Chapter 5 - Computer Networking a top-down Approach 7th
- 1. Computer Networking: A Top Down Approach A note on the use of these Powerpoint slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: If you use these slides (e.g., in a class) that you mention their source (after all, we’d like people to use our book!) If you post any slides on a www site, that you note that they are adapted from (or perhaps identical to) our slides, and note our copyright of this material. Thanks and enjoy! JFK/KWR All material copyright 1996-2016 J.F Kurose and K.W. Ross, All Rights Reserved 7th edition Jim Kurose, Keith Ross Pearson/Addison Wesley April 2016 Chapter 5 Network Layer: The Control Plane 5-1Network Layer: Control Plane
- 2. Chapter 5: network layer control plane chapter goals: understand principles behind network control plane traditional routing algorithms SDN controlllers Internet Control Message Protocol network management and their instantiation, implementation in the Internet: OSPF, BGP, OpenFlow, ODL and ONOS controllers, ICMP, SNMP 5-2Network Layer: Control Plane
- 3. 5.1 introduction 5.2 routing protocols link state distance vector 5.3 intra-AS routing in the Internet: OSPF 5.4 routing among the ISPs: BGP 5.5 The SDN control plane 5.6 ICMP: The Internet Control Message Protocol 5.7 Network management and SNMP Chapter 5: outline 5-3Network Layer: Control Plane
- 4. Network-layer functions forwarding: move packets from router’s input to appropriate router output data plane control plane Two approaches to structuring network control plane: per-router control (traditional) logically centralized control (software defined networking) Recall: two network-layer functions: 5-4Network Layer: Control Plane routing: determine route taken by packets from source to destination
- 5. Per-router control plane Routing Algorithm Individual routing algorithm components in each and every router interact with each other in control plane to compute forwarding tables data plane control plane 5-5Network Layer: Control Plane
- 6. data plane control plane Logically centralized control plane A distinct (typically remote) controller interacts with local control agents (CAs) in routers to compute forwarding tables Remote Controller CA CA CA CA CA 5-6Network Layer: Control Plane
- 7. 5.1 introduction 5.2 routing protocols link state distance vector 5.3 intra-AS routing in the Internet: OSPF 5.4 routing among the ISPs: BGP 5.5 The SDN control plane 5.6 ICMP: The Internet Control Message Protocol 5.7 Network management and SNMP Chapter 5: outline 5-7Network Layer: Control Plane
- 8. Routing protocols Routing protocol goal: determine “good” paths (equivalently, routes), from sending hosts to receiving host, through network of routers path: sequence of routers packets will traverse in going from given initial source host to given final destination host “good”: least “cost”, “fastest”, “least congested” routing: a “top-10” networking challenge! 5-8Network Layer: Control Plane
- 9. u yx wv z 2 2 1 3 1 1 2 5 3 5 graph: G = (N,E) N = set of routers = { u, v, w, x, y, z } E = set of links ={ (u,v), (u,x), (v,x), (v,w), (x,w), (x,y), (w,y), (w,z), (y,z) } Graph abstraction of the network aside: graph abstraction is useful in other network contexts, e.g., P2P, where N is set of peers and E is set of TCP connections 5-9Network Layer: Control Plane
- 10. Graph abstraction: costs u yx wv z 2 2 1 3 1 1 2 5 3 5 c(x,x’) = cost of link (x,x’) e.g., c(w,z) = 5 cost could always be 1, or inversely related to bandwidth, or inversely related to congestion cost of path (x1, x2, x3,…, xp) = c(x1,x2) + c(x2,x3) + … + c(xp-1,xp) key question: what is the least-cost path between u and z ? routing algorithm: algorithm that finds that least cost path 5-10Network Layer: Control Plane
- 11. Routing algorithm classification Q: global or decentralized information? global: all routers have complete topology, link cost info “link state” algorithms decentralized: router knows physically- connected neighbors, link costs to neighbors iterative process of computation, exchange of info with neighbors “distance vector” algorithms Q: static or dynamic? static: routes change slowly over time dynamic: routes change more quickly • periodic update • in response to link cost changes 5-11Network Layer: Control Plane
- 12. 5.1 introduction 5.2 routing protocols link state distance vector 5.3 intra-AS routing in the Internet: OSPF 5.4 routing among the ISPs: BGP 5.5 The SDN control plane 5.6 ICMP: The Internet Control Message Protocol 5.7 Network management and SNMP Chapter 5: outline 5-12Network Layer: Control Plane
