Circuit Switching, Packet Switching, Virtual Circuit Networks and Datagram Networks
22 likes10,156 views
This Slide includes the description about Circuit Switching, Packet Switching, Virtual Circuit Networks and Datagram Networks
1 of 25
Downloaded 247 times





















Ad
Recommended
Delay , Loss & Throughput



Delay , Loss & ThroughputTutor in Tuition Classes Delay refers to the time taken to transfer a message from sender to receiver. It is calculated based on processing delay, queuing delay, transmission delay, and propagation delay. Packet loss occurs when a router's queue is full and it must drop packets. Bandwidth is the maximum rate of data transfer, while throughput is the actual rate of successful data transfer from one point to another.
Presentation on Transmission Media



Presentation on Transmission MediaSyed Ahmed Zaki This document discusses different types of transmission media used for data communication. It describes guided media such as twisted pair cables, coaxial cables, and fiber optic cables. It also covers unguided or wireless media such as radio waves, microwaves, and infrared. For each medium, it provides details on their characteristics, applications, advantages and disadvantages. The document aims to classify and explain the basic concepts of different transmission media and their use in data communication networks.
Circuit and packet_switching



Circuit and packet_switchinghoanv Packet switching and circuit switching are two different technologies for sending messages over networks. Packet switching breaks messages into packets that can take different routes to the destination, while circuit switching establishes a dedicated connection for the duration of the call. Each approach has advantages - packet switching uses bandwidth efficiently but can experience delays, while circuit switching guarantees quality but is inefficient. Modern networks are shifting more towards packet switching as it allows for easier scaling.
Computer aided software engineering



Computer aided software engineeringČhauÐhařÿ Faísal Ãlï This document discusses computer aided software engineering (CASE) tools. It defines CASE tools as software tools that help with the development and maintenance of other software. The document then describes the need for CASE tools to speed up development, lists categories of tools including diagram, project management, documentation and quality assurance tools, and discusses how organizations use CASE tools and the advantages they provide like improved quality, productivity and documentation.
Multiplexing



MultiplexingAman Jaiswal This document discusses different types of multiplexing techniques. It describes that multiplexing allows simultaneous transmission of multiple signals across a single data link using a multiplexer device. At the receiving end, a demultiplexer separates the combined signals. The key types of multiplexing covered are frequency division multiplexing (FDM), time division multiplexing (TDM), and wave division multiplexing (WDM). FDM uses different frequencies, TDM divides time into slots, and WDM uses different light wavelengths. Synchronous and asynchronous TDM are also explained, with synchronous TDM assigning fixed time slots and asynchronous using flexible slots.
Persuasive Writing



Persuasive WritingUniversity of Santo Tomas This document provides guidance on writing persuasive essays. It explains that the goal of persuasive writing is to convince the reader of a position through arguments and evidence. It recommends choosing a clear thesis, researching to support at least three main arguments, addressing alternative viewpoints, and concluding by restating the thesis. The document also provides examples and tips for each section, such as using statistics, questions or stories to engage the reader in the introduction and calling readers to action in the conclusion.
Min-Max algorithm



Min-Max algorithmDr. C.V. Suresh Babu The minmax algorithm is used in two-player turn-based games to determine the optimal move for a player assuming the opponent plays optimally. It works by having one player act as the maximizer trying to maximize their score, and the other as the minimizer trying to minimize the score. The algorithm analyzes all possible moves and countermoves to determine the outcome with the best score for the maximizer. It is optimal if both players play optimally but has limitations due to its exhaustive search of all possibilities.
Multiplexing : FDM



Multiplexing : FDMDr Rajiv Srivastava These slides cover a topic on Multiplexing in Data Communication. All the slides are explained in a very simple manner.
Computer Networks Unit 1 Introduction and Physical Layer 



Computer Networks Unit 1 Introduction and Physical Layer Dr. SELVAGANESAN S This document discusses data communication and computer networks. It defines data communication as the exchange of data between devices via transmission medium. A data communication system has five components: sender, receiver, message, medium, and protocol. Communication can be simplex, half-duplex, or full-duplex. The document also defines networks, explaining that a network allows interconnected devices to communicate and share resources. Local area networks (LANs), metropolitan area networks (MANs), and wide area networks (WANs) are described as the main categories of networks.
Network Layer design Issues.pptx



Network Layer design Issues.pptxAcad The network layer provides two main services: connectionless and connection-oriented. Connectionless service routes packets independently through routers using destination addresses and routing tables. Connection-oriented service establishes a virtual circuit between source and destination, routing all related traffic along the pre-determined path. The document also discusses store-and-forward packet switching, where packets are stored until fully received before being forwarded, and services provided to the transport layer like uniform addressing.
Transmission Control Protocol (TCP)



Transmission Control Protocol (TCP)k33a The document discusses the key features and mechanisms of the Transmission Control Protocol (TCP). It begins with an introduction to TCP's main goals of reliable, in-order delivery of data streams between endpoints. It then covers TCP's connection establishment and termination processes, flow and error control techniques using acknowledgments and retransmissions, and congestion control methods like slow start, congestion avoidance, and detection.
Presentation Routing algorithm



Presentation Routing algorithmBasit Hussain Routing Algorithm
1. Link State Routing Algorithm with an example
2. Distance Vector Routing Algorithm with an example
Mobile Transport layer



Mobile Transport layerPallepati Vasavi This document discusses various approaches to improving TCP performance over mobile networks. It describes Indirect TCP, Snooping TCP, Mobile TCP, optimizations like fast retransmit/recovery and transmission freezing, and transaction-oriented TCP. Each approach is summarized in terms of its key mechanisms, advantages, and disadvantages. Overall, the document evaluates different ways TCP has been adapted to better support mobility and address challenges like frequent disconnections, packet losses during handovers, and high bit error rates over wireless links.
Transport layer 



Transport layer Mukesh Chinta The transport layer provides efficient, reliable, and cost-effective process-to-process delivery by making use of network layer services. The transport layer works through transport entities to achieve its goal of reliable delivery between application processes. It provides an interface for applications to access its services.
Hiperlan



