Chapter 2 Configure a Network Operating System
- 1. Introduction to Networks v5.1 Chapter 2: Configure a Network Operating System Jupriyadi, S.Kom., M.T. July 2020
- 2. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 2 2.0 Introduction 2.1 IOS Bootcamp 2.2 Basic Device Configuration 2.3 Address Schemes 2.4 Summary
- 3. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 3 Upon completion of this section, you should be able to: • Explain the purpose of Cisco IOS. • Explain how to access a Cisco IOS device for configuration purposes. • Explain how to navigate Cisco IOS to configure network devices. • Describe the command structure of Cisco IOS software.
- 4. Cisco Public© 2013 Cisco and/or its affiliates. All rights reserved. 4
- 5. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 5
- 6. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 6 • PC operating systems enable a user to: • Use a mouse to make selections and run programs. • Enter text and text-based commands. • View output on a monitor. • Cisco IOS enables a network technician to: • Use a keyboard to run CLI-based network programs. • Use a keyboard to enter text and text-based commands. • View output on a monitor. • All networking devices come with a default IOS. • It is possible to upgrade the IOS version or feature set.
- 7. Cisco Public© 2013 Cisco and/or its affiliates. All rights reserved. 7
- 8. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 8
- 9. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 9 PuTTY
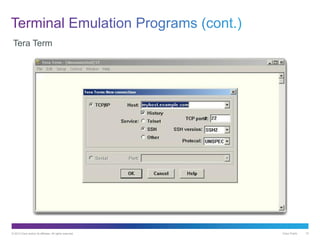
- 10. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 10 Tera Term
- 11. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 11 SecureCRT
- 12. Cisco Public© 2013 Cisco and/or its affiliates. All rights reserved. 12
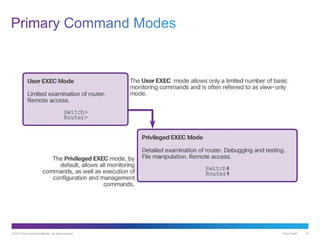
- 13. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 13 • A console connection must be established before initial configuration of a Cisco device. • After being consoled in, the network technician will have to navigate through various command modes of the IOS CLI. • The Cisco IOS modes use a hierarchical structure and are quite similar for both switches and routers. • Video Available
- 14. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 14
- 15. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 15 Global Configuration Mode • To configure the device must enter this mode with configure terminal command • Example: Switch(config)# • CLI configuration changes are made that affect the operation of the device as a whole • From this mode, the user can enter different sub-configuration modes Two common sub-configuration modes include: • Line Configuration Mode - Used to configure console, SSH, Telnet, or AUX access. Example: Switch(config-line)# • Interface Configuration Mode - Used to configure a switch port or router network interface. Example: Switch(config-if)# • Video Available
- 16. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 16
- 17. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 17 Exit End or Ctrl+Z Video Available
- 18. Cisco Public© 2013 Cisco and/or its affiliates. All rights reserved. 18
- 19. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 19
- 20. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 20
- 21. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 21 Video Available
- 22. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 22 Video Available
- 23. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 23 • Tab – Completes the remainder of a partially typed command or keyword • Ctrl-R – Redisplays a line • Ctrl-A – Moves cursor to the beginning of the line • Ctrl-Z – Exits configuration mode and returns to user EXEC • Down Arrow – Allows the user to scroll forward through former commands • Up Arrow – Allows the user to scroll backward through former commands • Ctrl-Shift-6 – Allows the user to interrupt an IOS process such as ping or traceroute. • Ctrl-C – Aborts the current command and exits the configuration mode
- 24. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 24 Upon completion of this section, you should be able to: • Configure hostnames on a Cisco IOS device using the CLI. • Use Cisco IOS commands to limit access to device configurations. • Use IOS commands to save the running configuration.
- 25. Cisco Public© 2013 Cisco and/or its affiliates. All rights reserved. 25
- 26. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 26 Guidelines to Choose a Hostname Configuring Device Names Hostnames allow devices to be identified by network administrators over a network or the Internet.
- 27. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 27 Syntax Checker Available
- 28. Cisco Public© 2013 Cisco and/or its affiliates. All rights reserved. 28
- 29. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 29
- 30. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 30 Privileged EXEC Password Example User EXEC Password Example VTY Line Password Example
- 31. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 31 • Use the enable secret command, not the older enable password command. • The enable secret command provides greater security because the password is encrypted.
- 32. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 32 Console port must be secured. • Reduces the chance of unauthorized personnel physically plugging a cable into the device and gaining device access. VTY lines allow access to a Cisco device via Telnet. • The number of VTY lines supported varies with the type of device and the IOS version.
