Chapter 3 programming concepts-ii
- 2. APPROACHES TO PROGRAMMING Understood to a small extent the tools needed for programming before getting into the actual programming, lets understand various approaches in programming Programming is a Art or a Skill Need of a good programmer is by getting a good grasp of the basics and following it up with keen studying and continuous practice
- 3. DOS DOS stands for Disk Operating Systems which could be an acronym for any OS but it is most often used as a shorthand for MS-DOS (Microsoft Disk Operating Systems) Originally deployed by Microsoft for IBM Initial versions of DOS were very simple and resembled another operating system called CP/M (Control Program for Microcomputers) DOS is still a 16-Bit OS, does not support multiple users or multitasking DOS in sufficient for graphical operations All windows have strongly dependency on DOS Newer version of DOS are inbuilt in all windows OS DOS is considered to control hardware directly
- 4. BIOS AND DOS FUNCTION CALLS Till now we were viewing 8086 processor as being connected only to memory i.e physical memory RAM But in reality Processor is also connected to various input and output devices As a programmer, we would like to input data into the processor using KB and get the results displaed on the monitor for we need to access the I/O devices, which contain a lot of extra hardware Software available to handle these problem, they come in the form of functions written to access input and output devices BIOS (Basic Input Output Systems) consists of set of functions written for this purpose
- 5. There is another set of functions called DOS functions or DOS interrupts They are part of DOS operating system there are written for accessing input and output devices called in the form of software interrupts one such DOS interrupt that .EXIT statement (shorthand notation) gets translated into: MOV AH, 4CH INT 21H here 4CH is the function number which has to be loaded to the AH register before calling the interrupt with type 21H This function cause exiting the program & returning to the DOS prompt
- 6. USING DOS FUNCTION CALLS Start with 4 important function calls, all of which are of interrupt type 21H i)Read the keyboard with echo MOV AH ,01 INT 21H This call exits with the ASCII value of the key pressed being available in AL Key pressed is also echoed on the screen
- 7. ii)Read Keyboard without echo MOV AH ,08 INT 21H This call exits with the ASCII value of the key pressed being available in AL key pressed is not echoed on the screen
- 8. iii)Write a character to the standard display unit. For this ,the ASCII value of the character to be displayed should be in DL MOV DL , ‘S’ MOV AH ,02 INT 21H with this the character S is displayed on the screen DISPLAYING A CHARACTER
- 9. iv) Display a character string on the standard display unit The logical address DS:DX should point to the beginning of the string . This is to be followed by the following instructions MOV AH ,09 INT 21H STRING DISPLAY
- 10. THE INSTRUCTION SET OF 8086 Instruction set of 8086 is reasonable large Besides each instructions are used in various addressing modes Some of the features are: Most instructions have 2 operands (Destination & Source ). These can be registers or memory operands. If there are two operands, one of them should be in a register ,or an immediate operand If only one operand ,it can be a destination or a source In some cases, the operand is implicit in the usage of these instructions
- 11. DATA TRANSFER INSTRUCTIONS MOV- Move Usage: MOV destination, source This instruction is for copying the source content to the destination data types of source and destination should be match- either bytes or word MOV AX,CX ; copy CX to AX- word operation MOV AL,AH ; copy AH to AL- byte operation MOV AX,[BX] ;copy into AX the data in the address pointed by BX MOV COST,DX ; copy the word in DX to the location labeled COST