HiperlanThen Murugeshwari HiperLAN was developed as a wireless local area network standard by ETSI to provide higher data rates than early 802.11 standards. HiperLAN Type 1 achieved data rates up to 2 Mbps for ad hoc networking. HiperLAN Type 2 was later developed to provide connection-oriented service up to 54 Mbps, with quality of service guarantees, security, and flexibility. It uses OFDM in the 5 GHz spectrum for robust transmission. While early products only achieved 25 Mbps, the standard provides a framework for higher speeds as technologies advance. HiperLAN is intended to complement wired networks by providing wireless connectivity in hotspot areas like offices, homes, and public places.
Frame relay



Frame relayAyesha Maqsood Frame relay is a high performance WAN protocol that operates at physical and data link layer of the OSI reference model
TCP over wireless slides



TCP over wireless slidesMahesh Rajawat The document discusses various protocols and approaches for improving the performance of TCP over wireless networks. It notes that wireless networks have higher bit error rates, lower bandwidth, and mobility issues compared to wired networks. Several protocols are described that aim to distinguish wireless losses from congestion losses to avoid unnecessary TCP reactions:
- Indirect TCP splits the connection and handles losses locally at the base station. Snoop caches packets at the base station for retransmission.
- Mobile TCP further splits the connection and has the base station defer acknowledgments. It can also inform the sender about handoffs versus interface switches.
- Multiple acknowledgments uses two types of ACKs to isolate the wireless and wired portions of the network.
-
Mobile Network Layer



Mobile Network LayerRahul Hada Mobile Network Layer protocols and mechanisms allow nodes to change their point of attachment to different networks while maintaining ongoing communication. Key concepts include:
- Mobile IP adds mobility support to IP, allowing nodes to use the same IP address even when changing networks. It relies on home agents and care-of addresses.
- Registration allows mobile nodes to inform their home agent of their current location when visiting foreign networks. Tunneling and encapsulation techniques are used to forward packets to mobile nodes' current locations.
- Various routing protocols like DSDV have been developed for mobile ad hoc networks which have no fixed infrastructure and dynamic topologies.
Routing algorithm



Routing algorithmBushra M The network layer is responsible for routing packets from the source to destination. The routing algorithm is the piece of software that decides where a packet goes next (e.g., which output line, or which node on a broadcast channel).For connectionless networks, the routing decision is made for each datagram. For connection-oriented networks, the decision is made once, at circuit setup time.
Routing Issues
The routing algorithm must deal with the following issues:
Correctness and simplicity: networks are never taken down; individual parts (e.g., links, routers) may fail, but the whole network should not.
Stability: if a link or router fails, how much time elapses before the remaining routers recognize the topology change? (Some never do..)
Fairness and optimality: an inherently intractable problem. Definition of optimality usually doesn't consider fairness. Do we want to maximize channel usage? Minimize average delay?
When we look at routing in detail, we'll consider both adaptive--those that take current traffic and topology into consideration--and nonadaptive algorithms.
Mobile IP



Mobile IPMukesh Chinta This ppt contains information about mobile ip, entities, delivery, mobile ip optimizations, mobile ipv4 vs ipv6
Data link layer 



Data link layer Mukesh Chinta This presentation covers the design issues of DLL, Error Correction and detection techniques, Sliding window protocols
Transport layer services



Transport layer servicesMelvin Cabatuan The document discusses transport layer protocols TCP and UDP. It provides an overview of process-to-process communication using transport layer protocols. It describes the roles, services, requirements, addressing, encapsulation, multiplexing, and error control functions of the transport layer. It specifically examines TCP and UDP, comparing their connection-oriented and connectionless services, typical applications, and segment/datagram formats.
switching techniques in data communication and networking



switching techniques in data communication and networkingHarshita Yadav This document discusses different types of network switching: circuit switching, packet switching, and message switching. It describes circuit switching as establishing a dedicated electrical path for communication between two ports. Packet switching breaks communication down into small packets that are routed through the network based on destination addresses. There are two approaches for packet switching - datagram and virtual circuit. Datagram packets can take different paths to the destination while virtual circuit establishes a pre-planned route. Message switching does not establish a dedicated path, and each message is treated independently with the destination address added. The document was submitted by several students to their professor.
Destination Sequenced Distance Vector Routing (DSDV)



Destination Sequenced Distance Vector Routing (DSDV)ArunChokkalingam Proactive routing protocol
Each node maintain a routing table.
Sequence number is used to update the topology information
Update can be done based on event driven or periodic
Observations
May be energy expensive due to high mobility of the nodes
Delay can be minimized, as path to destination is already known to all nodes.
Distance Vector & Link state Routing Algorithm



Distance Vector & Link state Routing AlgorithmMOHIT AGARWAL 1) Each router maintains a routing table containing the outgoing link and distance to reach each destination node. 2) Routers periodically share their routing tables with neighbors so each can update its own table. 3) This allows routers to continuously determine the shortest paths to all destinations as network conditions change.
Media Access Control (MAC Layer)



Media Access Control (MAC Layer)Meenakshi Paul Media Access Control, Random access, ALOHA, CSMA,CSMA/CD,CSMA/CA, Controlled access, Channelization, FDMA,TDMA,CDMA, MAC layer
Congestion control



Congestion controlAman Jaiswal The document discusses congestion control in computer networks. It defines congestion as occurring when the load on a network is greater than the network's capacity. Congestion control aims to control congestion and keep the load below capacity. The document outlines two categories of congestion control: open-loop control, which aims to prevent congestion; and closed-loop control, which detects congestion and takes corrective action using feedback from the network. Specific open-loop techniques discussed include admission control, traffic shaping using leaky bucket and token bucket algorithms, and traffic scheduling.
Error control