- 13. A link-state routing algorithm Dijkstra’s algorithm net topology, link costs known to all nodes • accomplished via “link state broadcast” • all nodes have same info computes least cost paths from one node (‘source”) to all other nodes • gives forwarding table for that node iterative: after k iterations, know least cost path to k dest.’s notation: c(x,y): link cost from node x to y; = ∞ if not direct neighbors D(v): current value of cost of path from source to dest. v p(v): predecessor node along path from source to v N': set of nodes whose least cost path definitively known 5-13Network Layer: Control Plane
- 14. Dijsktra’s algorithm 1 Initialization: 2 N' = {u} 3 for all nodes v 4 if v adjacent to u 5 then D(v) = c(u,v) 6 else D(v) = ∞ 7 8 Loop 9 find w not in N' such that D(w) is a minimum 10 add w to N' 11 update D(v) for all v adjacent to w and not in N' : 12 D(v) = min( D(v), D(w) + c(w,v) ) 13 /* new cost to v is either old cost to v or known 14 shortest path cost to w plus cost from w to v */ 15 until all nodes in N' 5-14Network Layer: Control Plane
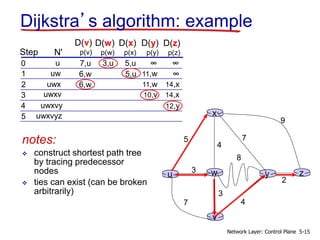
- 15. w3 4 v x u 5 3 7 4 y 8 z 2 7 9 Dijkstra’s algorithm: example Step N' D(v) p(v) 0 1 2 3 4 5 D(w) p(w) D(x) p(x) D(y) p(y) D(z) p(z) u ∞∞7,u 3,u 5,u uw ∞11,w6,w 5,u 14,x11,w6,wuwx uwxv 14,x10,v uwxvy 12,y notes: construct shortest path tree by tracing predecessor nodes ties can exist (can be broken arbitrarily) uwxvyz 5-15Network Layer: Control Plane
- 16. Dijkstra’s algorithm: another example Step 0 1 2 3 4 5 N' u ux uxy uxyv uxyvw uxyvwz D(v),p(v) 2,u 2,u 2,u D(w),p(w) 5,u 4,x 3,y 3,y D(x),p(x) 1,u D(y),p(y) ∞ 2,x D(z),p(z) ∞ ∞ 4,y 4,y 4,y u yx wv z 2 2 1 3 1 1 2 5 3 5 5-16Network Layer: Control Plane * Check out the online interactive exercises for more examples: http://gaia.cs.umass.edu/kurose_ross/interactive/
- 17. Dijkstra’s algorithm: example (2) u yx wv z resulting shortest-path tree from u: v x y w z (u,v) (u,x) (u,x) (u,x) (u,x) destination link resulting forwarding table in u: 5-17Network Layer: Control Plane
- 18. Dijkstra’s algorithm, discussion algorithm complexity: n nodes each iteration: need to check all nodes, w, not in N n(n+1)/2 comparisons: O(n2) more efficient implementations possible: O(nlogn) oscillations possible: e.g., support link cost equals amount of carried traffic: A D C B 1 1+e e0 e 1 1 0 0 initially A D C B given these costs, find new routing…. resulting in new costs 2+e 0 00 1+e 1 A D C B given these costs, find new routing…. resulting in new costs 0 2+e 1+e1 0 0 A D C B given these costs, find new routing…. resulting in new costs 2+e 0 00 1+e 1 5-18Network Layer: Control Plane
- 19. 5.1 introduction 5.2 routing protocols link state distance vector 5.3 intra-AS routing in the Internet: OSPF 5.4 routing among the ISPs: BGP 5.5 The SDN control plane 5.6 ICMP: The Internet Control Message Protocol 5.7 Network management and SNMP Chapter 5: outline 5-19Network Layer: Control Plane
- 20. Distance vector algorithm Bellman-Ford equation (dynamic programming) let dx(y) := cost of least-cost path from x to y then dx(y) = min {c(x,v) + dv(y) }v cost to neighbor v min taken over all neighbors v of x cost from neighbor v to destination y 5-20Network Layer: Control Plane
- 21. Bellman-Ford example u yx wv z 2 2 1 3 1 1 2 5 3 5 clearly, dv(z) = 5, dx(z) = 3, dw(z) = 3 du(z) = min { c(u,v) + dv(z), c(u,x) + dx(z), c(u,w) + dw(z) } = min {2 + 5, 1 + 3, 5 + 3} = 4 node achieving minimum is next hop in shortest path, used in forwarding table B-F equation says: 5-21Network Layer: Control Plane
- 22. Distance vector algorithm Dx(y) = estimate of least cost from x to y • x maintains distance vector Dx = [Dx(y): y є N ] node x: • knows cost to each neighbor v: c(x,v) • maintains its neighbors’ distance vectors. For each neighbor v, x maintains Dv = [Dv(y): y є N ] 5-22Network Layer: Control Plane
- 23. key idea: from time-to-time, each node sends its own distance vector estimate to neighbors when x receives new DV estimate from neighbor, it updates its own DV using B-F equation: Dx(y) ← minv{c(x,v) + Dv(y)} for each node y ∊ N under minor, natural conditions, the estimate Dx(y) converge to the actual least cost dx(y) Distance vector algorithm 5-23Network Layer: Control Plane
- 24. iterative, asynchronous: each local iteration caused by: local link cost change DV update message from neighbor distributed: each node notifies neighbors only when its DV changes • neighbors then notify their neighbors if necessary wait for (change in local link cost or msg from neighbor) recompute estimates if DV to any dest has changed, notify neighbors each node: Distance vector algorithm 5-24Network Layer: Control Plane