- 12. MOV instruction in the register and immediate addressing modes were covered earlier we will use MOV in other addressing modes . MODEL SMALL ; select small model .DATA ; start data segment COSTP DB 67H ; store cost price SELLP DB ? ; space for selling price .CODE ; start code segment .STARTUP ;start program PROFIT EQU 25H ;define the profit MOV AL,COSTP ; move COSTP to AL ADD AL, PROFIT ; add profit to AL MOVE SELLP, AL ; store sum in SEELP .EXIT ;exit to DOS END ; end of program
- 13. LIST OF 8086 DATA TRANSFER INSTRUCTIONS WITH FORMAT & FUNCTIONS
- 15. previous eg use mov instruction in the direct mode of addressing this mode uses a memory location as one operand here two memory locations labeled COSTP and SELLP have been defined in DS COSTP has a data byte stored in it SELLP is only allocated space for later storage MOV instruction gets the data byte in COSTP into AL After adding the sum in AL is stored in SELLP Both MOV use direct addressing remember the assembler will do the conversion of the labels to memory address
- 17. DS is first initialized with 5 bytes address of the first location is labeled as ARRAY DI is used to address the element numbers (with DI=0 1st element is accessed, DI=5 last element) EA will be [Array + DI] When DI=0, it will be Mov AL, Array[DI] Add 07, with DI=5 Array[DI] becomes address of the sixth location in memory
- 19. uses base indexed mode of addressing EA= base reg + index Reg MOV BX, offset array causes the offset of Array to be loaded into BX BX is now a pointer to the location labeled Array to point each element one by one, another register DI is also used With DI=o, the instruction MOV AL, [BX+DI] causes the data in the first location to be copied to AL with DI=5, [BX+DI] access the sixth location in the data segment
- 20. LEA - LOAD EFFECTIVE ADDRESS Usage: LEA reg16, memory this instruction causes the offset of the specified memory location to be loaded in the indicated register: LEA SI,COSTP ; load the offset of memory location COST in SI LEA BX, ARRAY ; load the offset of memory location ARRAY in BX Above is a replacement for the instruction MOV BX, OFFSET ARRAY of previous example lets see instruction for, display of two character strings on two lines on the monitor DOS function calls are needed for this
- 22. OUTPUT HELLO I AM SAM C:masm6.14BIN> Analyze the program In the data segment, two messages are stored at offsets with labels MESG1 and MESG2 character strings are enclosed in double quotes and terminated by the $ sign sign is mandatory to end a character string which is to be printed on the display device Eg shows the corresponding ASCII value for each character of the string ASCII value for space between each word of the second message i.e I AM SAM it is 20H, note that 24H is the ASCII value for $
- 23. Second line, we also see two characters 0AH and 0DH ASCII value for line feed and carriage return to print 1st message, DX points to the offset MESG1 using LEA instruction, which loads the offset of MESG1 in DX DOS function with number 09H is called for second message, DX should point to the offset of MESG2 Two messages as they are printed on the command window are seen .EXIT command causes control to return to DOS prompt
- 24. XLAT -TRANSLATE A BYTE IN AL Usage: XLAT this translates a byte in AL XLAT is an instruction that can handle look up tables and access data depending on the value of the pointing number one-to-one relationship between the number and the data in the table Before using XLAT, look up table must be in a memory and the offset of the table must be in BX Requirements : load into BX ,the offset of the look up table . Then use XLAT into AL, load the number which will extract the required data
- 25. WRITE A PROGRAM THAT GETS INTO THE MEMORY LOCATION STARTING FROM VALUES, THE ASCII VALUES OF 1, 3, 5, 4, 0 … IN THAT ORDER. THE LOOK- UP TABLE IS STORED IN THE ARRAY NAMED ASC
- 26. Look-Up Table for Decimal to ASCII Conversion
- 27. XLAT is equivalent to the following instructions: MOV AX, 0 MOV SI, 0 MOV AL, [BX + SI] SI or DI will be okay for showing the equivalence.