Error controlBhupendra sahu Error control techniques allow for detection and correction of errors during data transmission. Error control is implemented at the data link layer using automatic repeat request (ARQ) protocols like stop-and-wait and sliding window. Stop-and-wait involves transmitting a single frame and waiting for an acknowledgment before sending the next frame. Sliding window protocols allow multiple unacknowledged frames to be transmitted by using frame numbers and acknowledging receipt of frames. These protocols detect errors when frames are received out of sequence and trigger retransmission of lost frames.
circuit and virtual circuit switching.pptx



circuit and virtual circuit switching.pptxseetha394884 about circuit switching techniques based on computer networks
Chap 8 switching



Chap 8 switchingMukesh Tekwani Circuit-switched networks establish a dedicated connection between devices before communication can occur. This involves a connection setup phase, data transfer phase, and connection teardown phase. While circuit switching guarantees bandwidth for the connection, it is inefficient because resources are allocated for the entire duration even if no data is being sent. It also has longer delays than packet-switched networks due to the setup and teardown phases. Packet-switched networks break messages into packets that are transmitted independently and may take different routes to the destination, providing more efficient use of network resources but less reliability than circuit switching.
Ad
More Related Content
What's hot (20)
Computer Networks Unit 1 Introduction and Physical Layer 



Computer Networks Unit 1 Introduction and Physical Layer Dr. SELVAGANESAN S This document discusses data communication and computer networks. It defines data communication as the exchange of data between devices via transmission medium. A data communication system has five components: sender, receiver, message, medium, and protocol. Communication can be simplex, half-duplex, or full-duplex. The document also defines networks, explaining that a network allows interconnected devices to communicate and share resources. Local area networks (LANs), metropolitan area networks (MANs), and wide area networks (WANs) are described as the main categories of networks.
Network Layer design Issues.pptx



Network Layer design Issues.pptxAcad The network layer provides two main services: connectionless and connection-oriented. Connectionless service routes packets independently through routers using destination addresses and routing tables. Connection-oriented service establishes a virtual circuit between source and destination, routing all related traffic along the pre-determined path. The document also discusses store-and-forward packet switching, where packets are stored until fully received before being forwarded, and services provided to the transport layer like uniform addressing.
Transmission Control Protocol (TCP)



Transmission Control Protocol (TCP)k33a The document discusses the key features and mechanisms of the Transmission Control Protocol (TCP). It begins with an introduction to TCP's main goals of reliable, in-order delivery of data streams between endpoints. It then covers TCP's connection establishment and termination processes, flow and error control techniques using acknowledgments and retransmissions, and congestion control methods like slow start, congestion avoidance, and detection.
Presentation Routing algorithm



Presentation Routing algorithmBasit Hussain Routing Algorithm
1. Link State Routing Algorithm with an example
2. Distance Vector Routing Algorithm with an example
Mobile Transport layer



Mobile Transport layerPallepati Vasavi This document discusses various approaches to improving TCP performance over mobile networks. It describes Indirect TCP, Snooping TCP, Mobile TCP, optimizations like fast retransmit/recovery and transmission freezing, and transaction-oriented TCP. Each approach is summarized in terms of its key mechanisms, advantages, and disadvantages. Overall, the document evaluates different ways TCP has been adapted to better support mobility and address challenges like frequent disconnections, packet losses during handovers, and high bit error rates over wireless links.
Transport layer 



Transport layer Mukesh Chinta The transport layer provides efficient, reliable, and cost-effective process-to-process delivery by making use of network layer services. The transport layer works through transport entities to achieve its goal of reliable delivery between application processes. It provides an interface for applications to access its services.
Hiperlan



HiperlanThen Murugeshwari HiperLAN was developed as a wireless local area network standard by ETSI to provide higher data rates than early 802.11 standards. HiperLAN Type 1 achieved data rates up to 2 Mbps for ad hoc networking. HiperLAN Type 2 was later developed to provide connection-oriented service up to 54 Mbps, with quality of service guarantees, security, and flexibility. It uses OFDM in the 5 GHz spectrum for robust transmission. While early products only achieved 25 Mbps, the standard provides a framework for higher speeds as technologies advance. HiperLAN is intended to complement wired networks by providing wireless connectivity in hotspot areas like offices, homes, and public places.
Frame relay



Frame relayAyesha Maqsood Frame relay is a high performance WAN protocol that operates at physical and data link layer of the OSI reference model
TCP over wireless slides



TCP over wireless slidesMahesh Rajawat The document discusses various protocols and approaches for improving the performance of TCP over wireless networks. It notes that wireless networks have higher bit error rates, lower bandwidth, and mobility issues compared to wired networks. Several protocols are described that aim to distinguish wireless losses from congestion losses to avoid unnecessary TCP reactions:
- Indirect TCP splits the connection and handles losses locally at the base station. Snoop caches packets at the base station for retransmission.
- Mobile TCP further splits the connection and has the base station defer acknowledgments. It can also inform the sender about handoffs versus interface switches.
- Multiple acknowledgments uses two types of ACKs to isolate the wireless and wired portions of the network.
-
Mobile Network Layer



Mobile Network LayerRahul Hada Mobile Network Layer protocols and mechanisms allow nodes to change their point of attachment to different networks while maintaining ongoing communication. Key concepts include:
- Mobile IP adds mobility support to IP, allowing nodes to use the same IP address even when changing networks. It relies on home agents and care-of addresses.
- Registration allows mobile nodes to inform their home agent of their current location when visiting foreign networks. Tunneling and encapsulation techniques are used to forward packets to mobile nodes' current locations.
- Various routing protocols like DSDV have been developed for mobile ad hoc networks which have no fixed infrastructure and dynamic topologies.
Routing algorithm



Routing algorithmBushra M The network layer is responsible for routing packets from the source to destination. The routing algorithm is the piece of software that decides where a packet goes next (e.g., which output line, or which node on a broadcast channel).For connectionless networks, the routing decision is made for each datagram. For connection-oriented networks, the decision is made once, at circuit setup time.
Routing Issues
The routing algorithm must deal with the following issues:
Correctness and simplicity: networks are never taken down; individual parts (e.g., links, routers) may fail, but the whole network should not.
Stability: if a link or router fails, how much time elapses before the remaining routers recognize the topology change? (Some never do..)
Fairness and optimality: an inherently intractable problem. Definition of optimality usually doesn't consider fairness. Do we want to maximize channel usage? Minimize average delay?
When we look at routing in detail, we'll consider both adaptive--those that take current traffic and topology into consideration--and nonadaptive algorithms.
Mobile IP