- 33. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 33 service password- encryption • Prevents passwords from showing up as plain text when viewing the configuration. • Purpose of this command is to keep unauthorized individuals from viewing passwords in the configuration file. • After this command is applied, removing the encryption service does not reverse the encryption
- 34. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 34 • These are an important part of the legal process in the event that someone is prosecuted for breaking into a device. • Wording that implies that a login is "welcome" or "invited" is not appropriate. • Often used for legal notification because it is displayed to all connected terminals. • Video Available
- 35. Cisco Public© 2013 Cisco and/or its affiliates. All rights reserved. 35
- 36. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 36 • Startup configuration –File stored in NVRAM that contains all of the commands that will be used upon startup or reboot. NVRAM does not lose its contents when the device is powered off. • Running configuration – File stored in RAM that reflects the current configuration, modifying affects the operation of a Cisco device immediately. RAM loses all of its content when the device is powered off or restarted.
- 37. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 37 • Restore the device to its previous configuration by removing the changed commands individually. • Copy the startup configuration file to the running configuration with the copy startup-config running-config privileged EXEC mode command. • Reload the device with the reload command from privileged EXEC mode. • Switch# reload System configuration has been modified. Save? [yes/no]: n Proceed with reload? [confirm] • Video Available
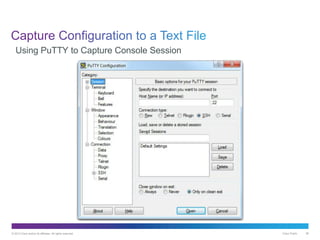
- 38. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 38 Using PuTTY to Capture Console Session
- 39. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 39 • All session output will be captured to the file specified, MySwitchLogs. • Execute the show running-config or show startup-config command at the privileged EXEC prompt. Text displayed in the terminal window will be placed into the chosen file. Enabling Session Logging in PuTTY
- 40. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 40 Disabling Session Logging in PuTTY
- 41. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 41 Chapter Objectives: • Explain how devices communicate across network media. • Configure a host device with an IP address. • Verify connectivity between two end devices.
- 42. Cisco Public© 2013 Cisco and/or its affiliates. All rights reserved. 42
- 43. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 43 Connecting End Devices Configuring a Static IP Address on a Host
- 44. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 44 • Network communications depend on end user device interfaces, networking device interfaces, and the cables that connect them. • Types of network media include twisted-pair copper cables, fiber-optic cables, coaxial cables, or wireless. • Different types of network media have different features and benefits. • Ethernet is the most common local area network (LAN) technology. • Ethernet ports are found on end user devices, switch devices, and other networking devices. • Cisco IOS switches have physical ports for devices to connect to, but they also have one or more switch virtual interfaces (SVIs). No physical hardware on the device is associated with it. It is created in software. • SVI provides a means to remotely manage a switch over a network.
- 45. Cisco Public© 2013 Cisco and/or its affiliates. All rights reserved. 45
- 46. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 46 Manually Assigning IPv4 Address InformationEthernet Adapter Properties
- 47. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 47 Assigning Dynamic Addresses
- 48. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 48 Verifying Windows PC IP Configuration
- 49. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 49 • IP address - Together with subnet mask, uniquely identifies end device on internetwork • Subnet mask - Determines which part of a larger network is used by an IP address • interface VLAN 1 - Interface configuration mode • ip address 192.168.10.2 255.255.255.0 - Configures the IP address and subnet mask for the switch • no shutdown - Administratively enables the interface • Switch still needs to have physical ports configured and VTY lines to enable remote management Video Available
- 50. Cisco Public© 2013 Cisco and/or its affiliates. All rights reserved. 50
- 51. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 51 Video Available
- 52. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 52 Video Available
- 53. © 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 53 Chapter Objectives: • Explain the features and functions of Cisco IOS Software. • Configure initial settings on a network device using the Cisco IOS software. • Given an IP addressing scheme, configure IP address parameters on end devices to provide end-to-end connectivity in a small to medium-sized business network.
- 54. Cisco Public© 2013 Cisco and/or its affiliates. All rights reserved. 54
- 55. Thank you.


































![© 2013 Cisco and/or its affiliates. All rights reserved. Cisco Public 37
• Restore the device to its previous configuration by removing the
changed commands individually.
• Copy the startup configuration file to the running configuration with
the copy startup-config running-config privileged EXEC mode
command.
• Reload the device with the reload command from privileged EXEC
mode.
• Switch# reload
System configuration has been modified. Save? [yes/no]: n
Proceed with reload? [confirm]
• Video Available](https://image.slidesharecdn.com/itnv51instructorpptch2-200719075547/85/Chapter-2-Configure-a-Network-Operating-System-37-320.jpg)