- 28. PUSH & POP The 8086 stack Is a LIFO stack the lowest address is the base address of the stack segment . The upper 16 bits of this base address will be in the SS register . The highest address will be in the SP register –or rather ,the SP will contain the offset of the highest address with respect to the base address .This is why it is called the TOP of STACK
- 29. STACK If the stack is defined from addresses 20000H to 203E8H , SS=2000H and SP=03E8H,.This stack then has a size of 3E8H bytes. In the 8086 ,only a word (16 bits ) can be pushed on to stack . A push thus causes two memory locations to be accessed – Ex: from the above SP mentioned, lets say PUSH BX instruction is executed Let BX=CC99H, with SP=03E8H, the operation of pushing is as follows: SP is first decremented by two The new data will be put in addresses (offsets) 03E7H (SP-1) & 03E6H (SP-2). It follows the ‘little endian ‘concept by higher byte of BX will be higher address & lower byte is the lower address
- 30. OPERATION OF THE STACK IF BX HAS THE CONTENT CC 99 AND THE INSTRUCTION IS PUSH BX-
- 31. REVERSE WILL BE THE CASE FOR POP OPERATION Assume POP CX operation at the time when SP is 0312H the content of the stack will be first loaded to the CX register With incrementing SP by two
- 32. PUSH AND POP Usage : PUSH source POP destination PUSH BX ; save the contents of BX to stack PUSH [BX ] ; save to stack the contents of the word pointed by BX PUSH DS ; save to stack the contents of the segment register DS PUSH COSTP ; save to stack the contents of the word location COSTP POP CX ; load the contents of the stack top to CX POP [SI] ; load the contents of the stack top to the memory location pointed by SI
- 33. DEFINING A STACK how to use stack in programming? Is stack is not defined it shows warning ‘ No stack segment’ appear on assembling This can be ignored To define
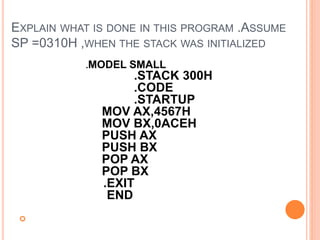
- 34. EXPLAIN WHAT IS DONE IN THIS PROGRAM .ASSUME SP =0310H ,WHEN THE STACK WAS INITIALIZED .MODEL SMALL .STACK 300H .CODE .STARTUP MOV AX,4567H MOV BX,0ACEH PUSH AX PUSH BX POP AX POP BX .EXIT END
- 35. Program defines a stack of 300 bytes by the use of the stack directive It loads two numbers in AX & BX Later these numbers are pushed into stack using PUSH operation, followed by POP operations. Note that POPing occurs in reverse direction what is pushed in last will be popped out first the last PUSH was PUSH BX hence by the POP AX operation, the content of AX is replaced by the content of BX Similarly the second POP causes the BX to get the content of AX Thus this program will exchange the contents of these two registers, using the stack as a temporary data storage area After execution, the contents of the registers are: BX=4567H & AX=0ACEH
- 36. BRANCHING INSTRUCTIONS Branching instructions is very important as they carry the full power of a computer Branching can be of two types: Conditional & Un- Conditional Unconditional branching becomes necessary when looping back or forward is done infinitely (Like generating square wave) Conditional branching is what may be more important taking decisions based on the result of a computation that gives computers their power & versatality Most instructions becomes meaningful when only conditional branching is used.
- 37. JMP- JUMP Usage: JMP destination Here destination is a memory location Jump destination is referred as ‘target’ Jump instructions breaks the normal sequence of program execution and takes control to a different location in code segment small example MOV….. ADD,----- JMP AGAIN ……….. -------- - - ------------ AGAIN: ……..
- 38. When the ADD instruction is being executed , IP(Instruction Pointer) points to the next instruction which is an unconditional JMP instruction . On decoding the JMP instruction ,the EU(Execution Unit) realizes that the next instruction should be taken from the location with label AGAIN . It is obvious then , that the IP content must be changed in such a way that a new sequence is to be followed .
- 39. SALIENT POINTS REGARDING JUMP The label of the destination address should be followed by a colon. Jumping can be backward or forward in the program sequence Jumping can be unconditional .Then the format of the jump instruction is JMP label ,where label is the address of the destination JMP can be conditional, based on the state of the flags which gets affected by arithmetic or logic instructions
- 40. TYPES OF JUMP INSTRUCTIONS an intrasegment (within segment) or near jump- needs a new value for IP jump location may be in a different code segment – i.e. inter segment -then it is called a far jump –needs a new value for CS and IP
- 41. EXAMPLE
- 43. OTHER FORMS OF THE UNCONDITIONAL JUMP INSTRUCTION i) JMP reg16 This is called an indirect jump The 16-bit registers contains the destination address (OffSet) This Jump is not a relative jump IP gets replaced by the value in the register examples: JMP BX ;jump to the destination address in BX. Make IP=BX JMP SI ; jump to the destination address in SI. Make IP=SI
- 44. ii. JMP [reg 16] The register points to an address which contains the jump location e.g.JMP [SI] ; jump to the address which is stored in the memory location pointed by SI
- 45. CONDITIONAL JUMPS Conditional jumps are the best part of the idea of control transfer. They change the sequence of program execution based on the result of a computation which causes flag bits to be set or reset. However, there is one case ( JCXZ) where the register content is checked.