- 25. x y z x y z 0 2 7 ∞ ∞ ∞ ∞ ∞ ∞ from cost to fromfrom x y z x y z 0 x y z x y z ∞ ∞ ∞ ∞ ∞ cost to x y z x y z ∞ ∞ ∞ 7 1 0 cost to ∞ 2 0 1 ∞ ∞ ∞ 2 0 1 7 1 0 time x z 12 7 y node x table Dx(y) = min{c(x,y) + Dy(y), c(x,z) + Dz(y)} = min{2+0 , 7+1} = 2 Dx(z) = min{c(x,y) + Dy(z), c(x,z) + Dz(z)} = min{2+1 , 7+0} = 3 32 node y table node z table cost to from 5-25Network Layer: Control Plane
- 26. x y z x y z 0 2 3 from cost to x y z x y z 0 2 7 from cost to x y z x y z 0 2 3 from cost to x y z x y z 0 2 3 from cost to x y z x y z 0 2 7 from cost to 2 0 1 7 1 0 2 0 1 3 1 0 2 0 1 3 1 0 2 0 1 3 1 0 2 0 1 3 1 0 time x y z x y z 0 2 7 ∞ ∞ ∞ ∞ ∞ ∞ from cost to fromfrom x y z x y z 0 x y z x y z ∞ ∞ ∞ ∞ ∞ cost to x y z x y z ∞ ∞ ∞ 7 1 0 cost to ∞ 2 0 1 ∞ ∞ ∞ 2 0 1 7 1 0 time x z 12 7 y node x table Dx(y) = min{c(x,y) + Dy(y), c(x,z) + Dz(y)} = min{2+0 , 7+1} = 2 Dx(z) = min{c(x,y) + Dy(z), c(x,z) + Dz(z)} = min{2+1 , 7+0} = 3 32 node y table node z table cost to from 5-26Network Layer: Control Plane
- 27. Distance vector: link cost changes link cost changes: node detects local link cost change updates routing info, recalculates distance vector if DV changes, notify neighbors“good news travels fast” x z 14 50 y 1 t0 : y detects link-cost change, updates its DV, informs its neighbors. t1 : z receives update from y, updates its table, computes new least cost to x , sends its neighbors its DV. t2 : y receives z’s update, updates its distance table. y’s least costs do not change, so y does not send a message to z. 5-27Network Layer: Control Plane * Check out the online interactive exercises for more examples: http://gaia.cs.umass.edu/kurose_ross/interactive/
- 28. Distance vector: link cost changes link cost changes: node detects local link cost change bad news travels slow - “count to infinity” problem! 44 iterations before algorithm stabilizes: see text x z 14 50 y 60 poisoned reverse: If Z routes through Y to get to X : Z tells Y its (Z’s) distance to X is infinite (so Y won’t route to X via Z) will this completely solve count to infinity problem? 5-28Network Layer: Control Plane
- 29. Comparison of LS and DV algorithms message complexity LS: with n nodes, E links, O(nE) msgs sent DV: exchange between neighbors only • convergence time varies speed of convergence LS: O(n2) algorithm requires O(nE) msgs • may have oscillations DV: convergence time varies • may be routing loops • count-to-infinity problem robustness: what happens if router malfunctions? LS: • node can advertise incorrect link cost • each node computes only its own table DV: • DV node can advertise incorrect path cost • each node’s table used by others • error propagate thru network 5-29Network Layer: Control Plane
- 30. 5.1 introduction 5.2 routing protocols link state distance vector 5.3 intra-AS routing in the Internet: OSPF 5.4 routing among the ISPs: BGP 5.5 The SDN control plane 5.6 ICMP: The Internet Control Message Protocol 5.7 Network management and SNMP Chapter 5: outline 5-30Network Layer: Control Plane
- 31. Making routing scalable scale: with billions of destinations: can’t store all destinations in routing tables! routing table exchange would swamp links! administrative autonomy internet = network of networks each network admin may want to control routing in its own network our routing study thus far - idealized all routers identical network “flat” … not true in practice 5-31Network Layer: Control Plane
- 32. aggregate routers into regions known as “autonomous systems” (AS) (a.k.a. “domains”) inter-AS routing routing among AS’es gateways perform inter- domain routing (as well as intra-domain routing) Internet approach to scalable routing intra-AS routing routing among hosts, routers in same AS (“network”) all routers in AS must run same intra-domain protocol routers in different AS can run different intra-domain routing protocol gateway router: at “edge” of its own AS, has link(s) to router(s) in other AS’es 5-32Network Layer: Control Plane
- 33. 3b 1d 3a 1c 2a AS3 AS1 AS2 1a 2c 2b 1b Intra-AS Routing algorithm Inter-AS Routing algorithm Forwarding table 3c Interconnected ASes forwarding table configured by both intra- and inter-AS routing algorithm • intra-AS routing determine entries for destinations within AS • inter-AS & intra-AS determine entries for external destinations5-33Network Layer: Control Plane