Mobile IPMukesh Chinta This ppt contains information about mobile ip, entities, delivery, mobile ip optimizations, mobile ipv4 vs ipv6
Data link layer 



Data link layer Mukesh Chinta This presentation covers the design issues of DLL, Error Correction and detection techniques, Sliding window protocols
Transport layer services



Transport layer servicesMelvin Cabatuan The document discusses transport layer protocols TCP and UDP. It provides an overview of process-to-process communication using transport layer protocols. It describes the roles, services, requirements, addressing, encapsulation, multiplexing, and error control functions of the transport layer. It specifically examines TCP and UDP, comparing their connection-oriented and connectionless services, typical applications, and segment/datagram formats.
switching techniques in data communication and networking



switching techniques in data communication and networkingHarshita Yadav This document discusses different types of network switching: circuit switching, packet switching, and message switching. It describes circuit switching as establishing a dedicated electrical path for communication between two ports. Packet switching breaks communication down into small packets that are routed through the network based on destination addresses. There are two approaches for packet switching - datagram and virtual circuit. Datagram packets can take different paths to the destination while virtual circuit establishes a pre-planned route. Message switching does not establish a dedicated path, and each message is treated independently with the destination address added. The document was submitted by several students to their professor.
Destination Sequenced Distance Vector Routing (DSDV)



Destination Sequenced Distance Vector Routing (DSDV)ArunChokkalingam Proactive routing protocol
Each node maintain a routing table.
Sequence number is used to update the topology information
Update can be done based on event driven or periodic
Observations
May be energy expensive due to high mobility of the nodes
Delay can be minimized, as path to destination is already known to all nodes.
Distance Vector & Link state Routing Algorithm



Distance Vector & Link state Routing AlgorithmMOHIT AGARWAL 1) Each router maintains a routing table containing the outgoing link and distance to reach each destination node. 2) Routers periodically share their routing tables with neighbors so each can update its own table. 3) This allows routers to continuously determine the shortest paths to all destinations as network conditions change.
Media Access Control (MAC Layer)



Media Access Control (MAC Layer)Meenakshi Paul Media Access Control, Random access, ALOHA, CSMA,CSMA/CD,CSMA/CA, Controlled access, Channelization, FDMA,TDMA,CDMA, MAC layer
Congestion control



Congestion controlAman Jaiswal The document discusses congestion control in computer networks. It defines congestion as occurring when the load on a network is greater than the network's capacity. Congestion control aims to control congestion and keep the load below capacity. The document outlines two categories of congestion control: open-loop control, which aims to prevent congestion; and closed-loop control, which detects congestion and takes corrective action using feedback from the network. Specific open-loop techniques discussed include admission control, traffic shaping using leaky bucket and token bucket algorithms, and traffic scheduling.
Error control



Error controlBhupendra sahu Error control techniques allow for detection and correction of errors during data transmission. Error control is implemented at the data link layer using automatic repeat request (ARQ) protocols like stop-and-wait and sliding window. Stop-and-wait involves transmitting a single frame and waiting for an acknowledgment before sending the next frame. Sliding window protocols allow multiple unacknowledged frames to be transmitted by using frame numbers and acknowledging receipt of frames. These protocols detect errors when frames are received out of sequence and trigger retransmission of lost frames.
Similar to Circuit Switching, Packet Switching, Virtual Circuit Networks and Datagram Networks (20)
circuit and virtual circuit switching.pptx



circuit and virtual circuit switching.pptxseetha394884 about circuit switching techniques based on computer networks
Chap 8 switching



Chap 8 switchingMukesh Tekwani Circuit-switched networks establish a dedicated connection between devices before communication can occur. This involves a connection setup phase, data transfer phase, and connection teardown phase. While circuit switching guarantees bandwidth for the connection, it is inefficient because resources are allocated for the entire duration even if no data is being sent. It also has longer delays than packet-switched networks due to the setup and teardown phases. Packet-switched networks break messages into packets that are transmitted independently and may take different routes to the destination, providing more efficient use of network resources but less reliability than circuit switching.
Lecture 2 review of network technologies



Lecture 2 review of network technologiesBatzaya Dashdondog This document provides an overview of network technologies including computer networks, types of networks (LAN and WAN), networking concepts like circuit switching and packet switching, and the OSI model. It compares LANs and WANs, discusses virtual circuits and datagrams, and describes common networking devices like hubs, bridges, and routers.
Switching techniques



Switching techniquesAmit Kumar Circuit switching establishes a dedicated electrical path between source and destination before data transmission, but it wastes bandwidth if no data is being sent and has high initial delays. Store-and-forward switching breaks messages into packets that are transmitted independently between nodes, allowing more efficient use of bandwidth. Packet switching is commonly used as it offers better delay characteristics than message switching and requires less buffer storage than transmitting full messages.
Ravi namboori switching



Ravi namboori switchingRavi namboori This document discusses different switching techniques used in digital networks, including circuit switching, message switching, and packet switching. Circuit switching establishes a dedicated connection between sender and receiver but can have long wait times and inefficient bandwidth usage. Message switching stores and forwards entire messages at each node without dedicated connections, allowing for priority and broadcasting but is incompatible with interactive applications. Packet switching breaks messages into packets that may take different paths to the destination, allowing for more efficient bandwidth sharing but requiring reassembly and possibly retransmission if packets are lost.
Switiching by Ravi Namboori Babson University USA



