized as background, external, or queue waits. The document demonstrates how to view wait statistics using DMVs and third party tools. It provides translations and guidelines for some common wait types like CXPACKET, PAGEIOLATCH, and LATCH. It concludes with additional resources for learning about waits.
Ad
Recently uploaded (20)
Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...



Enhancing ICU Intelligence: How Our Functional Testing Enabled a Healthcare I...Impelsys Inc. Impelsys provided a robust testing solution, leveraging a risk-based and requirement-mapped approach to validate ICU Connect and CritiXpert. A well-defined test suite was developed to assess data communication, clinical data collection, transformation, and visualization across integrated devices.
Mobile App Development Company in Saudi Arabia



Mobile App Development Company in Saudi ArabiaSteve Jonas EmizenTech is a globally recognized software development company, proudly serving businesses since 2013. With over 11+ years of industry experience and a team of 200+ skilled professionals, we have successfully delivered 1200+ projects across various sectors. As a leading Mobile App Development Company In Saudi Arabia we offer end-to-end solutions for iOS, Android, and cross-platform applications. Our apps are known for their user-friendly interfaces, scalability, high performance, and strong security features. We tailor each mobile application to meet the unique needs of different industries, ensuring a seamless user experience. EmizenTech is committed to turning your vision into a powerful digital product that drives growth, innovation, and long-term success in the competitive mobile landscape of Saudi Arabia.
Build Your Own Copilot & Agents For Devs



Build Your Own Copilot & Agents For DevsBrian McKeiver May 2nd, 2025 talk at StirTrek 2025 Conference.
Manifest Pre-Seed Update | A Humanoid OEM Deeptech In France



Manifest Pre-Seed Update | A Humanoid OEM Deeptech In Francechb3 The latest updates on Manifest's pre-seed stage progress.
The Evolution of Meme Coins A New Era for Digital Currency ppt.pdf



The Evolution of Meme Coins A New Era for Digital Currency ppt.pdfAbi john Analyze the growth of meme coins from mere online jokes to potential assets in the digital economy. Explore the community, culture, and utility as they elevate themselves to a new era in cryptocurrency.
Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep Dive



Designing Low-Latency Systems with Rust and ScyllaDB: An Architectural Deep DiveScyllaDB Want to learn practical tips for designing systems that can scale efficiently without compromising speed?
Join us for a workshop where we’ll address these challenges head-on and explore how to architect low-latency systems using Rust. During this free interactive workshop oriented for developers, engineers, and architects, we’ll cover how Rust’s unique language features and the Tokio async runtime enable high-performance application development.
As you explore key principles of designing low-latency systems with Rust, you will learn how to:
- Create and compile a real-world app with Rust
- Connect the application to ScyllaDB (NoSQL data store)
- Negotiate tradeoffs related to data modeling and querying
- Manage and monitor the database for consistently low latencies
Quantum Computing Quick Research Guide by Arthur Morgan



Quantum Computing Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
Role of Data Annotation Services in AI-Powered Manufacturing



Role of Data Annotation Services in AI-Powered ManufacturingAndrew Leo From predictive maintenance to robotic automation, AI is driving the future of manufacturing. But without high-quality annotated data, even the smartest models fall short.
Discover how data annotation services are powering accuracy, safety, and efficiency in AI-driven manufacturing systems.
Precision in data labeling = Precision on the production floor.
tecnologias de las primeras civilizaciones.pdf



tecnologias de las primeras civilizaciones.pdffjgm517 descaripcion detallada del avance de las tecnologias en mesopotamia, egipto, roma y grecia.
Procurement Insights Cost To Value Guide.pptx



Procurement Insights Cost To Value Guide.pptxJon Hansen Procurement Insights integrated Historic Procurement Industry Archives, serves as a powerful complement — not a competitor — to other procurement industry firms. It fills critical gaps in depth, agility, and contextual insight that most traditional analyst and association models overlook.
Learn more about this value- driven proprietary service offering here.
Andrew Marnell: Transforming Business Strategy Through Data-Driven Insights



