DDoS Attack Detection & Mitigation in SDN
- 1. DDoS Attack Detection & Mitigation in SDN FINAL VIVA PRESENTATION 2014-12-08 COMSE-6998 Presented by Chao CHEN (cc3736)
- 2. Key Words DDoS Attack Detection and Mitigation Type: ICMP Flood SYN Flood DNS Amplification UDP Flood InMon sFlow-RT + Floodlight controller + Mininet SDN Application to perform DDoS Protection
- 3. RESEARCH BACKGROUND SCHEME DESIGN APPLICATION DEVELOPMENT ENVIRONMENT ESTABLISHMENT TEST & EVALUATION
- 5. Research Background Real Time detection and mitigation with lowest cost of device deployment
- 6. Research Background sFlow = sampled Flow Device Capability → Easy Deployment Physical Device: Cisco Nexus 3000/3100 series IBM c/g/m/r/s/x/y series Juniper EX 2200/3200/3300/4200/6200 series …… Virtual Device: OpenVSwitch Apache Nginx …… sFlow Collectors: InMon sFlow-RT Brocade Network Advisor …… SDN analytics and control using sFlow standard
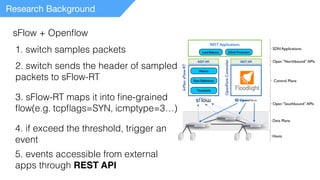
- 7. Research Background sFlow + Openflow 1. switch samples packets 2. switch sends the header of sampled packets to sFlow-RT 3. sFlow-RT maps it into fine-grained flow(e.g. tcpflags=SYN, icmptype=3…) 4. if exceed the threshold, trigger an event 5. events accessible from external apps through REST API
- 8. Research Background sFlow + Openflow 1. switch samples packets 2. switch sends the header of sampled packets to sFlow-RT 3. sFlow-RT maps it into fine-grained flow(e.g. tcpflags=SYN, icmptype=3…) 4. if exceed the threshold, trigger an event 5. events accessible from external apps through REST API detection mitigation processing
- 10. Scheme Design Yes No Overall Flowchart of Application need to be specified for different kinds of attacks
- 11. Scheme Design ICMP Flood Attack Mechanism: Each device in the botnet ping the server at a high rate. Flow Definition: ipsource=0.0.0.0/0, ipdestination=10.0.0.2/32, #suppose h2 is the server outputifindex!=discard, #packet is not discarded ipprotocol=1 #ICMP Match Field in blocking flow entry: ether-type, protocol, src-ip, dst-ip
- 12. Scheme Design SYN Flood Attack Mechanism: Each device in the botnet sends TCP SYN packets to the server at a high rate. Flow Definition: ipsource=0.0.0.0/0, ipdestination=10.0.0.2/32, #suppose h2 is the server outputifindex!=discard, #packet is not discarded tcpflags~…….1.=1 #TCP SYN packet Match Field in blocking flow entry: ether-type, protocol, src-ip, dst-ip
- 13. Scheme Design DNS Amplification Attack Mechanism: Each device in the botnet sends DNS query to several DNS servers with src-ip=victim’s ip. (take ANY(15) for example)
- 14. Scheme Design DNS Amplification Attack Flow Definition: ipsource=0.0.0.0/0, ipdestination=[10.0.0.1/32, 10.0.0.2/32], #suppose h1 and h2 are the DNS servers outputifindex!=discard, #packet is not discarded dnsqr=false, dnsqtype=255 Match Field in blocking flow entry: ether-type, protocol, src-ip, dst-ip Protect at the DNS servers (instead of the victim)
- 15. Scheme Design UDP Flood Attack Mechanism: Each device in the botnet sends UDP packets to all the ports if the server Attacker botnet/compromised system target server Command Command Command 1 5 7 9 11 13 15 … UDP port list UDP Packets ICMP Destination Unreachable
- 16. Scheme Design UDP Flood Attack Flow Definition: ipsource=10.0.0.2/32, #reversed ipdestination=0.0.0.0/0, outputifindex!=discard, #packet is not discarded ipprotocol=1, #ICMP icmptype=3, #Destination Unreachable Match Field in blocking flow entry: ether-type, protocol, src-ip=dst-ip_in_flow, dst-ip=server-ip Protect by monitoring ICMP Destination Unreachable packets
- 18. Application Development python Import requests & json to perform GET/PUT/POST via REST API Different attacks are implemented similarly. Take ICMP Flood attack as example. Definition of flows, thresholds,…: POST the definition to sFlow-RT:
- 19. Application Development Attack classification & Static Flow Entry Push:
- 21. Environment Establishment Laptop Ubuntu VM App Mininet 10.0.0.1 10.0.0.2 10.0.0.3 10.0.0.4 10.0.0.5 10.0.0.6 10.10.10.2:6633 10.10.10.2:8080 10.10.10.2:8008 10.10.10.2:6343
- 23. Test & Evaluation Launch floodlight: ./floodlight.sh Launch InMon sFlow-RT: ./start.sh Launch InMon sFlow-RT: sudo ./topo.sh set s1 is a sFlow agent, and set up bridge between s1 and sFlow-RT
- 24. Test & Evaluation Without mitigation: h1 ICMP attack on h2 with: ping -f 10.0.0.2 network traffic flow attack from h4 ICMP Flood Attack
- 25. Test & Evaluation With mitigation: h4 ICMP attack on h2 network traffic flow attack from h4 is mitigated ICMP Flood Attack
- 26. Test & Evaluation Continue: h5 ICMP attack on h2 network traffic flow attack from h5 is mitigated ICMP Flood Attack
- 27. Test & Evaluation ICMP Flood Attack ‘subflows’ in ICMP Attack Flow Events triggered in this case Flowtable of s1 (attacked by h3, h4, h6)
- 28. Test & Evaluation SYN Flood Attack Without mitigation: h1 SYN attack on h2 with: ping —tcp -p 80 —flag syn -rate 2000 —count 20000000 —no-capture —quiet 10.0.0.2 network traffic flow
- 29. Test & Evaluation SYN Flood Attack With mitigation: h6 and h4 SYN attack on h2 SYN Flood Traffic Flowtable of s1 (attacked by h3, h4, h5, h6) attacks from h6 and h4 are mitigated
- 30. Test & Evaluation DNS Amplification Attack & UDP Flood Attack: Cannot simulate attacks → No test result yet
- 31. Test & Evaluation Future Work: 1. Test on DNS Amplification Attack & UDP Flood Attack 2. {new_sample_rate, new_threshold} =update(old_sample_rate, old_threshold, network_congestion, server_status,…) 3. Sample Theory is efficient on large flows. Think about {tiny flows x n} 4. Reasonable unblock mechanism
- 32. Q&A












![Scheme Design DNS Amplification Attack
Flow Definition:
ipsource=0.0.0.0/0,
ipdestination=[10.0.0.1/32, 10.0.0.2/32], #suppose h1 and
h2 are the DNS servers
outputifindex!=discard, #packet is not discarded
dnsqr=false,
dnsqtype=255
Match Field in blocking flow entry:
ether-type, protocol, src-ip, dst-ip
Protect at the DNS servers (instead of the victim)](https://image.slidesharecdn.com/cc3736slides-150414170119-conversion-gate01/85/DDoS-Attack-Detection-Mitigation-in-SDN-14-320.jpg)

