- 46. LIST OF CONDITIONAL JUMP INSTRUCTIONS WHICH CATER TO UNSIGNED ARITHMETIC AND WHICH DIRECTLY ADDRESS FLAGS OR REGISTERS
- 48. FAR JUMP A far jump is an intersegment jump, which means that the destination address is in a different code segment. This will be a 5-byte instruction, the first byte being the opcode, the second and third, the new value of IP, and the fourth and fifth, the new values of CS.
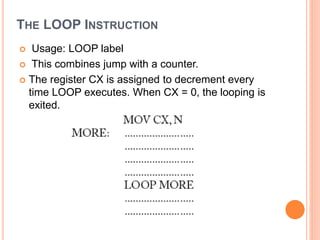
- 49. THE LOOP INSTRUCTION Usage: LOOP label This combines jump with a counter. The register CX is assigned to decrement every time LOOP executes. When CX = 0, the looping is exited.
- 50. What is to be understood here is that, the sequence of instructions up to the line containing the LOOP instruction, will execute once. Then, when the LOOP instruction is encountered, CX is decremented and then tested. If CX is found to be equal to zero, looping is exited and the next instruction in the sequence is taken up. If CX! = 0, control returns to the label MORE.
- 51. LOOP can be combined with other conditions, to make it a conditional instruction. LOOPNE / LOOPNZ and LOOPE / LOOPZ can be used. These instructions test the zero flag, as well as the value of CX
- 53. ARITHMETIC INSTRUCTIONS Complete list of Arithmetic instructions is shown below Instruction from 1 to 9 are discussed in detail For signed number arithmetic is discussed later
- 56. FLAG CONTROL INSTRUCTIONS Certain instructions which can be used to set/reset flags very relevant in case of flags like direction flag, interrupt flag etc.. There is one conditional flag which can be set/reset using instructions, and that is the carry flag. Relevant instructions to it are: i) CLC – Clear carry. ii) STC – Set carry. iii) CMC – Complement carry some of the important and commonly used arithmetic instructions with its format & usage are discussed.
- 57. ADDITION INSTRUCTIONS ADD – Add. Usage: ADD destination, source. This instruction adds the destination and source and puts the sum in the destination. All conditional flags get affected. Examples… ADD AH, AL ; add AL to AH, sum in AH ADD AL, COSTP ; add the byte in COSTP to AL, sum in AL ADD BX, 0987H ; add the number 987H to BX, sum in BX ADD CX, [BX] ; add the word in the location pointed by BX to CX sum in CX
- 58. ADC – Add with carry Usage: ADC destination, source This instruction adds CF and source to the destination, and puts the sum in the destination. There are three operands, of which the third is the carry. All conditional flags get affected. Examples…. ADC AH, 0 ; AH=AH+0+CF ADC [BX], AL ;add the byte pointed by BX with AL and CF, put sum in the location pointed by BX ADC AX, [BX][SI] ; add to AX, CF and the word with EA=BX+SI sum in AX
- 59. INC – Increment Usage: INC destination This instruction adds 1 to the destination. All conditional flags, except the carry flag, get affected. Examples… INC BX ; add 1 to the content of BX INC [BX] ; add 1 to the content of the m emory location pointed by BX INC AH ; add 1 to the content of AH
- 60. PTR DIRECTIVE When the size of the operand is not implicit in the instruction, a pointer is used to indicate whether the operand is a byte, a word, or a double word. This is the PTR directive. Examples … INC BYTE PTR [BX] ;byte pointer or INC WORD PTR [BX] ;word pointer or INC DWORD PTR [BX] ;double word pointer
- 62. First AX is loaded with 0 lets see how a byte addition causes a result to be a word the sum of two bytes which are added to AL is too large to fit in AL It needs to generate a carry flag next instruction adds CF,0 and AH which contains a 0 so the carry bit is accommodated in AH Thus AH-AL, i.e AX contains the sum in which is a word
- 63. SUBTRACTION SUB – Subtract. Usage: SUB destination, source. This instruction subtracts the source from the destination. The result is in the destination. All conditional flags are affected. Examples… SUB AX, BX ;subtract BX from AX SUB AL, [BX] ; Subtract the byte pointed by BX from AL SUB COST[SI], CX ; Subtract CX from the word with EA=COST+SI SUB AX, 8956H ;Subtract 8956H from AX SUB CL, BYTE PTR[SI] ; subtract from CL the byte pointed by SI