- 34. Inter-AS tasks suppose router in AS1 receives datagram destined outside of AS1: • router should forward packet to gateway router, but which one? AS1 must: 1. learn which dests are reachable through AS2, which through AS3 2. propagate this reachability info to all routers in AS1 job of inter-AS routing! AS3 AS2 3b 3c 3a AS1 1c 1a 1d 1b 2a 2c 2b other networks other networks 5-34Network Layer: Control Plane
- 35. Intra-AS Routing also known as interior gateway protocols (IGP) most common intra-AS routing protocols: • RIP: Routing Information Protocol • OSPF: Open Shortest Path First (IS-IS protocol essentially same as OSPF) • IGRP: Interior Gateway Routing Protocol (Cisco proprietary for decades, until 2016) 5-35Network Layer: Control Plane
- 36. OSPF (Open Shortest Path First) “open”: publicly available uses link-state algorithm • link state packet dissemination • topology map at each node • route computation using Dijkstra’s algorithm router floods OSPF link-state advertisements to all other routers in entire AS • carried in OSPF messages directly over IP (rather than TCP or UDP • link state: for each attached link IS-IS routing protocol: nearly identical to OSPF 5-36Network Layer: Control Plane
- 37. OSPF “advanced” features security: all OSPF messages authenticated (to prevent malicious intrusion) multiple same-cost paths allowed (only one path in RIP) for each link, multiple cost metrics for different TOS (e.g., satellite link cost set low for best effort ToS; high for real-time ToS) integrated uni- and multi-cast support: • Multicast OSPF (MOSPF) uses same topology data base as OSPF hierarchical OSPF in large domains. 5-37Network Layer: Control Plane
- 38. Hierarchical OSPF boundary router backbone router area 1 area 2 area 3 backbone area border routers internal routers 5-38Network Layer: Control Plane
- 39. two-level hierarchy: local area, backbone. • link-state advertisements only in area • each nodes has detailed area topology; only know direction (shortest path) to nets in other areas. area border routers: “summarize” distances to nets in own area, advertise to other Area Border routers. backbone routers: run OSPF routing limited to backbone. boundary routers: connect to other AS’es. Hierarchical OSPF 5-39Network Layer: Control Plane
- 40. 5.1 introduction 5.2 routing protocols link state distance vector 5.3 intra-AS routing in the Internet: OSPF 5.4 routing among the ISPs: BGP 5.5 The SDN control plane 5.6 ICMP: The Internet Control Message Protocol 5.7 Network management and SNMP Chapter 5: outline 5-40Network Layer: Control Plane
- 41. Internet inter-AS routing: BGP BGP (Border Gateway Protocol): the de facto inter-domain routing protocol • “glue that holds the Internet together” BGP provides each AS a means to: • eBGP: obtain subnet reachability information from neighboring ASes • iBGP: propagate reachability information to all AS-internal routers. • determine “good” routes to other networks based on reachability information and policy allows subnet to advertise its existence to rest of Internet: “I am here” 5-41Network Layer: Control Plane
- 42. eBGP, iBGP connections eBGP connectivity iBGP connectivity 1b 1d 1c1a 2b 2d 2c2a 3b 3d 3c3a AS 2 AS 3AS 1 5-42Network Layer: Control Plane 1c ∂ ∂ gateway routers run both eBGP and iBGP protools
- 43. BGP basics when AS3 gateway router 3a advertises path AS3,X to AS2 gateway router 2c: • AS3 promises to AS2 it will forward datagrams towards X BGP session: two BGP routers (“peers”) exchange BGP messages over semi-permanent TCP connection: • advertising paths to different destination network prefixes (BGP is a “path vector” protocol) 1b 1d 1c1a 2b 2d 2c2a 3b 3d 3c3a AS 2 AS 3 AS 1 X BGP advertisement: AS3, X 5-43Network Layer: Control Plane
- 44. Path attributes and BGP routes advertised prefix includes BGP attributes • prefix + attributes = “route” two important attributes: • AS-PATH: list of ASes through which prefix advertisement has passed • NEXT-HOP: indicates specific internal-AS router to next-hop AS Policy-based routing: • gateway receiving route advertisement uses import policy to accept/decline path (e.g., never route through AS Y). • AS policy also determines whether to advertise path to other other neighboring ASes 5-44Network Layer: Control Plane
- 45. BGP path advertisement Based on AS2 policy, AS2 router 2c accepts path AS3,X, propagates (via iBGP) to all AS2 routers 1b 1d 1c1a 2b 2d 2c2a 3b 3d 3c3a AS2 AS3 AS1 X AS3,X AS2,AS3,X AS2 router 2c receives path advertisement AS3,X (via eBGP) from AS3 router 3a Based on AS2 policy, AS2 router 2a advertises (via eBGP) path AS2, AS3, X to AS1 router 1c 5-45Network Layer: Control Plane