Switiching by Ravi Namboori Babson University USARavi Namboori Ravi Namboori currently serves as vice president of Data Center Solutions at Unigen. Combining extensive IT experience and leadership skills, Ravi Namboori oversees the entire business unit, motivating and energizing his team to contribute to the strategic vision of the company.
Namboori brings experience from a number of Silicon Valley tech companies to Unigen. During his time as director of IT for Glu Mobile, he established the architecture and carried out the implementation of the company’s data center. Designed to be scalable and reliable, the center provided a high performance environment for Glu Mobile’s e-commerce and gaming business.
Earlier in his career, Ravi Namboori worked for Hewlett-Packard Company (HP) in the Netherlands as a network manager. In this role, he designed the LAN and call center systems for HP’s facility and carried out networking projects to client specifications.
In addition to Microsoft and Novell certifications, Namboori holds seven Cisco professional certifications including a teaching credential. He received his MBA from Babson University’s F. W. Olin Graduate School of Business and his undergraduate degree from DNR College.
Ravi Namboori switching



Ravi Namboori switchingRavi Namboori Ravi Namboori, a Cisco evangelist and an IT entrepreneur, is based out of Bay Area, California. Ravi Namboori holds nine Cisco certifications, in addition to one each from Microsoft and Novell in networking. Ravi Namboori earned his MBA from The F.W. Olin Graduate School of Business at Babson College.
Refers to protocols in which messages are divided into packets before they are sent. Each packet is then transmitted individually and can even follow different routes to its destination. Once all the packets forming a message arrive at the destination, they are recompiled into the original message.
Most modern Wide Area Network (WAN) protocols, including TCP/IP, X.25, and Frame Relay, are based on packet-switching technologies. In contrast, normal telephone service is based on a circuit-switching technology, in which a dedicated line is allocated for transmission between two parties. Circuit-switching is ideal when data must be transmitted quickly and must arrive in the same order in which it's sent. This is the case with most real-time data, such as live audio and video. Packet switching is more efficient and robust for data that can withstand some delays in transmission, such as e-mail messages and Web pages.
A new technology, ATM, attempts to combine the best of both worlds -- the guaranteed delivery of circuit-switched networks and the robustness and efficiency of packet-switching networks.
Ravi Namboori_switching



Ravi Namboori_switchingravi-namboori-babson A network switch (sometimes known as a switching hub) is a computer networking device that is used to connect devices together on a computer network by performing a form of packet switching. A network switch is considered more advanced than a hub because a switch will only send a message to the device that needs or requests it, rather than broadcasting the same message out of each of its ports.
Unit 3 CND physical layer_switching_pranoti doke_MSBTE



Unit 3 CND physical layer_switching_pranoti doke_MSBTEPranoti Doke 3.6 Switching: Circuit-switched networks, Packet switched networks —Datagram approach, virtual circuit approach.
Unit 3 cnd physical layer_switching_pranoti doke_MSBTE



Unit 3 cnd physical layer_switching_pranoti doke_MSBTEPranoti Doke 3.6 Switching: Circuit-switched networks, Packet switched networks —Datagram approach, virtual circuit approach.
Data Communication and Network- Network Layer onward all layers



Data Communication and Network- Network Layer onward all layersDr. Chandrakant Divate Data Communication and Network- Network Layer onward all layers
data communication and networkig fibre optical cable and non fibre cable



data communication and networkig fibre optical cable and non fibre cableSanthanalakshmiSelva2 this is data communicaion and networking. this is in computer network. DCN notes include transmission media Your score increases as you pick a category, fill out a long description and add more tags.
•When data streams are received from network layer, to the data link layer, the number of bits may be less than, equal to, or more than the number of bits transmitted.
•The data link layer has to detect and correct the errors.
•The data link layer breaks the bit stream into discrete frames and computes a short token called checksum.
•Checksum is calculated for each frame and it is attached to the frame when transmitted.
•When the frame arrives the destination the checksum is recomputed.
•If the newly computed value is different from the one contained in the frame, it is discarded and is resent.
8 Packet Switching



8 Packet SwitchingWater Birds (Ali) A presentation prepared by my friend's friend. I have done no editing at all, I'm just uploading the presentation as it is.
Switching



SwitchingMeenakshi Paul Switching, Circuit switched networks, Packet switched network, Datagram networks, Virtual-circuit networks.
Switching Techniques



Switching Techniquestameemyousaf There are two main switching techniques used in communications networks: circuit switching and packet switching. Circuit switching establishes a dedicated communication path between two stations for the duration of the connection. Packet switching transmits data in small packets that are routed individually through the network on a non-dedicated basis, allowing for more efficient use of bandwidth. The telephone system uses circuit switching while the internet uses packet switching, which is more suitable for data traffic since it allows for variable bandwidth and priority routing.
Networks quiz #1 



Networks quiz #1 cairo university This document contains a quiz with multiple choice and completion questions about computer networks. The multiple choice questions cover topics like the services provided by TCP, how routers work using store and forward, what ADSL uses existing phone lines for, and how bandwidth is shared in packet switching networks. The completion questions ask about examples of guided and unguided media, what happens to packets if a router's buffer is full, and to draw graphs explaining bottleneck links, types of delays, and calculating total delay for a frame transmitted over a network with specific bandwidths, distances, and processing delays. It also asks to discuss the OSI layers, their responsibilities, modifications to the OSI model, and encapsulation in the TCP/IP model.
DCN-321-Chiwaya_Lesson7_DataElements_Switching.pdf



DCN-321-Chiwaya_Lesson7_DataElements_Switching.pdfOscarKelvinNsitu This document discusses different methods for switching data in communication networks. It describes circuit switching, packet switching, message switching, and fast packet switching. Circuit switching establishes a dedicated connection for transmission. Packet switching divides data into packets that are routed independently. Message switching stores data at switches before transmission. Fast packet switching reduces overhead to increase throughput. The document provides details on the characteristics and advantages and disadvantages of each switching method.
Topic: Virtual circuit & message switching



Topic: Virtual circuit & message switchingDr Rajiv Srivastava These slides cover a topic on Virtual circuit & message switching in Data Communication. All the slides are explained in a very simple manner. It is useful for engineering students & also for the candidates who want to master data communication & computer networking
Ad
More from Kaushik Panta (13)
Unit - 1 : Introduction to Computers || CSC - 109 || BScCSIT || BIM || BCA ||...