- 64. SBB – SUBTRACT WITH BORROW Usage: SBB destination, source This instruction subtracts the source and the carry flag from the destination. All conditional flags are affected. • Examples… SBB CH, 7 ;subtract from CH, 7 and CF – result in CH SBB AX, [BP + 2] ; subtract from AX, the word pointed by [BP+2]. Since BP is used, the data is taken from the stack segment. The result in AX
- 65. DEC – DECREMENT Usage: DEC destination. This instruction subtracts 1 from the destination. All conditional flags, except the carry flag, are affected. Examples.. DEC CL ;subtract 1 from CL DEC WORD PTR [SI] ; subtract 1 from the word pointed by SI DEC BYTE PTR NUMB[BX] ;subtract 1 from the byte pointed by the effective address NUMB+BX
- 66. UNSIGNED MULTIPLICATION MUL – Multiply. Usage: MUL source. This instruction multiplies a number in AL or AX by the source (where the source can be a register or a memory location, but not an immediate number). All the conditional flags are affected, but only the CF and ZF are defined as meaningful for the result. The destination depends on the size of the operand.
- 67. Two ways of performing multiplication i) Byte by byte In this, one of the operands must be in the AL register, and the source can be a byte in a register or memory location. The product (a word) will be in AX. Examples …. MUL BL MUL BYTE PTR[SI] MUL BIG
- 68. ii) Word by word In this, one of the operands must be in the AX register, and the source can be a word in a register or memory location. The product will be in DX and AX, with the upper word in DX. Examples… MUL CX MUL WORD PTR [DI]
- 69. iii)Word by byte This is only a special case of the word × word multiplication. The byte must be extended to be a word by making the upper byte to be 0. If the byte is in AL, extend it to be a word by making the content of AH to be zero. Th us, AX now contains one of the operands.
- 70. UNSIGNED MULTIPLICATION-FLAGS AFFECTED All conditional flags are affected, but only the carry (CF) and overflow (OF) flags have any significance. They will be set or reset according to the size of the product. We can summarize that if the product has a size equal to the size of the operands, both these flags are reset. i.e. CF = 0, OF = 0. However, if the product is large enough to occupy the registers assigned for it, these flags are set i.e., CF = 1, ZF = 1.
- 71. Two bytes stored in the data segment are multiplied. The result of multiplication is available in AX, which is then moved to the location PROD, a word location. Write a program for this.
- 72. FACTORIAL .Model Small .Data Fact DW 0 ;space allocated for the factorial .Code .Startup Mov ah,01 int 21h ; enter N from the KB sub al,30h ;convert ASCII to binary mov ah,0 ;convert N in AL to a word in AX mov bx,ax ;mov to bx mov ax,1 ; ax=1, to start the iteration cmp bx,0 ; compare bx(=N) to 0 jz final ; if N=0, jump to find 0! repea: mul bx ; for N not 0, multiply with AX dec bx ; decrement BX cmp bx,0 ;compare with 0 jne repea ;repeat if BX is not 0 final: mov fact,ax ; AX=1, hence 0!=1 .exit .end
- 73. UNSIGNED DIVISION DIV – Divide Usage: DIV source This instruction divides AX or DX – AX by the source, where the source can be a register or a memory location, but not an immediate number. • All the conditional flags are affected, but undefined – hence they do not give any interpretation or information about the result.
- 74. WAYS OF PERFORMING DIVISION i. Divide a word by a byte Here, the dividend must be a word placed in AX and the source must be a byte. The result of division causes AL to contain the quotient, and AH to contain the remainder. Examples……… DIV BL DIV BYTE PTR [BX] DIV DIG
- 75. ii. Dividing a byte by a byte. This is just a special case of a division of a word by a byte. In this case, convert the dividend byte to a word by loading the dividend in AL and 0 in AH. Thus, AX will be the word that acts as the dividend.