- 46. BGP path advertisement AS1 gateway router 1c learns path AS2,AS3,X from 2a 1b 1d 1c1a 2b 2d 2c2a 3b 3d 3c3a AS2 AS3 AS1 X AS3,X AS2,AS3,X gateway router may learn about multiple paths to destination: AS1 gateway router 1c learns path AS3,X from 3a Based on policy, AS1 gateway router 1c chooses path AS3,X, and advertises path within AS1 via iBGP 5-46Network Layer: Control Plane
- 47. BGP messages BGP messages exchanged between peers over TCP connection BGP messages: • OPEN: opens TCP connection to remote BGP peer and authenticates sending BGP peer • UPDATE: advertises new path (or withdraws old) • KEEPALIVE: keeps connection alive in absence of UPDATES; also ACKs OPEN request • NOTIFICATION: reports errors in previous msg; also used to close connection 5-47Network Layer: Control Plane
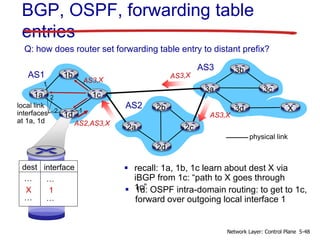
- 48. BGP, OSPF, forwarding table entries recall: 1a, 1b, 1c learn about dest X via iBGP from 1c: “path to X goes through 1c” 1b 1d 1c1a 2b 2d 2c2a 3b 3d 3c3a AS2 AS3 AS1 X AS3,X AS2,AS3,X 1d: OSPF intra-domain routing: to get to 1c, forward over outgoing local interface 1 Q: how does router set forwarding table entry to distant prefix? 12 1 2 dest interface … … X … … 1 physical link local link interfaces at 1a, 1d 5-48Network Layer: Control Plane
- 49. BGP, OSPF, forwarding table entries recall: 1a, 1b, 1c learn about dest X via iBGP from 1c: “path to X goes through 1c” 1b 1d 1c1a 2b 2d 2c2a 3b 3d 3c3a AS2 AS3 AS1 X 1d: OSPF intra-domain routing: to get to 1c, forward over outgoing local interface 1 Q: how does router set forwarding table entry to distant prefix? dest interface … … X … … 2 1a: OSPF intra-domain routing: to get to 1c, forward over outgoing local interface 2 1 2 5-49Network Layer: Control Plane
- 50. BGP route selection router may learn about more than one route to destination AS, selects route based on: 1. local preference value attribute: policy decision 2. shortest AS-PATH 3. closest NEXT-HOP router: hot potato routing 4. additional criteria 5-50Network Layer: Control Plane
- 51. Hot Potato Routing 2d learns (via iBGP) it can route to X via 2a or 2c hot potato routing: choose local gateway that has least intra-domain cost (e.g., 2d chooses 2a, even though more AS hops to X): don’t worry about inter-domain cost! 1b 1d 1c1a 2b 2d 2c2a 3b 3d 3c3a AS2 AS3 AS1 X AS3,X AS1,AS3,X OSPF link weights 201 152 112 263 5-51Network Layer: Control Plane
- 52. A advertises path Aw to B and to C B chooses not to advertise BAw to C: B gets no “revenue” for routing CBAw, since none of C, A, w are B’s customers C does not learn about CBAw path C will route CAw (not using B) to get to w A B C W X Y legend: customer network: provider network Suppose an ISP only wants to route traffic to/from its customer networks (does not want to carry transit traffic between other ISPs) 5-52Network Layer: Control Plane BGP: achieving policy via advertisements
- 53. BGP: achieving policy via advertisements A,B,C are provider networks X,W,Y are customer (of provider networks) X is dual-homed: attached to two networks policy to enforce: X does not want to route from B to C via X .. so X will not advertise to B a route to C A B C W X Y legend: customer network: provider network Suppose an ISP only wants to route traffic to/from its customer networks (does not want to carry transit traffic between other ISPs) 5-53Network Layer: Control Plane
- 54. Why different Intra-, Inter-AS routing ? policy: inter-AS: admin wants control over how its traffic routed, who routes through its net. intra-AS: single admin, so no policy decisions needed scale: hierarchical routing saves table size, reduced update traffic performance: intra-AS: can focus on performance inter-AS: policy may dominate over performance 5-54Network Layer: Control Plane
- 55. 5.1 introduction 5.2 routing protocols link state distance vector 5.3 intra-AS routing in the Internet: OSPF 5.4 routing among the ISPs: BGP 5.5 The SDN control plane 5.6 ICMP: The Internet Control Message Protocol 5.7 Network management and SNMP Chapter 5: outline 5-55Network Layer: Control Plane
- 56. Software defined networking (SDN) Internet network layer: historically has been implemented via distributed, per-router approach • monolithic router contains switching hardware, runs proprietary implementation of Internet standard protocols (IP, RIP, IS-IS, OSPF, BGP) in proprietary router OS (e.g., Cisco IOS) • different “middleboxes” for different network layer functions: firewalls, load balancers, NAT boxes, .. ~2005: renewed interest in rethinking network control plane 5-56Network Layer: Control Plane