Andrew Marnell: Transforming Business Strategy Through Data-Driven InsightsAndrew Marnell With expertise in data architecture, performance tracking, and revenue forecasting, Andrew Marnell plays a vital role in aligning business strategies with data insights. Andrew Marnell’s ability to lead cross-functional teams ensures businesses achieve sustainable growth and operational excellence.
Semantic Cultivators : The Critical Future Role to Enable AI



Semantic Cultivators : The Critical Future Role to Enable AIartmondano By 2026, AI agents will consume 10x more enterprise data than humans, but with none of the contextual understanding that prevents catastrophic misinterpretations.
HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungen



HCL Nomad Web – Best Practices und Verwaltung von Multiuser-Umgebungenpanagenda Webinar Recording: https://www.panagenda.com/webinars/hcl-nomad-web-best-practices-und-verwaltung-von-multiuser-umgebungen/
HCL Nomad Web wird als die nächste Generation des HCL Notes-Clients gefeiert und bietet zahlreiche Vorteile, wie die Beseitigung des Bedarfs an Paketierung, Verteilung und Installation. Nomad Web-Client-Updates werden “automatisch” im Hintergrund installiert, was den administrativen Aufwand im Vergleich zu traditionellen HCL Notes-Clients erheblich reduziert. Allerdings stellt die Fehlerbehebung in Nomad Web im Vergleich zum Notes-Client einzigartige Herausforderungen dar.
Begleiten Sie Christoph und Marc, während sie demonstrieren, wie der Fehlerbehebungsprozess in HCL Nomad Web vereinfacht werden kann, um eine reibungslose und effiziente Benutzererfahrung zu gewährleisten.
In diesem Webinar werden wir effektive Strategien zur Diagnose und Lösung häufiger Probleme in HCL Nomad Web untersuchen, einschließlich
- Zugriff auf die Konsole
- Auffinden und Interpretieren von Protokolldateien
- Zugriff auf den Datenordner im Cache des Browsers (unter Verwendung von OPFS)
- Verständnis der Unterschiede zwischen Einzel- und Mehrbenutzerszenarien
- Nutzung der Client Clocking-Funktion
TrsLabs - Fintech Product & Business Consulting



TrsLabs - Fintech Product & Business ConsultingTrs Labs Hybrid Growth Mandate Model with TrsLabs
Strategic Investments, Inorganic Growth, Business Model Pivoting are critical activities that business don't do/change everyday. In cases like this, it may benefit your business to choose a temporary external consultant.
An unbiased plan driven by clearcut deliverables, market dynamics and without the influence of your internal office equations empower business leaders to make right choices.
Getting things done within a budget within a timeframe is key to Growing Business - No matter whether you are a start-up or a big company
Talk to us & Unlock the competitive advantage
Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...



Noah Loul Shares 5 Steps to Implement AI Agents for Maximum Business Efficien...Noah Loul Artificial intelligence is changing how businesses operate. Companies are using AI agents to automate tasks, reduce time spent on repetitive work, and focus more on high-value activities. Noah Loul, an AI strategist and entrepreneur, has helped dozens of companies streamline their operations using smart automation. He believes AI agents aren't just tools—they're workers that take on repeatable tasks so your human team can focus on what matters. If you want to reduce time waste and increase output, AI agents are the next move.
Rusty Waters: Elevating Lakehouses Beyond Spark



Rusty Waters: Elevating Lakehouses Beyond Sparkcarlyakerly1 Spark is a powerhouse for large datasets, but when it comes to smaller data workloads, its overhead can sometimes slow things down. What if you could achieve high performance and efficiency without the need for Spark?
At S&P Global Commodity Insights, having a complete view of global energy and commodities markets enables customers to make data-driven decisions with confidence and create long-term, sustainable value. 🌍
Explore delta-rs + CDC and how these open-source innovations power lightweight, high-performance data applications beyond Spark! 🚀
How Can I use the AI Hype in my Business Context?