Unit - 1 : Introduction to Computers || CSC - 109 || BScCSIT || BIM || BCA ||...Kaushik Panta This slide includes the details on :
1. Introduction to Computer
2. Advantages and Disadvantages of Computer
3. History of Computer
4. Generations of Computer
5. Analog and Digital Computers
6. Classification of Computer
7. The Computer System
8. The Input - Output System
9. Components of Computer
10. Characteristics of Computer
Chapter 4 : I/O devices



Chapter 4 : I/O devicesKaushik Panta This video includes the details on Input and Output units, I/O Devices, I/O Ports and working mechanism of I/O Units
Computer networks : dial up, wireless, hfcc and dsl



Computer networks : dial up, wireless, hfcc and dslKaushik Panta Dial-up modems use phone lines to establish temporary internet connections, requiring an available phone line. Digital Subscriber Line (DSL) provides broadband internet over phone lines using modem technology, allowing simultaneous internet and phone service. Hybrid Fiber Coaxial (HFC) networks use fiber optic cables for long distances and coaxial cable for short distances, bringing fiber's benefits closer to users. Wireless networks connect devices without cables, avoiding installation costs, and use radio waves to connect laptops and other devices to the internet over various network types.
Final project report on Analysis of Packet on the basis of Delay on IPv6 and ...



Final project report on Analysis of Packet on the basis of Delay on IPv6 and ...Kaushik Panta In a packet network, the term packet delay characterizes as the difference in end-to-end one-
way delay between selected packets in a flow with any lost packets being ignored. The effect is
sometimes referred to as jitter, although the definition is an imprecise fit. The delay is specified
from the start of the packet being transmitted at the source to the start of the packet being
received at the destination. Analysis of packet delay in both protocol IPv4 and IPv6 is
essential to measure network performance.
This project entitled “Analysis of Packet on the basis of Delay on IPv6 and IPv4
Networks in Open Short Path First Routing Protocol ” intends to analyze the packet
delay in both protocol IPv4 and IPv6 under the same condition and find out the fact that
which one is better in term of packet delay parameter of network performance. Due to the
insufficient IPv4 addresses and other issues, the world should migrate to IPv6 in near future.
So, measuring the network parameter is necessary.
OSPF (Open Shortest Path First) is a routing protocol for Internet Protocol networks. It uses
a link state routing algorithm and falls into the group of interior gateway protocols, operating
within a single autonomous system. It is defined as OSPF Version 2 in IPv4 and the updates
for IPv6 are specified as OSPF Version 3.
This project deals with the techniques of measure and analyze the packet delay. As, the
number of Internet users growing exponentially, it is really necessary to reduce the packet
delay in every possible way to improve network performance.
Introduction to Information Technology || Unit - 11 : Multimedia



Introduction to Information Technology || Unit - 11 : MultimediaKaushik Panta This Slide includes the description about Multimedia, Its Characteristics, Elements of Multimedia and their Applications
Introduction to Information technology - Course Intro



Introduction to Information technology - Course IntroKaushik Panta This slide includes the Course information of Introduction to Information technology including its syllabus, course contents, Unit Informations, etc
Computer networks : intro to networking, pros and cons, uses, network edges :...



Computer networks : intro to networking, pros and cons, uses, network edges :...Kaushik Panta Computer networks : intro to networking, pros and cons, uses, network edges : end devices, client server and peer to peer
Computer Networks : CSC - 301 || BScCSIT



Computer Networks : CSC - 301 || BScCSITKaushik Panta A basic Course Introduction of Computer Networks showing the question formats, Units to study, Credit Hours and Others.
Analysis of Packet on the basis of Delay on IPv6 and IPv4 Networks in Open Sh...



Analysis of Packet on the basis of Delay on IPv6 and IPv4 Networks in Open Sh...Kaushik Panta In a packet network, the term packet delay characterizes as the difference in end-to-end one-
way delay between selected packets in a flow with any lost packets being ignored. The effect is
sometimes referred to as jitter, although the definition is an imprecise fit. The delay is specified
from the start of the packet being transmitted at the source to the start of the packet being
received at the destination. Analysis of packet delay in both protocol IPv4 and IPv6 is
essential to measure network performance.
This project entitled “Analysis of Packet on the basis of Delay on IPv6 and IPv4
Networks in Open Short Path First Routing Protocol ” intends to analyze the packet
delay in both protocol IPv4 and IPv6 under the same condition and find out the fact that
which one is better in term of packet delay parameter of network performance. Due to the
insufficient IPv4 addresses and other issues, the world should migrate to IPv6 in near future.
So, measuring the network parameter is necessary.
OSPF (Open Shortest Path First) is a routing protocol for Internet Protocol networks. It uses
a link state routing algorithm and falls into the group of interior gateway protocols, operating
within a single autonomous system. It is defined as OSPF Version 2 in IPv4 and the updates
for IPv6 are specified as OSPF Version 3.
This project deals with the techniques of measure and analyze the packet delay. As, the
number of Internet users growing exponentially, it is really necessary to reduce the packet
delay in every possible way to improve network performance.
Case study on ebay.com



Case study on ebay.comKaushik Panta This document provides an overview of eBay's business model and operations. It discusses:
- eBay was founded in 1995 and is an online marketplace that connects buyers and sellers.
- eBay generates revenue primarily from fees charged to sellers. It also owns PayPal which facilitates online payments.
- Common business models on eBay include reselling inventory purchased in bulk at low costs, dropshipping where suppliers ship directly to buyers, retail arbitrage by finding bargains, and liquidating surplus inventory.
- eBay aims to increase user acquisition, activation, and activity to drive overall marketplace growth and revenue. It focuses on expanding categories and formats like fixed-price listings to support different business models.
E governance in secretariat(sachivalaya vahini)



E governance in secretariat(sachivalaya vahini)Kaushik Panta E governance in secretariat(sachivalaya vahini) is the Project initialed by Government of Karnataka, Bangalore through the
help of Directorate of Information Technology (DIT) to promote e-
governance & to introduce the concept of information and knowledge
management.
Report of case study on an integrated university department information system