- 57. Recall: per-router control plane Routing Algorithm Individual routing algorithm components in each and every router interact with each other in control plane to compute forwarding tables data plane control plane 5-57Network Layer: Control Plane
- 58. data plane control plane Recall: logically centralized control plane A distinct (typically remote) controller interacts with local control agents (CAs) in routers to compute forwarding tables Remote Controller CA CA CA CA CA 5-58Network Layer: Control Plane
- 59. Software defined networking (SDN) Why a logically centralized control plane? easier network management: avoid router misconfigurations, greater flexibility of traffic flows table-based forwarding (recall OpenFlow API) allows “programming” routers • centralized “programming” easier: compute tables centrally and distribute • distributed “programming: more difficult: compute tables as result of distributed algorithm (protocol) implemented in each and every router open (non-proprietary) implementation of control plane 5-59Network Layer: Control Plane
- 60. Vertically integrated Closed, proprietary Slow innovation Small industry Specialized Operating System Specialized Hardware Ap p Ap p Ap p Ap p Ap p Ap p Ap p Ap p Ap p Ap p App Specialized Applications Horizontal Open interfaces Rapid innovation Huge industry Microprocessor Open Interface Linux Mac OS Windows (OS) or or Open Interface Analogy: mainframe to PC evolution* * Slide courtesy: N. McKeown 5-60Network Layer: Control Plane
- 61. Traffic engineering: difficult traditional routing Q: what if network operator wants u-to-z traffic to flow along uvwz, x-to-z traffic to flow xwyz? A: need to define link weights so traffic routing algorithm computes routes accordingly (or need a new routing algorithm)! Link weights are only control “knobs”: wrong! 5-61Network Layer: Control Plane 2 2 1 3 1 1 2 5 3 5 v w u z yx
- 62. Traffic engineering: difficult Q: what if network operator wants to split u-to-z traffic along uvwz and uxyz (load balancing)? A: can’t do it (or need a new routing algorithm) 5-62Network Layer: Control Plane 2 2 1 3 1 1 2 5 3 5 v w u z yx
- 63. yx wv z 2 2 1 3 1 1 2 5 3 5 Traffic engineering: difficult u v x w y z Q: what if w wants to route blue and red traffic differently? A: can’t do it (with destination based forwarding, and LS, DV routing) Networking 401 5-63Network Layer: Control Plane
- 64. Software defined networking (SDN) data plane control plane Remote Controller CA CA CA CA CA 1: generalized“ flow- based” forwarding (e.g., OpenFlow) 2. control, data plane separation 3. control plane functions external to data- plane switches … 4. programmable control applications routing access control load balance 5-64Network Layer: Control Plane
- 65. SDN perspective: data plane switches Data plane switches fast, simple, commodity switches implementing generalized data-plane forwarding (Section 4.4) in hardware switch flow table computed, installed by controller API for table-based switch control (e.g., OpenFlow) • defines what is controllable and what is not protocol for communicating with controller (e.g., OpenFlow) data plane control plane SDN Controller (network operating system) …routing access control load balance southbound API northbound API SDN-controlled switches network-control applications 5-65Network Layer: Control Plane
- 66. SDN perspective: SDN controller SDN controller (network OS): maintain network state information interacts with network control applications “above” via northbound API interacts with network switches “below” via southbound API implemented as distributed system for performance, scalability, fault-tolerance, robustness data plane control plane SDN Controller (network operating system) …routing access control load balance southbound API northbound API SDN-controlled switches network-control applications 5-66Network Layer: Control Plane
- 67. SDN perspective: control applications network-control apps: “brains” of control: implement control functions using lower-level services, API provided by SND controller unbundled: can be provided by 3rd party: distinct from routing vendor, or SDN controller data plane control plane SDN Controller (network operating system) …routing access control load balance southbound API northbound API SDN-controlled switches network-control applications 5-67Network Layer: Control Plane
- 68. Network-wide distributed, robust state management Communication to/from controlled devices Link-state info switch infohost info statistics flow tables… … OpenFlow SNMP… network graph intent RESTful API … Interface, abstractions for network control apps SDN controller routing access control load balance Components of SDN controller communication layer: communicate between SDN controller and controlled switches Network-wide state management layer: state of networks links, switches, services: a distributed database Interface layer to network control apps: abstractions API 5-68Network Layer: Control Plane