- 76. iii. Divide a double word by a word. In this case, the dividend has to be in AX and DX (the upper word in DX). The divisor should be a word. The result of this division causes the quotient to be in AX and the remainder to be in DX. Examples… DIV BX DIV WORD PTR [SI] DIV ANGLE
- 77. iv. Dividing a Word by a Word. Similar to the previous case, if we want a word by word division, extend the word in AX to be a double word by loading 0 in DX to get the dividend to be a double word in AX and DX.
- 78. DIVIDE BY ZERO ERROR For division, if the divisor is zero, the quotient becomes undefi ned. In attempting such a division, the 8086 will exit from this program and generate an interrupt. This state is said to be a ‘divide by zero error’. An interrupt generated by an error, is termed an exception. If the quotient register is too small to accommodate the quotient, then also this happens.
- 79. MOV AX, 09876H MOV CL, 25H DIV CL The above program segment will give a quotient of 41EH, which obviously cannot be accommodated in AL. Then ,program execution is aborted and the assembler displays the message ‘divide overflow error’.
- 80. WRITE A PROGRAM TO FIND THE AVERAGE OF TWO BYTES STORED IN MEMORY











![DATA TRANSFER INSTRUCTIONS
MOV- Move
Usage: MOV destination, source
This instruction is for copying the source content to the
destination
data types of source and destination should be match-
either bytes or word
MOV AX,CX ; copy CX to AX- word operation
MOV AL,AH ; copy AH to AL- byte operation
MOV AX,[BX] ;copy into AX the data in the address
pointed by BX
MOV COST,DX ; copy the word in DX to the location
labeled COST](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-11-320.jpg)





![ DS is first initialized with 5 bytes
address of the first location is labeled as ARRAY
DI is used to address the element numbers (with DI=0 1st
element is accessed, DI=5 last element)
EA will be [Array + DI]
When DI=0, it will be Mov AL, Array[DI]
Add 07, with DI=5 Array[DI] becomes address of the sixth
location in memory](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-17-320.jpg)

![ uses base indexed mode of addressing
EA= base reg + index Reg
MOV BX, offset array causes the offset of Array to
be loaded into BX
BX is now a pointer to the location labeled Array
to point each element one by one, another register
DI is also used
With DI=o, the instruction MOV AL, [BX+DI] causes
the data in the first location to be copied to AL
with DI=5, [BX+DI] access the sixth location in the
data segment](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-19-320.jpg)







![ XLAT is equivalent to the following instructions:
MOV AX, 0
MOV SI, 0
MOV AL, [BX + SI]
SI or DI will be okay for showing the equivalence.](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-27-320.jpg)




![PUSH AND POP
Usage : PUSH source
POP destination
PUSH BX ; save the contents of BX to stack
PUSH [BX ] ; save to stack the contents of the word
pointed by BX
PUSH DS ; save to stack the contents of the
segment register DS
PUSH COSTP ; save to stack the contents of the word
location COSTP
POP CX ; load the contents of the stack top to CX
POP [SI] ; load the contents of the stack top to the
memory location pointed by SI](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-32-320.jpg)










![ ii. JMP [reg 16]
The register points to an address which contains
the jump location
e.g.JMP [SI] ; jump to the address which is stored
in the memory location pointed by SI](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-44-320.jpg)









![ADDITION INSTRUCTIONS
ADD – Add.
Usage: ADD destination, source.
This instruction adds the destination and source and puts
the sum in the destination. All conditional flags get affected.
Examples…
ADD AH, AL ; add AL to AH, sum in AH
ADD AL, COSTP ; add the byte in COSTP to AL, sum in AL
ADD BX, 0987H ; add the number 987H to BX, sum in BX
ADD CX, [BX] ; add the word in the location pointed by BX
to CX sum in CX](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-57-320.jpg)
![ ADC – Add with carry
Usage: ADC destination, source
This instruction adds CF and source to the
destination, and puts the sum in the destination. There are
three operands, of which the third is the carry. All
conditional flags get affected.