Report of case study on an integrated university department information systemKaushik Panta University computer science and engineering departments often have budgets which are comparable with small companies and an integrated system to support all aspects of departmental administration is required. This should support student
records, laboratory administration, the ordering of goods and services, input and output payments, payments made for teaching assistants, research contract reporting, etc. It should be linked to a wider University system responsible for staff salaries etc. Factors which should be taken into account include:
1) Departmental chairmen who use such a system are usually very busy. Even if they are computer literate, they require a system with a straightforward user interface.
2) Users of the system range from secretaries through technicians to teaching and administrative staff. The range of users to be supported is very wide.
3) In some countries, the trend is for Universities is to devolve administration from a central organization to the individual departments. The system must
be able to be expanded to handle future, unforeseen tasks.
4)Sub-systems should be automatically linked so that, for example, the costs of a particular class or laboratory can be computed by considering payments made and received.
Case study on amazon.com



Case study on amazon.comKaushik Panta Amazon started as an online bookstore and has since expanded into many other product categories and business lines. It uses a business model of low prices, vast selection, and convenience for customers. The report analyzes Amazon's lines of business, business models, and e-commerce strategies. It finds that Amazon utilizes various intensive growth strategies like market development, market penetration, product development, and diversification. Its overarching generic strategy is cost leadership to offer competitive prices and gain market share.
Ad
Recently uploaded (20)
World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...



World war-1(Causes & impacts at a glance) PPT by Simanchala Sarab(BABed,sem-4...larencebapu132 This is short and accurate description of World war-1 (1914-18)
It can give you the perfect factual conceptual clarity on the great war
Regards Simanchala Sarab
Student of BABed(ITEP, Secondary stage)in History at Guru Nanak Dev University Amritsar Punjab 🙏🙏
apa-style-referencing-visual-guide-2025.pdf



apa-style-referencing-visual-guide-2025.pdfIshika Ghosh Title: A Quick and Illustrated Guide to APA Style Referencing (7th Edition)
This visual and beginner-friendly guide simplifies the APA referencing style (7th edition) for academic writing. Designed especially for commerce students and research beginners, it includes:
✅ Real examples from original research papers
✅ Color-coded diagrams for clarity
✅ Key rules for in-text citation and reference list formatting
✅ Free citation tools like Mendeley & Zotero explained
Whether you're writing a college assignment, dissertation, or academic article, this guide will help you cite your sources correctly, confidently, and consistent.
Created by: Prof. Ishika Ghosh,
Faculty.
📩 For queries or feedback: [email protected]
Metamorphosis: Life's Transformative Journey



Metamorphosis: Life's Transformative JourneyArshad Shaikh *Metamorphosis* is a biological process where an animal undergoes a dramatic transformation from a juvenile or larval stage to a adult stage, often involving significant changes in form and structure. This process is commonly seen in insects, amphibians, and some other animals.
Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...



Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...Library Association of Ireland
Geography Sem II Unit 1C Correlation of Geography with other school subjects



Geography Sem II Unit 1C Correlation of Geography with other school subjectsProfDrShaikhImran The correlation of school subjects refers to the interconnectedness and mutual reinforcement between different academic disciplines. This concept highlights how knowledge and skills in one subject can support, enhance, or overlap with learning in another. Recognizing these correlations helps in creating a more holistic and meaningful educational experience.
pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulse



pulse ppt.pptx Types of pulse , characteristics of pulse , Alteration of pulsesushreesangita003 what is pulse ?
Purpose
physiology and Regulation of pulse
Characteristics of pulse
factors affecting pulse
Sites of pulse
Alteration of pulse
for BSC Nursing 1st semester
for Gnm Nursing 1st year
Students .
vitalsign
Unit 6_Introduction_Phishing_Password Cracking.pdf



Unit 6_Introduction_Phishing_Password Cracking.pdfKanchanPatil34 Initial stages of attacks, Phishing, Password Cracking, guidelines to prevent password attacks, Strong password, weak password,
How to track Cost and Revenue using Analytic Accounts in odoo Accounting, App...



How to track Cost and Revenue using Analytic Accounts in odoo Accounting, App...Celine George Analytic accounts are used to track and manage financial transactions related to specific projects, departments, or business units. They provide detailed insights into costs and revenues at a granular level, independent of the main accounting system. This helps to better understand profitability, performance, and resource allocation, making it easier to make informed financial decisions and strategic planning.
Biophysics Chapter 3 Methods of Studying Macromolecules.pdf



Biophysics Chapter 3 Methods of Studying Macromolecules.pdfPKLI-Institute of Nursing and Allied Health Sciences Lahore , Pakistan. This chapter provides an in-depth overview of the viscosity of macromolecules, an essential concept in biophysics and medical sciences, especially in understanding fluid behavior like blood flow in the human body.
Key concepts covered include:
✅ Definition and Types of Viscosity: Dynamic vs. Kinematic viscosity, cohesion, and adhesion.
⚙️ Methods of Measuring Viscosity:
Rotary Viscometer
Vibrational Viscometer
Falling Object Method
Capillary Viscometer
🌡️ Factors Affecting Viscosity: Temperature, composition, flow rate.
🩺 Clinical Relevance: Impact of blood viscosity in cardiovascular health.
🌊 Fluid Dynamics: Laminar vs. turbulent flow, Reynolds number.
🔬 Extension Techniques:
Chromatography (adsorption, partition, TLC, etc.)
Electrophoresis (protein/DNA separation)
Sedimentation and Centrifugation methods.
Odoo Inventory Rules and Routes v17 - Odoo Slides



Odoo Inventory Rules and Routes v17 - Odoo SlidesCeline George Odoo's inventory management system is highly flexible and powerful, allowing businesses to efficiently manage their stock operations through the use of Rules and Routes.
SCI BIZ TECH QUIZ (OPEN) PRELIMS XTASY 2025.pptx



SCI BIZ TECH QUIZ (OPEN) PRELIMS XTASY 2025.pptxRonisha Das SCI BIZ TECH QUIZ (OPEN) PRELIMS - XTASY 2025
To study Digestive system of insect.pptx



To study Digestive system of insect.pptxArshad Shaikh Education is one thing no one can take away from you.”
Marie Boran Special Collections Librarian Hardiman Library, University of Gal...