- 69. OpenFlow protocol operates between controller, switch TCP used to exchange messages • optional encryption three classes of OpenFlow messages: • controller-to-switch • asynchronous (switch to controller) • symmetric (misc) OpenFlow Controller 5-69Network Layer: Control Plane
- 70. OpenFlow: controller-to-switch messages Key controller-to-switch messages features: controller queries switch features, switch replies configure: controller queries/sets switch configuration parameters modify-state: add, delete, modify flow entries in the OpenFlow tables packet-out: controller can send this packet out of OpenFlow Controller 5-70Network Layer: Control Plane
- 71. OpenFlow: switch-to-controller messages Key switch-to-controller messages packet-in: transfer packet (and its control) to controller. See packet-out message from controller flow-removed: flow table entry deleted at switch port status: inform controller of a change on a port. Fortunately, network operators don’t “program” switches by creating/sending OpenFlow messages directly. Instead use higher-level abstraction at controller OpenFlow Controller 5-71Network Layer: Control Plane
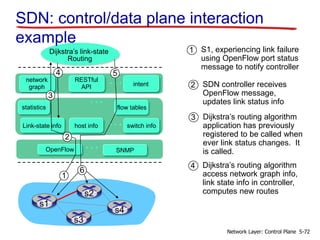
- 72. Link-state info switch infohost info statistics flow tables … … OpenFlow SNMP … network graph intent RESTful API … 1 2 3 4 5 Dijkstra’s link-state Routing s1 s2 s3 s4 SDN: control/data plane interaction example S1, experiencing link failure using OpenFlow port status message to notify controller 1 SDN controller receives OpenFlow message, updates link status info 2 Dijkstra’s routing algorithm application has previously registered to be called when ever link status changes. It is called. 3 Dijkstra’s routing algorithm access network graph info, link state info in controller, computes new routes 4 5-72Network Layer: Control Plane
- 73. Link-state info switch infohost info statistics flow tables … … OpenFlow SNMP … network graph intent RESTful API … 1 2 3 4 5 Dijkstra’s link-state Routing s1 s2 s3 s4 SDN: control/data plane interaction example link state routing app interacts with flow-table- computation component in SDN controller, which computes new flow tables needed 5 Controller uses OpenFlow to install new tables in switches that need updating 6 5-73Network Layer: Control Plane
- 74. topology manager Basic Network Service Functions REST API OpenFlow 1.0 … SNMP OVSDB forwarding manager switch manager host manager stats manager Network service apps Service Abstraction Layer (SAL) Access Control Traffic Engineering … OpenDaylight (ODL) controller ODL Lithium controller network apps may be contained within, or be external to SDN controller Service Abstraction Layer: interconnects internal, external applications and services 5-74Network Layer: Control Plane
- 75. Network control apps … REST API ONOS distributed core southbound abstractions, protocolsOpenFlow Netconf OVSDB device link host flow packet northbound abstractions, protocols Intent statisticsdevices hosts links paths flow rules topology ONOS controller control apps separate from controller intent framework: high-level specification of service: what rather than how considerable emphasis on distributed core: service reliability, replication performance scaling 5-75Network Layer: Control Plane
- 76. SDN: selected challenges hardening the control plane: dependable, reliable, performance-scalable, secure distributed system • robustness to failures: leverage strong theory of reliable distributed system for control plane • dependability, security: “baked in” from day one? networks, protocols meeting mission-specific requirements • e.g., real-time, ultra-reliable, ultra-secure Internet-scaling 5-76Network Layer: Control Plane
- 77. 5.1 introduction 5.2 routing protocols link state distance vector 5.3 intra-AS routing in the Internet: OSPF 5.4 routing among the ISPs: BGP 5.5 The SDN control plane 5.6 ICMP: The Internet Control Message Protocol 5.7 Network management and SNMP Chapter 5: outline 5-77Network Layer: Control Plane