How Can I use the AI Hype in my Business Context?Daniel Lehner 𝙄𝙨 𝘼𝙄 𝙟𝙪𝙨𝙩 𝙝𝙮𝙥𝙚? 𝙊𝙧 𝙞𝙨 𝙞𝙩 𝙩𝙝𝙚 𝙜𝙖𝙢𝙚 𝙘𝙝𝙖𝙣𝙜𝙚𝙧 𝙮𝙤𝙪𝙧 𝙗𝙪𝙨𝙞𝙣𝙚𝙨𝙨 𝙣𝙚𝙚𝙙𝙨?
Everyone’s talking about AI but is anyone really using it to create real value?
Most companies want to leverage AI. Few know 𝗵𝗼𝘄.
✅ What exactly should you ask to find real AI opportunities?
✅ Which AI techniques actually fit your business?
✅ Is your data even ready for AI?
If you’re not sure, you’re not alone. This is a condensed version of the slides I presented at a Linkedin webinar for Tecnovy on 28.04.2025.
Big Data Analytics Quick Research Guide by Arthur Morgan



Big Data Analytics Quick Research Guide by Arthur MorganArthur Morgan This is a Quick Research Guide (QRG).
QRGs include the following:
- A brief, high-level overview of the QRG topic.
- A milestone timeline for the QRG topic.
- Links to various free online resource materials to provide a deeper dive into the QRG topic.
- Conclusion and a recommendation for at least two books available in the SJPL system on the QRG topic.
QRGs planned for the series:
- Artificial Intelligence QRG
- Quantum Computing QRG
- Big Data Analytics QRG
- Spacecraft Guidance, Navigation & Control QRG (coming 2026)
- UK Home Computing & The Birth of ARM QRG (coming 2027)
Any questions or comments?
- Please contact Arthur Morgan at [email protected].
100% human made.
#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025