Marie Boran Special Collections Librarian Hardiman Library, University of Gal...Library Association of Ireland Phoenix – A Collaborative Renewal of Children’s and Young People’s Services Clare Doyle - Cork City Libraries
K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schools



K12 Tableau Tuesday - Algebra Equity and Access in Atlanta Public Schoolsdogden2 Algebra 1 is often described as a “gateway” class, a pivotal moment that can shape the rest of a student’s K–12 education. Early access is key: successfully completing Algebra 1 in middle school allows students to complete advanced math and science coursework in high school, which research shows lead to higher wages and lower rates of unemployment in adulthood.
Learn how The Atlanta Public Schools is using their data to create a more equitable enrollment in middle school Algebra classes.
How to manage Multiple Warehouses for multiple floors in odoo point of sale



How to manage Multiple Warehouses for multiple floors in odoo point of saleCeline George The need for multiple warehouses and effective inventory management is crucial for companies aiming to optimize their operations, enhance customer satisfaction, and maintain a competitive edge.
LDMMIA Reiki Master Spring 2025 Mini Updates



LDMMIA Reiki Master Spring 2025 Mini UpdatesLDM Mia eStudios As of Mid to April Ending, I am building a new Reiki-Yoga Series. No worries, they are free workshops. So far, I have 3 presentations so its a gradual process. If interested visit: https://www.slideshare.net/YogaPrincess
https://ldmchapels.weebly.com
Blessings and Happy Spring. We are hitting Mid Season.
How to Customize Your Financial Reports & Tax Reports With Odoo 17 Accounting



How to Customize Your Financial Reports & Tax Reports With Odoo 17 AccountingCeline George The Accounting module in Odoo 17 is a complete tool designed to manage all financial aspects of a business. Odoo offers a comprehensive set of tools for generating financial and tax reports, which are crucial for managing a company's finances and ensuring compliance with tax regulations.
Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...



Michelle Rumley & Mairéad Mooney, Boole Library, University College Cork. Tra...Library Association of Ireland
Biophysics Chapter 3 Methods of Studying Macromolecules.pdf



Biophysics Chapter 3 Methods of Studying Macromolecules.pdfPKLI-Institute of Nursing and Allied Health Sciences Lahore , Pakistan.
Marie Boran Special Collections Librarian Hardiman Library, University of Gal...



Marie Boran Special Collections Librarian Hardiman Library, University of Gal...Library Association of Ireland
Circuit Switching, Packet Switching, Virtual Circuit Networks and Datagram Networks
- 3. Circuit Switching Establishes a dedicated physical path between the sender and receiver of the message before a message is delivered The entire message travels through the established path from sender to the receiver Received Message is Acknowledged by Receiver Same as Telephone Communication
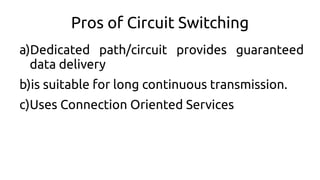
- 5. Pros of Circuit Switching a)Dedicated path/circuit provides guaranteed data delivery b)is suitable for long continuous transmission. c)Uses Connection Oriented Services
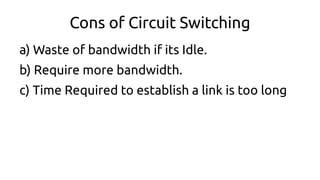
- 6. Cons of Circuit Switching a) Waste of bandwidth if its Idle. b) Require more bandwidth. c) Time Required to establish a link is too long
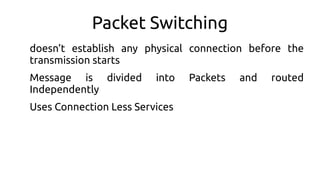
- 8. Packet Switching doesn’t establish any physical connection before the transmission starts Message is divided into Packets and routed Independently Uses Connection Less Services
- 10. Pros of Packet Switching a) High Data Transmission b) No time Lost for Establishing Link c) Faster d) Independent Travel
- 11. Cons of Packet Switching a) Packets May Lost their Routes b) Wrong Order of Packets c) Large Amount of Resources needed to handle Packets
- 13. Circuit Switching Packet Switching Connection Oriented Connection Less Entire Message Have to follow same route during transmission Entire Message can be divided and routed Independently Implemented at Physical Layer Implemented at Network Layer Waste of bandwidth if Idle No Waste of bandwidth if Idle Initially designed for Voice Transmission Initially designed for Data Transmission
- 15. Virtual Circuit Networks Is a packet switching methodology but establishes Link before communication Entire Message must have to follow same Link to destination is connection orientated Virtual circuit is cleared after the data transfer is completed
- 16. Pros of Virtual Circuits Networks a) Uses Connection Oriented Services b) Can use Diferent Physical Links each time
- 17. Cons of Virtual Circuits Networks a) Link Setup Time b) Resilience to the loss of a trunk i.e. no dynamic switching in case of link failure
- 19. Datagram Networks Is a packet switching methodology but no any Dedicated Link Message have to divided into Datagrams and Each Packets are treated Independently Connection Less
- 21. Pros of Datagram Networks a) It is connectionless service b) Every datagrams are treated Independently c) Faster
- 22. Cons of Datagram Networks a) Not Reliable b)Packet May lost and no Service for Retransmission c) Need of High Resources
- 23. Possible Questions a) Explain about Circuit Switching with Pros and Cons b) Explain about Packet Switching with Pros and Cons c) Explain about Virtual Circuit Networks with Pros and Cons d)Explain about Datagram Networks with Pros and Cons e) Compare Circuit Switching and Packet Switching f) How Virtual Circuit Networks are difer from Circuit Switching g) Compare Virtual Circuit Networks with Datagram Networks.
- 24. Next Lecture Dial Up Modem DSL Hybrid Fiber Coaxial Cable Wireless Networks
- 25. Thank You !!!!