Examples….
ADC AH, 0 ; AH=AH+0+CF
ADC [BX], AL ;add the byte pointed by BX with AL and
CF, put sum in the location pointed by BX
ADC AX, [BX][SI] ; add to AX, CF and the word with
EA=BX+SI sum in AX](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-58-320.jpg)
![ INC – Increment
Usage: INC destination
This instruction adds 1 to the destination. All conditional
flags, except the carry flag, get affected.
Examples…
INC BX ; add 1 to the content of BX
INC [BX] ; add 1 to the content of the m emory location
pointed by BX
INC AH ; add 1 to the content of AH](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-59-320.jpg)
![PTR DIRECTIVE
When the size of the operand is not implicit in the
instruction, a pointer is used to indicate whether
the operand is a byte, a word, or a double word.
This is the PTR directive.
Examples …
INC BYTE PTR [BX] ;byte pointer
or INC WORD PTR [BX] ;word pointer
or INC DWORD PTR [BX] ;double word pointer](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-60-320.jpg)


![SUBTRACTION
SUB – Subtract.
Usage: SUB destination, source.
This instruction subtracts the source from the destination.
The result is in the destination.
All conditional flags are affected.
Examples…
SUB AX, BX ;subtract BX from AX
SUB AL, [BX] ; Subtract the byte pointed by BX from
AL
SUB COST[SI], CX ; Subtract CX from the word with
EA=COST+SI
SUB AX, 8956H ;Subtract 8956H from AX
SUB CL, BYTE PTR[SI] ; subtract from CL the byte
pointed by SI](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-63-320.jpg)
![SBB – SUBTRACT WITH BORROW
Usage: SBB destination, source
This instruction subtracts the source and the carry
flag from the destination. All conditional flags are
affected.
• Examples…
SBB CH, 7 ;subtract from CH, 7 and CF – result in
CH
SBB AX, [BP + 2] ; subtract from AX, the word
pointed by [BP+2]. Since BP is used, the data is
taken from the stack segment. The result in AX](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-64-320.jpg)
![DEC – DECREMENT
Usage: DEC destination.
This instruction subtracts 1 from the destination. All
conditional flags, except the carry flag, are
affected.
Examples..
DEC CL ;subtract 1 from CL
DEC WORD PTR [SI] ; subtract 1 from the word
pointed by SI
DEC BYTE PTR NUMB[BX] ;subtract 1 from the
byte pointed by the effective address NUMB+BX](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-65-320.jpg)

![Two ways of performing multiplication
i) Byte by byte
In this, one of the operands must be in the AL
register, and the source can be a byte in a
register or memory location. The product (a
word) will be in AX.
Examples ….
MUL BL
MUL BYTE PTR[SI]
MUL BIG](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-67-320.jpg)
![ii) Word by word
In this, one of the operands must be in the AX
register, and the source can be a word in a
register or memory location. The product will be
in DX and AX, with the upper word in DX.
Examples…
MUL CX
MUL WORD PTR [DI]](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-68-320.jpg)





![WAYS OF PERFORMING DIVISION
i. Divide a word by a byte
Here, the dividend must be a word placed in AX
and the source must be a byte. The result of
division causes AL to contain the quotient, and AH
to contain the remainder.
Examples………
DIV BL
DIV BYTE PTR [BX]
DIV DIG](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-74-320.jpg)

![iii. Divide a double word by a word.
In this case, the dividend has to be in AX and DX
(the upper word in DX). The divisor should be a
word.
The result of this division causes the quotient to be
in AX and the remainder to be in DX.
Examples…
DIV BX
DIV WORD PTR [SI]
DIV ANGLE](https://image.slidesharecdn.com/chapter3-programmingconcepts-ii-170612053818/85/Chapter-3-programming-concepts-ii-76-320.jpg)






















































