- 78. ICMP: internet control message protocol used by hosts & routers to communicate network-level information • error reporting: unreachable host, network, port, protocol • echo request/reply (used by ping) network-layer “above” IP: • ICMP msgs carried in IP datagrams ICMP message: type, code plus first 8 bytes of IP datagram causing error Type Code description 0 0 echo reply (ping) 3 0 dest. network unreachable 3 1 dest host unreachable 3 2 dest protocol unreachable 3 3 dest port unreachable 3 6 dest network unknown 3 7 dest host unknown 4 0 source quench (congestion control - not used) 8 0 echo request (ping) 9 0 route advertisement 10 0 router discovery 11 0 TTL expired 12 0 bad IP header 5-78Network Layer: Control Plane
- 79. Traceroute and ICMP source sends series of UDP segments to destination • first set has TTL =1 • second set has TTL=2, etc. • unlikely port number when datagram in nth set arrives to nth router: • router discards datagram and sends source ICMP message (type 11, code 0) • ICMP message include name of router & IP address when ICMP message arrives, source records RTTs stopping criteria: UDP segment eventually arrives at destination host destination returns ICMP “port unreachable” message (type 3, code 3) source stops 3 probes 3 probes 3 probes 5-79Network Layer: Control Plane
- 80. 5.1 introduction 5.2 routing protocols link state distance vector 5.3 intra-AS routing in the Internet: OSPF 5.4 routing among the ISPs: BGP 5.5 The SDN control plane 5.6 ICMP: The Internet Control Message Protocol 5.7 Network management and SNMP Chapter 5: outline 5-80Network Layer: Control Plane
- 81. What is network management? autonomous systems (aka “network”): 1000s of interacting hardware/software components other complex systems requiring monitoring, control: • jet airplane • nuclear power plant • others? "Network management includes the deployment, integration and coordination of the hardware, software, and human elements to monitor, test, poll, configure, analyze, evaluate, and control the network and element resources to meet the real-time, operational performance, and Quality of Service requirements at a reasonable cost." 5-81Network Layer: Control Plane
- 82. Infrastructure for network management managed device managed device managed device managed device definitions: managed devices contain managed objects whose data is gathered into a Management Information Base (MIB) managing entity data managing entity agent data agent data network management protocol managed device agent data agent data agent data 5-82Network Layer: Control Plane
- 83. SNMP protocol Two ways to convey MIB info, commands: agent data managed device managing entity agent data managed device managing entity trap msg request request/response mode trap mode response 5-83Network Layer: Control Plane
- 84. SNMP protocol: message types GetRequest GetNextRequest GetBulkRequest manager-to-agent: “get me data” (data instance, next data in list, block of data) Message type Function InformRequest manager-to-manager: here’s MIB value SetRequest manager-to-agent: set MIB value Response Agent-to-manager: value, response to Request Trap Agent-to-manager: inform manager of exceptional event 5-84Network Layer: Control Plane
- 85. SNMP protocol: message formats …. PDU type (0-3) Request ID Error Status (0-5) Error Index Name Value Name Value …. PDU type 4 Enterprise Agent Addr Trap Type (0-7) Specific code Time stamp Name Value Get/set header Variables to get/set Trap header Trap info SNMP PDU 5-85Network Layer: Control Plane More on network management: see earlier editions of text!
- 86. Chapter 5: summary we’ve learned a lot! approaches to network control plane • per-router control (traditional) • logically centralized control (software defined networking) traditional routing algorithms • implementation in Internet: OSPF, BGP SDN controllers • implementation in practice: ODL, ONOS Internet Control Message Protocol network management next stop: link layer! 5-86Network Layer: Control Plane





















![Distance vector algorithm
Dx(y) = estimate of least cost from x to y
• x maintains distance vector Dx = [Dx(y): y є N ]
node x:
• knows cost to each neighbor v: c(x,v)
• maintains its neighbors’ distance vectors.
For each neighbor v, x maintains
Dv = [Dv(y): y є N ]
5-22Network Layer: Control Plane](https://image.slidesharecdn.com/chapter5v701-200606183824/85/Chapter-5-Computer-Networking-a-top-down-Approach-7th-22-320.jpg)


































































































































![[HIFLUX] Lok Fitting&Valve Catalog 2025 (Eng)](https://cdn.slidesharecdn.com/ss_thumbnails/lokfittingen-250528072439-8696f1c6-thumbnail.jpg?width=560&fit=bounds)










![[HIFLUX] High Pressure Tube Support Catalog 2025](https://cdn.slidesharecdn.com/ss_thumbnails/tubesupporten-250529073613-16c22974-thumbnail.jpg?width=560&fit=bounds)