#StandardsGoals for 2025: Standards & certification roundup - Tech Forum 2025BookNet Canada Book industry standards are evolving rapidly. In the first part of this session, we’ll share an overview of key developments from 2024 and the early months of 2025. Then, BookNet’s resident standards expert, Tom Richardson, and CEO, Lauren Stewart, have a forward-looking conversation about what’s next.
Link to recording, transcript, and accompanying resource: https://bnctechforum.ca/sessions/standardsgoals-for-2025-standards-certification-roundup/
Presented by BookNet Canada on May 6, 2025 with support from the Department of Canadian Heritage.
BuildingSecurity Audits with Extended Events
- 1. Building Security Audits with Extended Events
- 2. Jason Strate e: [email protected] e: [email protected] b: www.jasonstrate.com t: StrateSQL Resources jasonstrate.com/go/xevents Introduction MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 3. MAKING BUSINESS INTELLIGENT www.pragmaticworks.com • Founded 2008 by MSFT MVP Brian Knight • Focused on the MSFT SQL Server Platform • Provides services, training and software • MSFT/HP “go to” partner: • Gold Certified: o BI o Data Management o SQL Performance • Team led by multiple MVP’s • Offices throughout the US with Corporate HQ in Jacksonville, FL Pragmatic Works Company History
- 5. Do you know where your data is?
- 6. Do you know who is accessing your data?
- 9. Agenda Why Security Audits? Security Audit Components Building a Login Audit Building a Query Audit
- 10. Agenda Why Security Audits? Security Audit Components Building a Login Audit Building a Query Audit
- 11. Why Do We Need Security Audits? Regulations Corporate Policy Responsibilities
- 12. Most Important Reason Everyone Lies! Even Unicorns, While They Are Doing Their Jobs
- 14. Types of Audits Common Criteria Compliance C2 Audit Tracing SQL Audit Extended Events
- 15. Types of Audits Common Criteria Compliance C2 Audit Tracing SQL Audit Extended Events
- 16. CCC and C2 Concerns • Difficult to manage • Too much data • Too little control • Behavior changes in SQL Server MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 17. SQL Audit • Two audit levels – Server (Instance) – Database • Captures preset data • Sync or async targets – File – Security log – Application log • Standard and Enterprise – SQL Server 2012 MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 18. SQL Audit • No control on columns – Maybe too much data • Limited output formats – Maybe need in-flight aggregation • Need something less? MAKING BUSINESS INTELLIGENT www.pragmaticworks.com Perfect for tracking permissions changes, login creation, DBCC activity, backups and restores, etc.
- 19. Do you know SQL Audit?
- 20. SQL AUDIT Demo
- 21. “Lower” Solution • Less invasive • Temporary need • Scenarios… – What about Bob, the New DBA? – How often is Sally accessing the database? – What is the application logon/logout frequency? MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 22. Agenda Why Security Audits? Security Audit Components Building a Login Audit Building a Query Audit
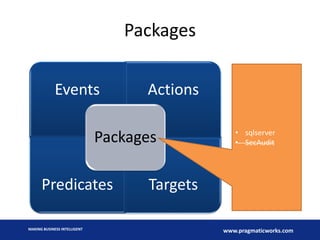
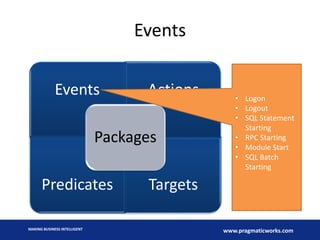
- 23. Components Events Actions Predicates Targets Packages MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 24. Packages Events Actions Predicates Targets Packages • sqlserver • SecAudit MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 25. Events Events Actions Predicates Targets Packages • Logon • Logout • SQL Statement Starting • RPC Starting • Module Start • SQL Batch Starting MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 26. Actions Events Actions Predicates Targets Packages • User Name • Client App Name • Client Hostname • Database Id • Database Name • NT Username • Server Instance Name • Server Principal Name • SQL Text • User Name MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 27. PREDICATES Events Actions Predicates Targets Packages WHERE • Equal • Greater Than • Less Than • Not Equal • LIKE FILTERS • AND • OR MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 28. Targets Events Actions Predicates Targets Packages • File Target • Ring Buffer • Event Stream MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 29. Agenda Why Security Audits? Security Audit Components Building a Login Audit Building a Query Audit
- 30. Login Scenario • How often is a login being used? • When are logins occurring? • What applications are using a login? • What host has the most logins? MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 31. Login Audits • Connection Tracking template – Login – Logout – Connectivity Ring Buffer Recorded • Targets – File target for long term analysis – Ring buffer for shorty term activity – Event stream for real-time analysis MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 32. LOGIN AUDITS Demo MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 33. Agenda Why Security Audits? Security Audit Components Building a Permissions Audit Building a Query Audit
- 34. Query Audit • What queries did the new DBA run? • What is being run against XYZ database? • What is the developer doing that keeps causing SEVERITY 20 errors? MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 35. Query Audit • Query level auditing – RPC Starting – Module Start – SP Statement Starting – SQL Batch Starting – SQL Statement Starting • Targets – Same as Login Audit MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 36. QUERY AUDIT Demo MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 37. Any Questions?
- 38. Learn More About Extended Events MAKING BUSINESS INTELLIGENT www.pragmaticworks.com
- 39. Services Speed development through training, and rapid development services from Pragmatic Works. Products BI products to covert to a Microsoft BI platform and simplify development on the platform. Foundation Helping those who do not have the means to get into information technology achieve their dreams. For more information… Name: Jason Strate Email: [email protected] Blog: www.jasonstrate.com Resource: jasonstrate.com/go/xevents

